Powerpoint Templates and Google slides for Implement Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Sales CRM Cloud Implementation Securing Our Data With CRM Ppt Slides Image
Sales CRM Cloud Implementation Securing Our Data With CRM Ppt Slides ImageThis slide illustrates the issues that trigger poor relationship with customers which includes no real time support, no innovative product launched, bad after sale service and lack of engagement. Present the topic in a bit more detail with this Sales CRM Cloud Implementation Poor Relationship With Customers Ppt Slides Picture. Use it as a tool for discussion and navigation on Weak Relationship Building, Poor Customer Service, Product Launched. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Securing Our Data With Crm Crm Software Implementation Ppt Slides Demonstration
Securing Our Data With Crm Crm Software Implementation Ppt Slides DemonstrationThis slide highlights the data security using CRM which incorporates IP restriction, two factor authentication, data storage, communication protection and data security. Deliver an outstanding presentation on the topic using this Securing Our Data With Crm Crm Software Implementation Ppt Slides Demonstration. Dispense information and present a thorough explanation of Data Storage And Failover, Communication Protection, Data Backup using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Conducting Cyber Security Gap Analysis Of Organization Implementing Security Awareness Training
Conducting Cyber Security Gap Analysis Of Organization Implementing Security Awareness TrainingThe purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. Present the topic in a bit more detail with this Conducting Cyber Security Gap Analysis Of Organization Implementing Security Awareness Training. Use it as a tool for discussion and navigation on Desired State, Reasons Identified, Approaches To Be Deployed. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determining The Actors Behind Most Significant Implementing Security Awareness Training
Determining The Actors Behind Most Significant Implementing Security Awareness TrainingThe purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Present the topic in a bit more detail with this Determining The Actors Behind Most Significant Implementing Security Awareness Training. Use it as a tool for discussion and navigation on Online Criminals, Foreign Government Officials, Malicious Insiders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 How To Overcome The Security Awareness Training Implementing Security Awareness Training
How To Overcome The Security Awareness Training Implementing Security Awareness TrainingThe purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program, convenient program etc. Present the topic in a bit more detail with this How To Overcome The Security Awareness Training Implementing Security Awareness Training. Use it as a tool for discussion and navigation on Outdated Content, Burden On Administrators, Low Employee Participation Rate. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Statistics Showing The Impact Of Security Awareness Implementing Security Awareness Training
Key Statistics Showing The Impact Of Security Awareness Implementing Security Awareness TrainingPresent the topic in a bit more detail with this Key Statistics Showing The Impact Of Security Awareness Implementing Security Awareness Training. Use it as a tool for discussion and navigation on Key Statistics, Security Awareness, Training Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 KPI Dashboard To Monitor Cyber Security Performance Implementing Security Awareness Training
KPI Dashboard To Monitor Cyber Security Performance Implementing Security Awareness TrainingThe purpose of this slide is to highlight key performance indicator KPI dashboard which can be used to track the performance of organization cyber security. The KPI metrics covered in the slide are asset type control, control issues by standard and regulation etc. Deliver an outstanding presentation on the topic using this KPI Dashboard To Monitor Cyber Security Performance Implementing Security Awareness Training. Dispense information and present a thorough explanation of Asset Type Control, Control Issues By Standard, Review Effectiveness using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 KPI Metrics Dashboard To Effectively Track Cyber Threat Implementing Security Awareness Training
KPI Metrics Dashboard To Effectively Track Cyber Threat Implementing Security Awareness TrainingThe purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Present the topic in a bit more detail with this KPI Metrics Dashboard To Effectively Track Cyber Threat Implementing Security Awareness Training. Use it as a tool for discussion and navigation on Current Risk Status, Threats By Owners, Risk By Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Measuring The Impact Of Security Awareness Training Implementing Security Awareness Training
Measuring The Impact Of Security Awareness Training Implementing Security Awareness TrainingThe purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. Deliver an outstanding presentation on the topic using this Measuring The Impact Of Security Awareness Training Implementing Security Awareness Training. Dispense information and present a thorough explanation of Measuring, Impact Of Security, Awareness Training using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Most Common Cyber Attack Faced By Our Employees Implementing Security Awareness Training
Most Common Cyber Attack Faced By Our Employees Implementing Security Awareness TrainingThe purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, IoT based attacks, malware, social engineering attack and business email compromise. Introducing Most Common Cyber Attack Faced By Our Employees Implementing Security Awareness Training to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Ransomware, Password Attack, Cryptojacking, Malware, using this template. Grab it now to reap its full benefits.
