Powerpoint Templates and Google slides for Implement Security System
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Implementing Intrusion Prevention System For Effective Network Security Cybersecurity CD
Implementing Intrusion Prevention System For Effective Network Security Cybersecurity CDWhile your presentation may contain top-notch content, if it lacks visual appeal, you are not fully engaging your audience. Introducing our Implementing Intrusion Prevention System For Effective Network Security Cybersecurity CD deck, designed to engage your audience. Our complete deck boasts a seamless blend of Creativity and versatility. You can effortlessly customize elements and color schemes to align with your brand identity. Save precious time with our pre-designed template, compatible with Microsoft versions and Google Slides. Plus, it is downloadable in multiple formats like JPG, JPEG, and PNG. Elevate your presentations and outshine your competitors effortlessly with our visually stunning 100 percent editable deck.
-
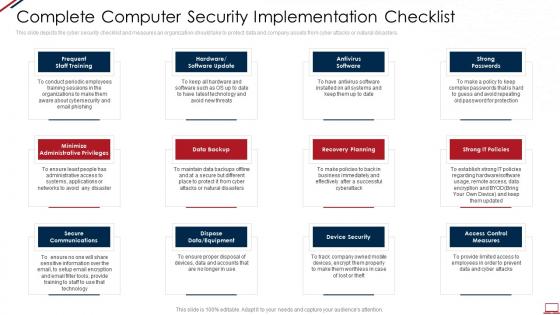 Computer system security complete computer security implementation checklist
Computer system security complete computer security implementation checklistThis slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Increase audience engagement and knowledge by dispensing information using Computer System Security Complete Computer Security Implementation Checklist. This template helps you present information on twelve stages. You can also present information on Data Backup, Secure Communications, Recovery Planning, Strong Passwords, Device Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Computer system security impact on organization after implementing computer security strategy and training
Computer system security impact on organization after implementing computer security strategy and trainingThis slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Increase audience engagement and knowledge by dispensing information using Computer System Security Impact On Organization After Implementing Computer Security Strategy And Training. This template helps you present information on five stages. You can also present information on Phishing, Network Intrusion, Inadvertent Disclosure, Stolen Or Lost Devises Or Records, System Misconfiguration using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Computer system security implementation of strong password policy
Computer system security implementation of strong password policyThis slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Introducing Computer System Security Implementation Of Strong Password Policy to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Implementation Of Strong Password Policy, using this template. Grab it now to reap its full benefits.
-
 Computer system security timeline for the implementation of computer security
Computer system security timeline for the implementation of computer securityThis slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Present the topic in a bit more detail with this Computer System Security Timeline For The Implementation Of Computer Security. Use it as a tool for discussion and navigation on Security, Risk Assessments, Perform. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Security System In Organization
Implementing Security System In OrganizationThis slide highlights implementing security system in organization process. This further includes business model, threat assessment, security policies, incident response, security controls and maintain security. Presenting our set of slides with Implementing Security System In Organization. This exhibits information on eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Maintain Security, Managed Security, Security Controls.
-
 Roadmap To Implement Information Security Management System In Organization
Roadmap To Implement Information Security Management System In OrganizationThis slide represents roadmap that helps organizations implement system for information security management systems to protect sensitive data. It includes steps such as defining scope and objectives, identifying assets, recognizing risk, etc. Introducing our premium set of slides with Roadmap To Implement Information Security Management System In Organization. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Recognize Risk, Make Improvement, Identify Mitigation Measures. So download instantly and tailor it with your information.
-
 Implement Security Systems Icon Using Operating System
Implement Security Systems Icon Using Operating SystemIntroducing our premium set of slides with Implement Security Systems Icon Using Operating System. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Implement Security, Systems Icon, Using Operating System. So download instantly and tailor it with your information.
