Powerpoint Templates and Google slides for Implement Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 DevSecOps Process To Integrate Security Into CI CD Pipeline Strategic Roadmap To Implement DevSecOps
DevSecOps Process To Integrate Security Into CI CD Pipeline Strategic Roadmap To Implement DevSecOpsThis slide discusses the integration of security in the CI pipeline for DevSecOps. The purpose of this slide is to explain the procedure of security implementation, including steps that are backlog, code or commit, build or test, deploy, and monitor. Present the topic in a bit more detail with this DevSecOps Process To Integrate Security Into CI CD Pipeline Strategic Roadmap To Implement DevSecOps. Use it as a tool for discussion and navigation on Integrate Security, Encourage Developer Ownership, Static Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
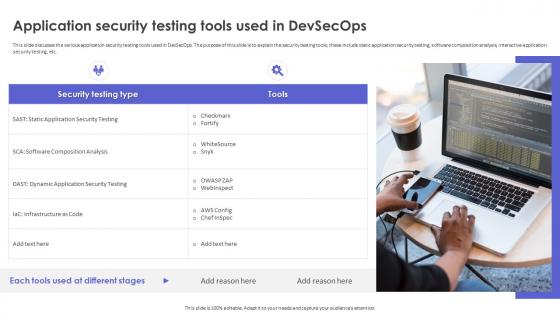 Strategic Roadmap To Implement DevSecOps Application Security Testing Tools Used In DevSecOps
Strategic Roadmap To Implement DevSecOps Application Security Testing Tools Used In DevSecOpsThis slide discusses the various application security testing tools used in DevSecOps. The purpose of this slide is to explain the security testing tools these include static application security testing, software composition analysis, interactive application security testing, etc. Increase audience engagement and knowledge by dispensing information using Strategic Roadmap To Implement DevSecOps Application Security Testing Tools Used In DevSecOps. This template helps you present information on one stages. You can also present information on Application Security Testing, Software Composition Analysis, Interactive Application Security Testing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategic Roadmap To Implement DevSecOps Pipeline Security Working Of DevSecOps Model
Strategic Roadmap To Implement DevSecOps Pipeline Security Working Of DevSecOps ModelThis slide discusses the pipeline security of DevSecOps. The purpose of this slide is to explain pipeline security and its importance in DevSecOps, which includes maximizing security personnel efficiency, automating non-intellectual tasks, improving the tracking of task statuses, and so on. Deliver an outstanding presentation on the topic using this Strategic Roadmap To Implement DevSecOps Pipeline Security Working Of DevSecOps Model. Dispense information and present a thorough explanation of Boost Workflow Efficiency, Performance Metrics, Pipeline Security Working using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 30 60 90 Days Plan For Security Testing Implementation
30 60 90 Days Plan For Security Testing ImplementationThis slide showcases the 30-60-90 plan for Wireless LAN controller installation. The purpose of this slide is to highlight the plan for installation such as planning and preparations, implementations and configurations, optimization, and documentation, etc. Introducing 30 60 90 Days Plan For Security Testing Implementation to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Assess And Plan, Skill And Tool Acquisition, Implementation And Integration, using this template. Grab it now to reap its full benefits.
