Powerpoint Templates and Google slides for Implementing Cybersecurity
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Implementing Intrusion Prevention System For Effective Network Security Cybersecurity CD
Implementing Intrusion Prevention System For Effective Network Security Cybersecurity CDWhile your presentation may contain top-notch content, if it lacks visual appeal, you are not fully engaging your audience. Introducing our Implementing Intrusion Prevention System For Effective Network Security Cybersecurity CD deck, designed to engage your audience. Our complete deck boasts a seamless blend of Creativity and versatility. You can effortlessly customize elements and color schemes to align with your brand identity. Save precious time with our pre-designed template, compatible with Microsoft versions and Google Slides. Plus, it is downloadable in multiple formats like JPG, JPEG, and PNG. Elevate your presentations and outshine your competitors effortlessly with our visually stunning 100 percent editable deck.
-
 Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity CD
Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity CDStep up your game with our enchanting Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity CD deck, guaranteed to leave a lasting impression on your audience. Crafted with a perfect balance of simplicity, and innovation, our deck empowers you to alter it to your specific needs. You can also change the color theme of the slide to mold it to your companys specific needs. Save time with our ready-made design, compatible with Microsoft versions and Google Slides. Additionally, it is available for download in various formats including JPG, JPEG, and PNG. Outshine your competitors with our fully editable and customized deck.
-
 Implementing cybersecurity management framework powerpoint presentation slides
Implementing cybersecurity management framework powerpoint presentation slidesSlideTeam brings Implementing Cybersecurity Management Framework Powerpoint Presentation Slides. There are 55 visually-gripping PowerPoint templates in this 100% editable deck. Customize font, text, patterns, shapes, colors, orientation, and background as required. Convert the PPT file format into PDF, PNG, and JPG according to your convenience. Use Google slides to view this presentation. It also works well with standard and widescreen resolutions.
-
 Network Vulnerabilities Logged Off In Previous Years Implementing Strategies For Mitigating Cybersecurity SS
Network Vulnerabilities Logged Off In Previous Years Implementing Strategies For Mitigating Cybersecurity SSThis slide represents network vulnerabilities faced by the organization, which led to the theft of confidential and sensitive information due to opening of infected email attachments etc.Deliver an outstanding presentation on the topic using this Network Vulnerabilities Logged Off In Previous Years Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Phishing Attacks, Malware Attacks, Reasons, Key Insights using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implementing Robust Cybersecurity Elevating Small And Medium Enterprises Digital Transformation DT SS
Implementing Robust Cybersecurity Elevating Small And Medium Enterprises Digital Transformation DT SSThis slide presents various cybersecurity measures to safeguard organization in the digital era. It includes measures such as continuous vulnerability management, secure configurations, data protection, data recovery, proactive monitoring and detection, and boundary defence. Present the topic in a bit more detail with this Implementing Robust Cybersecurity Elevating Small And Medium Enterprises Digital Transformation DT SS. Use it as a tool for discussion and navigation on Organization Networks, Data Protection, Controlled Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Budget Share For Implementing Mobile Security Solutions Mobile Device Security Cybersecurity SS
Budget Share For Implementing Mobile Security Solutions Mobile Device Security Cybersecurity SSBudget Share For Implementing Mobile Security Solutions Mobile Device Security Cybersecurity SS This slide showcases expenses share to implement mobile device threat management solutions. Its key elements are biometric solutions, VPN, software upgradation, mobile device management Present the topic in a bit more detail with this Biometric Solutions, Security Awareness Use it as a tool for discussion and navigation on Biometric Solutions, Security Awareness This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attacks Reduction After Implementing Mobile Security Techniques Mobile Device Security Cybersecurity SS