-
 Steps To Implement Network Segmentation In IoT System IoT Security And Privacy Safeguarding IoT SS
Steps To Implement Network Segmentation In IoT System IoT Security And Privacy Safeguarding IoT SSThis slide highlights network segmentation structure and steps in the IoT ecosystem to increase security and data privacy. It includes steps such as determine all IoT assets, group assets, identify segment strategy, deploy strict access control, and test and monitor. Deliver an outstanding presentation on the topic using this Steps To Implement Network Segmentation In IoT System IoT Security And Privacy Safeguarding IoT SS. Dispense information and present a thorough explanation of Assets Organisations, Between Segments, Monitor Segments using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Identify Threat And Vulnerabilities Within Information System Implementing Strategies To Mitigate Cyber Security
Identify Threat And Vulnerabilities Within Information System Implementing Strategies To Mitigate Cyber SecurityThe following slide highlights threats and vulnerabilities within companys information system to prevent adverse impact and severity. It includes elements such as unclear storage mechanism, inappropriate structure to privilege access, no framework to monitor user behavior etc. Deliver an outstanding presentation on the topic using this Identify Threat And Vulnerabilities Within Information System Implementing Strategies To Mitigate Cyber Security Dispense information and present a thorough explanation of Vulnerability, Threat, Threat Source using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implementing Security Gap Visualization In System
Implementing Security Gap Visualization In SystemThis slide showcases process of implementing visualization security. The main purpose of this template is to showcase various steps of data visualization in business. This includes data assessment, access control policies, train employees, etc. Presenting our set of slides with name Implementing Security Gap Visualization In System. This exhibits information on Six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Assessment, Select Secure Visualization Tools, Establish Access Control Policies, Regular Security Monitoring.
-
 Implementing Smart Security System To Enhance Home Automation
Implementing Smart Security System To Enhance Home AutomationThis slide represents implementation of smart security system that assist people in enhancing their home security and easy assess to home automation system. It includes various features such as access limitation tools, activity detectors, etc. Presenting our set of slides with Implementing Smart Security System To Enhance Home Automation This exhibits information on Six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Access Limitation Tools, Access And Control, Adopt Voice Assistants
-
 30 60 90 Days Plan For IAM Implementation Securing Systems With Identity
30 60 90 Days Plan For IAM Implementation Securing Systems With IdentityThis slide represents the 30-60-90-day plan for Identity and Access Management implementation. The purpose of this slide is to showcase the approaches that need to be followed as short-term, medium, and long-term goals to implement the IAM process. Introducing 30 60 90 Days Plan For IAM Implementation Securing Systems With Identity to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Implementation Plan, Policies And Procedures using this template. Grab it now to reap its full benefits.
-
 Best Practices For IAM Process Implementation Securing Systems With Identity
Best Practices For IAM Process Implementation Securing Systems With IdentityThis slide highlights the Identity and Access Management implementation best practices. The purpose of this slide is to discuss the steps involved these are aligning IT and business needs, shifting security methodology, creating policies and processes, etc. Present the topic in a bit more detail with this Best Practices For IAM Process Implementation Securing Systems With Identity Use it as a tool for discussion and navigation on Change Management, Create Policies And Processes This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Budget Allocation For IAM Implementation In Organization Securing Systems With Identity
Budget Allocation For IAM Implementation In Organization Securing Systems With IdentityThis slide represents the estimated and actual cost of implementing an IAM plan in an organization. The cost categories are IAM software licensing, hardware and infrastructure, implementing service, training and education, testing, and quality assurance. Deliver an outstanding presentation on the topic using this Budget Allocation For IAM Implementation In Organization Securing Systems With Identity Dispense information and present a thorough explanation of Estimated Cost, Actual Cost, Variance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Implement Identity And Access Management Securing Systems With Identity
Checklist To Implement Identity And Access Management Securing Systems With IdentityThis slide represents the checklist to implement the Identity and Access Management plan in an organization. The purpose of this slide is to provide key functional requirements for implementing and deploying IAM in an enterprise environment. Deliver an outstanding presentation on the topic using this Checklist To Implement Identity And Access Management Securing Systems With Identity Dispense information and present a thorough explanation of Iam Policy And Strategy, User Lifecycle Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Parameters Of IAM Implementation Process Securing Systems With Identity
Key Parameters Of IAM Implementation Process Securing Systems With IdentityThis slide highlights the key function of the Identity and Access Management implementation process. The purpose of this slide is to explain the various parameters of IAM implementation these include identity lifecycle management, access control, authentication, and so on. Introducing Key Parameters Of IAM Implementation Process Securing Systems With Identity to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Authentication, Authorization, Identity Governance using this template. Grab it now to reap its full benefits.
