Powerpoint Templates and Google slides for Implementing Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Timeline To Implement Secure Access Service Edge Cloud Security Model
Timeline To Implement Secure Access Service Edge Cloud Security ModelThis slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Increase audience engagement and knowledge by dispensing information using Timeline To Implement Secure Access Service Edge Cloud Security Model. This template helps you present information on seven stages. You can also present information on Objectives, Solutions, Deployment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icon For Implementation Of Cyber Security Strategy Action Plan
Icon For Implementation Of Cyber Security Strategy Action PlanPresenting our set of slides with Icon For Implementation Of Cyber Security Strategy Action Plan. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Implementation, Strategy, Security.
-
 Strategic Cyber Security Action And Implementation Plan
Strategic Cyber Security Action And Implementation PlanThe slide showcases strategic cyber security action and implementation plan for protecting confidential data in an organization. It contains quarterly timeline with points, such as benchmark, analysis, vision, roadmap, mobilization, etc. Introducing our Strategic Cyber Security Action And Implementation Plan set of slides. The topics discussed in these slides are Analysis, Vision, Implementation. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Sase Security Approaches To Implement Zero Trust Network Access
Sase Security Approaches To Implement Zero Trust Network AccessThis slide depicts the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access. It also includes how users access business services and applications in both approaches. Deliver an outstanding presentation on the topic using this Sase Security Approaches To Implement Zero Trust Network Access. Dispense information and present a thorough explanation of Approaches, Organizations, Business using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Security Best Practices To Implement Cloud Access Security Broker
Sase Security Best Practices To Implement Cloud Access Security BrokerThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Sase Security Best Practices To Implement Cloud Access Security Broker. Dispense information and present a thorough explanation of Implementing, Solutions, Consumption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Security Budget To Implement Secure Access Service Edge
Sase Security Budget To Implement Secure Access Service EdgeThis slide depicts the budget calculation for implementing a secure access service edge model in an organization. The purpose of this slide is to showcase the estimated and actual cost and variance for SASE model spending. The key components include SD-WAN, SWG, ZTNA, CASB, and FWaaS. Present the topic in a bit more detail with this Sase Security Budget To Implement Secure Access Service Edge. Use it as a tool for discussion and navigation on Organization, Service, Implementing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Security Challenges And Solutions For Sase Implementation
Sase Security Challenges And Solutions For Sase ImplementationThis slide represents the challenges and solutions for implementing a secure access service edge in an organization. The purpose of this slide is to showcase the different challenges that a business can face while deploying the SASE model into a business. The key challenges include networking and security team misalignment, change management, etc. Present the topic in a bit more detail with this Sase Security Challenges And Solutions For Sase Implementation. Use it as a tool for discussion and navigation on Implementation, Solutions, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Security Checklist To Implement Secure Access Service Edge
Sase Security Checklist To Implement Secure Access Service EdgePresent the topic in a bit more detail with this Sase Security Checklist To Implement Secure Access Service Edge. Use it as a tool for discussion and navigation on Service, Implement, Secure Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Security Cloud Security Broker Implementation Models Ppt Show Graphics Tutorials
Sase Security Cloud Security Broker Implementation Models Ppt Show Graphics TutorialsThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Present the topic in a bit more detail with this Sase Security Cloud Security Broker Implementation Models Ppt Show Graphics Tutorials. Use it as a tool for discussion and navigation on Implementation, Technique, Applications. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Security Roadmap To Implement Secure Access Service Edge
Sase Security Roadmap To Implement Secure Access Service EdgeThis slide depicts the roadmap to implementing secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and, discovering gaps, etc. Increase audience engagement and knowledge by dispensing information using Sase Security Roadmap To Implement Secure Access Service Edge. This template helps you present information on seven stages. You can also present information on Roadmap, Service, Solutions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Security Secure Edge Implementation Steps Ppt Show Design Inspiration
Sase Security Secure Edge Implementation Steps Ppt Show Design InspirationThis slide outlines the steps to implement a secure service edge in a business. The purpose of this slide is to demonstrate the various guidelines to consider while implementing the SASE model in an organization. The main steps include defining SASE goals and requirements, selecting the SD-WAN backbone, incorporating zero-trust solutions, etc. Introducing Sase Security Secure Edge Implementation Steps Ppt Show Design Inspiration to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Incorporate Zero Trust Solutions, Test Troubleshoot, Optimize SASE Setup, using this template. Grab it now to reap its full benefits.
