Powerpoint Templates and Google slides for Hardware
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Core Background Colourful Hardware Protection Circle
Core Background Colourful Hardware Protection CircleThis complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Core Background Colourful Hardware Protection Circle and has templates with professional background images and relevant content. This deck consists of total of twelve slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the colour, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.
-
 Web application firewall waf it hardware based web application firewall
Web application firewall waf it hardware based web application firewallThis slide depicts the hardware based web application firewall system, which is also known as on site WAF, and it is implemented on the LAN of the organization through a hardware device. Increase audience engagement and knowledge by dispensing information using Web Application Firewall Waf It Hardware Based Web Application Firewall. This template helps you present information on four stages. You can also present information on Businesses, Performance, Implemented using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Hardware Powerpoint Presentation Slides
Confidential Computing Hardware Powerpoint Presentation SlidesEnthrall your audience with this Confidential Computing Hardware Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising eighty three slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Confidential Computing Hardware Trusted Execution Environment Tee Hardware Platform
Confidential Computing Hardware Trusted Execution Environment Tee Hardware PlatformThis slide represents the trusted execution environment hardware platform used in confidential computing. The TEE environment is supported by three hardware platforms covering intel SGX, ARM trustZone, and advanced micro devices AMD. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Trusted Execution Environment Tee Hardware Platform. This template helps you present information on three stages. You can also present information on Protects Guest Memory, Provide Virtual Machine Isolation, Secure Memory Encryption, Encrypted State Technologies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Dimensioning The Hardware Infrastructure Strategies To Implement Cloud Computing Infrastructure
Dimensioning The Hardware Infrastructure Strategies To Implement Cloud Computing InfrastructureBelow slide demonstrates recommended configuration for cloud hardware infrastructure to smooth and uninterrupted operations. This consists of Hardware type, minimum and suggested requirements and remarks. Deliver an outstanding presentation on the topic using this Dimensioning The Hardware Infrastructure Strategies To Implement Cloud Computing Infrastructure. Dispense information and present a thorough explanation of Hardware, Infrastructure, Requirements using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Software And Hardware Product Distribution Channel Strategy
Software And Hardware Product Distribution Channel StrategyThis slide represents distribution channel strategy of software and hardware product. It further includes producers, distributors, retailers, dealers, and other methods of sales, etc Presenting our well structured Software And Hardware Product Distribution Channel Strategy. The topics discussed in this slide are Distributors, Producer.This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Global Bitcoin Mining Hardware Market Report With Incremental Growth
Global Bitcoin Mining Hardware Market Report With Incremental GrowthThis showcases report that can help in identifying future growth prediction of bitcoin mining hardware market and CAGR for next three years. It also outline top players available in market of bitcoin hardware. Introducing our Global Bitcoin Mining Hardware Market Report With Incremental Growth set of slides. The topics discussed in these slides are Bitcoin Hardware Market, Market Fragmented, Incremental Growth. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Confidential Computing Hardware Role Of Hardware In Confidential Computing Technology
Confidential Computing Hardware Role Of Hardware In Confidential Computing TechnologyThis slide outlines the role and requirement of hardware in confidential computing. The purpose of this slide is to showcase the various constraints issued by confidential computing consortium while choosing the hardware. Introducing Confidential Computing Hardware Role Of Hardware In Confidential Computing Technology to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Environment, Service Admins And Providers, Operating System, Device Driver, Peripheral Vendors, using this template. Grab it now to reap its full benefits.
-
 Digital ecosystem identify content software hardware network and services
Digital ecosystem identify content software hardware network and servicesPresenting this set of slides with name - Digital Ecosystem Identify Content Software Hardware Network And Services. This is a one stage process. The stages in this process are Digital Ecosystem, Knowledge Ecosystems, Natural Ecosystems.
-
 Hardware Trouble Shooting Best Practices
Hardware Trouble Shooting Best PracticesThis slide highlights various practices for trouble shooting a computer system to repair and restore software issues. It includes reboot, check connections. Look for program updates, clean hard drive and run antivirus programs. Introducing our Hardware Trouble Shooting Best Practices set of slides. The topics discussed in these slides are Reboot, Check Connections, Run Antivirus Program, Look Program Updates. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Hardware As A Challenge To Metaverse Training Ppt
Hardware As A Challenge To Metaverse Training PptPresenting Hardware as a Challenge to Metaverse. This slide is well crafted and designed by our PowerPoint specialists. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. You can add or delete the content as per your need.
-
 Hardware platform architecture example of ppt
Hardware platform architecture example of pptPresenting, our hardware platform architecture PPT. Use this presentation to give an insight into this 5 step process. Use this design for displaying your e-commerce business data through a PowerPoint presentation. You can download this enticing PPT template and take account of the full version of this slide which includes editing the text, changing the colors according to your liking. Use in both standard 4:3 and widescreen format 16:9 after downloading. Watermark gets removed after downloading, insert your company's logo and get slides in the widescreen version. Include your company information here in this predesigned PowerPoint format.