-
 Operational Outlook Of Security Awareness Training Implementing Security Awareness Training
Operational Outlook Of Security Awareness Training Implementing Security Awareness TrainingThe purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered etc. Present the topic in a bit more detail with this Operational Outlook Of Security Awareness Training Implementing Security Awareness Training. Use it as a tool for discussion and navigation on Operational Outlook, Security Awareness, Training Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Practices To Improve Security Awareness Level Amongst Implementing Security Awareness Training
Practices To Improve Security Awareness Level Amongst Implementing Security Awareness TrainingThe purpose of this slide is to outline different approaches used to enhance the cyber security awareness level. Creating security awareness program, conducting quarterly training session and implementing cyber security drills are some of the major approaches which are highlighted in the slide. Deliver an outstanding presentation on the topic using this Practices To Improve Security Awareness Level Amongst Implementing Security Awareness Training. Dispense information and present a thorough explanation of Create Security, Awareness Program, Cyber Security Training using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Awareness Training Program Challenges Implementing Security Awareness Training
Security Awareness Training Program Challenges Implementing Security Awareness TrainingThe purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Introducing Security Awareness Training Program Challenges Implementing Security Awareness Training to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Outdated Content, Burden On Administrators, Employees Lose Interest, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents Implementing Security Awareness Training To Prevent Cyber Attacks
Table Of Contents Implementing Security Awareness Training To Prevent Cyber AttacksPresent the topic in a bit more detail with this Table Of Contents Implementing Security Awareness Training To Prevent Cyber Attacks. Use it as a tool for discussion and navigation on Security Awareness, Current Assessment, Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Consequences Of Data Breaches Faced By Organization Implementing Cyber Security Ppt Diagrams
Consequences Of Data Breaches Faced By Organization Implementing Cyber Security Ppt DiagramsThis slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Deliver an outstanding presentation on the topic using this Consequences Of Data Breaches Faced By Organization Implementing Cyber Security Ppt Diagrams. Dispense information and present a thorough explanation of Data Breaches, Consequences, Organization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enterprise Cyber Risk Management Dashboard Implementing Cyber Security Ppt Demonstration
Enterprise Cyber Risk Management Dashboard Implementing Cyber Security Ppt DemonstrationThis slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Deliver an outstanding presentation on the topic using this Enterprise Cyber Risk Management Dashboard Implementing Cyber Security Ppt Demonstration. Dispense information and present a thorough explanation of Enterprise Cyber, Risk Management, Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Financial Implementing Cyber Security Incident Management Ppt Topics
Financial Implementing Cyber Security Incident Management Ppt TopicsPresent the topic in a bit more detail with this Financial Implementing Cyber Security Incident Management Ppt Topics. Use it as a tool for discussion and navigation on Minimum, Medium, Maximum. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Attack Prevention Techniques Implementing Security Awareness Training