-
 Sase Security Timeline To Implement Cloud Access Security Broker
Sase Security Timeline To Implement Cloud Access Security BrokerThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Increase audience engagement and knowledge by dispensing information using Sase Security Timeline To Implement Cloud Access Security Broker. This template helps you present information on seven stages. You can also present information on Timeline, Applications, Environments using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Security Timeline To Implement Secure Access Service Edge
Sase Security Timeline To Implement Secure Access Service EdgeThis slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Introducing Sase Security Timeline To Implement Secure Access Service Edge to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Timeline, Service, Troubleshooting, using this template. Grab it now to reap its full benefits.
-
 Approaches To Implement Zero Trust Network Access Secure Access Service Edge Sase
Approaches To Implement Zero Trust Network Access Secure Access Service Edge SaseThis slide depicts the two primary approaches to implementing zero-trust network access for organizations. The purpose of this slide is to showcase the endpoint-initiated and service-initiated approach of zero-trust network access. It also includes how users access business services and applications in both approaches. Deliver an outstanding presentation on the topic using this Approaches To Implement Zero Trust Network Access Secure Access Service Edge Sase. Dispense information and present a thorough explanation of Approaches, Endpoint Initiated, Service Initiated using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices To Implement Cloud Access Security Broker Secure Access Service Edge Sase
Best Practices To Implement Cloud Access Security Broker Secure Access Service Edge SaseThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Best Practices To Implement Cloud Access Security Broker Secure Access Service Edge Sase. Dispense information and present a thorough explanation of Consumption, Implementing, Solutions using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Budget To Implement Secure Access Service Edge Secure Access Service Edge Sase
Budget To Implement Secure Access Service Edge Secure Access Service Edge SaseThis slide depicts the budget calculation for implementing a secure access service edge model in an organization. The purpose of this slide is to showcase the estimated and actual cost and variance for SASE model spending. The key components include SD-WAN, SWG, ZTNA, CASB, and FWaaS. Present the topic in a bit more detail with this Budget To Implement Secure Access Service Edge Secure Access Service Edge Sase. Use it as a tool for discussion and navigation on Service, Implementing, Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Challenges And Solutions For Sase Implementation Secure Access Service Edge Sase
Challenges And Solutions For Sase Implementation Secure Access Service Edge SaseThis slide represents the challenges and solutions for implementing a secure access service edge in an organization. The purpose of this slide is to showcase the different challenges that a business can face while deploying the SASE model into a business. The key challenges include networking and security team misalignment, change management, etc. Present the topic in a bit more detail with this Challenges And Solutions For Sase Implementation Secure Access Service Edge Sase. Use it as a tool for discussion and navigation on Organization, Implementation, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist To Implement Secure Access Service Edge Secure Access Service Edge Sase
Checklist To Implement Secure Access Service Edge Secure Access Service Edge SaseDeliver an outstanding presentation on the topic using this Checklist To Implement Secure Access Service Edge Secure Access Service Edge Sase. Dispense information and present a thorough explanation of Service, Responsible Person, Implement using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Security Broker Implementation Models Secure Access Service Edge Sase
Cloud Security Broker Implementation Models Secure Access Service Edge SaseThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Increase audience engagement and knowledge by dispensing information using Cloud Security Broker Implementation Models Secure Access Service Edge Sase. This template helps you present information on three stages. You can also present information on Implementation, Applications, Inline Deployment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Roadmap To Implement Secure Access Service Edge Secure Access Service Edge Sase
Roadmap To Implement Secure Access Service Edge Secure Access Service Edge SaseThis slide depicts the roadmap to implementing secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and, discovering gaps, etc. Increase audience engagement and knowledge by dispensing information using Roadmap To Implement Secure Access Service Edge Secure Access Service Edge Sase. This template helps you present information on six stages. You can also present information on Environment, Solutions, Troubleshooting using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Secure Access Edge Implementation Steps Secure Access Service Edge Sase
Secure Access Edge Implementation Steps Secure Access Service Edge SaseThis slide outlines the steps to implement a secure service edge in a business. The purpose of this slide is to demonstrate the various guidelines to consider while implementing the SASE model in an organization. The main steps include defining SASE goals and requirements, selecting the SD-WAN backbone, incorporating zero-trust solutions, etc. Introducing Secure Access Edge Implementation Steps Secure Access Service Edge Sase to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Incorporate Zero Trust Solutions, Optimize SASE Setup, Service, using this template. Grab it now to reap its full benefits.
