Powerpoint Templates and Google slides for Implementing Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Review Cyber Security Status With Due Diligence Checklist Implementing Cyber Risk Management Process
Review Cyber Security Status With Due Diligence Checklist Implementing Cyber Risk Management ProcessThe following slide showcases checklist to monitor security progress status and ensure business credibility. It includes elements such as mobility and clean up policy, disaster recovery, password encryption, tasks, reviews etc. Present the topic in a bit more detail with this Review Cyber Security Status With Due Diligence Checklist Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Parameters, Tasks, Status, Reviews. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Select Tools To Reduce Cyber Security Failure Implementing Cyber Risk Management Process
Select Tools To Reduce Cyber Security Failure Implementing Cyber Risk Management ProcessThe following slide highlights some best tools to track and minimize the impact of cyber risks. It includes elements such as tool anme, features, trial period, cost and reviews etc. Deliver an outstanding presentation on the topic using this Select Tools To Reduce Cyber Security Failure Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Features, Free Trial, Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implementing Byod Policy To Enhance Develop Security Policies For Data Protection
Implementing Byod Policy To Enhance Develop Security Policies For Data ProtectionThis slide shows major data protection policies for handling sensitive data of corporate. It include policies such as device security, network and data handling, etc. Introducing Implementing Byod Policy To Enhance Develop Security Policies For Data Protection to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Network Security, Data Handling, Device Security, Data Protection, using this template. Grab it now to reap its full benefits.
-
 Implementing Byod Policy To Enhance Security Considerations For Data Protection Under Byod Policy
Implementing Byod Policy To Enhance Security Considerations For Data Protection Under Byod PolicyThis slide shows essential considerations for protecting crucial data of company in organization. It include security areas such as device security, network security and software updates, etc. Increase audience engagement and knowledge by dispensing information using Implementing Byod Policy To Enhance Security Considerations For Data Protection Under Byod Policy. This template helps you present information on five stages. You can also present information on Device Security, Mobile Device Management, Network Security, Malware Protection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices To Implement Cloud Access Security Broker Next Generation CASB
Best Practices To Implement Cloud Access Security Broker Next Generation CASBThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Best Practices To Implement Cloud Access Security Broker Next Generation CASB Dispense information and present a thorough explanation of Build Visibility, Forecast Risk, Release CASB, Best Practices using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker Implementation Roadmap Next Generation CASB
Cloud Access Security Broker Implementation Roadmap Next Generation CASBThis slide outlines the roadmap for deploying a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to implement the cloud access security broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc. Introducing Cloud Access Security Broker Implementation Roadmap Next Generation CASB to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Portfolio, Cloud Application, Systems using this template. Grab it now to reap its full benefits.
-
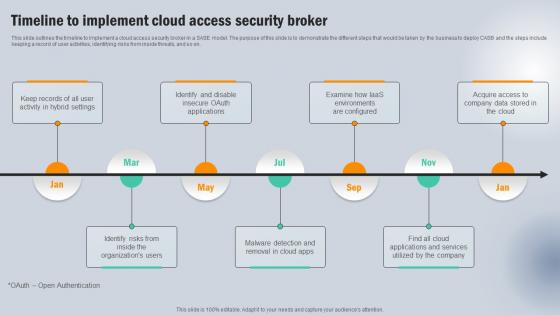 Timeline To Implement Cloud Access Security Broker Next Generation CASB
Timeline To Implement Cloud Access Security Broker Next Generation CASBThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Introducing Timeline To Implement Cloud Access Security Broker Next Generation CASB to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Acquire Access , Company, Applications And Services using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Standard Architectural Implementations Of Network Firewalls
