Powerpoint Templates and Google slides for Implementing Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Ways To Educate Users On Secure Online Practices Implementing E Commerce Security Measures
Ways To Educate Users On Secure Online Practices Implementing E Commerce Security MeasuresThe purpose of the slide is to educate consumers on secure online practices. It include education on strong password habits, phasing attacks and secure payment methods . Introducing Ways To Educate Users On Secure Online Practices Implementing E Commerce Security Measures to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Strong Password Habits, Secure Payment Methods, Educate On Phishing, using this template. Grab it now to reap its full benefits.
-
 Solutions To Overcome Challenges For Implementing Cyber Security In Banking
Solutions To Overcome Challenges For Implementing Cyber Security In BankingThis slide showcases key solutions to overcome problems in banking cyber security. This slide aims to implement security solutions to prevent instances of misused or lost data and counter emerging cyber attacks. It includes various elements such as challenges, solutions and impact. Presenting our well structured Solutions To Overcome Challenges For Implementing Cyber Security In Banking. The topics discussed in this slide are Knowledge, Ransomware, Social Media. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 IT Security Awareness Training Program Implementing Table Of Contents Cybersecurity SS
IT Security Awareness Training Program Implementing Table Of Contents Cybersecurity SSIncrease audience engagement and knowledge by dispensing information using IT Security Awareness Training Program Implementing Table Of Contents Cybersecurity SS. This template helps you present information on one stages. You can also present information on Phishing Awareness, Objectives, Detecting Phishing Attacks, Preventing Phishing Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Objectives Of Implementing Anti Phishing Training IT Security Awareness Training Cybersecurity SS
Objectives Of Implementing Anti Phishing Training IT Security Awareness Training Cybersecurity SSThis slide represents details related to need of implementing training program for employees regarding attacks that are attempted to steal sensitive information in the form of user names, credit card numbers etc. Introducing Objectives Of Implementing Anti Phishing Training IT Security Awareness Training Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Anti Phishing Training Program, Steal Sensitive Information, Employees Regarding Attacks, using this template. Grab it now to reap its full benefits.
-
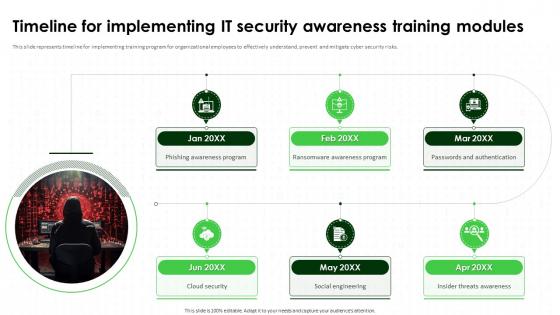 Timeline For Implementing IT Security Awareness Training Modules Cybersecurity SS
Timeline For Implementing IT Security Awareness Training Modules Cybersecurity SSThis slide represents timeline for implementing training program for organizational employees to effectively understand, prevent and mitigate cyber security risks. Increase audience engagement and knowledge by dispensing information using Timeline For Implementing IT Security Awareness Training Modules Cybersecurity SS. This template helps you present information on six stages. You can also present information on Ransomware Awareness Program, Passwords And Authentication, Social Engineering, Insider Threats Awareness using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Least Privilege Implementation For Accidental Building Next Generation Endpoint Security Cybersecurity SS
Least Privilege Implementation For Accidental Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases implementation of least privilege principle for avoiding accidental misuses. It provides details about security controls, data discovery, etc.Deliver an outstanding presentation on the topic using this Least Privilege Implementation For Accidental Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Action Steps, Real Problem Solved, Layering Security Controls using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Least Privilege Implementation For Segregation Building Next Generation Endpoint Security Cybersecurity SS
Least Privilege Implementation For Segregation Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases implementation of least privilege principle for segregation of duties. It provides details about time limits, certain access, etc.Introducing Least Privilege Implementation For Segregation Building Next Generation Endpoint Security Cybersecurity SS to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Action Steps, Real Problem Solved, Financial Data, using this template. Grab it now to reap its full benefits.
