Powerpoint Templates and Google slides for Implementing Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Network Security Model To Effective Implementation Of ICT Strategic Plan Strategy SS
Network Security Model To Effective Implementation Of ICT Strategic Plan Strategy SSThis slide represents the network security model for effective communication in the organization. It covers information regarding security threats, firewalls, virtual private networks, etc.Present the topic in a bit more detail with this Network Security Model To Effective Implementation Of ICT Strategic Plan Strategy SS. Use it as a tool for discussion and navigation on Message Transformation, Secure Message, Security Breaches. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview Of Business ICT Security Data Protection Implementation ICT Strategic Plan Strategy SS
Overview Of Business ICT Security Data Protection Implementation ICT Strategic Plan Strategy SSThis slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc.Present the topic in a bit more detail with this Overview Of Business ICT Security Data Protection Implementation ICT Strategic Plan Strategy SS. Use it as a tool for discussion and navigation on Factor Authentication, Organizations Information, Ensure Confidentiality. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Introduction To Secure Digital Wallets For Financial Omnichannel Banking Services Implementation
Introduction To Secure Digital Wallets For Financial Omnichannel Banking Services ImplementationThis slide covers brief summary of digital wallets provided by banking sector to facilitate financial transactions. The purpose of this template is to provide the benefits derived from using e wallets. It includes benefits such as offering more prominent security, discount and rewards, eliminates role of physical banks, streamlines checkout process, etc. Introducing Introduction To Secure Digital Wallets For Financial Omnichannel Banking Services Implementation to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Digital Wallets, Benefits Of Digital Wallets, Discount Coupons, using this template. Grab it now to reap its full benefits.
-
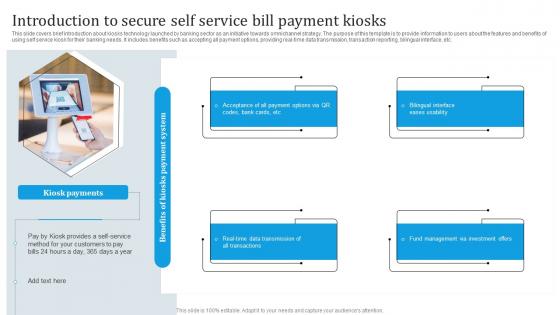 Introduction To Secure Self Service Bill Payment Omnichannel Banking Services Implementation
Introduction To Secure Self Service Bill Payment Omnichannel Banking Services ImplementationThis slide covers brief introduction about kiosks technology launched by banking sector as an initiative towards omnichannel strategy. The purpose of this template is to provide information to users about the features and benefits of using self service kiosk for their banking needs. It includes benefits such as accepting all payment options, providing real time data transmission, transaction reporting, bilingual interface, etc. Increase audience engagement and knowledge by dispensing information using Introduction To Secure Self Service Bill Payment Omnichannel Banking Services Implementation. This template helps you present information on four stages. You can also present information on Payment System, Payment Options, Investment Offers using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SASE IT Best Practices To Implement Cloud Access Security Broker Ppt Powerpoint Microsoft
SASE IT Best Practices To Implement Cloud Access Security Broker Ppt Powerpoint MicrosoftThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this SASE IT Best Practices To Implement Cloud Access Security Broker Ppt Powerpoint Microsoft. Dispense information and present a thorough explanation of Build Visibility, Forecast Risk, Release CASB using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SASE IT Budget To Implement Secure Access Service Edge Ppt Powerpoint Designs
SASE IT Budget To Implement Secure Access Service Edge Ppt Powerpoint DesignsThis slide depicts the budget calculation for implementing a secure access service edge model in an organization. The purpose of this slide is to showcase the estimated and actual cost and variance for SASE model spending. The key components include SD-WAN, SWG, ZTNA, CASB, and FWaaS. Present the topic in a bit more detail with this SASE IT Budget To Implement Secure Access Service Edge Ppt Powerpoint Designs. Use it as a tool for discussion and navigation on Secure Web Gateway, Zero Trust Network Access, Cloud Access Security Broker. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SASE IT Checklist To Implement Secure Access Service Edge Ppt Powerpoint Demonstration
SASE IT Checklist To Implement Secure Access Service Edge Ppt Powerpoint DemonstrationPresent the topic in a bit more detail with this SASE IT Checklist To Implement Secure Access Service Edge Ppt Powerpoint Demonstration. Use it as a tool for discussion and navigation on Test And Troubleshoot, Incorporate Zero Trust Solutions, SASE Goals And Requirements. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SASE IT Cloud Access Security Broker Implementation Models Ppt Powerpoint Template
SASE IT Cloud Access Security Broker Implementation Models Ppt Powerpoint TemplateThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Introducing SASE IT Cloud Access Security Broker Implementation Models Ppt Powerpoint Template to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on API Scanning, Forward Proxy, Reverse Proxy, using this template. Grab it now to reap its full benefits.