-
 Future Of Quantum Hardware Quantum Computation
Future Of Quantum Hardware Quantum ComputationThis slide depicts the quantum hardware in the future and how we will be able to build hardware that will operate on thousands of qubits simultaneously. Present the topic in a bit more detail with this Future Of Quantum Hardware Quantum Computation. Use it as a tool for discussion and navigation on Consistently, Techniques, Simultaneously. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Hardware Budget For Implementing Confidential Computing
Confidential Computing Hardware Budget For Implementing Confidential ComputingThis slide describes the implementation cost of confidential computing, including required tools, hardware and software costs, and other expenditures. The purpose of this slide is to showcase the estimated cost, actual cost and variance. Present the topic in a bit more detail with this Confidential Computing Hardware Budget For Implementing Confidential Computing. Use it as a tool for discussion and navigation on Cost Of Confidential Computing, Hardware And Software Costs, Estimated Cost, Actual Cost And Variance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Hardware Primary Approaches To Obtain Confidential Computing
Confidential Computing Hardware Primary Approaches To Obtain Confidential ComputingThis slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. Deliver an outstanding presentation on the topic using this Confidential Computing Hardware Primary Approaches To Obtain Confidential Computing. Dispense information and present a thorough explanation of Operating System, Hypervisor, Restrict Local Administrator, Cloud Administrator using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Hardware Technical Stack For Evaluating Confidential Computing
Confidential Computing Hardware Technical Stack For Evaluating Confidential ComputingThis slide depicts the technical stack while assessing confidential computing solutions. The stack divides these solutions into four levels, including application software vendors, infrastructure providers, hardware vendors, and cryptographic building blocks. Deliver an outstanding presentation on the topic using this Confidential Computing Hardware Technical Stack For Evaluating Confidential Computing. Dispense information and present a thorough explanation of Application Software Vendors, Infrastructure Providers, Hardware Vendors, Cryptographic Building Blocks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Project status meeting procure hardware evaluation recommendation sales team
Project status meeting procure hardware evaluation recommendation sales teamPresenting this set of slides with name - Project Status Meeting Procure Hardware Evaluation Recommendation Sales Team. This is an editable four stages graphic that deals with topics like Project Status Meeting, Procure Hardware, Evaluation Recommendation, Sales Team to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Roll out plan showing hardware service and user test
Roll out plan showing hardware service and user testPresenting this set of slides with name - Roll Out Plan Showing Hardware Service And User Test. This is a five stage process. The stages in this process are Roll Out Plan, Roll Out Strategies, Action Plan.
-
 Production applications purchase software purchase hardware install hardware
Production applications purchase software purchase hardware install hardwarePresenting this set of slides with name - Production Applications Purchase Software Purchase Hardware Install Hardware. This is an editable seven stages graphic that deals with topics like Production Applications, Purchase Software, Purchase Hardware, Install Hardware to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Software stack for hardware and user mode
Software stack for hardware and user modePresenting software stack for hardware and user mode. This is a software stack for hardware and user mode. This is a three stage process. The stages in this process are technology stack, software stack, software application.
-
 Deutero triple loop learning hardware setup hardware setup
Deutero triple loop learning hardware setup hardware setupPresenting this set of slides with name - Deutero Triple Loop Learning Hardware Setup Hardware Setup. This is an editable three graphic that deals with topics like deutero triple loop learning, hardware setup, hardware setup to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Confidential Computing Hardware Powerpoint Presentation Slides
Confidential Computing Hardware Powerpoint Presentation SlidesEnthrall your audience with this Confidential Computing Hardware Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising eighty three slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Hardware As A Challenge To Metaverse Training Ppt
Hardware As A Challenge To Metaverse Training PptPresenting Hardware as a Challenge to Metaverse. This slide is well crafted and designed by our PowerPoint specialists. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. You can add or delete the content as per your need.
-
 Hardware Wallets As One Of The Types Of Cryptocurrency Wallets Training Ppt
Hardware Wallets As One Of The Types Of Cryptocurrency Wallets Training PptPresenting Hardware Wallets as One of the Types of Cryptocurrency Wallets. Our PowerPoint experts have included all the necessary templates, designs, icons, graphs, and other essential material. This deck is well crafted by extensive research. Slides consist of amazing visuals and appropriate content. These PPT slides can be instantly downloaded with just a click. Compatible with all screen types and monitors. Supports Google Slides. Premium Customer Support is available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Core Background Colourful Hardware Protection Circle
Core Background Colourful Hardware Protection CircleThis complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Core Background Colourful Hardware Protection Circle and has templates with professional background images and relevant content. This deck consists of total of twelve slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the colour, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.