Firewall Network Security Standard Architectural Implementations Of Network FirewallsThis slide outlines the common architectural deployments of network firewalls. The purpose of this slide is to showcase the different architectural implementations of firewalls, including packet filtering routers, screened host firewalls, dual-homed host, and screened subnet with DMZ. Present the topic in a bit more detail with this Firewall Network Security Standard Architectural Implementations Of Network Firewalls Use it as a tool for discussion and navigation on Access Control List, Workflow, Overview This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security 30 60 90 Days Plan To Implement Firewall Security
Firewall Network Security 30 60 90 Days Plan To Implement Firewall SecurityThis slide outlines the 30-60-90 days plan to integrate firewalls in a business. The purpose of this slide is to showcase the various steps that should be taken at the interval of every 30 days, such as assessing the current security landscape, defining firewall requirements and selecting solutions, etc. Present the topic in a bit more detail with this Firewall Network Security 30 60 90 Days Plan To Implement Firewall Security Use it as a tool for discussion and navigation on 30 Days, 60 Days, 90 Days This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Cost Summary For Firewall Network Security Implementation
Firewall Network Security Cost Summary For Firewall Network Security ImplementationThis slide outlines the summary of total budget for implementing firewalls in the organization. The purpose of this slide is to showcase the project cost summary, amount, and project details such as company name, project name, project lead, and starting date of the project. Deliver an outstanding presentation on the topic using this Firewall Network Security Cost Summary For Firewall Network Security Implementation Dispense information and present a thorough explanation of Project Cost Summary, Project Details using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implement Authentication Techniques For Wireless Lan Security
Implement Authentication Techniques For Wireless Lan SecurityThis slide highlights wireless security LAN checklist for preventing security threats and compile standard authentication and encryption techniques. It includes elements such as wireless lan security recommendations, applicable, not applicable and notes. Introducing our Implement Authentication Techniques For Wireless Lan Security set of slides. The topics discussed in these slides are Authentication, Techniques, Applicable. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 SD WAN Model Best Practices To Implement Cloud Access Security Broker
SD WAN Model Best Practices To Implement Cloud Access Security BrokerThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this SD WAN Model Best Practices To Implement Cloud Access Security Broker. Dispense information and present a thorough explanation of Network And Cloud Infrastructure Monitoring, Protection Against Risks, Specific Risk Prototypes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SD WAN Model Budget To Implement Secure Access Service Edge
SD WAN Model Budget To Implement Secure Access Service EdgeThis slide depicts the budget calculation for implementing a secure access service edge model in an organization. The purpose of this slide is to showcase the estimated and actual cost and variance for SASE model spending. The key components include SD-WAN, SWG, ZTNA, CASB, and FWaaS. Present the topic in a bit more detail with this SD WAN Model Budget To Implement Secure Access Service Edge. Use it as a tool for discussion and navigation on Secure Web Gateway, Cloud Access Security Broker, Zero Trust Network Access, Firewall As A Service. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SD WAN Model Checklist To Implement Secure Access Service Edge
SD WAN Model Checklist To Implement Secure Access Service EdgePresent the topic in a bit more detail with this SD WAN Model Checklist To Implement Secure Access Service Edge. Use it as a tool for discussion and navigation on Test And Troubleshoot, Incorporate Zero Trust Solutions, Goals And Requirements. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SD WAN Model Cloud Access Security Broker Implementation Models