-
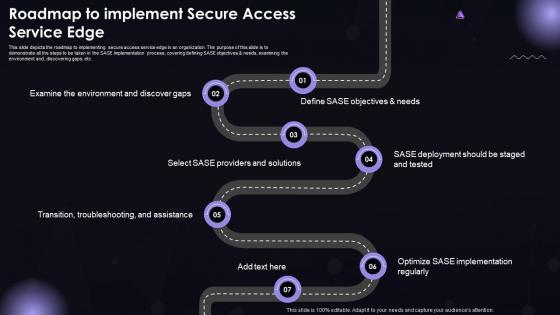 SASE IT Roadmap To Implement Secure Access Service Edge Ppt Powerpoint Formats
SASE IT Roadmap To Implement Secure Access Service Edge Ppt Powerpoint FormatsThis slide depicts the roadmap to implementing secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and, discovering gaps, etc. Introducing SASE IT Roadmap To Implement Secure Access Service Edge Ppt Powerpoint Formats to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Transition, Troubleshooting, And Assistance, SASE Providers And Solutions, using this template. Grab it now to reap its full benefits.
-
 SASE IT Secure Access Service Edge Implementation Steps Ppt Powerpoint Guidelines
SASE IT Secure Access Service Edge Implementation Steps Ppt Powerpoint GuidelinesThis slide outlines the steps to implement a secure service edge in a business. The purpose of this slide is to demonstrate the various guidelines to consider while implementing the SASE model in an organization. The main steps include defining SASE goals and requirements, selecting the SD-WAN backbone, incorporating zero-trust solutions, etc. Increase audience engagement and knowledge by dispensing information using SASE IT Secure Access Service Edge Implementation Steps Ppt Powerpoint Guidelines. This template helps you present information on five stages. You can also present information on SASE Goals And Requirements, Select SD-WAN Backbone, Incorporate Zero Trust Solutions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SASE IT Timeline To Implement Cloud Access Security Broker Ppt Powerpoint Portrait
SASE IT Timeline To Implement Cloud Access Security Broker Ppt Powerpoint PortraitThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Increase audience engagement and knowledge by dispensing information using SASE IT Timeline To Implement Cloud Access Security Broker Ppt Powerpoint Portrait. This template helps you present information on seven stages. You can also present information on Hybrid Settings, Organizations Users, Cloud Apps using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SASE IT Timeline To Implement Secure Access Service Edge Ppt Powerpoint Brochure
SASE IT Timeline To Implement Secure Access Service Edge Ppt Powerpoint BrochureThis slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Introducing SASE IT Timeline To Implement Secure Access Service Edge Ppt Powerpoint Brochure to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on SASE Objectives And Needs, SASE Providers And Solutions,Transition, Troubleshooting, And Assistance, using this template. Grab it now to reap its full benefits.
-
 Principles Of Enterprise Blockchain Security Implementation
Principles Of Enterprise Blockchain Security ImplementationThis slide highlights principles for blockchain security implementation aimed at implementing technology to strengthen platform by aligning with current trends. It covers open source, permissioning, governance, security and standards. Introducing our premium set of slides with Principles Of Enterprise Blockchain Security Implementation. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Permissioning, Security, Open Source, Governance. So download instantly and tailor it with your information.
