Powerpoint Templates and Google slides for Implementing Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Roadmap To Implement Cyber Security Cyber Terrorism Attacks
Roadmap To Implement Cyber Security Cyber Terrorism AttacksThis slide depicts the roadmap to implement strategies to mitigate cyber terrorism such as training employees about cyber terrorism, creating personal accounts. Introducing Roadmap To Implement Cyber Security Cyber Terrorism Attacks to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Personal Accounts, Awareness Training, Software Updated, using this template. Grab it now to reap its full benefits.
-
 Building organizational security strategy plan facilities offered by implementation of security centre
Building organizational security strategy plan facilities offered by implementation of security centreThis slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Introducing Building Organizational Security Strategy Plan Facilities Offered By Implementation Of Security Centre to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Implementation, Investigation, Prevention, using this template. Grab it now to reap its full benefits.
-
 Enhancing overall project security it facilities rendered by security centre implementation
Enhancing overall project security it facilities rendered by security centre implementationThis slide provides information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Introducing Enhancing Overall Project Security It Facilities Rendered By Security Centre Implementation to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Implementation, Investigation, Prevention, using this template. Grab it now to reap its full benefits.
-
 Implementing Mobile Device Security Effective Mobile Device Management Ppt Formats
Implementing Mobile Device Security Effective Mobile Device Management Ppt FormatsThis slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Present the topic in a bit more detail with this Implementing Mobile Device Security Effective Mobile Device Management Ppt Formats. Use it as a tool for discussion and navigation on Implement Enterprise Security Program, Implement Control Environment, Implement Security Processes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Mobile Device Security Framework Roadmap Android Device Security Management
Implementing Mobile Device Security Framework Roadmap Android Device Security ManagementThis slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Present the topic in a bit more detail with this Implementing Mobile Device Security Framework Roadmap Android Device Security Management. Use it as a tool for discussion and navigation on Implement Enterprise, Security Program, Implement Security Processes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Hacker Roadmap To Implement New Security Strategies Ppt Inspiration
Security Hacker Roadmap To Implement New Security Strategies Ppt InspirationThis slide represents the roadmap to implement new security strategies, including hiring new professionals, new software or hardware installation, employee awareness sessions, etc. Introducing Security Hacker Roadmap To Implement New Security Strategies Ppt Inspiration to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Security Consultants, Tracking And Monitoring, Cyber Security Awareness Session, using this template. Grab it now to reap its full benefits.
-
 Checklist To Implement Cloud Security In Business Cloud Information Security
Checklist To Implement Cloud Security In Business Cloud Information SecurityThis slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc.Introducing Checklist To Implement Cloud Security In Business Cloud Information Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Impact Analysis, Recovery Strategies, Plan Development using this template. Grab it now to reap its full benefits.
-
 Roadmap Of Cloud Security Implementation Cloud Information Security
Roadmap Of Cloud Security Implementation Cloud Information SecurityThis slide defines the roadmap of cloud security implementation in an organization and what tasks would be performed in each months interval starting from January.Increase audience engagement and knowledge by dispensing information using Roadmap Of Cloud Security Implementation Cloud Information Security This template helps you present information on seven stages. You can also present information on Information Division, Access Control, Data Compliance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 In House Training Schedule We Will Implement Building A Security Awareness Program
In House Training Schedule We Will Implement Building A Security Awareness ProgramThe purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto jacking and IoT Based attack. Deliver an outstanding presentation on the topic using this In House Training Schedule We Will Implement Building A Security Awareness Program. Dispense information and present a thorough explanation of Social Engineering Attack, Business Email Compromise, Ransomware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategies We Will Implement To Make Building A Security Awareness Program
Strategies We Will Implement To Make Building A Security Awareness ProgramThe purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high quality content and variety. Increase audience engagement and knowledge by dispensing information using Strategies We Will Implement To Make Building A Security Awareness Program. This template helps you present information on four stages. You can also present information on Gamification, Personalization, High Quality Content using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Implementation Steps Enable Data Security Crm Software Deployment Guide
Implementation Steps Enable Data Security Crm Software Deployment GuideThis slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Present the topic in a bit more detail with this Implementation Steps Enable Data Security Crm Software Deployment Guide. Use it as a tool for discussion and navigation on Implementation, Authentication, Restrictions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementation Steps Enable Data Security Crm Platform Implementation Plan