SD WAN Model Cloud Access Security Broker Implementation ModelsThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Increase audience engagement and knowledge by dispensing information using SD WAN Model Cloud Access Security Broker Implementation Models. This template helps you present information on three stages. You can also present information on Cloud Access Security Broker, Api Scanning, Forward Proxy, Reverse Proxy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SD WAN Model Roadmap To Implement Secure Access Service Edge
SD WAN Model Roadmap To Implement Secure Access Service EdgeThis slide depicts the roadmap to implementing secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and, discovering gaps, etc. Introducing SD WAN Model Roadmap To Implement Secure Access Service Edge to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Implementation Regularly, Transition, Troubleshooting And Assistance, Secure Access Service Edge, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Secure Access Service Edge Implementation Steps
SD WAN Model Secure Access Service Edge Implementation StepsThis slide outlines the steps to implement a secure service edge in a business. The purpose of this slide is to demonstrate the various guidelines to consider while implementing the SASE model in an organization. The main steps include defining SASE goals and requirements, selecting the SD-WAN backbone, incorporating zero-trust solutions, etc. Increase audience engagement and knowledge by dispensing information using SD WAN Model Secure Access Service Edge Implementation Steps. This template helps you present information on five stages. You can also present information on Incorporate Zero Trust Solutions, Test And Troubleshoot, Secure Access Service Edge, Infrastructure Gaps using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
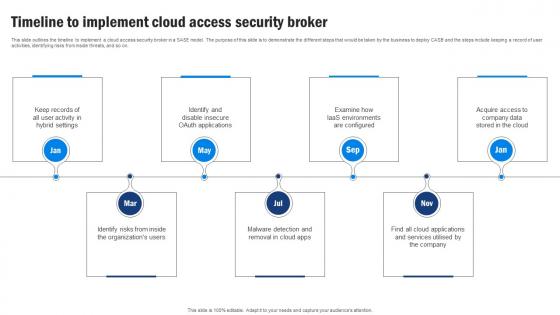 SD WAN Model Timeline To Implement Cloud Access Security Broker
SD WAN Model Timeline To Implement Cloud Access Security BrokerThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Increase audience engagement and knowledge by dispensing information using SD WAN Model Timeline To Implement Cloud Access Security Broker. This template helps you present information on seven stages. You can also present information on Cloud Access Security Broker, Environments Are Configured, Identify Risks, Malware Detection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
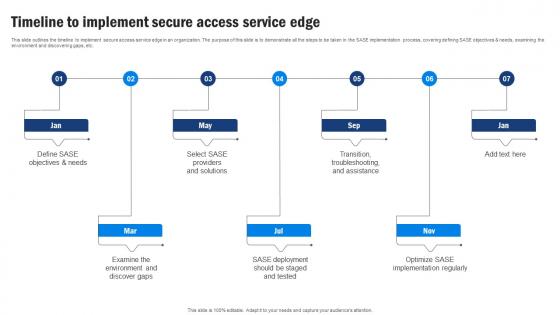 SD WAN Model Timeline To Implement Secure Access Service Edge
SD WAN Model Timeline To Implement Secure Access Service EdgeThis slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Introducing SD WAN Model Timeline To Implement Secure Access Service Edge to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Secure Access Service Edge, Examining The Environment, Discovering Gaps, Timeline, using this template. Grab it now to reap its full benefits.
-
 Data Breach Response Plan Implementation Secure Operations
Data Breach Response Plan Implementation Secure OperationsThis slide represents actions to be taken, the responsible team, the deadline, and tasks for securing operations after a data breach. The action items include secure physical areas, assemble expert team, consult with legal counsel, secure website and contact search engines, etc. Present the topic in a bit more detail with this Data Breach Response Plan Implementation Secure Operations. Use it as a tool for discussion and navigation on Secure Physical Areas, Assemble Expert Team, Consult With Legal Counsel, Secure Website. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Devsecops Best Practices For Secure 30 60 90 Days Plan For Devsecops Implementation
Devsecops Best Practices For Secure 30 60 90 Days Plan For Devsecops ImplementationThis slide represents the 30-60-90-day plan for DevSecOps implementation. The purpose of this slide is to showcase the approaches that need to be followed as short-term, medium, and long-term goals to implement the DevSecOps. Introducing Devsecops Best Practices For Secure 30 60 90 Days Plan For Devsecops Implementation to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Devsecops Implementation, Vulnerability Scanning, Relevant Security Standards, using this template. Grab it now to reap its full benefits.