-
 Confidential Computing Adoption By Regulated Industries Confidential Computing Hardware
Confidential Computing Adoption By Regulated Industries Confidential Computing HardwareThis slide outlines the regulated industries leading the way in confidential computing adoption. The purpose of this slide is to demonstrate the adoption rate of confidential computing in regulated industries such as hi-tech, BSFI, HLS, public sector, retail and CPG, manufacturing and others. Present the topic in a bit more detail with this Confidential Computing Adoption By Regulated Industries Confidential Computing Hardware. Use it as a tool for discussion and navigation on Confidential Computing Adoption, Demonstrate The Adoption Rate, Public Sector, Retail And CPG. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Adoption In North America Confidential Computing Hardware
Confidential Computing Adoption In North America Confidential Computing HardwareThis slide represents the adoption rate of confidential computing in North America and ex-China. The purpose of this slide is to demonstrate the usage of confidential computing. The key growth drivers include the large market of North America, China and APAC, country-specific data privacy legislation, and the European market. Deliver an outstanding presentation on the topic using this Confidential Computing Adoption In North America Confidential Computing Hardware. Dispense information and present a thorough explanation of Adoption Rate, Confidential Computing, Demonstrate, Growth Drivers, Specific Data Privacy Legislation, European Market using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
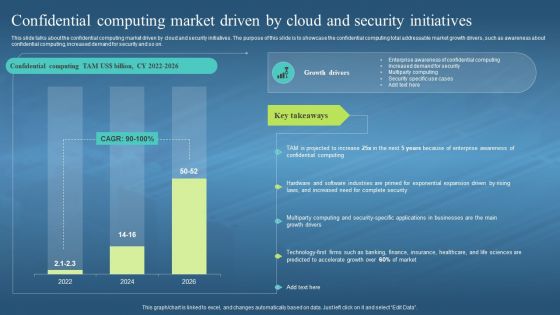 Confidential Computing Market Driven By Cloud And Security Confidential Computing Hardware
Confidential Computing Market Driven By Cloud And Security Confidential Computing HardwareThis slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. Deliver an outstanding presentation on the topic using this Confidential Computing Market Driven By Cloud And Security Confidential Computing Hardware. Dispense information and present a thorough explanation of Confidential Computing, Market Driven By Cloud, Security Initiatives, Awareness About Confidential Computing, Demand For Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Technology Segment Market Confidential Computing Hardware
Confidential Computing Technology Segment Market Confidential Computing HardwareThis slide depicts the technology segment market growth of confidential computing. The purpose of this slide is to showcase the confidential computing total addressable market by technology segment, and it caters to the segments such as services, software and hardware. Present the topic in a bit more detail with this Confidential Computing Technology Segment Market Confidential Computing Hardware. Use it as a tool for discussion and navigation on Technology Segment, Market Growth, Confidential Computing, Software And Hardware. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Total Addressable Market Confidential Computing Hardware
Confidential Computing Total Addressable Market Confidential Computing HardwareThis slide outlines the overview of the confidential computing total addressable market. The purpose of this slide is to demonstrate the best, median and worst-case scenarios of the TAM market for the next five years. In the best case scenario, the market is expected to increase by ninety-five percent by 2026. Present the topic in a bit more detail with this Confidential Computing Total Addressable Market Confidential Computing Hardware. Use it as a tool for discussion and navigation on Confidential Computing, Addressable Market, Demonstrate The Best, Cloud Computing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents Confidential Computing Hardware Ppt Icon File Formats
Table Of Contents Confidential Computing Hardware Ppt Icon File FormatsIncrease audience engagement and knowledge by dispensing information using Table Of Contents Confidential Computing Hardware Ppt Icon File Formats. This template helps you present information on six stages. You can also present information on Importance Of Confidential Computing, Confidential Computing Overview, Architecture, Working And Approaches Of Confidential Computing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Smart Agriculture Market Size By Hardware Improving Agricultural IoT SS
Smart Agriculture Market Size By Hardware Improving Agricultural IoT SSThe following slide displays graphical representation of IoT agriculture market size by hardware. Information covered in this slide is related to period from 2018 2025 along with Compound Annual Growth Rate CAGR. Present the topic in a bit more detail with this Smart Agriculture Market Size By Hardware Improving Agricultural IoT SS. Use it as a tool for discussion and navigation on Hardware Market, Smart Farming. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Storage Area Network San Hardware And Software Deployment Method Of Hci
Storage Area Network San Hardware And Software Deployment Method Of HciThis Slide Represents The Deployment Methods Of Hyper-Converged Infrastructure, Including Hardware And Software. The Purpose Of This Slide Is To Showcase The Comparison Between Hardware And Software HCI Deployment Based On Form, Intention, Applications, Benefits And Concerns. Deliver An Outstanding Presentation On The Topic Using This Storage Area Network San Hardware And Software Deployment Method Of Hci. Dispense Information And Present A Thorough Explanation Of Software, Deployment, Hardware Using The Slides Given. This Template Can Be Altered And Personalized To Fit Your Needs. It Is Also Available For Immediate Download. So Grab It Now.