Cyber Attacks Reduction After Implementing Mobile Security Techniques Mobile Device Security Cybersecurity SSThis slide showcases decrease in cyber attacks after implementation of mobile security. Its key elements are malware, phishing attacks and ransomware Deliver an outstanding presentation on the topic using this Cyber Attacks Reduction After Implementing Mobile Security Techniques Mobile Device Security Cybersecurity SS Dispense information and present a thorough explanation of Advanced Persistent Threats, Diverse Cyber Threat Landscape using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implementing Intrusion Prevention Gap Analysis For Intrusion Prevention System Cybersecurity SS
Implementing Intrusion Prevention Gap Analysis For Intrusion Prevention System Cybersecurity SSThis slide represents the gap analysis to help organizations understand the gaps so that they can build effective strategies to eliminate these gaps and achieve desired results. Present the topic in a bit more detail with this Implementing Intrusion Prevention Gap Analysis For Intrusion Prevention System Cybersecurity SS. Use it as a tool for discussion and navigation on Proactive Security Measures, Average Incident Response, Network Traffic Monitored. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
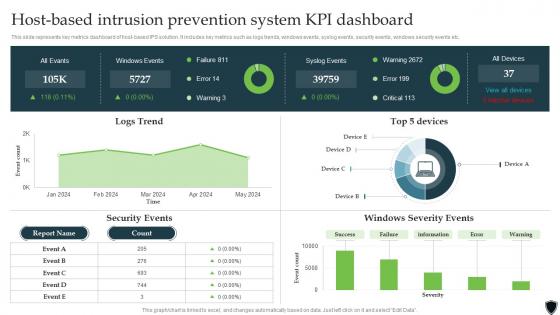 Implementing Intrusion Prevention Host Based Intrusion Prevention System KPI Cybersecurity SS
Implementing Intrusion Prevention Host Based Intrusion Prevention System KPI Cybersecurity SSThis slide represents key metrics dashboard of host-based IPS solution. It includes key metrics such as logs trends, windows events, syslog events, security events, windows security events etc. Present the topic in a bit more detail with this Implementing Intrusion Prevention Host Based Intrusion Prevention System Kpi Cybersecurity SS. Use it as a tool for discussion and navigation on Success, Failure, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
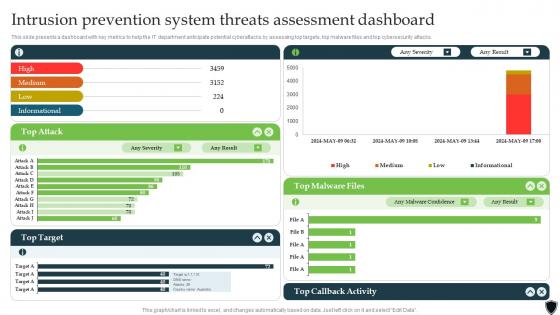 Implementing Intrusion Prevention Intrusion Prevention System Threats Assessment Cybersecurity SS
Implementing Intrusion Prevention Intrusion Prevention System Threats Assessment Cybersecurity SSThis slide presents a dashboard with key metrics to help the IT department anticipate potential cyberattacks by assessing top targets, top malware files and top cybersecurity attacks. Present the topic in a bit more detail with this Implementing Intrusion Prevention Intrusion Prevention System Threats Assessment Cybersecurity SS. Use it as a tool for discussion and navigation on Callback Activity, Malware Files, Target. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Intrusion Prevention Overview Steps For Implementing Intrusion Cybersecurity SS
Implementing Intrusion Prevention Overview Steps For Implementing Intrusion Cybersecurity SSThis slide represents the process for effectively deploying a network security tool that monitors the network for malicious activities. It includes steps such as defining network segmentation etc. Introducing Implementing Intrusion Prevention Overview Steps For Implementing Intrusion Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Define Network Segmentation, Select Right Hardware And Software, Installation And Configuration, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Potential Impact Of Intrusion Prevention Cybersecurity SS
Implementing Intrusion Prevention Potential Impact Of Intrusion Prevention Cybersecurity SSThis slide highlights the impact of deploying effective Intrusion prevention system solution on organizational operations, such as increased real-time threat visibility, proactive threat detection etc. Present the topic in a bit more detail with this Implementing Intrusion Prevention Potential Impact Of Intrusion Prevention Cybersecurity SS. Use it as a tool for discussion and navigation on Increase In Real-Time Threat Visibility, Increase In Proactive Threat Detection Rates, Decrease In Average Cost Per Breach. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Intrusion Prevention Potential Roi After Implementing Intrusion Cybersecurity SS
Implementing Intrusion Prevention Potential Roi After Implementing Intrusion Cybersecurity SSThis slide demonstrates the positive impact of implementing Intrusion prevention system solution on returns on investments. The graph depicts an increase in ROI and savings over time. Present the topic in a bit more detail with this Implementing Intrusion Prevention Potential Roi After Implementing Intrusion Cybersecurity SS. Use it as a tool for discussion and navigation on Potential ROI After Implementing, Intrusion Prevention System. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Network Vulnerabilities Assessment KPI Dashboard Implementing Strategies For Mitigating Cybersecurity SS