Implementation Steps Enable Data Security Crm Platform Implementation PlanThis slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Deliver an outstanding presentation on the topic using this Implementation Steps Enable Data Security Crm Platform Implementation Plan. Dispense information and present a thorough explanation of Authentication, Implementation, Security Control using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Customer Relationship Management System Implementation Steps Enable Data Security
Customer Relationship Management System Implementation Steps Enable Data SecurityThis slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Deliver an outstanding presentation on the topic using this Customer Relationship Management System Implementation Steps Enable Data Security. Dispense information and present a thorough explanation of Implementation, Authentication, Restrictions using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Computing Security 30 60 90 Days Plan To Implement Cloud Security In Business
Cloud Computing Security 30 60 90 Days Plan To Implement Cloud Security In BusinessThis slide defines the 30,60 and 90 days plan to implement cloud security in the organization and what tasks would be performed on each 30 days interval. Increase audience engagement and knowledge by dispensing information using Cloud Computing Security 30 60 90 Days Plan To Implement Cloud Security In Business. This template helps you present information on three stages. You can also present information on Monitor Data Activities, User Behavior, Cloud Services using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Computing Security Checklist To Implement Cloud Security In Business
Cloud Computing Security Checklist To Implement Cloud Security In BusinessThis slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Introducing Cloud Computing Security Checklist To Implement Cloud Security In Business to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Logging And Monitoring, Data Encryption, Backup And Data Recovery, Policies And Procedures, Networking, using this template. Grab it now to reap its full benefits.
-
 Cloud Computing Security Roadmap Of Cloud Security Implementation
Cloud Computing Security Roadmap Of Cloud Security ImplementationThis slide defines the roadmap of cloud security implementation in an organization and what tasks would be performed in each months interval starting from January. Introducing Cloud Computing Security Roadmap Of Cloud Security Implementation to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Network Security, End User Control, Configuration Management Applications, Services Management, Cloud Services Monitoring, using this template. Grab it now to reap its full benefits.
-
 Roadmap For Implementation Of Cyber Security
Roadmap For Implementation Of Cyber SecurityThis slide represents quarterly roadmap for implementing cyber security in various aspects of an organization . It consists control, audit , testing, update and training. Presenting our set of slides with name Roadmap For Implementation Of Cyber Security. This exhibits information on four stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Roadmap, Implementation, Assessment.
-
 Sales CRM Cloud Implementation Implementation Add Roles And Enable Security
Sales CRM Cloud Implementation Implementation Add Roles And Enable SecurityThis slide illustrates the issues that trigger poor relationship with customers which includes no real time support, no innovative product launched, bad after sale service and lack of engagement. Present the topic in a bit more detail with this Sales CRM Cloud Implementation Poor Relationship With Customers Ppt Slides Picture. Use it as a tool for discussion and navigation on Weak Relationship Building, Poor Customer Service, Product Launched. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementation Add Roles And Enable Security Customer Relationship Management Deployment Strategy
Implementation Add Roles And Enable Security Customer Relationship Management Deployment StrategyThis slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management.Deliver an outstanding presentation on the topic using this Implementation Add Roles And Enable Security Customer Relationship Management Deployment Strategy Dispense information and present a thorough explanation of Restrictions Enabling, Double Authentication, Prevent Unauthorized using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implementation Add Roles And Enable Security Crm Software Implementation
Implementation Add Roles And Enable Security Crm Software ImplementationThis slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management. Present the topic in a bit more detail with this Implementation Add Roles And Enable Security Crm Software Implementation. Use it as a tool for discussion and navigation on Implementation, Generation, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Crm Implementation Process Implementation Steps Enable Data Security
Crm Implementation Process Implementation Steps Enable Data SecurityThis slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Present the topic in a bit more detail with this Crm Implementation Process Implementation Steps Enable Data Security. Use it as a tool for discussion and navigation on Implementation, Authentication, Restrictions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 30 60 90 Days Plan To Implement Cloud Security In Business
30 60 90 Days Plan To Implement Cloud Security In BusinessThis slide defines the 30,60 and 90-days plan to implement cloud security in the organization and what tasks would be performed on each 30 days interval. Introducing 30 60 90 Days Plan To Implement Cloud Security In Business to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispense information on Data Access, Operations Performed, Cloud Services, using this template. Grab it now to reap its full benefits.