Social Engineering Attack Prevention Techniques Implementing Security Awareness TrainingThe purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no s haring of password. Present the topic in a bit more detail with this Social Engineering Attack Prevention Techniques Implementing Security Awareness Training. Use it as a tool for discussion and navigation on Limit Public Information, Verify The Source, No Sharing Of Password. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
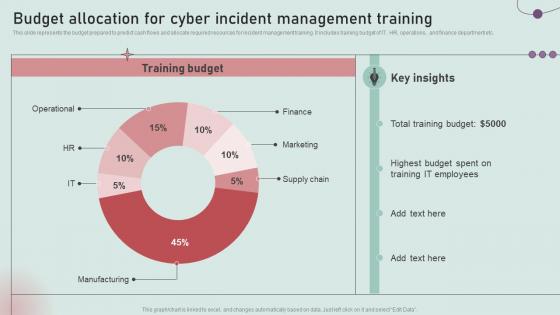 Budget Allocation For Cyber Incident Management Training Development And Implementation Of Security
Budget Allocation For Cyber Incident Management Training Development And Implementation Of SecurityThis slide represents the budget prepared to predict cash flows and allocate required resources for incident management training. It includes training budget of IT, HR, operations, and finance department etc. Deliver an outstanding presentation on the topic using this Budget Allocation For Cyber Incident Management Training Development And Implementation Of Security. Dispense information and present a thorough explanation of Total Training Budget, It Employees, Highest Budget using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Consequences Of Data Breaches Faced By Organization Development And Implementation Of Security
Consequences Of Data Breaches Faced By Organization Development And Implementation Of SecurityThis slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Deliver an outstanding presentation on the topic using this Consequences Of Data Breaches Faced By Organization Development And Implementation Of Security. Dispense information and present a thorough explanation of Payment Card Fraud, Physical Loss, Insider Leak using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Incident Response KPI Dashboard Development And Implementation Of Security Incident
Cyber Security Incident Response KPI Dashboard Development And Implementation Of Security IncidentThis slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. Deliver an outstanding presentation on the topic using this Cyber Security Incident Response KPI Dashboard Development And Implementation Of Security Incident. Dispense information and present a thorough explanation of Total Financial Risk, Compliance, Monitoring using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Risk Assessment And Management Dashboard Development And Implementation Of Security
Cyber Security Risk Assessment And Management Dashboard Development And Implementation Of SecurityThis slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Deliver an outstanding presentation on the topic using this Cyber Security Risk Assessment And Management Dashboard Development And Implementation Of Security. Dispense information and present a thorough explanation of Medium Risk, Unresolved Side, Inactive Accounts using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
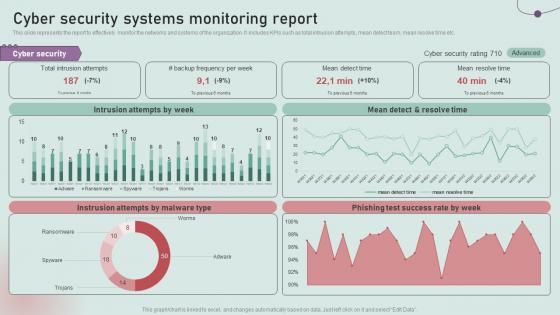 Cyber Security Systems Monitoring Report Development And Implementation Of Security Incident Management
Cyber Security Systems Monitoring Report Development And Implementation Of Security Incident ManagementThis slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Deliver an outstanding presentation on the topic using this Cyber Security Systems Monitoring Report Development And Implementation Of Security Incident Management. Dispense information and present a thorough explanation of Intrusion Attempts, Mean Detect, Resolve Time using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
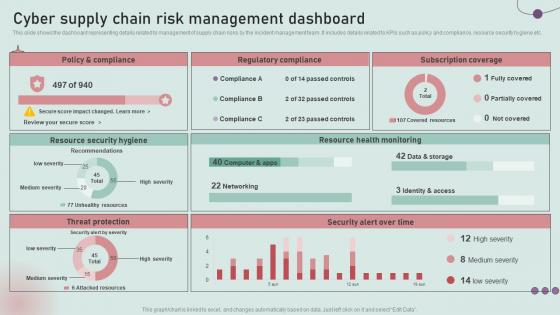 Cyber Supply Chain Risk Management Dashboard Development And Implementation Of Security Incident
Cyber Supply Chain Risk Management Dashboard Development And Implementation Of Security IncidentThis slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Deliver an outstanding presentation on the topic using this Cyber Supply Chain Risk Management Dashboard Development And Implementation Of Security Incident. Dispense information and present a thorough explanation of Regulatory Compliance, Subscription Coverage, Resource Health using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