-
 Confidential Computing Hardware Confidential Computing Performance Tracking Dashboard
Confidential Computing Hardware Confidential Computing Performance Tracking DashboardThis slide represents the performance tracking dashboard for confidential computing. The purpose of this slide is to represent the overall performance of the confidential computing cloud environment visually. The main components include overall health, operations, progress, time, cost and workloads. Deliver an outstanding presentation on the topic using this Confidential Computing Hardware Confidential Computing Performance Tracking Dashboard. Dispense information and present a thorough explanation of Performance Tracking Dashboard, Confidential Computing, Cloud Environment Visually, Cost And Workloads using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Banking Trend With Hardware And Software Support Services
Banking Trend With Hardware And Software Support ServicesThis slide showcase banking opportunity trend grown from FY2019 to FY2021 with software and hardware optimization in ATM and banking services. Introducing our Banking Trend With Hardware And Software Support Services set of slides. The topics discussed in these slides are Hardware, Banking, Services. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Edge Computing Technology Key Characteristics Of Edge Computing Hardware AI SS
Edge Computing Technology Key Characteristics Of Edge Computing Hardware AI SSThis slide showcases major characteristics of edge computing hardware, enabling developers and industrialists to use this technology in careful manner. It provides details about vent, fan, shock, temperature, small form, storage, etc. Increase audience engagement and knowledge by dispensing information using Edge Computing Technology Key Characteristics Of Edge Computing Hardware AI SS. This template helps you present information on five stages. You can also present information on Impervious To Sudden Movements, Equipped With Ample Storage, Fan Less And Ventless using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Global Market Overview Of Technology Hardware Digital Transformation In Education DT SS
Global Market Overview Of Technology Hardware Digital Transformation In Education DT SSThis slide provides glimpse about summary of global technology hardware in education sector for understanding its growing market and utilizing the opportunities. It includes CAGR, growth drivers, global players, etc. Deliver an outstanding presentation on the topic using this Global Market Overview Of Technology Hardware Digital Transformation In Education DT SS. Dispense information and present a thorough explanation of Global, Technology, Hardware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Global Hardware Encryption Market Analysis Encryption For Data Privacy In Digital Age It
Global Hardware Encryption Market Analysis Encryption For Data Privacy In Digital Age ItThis slide depicts the market analysis of the global hardware encryption usage. The purpose of this slide is to showcase the market analysis based on regions and applications such as commercial, residential, industrial and government agencies. Deliver an outstanding presentation on the topic using this Global Hardware Encryption Market Analysis Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Hardware, Encryption, Analysisusing the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Smart Agriculture Market Size By Hardware Smart Agriculture Using IoT System IoT SS V
Smart Agriculture Market Size By Hardware Smart Agriculture Using IoT System IoT SS VThe following slide displays graphical representation of IoT agriculture market size by hardware. Information covered in this slide is related to period from 2018-2025 along with Compound Annual Growth Rate CAGR. Deliver an outstanding presentation on the topic using this Smart Agriculture Market Size By Hardware Smart Agriculture Using IoT System IoT SS V. Dispense information and present a thorough explanation of Monitoring Devices, Market Size, Agriculture Market using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 It Hardware Market Size Overview
It Hardware Market Size OverviewThis slide showcases evaluating the competitive landscape reporting substantial growth in projected number of years with key insights to make informed decisions. Introducing our It Hardware Market Size Overview set of slides. The topics discussed in these slides are Increasing Digitalization, Cloud Computing, Reasons Behind Boost. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 3d Printing Hardware Market Global Overview Global 3d Printing Industry Outlook IR SS
3d Printing Hardware Market Global Overview Global 3d Printing Industry Outlook IR SSThe slide presents a comprehensive overview of the 3D printing hardware market in order to give stakeholders useful information that will help them make strategic decisions. The statistics for the global markets and the key growth drivers are covered in the slide indicating the potential for any new business, product, or service. Present the topic in a bit more detail with this 3d Printing Hardware Market Global Overview Global 3d Printing Industry Outlook IR SS. Use it as a tool for discussion and navigation on Rapid Industrialization, Electronic Devices, Rising Popularity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data security it hardware and software update in company
Data security it hardware and software update in companyThis slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. Introducing Data Security IT Hardware And Software Update In Company to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Peripheral Devices, Technology, Computers And Servers, using this template. Grab it now to reap its full benefits.