-
 Web Security Upgradation Before Vs After Implementing Web Security
Web Security Upgradation Before Vs After Implementing Web SecurityThis slide showcases the different performance metrics and how web security have improved these metrics. Present the topic in a bit more detail with this Web Security Upgradation Before Vs After Implementing Web Security. Use it as a tool for discussion and navigation on Threats, CSRF Vulnerabilities, SQL Injection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Web Security Upgradation Budget Allocation To Implement Web Security
Web Security Upgradation Budget Allocation To Implement Web SecurityThis slide represents the budget allocation for web security which includes training fees, security infrastructure, security audits, incident response, etc. Present the topic in a bit more detail with this Web Security Upgradation Budget Allocation To Implement Web Security. Use it as a tool for discussion and navigation on Budget Item, Estimated Cost, Actual Cost. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Web Security Upgradation Process Stages Of Implementing Vulnerability Scanning
Web Security Upgradation Process Stages Of Implementing Vulnerability ScanningThis slide gives an overview of the phases in the process of web security such as requirement analysis, test planning, test case development, etc. Present the topic in a bit more detail with this Web Security Upgradation Process Stages Of Implementing Vulnerability Scanning. Use it as a tool for discussion and navigation on Asset Inventory, Surface Scanning, Detection And Classification, Remediation Actions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Web Security Upgradation Project Summary For Implementing Web Security
Web Security Upgradation Project Summary For Implementing Web SecurityThe purpose of this slide is to represent the summary of the web security project providing information regarding problems faced, recommended solution, etc. Introducing Web Security Upgradation Project Summary For Implementing Web Security to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Problems, Solutions, Estimated Cost, Estimated Timeline, using this template. Grab it now to reap its full benefits.
-
 Web Security Upgradation Roadmap For Implementing Web Security In Organization
Web Security Upgradation Roadmap For Implementing Web Security In OrganizationThis slide outlines the steps that an organization should take while conducting web security which include education, infrastructure security, etc. Introducing Web Security Upgradation Roadmap For Implementing Web Security In Organization to increase your presentation threshold. Encompassed with Seven stages, this template is a great option to educate and entice your audience. Dispence information on Education And Planning, Infrastructure Security, Incident Response, using this template. Grab it now to reap its full benefits.
-
 Web Security Upgradation Steps For Implementing Vulnerability Scanning In Web Security
Web Security Upgradation Steps For Implementing Vulnerability Scanning In Web SecurityThis slide highlights the process phases for implementing vulnerability scanning which include creating asset inventory, scanning the attack surface, etc. Introducing Web Security Upgradation Steps For Implementing Vulnerability Scanning In Web Security to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Information Regarding Vulnerabilities Discovered, Creates Asset Inventory, using this template. Grab it now to reap its full benefits.
-
 Web Security Upgradation Team Structure For Implementing Web Security
Web Security Upgradation Team Structure For Implementing Web SecurityThis slide represents the team structure for the web security in the IT infrastructure which includes manager, team lead, web security team, etc. Present the topic in a bit more detail with this Web Security Upgradation Team Structure For Implementing Web Security. Use it as a tool for discussion and navigation on Team Lead, Web Security Team, Security Analyst. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Email Security Best Practices Before Vs After Implementing Email Security Policies
Email Security Best Practices Before Vs After Implementing Email Security PoliciesThis slide shows the before vs. after comparison of implementing email security policies. The different aspects compared in this slide are data security, phishing incidents, productivity, regulatory compliance, and system downtime. Present the topic in a bit more detail with this Email Security Best Practices Before Vs After Implementing Email Security Policies. Use it as a tool for discussion and navigation on Data Security, Phishing Incidents, Productivity, Regulatory Compliance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Email Security Best Practices Budget Of Implementing Email Security Policies
Email Security Best Practices Budget Of Implementing Email Security PoliciesThis slide represents the budget of incorporating email security policies in an organization. The different cost components are email security software, hardware and infrastructure, employee training, managed services, incident response, etc. Present the topic in a bit more detail with this Email Security Best Practices Budget Of Implementing Email Security Policies. Use it as a tool for discussion and navigation on Email Security Software, Hardware And Infrastructure, Employee Training, Managed Services. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Email Security Best Practices Email Security Implementation Impact On Businesses
Email Security Best Practices Email Security Implementation Impact On BusinessesThis slide illustrates the business impact of implementing email security policies. The parameters described in this slide are improved data protection, reduced phishing attacks, increased employee productivity, enhanced brand reputation, etc. Present the topic in a bit more detail with this Email Security Best Practices Email Security Implementation Impact On Businesses. Use it as a tool for discussion and navigation on Improved Data Protection, Reduced Phishing Attacks, Increased Employee Productivity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Email Security Best Practices Roadmap For Implementing Email Security Policies
Email Security Best Practices Roadmap For Implementing Email Security PoliciesThis slide represents the roadmap to implement email security policies. These include strong password, two-factor authentication, email encryption, software updating, choose a trustworthy email provider, use a VPN Virtual Private Network , etc. Introducing Email Security Best Practices Roadmap For Implementing Email Security Policies to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Two-Factor Authentication, Email Encryption, Trustworthy Email Provider, Virtual Private Network, using this template. Grab it now to reap its full benefits.