-
 Security Practices For Enterprise Blockchain Implementation
Security Practices For Enterprise Blockchain ImplementationThis slide presents security practices for blockchain implementation aimed at optimizing security and mitigation practices to improve cybersecurity technology. It covers permissioned blockchain, case analysis, create governance structure and file storage. Presenting our set of slides with Security Practices For Enterprise Blockchain Implementation. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Permissioned Blockchain, Create Governance Structure, Case Analysis, File Storage.
-
 Steps To Implement Enterprise Blockchain Security
Steps To Implement Enterprise Blockchain SecurityThis slide conveys steps to implement blockchain security for enterprises aimed at increasing data trust, transparency and traceability across a business network. It covers choosing platform, experimenting, scalability and security, build framework, gamification and modelling ecosystems. Introducing our premium set of slides with Steps To Implement Enterprise Blockchain Security. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Choose Platform, Scalability And Security, Gamification, Build Framework. So download instantly and tailor it with your information.
-
 Implement Automated Generating Security Awareness Among Employees To Reduce
Implement Automated Generating Security Awareness Among Employees To ReduceThe following slide showcases the automated patch management process to fix software vulnerabilities and ensure smooth functioning of systems. It includes activities such as scanning of systems, requesting to take back up etc. Deliver an outstanding presentation on the topic using this Implement Automated Generating Security Awareness Among Employees To Reduce Dispense information and present a thorough explanation of Vulnerability Assessment, Request Cancelled using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Analyzing Multiple Sales Tactics For Securing New Leads Implementation Guidelines For Sales MKT SS V
Analyzing Multiple Sales Tactics For Securing New Leads Implementation Guidelines For Sales MKT SS VThis slide provides glimpse about employing different techniques that can help the business in new lead generation. It includes techniques such as social media marketing, cold calling, email marketing, their impact, etc. Introducing Analyzing Multiple Sales Tactics For Securing New Leads Implementation Guidelines For Sales MKT SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Multiple, Analyzing, Sales, using this template. Grab it now to reap its full benefits.
-
 Addressing Compliance Classes In IOT Security Internet Of Things IOT Implementation At Workplace
Addressing Compliance Classes In IOT Security Internet Of Things IOT Implementation At WorkplaceThis slide provides information regarding different compliance classes in IoT security framework catering different security objective. Present the topic in a bit more detail with this Addressing Compliance Classes In IOT Security Internet Of Things IOT Implementation At Workplace Use it as a tool for discussion and navigation on Confidentiality, Integrity, Availability. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine IOT Security Compliance Framework Internet Of Things IOT Implementation At Workplace
Determine IOT Security Compliance Framework Internet Of Things IOT Implementation At WorkplaceThis slide provides information regarding IoT security compliance framework addressing key security issues such as governance of management, security engineering, etc. Present the topic in a bit more detail with this Determine IOT Security Compliance Framework Internet Of Things IOT Implementation At Workplace. Use it as a tool for discussion and navigation on Governance Of Management, Security Engineering This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Timeline To Implement Cloud Access Security Broker Ppt Ideas Tips
Timeline To Implement Cloud Access Security Broker Ppt Ideas TipsThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Increase audience engagement and knowledge by dispensing information using Timeline To Implement Cloud Access Security Broker Ppt Ideas Tips. This template helps you present information on seven stages. You can also present information on Keep Records, Identify And Disable, Examine using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices Implement Cloud Access Security Broker Ppt Professional Graphics Design
Best Practices Implement Cloud Access Security Broker Ppt Professional Graphics DesignThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Best Practices Implement Cloud Access Security Broker Ppt Professional Graphics Design. Dispense information and present a thorough explanation of Best Practices, Description, Impact using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker Implementation Roadmap
Cloud Access Security Broker Implementation RoadmapThis slide outlines the roadmap for deploying a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to implement the cloud access security broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Implementation Roadmap. This template helps you present information on six stages. You can also present information on Security Profile, Determine Whether, Sso Systems using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Advantages Of Blockchain Implementing Blockchain Security Solutions
Advantages Of Blockchain Implementing Blockchain Security SolutionsThis slide represents the various advantages of blockchain technology based on information security, digital freedom, privacy, and lower transaction fees.Introducing Advantages Of Blockchain Implementing Blockchain Security Solutions to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Immutable Information, Anonymity Privacy, No Intermediaries, using this template. Grab it now to reap its full benefits.