-
 Checklist To Implement Cloud Security In Business Cloud Data Protection
Checklist To Implement Cloud Security In Business Cloud Data ProtectionThis slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Introducing Checklist To Implement Cloud Security In Business Cloud Data Protection to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispense information on Logging And Monitoring, Networking, Data Encryption, using this template. Grab it now to reap its full benefits.
-
 Roadmap Of Cloud Security Implementation Cloud Data Protection
Roadmap Of Cloud Security Implementation Cloud Data ProtectionThis slide defines the roadmap of cloud security implementation in an organization and what tasks would be performed in each months interval starting from January. Introducing Roadmap Of Cloud Security Implementation Cloud Data Protection to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispense information on Cloud Services Monitoring, Services Management, Database Security Measures, Network Security, using this template. Grab it now to reap its full benefits.
-
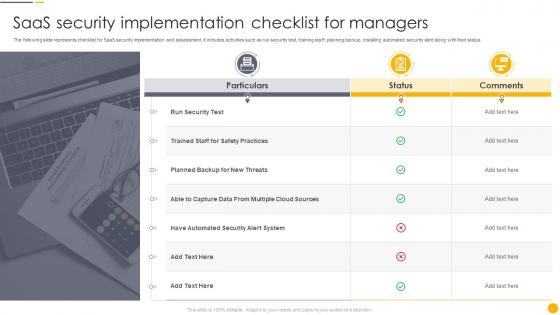 Saas Security Implementation Checklist For Managers
Saas Security Implementation Checklist For ManagersThe following slide represents checklist for SaaS security implementation and assessment. It includes activities such as run security test, training staff, planning backup, installing automated security alert along with their status. Presenting our well structured Saas Security Implementation Checklist For Managers. The topics discussed in this slide are Implementation, Automated, Represents. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Implementation Steps Enable Data Security Crm System Implementation Guide For Businesses
Implementation Steps Enable Data Security Crm System Implementation Guide For BusinessesThis slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Present the topic in a bit more detail with this Implementation Steps Enable Data Security Crm System Implementation Guide For Businesses. Use it as a tool for discussion and navigation on Implementation, Compliance, Authentication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Keyways To Secure Cloud Infrastructure Strategies To Implement Cloud Computing Infrastructure
Keyways To Secure Cloud Infrastructure Strategies To Implement Cloud Computing InfrastructureMentioned slide provides keyways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security. Introducing Keyways To Secure Cloud Infrastructure Strategies To Implement Cloud Computing Infrastructure to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Encryption Services, Internal Security, Security Design, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Transformation Strategy With Implementation
Cyber Security Transformation Strategy With ImplementationThe following slide highlights the cyber security transformation strategy with implementation illustrating benchmark, analysis, vision, roadmap, mobilization, and implementation which assists in transforming cyber security of organisation. Introducing our premium set of slides with name Cyber Security Transformation Strategy With Implementation. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Implementation, Mobilization, Vision, Analysis. So download instantly and tailor it with your information.
-
 Third Party Cyber Security Implementation Checklist
Third Party Cyber Security Implementation ChecklistIntroducing our premium set of slides with name Third Party Cyber Security Implementation Checklist. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Third Party Cyber Security, Implementation Checklist. So download instantly and tailor it with your information.