-
 Email Security Best Practices Timeline For Email Security Measures Implementation
Email Security Best Practices Timeline For Email Security Measures ImplementationThis slide shows the timeline for applying email security policies in organization. These include strong password, two-factor authentication, email encryption, software updating, choose a trustworthy email provider, use a VPN Virtual Private Network , etc. Introducing Email Security Best Practices Timeline For Email Security Measures Implementation to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Two-Factor Authentication, Email Encryption, Virtual Private Network, using this template. Grab it now to reap its full benefits.
-
 Different Strategies For Securing Appropriate Grants Implementation Of Fundraising Strategy For Social
Different Strategies For Securing Appropriate Grants Implementation Of Fundraising Strategy For SocialThe slide illustrates various strategies to secure the right grant option as per the fiscal needs of the social enterprise. Various strategies included are align project with funding requirements, review fiscal needs and improve funding information.Introducing Different Strategies For Securing Appropriate Grants Implementation Of Fundraising Strategy For Social to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Improve Funding Information, Review Fiscal Needs, Funding Requirements, using this template. Grab it now to reap its full benefits.
-
 Before Vs After Implementing Web Security Solution
Before Vs After Implementing Web Security SolutionThis slide showcases the different performance metrics and how web security have improved these metrics. Present the topic in a bit more detail with this Before Vs After Implementing Web Security Solution. Use it as a tool for discussion and navigation on Csrf Vulnerabilities, Parameterized Queries, Sql Injection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Business Benefits Of Implementing Web Security Solution
Business Benefits Of Implementing Web Security SolutionThis slide outlines the pros of web security in business which include safeguarding sensitive data, securing private information, etc. Introducing Business Benefits Of Implementing Web Security Solution to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Safeguard Sensitive Data, Secure Private Information, Prevent Costly Service Disruptions, using this template. Grab it now to reap its full benefits.
-
 Key Features Of Implementing Web Security Solution
Key Features Of Implementing Web Security SolutionThis slide highlights the main objectives of implementing web security in an organization which include security, password control, etc. Introducing Key Features Of Implementing Web Security Solution to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Secure Socket Layer, Password Control, Security, Firewall, using this template. Grab it now to reap its full benefits.
-
 Roadmap For Implementing Web Security In Organization
Roadmap For Implementing Web Security In OrganizationThis slide outlines the steps that an organization should take while conducting web security such as education, infrastructure security, etc. Introducing Roadmap For Implementing Web Security In Organization to increase your presentation threshold. Encompassed with Seven stages, this template is a great option to educate and entice your audience. Dispence information on Education And Planning, Infrastructure Security, Application Security, using this template. Grab it now to reap its full benefits.
-
 Web Security Solution Budget Allocation For Web Security Implementation
Web Security Solution Budget Allocation For Web Security ImplementationThis slide showcases the breakdown cost for different components such as hardware, connectivity, maintenance and support, etc. Present the topic in a bit more detail with this Web Security Solution Budget Allocation For Web Security Implementation. Use it as a tool for discussion and navigation on Estimated Cost, Actual Cost, Encryption Tools, Connectivity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 A247 Best Practices For Web Security Implementation
A247 Best Practices For Web Security ImplementationThe purpose of this slide is to highlight the best practices for web security such as inclusive security practices, cybersecurity adoption, etc. Introducing A247 Best Practices For Web Security Implementation to increase your presentation threshold. Encompassed with Seven stages, this template is a great option to educate and entice your audience. Dispence information on Inclusive Security Practices, Diverse Security Measures, Security Exercises, using this template. Grab it now to reap its full benefits.