-
 Computer system security hardware and software update in company
Computer system security hardware and software update in companyThis slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. Introducing Computer System Security Hardware And Software Update In Company to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Technology, Security, Servers, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Market Role Of Hardware In Confidential Computing Technology
Confidential Computing Market Role Of Hardware In Confidential Computing TechnologyThis slide outlines the role and requirement of hardware in confidential computing. The purpose of this slide is to showcase the various constraints issued by confidential computing consortium while choosing the hardware. Increase audience engagement and knowledge by dispensing information using Confidential Computing Market Role Of Hardware In Confidential Computing Technology. This template helps you present information on five stages. You can also present information on Confidential, Computing, Technology using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Market Trusted Execution Environment Tee Hardware Platform
Confidential Computing Market Trusted Execution Environment Tee Hardware PlatformThis slide represents the trusted execution environment hardware platform used in confidential computing. The TEE environment is supported by three hardware platforms covering Intel SGX, ARM TrustZone, and Advanced Micro Devices AMD. Present the topic in a bit more detail with this Confidential Computing Market Trusted Execution Environment Tee Hardware Platform. Use it as a tool for discussion and navigation on Execution, Environment, Hardware Platform. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Essential World Hardware Decoding Digital Reality Of Physical World With Megaverse AI SS V
Essential World Hardware Decoding Digital Reality Of Physical World With Megaverse AI SS VThis slide provides information regarding essential components associated of metaverse world such as hardware. They are responsible for managing human interactivity in virtual space. The types of hardware components include head-mounted displays, motion input device, etc. Introducing Essential World Hardware Decoding Digital Reality Of Physical World With Megaverse AI SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Technological, Advancement, Improvement, using this template. Grab it now to reap its full benefits.
-
 Best Hardware Firewall Large Business In Powerpoint And Google Slides Cpb
Best Hardware Firewall Large Business In Powerpoint And Google Slides CpbPresenting Best Hardware Firewall Large Business In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Best Hardware Firewall Large Business. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Agenda Confidential Computing Hardware Ppt Ideas Infographic Template
Agenda Confidential Computing Hardware Ppt Ideas Infographic TemplateIntroducing Agenda Confidential Computing Hardware Ppt Ideas Infographic Template to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Consortium, Architecture, Confidential Computing, Hardware And Technologies, Computing Environment, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Architecture And Realms Working Confidential Computing Hardware
Confidential Computing Architecture And Realms Working Confidential Computing HardwareThis slide outlines the architecture of confidential computing and the working of realms. The purpose of this slide is to demonstrate the confidential computing architecture, including its components such as realm, applications, operating system, realm manager, hypervisor, and so on. Present the topic in a bit more detail with this Confidential Computing Architecture And Realms Working Confidential Computing Hardware. Use it as a tool for discussion and navigation on Architecture Of Confidential Computing, Working Of Realms, Demonstrate, Operating System, Realm Manager, Hypervisor. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Architecture Based On Azure Services Confidential Computing Hardware
Confidential Computing Architecture Based On Azure Services Confidential Computing HardwareThis slide represents the architecture of confidential computing based on Azure confidential computing services. The purpose of this slide is to showcase the problems with typical approaches and confidential computing solutions. It also includes the architecture components such as sensitive data, etc. Present the topic in a bit more detail with this Confidential Computing Architecture Based On Azure Services Confidential Computing Hardware. Use it as a tool for discussion and navigation on Architecture Of Confidential Computing, Azure Confidential Computing Services, Typical Approaches, Sensitive Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Architecture Implementation Roadmap Confidential Computing Hardware
Confidential Computing Architecture Implementation Roadmap Confidential Computing HardwareThis slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Introducing Confidential Computing Architecture Implementation Roadmap Confidential Computing Hardware to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Implementation Roadmap, Confidential Computing Architecture, Demonstrate, Deploy Confidential Computing, Cloud Environment, Existing Redis Database Unprotected, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Consortium Membership Levels Confidential Computing Hardware
Confidential Computing Consortium Membership Levels Confidential Computing HardwareThis slide represents the confidential computing consortium membership and participation levels. The purpose of this slide is to demonstrate the various partnership levels, annual fees, board seats, technical advisory committee seats, outreach committees, and notes. Deliver an outstanding presentation on the topic using this Confidential Computing Consortium Membership Levels Confidential Computing Hardware. Dispense information and present a thorough explanation of Confidential Computing, Consortium Membership, Participation Levels, Technical Advisory Committee Seats, Outreach Committees using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Hardware Ack Tee 2 0 Architecture And Workflow