-
 Before Vs After Implementing Security Testing
Before Vs After Implementing Security TestingThis slide represents the before vs. after implementing security testing based on several known vulnerabilities, high-risk vulnerability, low-risk vulnerability, etc. Deliver an outstanding presentation on the topic using this Before Vs After Implementing Security Testing. Dispense information and present a thorough explanation of High Risk Vulnerabilities, Medium Risk Vulnerabilities, Low Risk Vulnerabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Budget For Implementing Security Testing In Organization
Budget For Implementing Security Testing In OrganizationThis slide represents the budget for implementing security testing components such as security assessment tools, training and workshops, security testing software, etc. Present the topic in a bit more detail with this Budget For Implementing Security Testing In Organization. Use it as a tool for discussion and navigation on Security Assessment Tools, Training And Workshops, Security Testing Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist For Implementing Application Security Testing
Checklist For Implementing Application Security TestingThis slide represents the checklist for implementing application security testing components such as coverage, low false positive, exploitability, code visibility, etc. Deliver an outstanding presentation on the topic using this Checklist For Implementing Application Security Testing. Dispense information and present a thorough explanation of Static Application Security Testing, Dynamic Application Security Testing, Interactive Application Security Testing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist For Implementing Security Testing In Organization
Checklist For Implementing Security Testing In OrganizationThe purpose of this slide is to highlight the key approaches for implementing security testing such as identifying and prioritizing assets, choosing appropriate testing tools, etc. Present the topic in a bit more detail with this Checklist For Implementing Security Testing In Organization. Use it as a tool for discussion and navigation on Identify And Prioritize Assets, Choose Appropriate Testing Tools, Conduct Threat Modelling. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Roadmap For Implementing Security Testing In Organization
Roadmap For Implementing Security Testing In OrganizationThis slide showcases the schedule for putting wireless LAN controllers into practice. The purpose of this slide is to highlight the installation plan for wireless LAN controllers such as need assessment and goal defining, infrastructure planning, etc. Introducing Roadmap For Implementing Security Testing In Organization to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Security Testing, Infrastructure Planning, Installation Plan For Wireless, using this template. Grab it now to reap its full benefits.
-
 Security Testing Implementation Training Program
Security Testing Implementation Training ProgramThe purpose of this slide is to outline the security testing implementation training program such as mode, cost, agenda, and schedule for the training programs. Present the topic in a bit more detail with this Security Testing Implementation Training Program. Use it as a tool for discussion and navigation on Security Testing Implementation, Training Program, Web Application Security Testing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Software Security Testing Implementation Challenges
Software Security Testing Implementation ChallengesThis slide highlights the challenges faced during the implementation of security testing such as the velocity of software development, weaknesses in the code, etc. Increase audience engagement and knowledge by dispensing information using Several Emerging Trends In Security Testing. This template helps you present information on five stages. You can also present information on Weaknesses In The Code, Velocity Of Software Development, Application Security Planning using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IoT Device Identity Platform Implementation Internet Of Things IoT Security Cybersecurity SS
IoT Device Identity Platform Implementation Internet Of Things IoT Security Cybersecurity SSThis slide showcases internet of things IoT device identity platform deployment, referable for businesses in developing mitigation process. It provides details about APIs, architecture, device client, etc. Deliver an outstanding presentation on the topic using this IoT Device Identity Platform Implementation Internet Of Things IoT Security Cybersecurity SS. Dispense information and present a thorough explanation of IoT Device, Platform Deployment, Developing Mitigation Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Timeline For Implementing IoT Security Strategy Internet Of Things IoT Security Cybersecurity SS
Timeline For Implementing IoT Security Strategy Internet Of Things IoT Security Cybersecurity SSThis slide showcases internet of things IoT security strategy timeline, referable for developers and businesses in protection of connected devices. It provides details about credentials, authentication, cryptography, etc. Introducing Timeline For Implementing IoT Security Strategy Internet Of Things IoT Security Cybersecurity SS to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Avoid Unnecessary Data Handling, Cryptographic Network Protocol Usage, Enforce Authentication Controls, using this template. Grab it now to reap its full benefits.
-
 Benefits Of Implementing NIPS Cyber Security
Benefits Of Implementing NIPS Cyber SecurityThis slide depicts the advantages of executing NIPS cybersecurity. This slide aims to help the business leverage NIPS cybersecurity to prevent external attacks. It includes advantages such as reducing the likelihood of cyber attacks, increasing threat protection, etc. Introducing our Benefits Of Implementing NIPS Cyber Security set of slides. The topics discussed in these slides are Advantages, Description, Impact This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security Methods For Implementing Email Encryption
Security Methods For Implementing Email EncryptionThis slide outlines the security methods for implementing email encryption which includes encrypted PDFs secure attachments, web portal encryption, etc. Introducing our premium set of slides with Security Methods For Implementing Email Encryption. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Secure Attachments, Web Portal, Gateway Software. So download instantly and tailor it with your information.