-
 Security Measures To Implement In Automated Messaging
Security Measures To Implement In Automated MessagingThe purpose of this slide is to outline security measures to be implemented in automated messaging systems such as opting for a reliable SMS provider, SMS verification, etc., for ensuring data protection, encryption, etc. Introducing our premium set of slides with Security Measures To Implement In Automated Messaging. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Reliable SMS Provider, SMS Verification, Otps Keywords. So download instantly and tailor it with your information.
-
 Penetration Testing Implementation Plan Existing It Security Infrastructure Constituants
Penetration Testing Implementation Plan Existing It Security Infrastructure ConstituantsThis slide highlights the components of the current IT security infrastructure, which are prone to several security concerns. These constituents are access control, application security, firewalls, virtual private networks VPN, antivirus, etc. Deliver an outstanding presentation on the topic using this Penetration Testing Implementation Plan Existing It Security Infrastructure Constituants. Dispense information and present a thorough explanation of Access Control, Application Security, Antivirus Or Antimalware Systems, Password Auditing Tools using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Penetration Testing Implementation Plan Key Challenges Of Existing It Security
Penetration Testing Implementation Plan Key Challenges Of Existing It SecurityThis slide discusses the security issues faced by the organization due to a lack of security in infrastructure. These concerns are unauthorized access, data breaches, malware and ransomware, phishing attacks, data loss or corruption, compliance, etc. Deliver an outstanding presentation on the topic using this Penetration Testing Implementation Plan Key Challenges Of Existing It Security. Dispense information and present a thorough explanation of Unauthorized Access, Data Breaches, Malware And Ransomware, Phishing Attacks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Penetration Testing Implementation Plan Performance Analysis Of Existing It Security
Penetration Testing Implementation Plan Performance Analysis Of Existing It SecurityThe purpose of this slide is to indicate the performance analysis of the organizations current security infrastructure. The key components include where we are, the gap, where we want to be, and recommended solutions. Increase audience engagement and knowledge by dispensing information using Penetration Testing Implementation Plan Performance Analysis Of Existing It Security. This template helps you present information on Four stages. You can also present information on Ideal Testing, Organization, Penetration Testing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Penetration Testing Implementation Plan Stages Of Penetration Testing In Cyber Security
Penetration Testing Implementation Plan Stages Of Penetration Testing In Cyber SecurityThis slide represents the process included in penetration testing. The purpose of this slide is to showcase the different steps of penetration testing, such as planning the penetration test, gathering information, scanning for vulnerabilities, and so on. Increase audience engagement and knowledge by dispensing information using Penetration Testing Implementation Plan Stages Of Penetration Testing In Cyber Security. This template helps you present information on Six stages. You can also present information on Plan The Penetration Test, Gather Information, Scan using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Architecture Of Effective Application Security Implementation
Architecture Of Effective Application Security ImplementationThis slide represents the architecture of efficient application security deployment which includes components such as client tier, user applications and data, etc. Presenting our well structured Architecture Of Effective Application Security Implementation The topics discussed in this slide are Clients Tier, Users Data and ApplicationsThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Budget Distribution For Mobile Security Implementation Mobile Device Security Cybersecurity SS
Budget Distribution For Mobile Security Implementation Mobile Device Security Cybersecurity SSThis slide showcases budget distribution that can help to implement mobile security solutions. Its key elements are biometric solution, virtual private network, employee training, data encryption etc. Introducing Budget Distribution For Mobile Security Implementation Mobile Device Security Cybersecurity SS to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Biometric Solution, Virtual Private Network, Employee Training using this template. Grab it now to reap its full benefits.