-
 Devsecops Best Practices For Secure Before Vs After Impact Of Devsecops Implementation
Devsecops Best Practices For Secure Before Vs After Impact Of Devsecops ImplementationThis slide showcases the comparative analysis of the before versus after DevSecOps implementation. The purpose of this slide is to discuss the different performance aspects and how DevSecOps has proved beneficial for these aspects. Deliver an outstanding presentation on the topic using this Devsecops Best Practices For Secure Before Vs After Impact Of Devsecops Implementation. Dispense information and present a thorough explanation of Collaboration And Communication, Development Cycles, Operational Costs, Infrastructure Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Devsecops Best Practices For Secure Checklist To Implement Devsecops In Organization
Devsecops Best Practices For Secure Checklist To Implement Devsecops In OrganizationThis slide represents the checklist to implement the DevSecOps in an organization. The purpose of this slide is to provide key functional requirements for implementing and deploying the DevSecOps system in an enterprise environment. Present the topic in a bit more detail with this Devsecops Best Practices For Secure Checklist To Implement Devsecops In Organization. Use it as a tool for discussion and navigation on Security Training And Awareness, Collaboration And Communication, Security Automation, Vulnerability Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Devsecops Best Practices For Secure Devsecops Implementation Budget For Organization
Devsecops Best Practices For Secure Devsecops Implementation Budget For OrganizationThis slide represents the estimated and actual cost of implementing a DevSecOps system in an organization. The cost categories are infrastructure, security assessment, consulting or training, tool evolution, training programs, and certification. Present the topic in a bit more detail with this Devsecops Best Practices For Secure Devsecops Implementation Budget For Organization. Use it as a tool for discussion and navigation on Security Assessment, Consulting Or Training, Training Programs, Budget For Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Devsecops Best Practices For Secure Enabling Devsecops Implementation Through Process
Devsecops Best Practices For Secure Enabling Devsecops Implementation Through ProcessThis slide explains the process involved in DevSecOps implementation. The purpose of his slide is to discuss the process involving automate dev. and production environments, automate software testing, automate software deployment, automate monitoring and alerting, and so on. Increase audience engagement and knowledge by dispensing information using Devsecops Best Practices For Secure Enabling Devsecops Implementation Through Process. This template helps you present information on eight stages. You can also present information on Devsecops Implementation, Production Environments, Automate Software Testing, Automate Software Deployment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Devsecops Best Practices For Secure Roadmap For Devsecops Implementation Strategy
Devsecops Best Practices For Secure Roadmap For Devsecops Implementation StrategyThis slide highlights the project roadmap to implement the DevSecOps plan in an organization. The purpose of this slide is to showcase the different phases of the DevSecOps implementation plan, such as foundation and preparation, tool selection and integration, etc. Introducing Devsecops Best Practices For Secure Roadmap For Devsecops Implementation Strategy to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Tool Selection And Integration, Compliance And Governance, Foundation And Preparation, Security As Code, using this template. Grab it now to reap its full benefits.
-
 Devsecops Best Practices For Secure Timeline To Implement Devsecops Process In Organization
Devsecops Best Practices For Secure Timeline To Implement Devsecops Process In OrganizationThis slide shows the timeline for implementing the DevSecOps process. The key steps include defining the project objective, identifying key stakeholders, sharing basic guidelines on secure coding, basic compliance checks, regularly reviewing and updating security tools, etc. Increase audience engagement and knowledge by dispensing information using Devsecops Best Practices For Secure Timeline To Implement Devsecops Process In Organization. This template helps you present information on five stages. You can also present information on Timeline To Implement Devsecops, Regularly Reviewing, Updating Security Tools, Sharing Basic Guidelines using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Devsecops Best Practices For Secure Training Schedule For Devsecops Strategy Implementation
Devsecops Best Practices For Secure Training Schedule For Devsecops Strategy ImplementationThis slide represents the training schedule for strategy implementation for customers to manage, monitor, and troubleshoot DevSecOps implementation procedures. It includes the time slots for training, the total days of training, and the modules to be covered in the training. Deliver an outstanding presentation on the topic using this Devsecops Best Practices For Secure Training Schedule For Devsecops Strategy Implementation. Dispense information and present a thorough explanation of Strategy Implementation, Monitor And Troubleshoot, Devsecops Implementation Procedures using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Model Best Practices To Implement Cloud Access Security Broker
Sase Model Best Practices To Implement Cloud Access Security BrokerThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Present the topic in a bit more detail with this Sase Model Best Practices To Implement Cloud Access Security Broker. Use it as a tool for discussion and navigation on Best Practices, Description, Impact. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Model Budget To Implement Secure Access Service Edge
Sase Model Budget To Implement Secure Access Service EdgeThis slide depicts the budget calculation for implementing a secure access service edge model in an organization. The purpose of this slide is to showcase the estimated and actual cost and variance for SASE model spending. The key components include SD-WAN, SWG, ZTNA, CASB, and FWaaS. Deliver an outstanding presentation on the topic using this Sase Model Budget To Implement Secure Access Service Edge. Dispense information and present a thorough explanation of Components, Estimated Cost, Actual Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Model Checklist To Implement Secure Access Service Edge
Sase Model Checklist To Implement Secure Access Service EdgeDeliver an outstanding presentation on the topic using this Sase Model Checklist To Implement Secure Access Service Edge. Dispense information and present a thorough explanation of Steps, Responsible Person, Status using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Model Cloud Access Security Broker Implementation Models
Sase Model Cloud Access Security Broker Implementation ModelsThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Introducing Sase Model Cloud Access Security Broker Implementation Models to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Scanning, Forward Proxy, Reverse Proxy, using this template. Grab it now to reap its full benefits.