-
 Implement Robust Security Measures Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Implement Robust Security Measures Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon features a powerful and secure lock symbol, representing the implementation of robust security measures for big data platforms. It is perfect for presentations and documents related to data security, providing a visual representation of the importance of protecting sensitive information.
-
 Implement Robust Security Measures Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Implement Robust Security Measures Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone PowerPoint icon represents the implementation of robust security measures for big data platforms. It is designed to convey the importance of protecting sensitive data in a professional and efficient manner. With its clean and simple design, it is perfect for use in presentations, reports, and other materials related to big data security.
-
 Existing IT Security Strategic Implementation Of Regression Testing
Existing IT Security Strategic Implementation Of Regression TestingThis slide highlights the components of the current IT security infrastructure, which are prone to several functionality concerns. These constituents are vulnerability scanners, improper functioning, functional disrupt, and so on. Deliver an outstanding presentation on the topic using this Existing IT Security Strategic Implementation Of Regression Testing. Dispense information and present a thorough explanation of Existing IT Security, Infrastructure Constituents using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 30 60 90 Day Plan For Cyber Security Framework Implementation
30 60 90 Day Plan For Cyber Security Framework ImplementationThis slide discusses the 30-60-90-day plan for cyber security framework implementation which include stakeholder alignment, awareness training and so on. Introducing 30 60 90 Day Plan For Cyber Security Framework Implementation to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Stakeholder Alignment, Conduct Initial Gap Analysis, Conduct Awareness Training, using this template. Grab it now to reap its full benefits.
-
 Before Vs After Of Cyber Security Framework Implementation
Before Vs After Of Cyber Security Framework ImplementationThis slide discusses the before vs after impact of cyber security framework implementation based on aspects like security posture, incident response, etc. Present the topic in a bit more detail with this Before Vs After Of Cyber Security Framework Implementation. Use it as a tool for discussion and navigation on Incident Response, Cyber Security, Framework Implementation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Framework Implementation Budget
Cyber Security Framework Implementation BudgetThis slide discusses the implementation budget for cyber security framework which includes compliance requirements, risk assessments and security training. Deliver an outstanding presentation on the topic using this Cyber Security Framework Implementation Budget. Dispense information and present a thorough explanation of Compliance Requirements, Risk Assessments, Security Training, Security Requirements For Business Initiatives using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Framework Implementation Challenges
Cyber Security Framework Implementation ChallengesThis slide discusses the major challenges of cyber security framework implementation which include budget constraints, lack of integration and so on. Introducing Cyber Security Framework Implementation Challenges to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Insufficiently Trained Personnel, Budget Constraints, Cyber Security Framework, Implementation Challenges, using this template. Grab it now to reap its full benefits.
-
 Need For Implementing Cyber Security Framework
Need For Implementing Cyber Security FrameworkThis slide highlights the need for implementing cyber security framework which includes easily adaptable and cost efficient, collaboration opportunities, etc. Introducing Need For Implementing Cyber Security Framework to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Collaboration Opportunities, Easily Maintain Compliance, Secure Supply Chain, using this template. Grab it now to reap its full benefits.
-
 Strategies For Implementing AI Powered Global Technology In Cyber Security
Strategies For Implementing AI Powered Global Technology In Cyber SecurityThis slide shows strategic approaches for implementing AI in cyber security. The purpose of this slide is to strengthen organizations defence against potential cyber attacks to maximize effectiveness of global technological solutions. It covers strategies such as resource allocation, training data, internal processes, etc. Presenting our set of slides with Strategies For Implementing AI Powered Global Technology In Cyber Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Resource Allocation, Training Data, Internal Processes.