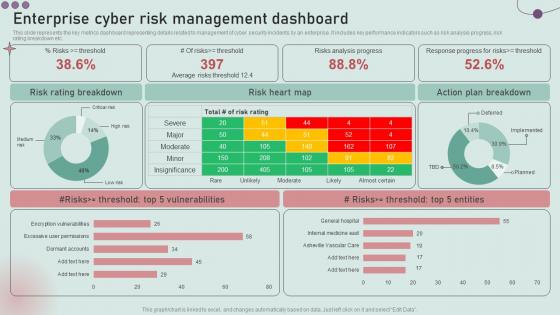 Enterprise Cyber Risk Management Dashboard Development And Implementation Of Security Incident
Enterprise Cyber Risk Management Dashboard Development And Implementation Of Security IncidentThis slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Present the topic in a bit more detail with this Enterprise Cyber Risk Management Dashboard Development And Implementation Of Security Incident. Use it as a tool for discussion and navigation on Risk Rating Breakdown, Risk Heart Map, Action Plan Breakdown. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 ICT Business Security KPI Dashboard Implementation Of ICT Strategic Plan Strategy SS
ICT Business Security KPI Dashboard Implementation Of ICT Strategic Plan Strategy SSThis slide represents ICT Information and Communication Technology business security dashboard to track threats and incidents. It covers details regarding issues by control type, risk categories, etc.Present the topic in a bit more detail with this ICT Business Security KPI Dashboard Implementation Of ICT Strategic Plan Strategy SS. Use it as a tool for discussion and navigation on Risk Categories, Control Review, Control Review Effectiveness. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SecOps Effective Implementation Impact On Security Breaches Ppt Elements
SecOps Effective Implementation Impact On Security Breaches Ppt ElementsThis slide outlines the successful implementation impact of SecOps on organizational security breaches. The purpose of this slide is to highlight the number of reduced security breaches inside a company after implementing SecOps. Security breaches include phishing, network intrusion, and so on. Present the topic in a bit more detail with this SecOps Effective Implementation Impact On Security Breaches Ppt Elements. Use it as a tool for discussion and navigation on Security Breaches, Implementing Secops System. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
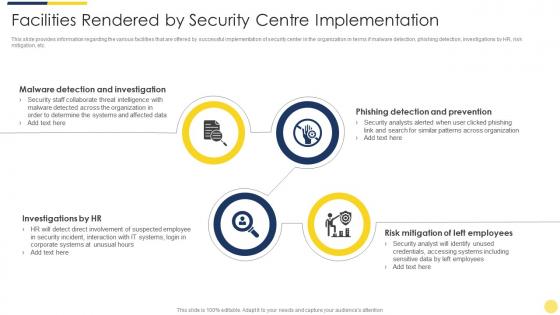 Facilities rendered by security centre implementation key initiatives for project safety it
Facilities rendered by security centre implementation key initiatives for project safety itThis slide provides information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Increase audience engagement and knowledge by dispensing information using Enabling Data Security Risk Management Action Plan Key Initiatives For Project Safety It. This template helps you present information on four stages. You can also present information on Determine, Organization, Data, Security, Organization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
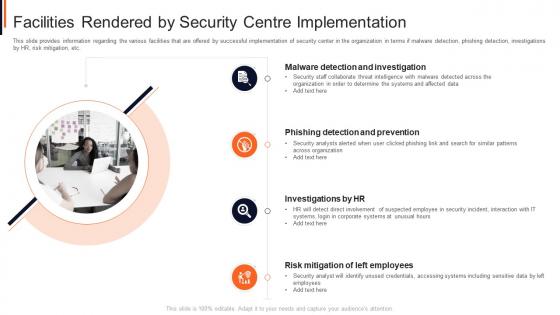 Facilities rendered by security centre implementation project safety management it
Facilities rendered by security centre implementation project safety management itThis slide provides information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Increase audience engagement and knowledge by dispensing information using Facilities Rendered By Security Centre Implementation Project Safety Management It. This template helps you present information on four stages. You can also present information on Analysts, Security, Organization, Data, Determine using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Electronic information security implementation strong password policy
Electronic information security implementation strong password policyThis slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Introducing Electronic Information Security Implementation Strong Password Policy to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Special Characters, Employees, Protected Accounts, using this template. Grab it now to reap its full benefits.