-
 Sase Model Roadmap To Implement Secure Access Service Edge
Sase Model Roadmap To Implement Secure Access Service EdgeThis slide depicts the roadmap to implementing secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and, discovering gaps, etc. Introducing Sase Model Roadmap To Implement Secure Access Service Edge to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Examine The Environment, Providers And Solutions, Implementation Regularly, using this template. Grab it now to reap its full benefits.
-
 Sase Model Secure Access Service Edge Implementation Steps
Sase Model Secure Access Service Edge Implementation StepsThis slide outlines the steps to implement a secure service edge in a business. The purpose of this slide is to demonstrate the various guidelines to consider while implementing the SASE model in an organization. The main steps include defining SASE goals and requirements, selecting the SD-WAN backbone, incorporating zero-trust solutions, etc. Increase audience engagement and knowledge by dispensing information using Sase Model Secure Access Service Edge Implementation Steps. This template helps you present information on five stages. You can also present information on Goals And Requirements, Incorporate Zero Trust Solutions, Test And Troubleshoot using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Model Timeline To Implement Cloud Access Security Broker
Sase Model Timeline To Implement Cloud Access Security BrokerThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Increase audience engagement and knowledge by dispensing information using Sase Model Timeline To Implement Cloud Access Security Broker. This template helps you present information on seven stages. You can also present information on Hybrid Settings, Environments Are Configured, Cloud App using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Model Timeline To Implement Secure Access Service Edge
Sase Model Timeline To Implement Secure Access Service EdgeThis slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Introducing Sase Model Timeline To Implement Secure Access Service Edge to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Jan, Mar, May, Jul, using this template. Grab it now to reap its full benefits.
-
 Implementing Blockchain Cybersecurity Securing Blockchain Transactions A Beginners Guide BCT SS V
Implementing Blockchain Cybersecurity Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide showcases blockchain cybersecurity threat assessment to determine type and major causes of attacks. It includes elements such as double spending, mining threats, wallet, network, smart contract threats, etc. Introducing Implementing Blockchain Cybersecurity Securing Blockchain Transactions A Beginners Guide BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Reduce, Accept, Transfer, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Plan Implementation Timeline Cyber Risk Assessment
Cyber Security Plan Implementation Timeline Cyber Risk AssessmentThe following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Introducing Cyber Security Plan Implementation Timeline Cyber Risk Assessment to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Systems And Passwords, Cyber Security Plan, Implementation Timeline using this template. Grab it now to reap its full benefits.
-
 Cyber Security Plan Implementation Timeline Creating Cyber Security Awareness
Cyber Security Plan Implementation Timeline Creating Cyber Security AwarenessThe following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Present the topic in a bit more detail with this Cyber Security Plan Implementation Timeline Creating Cyber Security Awareness Use it as a tool for discussion and navigation on Malware Attacks, Breaches To Company, More Challenging This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implement Automated Patch Management Solution Creating Cyber Security Awareness
Implement Automated Patch Management Solution Creating Cyber Security AwarenessThe following slide showcases the automated patch management process to fix software vulnerabilities and ensure smooth functioning of systems. It includes activities such as scanning of systems, requesting to take back-up etc. Present the topic in a bit more detail with this Implement Automated Patch Management Solution Creating Cyber Security Awareness Use it as a tool for discussion and navigation on Cyber Attack Type, Ransomware Attacks This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implement Opsec Cybersecurity Measures To Maximize Operational Security
Implement Opsec Cybersecurity Measures To Maximize Operational SecurityThis slide showcases the tactics to execute opsec cybersecurity measures. The purpose of this slide is to help the business ensure opsec security is suitably implemented through the use of strategies such as identification and access management, business continuity and disaster recovery, etc Introducing our premium set of slides with Implement Opsec Cybersecurity Measures To Maximize Operational Security. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Access Management, Disaster Recovery, AI Driven Automation . So download instantly and tailor it with your information.