-
 Bitcoin Vs Blockchain Technology Implementing Blockchain Security Solutions
Bitcoin Vs Blockchain Technology Implementing Blockchain Security SolutionsThis slide defines the difference between bitcoin and blockchain technology based on goal, trade, scope, strategy and status.Increase audience engagement and knowledge by dispensing information using Bitcoin Vs Blockchain Technology Implementing Blockchain Security Solutions. This template helps you present information on five stages. You can also present information on Efficiently Government Restrictions, Numerical Sequence, Property Currency using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Blockchain Hashing Sha 256 Implementing Blockchain Security Solutions
Blockchain Hashing Sha 256 Implementing Blockchain Security SolutionsThis slide talks about the hashing SHA256 algorithm used in blockchain technology, including its properties. The purpose of this slide is to give an overview of hashing and its properties, such as collision resistance, deterministic, quick, and irreversible.Introducing Blockchain Hashing Sha 256 Implementing Blockchain Security Solutions to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Collision Resistance, Protecting Integrity, Completely Different, using this template. Grab it now to reap its full benefits.
-
 Checklist To Build Secure Blockchain Implementing Blockchain Security Solutions
Checklist To Build Secure Blockchain Implementing Blockchain Security SolutionsThis slide represents the best practices for businesses to develop secure blockchain solutions. The purpose of this slide is to showcase the different steps that should be considered for building secure blockchain solutions.Deliver an outstanding presentation on the topic using this Checklist To Build Secure Blockchain Implementing Blockchain Security Solutions. Dispense information and present a thorough explanation of Blockchain Penetration Testing, Protection Personal, Penetration Testing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyberattacks And Fraud Incidents Implementing Blockchain Security Solutions
Cyberattacks And Fraud Incidents Implementing Blockchain Security SolutionsThis slide outlines a few cyber attacks and fraud incidents that happened in the blockchain infrastructure. The purpose of this slide is to showcase the cyberattacks and fraud that occurred in the past, including code exploitation, stolen keys and employee computer hacking.Present the topic in a bit more detail with this Cyberattacks And Fraud Incidents Implementing Blockchain Security Solutions. Use it as a tool for discussion and navigation on Resulting In Substantial Financial, Bitcoins Belonging, Gain Unauthorized. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Disadvantages Of Blockchain Implementing Blockchain Security Solutions
Disadvantages Of Blockchain Implementing Blockchain Security SolutionsThis slide defines the various disadvantages of blockchain technology based on speed, energy, cost, scalability, maturity, and integration.Introducing Disadvantages Of Blockchain Implementing Blockchain Security Solutions to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Energy Consumption, Difficult Scale, Self Maintenance, using this template. Grab it now to reap its full benefits.