Network Vulnerabilities Assessment KPI Dashboard Implementing Strategies For Mitigating Cybersecurity SSThis dashboard tracks and assesses the network vulnerabilities faced by the organization. It includes KPIs such as critical vulnerabilities, new vulnerabilities, and unresolved vulnerabilities etc.Present the topic in a bit more detail with this Network Vulnerabilities Assessment KPI Dashboard Implementing Strategies For Mitigating Cybersecurity SS. Use it as a tool for discussion and navigation on New Vulnerabilities, Unresolved Vulnerabilities, Activity, Insecure Libraries. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Potential Roi After Implementing Tools And Technologies To Reduce Network Vulnerabilities Cybersecurity SS
Potential Roi After Implementing Tools And Technologies To Reduce Network Vulnerabilities Cybersecurity SSThis slide demonstrates the positive impact of implementing network vulnerability management solutions on returns on investments. The graph depicts an increase in ROI and savings over time..Deliver an outstanding presentation on the topic using this Potential Roi After Implementing Tools And Technologies To Reduce Network Vulnerabilities Cybersecurity SS. Dispense information and present a thorough explanation of Key Insights, Improved Compliance, Password Hacking using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ways To Implement Cybersecurity Awareness And Training Communication Plan
Ways To Implement Cybersecurity Awareness And Training Communication PlanThe slide consists of ways to implement cyber security awareness programs and training communication plans in organization. It consist of points such as create engaging content, multichannel distribution, gamification, etc. Presenting our well structured Ways To Implement Cybersecurity Awareness And Training Communication Plan. The topics discussed in this slide are Impact, Engaging, Distribution. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Unlocking The Impact Of Technology Best Practices For Implementing Cybersecurity Techniques
Unlocking The Impact Of Technology Best Practices For Implementing Cybersecurity TechniquesThis slide showcases best practices required for securing data. This template focuses on maintaining continuity of operations and minimizing potential for costly interruptions. It covers aspects related to threat detection, firewall, antivirus software, etc. Increase audience engagement and knowledge by dispensing information using Unlocking The Impact Of Technology Best Practices For Implementing Cybersecurity Techniques. This template helps you present information on four stages. You can also present information on Threat Detection And Prevention, Antivirus Software, Two Factor Authentication, Cybersecurity Techniques using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Change Management Agents Driving Case Study On Implementing Cybersecurity System CM SS
Change Management Agents Driving Case Study On Implementing Cybersecurity System CM SSThis slide defines the case study of an IT Information technology professional implementing a new company-wide cybersecurity system. It consists of details related to a case study that reflects the importance of change agents in an organization. Introducing Change Management Agents Driving Case Study On Implementing Cybersecurity System CM SS to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Preventing Cyberattacks, Risk Of Cyberattacks, Cybersecurity System, Adequately Trained, using this template. Grab it now to reap its full benefits.
-
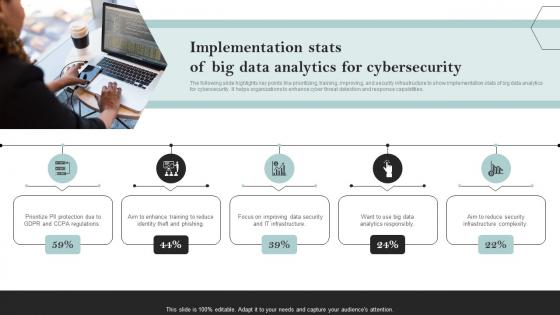 Implementation Stats Of Big Data Analytics For Cybersecurity
Implementation Stats Of Big Data Analytics For CybersecurityThe following slide highlights key points like prioritizing, training, improving, and security infrastructure to show implementation stats of big data analytics for cybersecurity. It helps organizations to enhance cyber threat detection and response capabilities. Introducing our premium set of slides with Implementation Stats Of Big Data Analytics For Cybersecurity. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Regulations, Reduce, Improving. So download instantly and tailor it with your information.
-
 Need To Implement IoT Cyber Security Improving IoT Device Cybersecurity IoT SS
Need To Implement IoT Cyber Security Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to exhibit need to implement Internet of Things IoT security in order to avoid cyber attack and minimize losses. The slide covers information about data protection of users, adhering to regulatory standards, limited security of IoT devices, etc. Introducing Need To Implement IoT Cyber Security Improving IoT Device Cybersecurity IoT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Required, Companies, Potential, using this template. Grab it now to reap its full benefits.