-
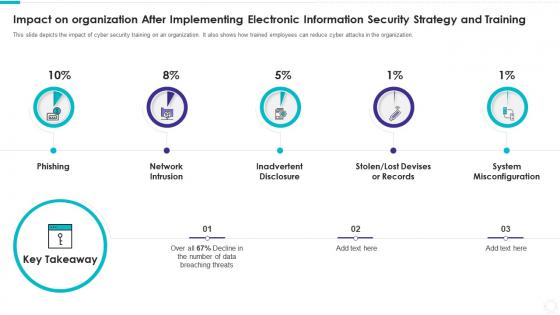 Impact on organization after implementing electronic information security strategy
Impact on organization after implementing electronic information security strategyThis slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Introducing Impact On Organization After Implementing Electronic Information Security Strategy to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Phishing, Network Intrusion, Inadvertent Disclosure, Stolen, Lost Devises Or Records, System Misconfiguration, using this template. Grab it now to reap its full benefits.
-
 Timeline for the implementation of electronic information security
Timeline for the implementation of electronic information securityThis slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an outstanding presentation on the topic using this Timeline For The Implementation Of Electronic Information Security. Dispense information and present a thorough explanation of Conduct Simulated Phishing Exercise, Change System, Network Passwords, Perform Third Party Vendor Risk Assessments using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Complete electronic information security implementation checklist
Complete electronic information security implementation checklistThis slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Increase audience engagement and knowledge by dispensing information using Complete Electronic Information Security Implementation Checklist. This template helps you present information on nine stages. You can also present information on Frequent Staff Training, Antivirus Software, Strong Passwords, Recovery Planning, Strong IT Policies, Device Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Implementing advanced analytics system at workplace contingency plan for threat handling security
Implementing advanced analytics system at workplace contingency plan for threat handling securityThis slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver an outstanding presentation on the topic using this Implementing Advanced Analytics System At Workplace Contingency Plan For Threat Handling Security. Dispense information and present a thorough explanation of Contingency Plan For Threat Handling In Security Centre using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implementing advanced analytics system at workplace determine role of security centre in firm
Implementing advanced analytics system at workplace determine role of security centre in firmThis slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security centre implementation. Present the topic in a bit more detail with this Implementing Advanced Analytics System At Workplace Determine Role Of Security Centre In Firm. Use it as a tool for discussion and navigation on Determine Role Of Security Centre In Firm. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing advanced analytics system at workplace enabling data security risk management action plan
Implementing advanced analytics system at workplace enabling data security risk management action planThe data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver an outstanding presentation on the topic using this Implementing Advanced Analytics System At Workplace Enabling Data Security Risk Management Action Plan. Dispense information and present a thorough explanation of Management, Resources, Enabling using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