-
 Timeline To Implement Secure Access Service Edge Secure Access Service Edge Sase
Timeline To Implement Secure Access Service Edge Secure Access Service Edge SaseThis slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Introducing Timeline To Implement Secure Access Service Edge Secure Access Service Edge Sase to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Timeline, Service, Environment, using this template. Grab it now to reap its full benefits.
-
 Strategic Plan To Implement Best Practices For Effective Endpoint Security Strategy SS V
Strategic Plan To Implement Best Practices For Effective Endpoint Security Strategy SS VThis slide represents best practices for effective endpoint security. It covers educating users, finding and tracking business-owned devices, and installation maintenance of operating systems. Increase audience engagement and knowledge by dispensing information using Strategic Plan To Implement Best Practices For Effective Endpoint Security Strategy SS V This template helps you present information on Three stages. You can also present information on Educate Users, Find And Track Devices using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategic Plan To Implement Data Encryption Model For Effective Information Security Strategy SS V
Strategic Plan To Implement Data Encryption Model For Effective Information Security Strategy SS VThis slide represents data encryption model for effective information security. It includes data encoding, data decoding, backup repository etc. Present the topic in a bit more detail with this Strategic Plan To Implement Data Encryption Model For Effective Information Security Strategy SS V Use it as a tool for discussion and navigation on Employee Headcount, Average Employee Age, Gender Diversity Ratio This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategic Plan To Implement Key Access Security Control Models Strategy SS V
Strategic Plan To Implement Key Access Security Control Models Strategy SS VThis slide represents key access security control models for organizations. It includes discretionary access control, mandatory access control, role-based access control and attributes based access control. Deliver an outstanding presentation on the topic using this Strategic Plan To Implement Key Access Security Control Models Strategy SS V Dispense information and present a thorough explanation of This slide represents key access security control models for organizations. It includes discretionary access control, mandatory access control, role-based access control and attributes based access control, using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategic Plan To Implement Most Commonly Types Of Ict Securities Used By Businesses Strategy SS V
Strategic Plan To Implement Most Commonly Types Of Ict Securities Used By Businesses Strategy SS VThis slide represents various types of information and communication technology ICT securities used by businesses. It covers network security, endpoint security, access security, and data encryption. Introducing Strategic Plan To Implement Most Commonly Types Of Ict Securities Used By Businesses Strategy SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on IT Governance, Visualization, Resource Management using this template. Grab it now to reap its full benefits.
-
 Strategic Plan To Implement Network Security Model To Effective Communication Strategy SS V
Strategic Plan To Implement Network Security Model To Effective Communication Strategy SS VThis slide represents the network security model for effective communication in the organization. It covers information regarding security threats, firewalls, virtual private networks, etc. Deliver an outstanding presentation on the topic using this Strategic Plan To Implement Network Security Model To Effective Communication Strategy SS V Dispense information and present a thorough explanation of Communication, Data Management, Marketing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS V
Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS VThis slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc. Introducing Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS V to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Incident Management, Request Fulfillment using this template. Grab it now to reap its full benefits.