-
 Timeline For Cyber Security Implementation In Company
Timeline For Cyber Security Implementation In CompanyIntroducing our premium set of slides with name Timeline For Cyber Security Implementation In Company. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Timeline For Cyber Security, Implementation In Company. So download instantly and tailor it with your information.
-
 Implementing Iot Architecture In Shipping Business Securing Operations Of Logistics Through Integrated Iot
Implementing Iot Architecture In Shipping Business Securing Operations Of Logistics Through Integrated IotThis slide showcases securing operations of logistics through integrated internet of things IoT. It provides details such as field network, automation network, process network, operations, operating system, remote access, etc. Present the topic in a bit more detail with this Implementing Iot Architecture In Shipping Business Securing Operations Of Logistics Through Integrated Iot. Use it as a tool for discussion and navigation on Operations, Integrated, Workstation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Iot Security Lock For Safe Fleet Management Implementing Iot Architecture In Shipping Business
Iot Security Lock For Safe Fleet Management Implementing Iot Architecture In Shipping BusinessThe following slide illustrates internet of things IoT security lock for safe fleet management. It provides information about unlocking methods, Bluetooth, QR code, power saving, alarm notifications, large memory, etc. Deliver an outstanding presentation on the topic using this Iot Security Lock For Safe Fleet Management Implementing Iot Architecture In Shipping Business. Dispense information and present a thorough explanation of Management, Potential Impact, Key Applications using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategy To Provide Layered Security Across Networks Implementing Iot Architecture In Shipping Business
Strategy To Provide Layered Security Across Networks Implementing Iot Architecture In Shipping BusinessThis slide showcases strategy to provide layered security across networks. It provides information about user level, device level, network level, risk, malware, vulnerabilities, unusual traffic, access points, user authentication, etc. Present the topic in a bit more detail with this Strategy To Provide Layered Security Across Networks Implementing Iot Architecture In Shipping Business. Use it as a tool for discussion and navigation on Strategy, Authentication, Appropriate Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 In House Training Schedule We Will Implement Developing Cyber Security Awareness Training Program
In House Training Schedule We Will Implement Developing Cyber Security Awareness Training ProgramThe purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto jacking and IoT Based attack. Present the topic in a bit more detail with this In House Training Schedule We Will Implement Developing Cyber Security Awareness Training Program. Use it as a tool for discussion and navigation on Social Engineering Attack, Business Email Compromise, Ransomware, Password Attack. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategies We Will Implement To Make Security Awareness Training Interactive Developing Cyber Security Awareness
Strategies We Will Implement To Make Security Awareness Training Interactive Developing Cyber Security AwarenessThe purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high quality content and variety. Introducing Strategies We Will Implement To Make Security Awareness Training Interactive Developing Cyber Security Awareness to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Gamification, Personalization, High Quality Content, Variety, using this template. Grab it now to reap its full benefits.
-
 Implementing Mobile Device Security Framework Roadmap Management And Monitoring
Implementing Mobile Device Security Framework Roadmap Management And MonitoringThis slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Present the topic in a bit more detail with this Implementing Mobile Device Security Framework Roadmap Management And Monitoring. Use it as a tool for discussion and navigation on Security Program, Implementing Mobile Device, Security Framework. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Architecture And Security Multi Cloud It Environments After Implementing Solutions
Cloud Architecture And Security Multi Cloud It Environments After Implementing SolutionsThis slide covers the running all the workloads on a variety of clouds including public cloud, third party public clouds, hosted private clouds, and colocation servers while managing them. Increase audience engagement and knowledge by dispensing information using Cloud Architecture And Security Multi Cloud It Environments After Implementing Solutions. This template helps you present information on seven stages. You can also present information on Colocation, Hosted Private Cloud, Migration Services using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Conducting Security Awareness Strategies We Will Implement To Make Security Awareness
Conducting Security Awareness Strategies We Will Implement To Make Security AwarenessThe purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high-quality content and variety. Introducing Conducting Security Awareness Strategies We Will Implement To Make Security Awareness to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Gamification, Personalization, High Quality Content, using this template. Grab it now to reap its full benefits.