-
 Roadmap For Identity And Access Management Implementation Securing Systems With Identity
Roadmap For Identity And Access Management Implementation Securing Systems With IdentityThis slide highlights the project roadmap to implement the Identity and Access Management process. The purpose of this slide is to showcase the different phases of the IAM implementation plan, such as implementing emerging IAM technologies, BYOI adoption, etc. Increase audience engagement and knowledge by dispensing information using Roadmap For Identity And Access Management Implementation Securing Systems With Identity This template helps you present information on Four stages. You can also present information on Iam Technologies, Byoi Adoption, Testing And Security Assurance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Steps To Implement Digital Authentication With IAM Securing Systems With Identity
Steps To Implement Digital Authentication With IAM Securing Systems With IdentityThis slide discusses the IAM implementing digital authentication. The purpose of this slide is to highlight the various types of digital authentication done by IAM, which are unique passwords, pre-shared keys, Behavioral authentication, and biometrics. Increase audience engagement and knowledge by dispensing information using Steps To Implement Digital Authentication With IAM Securing Systems With Identity This template helps you present information on Five stages. You can also present information on Unique Passwords, Biometrics using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Steps To Implement Identity And Access Management In Enterprises Securing Systems With Identity
Steps To Implement Identity And Access Management In Enterprises Securing Systems With IdentityThis slide discusses the Identity and Access Management implementing process in enterprises. The purpose of this slide is to highlight the implementation process, including usage assessment, environment understanding, key IAM considerations, and so on. Introducing Steps To Implement Identity And Access Management In Enterprises Securing Systems With Identity to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Usage Assessment, Environment Understanding using this template. Grab it now to reap its full benefits.
-
 Steps To Implement Identity And Access Management Securing Systems With Identity
Steps To Implement Identity And Access Management Securing Systems With IdentityThis slide discusses the Identity and Access Management implementing program. The purpose of this slide is to highlight the implementation process of IAM, including scope identification, evaluating the right IAM approach, finding the best solution, and so on. Increase audience engagement and knowledge by dispensing information using Steps To Implement Identity And Access Management Securing Systems With Identity This template helps you present information on Six stages. You can also present information on Scope Identification, Define A Strategy, Assess Cost Factors using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Timeline To Implement Identity And Access Management Plan Securing Systems With Identity
Timeline To Implement Identity And Access Management Plan Securing Systems With IdentityThis slide shows the timeline for implementing the Identity and Access Management plan. The key steps include defining the project objective, identifying key stakeholders, determining compliance, integrating IAM with the existing system, etc. Introducing Timeline To Implement Identity And Access Management Plan Securing Systems With Identity to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Applications And Data, Public Cloud Platforms using this template. Grab it now to reap its full benefits.
-
 Address Verification System To Reduce Payment Fraud Implementing E Commerce Security Measures
Address Verification System To Reduce Payment Fraud Implementing E Commerce Security MeasuresThe slide illustrates address verification process to prevent payment fraud along with its key impacts. The process include buyer, billing address, comparing address, and return code. Introducing Address Verification System To Reduce Payment Fraud Implementing E Commerce Security Measures to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Billing Address, Cardholder Records, Potential Impact, using this template. Grab it now to reap its full benefits.
-
 Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Suspicious Activities And Prevent Threats, Protect Organizations Networks, Filter Out Malicious Activities, Security Devices Or Controls, using this template. Grab it now to reap its full benefits.