-
 Need To Implement IoT Cyber Security Improving IoT Device Cybersecurity IoT SS
Need To Implement IoT Cyber Security Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to exhibit need to implement Internet of Things IoT security in order to avoid cyber attack and minimize losses. The slide covers information about data protection of users, adhering to regulatory standards, limited security of IoT devices, etc. Introducing Need To Implement IoT Cyber Security Improving IoT Device Cybersecurity IoT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Required, Companies, Potential, using this template. Grab it now to reap its full benefits.
-
 Steps To Implement Cryptographic Cloud Security Cloud Cryptography
Steps To Implement Cryptographic Cloud Security Cloud CryptographyThe purpose of this slide is to outline the various steps to be followed while implementing cloud cryptography. These include identify and classify sensitive data, choose the appropriate cryptographic algorithm, use strong encryption keys, manage keys effectively, etc. Increase audience engagement and knowledge by dispensing information using Steps To Implement Cryptographic Cloud Security Cloud Cryptography. This template helps you present information on eight stages. You can also present information on Cryptographic, Appropriate, Implement Access Controls using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Plan Implementation Timeline Improving Cyber Security Risks Management
Cyber Security Plan Implementation Timeline Improving Cyber Security Risks ManagementThe following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Introducing Cyber Security Plan Implementation Timeline Improving Cyber Security Risks Management to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Systems And Passwords, Perform Simulated, Phishing Exercise, using this template. Grab it now to reap its full benefits.
-
 Implement Best Practices To Prevent Cyber Attacks Improving Cyber Security Risks Management
Implement Best Practices To Prevent Cyber Attacks Improving Cyber Security Risks ManagementThe following slide illustrates some best practices to execute preventive actions for cyber attacks. It includes elements such as train employees, updating systems and software, developing incident response plan, backing up data, maintaining compliance etc. Increase audience engagement and knowledge by dispensing information using Implement Best Practices To Prevent Cyber Attacks Improving Cyber Security Risks Management. This template helps you present information on six stages. You can also present information on Train Employees, Maintain Compliance, Develop Incident Response Plan using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Challenges In Implementing Security Patch Management Process
Challenges In Implementing Security Patch Management ProcessFollowing slide showcases constraints in establishing security patch management process. The purpose of this slide is to provide information regarding challenges faced by businesses in ensuring the security of an organizations infrastructure. It also provides solutions to overcome challenges.Introducing our Challenges In Implementing Security Patch Management Process set of slides. The topics discussed in these slides are Existing Software, Vulnerabilities Prioritize, Compatibility Issues. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Best Practices To Implement Cloud Access Security Broker SASE Network Security
Best Practices To Implement Cloud Access Security Broker SASE Network SecurityThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Best Practices To Implement Cloud Access Security Broker SASE Network Security. Dispense information and present a thorough explanation of Visibility, Risk, Release using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker Implementation Models SASE Network Security
Cloud Access Security Broker Implementation Models SASE Network SecurityThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out of band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Introducing Cloud Access Security Broker Implementation Models SASE Network Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Scanning, Forward, Reverse, using this template. Grab it now to reap its full benefits.