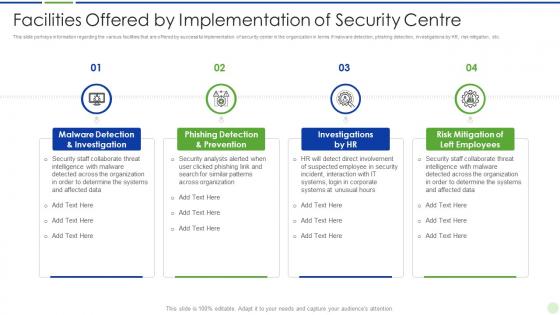 Implementing advanced analytics system at workplace facilities offered by implementation of security
Implementing advanced analytics system at workplace facilities offered by implementation of securityThis slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Deliver an outstanding presentation on the topic using this Implementing Advanced Analytics System At Workplace Facilities Offered By Implementation Of Security. Dispense information and present a thorough explanation of Implementation, Prevention, Investigation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implementing advanced analytics system at workplace overview established security centre
Implementing advanced analytics system at workplace overview established security centreThis slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Present the topic in a bit more detail with this Implementing Advanced Analytics System At Workplace Overview Established Security Centre. Use it as a tool for discussion and navigation on Business, Management, Steering. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing advanced analytics system at workplace timeframe for incident management in security centre
Implementing advanced analytics system at workplace timeframe for incident management in security centreThis slide provides information regarding entire duration of incident handling process which occur in various phases. Present the topic in a bit more detail with this Implementing Advanced Analytics System At Workplace Timeframe For Incident Management In Security Centre. Use it as a tool for discussion and navigation on Timeframe, Management, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implement traffic monitoring to secure redis server ppt portfolio information
Implement traffic monitoring to secure redis server ppt portfolio informationThis slide describes implementing traffic monitoring to check the usage patterns and raise flags to incase anything unusual happens. Introducing Implement Traffic Monitoring To Secure Redis Server Ppt Portfolio Information to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Implement Traffic Monitoring To Secure Redis Server, using this template. Grab it now to reap its full benefits.
-
 6 step process to implement data availability security
6 step process to implement data availability securityThis slide represents 6 step process to implement data availability security illustrating simplified recording, on-site maintenance and online security, training, record disposal and plan. Presenting our set of slides with 6 Step Process To Implement Data Availability Security. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Management, Implement, Organization.
-
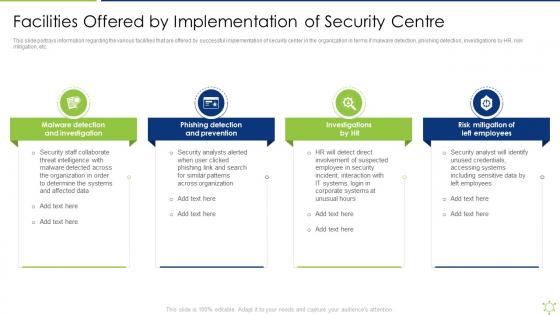 Facilities Offered By Implementation Of Security Centre Enabling It Intelligence Framework
Facilities Offered By Implementation Of Security Centre Enabling It Intelligence FrameworkThis slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc.Introducing Facilities Offered By Implementation Of Security Centre Enabling It Intelligence Framework to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Phishing Detection And Prevention, Risk Mitigation Of Left Employees, Malware Detection using this template. Grab it now to reap its full benefits.