-
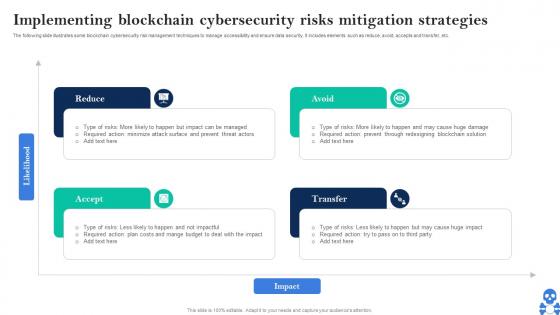
 Implementing Blockchain Cybersecurity Risks Mitigation Hands On Blockchain Security Risk BCT SS V
Implementing Blockchain Cybersecurity Risks Mitigation Hands On Blockchain Security Risk BCT SS VThe following slide illustrates some blockchain cybersecurity risk management techniques to manage accessibility and ensure data security. It includes elements such as reduce, avoid, accepts and transfer, etc. Present the topic in a bit more detail with this Implementing Blockchain Cybersecurity Risks Mitigation Hands On Blockchain Security Risk BCT SS V. Use it as a tool for discussion and navigation on Reduce, Accept, Avoid. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Blockchain And Cybersecurity Implementing Blockchain Cybersecurity Risks Mitigation Strategies BCT SS V
Blockchain And Cybersecurity Implementing Blockchain Cybersecurity Risks Mitigation Strategies BCT SS VThe following slide illustrates some blockchain cybersecurity risk management techniques to manage accessibility and ensure data security. It includes elements such as reduce, avoid, accepts and transfer, etc. Increase audience engagement and knowledge by dispensing information using Blockchain And Cybersecurity Implementing Blockchain Cybersecurity Risks Mitigation Strategies BCT SS V This template helps you present information on Two stages. You can also present information on Reduce, Avoid, Transfer, Accept using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Threats In Blockchain Implementing Blockchain Cybersecurity Risks Mitigation Strategies BCT SS V
Cyber Threats In Blockchain Implementing Blockchain Cybersecurity Risks Mitigation Strategies BCT SS VThe following slide illustrates some blockchain cybersecurity risk management techniques to manage accessibility and ensure data security. It includes elements such as reduce, avoid, accepts and transfer, etc. Introducing Cyber Threats In Blockchain Implementing Blockchain Cybersecurity Risks Mitigation Strategies BCT SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Reduce, Avoid, Transfer, Accept using this template. Grab it now to reap its full benefits.
-
 Select Cybersecurity Training Program Courses Implementing Cyber Risk Management Process
Select Cybersecurity Training Program Courses Implementing Cyber Risk Management ProcessThe following slide showcases the best cybersecurity training courses to educate employees and minimize the possibility of cyber-attacks. It includes cloud, disaster recovery, hardware, information security programs, duration, mode and cost. Present the topic in a bit more detail with this Select Cybersecurity Training Program Courses Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Course Name, Duration, Mode, Start Date. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Operational Map To Implement SAP Cybersecurity
Operational Map To Implement SAP CybersecurityThis slide showcases the operational structure to execute SAP cybersecurity. The purpose of this template is to ensure proper establishment of SAP security procedures through elements such as enterprise, procedures, applications, systems and environment. Presenting our well structured Operational Map To Implement SAP Cybersecurity. The topics discussed in this slide are Security Governance Policies, Data Privacy And Protection, Client Security. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Benefits Of Implementing Cybersecurity Measures To Safeguard It Infrastructure
Benefits Of Implementing Cybersecurity Measures To Safeguard It InfrastructureThis slide highlights the cybersecurity measures implemented to safeguard the It infrastructure. The purpose of this slide is to help the business capitalize on the benefits such as protection against cyber attacks, protection of data networks, etc. Presenting our set of slides with Benefits Of Implementing Cybersecurity Measures To Safeguard It Infrastructure This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Protection Against, Data Networks, Unauthorized Access
-
 Implementing Blockchain Cybersecurity Risks Mitigation Strategies Guide For Blockchain BCT SS V
Implementing Blockchain Cybersecurity Risks Mitigation Strategies Guide For Blockchain BCT SS VThe following slide illustrates some blockchain cybersecurity risk management techniques to manage accessibility and ensure data security. It includes elements such as reduce, avoid, accepts and transfer, etc. Increase audience engagement and knowledge by dispensing information using Implementing Blockchain Cybersecurity Risks Mitigation Strategies Guide For Blockchain BCT SS V This template helps you present information on four stages. You can also present information on Reduce, Avoid, Transfer, Accept using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Implementing Blockchain Cybersecurity Securing Blockchain Transactions A Beginners Guide BCT SS V
Implementing Blockchain Cybersecurity Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide showcases blockchain cybersecurity threat assessment to determine type and major causes of attacks. It includes elements such as double spending, mining threats, wallet, network, smart contract threats, etc. Introducing Implementing Blockchain Cybersecurity Securing Blockchain Transactions A Beginners Guide BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Reduce, Accept, Transfer, using this template. Grab it now to reap its full benefits.