-
 SASE Network Security Approaches To Implement Zero Trust Network Access
SASE Network Security Approaches To Implement Zero Trust Network AccessThis slide depicts the two primary approaches to implementing zero trust network access for organizations. The purpose of this slide is to showcase the endpoint initiated and service initiated approach of zero trust network access. It also includes how users access business services and applications in both approaches. Increase audience engagement and knowledge by dispensing information using SASE Network Security Approaches To Implement Zero Trust Network Access. This template helps you present information on two stages. You can also present information on Program, Environment, Service using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SASE Network Security Budget To Implement Secure Access Service Edge
SASE Network Security Budget To Implement Secure Access Service EdgeThis slide depicts the budget calculation for implementing a secure access service edge model in an organization. The purpose of this slide is to showcase the estimated and actual cost and variance for SASE model spending. The key components include SD WAN, SWG, ZTNA, CASB, and FWaaS. Deliver an outstanding presentation on the topic using this SASE Network Security Budget To Implement Secure Access Service Edge. Dispense information and present a thorough explanation of Network, Secure, Access using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SASE Network Security Challenges And Solutions For SASE Implementation
SASE Network Security Challenges And Solutions For SASE ImplementationThis slide represents the challenges and solutions for implementing a secure access service edge in an organization. The purpose of this slide is to showcase the different challenges that a business can face while deploying the SASE model into a business. The key challenges include networking and security team misalignment, change management, etc. Deliver an outstanding presentation on the topic using this SASE Network Security Challenges And Solutions For SASE Implementation. Dispense information and present a thorough explanation of Security, Management, Capabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SASE Network Security Checklist To Implement Secure Access Service Edge
SASE Network Security Checklist To Implement Secure Access Service EdgePresent the topic in a bit more detail with this SASE Network Security Checklist To Implement Secure Access Service Edge. Use it as a tool for discussion and navigation on Responsible, Service, Secure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SASE Network Security Roadmap To Implement Secure Access Service Edge
SASE Network Security Roadmap To Implement Secure Access Service EdgeThis slide depicts the roadmap to implementing secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and, discovering gaps, etc. Introducing SASE Network Security Roadmap To Implement Secure Access Service Edge to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Objectives, Providers, Deployment, using this template. Grab it now to reap its full benefits.
-
 SASE Network Security Secure Access Service Edge Implementation Steps
SASE Network Security Secure Access Service Edge Implementation StepsThis slide outlines the steps to implement a secure service edge in a business. The purpose of this slide is to demonstrate the various guidelines to consider while implementing the SASE model in an organization. The main steps include defining SASE goals and requirements, selecting the SD WAN backbone, incorporating zero trust solutions, etc. Introducing SASE Network Security Secure Access Service Edge Implementation Steps to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Requirements, Solutions, Service, using this template. Grab it now to reap its full benefits.
-
 SASE Network Security Timeline To Implement Cloud Access Security Broker
SASE Network Security Timeline To Implement Cloud Access Security BrokerThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Introducing SASE Network Security Timeline To Implement Cloud Access Security Broker to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Activity, Applications, Company, using this template. Grab it now to reap its full benefits.
-
 Timeline To Implement Secure Access Service Edge SASE Network Security
Timeline To Implement Secure Access Service Edge SASE Network SecurityThis slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Introducing Timeline To Implement Secure Access Service Edge SASE Network Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Objectives, Solutions, Regularly, using this template. Grab it now to reap its full benefits.
-
 Roadmap To Implement Information Security Management System In Organization
Roadmap To Implement Information Security Management System In OrganizationThis slide represents roadmap that helps organizations implement system for information security management systems to protect sensitive data. It includes steps such as defining scope and objectives, identifying assets, recognizing risk, etc. Introducing our premium set of slides with Roadmap To Implement Information Security Management System In Organization. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Recognize Risk, Make Improvement, Identify Mitigation Measures. So download instantly and tailor it with your information.