-
 In House Training Schedule We Will Implement Conducting Security Awareness
In House Training Schedule We Will Implement Conducting Security AwarenessThe purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto-jacking and iot-based attack. Introducing In House Training Schedule We Will Implement Conducting Security Awareness to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Ransomware, Time, Crypto Jacking, using this template. Grab it now to reap its full benefits.
-
 Implementing Mobile Device Security Roadmap Enterprise Mobile Security For On Device
Implementing Mobile Device Security Roadmap Enterprise Mobile Security For On DeviceThis slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Present the topic in a bit more detail with this Implementing Mobile Device Security Roadmap Enterprise Mobile Security For On Device. Use it as a tool for discussion and navigation on Risk Management, Implement Security, Control Environment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Importance Of Secure Ecommerce Payment Systems Analyzing And Implementing Management System
Importance Of Secure Ecommerce Payment Systems Analyzing And Implementing Management SystemThis slide represents the importance of payment gateways in facilitating systemized payment methods and providing consumers with fast and flexible way for making payments. It includes benefits of ecommerce payment systems such as meets digital needs, customer retention, security etc. Deliver an outstanding presentation on the topic using this Importance Of Secure Ecommerce Payment Systems Analyzing And Implementing Management System. Dispense information and present a thorough explanation of Customer Retention, Security, Multiple Payment Modes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Practices To Implement Security Automation
Key Practices To Implement Security AutomationThe following slide highlights best practices which can be implemented by firm for security automation. The major practices are prioritize automation, start with manual playbooks, adopt automation gradually and invest in the training of IT team. Introducing our premium set of slides with Key Practices To Implement Security Automation. Elucidate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Prioritize Automation, Start Manual Playbooks, Adopt Automation Gradually. So download instantly and tailor it with your information.
-
 6 Stage Process For Implementation Of Risk Management In Cyber Security Project
6 Stage Process For Implementation Of Risk Management In Cyber Security ProjectThis This slide signifies the six step process for successful implementation of risk assessment in cyber security project. It covers information about stages like identify, analyse, evaluate, prioritize, treat and monitor. Presenting our set of slides with name 6 Stage Process For Implementation Of Risk Management In Cyber Security Project. This exhibits information on six stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify, Analyse, Evaluate, Prioritize, Treat.
-
 Business Security Policy And Program Implementation
Business Security Policy And Program ImplementationThis slide covers business security policy and program implementation which includes business impact and effectiveness. Presenting our well structured Business Security Policy And Program Implementation. The topics discussed in this slide are Policy Program, Implementation, Business Impact. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Business Security Program Implementation With Review
Business Security Program Implementation With ReviewThis slide covers business security program implementation with review which includes organizational facility security risk assessment with service vendors. Presenting our set of slides with name Business Security Program Implementation With Review. This exhibits information on eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Program Review, Security Option, Control Assessment.
-
 Agenda For Implementing Security Awareness Training To Prevent Cyber Attacks
Agenda For Implementing Security Awareness Training To Prevent Cyber AttacksIntroducing Agenda For Implementing Security Awareness Training To Prevent Cyber Attacks to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Awareness Campaign, Cyber Security, Awareness Training, using this template. Grab it now to reap its full benefits.