-
 How Blockchain Prevents Fraud And Implementing Blockchain Security Solutions
How Blockchain Prevents Fraud And Implementing Blockchain Security SolutionsThis slide describes the different methods used by blockchain technology to prevent data from fraud and stealing. The purpose of this slide is to showcase the various techniques and technologies used in blockchain technology to prevent fraud and data theft.Increase audience engagement and knowledge by dispensing information using How Blockchain Prevents Fraud And Implementing Blockchain Security Solutions. This template helps you present information on four stages. You can also present information on Extremely Difficult, Blockchain Incorporates, Techniques Such using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How Ddos Attack Works In Implementing Blockchain Security Solutions
How Ddos Attack Works In Implementing Blockchain Security SolutionsThis slide represents the overview of distributed denialofservice DDOS attacks in blockchain technology. This slide aims to showcase how distributed denialofservice DDOS works to exploit a blockchain network by generating multiple requests from a single source.Present the topic in a bit more detail with this How Ddos Attack Works In Implementing Blockchain Security Solutions. Use it as a tool for discussion and navigation on Network Resource Unavailable, Mitigation Strategies, Distinguishing Malicious. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 How Fraudsters Attack Implementing Blockchain Security Solutions
How Fraudsters Attack Implementing Blockchain Security SolutionsThis slide describes the primary attacks that hackers can use to exploit blockchain technology networks. The purpose of this slide is to showcase some basic threats that hackers can use to manipulate a blockchain network, such as phishing attacks, routing attacks, sybil, and 51 precent.Increase audience engagement and knowledge by dispensing information using How Fraudsters Attack Implementing Blockchain Security Solutions. This template helps you present information on four stages. You can also present information on Phishing Attacks, Routing Attacks, Sybil Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How Organizations Maintaining Implementing Blockchain Security Solutions
How Organizations Maintaining Implementing Blockchain Security SolutionsThis slide represents the various organizations that are taking security measures to prevent cyberattacks on blockchain network. The purpose of this slide is to highlight the various steps taken by US based organizations to prevent blockchain from cyber attacks and frauds.Deliver an outstanding presentation on the topic using this How Organizations Maintaining Implementing Blockchain Security Solutions. Dispense information and present a thorough explanation of Comprehensive Background, Healthcare Organizations, Credibility Influence using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Major Security Concerns For Implementing Blockchain Security Solutions
Major Security Concerns For Implementing Blockchain Security SolutionsThis slide outlines the critical security concerns related to blockchain networks. The purpose of this slide is to showcase the major risks associated with blockchain technology, including confidentiality, integrity, nonrepudiation, and authentication.Introducing Major Security Concerns For Implementing Blockchain Security Solutions to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Prevent Unauthorized, Safeguarding Sensitive, Prevent Unauthorized, using this template. Grab it now to reap its full benefits.
-
 Overview Of Sybil Attack In Implementing Blockchain Security Solutions
Overview Of Sybil Attack In Implementing Blockchain Security SolutionsThis slide gives an overview of the sybil attack in the blockchain network. The purpose of this slide is to showcase the use case of a sybil attack, also known as eclipse attack, and how the sybil attack works to manipulate a blockchain network.Deliver an outstanding presentation on the topic using this Overview Of Sybil Attack In Implementing Blockchain Security Solutions. Dispense information and present a thorough explanation of Hindering Communication, Potential Application, Fake Identities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phases To Perform Blockchain Implementing Blockchain Security Solutions
Phases To Perform Blockchain Implementing Blockchain Security SolutionsThis slide highlights the main phases of blockchain penetration testing. The purpose of this slide is to showcase the different stages of penetration testing, including information gathering and threat modeling, testing and discovery, and exploitation.Increase audience engagement and knowledge by dispensing information using Phases To Perform Blockchain Implementing Blockchain Security Solutions. This template helps you present information on three stages. You can also present information on Information Gathering, Functionality Assess, Retrieving Information using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Preventive Measures Against Implementing Blockchain Security Solutions
Preventive Measures Against Implementing Blockchain Security SolutionsThis slide represents the steps to prevent distributed daniel of service attacks in blockchain technology. The purpose of this slide is to showcase the different security measures against ddos attacks, including implementing traffic filtering, employing load balancing, utilizing rate limiting and so on..Present the topic in a bit more detail with this Preventive Measures Against Implementing Blockchain Security Solutions. Use it as a tool for discussion and navigation on Collaborate Communicate, Decentralized Network, Implement Traffic Filtering. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Primary Security Attributes Of Implementing Blockchain Security Solutions
Primary Security Attributes Of Implementing Blockchain Security SolutionsThis slide outlines the main attributes of blockchain network security. The purpose of this slide is to highlight the security attributes of blockchain technology, including transaction integrity, tamper resistance, consistency, access to network and data, confidentiality of transactions, and so on.Deliver an outstanding presentation on the topic using this Primary Security Attributes Of Implementing Blockchain Security Solutions. Dispense information and present a thorough explanation of Transaction Integrity, Confidentiality Transactions, Resistance Attacks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Reasons To Implement Security In Organizational Communication Plan
Reasons To Implement Security In Organizational Communication PlanThis slide showcases reasons for securing organizational networks. This template focuses on encrypting communication to safeguard business, employees clients. It includes information related to advanced privacy, protecting cyber attacks, etc.Introducing our premium set of slides with Reasons To Implement Security In Organizational Communication Plan. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Improves Customer Confidence, Protects Intellectual Property, Builds Consumer. So download instantly and tailor it with your information.