Confidential Computing Hardware Ack Tee 2 0 Architecture And WorkflowThis slide outlines the architecture of Container Service for Kubernetes trusted execution environment version 2. The purpose of this slide is to demonstrate the features, date of launch and target users. It also covers the architecture and working of ACK TEE 2.0. Deliver an outstanding presentation on the topic using this Confidential Computing Hardware Ack Tee 2 0 Architecture And Workflow. Dispense information and present a thorough explanation of Architecture Of Container Service, Kubernetes Trusted, Execution Environment Version, Data Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Hardware Ack Tee Introduction And Version 1 0
Confidential Computing Hardware Ack Tee Introduction And Version 1 0This slide talks about the introduction of Container Service for Kubernetes trusted execution environment and its version 1.0. The purpose of this slide is to showcase its features, data of launch, objective and target users. It also includes the architecture and workflow of ACK TEE and its working. Present the topic in a bit more detail with this Confidential Computing Hardware Ack Tee Introduction And Version 1 0. Use it as a tool for discussion and navigation on Hardware Encryption Technology, Strict Security Needs, Delivering And Maintaining Trusted, Confidential Apps, Computing Technologies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Hardware Benefits Of Confidential Computing For Businesses
Confidential Computing Hardware Benefits Of Confidential Computing For BusinessesThis slide depicts the benefits of confidential computing for organizations, including protecting crucial data while processing, securing valuable intellectual resources, partnership with stakeholders to develop new cloud solutions, securing information processing at the edge and so on. Deliver an outstanding presentation on the topic using this Confidential Computing Hardware Benefits Of Confidential Computing For Businesses. Dispense information and present a thorough explanation of Confidential Computing For Organizations, Protecting Crucial Data, Securing Valuable Intellectual Resources, New Cloud Solutions using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
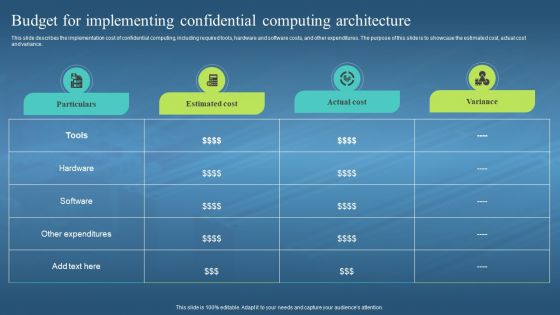 Confidential Computing Hardware Budget For Implementing Confidential Computing
Confidential Computing Hardware Budget For Implementing Confidential ComputingThis slide describes the implementation cost of confidential computing, including required tools, hardware and software costs, and other expenditures. The purpose of this slide is to showcase the estimated cost, actual cost and variance. Present the topic in a bit more detail with this Confidential Computing Hardware Budget For Implementing Confidential Computing. Use it as a tool for discussion and navigation on Cost Of Confidential Computing, Hardware And Software Costs, Estimated Cost, Actual Cost And Variance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Hardware Business Scenarios Of Confidential Computing Platform
Confidential Computing Hardware Business Scenarios Of Confidential Computing PlatformThis slide represents the business scenarios of confidential computing platform and it includes blockchain, key management, finance, artificial intelligence, multi-party computing, data leasing, and edge computing. Organizations can use confidential computing to secure their data while generating high economic value. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Business Scenarios Of Confidential Computing Platform. This template helps you present information on seven stages. You can also present information on Blockchain, Key Management, Finance, Edge Computing, Data Leasing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Hardware Case Study Irene Energy Ppt Icon Guidelines
Confidential Computing Hardware Case Study Irene Energy Ppt Icon GuidelinesThis slide talks about the case study carried out at Irene Energy organization. The purpose of this slide is to demonstrate how this corporation uses confidential computing technologies to provide electricity to remote American areas. The case study includes issues experienced, objectives, provided solutions and impact. Deliver an outstanding presentation on the topic using this Confidential Computing Hardware Case Study Irene Energy Ppt Icon Guidelines. Dispense information and present a thorough explanation of Irene Energy Organization, Demonstrate, Confidential Computing Technologies, Electricity To Remote American Areas, Electricity Roaming using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Hardware Checklist To Implement Confidential Computing
Confidential Computing Hardware Checklist To Implement Confidential ComputingThis slide depicts the checklist to implement confidential computing architecture in a cloud environment. The purpose of this slide is to showcase the various steps to be taken to deploy confidential computing, including its status and the responsible person. Present the topic in a bit more detail with this Confidential Computing Hardware Checklist To Implement Confidential Computing. Use it as a tool for discussion and navigation on Execute Within Confidential Cloud, Confidential Computing Architecture, Cloud Environment. Deploy Confidential Computing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Hardware Client Signature And Server Signature In Inclavare
Confidential Computing Hardware Client Signature And Server Signature In InclavareThis slide represents the client and server signature used in inclavare containers to protect sensitive applications and data. The purpose of this slide is to demonstrate the comparison between the client signature and the server signature and the benefits of the server signature. Deliver an outstanding presentation on the topic using this Confidential Computing Hardware Client Signature And Server Signature In Inclavare. Dispense information and present a thorough explanation of Client And Server Signature, Inclavare Containers, Protect Sensitive Applications, Demonstrate, Intel Business Certifications using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Hardware Companies Paving The Path For Confidential Computing