-
 Checklist To Implement Opsec Cybersecurity In Organization
Checklist To Implement Opsec Cybersecurity In OrganizationThis slide showcases the checklist to implement opsec cybersecurity in organizations. The purpose of this slide is to help ensure opsec measures are correctly implemented through the use of this checklist. It includes elements such as checklist item, description, etc. Introducing our Checklist To Implement Opsec Cybersecurity In Organization set of slides. The topics discussed in these slides are Information Classification, Access Controls, Communication Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Five Levels Of Opsec Cybersecurity Implementation
Five Levels Of Opsec Cybersecurity ImplementationThis slide showcases the five levels of opsec cybersecurity implementation. The purpose of this slide is to help the business implement all five levels to maintain cybersecurity. It includes levels such as identification of sensitive information, assessment of vulnerabilities, etc. Introducing our premium set of slides with Five Levels Of Opsec Cybersecurity Implementation. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Identify Sensitive Information, Recognize Potential Threats, Asses Vulnerabilities . So download instantly and tailor it with your information.
-
 Icon For Opsec Cybersecurity Implementation Steps
Icon For Opsec Cybersecurity Implementation StepsIntroducing our premium set of slides with Icon For Opsec Cybersecurity Implementation Steps. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon, Cybersecurity, Implementation. So download instantly and tailor it with your information.
-
 Implement Opsec Cybersecurity Measures To Maximize Operational Security
Implement Opsec Cybersecurity Measures To Maximize Operational SecurityThis slide showcases the tactics to execute opsec cybersecurity measures. The purpose of this slide is to help the business ensure opsec security is suitably implemented through the use of strategies such as identification and access management, business continuity and disaster recovery, etc Introducing our premium set of slides with Implement Opsec Cybersecurity Measures To Maximize Operational Security. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Access Management, Disaster Recovery, AI Driven Automation . So download instantly and tailor it with your information.
-
 Key Practices For Implementation Of Opsec Cybersecurity
Key Practices For Implementation Of Opsec CybersecurityThis slide depicts the key practices for opsec cybersecurity implementation. This slide aims to help the business leverage opsec through practices such as implementation of relevant processes, selection of suitable providers, restriction of access to networks, etc. Introducing our premium set of slides with Key Practices For Implementation Of Opsec Cybersecurity. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Practices, Description, Networks And Devices. So download instantly and tailor it with your information.
-
 Select Cybersecurity Training Program Courses Implementing Strategies To Mitigate Cyber Security Threats
Select Cybersecurity Training Program Courses Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the best cybersecurity training courses to educate employees and minimize the possibility of cyber attacks. It includes cloud, disaster recovery, hardware, information security programs, duration, mode and cost Deliver an outstanding presentation on the topic using this Select Cybersecurity Training Program Courses Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Cloud Security, Information Security, Disaster Recovery using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
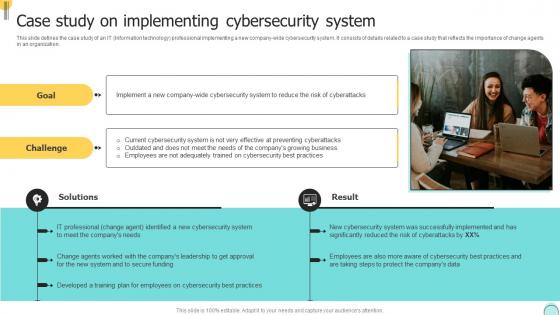 Q101 Changemakers Catalysts Organizational Case Study On Implementing Cybersecurity System CM SS V
Q101 Changemakers Catalysts Organizational Case Study On Implementing Cybersecurity System CM SS VThis slide defines the case study of an IT Information technology professional implementing a new company-wide cybersecurity system. It consists of details related to a case study that reflects the importance of change agents in an organization. Introducing Q101 Changemakers Catalysts Organizational Case Study On Implementing Cybersecurity System CM SS V to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Goal, Challenge, Solutions, using this template. Grab it now to reap its full benefits.