-
 Steps To Implement Network Segmentation In IoT System IoT Security And Privacy Safeguarding IoT SS
Steps To Implement Network Segmentation In IoT System IoT Security And Privacy Safeguarding IoT SSThis slide highlights network segmentation structure and steps in the IoT ecosystem to increase security and data privacy. It includes steps such as determine all IoT assets, group assets, identify segment strategy, deploy strict access control, and test and monitor. Deliver an outstanding presentation on the topic using this Steps To Implement Network Segmentation In IoT System IoT Security And Privacy Safeguarding IoT SS. Dispense information and present a thorough explanation of Assets Organisations, Between Segments, Monitor Segments using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implementing Effective Software Testing Existing IT Security Infrastructure Constituents
Implementing Effective Software Testing Existing IT Security Infrastructure ConstituentsThis slide highlights the components of the current IT security infrastructure, which are prone to several functionality concerns. These constituents are regulatory and compliance, budget, complex integration, and so on. Present the topic in a bit more detail with this Implementing Effective Software Testing Existing IT Security Infrastructure Constituents. Use it as a tool for discussion and navigation on Complex Integration, Strict Compliance Requirements, Functional Disrupt, IT Security Infrastructure Constituents. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Before Vs After Implementing Secure Web
Internet Gateway Security IT Before Vs After Implementing Secure WebThis slide compares the scenario after integrating SWG in organizational network. The purpose of this slide is to represent before and after situation based on several parameters. The factors used to do the comparison are cost, security, productivity, etc. Present the topic in a bit more detail with this Internet Gateway Security IT Before Vs After Implementing Secure Web. Use it as a tool for discussion and navigation on Security, Visibility, Compliance, Productivity, Costs. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Checklist To Implement Secure Web Gateway
Internet Gateway Security IT Checklist To Implement Secure Web GatewayThis slide represents the checklist to implement Secure Web Gateway for application security. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. Present the topic in a bit more detail with this Internet Gateway Security IT Checklist To Implement Secure Web Gateway. Use it as a tool for discussion and navigation on Determine Use Case, Select Best Solution, Plan Deployment, Configure Solution, Test And Improve, Roll Out And Monitor. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Methods To Implement Security Policies
Internet Gateway Security IT Methods To Implement Security PoliciesThis slide demonstrates the different ways to enforce policies on remote and on-site employees using SWG. These are data loss prevention, encrypted traffic examination, protocol support, integration with anti-malware zero-day products, location flexibility, etc. Present the topic in a bit more detail with this Internet Gateway Security IT Methods To Implement Security Policies. Use it as a tool for discussion and navigation on Data Loss Prevention, Encrypted Traffic Examination, Protocol Support, Constant Security Monitoring. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Internet Gateway Security IT Secure Web Gateway Implementation
Internet Gateway Security IT Secure Web Gateway ImplementationThis slide talks about the transparent scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of transparent SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Introducing Internet Gateway Security IT Secure Web Gateway Implementation to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Internet Gateway, Internet Connected Network Site, Administrative Costs, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Secure Web Gateway Implementation Scenarios
Internet Gateway Security IT Secure Web Gateway Implementation ScenariosThis slide represents the different types of Secure Web Gateway deployment methods. The purpose of this slide is to outline SWG implementation methodologies. These are inline, explicit, transparent and SPAN Switched Port Analyzer port. Introducing Internet Gateway Security IT Secure Web Gateway Implementation Scenarios to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Inline, Transparent, Explicit, SPAN, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Swg Implementation Methodology Span Switched
Internet Gateway Security IT Swg Implementation Methodology Span SwitchedThis slide talks about the SPAN scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of SPAN SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Introducing Internet Gateway Security IT Swg Implementation Methodology Span Switched to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Internet Gateway Rules, Deployment, Monitoring, Transparent Modes, using this template. Grab it now to reap its full benefits.
-
 Secure Web Gateway Implementation Internet Gateway Security IT
Secure Web Gateway Implementation Internet Gateway Security ITThis slide talks about explicit scenario of Secure Web Gateway implementation. The purpose of this slide is to demonstrate the concept of explicit SWG deployment technique with the help of a diagram. This slide also outlines the benefits of this method. Introducing Secure Web Gateway Implementation Internet Gateway Security IT to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Manages Network Connection, Concentrates Most Sensitive, Protocols And Channels, Fewer Possible Disturbances Network, using this template. Grab it now to reap its full benefits.