-
 Implementation Of Cyber Security Risk Management Action Plan
Implementation Of Cyber Security Risk Management Action PlanThis slide represents implementation process of cyber security risk management action plan. It further includes steps such as evaluate cyber security risks, prioritize cyber risks Presenting our well structured Implementation Of Cyber Security Risk Management Action Plan. The topics discussed in this slide are Security, Management, Plan. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Blockchain Penetration Testing Implementing Blockchain Security Solutions
Blockchain Penetration Testing Implementing Blockchain Security SolutionsThis slide gives an overview of blockchain penetration testing and its primary goal. The purpose of this slide is to highlight the benefits of penetration testing in blockchain technology and its objectives, such as finding vulnerabilities, security loopholes, and misconfiguration errors within the solution.Present the topic in a bit more detail with this Blockchain Penetration Testing Implementing Blockchain Security Solutions. Use it as a tool for discussion and navigation on Deployment Procedure, Assessment Examine, Specialists Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risks Involved In Public Blockchain Implementing Blockchain Security Solutions
Risks Involved In Public Blockchain Implementing Blockchain Security SolutionsThis slide represents the challenges involved in public blockchains classified as basic risks, implementation risks, security risks, and legal risks.Introducing Risks Involved In Public Blockchain Implementing Blockchain Security Solutions to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Integrate Standards, Lack Standardization, Vendor Challenges, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents For Implementing Blockchain Security Solutions
Table Of Contents For Implementing Blockchain Security SolutionsPresent the topic in a bit more detail with this Table Of Contents For Implementing Blockchain Security Solutions. Use it as a tool for discussion and navigation on Risks Involved, Public Blockchain, Attack Blockchain Network. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Understanding 51 Precent Attack Implementing Blockchain Security Solutions
Understanding 51 Precent Attack Implementing Blockchain Security SolutionsThis slide outlines the overview of 51 precent attack in blockchain technology. The purpose of this slide is to showcase how malicious miners possess control over 51 precent of blockchain blocks, including a before and after use case.Deliver an outstanding presentation on the topic using this Understanding 51 Precent Attack Implementing Blockchain Security Solutions. Dispense information and present a thorough explanation of Chain Simultaneously, Attacker Controls, Mining Protocol using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Internet security electronic payment system eviction ec implementation
Internet security electronic payment system eviction ec implementationPresenting this set of slides with name - Internet Security Electronic Payment System Eviction Ec Implementation. This is an editable seven stages graphic that deals with topics like Internet Security Electronic Payment System, Eviction Ec Implementation to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Security distributor post implementation middle east africa knowledge centers
Security distributor post implementation middle east africa knowledge centersPresenting this set of slides with name - Security Distributor Post Implementation Middle East Africa Knowledge Centers. This is an editable three graphic that deals with topics like Security Distributor, Post Implementation, Middle East Africa, Knowledge Centers to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Introduction new technology product security policy implementation phase cpb
Introduction new technology product security policy implementation phase cpbPresenting this set of slides with name - Introduction New Technology Product Security Policy Implementation Phase Cpb. This is an editable three graphic that deals with topics like Introduction New Technology, Product Security Policy, Implementation Phase to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Firewall Implementation For Cyber Security Post Firewall Implementation Impact On Business
Firewall Implementation For Cyber Security Post Firewall Implementation Impact On BusinessThis slide represents the impact of firewall implementation on the organization. The purpose of this slide is to showcase the decline in various cyber security threats such as malware, worms, Daniel of Service, botnets, and phishing attacks. Deliver an outstanding presentation on the topic using this Firewall Implementation For Cyber Security Post Firewall Implementation Impact On Business. Dispense information and present a thorough explanation of Post Firewall Implementation, Data Breaching Threats, Daniel Of Service using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Bi design and implementation security ppt powerpoint presentation picture