-
 Budget Plan For Implementing Maritime Cybersecurity
Budget Plan For Implementing Maritime CybersecurityThis slide showcases budget plan for maritime cybersecurity. The main purpose of this is to increase efficiency and upgrade the firewall. This includes Category such as cybersecurity assessment, training, and awareness, network security, etc. Introducing our Budget Plan For Implementing Maritime Cybersecurity set of slides. The topics discussed in these slides are Cybersecurity Assessment, Security Software Licenses, Incident Response Planning. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Steps For Cybersecurity Implementation To Ensure Data Safety
Steps For Cybersecurity Implementation To Ensure Data SafetyThe highlighted slide outlines essential steps for cybersecurity implementation, including risk analysis, defining security objectives, technology assessment, policy review, strategy formulation, translating plans into practice, and ongoing review. These steps collectively contribute to ensuring data safety by establishing a robust and proactive cybersecurity framework. Presenting our set of slides with Steps For Cybersecurity Implementation To Ensure Data Safety. This exhibits information on seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Risk Analysis, Management Strategy, Set Security Objectives.
-
 Implementing Cybersecurity In BCP For Enhancing Risk Protection
Implementing Cybersecurity In BCP For Enhancing Risk ProtectionThis slide represents process to implement cybersecurity in business continuity planning BCP for improving company data protection from cyber risks. It includes steps such as conducting business impact analysis, developing risk assessment, maintaining total vison, etc. Presenting our set of slides with Implementing Cybersecurity In BCP For Enhancing Risk Protection This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Maintain Total Vision, Risk Management, Implement Controls
-
 Maturity Model For Monitoring SCADA Cybersecurity Implementation
Maturity Model For Monitoring SCADA Cybersecurity ImplementationThis slide represents maturity model that assist IT companies to track implementation of SCADA cybersecurity for optimizing data protection. It includes various phases such as defining standards, increasing awareness, deploying solutions, etc. Introducing our premium set of slides with Maturity Model For Monitoring SCADA Cybersecurity Implementation Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Objectives, Operate And Maintain, Actions Required, Cybersecurity Implementation. So download instantly and tailor it with your information.
-
 Implementation Steps For Cybersecurity Mesh
Implementation Steps For Cybersecurity MeshThe following slide showcases critical aspects such as threat intelligence, attack detection, role-based access, authentication security, and file actions in the implementation steps of cybersecurity mesh. This assists in understanding the essential elements for effective cybersecurity mesh deployment. Introducing our premium set of slides with Implementation Steps For Cybersecurity Mesh Ellicudate the Five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Threat Intelligence, Minimized Risk, Security With Authentication. So download instantly and tailor it with your information.
-
 Benefits Of Implementing Cybersecurity In Education Organization
Benefits Of Implementing Cybersecurity In Education OrganizationThis slide showcases the advantages of utilizing cybersecurity in education institutes to enhance their safety. The purpose of this slide is to help the business leverage cybersecurity to improve its overall security. It includes advantages such as protection of user information, remote workspace management, etc. Introducing our Benefits Of Implementing Cybersecurity In Education Organization set of slides. The topics discussed in these slides are Protect User Information, Remote Workspace Management, Streamline Access Control. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Best Practices To Implement Strong Cybersecurity In Education
Best Practices To Implement Strong Cybersecurity In EducationThis slide highlights the best practices for implementing strong cybersecurity in education. The purpose of this slide is to help ensure that educational institutes safeguard their internal networks through the use of practices such as employee training, attack surface management, etc. Introducing our premium set of slides with Best Practices To Implement Strong Cybersecurity In Education. Ellicudate the Five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Employee Training, Identity And Access Management, Attack Surface Management. So download instantly and tailor it with your
-
 Steps To Implement Cybersecurity In Education
Steps To Implement Cybersecurity In EducationThis slide depicts the steps to implement cybersecurity in education. The purpose of this slide is to help the business ensure it correctly implements cybersecurity techniques to prevent cyberattacks. It includes steps such as conducting risk analysis, determining security objectives, etc. Presenting our set of slides with Steps To Implement Cybersecurity In Education. This exhibits information on Seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Execute Security Plan, Review Security Policy, Review Security Plan
-
 Strategies To Implement Cybersecurity In Education
Strategies To Implement Cybersecurity In EducationThis slide showcases the strategies to implement cybersecurity in education. The purpose of this slide is to help the business manage and ensure cybersecurity is correctly established in an educational institute. It includes strategies such as conducting audits, immediate response to cyber attacks, etc. Introducing our premium set of slides with Strategies To Implement Cybersecurity In Education. Ellicudate the Five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Rules And Regulations, Technical Control Methods, Cyber Attacks. So download instantly and tailor it with your information.