-
 Implementing Blockchain Cybersecurity Risks Mitigation Hands On Blockchain Security Risk BCT SS V
Implementing Blockchain Cybersecurity Risks Mitigation Hands On Blockchain Security Risk BCT SS VThe following slide illustrates some blockchain cybersecurity risk management techniques to manage accessibility and ensure data security. It includes elements such as reduce, avoid, accepts and transfer, etc. Present the topic in a bit more detail with this Implementing Blockchain Cybersecurity Risks Mitigation Hands On Blockchain Security Risk BCT SS V. Use it as a tool for discussion and navigation on Reduce, Accept, Avoid. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Virtual Infrastructure Security Integration Roadmap
Implementing Virtual Infrastructure Security Integration RoadmapThis slide showcases timeline that assist businesses to implement virtual infrastructure to enhance data security integration and management. It includes carious phases such as resource virtualization, application virtualization, internal cloud and hybrid cloud. Introducing our premium set of slides with Implementing Virtual Infrastructure Security Integration Roadmap. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Trusted Platform Incorporation, Zero Data Loss, Trusted Security. So download instantly and tailor it with your information.
-
 Implement Security Systems Icon Using Operating System
Implement Security Systems Icon Using Operating SystemIntroducing our premium set of slides with Implement Security Systems Icon Using Operating System. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Implement Security, Systems Icon, Using Operating System. So download instantly and tailor it with your information.
-
 Checklist To Implement Data Breach Security Response Plan
Checklist To Implement Data Breach Security Response PlanThis slide depicts the checklist to execute response plans during data security breaches. The purpose of this checklist is to help the business ensure all suitable actions are implemented in order to prevent data leaks. It includes elements such as activity status, person responsible, etc. Presenting our well structured Checklist To Implement Data Breach Security Response Plan. The topics discussed in this slide are Isolate Affected Systems, Notify Appropriate Stakeholders, Identify The Nature. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Overview Need For Implementing Data Security Across Retail Digital Transformation Of Retail DT SS
Overview Need For Implementing Data Security Across Retail Digital Transformation Of Retail DT SSThis slide analyses the need of implementing data security initiatives to address key customer data challenges in retail industry. It also mentions types of customer data collected such as account, location, browsing, and profile. Deliver an outstanding presentation on the topic using this Overview Need For Implementing Data Security Across Retail Digital Transformation Of Retail DT SS Dispense information and present a thorough explanation of Customer Trust, Sensitive Information, Balancing Personalization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Build Cyber Security Team Structure Implementing Cyber Risk Management Process
Build Cyber Security Team Structure Implementing Cyber Risk Management ProcessThe following slide showcases the organizational cyber security team hierarchy to prevent sensitive data loss and damage. It mainly includes elements such as security manager, engineer, analyst, chief information security officer etc. Deliver an outstanding presentation on the topic using this Build Cyber Security Team Structure Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Security Analyst, Security Manager, Chief Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Awareness Facts And Statistics Implementing Cyber Risk Management Process
Cyber Security Awareness Facts And Statistics Implementing Cyber Risk Management ProcessThe following slide showcases some facts and figures to generate awareness about cyber-crimes. It includes elements such as hike in ransomware attacks, more employees are expected to be target of malware attacks, increasing cost of data breaches etc. Introducing Cyber Security Awareness Facts And Statistics Implementing Cyber Risk Management Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Social Engineering, Data Breaches, Mobile Malware Attacks, using this template. Grab it now to reap its full benefits.