-
 Plan To Implement Different Mobile Biometric Techniques Mobile Device Security Cybersecurity SS
Plan To Implement Different Mobile Biometric Techniques Mobile Device Security Cybersecurity SSThis slide showcases plan that can help company to implement mobile biometric solutions. Its key components are biometric technique, team responsible, expected benefits, progress and budget allocated. Deliver an outstanding presentation on the topic using this Plan To Implement Different Mobile Biometric Techniques Mobile Device Security Cybersecurity SS Dispense information and present a thorough explanation of Policy Development, Choose Solution, Train Users using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Process To Implement Mobile Device Management Mobile Device Security Cybersecurity SS
Process To Implement Mobile Device Management Mobile Device Security Cybersecurity SSThis slide showcases procedure that can help organization to implement mobile device management solution. Its key steps are current scenario assessment, policy development, choose solution etc. Increase audience engagement and knowledge by dispensing information using Process To Implement Mobile Device Management Mobile Device Security Cybersecurity SS This template helps you present information on Five stages. You can also present information on Estimated Budget, Phase Duration using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Process To Implement Mobile Vpn In Organization Mobile Device Security Cybersecurity SS
Process To Implement Mobile Vpn In Organization Mobile Device Security Cybersecurity SSThis slide showcases procedure that can help organization to implement VPN for mobile security. Its key steps are assessment, VPN technology selection, infrastructure setup etc. Introducing Process To Implement Mobile Vpn In Organization Mobile Device Security Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Rating, Ideal, Softwares using this template. Grab it now to reap its full benefits.
-
 Roadmap For Mobile Security Solutions Implementation Mobile Device Security Cybersecurity SS
Roadmap For Mobile Security Solutions Implementation Mobile Device Security Cybersecurity SSThis slide showcases roadmap that can help to implement mobile security solutions. Its key elements are estimated budget, duration of different phases etc. Present the topic in a bit more detail with this Roadmap For Mobile Security Solutions Implementation Mobile Device Security Cybersecurity SS Use it as a tool for discussion and navigation on Device Security Budget, Device Security Solutions, Techniques Effectiveness This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Adopting Homomorphic Encryption To Secure Cloud Computing Implementing Digital Transformation And Ai DT SS
Adopting Homomorphic Encryption To Secure Cloud Computing Implementing Digital Transformation And Ai DT SSThis slide provides glimpse about utilizing homomorphic encryption approach that can help businesses in privacy preservation. It includes stages such as encryption, computation, decryption, etc. Increase audience engagement and knowledge by dispensing information using Adopting Homomorphic Encryption To Secure Cloud Computing Implementing Digital Transformation And Ai DT SS. This template helps you present information on three stages. You can also present information on Privacy Preservation, Secure Cloud Computing, Model Owner using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Incorporating Secure Multi Party Computation To Boost Data Implementing Digital Transformation And Ai DT SS
Incorporating Secure Multi Party Computation To Boost Data Implementing Digital Transformation And Ai DT SSThis slide provides glimpse about utilizing secure multi party computation SMPC approach that can help businesses in boosting data confidentiality. It includes stages such as input sharing, secure computation, output reconstruction, etc. Increase audience engagement and knowledge by dispensing information using Incorporating Secure Multi Party Computation To Boost Data Implementing Digital Transformation And Ai DT SS. This template helps you present information on three stages. You can also present information on Increase Security Against Attacks, Boost Data Confidentiality, Input Sharing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 United Nations And Cyber Security Initiatives Strategic Guide To Implement Strategy SS
United Nations And Cyber Security Initiatives Strategic Guide To Implement Strategy SSThis slide showcases the United nations and cyber security initiatives. It includes initiatives such as UN general assembly resolutions, UNODA, UNIDIR, CTC and UNODC.Increase audience engagement and knowledge by dispensing information using United Nations And Cyber Security Initiatives Strategic Guide To Implement Strategy SS. This template helps you present information on five stages. You can also present information on General Assembly Resolutions, Disarmament Affairs, Disarmament Research using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 User Based Security Training Model Strategic Guide To Implement Strategy SS
User Based Security Training Model Strategic Guide To Implement Strategy SSIntroducing User Based Security Training Model Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Compromised System, Compromised Network, Critical Assets, Exfiltrate Sensitive Data, using this template. Grab it now to reap its full benefits.