-
 Web Based Software Security Implementation Checklist For Managers
Web Based Software Security Implementation Checklist For ManagersThis slide showcases checklist for SaaS security implementation and assessment. This includes activities such as running security tests, trAIning staff for safety practices, and planning backups for new threats, cloud sources, and security alert systems. Introducing our Web Based Software Security Implementation Checklist For Managers set of slides. The topics discussed in these slides are Run Security Test, Monitoring And Logging, Checklist For Managers. This is an immediately avAIlable PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Application Security Implementation Plan Budget Allocation To Implement Application Security
Application Security Implementation Plan Budget Allocation To Implement Application SecurityThis slide showcases the training cost breakdown for different components such as instructor, training cost, etc. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Budget Allocation To Implement Application Security. Dispense information and present a thorough explanation of Security Infrastructure, Security Personnel, Insurance And Legal Costs, Budget Allocation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Implementation Plan Checklist For Effective Application Security Implementation
Application Security Implementation Plan Checklist For Effective Application Security ImplementationThis slide showcases the actions performed while deploying application security, person responsible, status and comments for the same. Present the topic in a bit more detail with this Application Security Implementation Plan Checklist For Effective Application Security Implementation. Use it as a tool for discussion and navigation on Assessment And Planning, Education And Training, Incident Response Planning. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Application Security Implementation Plan Comparative Analysis Of Application Security Tools
Application Security Implementation Plan Comparative Analysis Of Application Security ToolsThis slide highlights the comparison of different application security tools and optimal selection of the tool along with the reason of selection. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Comparative Analysis Of Application Security Tools. Dispense information and present a thorough explanation of Comparative Analysis, Application Security Tools, Commercial, License using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Implementation Plan Existing IT Security Infrastructure Threats
Application Security Implementation Plan Existing IT Security Infrastructure ThreatsThis slide highlights the components of the current IT security infrastructure, which are prone to several functionality concerns. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Existing IT Security Infrastructure Threats. Dispense information and present a thorough explanation of Broken Authentication, Cross Site Scripting, Denial Of Service, Infrastructure Threats using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Implementation Plan Five Step Roadmap To Implement Application Security
Application Security Implementation Plan Five Step Roadmap To Implement Application SecurityThis slide outlines the steps to deploy application security in organization such as defining objectives, planning, monitoring, etc. Introducing Application Security Implementation Plan Five Step Roadmap To Implement Application Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Monitoring And Logging, Incident Response, Education And Planning, Application Security, using this template. Grab it now to reap its full benefits.
-
 Application Security Implementation Plan Implementing Effective Security Testing In Organization
Application Security Implementation Plan Implementing Effective Security Testing In OrganizationThis slide showcases the deployment process of security testing parallel to Software Development Testing Lifecycle SDLC stages. Increase audience engagement and knowledge by dispensing information using Application Security Implementation Plan Implementing Effective Security Testing In Organization. This template helps you present information on seven stages. You can also present information on System Testing, Implementation System Testing, Integration Testing, Requirement using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Application Security Implementation Plan Key Challenges Of Existing Application Security Infrastructure
Application Security Implementation Plan Key Challenges Of Existing Application Security InfrastructureThis slide discusses the issues faced by the organization after implementation of application security such as outdated technology, scalability concerns, etc. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Key Challenges Of Existing Application Security Infrastructure. Dispense information and present a thorough explanation of Inadequate User Training, Scalability Concerns, Outdated Technology using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Implementation Plan Major Impact Of Application Security On Business
Application Security Implementation Plan Major Impact Of Application Security On BusinessThis slide showcases the after application security impact on business along with factors that have improved the overall performance. Introducing Application Security Implementation Plan Major Impact Of Application Security On Business to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Threats Surge, Security Increase, Reduced Attacks On Applications, using this template. Grab it now to reap its full benefits.