-
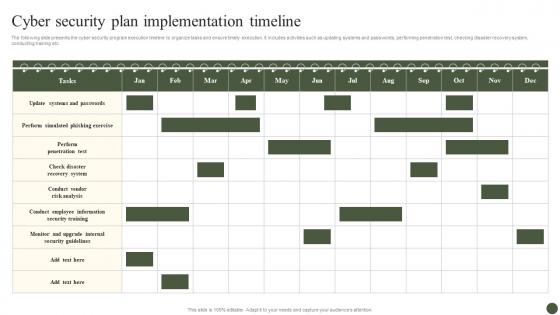 Cyber Security Plan Implementation Timeline Implementing Cyber Risk Management Process
Cyber Security Plan Implementation Timeline Implementing Cyber Risk Management ProcessThe following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Present the topic in a bit more detail with this Cyber Security Plan Implementation Timeline Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Cyber Security Plan, Implementation Timeline. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Highlighting Cyber Security Unawareness Among Implementing Cyber Risk Management Process
Data Highlighting Cyber Security Unawareness Among Implementing Cyber Risk Management ProcessThe following slide depicts some figures to analyse the awareness gap among staff regarding cyber safety. It includes statistics such as clicking suspicious links, transferring data over personal cloud, securing systems with weak passwords etc. Increase audience engagement and knowledge by dispensing information using Data Highlighting Cyber Security Unawareness Among Implementing Cyber Risk Management Process. This template helps you present information on five stages. You can also present information on Malware Infection, Systems With Passwords, Employees Feels, Allow Official Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine Cyber Security Risks And Threats Implementing Cyber Risk Management Process
Determine Cyber Security Risks And Threats Implementing Cyber Risk Management ProcessThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Present the topic in a bit more detail with this Determine Cyber Security Risks And Threats Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Details, Objectives, Issue Identifier. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Global Cyber Security Trend Analysis Implementing Cyber Risk Management Process
Global Cyber Security Trend Analysis Implementing Cyber Risk Management ProcessThe following slide depicts the key statistics about cyber security trends to project future performance. It mainly includes elements such as increase in ransomware attacks, average data breach costs, approximate number of businesses prone to cyber-attacks etc. Introducing Global Cyber Security Trend Analysis Implementing Cyber Risk Management Process to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Businesses Targeted, Ransomware Attack, Cyber Attacks, using this template. Grab it now to reap its full benefits.
-
 Impact Of Cyber Safety Security Measures Implementing Cyber Risk Management Process
Impact Of Cyber Safety Security Measures Implementing Cyber Risk Management ProcessThe following slide depicts the projected consequences of implementing cyber security preventive measures. It includes data about number of cyber attracts pre and post adopting latest strategies. Present the topic in a bit more detail with this Impact Of Cyber Safety Security Measures Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Cyber Attack Type, Remarks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Of Cyber Security Policies And Practices Implementing Cyber Risk Management Process
Impact Of Cyber Security Policies And Practices Implementing Cyber Risk Management ProcessThe following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions. Deliver an outstanding presentation on the topic using this Impact Of Cyber Security Policies And Practices Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Inadequate Security Guidelines, Inappropriate Privacy Policies, Insufficient Background Check using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 KPIs To Evaluate Cyber Security Risk Management Implementing Cyber Risk Management Process
KPIs To Evaluate Cyber Security Risk Management Implementing Cyber Risk Management ProcessThe following slide highlights some key performance indicators to measure the impact of cyber security risk administration to assess its effectiveness and take improved decisions. It includes elements such as level of preparedness, mean time to detect, success rating etc. Present the topic in a bit more detail with this KPIs To Evaluate Cyber Security Risk Management Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Details, Before, After. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Organize Cyber Security Training For Employees Regularly Implementing Cyber Risk Management Process
Organize Cyber Security Training For Employees Regularly Implementing Cyber Risk Management ProcessThe following slide depicts the staff cyber security training plan to educate them regarding technology threats and practices. It mainly includes elements such as topics to be covered, target audience, trainer name, mode, proposed date, timings etc. Present the topic in a bit more detail with this Organize Cyber Security Training For Employees Regularly Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Target Audience, Trainer Name, Mode. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Prioritize Cyber Security Risk With Severity Matrix Implementing Cyber Risk Management Process
Prioritize Cyber Security Risk With Severity Matrix Implementing Cyber Risk Management ProcessThe following slide depicts cyber security risk assessment grid to prioritize and eliminate occurrence of threats. It includes elements such as moderate, severe, minor, negligible, rate, possible, likely, unlikely etc. Present the topic in a bit more detail with this Prioritize Cyber Security Risk With Severity Matrix Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Rare, Unlikely, Possible. This template is free to edit as deemed fit for your organization. Therefore download it now.