-
 Assessment Test To Measure Effectiveness Of Training Implementing Security Awareness Training
Assessment Test To Measure Effectiveness Of Training Implementing Security Awareness TrainingThe purpose of this slide is to outline a comprehensive assessment test which can be used by the trainer to evaluate the effectiveness of cyber security training plan. The questions covered in the slide is related to spam, ways to protect from cyberbullying etc. Increase audience engagement and knowledge by dispensing information using Assessment Test To Measure Effectiveness Of Training Implementing Security Awareness Training. This template helps you present information on four stages. You can also present information on Describes Spam, Cyberbullying, Protect The Confidential Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Comparative Assessment Of Security Awareness Implementing Security Awareness Training
Comparative Assessment Of Security Awareness Implementing Security Awareness TrainingThe purpose of this slide is to showcase comparison of various advance cyber security training courses. The comparison is drawn on the basis of course description, level, duration, no. of companies enrolled for this course etc. Present the topic in a bit more detail with this Comparative Assessment Of Security Awareness Implementing Security Awareness Training. Use it as a tool for discussion and navigation on Comparative Assessment, Security Awareness, Online Courses. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparison Of Various Security Awareness Training Implementing Security Awareness Training
Comparison Of Various Security Awareness Training Implementing Security Awareness TrainingThe purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. Deliver an outstanding presentation on the topic using this Comparison Of Various Security Awareness Training Implementing Security Awareness Training. Dispense information and present a thorough explanation of Phishing Simulations, Security Reporting, Deployment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Awareness Checklist To Ensure Implementing Security Awareness Training
Cyber Security Awareness Checklist To Ensure Implementing Security Awareness TrainingThe purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Deliver an outstanding presentation on the topic using this Cyber Security Awareness Checklist To Ensure Implementing Security Awareness Training. Dispense information and present a thorough explanation of Cyber Security, Awareness Checklist, Asset Protection using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Awareness Trends In 2023 Implementing Security Awareness Training
Cyber Security Awareness Trends In 2023 Implementing Security Awareness TrainingThe purpose of this slide is to showcase security awareness trends which the organization has to look out for in 2023. Increase malware and ransomware attack, more employees will be targeted by mobile malware attack and advancement of phishing attack are some of the major trends mentioned in the slide. Introducing Cyber Security Awareness Trends In 2023 Implementing Security Awareness Training to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Ransomware Attack, Malware Attack, Phishing Attack, using this template. Grab it now to reap its full benefits.
-
 Dos And Donts Of Prevention From Ransomware Attack Implementing Security Awareness Training
Dos And Donts Of Prevention From Ransomware Attack Implementing Security Awareness TrainingThe purpose of this slide is to showcase the Dos and donts of ransomware prevention attack. The slide covers information about updating the software, installing a firewall software, using reliable website and sources etc. Introducing Dos And Donts Of Prevention From Ransomware Attack Implementing Security Awareness Training to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Prevention, Ransomware Attack, using this template. Grab it now to reap its full benefits.
-
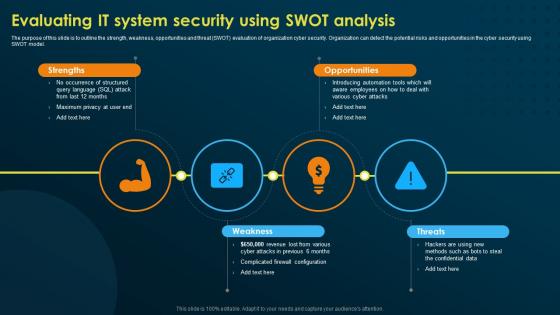 Evaluating It System Security Using Swot Analysis Implementing Security Awareness Training
Evaluating It System Security Using Swot Analysis Implementing Security Awareness TrainingThe purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Increase audience engagement and knowledge by dispensing information using Evaluating It System Security Using Swot Analysis Implementing Security Awareness Training. This template helps you present information on four stages. You can also present information on Strengths, Opportunities, Weakness, Threats using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Functional Chart Of Cyber Security Team Implementing Security Awareness Training
Functional Chart Of Cyber Security Team Implementing Security Awareness TrainingThe purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc. Present the topic in a bit more detail with this Functional Chart Of Cyber Security Team Implementing Security Awareness Training. Use it as a tool for discussion and navigation on Cyber Risk Manger, Security Operations Monitor, Threat Intelligence. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 G33 Table Of Contents Implementing Security Awareness Training To Prevent Cyber Attacks
G33 Table Of Contents Implementing Security Awareness Training To Prevent Cyber AttacksIntroducing G33 Table Of Contents Implementing Security Awareness Training To Prevent Cyber Attacks to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Current Assessment, Organization, Cyber Security, using this template. Grab it now to reap its full benefits.