-
 Application Security Implementation Plan Of Table Of Contents
Application Security Implementation Plan Of Table Of ContentsPresent the topic in a bit more detail with this Application Security Implementation Plan Of Table Of Contents. Use it as a tool for discussion and navigation on Application Security, Implementation Plan, Attacks On Application. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Application Security Implementation Plan Performance Gap Analysis For Implementing Application Security
Application Security Implementation Plan Performance Gap Analysis For Implementing Application SecurityThe purpose of this slide is to indicate the performance analysis of the organizations current security infrastructure. Increase audience engagement and knowledge by dispensing information using Application Security Implementation Plan Performance Gap Analysis For Implementing Application Security. This template helps you present information on four stages. You can also present information on Proper Functioning, Implement Robust Encryption Protocols, Lack Of Ideal Security Measures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Application Security Implementation Plan Process Of Implementing Cloud Native Application Security
Application Security Implementation Plan Process Of Implementing Cloud Native Application SecurityThis slide highlights the steps for deploying cloud-native application security which include understanding principles, risk assessment, etc. Introducing Application Security Implementation Plan Process Of Implementing Cloud Native Application Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Risk Assessment, Continuous Monitoring, Container Security, Implement Strong Access Controls, using this template. Grab it now to reap its full benefits.
-
 Application Security Implementation Plan Process Phases For Effective Authentication Implementation
Application Security Implementation Plan Process Phases For Effective Authentication ImplementationThis slide showcases the steps for deploying effective authentication which include defining requirements, selecting authentication method, etc. Increase audience engagement and knowledge by dispensing information using Application Security Implementation Plan Process Phases For Effective Authentication Implementation. This template helps you present information on seven stages. You can also present information on Implement Login Mechanism, Choose Authentication Method, Secure Storage Of Credentials using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Application Security Implementation Plan Project Summary For Implementing Application Security
Application Security Implementation Plan Project Summary For Implementing Application SecurityThe purpose of this slide is to represent the summary of the application security project providing information regarding problems faced, solution, etc. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Project Summary For Implementing Application Security. Dispense information and present a thorough explanation of Vulnerability In Application, Estimated Cost, Estimated Timeline, Application Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Implementation Plan RACI Matrix To Deploy Application Security
Application Security Implementation Plan RACI Matrix To Deploy Application SecurityThis slide showcases a RACI matrix for application security, outlining the appropriate roles and steps to be taken during application security implementation. Present the topic in a bit more detail with this Application Security Implementation Plan RACI Matrix To Deploy Application Security. Use it as a tool for discussion and navigation on Secure Development Practices, Risk Assessment, Data Encryption, Application Security . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Application Security Implementation Plan Risks And Mitigation Strategies While Deploying Application Security
Application Security Implementation Plan Risks And Mitigation Strategies While Deploying Application SecurityThe purpose of this slide is to discuss the challenges faced while implementing application security such as data breaches, third-party risks, etc. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Risks And Mitigation Strategies While Deploying Application Security. Dispense information and present a thorough explanation of Vulnerabilities In Applications, Data Breaches, Application Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Implementation Plan Statistics Of It Infrastructure Attacks On Organization
Application Security Implementation Plan Statistics Of It Infrastructure Attacks On OrganizationThis slide summarizes security attacks across different organizational departments, such as IT, HR, Sales, Finance, etc. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Statistics Of IT Infrastructure Attacks On Organization. Dispense information and present a thorough explanation of Statistics Of IT Infrastructure, Attacks On Organization, Organizational Departments, Finance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Implementation Plan Steps For Deploying Application Security Testing
Application Security Implementation Plan Steps For Deploying Application Security TestingThis slide showcases the steps for deploying effective application security testing which include establishing test case, including security exam, etc. Introducing Application Security Implementation Plan Steps For Deploying Application Security Testing to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Execute Security Exam, Examine Outcomes, Include Security Exam, Stablish Working Test Case, using this template. Grab it now to reap its full benefits.