-
 Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Suspicious Activities And Prevent Threats, Protect Organizations Networks, Filter Out Malicious Activities, Security Devices Or Controls, using this template. Grab it now to reap its full benefits.
-
 Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing our well researched set of slides titled Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Implementing Intrusion Prevention Impact Of Inefficient Network Security Cybersecurity SS
Implementing Intrusion Prevention Impact Of Inefficient Network Security Cybersecurity SSThis slide represents the impact of outdated cybersecurity solutions on organizational operations which leads to compromised data security, data leakage, and damage to the organizations reputation. Introducing Implementing Intrusion Prevention Impact Of Inefficient Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Compromised Data Integrity, Increase In Risk Of Data Leakage, Increase In Recovery Costs, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents For Implementing Intrusion Prevention System For Effective Network Security
Table Of Contents For Implementing Intrusion Prevention System For Effective Network SecurityIntroducing Table Of Contents For Implementing Intrusion Prevention System For Effective Network Security to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Issues Experienced Due Inefficient Network Security, Impact On Organizational Operations, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Budget Plan, Impact Assessment, Dashboards, Case Study Analysis, using this template. Grab it now to reap its full benefits.
-
 Cost Benefit Analysis For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SS
Cost Benefit Analysis For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SSThis slide shows the cost-benefit analysis of implementing network vulnerability management strategies, including the costs incurred in end-to-end encryption and phishing awareness training, etc.Deliver an outstanding presentation on the topic using this Cost Benefit Analysis For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Costs, Benefits, Description, Initial Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Investment Plan For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SS
Investment Plan For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SSThis slide details the costs associated with deploying network vulnerability management solutions for an enterprise. It includes expenses for implementing E2E software, IT talent acquisition costs etc.Deliver an outstanding presentation on the topic using this Investment Plan For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Parameters, Forecasted Budget, Actual Costs, Variance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
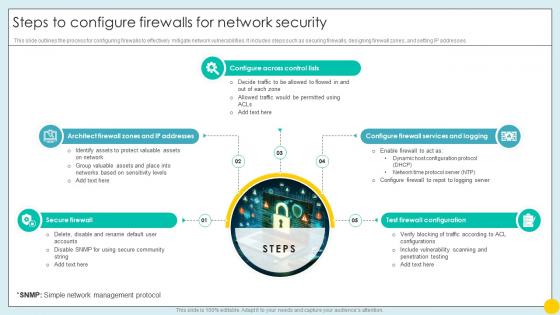 Steps To Configure Firewalls For Network Security Implementing Strategies For Mitigating Cybersecurity SS
Steps To Configure Firewalls For Network Security Implementing Strategies For Mitigating Cybersecurity SSThis slide outlines the process for configuring firewalls to effectively mitigate network vulnerabilities. It includes steps such as securing firewalls, designing firewall zones, and setting IP addresses.Increase audience engagement and knowledge by dispensing information using Steps To Configure Firewalls For Network Security Implementing Strategies For Mitigating Cybersecurity SS. This template helps you present information on five stages. You can also present information on Secure Firewall, Configure Across Control Lists, Test Firewall Configuration using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategies To Implement Encryption Trends In Data Security
Strategies To Implement Encryption Trends In Data SecurityThe purpose of this slide is to guide and inform on effective strategies for implementing encryption trends in data security. It provides actionable insights to enhance data protection and address evolving cyber threats. Introducing our Strategies To Implement Encryption Trends In Data Security set of slides. The topics discussed in these slides are Biometric Authentication, Multi-Factor Authentication, Cloud Encryption, Blockchain Encryption. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Attacks Faced By The Company In Previous Year Implementing Cyber Security Ppt Demonstration
Cyber Attacks Faced By The Company In Previous Year Implementing Cyber Security Ppt DemonstrationThis slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Present the topic in a bit more detail with this Cyber Attacks Faced By The Company In Previous Year Implementing Cyber Security Ppt Demonstration. Use it as a tool for discussion and navigation on Ransomware Attacks, Phishing Attacks, Previous Year. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