Confidential Computing Hardware Companies Paving The Path For Confidential ComputingThis slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc. Introducing Confidential Computing Hardware Companies Paving The Path For Confidential Computing to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Confidential Computing, Cloud Environments, Cloud Platform, Hardware And Software Solutions, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Hardware Critical Functions Of Confidential Computing Technology
Confidential Computing Hardware Critical Functions Of Confidential Computing TechnologyThis slide represents the critical functions of confidential computing. The purpose of this slide is to show the various features of confidential computing, such as popular and holistic data security model, data confidentiality, data integrity and code integrity. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Critical Functions Of Confidential Computing Technology. This template helps you present information on three stages. You can also present information on Data Confidentially, Data Integrity, Code Integrity, Confidential Computing Technology using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Hardware Financial Services And Healthcare Industry Scenario
Confidential Computing Hardware Financial Services And Healthcare Industry ScenarioThis slide represents the comparative analysis of financial services and healthcare industries based on different scenarios. The purpose of this slide is to demonstrate the different scenarios of financial services and healthcare industries. The different scenarios include best case, median case and worst case scenario. Introducing Confidential Computing Hardware Financial Services And Healthcare Industry Scenario to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Banking, Financial Services, Insurance Confidential Computing Market, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Hardware For Table Of Contents Ppt Icon Designs Download
Confidential Computing Hardware For Table Of Contents Ppt Icon Designs DownloadPresent the topic in a bit more detail with this Confidential Computing Hardware For Table Of Contents Ppt Icon Designs Download. Use it as a tool for discussion and navigation on Confidential Computing Market, Technology Segment Market Growth, Scenario Case Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Hardware Functional Comparison Of Different Tee Environments
Confidential Computing Hardware Functional Comparison Of Different Tee EnvironmentsThis slide talks about the functional comparison between different TEE environments available in the market. The purpose of this slide is to demonstrate the comparison and challenges with TEE environments. The main TEE environment provider includes Intel SGX, AMD SEV-ES, and IBM SE. Deliver an outstanding presentation on the topic using this Confidential Computing Hardware Functional Comparison Of Different Tee Environments. Dispense information and present a thorough explanation of Functional Comparison, Tee Environments, Restricted Parameters, Secure Execution Framework using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Hardware Future Of Confidential Computing Technology
Confidential Computing Hardware Future Of Confidential Computing TechnologyThis slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Future Of Confidential Computing Technology. This template helps you present information on five stages. You can also present information on Confidential Computing Technology, Demonstrate, Cloud Environment, Prerequisite For Commercial Sectors using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
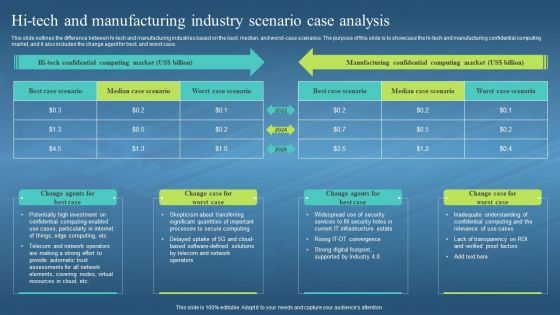 Confidential Computing Hardware HI Tech And Manufacturing Industry Scenario Case Analysis
Confidential Computing Hardware HI Tech And Manufacturing Industry Scenario Case AnalysisThis slide outlines the difference between hi-tech and manufacturing industries based on the best, median, and worst-case scenarios. The purpose of this slide is to showcase the hi-tech and manufacturing confidential computing market, and it also includes the change agent for best, and worst case. Introducing Confidential Computing Hardware HI Tech And Manufacturing Industry Scenario Case Analysis to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on HI Tech And Manufacturing Industries, Worst Case Scenarios, It Infrastructure Estate, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Hardware In And Out Scope Threat Vectors For Confidential Computing
Confidential Computing Hardware In And Out Scope Threat Vectors For Confidential ComputingThis slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware In And Out Scope Threat Vectors For Confidential Computing. This template helps you present information on four stages. You can also present information on Software Attacks, Protocol Attacks, Cryptographic Attacks, Physical Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Hardware Inclavare Confidential Containers Architecture In Tee
Confidential Computing Hardware Inclavare Confidential Containers Architecture In TeeThis slide represents the architecture of inclavare confidential containers in the TEE environment. The purpose of this slide is to showcase the various components and features of inclavare containers. The primary components include Kubelet, containerd, shim-rune, rune, PAL API, Pod and so on. Introducing Confidential Computing Hardware Inclavare Confidential Containers Architecture In Tee to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Architecture Of Inclavare, Confidential Containers, Tee Environment, Kubernetes Ecosystem, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Hardware Intel SGX With A Smaller Trusted Computing Base TCB
Confidential Computing Hardware Intel SGX With A Smaller Trusted Computing Base TCBThis slide describes the deployment of applications in Intel SGX with smaller TCB. The purpose of this slide is to showcase the difference between standard deployment and deployment in TEE. The main components include the operating system, virtual machine monitor, applications and hardware. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Intel SGX With A Smaller Trusted Computing Base TCB. This template helps you present information on two stages. You can also present information on Operating System, Virtual Machine Monitor, Hardware, Cloud Vendors using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Hardware Introduction To Confidential Computing Technology