-
 Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing our well researched set of slides titled Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Table Of Contents For Implementing Intrusion Prevention System For Effective Network Security
Table Of Contents For Implementing Intrusion Prevention System For Effective Network SecurityIntroducing Table Of Contents For Implementing Intrusion Prevention System For Effective Network Security to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Issues Experienced Due Inefficient Network Security, Impact On Organizational Operations, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Budget Plan, Impact Assessment, Dashboards, Case Study Analysis, using this template. Grab it now to reap its full benefits.
-
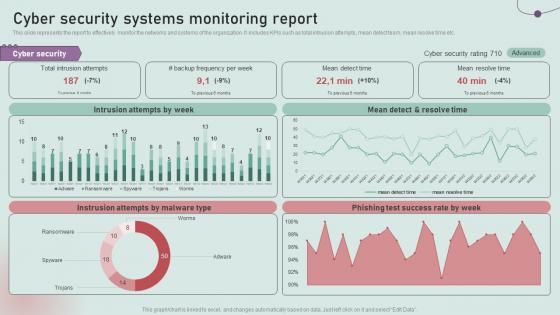 Cyber Security Systems Monitoring Report Development And Implementation Of Security Incident Management
Cyber Security Systems Monitoring Report Development And Implementation Of Security Incident ManagementThis slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Deliver an outstanding presentation on the topic using this Cyber Security Systems Monitoring Report Development And Implementation Of Security Incident Management. Dispense information and present a thorough explanation of Intrusion Attempts, Mean Detect, Resolve Time using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implementing advanced analytics system at workplace contingency plan for threat handling security
Implementing advanced analytics system at workplace contingency plan for threat handling securityThis slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver an outstanding presentation on the topic using this Implementing Advanced Analytics System At Workplace Contingency Plan For Threat Handling Security. Dispense information and present a thorough explanation of Contingency Plan For Threat Handling In Security Centre using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implementing advanced analytics system at workplace determine role of security centre in firm
Implementing advanced analytics system at workplace determine role of security centre in firmThis slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security centre implementation. Present the topic in a bit more detail with this Implementing Advanced Analytics System At Workplace Determine Role Of Security Centre In Firm. Use it as a tool for discussion and navigation on Determine Role Of Security Centre In Firm. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing advanced analytics system at workplace enabling data security risk management action plan
Implementing advanced analytics system at workplace enabling data security risk management action planThe data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver an outstanding presentation on the topic using this Implementing Advanced Analytics System At Workplace Enabling Data Security Risk Management Action Plan. Dispense information and present a thorough explanation of Management, Resources, Enabling using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
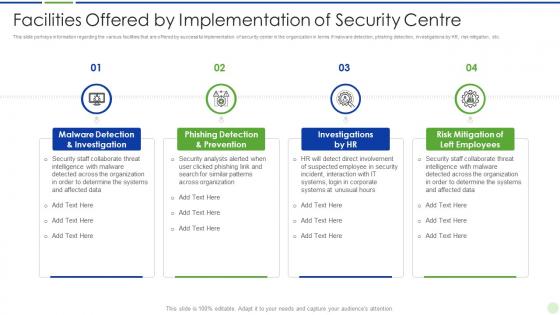 Implementing advanced analytics system at workplace facilities offered by implementation of security
Implementing advanced analytics system at workplace facilities offered by implementation of securityThis slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Deliver an outstanding presentation on the topic using this Implementing Advanced Analytics System At Workplace Facilities Offered By Implementation Of Security. Dispense information and present a thorough explanation of Implementation, Prevention, Investigation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implementing advanced analytics system at workplace overview established security centre
Implementing advanced analytics system at workplace overview established security centreThis slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Present the topic in a bit more detail with this Implementing Advanced Analytics System At Workplace Overview Established Security Centre. Use it as a tool for discussion and navigation on Business, Management, Steering. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing advanced analytics system at workplace timeframe for incident management in security centre
Implementing advanced analytics system at workplace timeframe for incident management in security centreThis slide provides information regarding entire duration of incident handling process which occur in various phases. Present the topic in a bit more detail with this Implementing Advanced Analytics System At Workplace Timeframe For Incident Management In Security Centre. Use it as a tool for discussion and navigation on Timeframe, Management, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Customer Relationship Management System Implementation Steps Enable Data Security