-
 Application Security Implementation Plan Steps For Effective Encryption Method Deployment
Application Security Implementation Plan Steps For Effective Encryption Method DeploymentThis slide highlights the steps for deploying effective encryption which include selecting appropriate algorithm, choosing correct key size, etc. Increase audience engagement and knowledge by dispensing information using Application Security Implementation Plan Steps For Effective Encryption Method Deployment. This template helps you present information on six stages. You can also present information on Select Appropriate Algorithm, Select Appropriate Program, Maintain Key Security, Encryption Method Deployment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Application Security Implementation Plan Steps To Deploy Efficient Access Control
Application Security Implementation Plan Steps To Deploy Efficient Access ControlThis slide discusses the process phases of implementing access control which include taking inventory of systems, examining staffs, etc. Introducing Application Security Implementation Plan Steps To Deploy Efficient Access Control to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Establish Roles, Resist Sporadic Adjustments, Examine The Staff, Take Inventory Of Systems, using this template. Grab it now to reap its full benefits.
-
 Application Security Implementation Plan Team Structure For Application Security Deployment
Application Security Implementation Plan Team Structure For Application Security DeploymentThis slide represents the team structure for the application security in the IT infrastructure which includes manager, team lead, application security team, etc. Present the topic in a bit more detail with this Application Security Implementation Plan Team Structure For Application Security Deployment. Use it as a tool for discussion and navigation on Application Security Team, Database Management Team, Security Analyst, Malware Analyst. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Application Security Implementation Plan Timeline For Deploying Efficient Application Security
Application Security Implementation Plan Timeline For Deploying Efficient Application SecurityThis slide outlines the different steps performed while deploying application security, including planning phase, requirement gathering, etc. Increase audience engagement and knowledge by dispensing information using Application Security Implementation Plan Timeline For Deploying Efficient Application Security. This template helps you present information on six stages. You can also present information on Education And Training, Patch Management, Incident Response Planning, Establish Security Policies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Application Security Implementation Plan Top Application Security Service Providers
Application Security Implementation Plan Top Application Security Service ProvidersThis slide outlines the comparison of different application security service providers and optimal selection of the provider along with the reason of selection. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Top Application Security Service Providers. Dispense information and present a thorough explanation of Service Provider Application, Security Service using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Security Implementation Plan Working Process Of Effective Logging Implementation
Application Security Implementation Plan Working Process Of Effective Logging ImplementationThis slide outlines the steps for deploying effective logging which include assess requirements, select logging tool, defining logging standards, etc. Introducing Application Security Implementation Plan Working Process Of Effective Logging Implementation to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Ensure Security, Centralize Log Management, Define Logging Standards, Select Logging Tools, using this template. Grab it now to reap its full benefits.
-
 Icons Slide For Application Security Implementation Plan
Icons Slide For Application Security Implementation PlanIntroducing our well researched set of slides titled Icons Slide For Application Security Implementation Plan. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Table Of Contents For Application Security Implementation Plan
Table Of Contents For Application Security Implementation PlanIncrease audience engagement and knowledge by dispensing information using Table Of Contents For Application Security Implementation Plan. This template helps you present information on fifteen stages. You can also present information on Implementation Process, Project Roadmap, Risks And Mitigation Strategies, Project Implementation Budget using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Endpoint Security Approaches To Implement Effective Endpoint Security
Endpoint Security Approaches To Implement Effective Endpoint SecurityThis slide showcases the techniques of deploying effective endpoint security which include on-location, cloud, hybrid endpoint security, etc. Introducing Endpoint Security Approaches To Implement Effective Endpoint Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Agent Based Security, Remote Device Connection, Effective Endpoint Security, using this template. Grab it now to reap its full benefits.