-
 IoT Device Identity Platform Implementation Internet Of Things IoT Security Cybersecurity SS
IoT Device Identity Platform Implementation Internet Of Things IoT Security Cybersecurity SSThis slide showcases internet of things IoT device identity platform deployment, referable for businesses in developing mitigation process. It provides details about APIs, architecture, device client, etc. Deliver an outstanding presentation on the topic using this IoT Device Identity Platform Implementation Internet Of Things IoT Security Cybersecurity SS. Dispense information and present a thorough explanation of IoT Device, Platform Deployment, Developing Mitigation Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Timeline For Implementing IoT Security Strategy Internet Of Things IoT Security Cybersecurity SS
Timeline For Implementing IoT Security Strategy Internet Of Things IoT Security Cybersecurity SSThis slide showcases internet of things IoT security strategy timeline, referable for developers and businesses in protection of connected devices. It provides details about credentials, authentication, cryptography, etc. Introducing Timeline For Implementing IoT Security Strategy Internet Of Things IoT Security Cybersecurity SS to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Avoid Unnecessary Data Handling, Cryptographic Network Protocol Usage, Enforce Authentication Controls, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Caesar Algorithm Implementation For Basic Encryption Cybersecurity SS
Encryption For Data Caesar Algorithm Implementation For Basic Encryption Cybersecurity SSThis slide showcases caesar algorithm deployment which can help employees learn basic techniques for basic encryption. It provides details about shift, displacement, shift value, decryption, etc. Introducing Encryption For Data Caesar Algorithm Implementation For Basic Encryption Cybersecurity SS to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Pre-Implementation Stage, Implementation Steps, Potential Benefit, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Encryption Awareness Training Implementation Plan Cybersecurity SS
Encryption For Data Encryption Awareness Training Implementation Plan Cybersecurity SSThis slide showcases training plan focused on building key encryption skills amongst organizations employees. It provides details about retention of training, backdoor access, internet society, etc. Introducing Encryption For Data Encryption Awareness Training Implementation Plan Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Existing Training Scenario, Details, Modules, Training Initiatives, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Implementing Encryption Gap Analysis For Organization Cybersecurity SS
Encryption For Data Implementing Encryption Gap Analysis For Organization Cybersecurity SSThis slide showcases gap analysis relating to encryption running in the organization. Its purpose is to make businesses aware of major and potential vulnerabilities. It provides information about sensitive data, employee awareness, key management, etc. Introducing Encryption For Data Implementing Encryption Gap Analysis For Organization Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Current State, Desired State, Action Items, Priority, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Timeline For Implementing Encryption Best Practices Cybersecurity SS
Encryption For Data Timeline For Implementing Encryption Best Practices Cybersecurity SSThis slide showcases timeline of encryption to be implemented in the organization. Its purpose is to make businesses ready for future plans of cyber security. It provides information about foundation, rollout, secure communication, etc. Introducing Encryption For Data Timeline For Implementing Encryption Best Practices Cybersecurity SS to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Foundation And Training, Asymmetric Encryption Rollout, Additional Security Measures, using this template. Grab it now to reap its full benefits.
-
 Business Rationales For Implementing OT Cybersecurity Measures
Business Rationales For Implementing OT Cybersecurity MeasuresThis slide represents various business rationales that motivate companies to adopt and implement OT cyber security measures for effective data protection. It includes rationales such as improved production uptime, enhanced data protection, etc. Introducing our premium set of slides with Business Rationales For Implementing OT Cybersecurity Measures Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Improved Production Uptime, Improved Reputation, Enhanced Data Protection So download instantly and tailor it with your information.