-
 General Outlook Of Ransomware Attack Implementing Security Awareness Training
General Outlook Of Ransomware Attack Implementing Security Awareness TrainingThe purpose of this slide is to outline an example of ransomware attack. The slide provides information about the working of ransomware attack work and how it can encrypts the victims data. Increase audience engagement and knowledge by dispensing information using General Outlook Of Ransomware Attack Implementing Security Awareness Training. This template helps you present information on four stages. You can also present information on Programme, General Outlook, Ransomware Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
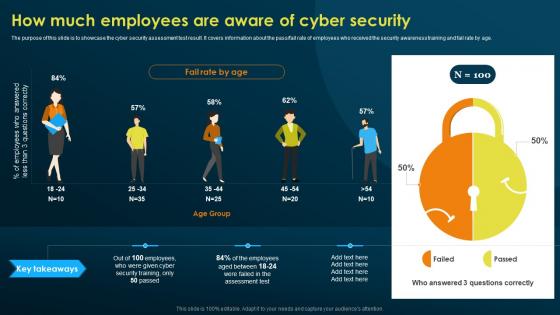 How Much Employees Are Aware Of Cyber Security Implementing Security Awareness Training
How Much Employees Are Aware Of Cyber Security Implementing Security Awareness TrainingThe purpose of this slide is to showcase the cyber security assessment test result. It covers information about the pass or fail rate of employees who received the security awareness training and fail rate by age. Introducing How Much Employees Are Aware Of Cyber Security Implementing Security Awareness Training to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Much Employees, Aware Of Cyber Security, using this template. Grab it now to reap its full benefits.
-
 Icons Slide For Implementing Security Awareness Training To Prevent Cyber Attacks
Icons Slide For Implementing Security Awareness Training To Prevent Cyber AttacksIntroducing our well researched set of slides titled Icons Slide For Implementing Security Awareness Training To Prevent Cyber Attacks. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Impact Of Cyber Security Breach General Consequences Implementing Security Awareness Training
Impact Of Cyber Security Breach General Consequences Implementing Security Awareness TrainingThe purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetary penalty and operational disruption. Introducing Impact Of Cyber Security Breach General Consequences Implementing Security Awareness Training to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on V, using this template. Grab it now to reap its full benefits.
-
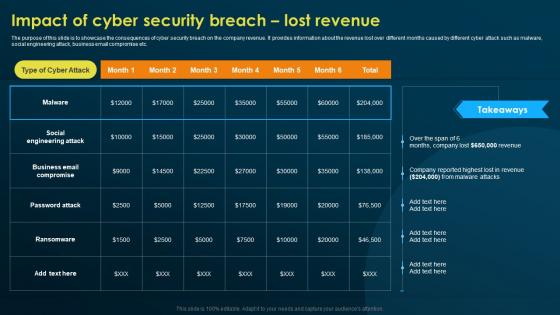 Impact Of Cyber Security Breach Lost Revenue Implementing Security Awareness Training
Impact Of Cyber Security Breach Lost Revenue Implementing Security Awareness TrainingThe purpose of this slide is to showcase the consequences of cyber security breach on the company revenue. It provides information about the revenue lost over different months caused by different cyber attack such as malware, social engineering attack, business email compromise etc. Present the topic in a bit more detail with this Impact Of Cyber Security Breach Lost Revenue Implementing Security Awareness Training. Use it as a tool for discussion and navigation on Social Engineering Attack, Business Email Compromise, Ransomware. This template is free to edit as deemed fit for your organization. Therefore download it now.