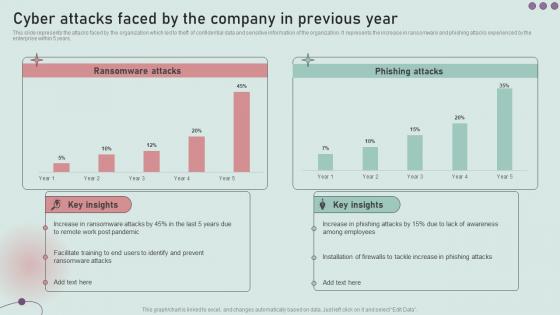 Cyber Attacks Faced By The Company In Previous Year Development And Implementation Of Security
Cyber Attacks Faced By The Company In Previous Year Development And Implementation Of SecurityThis slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Present the topic in a bit more detail with this Cyber Attacks Faced By The Company In Previous Year Development And Implementation Of Security. Use it as a tool for discussion and navigation on Ransomware Attacks, Phishing Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
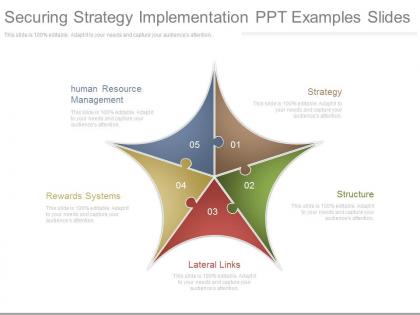 Securing strategy implementation ppt examples slides
Securing strategy implementation ppt examples slidesQuick and simple download without any hassles. Modify text anywhere as per the context. Insert your own company logo, tagline, trademark, brand name etc. Absolutely modifiable PPT infographics- change color and contrast as required. No change in resolution of PPT images after editing. Fully alterable size and orientation of presentation icons.The stages in this process are human resource management, strategy, structure, lateral links, rewards systems.
-
 Securing strategy implementation powerpoint ideas
Securing strategy implementation powerpoint ideasPresenting securing strategy implementation powerpoint ideas. This is a securing strategy implementation powerpoint ideas. This is a five stage process. The stages in this process are strategy, structure, lateral links, reward systems, human resource management.
-
 Security policy and implementation guidance template ppt design
Security policy and implementation guidance template ppt designPresenting security policy and implementation guidance template ppt design. This is a security policy and implementation guidance template ppt design. This is a six stage process. The stages in this process are client and operation structure, training and presentation, information flow, aggregation control, department size vs operation size, access control and network infrastructure.
-
 Cyberterrorism it impact of implementing cyber security measures in the company
Cyberterrorism it impact of implementing cyber security measures in the companyThis slide represents the current state of cyber assaults in a business after implementing the cyber security model. Present the topic in a bit more detail with this Cyberterrorism IT Impact Of Implementing Cyber Security Measures In The Company. Use it as a tool for discussion and navigation on Number Attacks, Cyber Terrorists Attacks 2021, Cyber Terrorists Attacks 2022. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Impact On Organization After Implementing Information Strategy Training
Information Security Impact On Organization After Implementing Information Strategy TrainingThis slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Present the topic in a bit more detail with this Information Security Impact On Organization After Implementing Information Strategy Training. Use it as a tool for discussion and navigation on Implementing, Information, Strategy. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Network Security Impact On Organization After Implementing
Network Security Impact On Organization After ImplementingThis slide depicts the impact of network security training on an organization. It also shows how trained employees can reduce network attacks in the organization. Deliver an outstanding presentation on the topic using this Network Security Impact On Organization After Implementing. Dispense information and present a thorough explanation of Impact On Organization After Implementing Network Security Strategy And Training using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Impact Organization After Implementing Strategy Training
Information Technology Security Impact Organization After Implementing Strategy TrainingThis slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Present the topic in a bit more detail with this Information Technology Security Impact Organization After Implementing Strategy Training. Use it as a tool for discussion and navigation on Organization, Implementing, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Terrorism Attacks Impact Of Implementing Cyber Security
Cyber Terrorism Attacks Impact Of Implementing Cyber SecurityThis slide represents the current state of cyber assaults in a business after implementing the cyber security model. Deliver an outstanding presentation on the topic using this Cyber Terrorism Attacks Impact Of Implementing Cyber Security. Dispense information and present a thorough explanation of Impact Of Implementing Cyber Security Measures In The Company using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