-
 Cyberterrorism it roadmap to implement cyber security to mitigate cyber terrorism
Cyberterrorism it roadmap to implement cyber security to mitigate cyber terrorismThis slide depicts the roadmap to implement strategies to mitigate cyber terrorism such as training employees about cyber terrorism, creating personal accounts. Increase audience engagement and knowledge by dispensing information using Cyberterrorism IT Roadmap To Implement Cyber Security To Mitigate Cyber Terrorism. This template helps you present information on four stages. You can also present information on Creating Personal Accounts, Awareness Training Employees, Keep Hardware And Software Updated using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyberterrorism it timeline for implementation of cyber security in the company
Cyberterrorism it timeline for implementation of cyber security in the companyThis slide shows the timeframe for implementing a cyber security model in a business and the monthly activities that must be completed to fight cyber terrorism. Present the topic in a bit more detail with this Cyberterrorism IT Timeline For Implementation Of Cyber Security In The Company. Use it as a tool for discussion and navigation on Changes System, Network Passwords, Penetration Test. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Complete Information Security Implementation Checklist
Information Security Complete Information Security Implementation ChecklistThis slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Present the topic in a bit more detail with this Information Security Complete Information Security Implementation Checklist. Use it as a tool for discussion and navigation on Information, Security, Implementation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Implementation Of Strong Password Policy
Information Security Implementation Of Strong Password PolicyThis slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Present the topic in a bit more detail with this Information Security Implementation Of Strong Password Policy. Use it as a tool for discussion and navigation on Implementation Of Strong Password Policy. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Timeline For The Implementation Of Information Security
Information Security Timeline For The Implementation Of Information SecurityThis slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an outstanding presentation on the topic using this Information Security Timeline For The Implementation Of Information Security. Dispense information and present a thorough explanation of Timeline, Implementation, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Facilities Offered By Implementation Of Security Centre Building Business Analytics Architecture
Facilities Offered By Implementation Of Security Centre Building Business Analytics ArchitectureThis slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Introducing Facilities Offered By Implementation Of Security Centre Building Business Analytics Architecture to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Malware Detection And Investigation, Phishing Detection And Prevention, Investigations By HR, Risk Mitigation Of Left Employees, using this template. Grab it now to reap its full benefits.
-
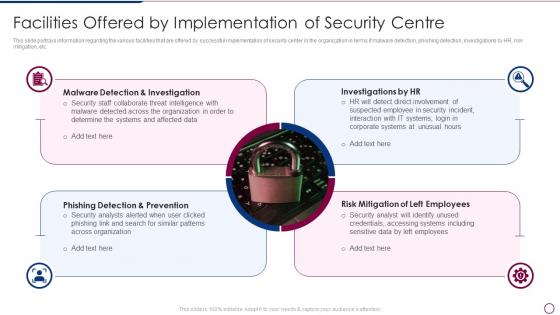 Unlocking Business Infrastructure Capabilities Facilities Offered By Implementation Of Security Centre
Unlocking Business Infrastructure Capabilities Facilities Offered By Implementation Of Security CentreThis slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Increase audience engagement and knowledge by dispensing information using Unlocking Business Infrastructure Capabilities Facilities Offered By Implementation Of Security Centre. This template helps you present information on four stages. You can also present information on Investigation, Implementation, Organization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
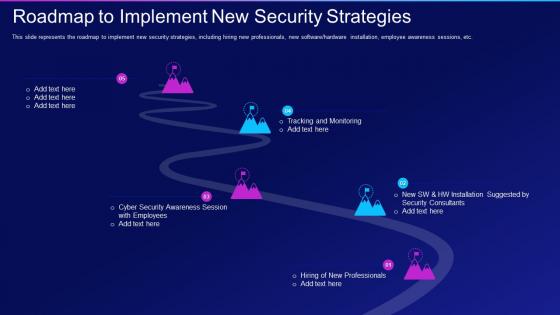 Hacking it roadmap to implement new security strategies
Hacking it roadmap to implement new security strategiesThis slide represents the roadmap to implement new security strategies, including hiring new professionals, new software or hardware installation, employee awareness sessions, etc. Increase audience engagement and knowledge by dispensing information using Hacking It Roadmap To Implement New Security Strategies. This template helps you present information on five stages. You can also present information on Roadmap To Implement New Security Strategies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security And Iso 27001 Communication Plan For Successful Implementation Of Isms
Information Security And Iso 27001 Communication Plan For Successful Implementation Of IsmsThis slide shows internal and external communication plan for successful implementation of ISMS. It includes sections namely reason for communication, initiator, recipient, frequency and medium. Present the topic in a bit more detail with this Information Security And Iso 27001 Communication Plan For Successful Implementation Of Isms. Use it as a tool for discussion and navigation on Successful, Implementation, Communication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Network Security Complete Network Security Implementation Checklist
Network Security Complete Network Security Implementation ChecklistThis slide depicts the network security checklist and measures an organization should take to protect data and company assets from network attacks or natural disasters. Introducing Network Security Complete Network Security Implementation Checklist to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Complete Network Security Implementation Checklist, using this template. Grab it now to reap its full benefits.
