Powerpoint Templates and Google slides for Implement End To End Encryption
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Encryption Implementation Strategies Data Confidentiality Using End To End Encryption
Encryption Implementation Strategies Data Confidentiality Using End To End EncryptionThis slide illustrates the use of end-to-end encryption mechanism to maintain data confidentiality and secure digital ecosystems. The purpose of this slide is to demonstrate how data can be transformed into an encrypted format to transmit it over a network. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Data Confidentiality Using End To End Encryption. Dispense information and present a thorough explanation of Data Confidentiality, Encryption Mechanism, Demonstrate, Digital Ecosystems using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Public And Private Keys For End To End Encryption
Encryption Implementation Strategies Public And Private Keys For End To End EncryptionThis slide discusses the utilization of asymmetric public key encryption technique to provide E2EE. The purpose of this slide is to explain how client-side encryption employs public and private keys to encrypt the message before transmission. Present the topic in a bit more detail with this Encryption Implementation Strategies Public And Private Keys For End To End Encryption. Use it as a tool for discussion and navigation on Public And Private Keys, Encryption Employs, Encryption Technique, Server Transmitting And Storing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Five Step Process To Implement End To End Encryption
Five Step Process To Implement End To End EncryptionThis slide covers a 5-stage process for implementing end-to-end encryption. The purpose of this template is to provide a comprehensive roadmap for effectively working on end-to-end encryption, including defining requirements, selecting encryption algorithms, testing, deploying, and monitoring the solution.Introducing Five Step Process To Implement End To End Encryption to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Select Encryption Algorithms, Testing And Validation, using this template. Grab it now to reap its full benefits.
-
 Comparative Analysis Of End To End Encryption Tools Implementing Strategies For Mitigating Cybersecurity SS
Comparative Analysis Of End To End Encryption Tools Implementing Strategies For Mitigating Cybersecurity SSThis slide compares the best end-to-end encryption software solutions based on different parameters such as password management, on-the-fly decryption, and enterprise-grade decryption.Deliver an outstanding presentation on the topic using this Comparative Analysis Of End To End Encryption Tools Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Offers Support, Password Management, Enterprise Grade Decryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implementing End To End Encryption To Communication Channels Cybersecurity SS
Implementing End To End Encryption To Communication Channels Cybersecurity SSThis slide provides information about implementing end-to-end encryption E2EE to secure an organizations communication channels, including email communication, instant messaging, software and programs.Deliver an outstanding presentation on the topic using this Implementing End To End Encryption To Communication Channels Cybersecurity SS. Dispense information and present a thorough explanation of Communication Channels, Description, Impact using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
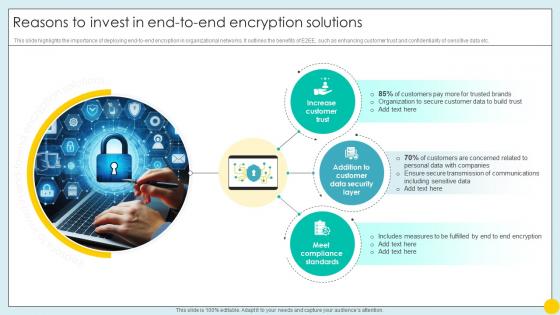 Reasons To Invest In End To End Encryption Solutions Implementing Strategies For Mitigating Cybersecurity SS
Reasons To Invest In End To End Encryption Solutions Implementing Strategies For Mitigating Cybersecurity SSThis slide highlights the importance of deploying end-to-end encryption in organizational networks. It outlines the benefits of E2EE, such as enhancing customer trust and confidentiality of sensitive data etc.Introducing Reasons To Invest In End To End Encryption Solutions Implementing Strategies For Mitigating Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Increase Customer Trust, Meet Compliance Standards, Customer Data Security Layer, using this template. Grab it now to reap its full benefits.
-
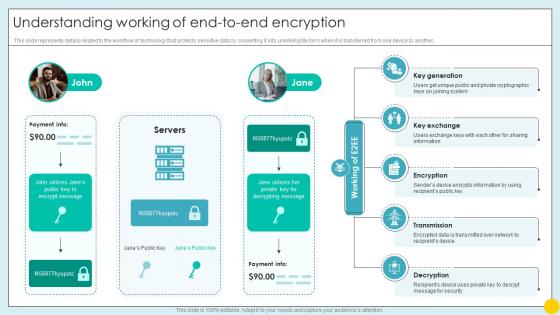 Understanding Working Of End To End Encryption Implementing Strategies For Mitigating Cybersecurity SS
Understanding Working Of End To End Encryption Implementing Strategies For Mitigating Cybersecurity SSThis slide represents details related to the workflow of technology that protects sensitive data by converting it into unintelligible form when it is transferred from one device to another. Increase audience engagement and knowledge by dispensing information using Understanding Working Of End To End Encryption Implementing Strategies For Mitigating Cybersecurity SS. This template helps you present information on five stages. You can also present information on Key Exchange, Encryption, Transmission, Decryption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Implement end to end encryption ppt powerpoint presentation gallery backgrounds cpb
Implement end to end encryption ppt powerpoint presentation gallery backgrounds cpbPresenting this set of slides with name Implement End To End Encryption Ppt Powerpoint Presentation Gallery Backgrounds Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Implement End To End Encryption to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.