Bi design and implementation security ppt powerpoint presentation picturePresenting this set of slides with name BI Design And Implementation Security Ppt Powerpoint Presentation Picture. This is a four stage process. The stages in this process are Web Based, Architecture, Scalability, Security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Five yearly roadmap for infrastructure security implementation in organization
Five yearly roadmap for infrastructure security implementation in organizationPresenting Five Yearly Roadmap For Infrastructure Security Implementation In Organization PowerPoint slide. This PPT presentation is Google Slides compatible hence it is easily accessible. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 Half yearly roadmap for infrastructure security implementation in organization
Half yearly roadmap for infrastructure security implementation in organizationPresenting Half Yearly Roadmap For Infrastructure Security Implementation In Organization PowerPoint slide. This PPT presentation is Google Slides compatible hence it is easily accessible. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 Quarterly roadmap for infrastructure security implementation in organization
Quarterly roadmap for infrastructure security implementation in organizationPresenting Quarterly Roadmap For Infrastructure Security Implementation In Organization PowerPoint slide. This PPT presentation is Google Slides compatible hence it is easily accessible. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 Six months roadmap for infrastructure security implementation in organization
Six months roadmap for infrastructure security implementation in organizationPresenting Six Months Roadmap For Infrastructure Security Implementation In Organization PowerPoint slide. This PPT presentation is Google Slides compatible hence it is easily accessible. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 Three months roadmap for infrastructure security implementation in organization
Three months roadmap for infrastructure security implementation in organizationPresenting Three Months Roadmap For Infrastructure Security Implementation In Organization PowerPoint slide. This PPT presentation is Google Slides compatible hence it is easily accessible. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 Five years cyber security implementation approach roadmap
Five years cyber security implementation approach roadmapPresenting Five Years Cyber Security Implementation Approach Roadmap PowerPoint slide. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 Half yearly cyber security implementation approach roadmap
Half yearly cyber security implementation approach roadmapPresenting Half Yearly Cyber Security Implementation Approach Roadmap PowerPoint slide. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 Quarterly cyber security implementation approach roadmap
Quarterly cyber security implementation approach roadmapPresenting Quarterly Cyber Security Implementation Approach Roadmap PowerPoint slide. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 Six months cyber security implementation approach roadmap
Six months cyber security implementation approach roadmapPresenting Six Months Cyber Security Implementation Approach Roadmap PowerPoint slide. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 Three months cyber security implementation approach roadmap
Three months cyber security implementation approach roadmapPresenting Three Months Cyber Security Implementation Approach Roadmap PowerPoint slide. This PPT theme is available in both 4,3 and 16,9 aspect ratios. This PowerPoint template is customizable so you can modify the font size, font type, color, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG.
-
 Business security implementation ppt powerpoint presentation pictures background cpb
Business security implementation ppt powerpoint presentation pictures background cpbPresenting this set of slides with name Business Security Implementation Ppt Powerpoint Presentation Pictures Background Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Business Security Implementation to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Implement enterprise security ppt powerpoint presentation outline format ideas cpb
Implement enterprise security ppt powerpoint presentation outline format ideas cpbPresenting this set of slides with name Implement Enterprise Security Ppt Powerpoint Presentation Outline Format Ideas Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Implement Enterprise Security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.