-
 Case Study For Implementing Optimized OT Cybersecurity Strategy
Case Study For Implementing Optimized OT Cybersecurity StrategyThis slide represents case study for implementing effective OT cybersecurity approach to mitigate cyber threats and enhance infrastructure protection. It includes various elements such as overview, challenges, solutions, and benefits. Presenting our set of slides with Case Study For Implementing Optimized OT Cybersecurity Strategy This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Overview, Challenges, Solution, Benefits
-
 Addressing Challenges For Implementing Pam To Optimize Cybersecurity
Addressing Challenges For Implementing Pam To Optimize CybersecurityThis slide represents various strategies that assist companies in mitigating challenges in implementing and monitoring PAM for enhancing cybersecurity. It includes challenges such as managing account credentials, tracking privileged activity, etc. Introducing our Addressing Challenges For Implementing Pam To Optimize Cybersecurity set of slides. The topics discussed in these slides are Managing Account Credentials, Tracking Privileged Activity, Controlling Privileged User Access. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Gantt Chart To Implement Pam Strategy For Cybersecurity
Gantt Chart To Implement Pam Strategy For CybersecurityThis slide represents gantt chart that assist companies to implement PAM strategy for enhancing their data cybersecurity effectively. It includes various steps such as accountability, understanding vulnerabilities, securing cloud, etc. Presenting our well structured Gantt Chart To Implement Pam Strategy For Cybersecurity. The topics discussed in this slide are Accountability For Privileged Passwords, Implement Least Privileged Access, Understand Vulnerabilities. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Pam Implementation Icon To Optimize Data Cybersecurity
Pam Implementation Icon To Optimize Data CybersecurityIntroducing our premium set of slides with Pam Implementation Icon To Optimize Data Cybersecurity. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like PAM Implementation, Optimize, Data Cybersecurity. So download instantly and tailor it with your information.
-
 IT Security Awareness Training Program Implementing Table Of Contents Cybersecurity SS
IT Security Awareness Training Program Implementing Table Of Contents Cybersecurity SSIncrease audience engagement and knowledge by dispensing information using IT Security Awareness Training Program Implementing Table Of Contents Cybersecurity SS. This template helps you present information on one stages. You can also present information on Phishing Awareness, Objectives, Detecting Phishing Attacks, Preventing Phishing Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Objectives Of Implementing Anti Phishing Training IT Security Awareness Training Cybersecurity SS
Objectives Of Implementing Anti Phishing Training IT Security Awareness Training Cybersecurity SSThis slide represents details related to need of implementing training program for employees regarding attacks that are attempted to steal sensitive information in the form of user names, credit card numbers etc. Introducing Objectives Of Implementing Anti Phishing Training IT Security Awareness Training Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Anti Phishing Training Program, Steal Sensitive Information, Employees Regarding Attacks, using this template. Grab it now to reap its full benefits.
-
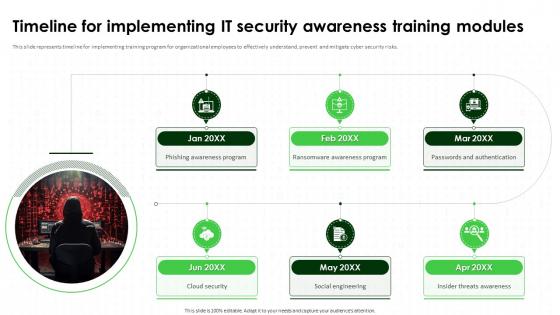 Timeline For Implementing IT Security Awareness Training Modules Cybersecurity SS
Timeline For Implementing IT Security Awareness Training Modules Cybersecurity SSThis slide represents timeline for implementing training program for organizational employees to effectively understand, prevent and mitigate cyber security risks. Increase audience engagement and knowledge by dispensing information using Timeline For Implementing IT Security Awareness Training Modules Cybersecurity SS. This template helps you present information on six stages. You can also present information on Ransomware Awareness Program, Passwords And Authentication, Social Engineering, Insider Threats Awareness using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Least Privilege Implementation For Accidental Building Next Generation Endpoint Security Cybersecurity SS
Least Privilege Implementation For Accidental Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases implementation of least privilege principle for avoiding accidental misuses. It provides details about security controls, data discovery, etc.Deliver an outstanding presentation on the topic using this Least Privilege Implementation For Accidental Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Action Steps, Real Problem Solved, Layering Security Controls using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Least Privilege Implementation For Segregation Building Next Generation Endpoint Security Cybersecurity SS
Least Privilege Implementation For Segregation Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases implementation of least privilege principle for segregation of duties. It provides details about time limits, certain access, etc.Introducing Least Privilege Implementation For Segregation Building Next Generation Endpoint Security Cybersecurity SS to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Action Steps, Real Problem Solved, Financial Data, using this template. Grab it now to reap its full benefits.