Customer Relationship Management System Implementation Steps Enable Data SecurityThis slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Deliver an outstanding presentation on the topic using this Customer Relationship Management System Implementation Steps Enable Data Security. Dispense information and present a thorough explanation of Implementation, Authentication, Restrictions using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implementation Steps Enable Data Security Crm System Implementation Guide For Businesses
Implementation Steps Enable Data Security Crm System Implementation Guide For BusinessesThis slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Present the topic in a bit more detail with this Implementation Steps Enable Data Security Crm System Implementation Guide For Businesses. Use it as a tool for discussion and navigation on Implementation, Compliance, Authentication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Importance Of Secure Ecommerce Payment Systems Analyzing And Implementing Management System
Importance Of Secure Ecommerce Payment Systems Analyzing And Implementing Management SystemThis slide represents the importance of payment gateways in facilitating systemized payment methods and providing consumers with fast and flexible way for making payments. It includes benefits of ecommerce payment systems such as meets digital needs, customer retention, security etc. Deliver an outstanding presentation on the topic using this Importance Of Secure Ecommerce Payment Systems Analyzing And Implementing Management System. Dispense information and present a thorough explanation of Customer Retention, Security, Multiple Payment Modes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
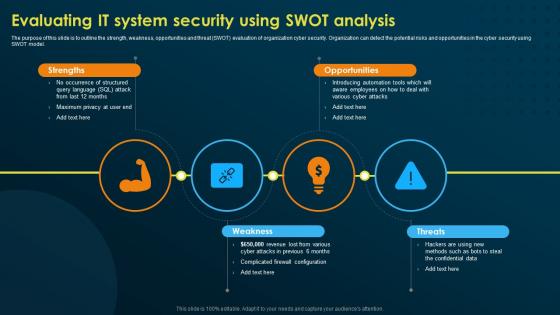 Evaluating It System Security Using Swot Analysis Implementing Security Awareness Training
Evaluating It System Security Using Swot Analysis Implementing Security Awareness TrainingThe purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Increase audience engagement and knowledge by dispensing information using Evaluating It System Security Using Swot Analysis Implementing Security Awareness Training. This template helps you present information on four stages. You can also present information on Strengths, Opportunities, Weakness, Threats using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Importance Of Secure Ecommerce Payment Systems Implementing Ecommerce Management
Importance Of Secure Ecommerce Payment Systems Implementing Ecommerce ManagementThis slide represents the importance of payment gateways in facilitating systemized payment methods and providing consumers with fast and flexible way for making payments. It includes benefits of ecommerce payment systems such as meets digital needs, customer retention, security etc. Introducing Importance Of Secure Ecommerce Payment Systems Implementing Ecommerce Management to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Meets Digital Needs, Customer Retention, Multiple Payment Modes, using this template. Grab it now to reap its full benefits.
-
 Impact Of E Security System Implementation In Organizations
Impact Of E Security System Implementation In OrganizationsThis slide mentions the impact of implementing e-security systems in organizations. The effects include Asset Protection, Security Updates, Conflict Resolution and Automation and Analytics. Presenting our set of slides with name Impact Of E Security System Implementation In Organizations. This exhibits information on four stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Implementation, Organizations, Automation.
-
 Internet security electronic payment system eviction ec implementation
Internet security electronic payment system eviction ec implementationPresenting this set of slides with name - Internet Security Electronic Payment System Eviction Ec Implementation. This is an editable seven stages graphic that deals with topics like Internet Security Electronic Payment System, Eviction Ec Implementation to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Implement security system ppt powerpoint presentation gallery inspiration cpb
Implement security system ppt powerpoint presentation gallery inspiration cpbPresenting our Implement Security System Ppt Powerpoint Presentation Gallery Inspiration Cpbs PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Implement Security System This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Enhanced security event management impact of successful implementation of secops system ppt icon
Enhanced security event management impact of successful implementation of secops system ppt iconThis slide portrays information regarding the impact of successful implementation of SecOps system in terms alert fatigue reduction, threat hunting improvement, etc. Introducing Enhanced Security Event Management Impact Of Successful Implementation Of Secops System Ppt Icon to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Security, Analyst, Improvement, Reduction, using this template. Grab it now to reap its full benefits.