-
 Network Security Implementation Of Strong Password Policy
Network Security Implementation Of Strong Password PolicyThis slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Introducing Network Security Implementation Of Strong Password Policy to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Implementation Of Strong Password Policy, using this template. Grab it now to reap its full benefits.
-
 Network Security Timeline For The Implementation Of Network Security
Network Security Timeline For The Implementation Of Network SecurityThis slide shows the timeline for network security model implementation in an organization and the tasks to be performed every month. Present the topic in a bit more detail with this Network Security Timeline For The Implementation Of Network Security. Use it as a tool for discussion and navigation on Timeline For The Implementation Of Network Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementation Of Strong Password Policy Information Technology Security
Implementation Of Strong Password Policy Information Technology SecurityThis slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Introducing Implementation Of Strong Password Policy Information Technology Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Americans, Implementation, Passwords, using this template. Grab it now to reap its full benefits.
-
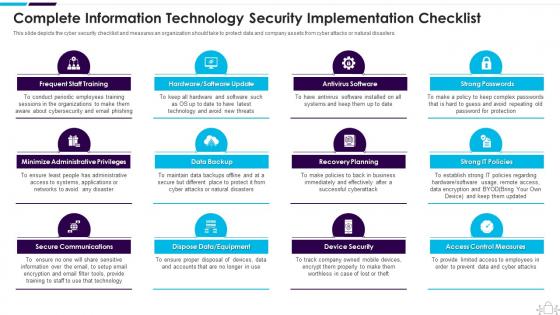 Information Technology Security Complete Information Security Implementation Checklist
Information Technology Security Complete Information Security Implementation ChecklistThis slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Introducing Information Technology Security Complete Information Security Implementation Checklist to increase your presentation threshold. Encompassed with twelve stages, this template is a great option to educate and entice your audience. Dispence information on Frequent Staff Training, Administrative Privileges, Data Backup, using this template. Grab it now to reap its full benefits.
-
 Timeline For The Implementation Of Information Technology Security
Timeline For The Implementation Of Information Technology SecurityThis slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an outstanding presentation on the topic using this Timeline For The Implementation Of Information Technology Security. Dispense information and present a thorough explanation of Implementation, Information, Technology using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implementation Add Roles And Enable Security Planning And Implementation Crm Software
Implementation Add Roles And Enable Security Planning And Implementation Crm SoftwareThis slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management. Present the topic in a bit more detail with this Implementation Add Roles And Enable Security Planning And Implementation Crm Software. Use it as a tool for discussion and navigation on Implementation Add Roles And Enable Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Planning And Implementation Of Crm Software Securing Our Data With Crm
Planning And Implementation Of Crm Software Securing Our Data With CrmThis slide highlights the CRM data security model which includes the user based, profile based, group based, record sharing and login based security. Deliver an outstanding presentation on the topic using this Planning And Implementation Of Crm Software Securing Our Data With Crm. Dispense information and present a thorough explanation of User Role Based Security, Profile Based Security, Record Sharing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Securing Our Data With Crm Planning And Implementation Of Crm Software
Securing Our Data With Crm Planning And Implementation Of Crm SoftwareThis slide highlights the data security using CRM which incorporates IP restriction, two factor authentication, data storage, communication protection and data security. Present the topic in a bit more detail with this Securing Our Data With Crm Planning And Implementation Of Crm Software. Use it as a tool for discussion and navigation on Securing Our Data With CRM. This template is free to edit as deemed fit for your organization. Therefore download it now.