-
 Endpoint Security Before Vs After Implementing Of Endpoint Security
Endpoint Security Before Vs After Implementing Of Endpoint SecurityThis slide showcases the comparative analysis of the before versus after implementation of endpoint security situation of an organization. Increase audience engagement and knowledge by dispensing information using Endpoint Security Before Vs After Implementing Of Endpoint Security. This template helps you present information on four stages. You can also present information on Enhanced Compliance, Improved Incident Detection, High Vulnerability To Malware using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Endpoint Security Best Practices For Implementing Endpoint Security
Endpoint Security Best Practices For Implementing Endpoint SecurityThis slide discusses the best approaches for endpoint security deployment which include anti-phishing deployment, ransomware protection, etc. Introducing Endpoint Security Best Practices For Implementing Endpoint Security to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Enhanced Compliance, Improved Incident Detection, High Vulnerability To Malware, using this template. Grab it now to reap its full benefits.
-
 Endpoint Security Budget Allocation For Implementing Endpoint Security
Endpoint Security Budget Allocation For Implementing Endpoint SecurityThis slide showcases the technology cost breakdown for different components such as internet, software, IT staff, etc. Present the topic in a bit more detail with this Endpoint Security Budget Allocation For Implementing Endpoint Security. Use it as a tool for discussion and navigation on Budget Allocation, Implementing Endpoint Security, Technology Cost Breakdown. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Endpoint Security Checklist To Implement Effective Endpoint Security
Endpoint Security Checklist To Implement Effective Endpoint SecurityThis slide showcases the actions performed while deploying endpoint security, person responsible, status and comments for the same. Deliver an outstanding presentation on the topic using this Endpoint Security Checklist To Implement Effective Endpoint Security. Dispense information and present a thorough explanation of Education And Training, Recognize Known Malware, Endpoint Protection Software using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Endpoint Security Implementation Process Of Endpoint Security Solutions
Endpoint Security Implementation Process Of Endpoint Security SolutionsThis slide highlights the process stages of endpoint security which include information gathering, choosing security solutions, etc. Increase audience engagement and knowledge by dispensing information using Endpoint Security Implementation Process Of Endpoint Security Solutions. This template helps you present information on three stages. You can also present information on Gather Information, Deploy Selected Solutions, Select Security Solutions, Endpoint Security Solutions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Endpoint Security Roadmap To Implement Effective Endpoint Security
Endpoint Security Roadmap To Implement Effective Endpoint SecurityThis slide outlines the steps to deploy endpoint security which include recognizing known malware, reduce end user access, utilizing application control, etc. Increase audience engagement and knowledge by dispensing information using Endpoint Security Roadmap To Implement Effective Endpoint Security. This template helps you present information on six stages. You can also present information on Utilize Sensible Application Control, Recognize And Avoid Known Malware, Block Dangerous Activity, Effective Endpoint Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Endpoint Security Timeline For Implementing Efficient Endpoint Security
Endpoint Security Timeline For Implementing Efficient Endpoint SecurityThis slide outlines the different steps performed while deploying endpoint security, including planning phase, solution selection, etc. Introducing Endpoint Security Timeline For Implementing Efficient Endpoint Security to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Testing And Optimization, Solution Selection, Deployment, Endpoint Security, using this template. Grab it now to reap its full benefits.
-
 Application Security Implementation Plan Selection Of Optimal Application Security Technique
Application Security Implementation Plan Selection Of Optimal Application Security TechniqueThis slide outlines the comparison of different application testing techniques on the basis of parameters such as security provided and cost. Present the topic in a bit more detail with this Application Security Implementation Plan Selection Of Optimal Application Security Technique. Use it as a tool for discussion and navigation on Authorization, Encryption, Security Testing, Access Control. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Six Steps For Implementing Visualization Security
Six Steps For Implementing Visualization SecurityThis slide showcases process of implementing visualization security. The main purpose of this template is to showcase various steps of data visualization in business. This includes data assessment, access control policies, train employees, etc. Introducing our premium set of slides with Six Steps For Implementing Visualization Security. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Regular Security, Train Employee, Data Encryption. So download instantly and tailor it with your information.