-
 Implementation Checklist Plan For Security Incident
Implementation Checklist Plan For Security IncidentPresenting our set of slides with Implementation Checklist Plan For Security Incident. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Implementation Checklist Plan, Security Incident.
-
 Best Practices For Web Security Implementation
Best Practices For Web Security ImplementationThe purpose of this slide is to highlight the best practices for web security such as inclusive security practices, cybersecurity adoption, etc. Introducing our premium set of slides with name Best Practices For Web Security Implementation. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cybersecurity Framework Adoption, Automation Of Security Tools, Diverse Security Measures, Web Security Implementation. So download instantly and tailor it with your information.
-
 Roadmap For Implementing Effective Web Security
Roadmap For Implementing Effective Web SecurityThis slide outlines the steps that an organization should take while conducting web security such as education, infrastructure security, etc. Presenting our set of slides with name Roadmap For Implementing Effective Web Security. This exhibits information on seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Monitoring, Application Security, Incident Response, Assessment And Planning.
-
 Implementing Wireless Internet Security For Smart Home
Implementing Wireless Internet Security For Smart HomeThe following slide illustrates the implementation of wireless internet security in smart homes, emphasizing router setup, strong passwords, separate networks for IoT devices, 2FA, and NGFW, providing valuable guidance for securing connected environments Introducing our premium set of slides with Implementing Wireless Internet Security For Smart Home. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Set Up Router Correctly, Use Super Strong Passwords, Implementing. So download instantly and tailor it with your information.
-
 Best Practices To Maintain Digital Wallet Security Implementation Of Cashless Payment
Best Practices To Maintain Digital Wallet Security Implementation Of Cashless PaymentMentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private.Increase audience engagement and knowledge by dispensing information using Best Practices To Maintain Digital Wallet Security Implementation Of Cashless Payment This template helps you present information on five stages. You can also present information on Responsible Managers, Segregate Duties, Bank Statements using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Agenda Implementing Strategies To Mitigate Cyber Security Threats
Agenda Implementing Strategies To Mitigate Cyber Security ThreatsIntroducing Agenda Implementing Strategies To Mitigate Cyber Security Threats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Security Awareness, Risk Management Process, Cyber Risk using this template. Grab it now to reap its full benefits.
-
 Allocate Team Roles And Responsibilities Implementing Strategies To Mitigate Cyber Security Threats
Allocate Team Roles And Responsibilities Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the key roles and responsibilities of cyber security team to enhance decision making and goal accomplishment. It includes activities such as developing information security strategies, managing security architecture, planning disaster recovery etc. Deliver an outstanding presentation on the topic using this Allocate Team Roles And Responsibilities Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Technical Directors, Team Leads, Engineers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Analyse And Rank Impact Of Cyber Threat Implementing Strategies To Mitigate Cyber Security Threats
Analyse And Rank Impact Of Cyber Threat Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide highlights the prioritization of cyber security threats to minimize possibility of likelihood and severity. It mainly includes elements such as vulnerability, threat, source, likelihood, impact and ranking etc. Present the topic in a bit more detail with this Analyse And Rank Impact Of Cyber Threat Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Vulnerability, Threat, Threat Source This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Analyse Impact Of Cyber Attack On Valuable Implementing Strategies To Mitigate Cyber Security Threats
Analyse Impact Of Cyber Attack On Valuable Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the consequences of data breach threats to prevent information leakage. It mainly includes elements such as impact on revenue, protection cost, liability if lost, weightage criteria, asset importance etc. Deliver an outstanding presentation on the topic using this Analyse Impact Of Cyber Attack On Valuable Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Criteria, Impact On Revenue, Protection Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices To Prevent Cyber Attacks Implementing Strategies To Mitigate Cyber Security Threats
Best Practices To Prevent Cyber Attacks Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide illustrates some activities to minimize the probability of cybercrimes within the organization. It includes elements such as utilizing anti virus, preventing to open suspicious emails, keeping systems up to date etc. Introducing Best Practices To Prevent Cyber Attacks Implementing Strategies To Mitigate Cyber Security Threats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Leverage Firewalls, Prevent Opening Suspicious Emails using this template. Grab it now to reap its full benefits.