-
 Security information system implementing security management plan ppt gallery clipart
Security information system implementing security management plan ppt gallery clipartThis slide provides information about the fourth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Defining the Information Security Management System. Deliver an outstanding presentation on the topic using this Security Information System Implementing Security Management Plan Ppt Gallery Clipart. Dispense information and present a thorough explanation of Information Security, Security Measures, Acquisition using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enterprise security operations impact of successful implementation of secops system ppt outline
Enterprise security operations impact of successful implementation of secops system ppt outlineThis slide portrays information regarding the impact of successful implementation of SecOps system in terms alert fatigue reduction, threat hunting improvement, etc. Introducing Enterprise Security Operations Impact Of Successful Implementation Of Secops System Ppt Outline to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Security, Analyst, Improvement, Reduction, using this template. Grab it now to reap its full benefits.
-
 Impact of successful implementation of secops system security operations integration
Impact of successful implementation of secops system security operations integrationThis slide portrays information regarding the impact of successful implementation of SecOps system in terms alert fatigue reduction, threat hunting improvement, etc. Increase audience engagement and knowledge by dispensing information using Impact Of Successful Implementation Of Secops System Security Operations Integration. This template helps you present information on four stages. You can also present information on Mean Time To Detection, Total Cases Per Month, Security Analyst Productivity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 It security operations impact of successful implementation of secops system ppt inspiration
It security operations impact of successful implementation of secops system ppt inspirationThis slide portrays information regarding the impact of successful implementation of SecOps system in terms alert fatigue reduction, threat hunting improvement, etc. Introducing IT Security Operations Impact Of Successful Implementation Of Secops System Ppt Inspiration to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Security, Analyst, Improvement, Reduction, using this template. Grab it now to reap its full benefits.
-
 Firewall Implementation For Cyber Security Problems With Current Network Security System
Firewall Implementation For Cyber Security Problems With Current Network Security SystemThis slide highlights the loss experienced by the organization due to the existing security system. The purpose of this slide is to showcase the various cyber attack incidents and losses caused by them to the organization, such as malware infections, unauthorized access, phishing, etc. Present the topic in a bit more detail with this Firewall Implementation For Cyber Security Problems With Current Network Security System. Use it as a tool for discussion and navigation on Existing Security System, Cyber Attack Incidents, Malware Infections, Unauthorized Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Implementation For Cyber Security Threat Tracking Dashboard For Firewall System
Firewall Implementation For Cyber Security Threat Tracking Dashboard For Firewall SystemThis slide represents the dashboard for threat tracking in a firewall-protected network. The purpose of this slide is to showcase the various threats based on categories such as threats by owners, risk by threats, threat report, monthly threat status, current risk status, and threats based on user role. Deliver an outstanding presentation on the topic using this Firewall Implementation For Cyber Security Threat Tracking Dashboard For Firewall System. Dispense information and present a thorough explanation of Threat Tracking Dashboard, Firewall System, Current Risk Status, Firewall Protected Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Implementation For Cyber Security Impact Of Poor Network Security System On Business
Firewall Implementation For Cyber Security Impact Of Poor Network Security System On BusinessThis slide outlines the impact of the existing network security system on the company. The purpose of this slide is to showcase the incidents that happen because of poor network security and the total losses caused by those incidents, such as data breaches and loss, downtime, and so on. Deliver an outstanding presentation on the topic using this Firewall Implementation For Cyber Security Impact Of Poor Network Security System On Business. Dispense information and present a thorough explanation of Downtime And Productivity Loss, Intellectual Property Theft, Legal And Regulatory Consequences using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.