Confidential Computing Hardware Introduction To Confidential Computing TechnologyThis slide represents the introduction to confidential computing, including its overview and objectives. Confidential computing is a cloud computing method to secure data while processing and gives business confidence to migrate their information and valuable assets to the cloud. Present the topic in a bit more detail with this Confidential Computing Hardware Introduction To Confidential Computing Technology. Use it as a tool for discussion and navigation on Confidential Computing, Cloud Computing Method, CPU Environment While Processing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Hardware Key Features Of Confidential Computing Platform
Confidential Computing Hardware Key Features Of Confidential Computing PlatformThis slide depicts the key features of confidential computing platform, including confidential virtual machines, confidential space, confidential dataproc, and confidential Google Kubernetes Engine node. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Key Features Of Confidential Computing Platform. This template helps you present information on four stages. You can also present information on Confidential Computing Platform, Confidential Virtual Machines, Confidential Space, Confidential Google Kubernetes Engine Node using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Hardware Multi Team Construction And Cooperation In Inclavare
Confidential Computing Hardware Multi Team Construction And Cooperation In InclavareThis slide outlines the architecture of multi-team construction and cooperation. The components of the architecture include occlum, graphene SGX, dragon well, customer enclave runtime, SGX-device-plugin, cloud Linux, shim-rune, and Kubernetes. Deliver an outstanding presentation on the topic using this Confidential Computing Hardware Multi Team Construction And Cooperation In Inclavare. Dispense information and present a thorough explanation of Efficient Multitasking, Multiple File System Support, Memory Safety, Cloud Container Service Team using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Hardware Multiparty Privacy Preserving Computation Architecture
Confidential Computing Hardware Multiparty Privacy Preserving Computation ArchitectureThis slide represents the overview of the architecture design of multiparty computing used in confidential computing. This slide aims to demonstrate the different attributes, benefits and technology options available such as blockchain with Azure virtual machine, blockchain as a service, and so on. Introducing Confidential Computing Hardware Multiparty Privacy Preserving Computation Architecture to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Architecture Design, Multiparty Computing, Confidential Computing, Blockchain With Azure Virtual Machine, Blockchain As A Service, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Hardware Need For Confidential Computing In Cloud Environment
Confidential Computing Hardware Need For Confidential Computing In Cloud EnvironmentThis slide depicts the need for confidential computing in a cloud environment and by showcasing the security concerns with early data processing system and confidential computing solutions to overcome those problems. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Need For Confidential Computing In Cloud Environment. This template helps you present information on six stages. You can also present information on Computing Memory, Competitors Or Cloud Providers, Memory Dump Attacks, Cloud Environment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Hardware Occlum System Architecture And Features
Confidential Computing Hardware Occlum System Architecture And FeaturesThis slide depicts the features and architecture of the Occlum system in confidential computing. The purpose of this slide is to showcase the features, architecture and process of the trusted and untrusted environment. The components include the build command, Occlum CLI tool, deployment environment, and so on. Introducing Confidential Computing Hardware Occlum System Architecture And Features to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Trusted Environment, Efficient Multi Process Support, Memory Security Guarantee, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Hardware Operational And Technical Assurance Of Data Privacy
Confidential Computing Hardware Operational And Technical Assurance Of Data PrivacyThis slide outlines the overview of operational and technical assurance of data privacy by demonstrating that technical assurance offers the highest degree of data protection and privacy. In technical assurance, cloud providers cannot tamper with user data. Present the topic in a bit more detail with this Confidential Computing Hardware Operational And Technical Assurance Of Data Privacy. Use it as a tool for discussion and navigation on Operational Assurance, Technical Assurance, Data Privacy, Integration And Continuous Deployment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Hardware Overview Of Confidential Computing Technologies
Confidential Computing Hardware Overview Of Confidential Computing TechnologiesThis slide talks about the technologies used in confidential computing, such as homomorphic encryption, trusted execution environment, secure multi-party computation, differential privacy, synthetic data, and federated learning. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Overview Of Confidential Computing Technologies. This template helps you present information on six stages. You can also present information on Homomorphic Encryption, Trusted Execution Environment, Federated Learning, Synthetic Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Hardware Primary Approaches To Obtain Confidential Computing
Confidential Computing Hardware Primary Approaches To Obtain Confidential ComputingThis slide describes the main methods to obtain confidential computing. The purpose of this slide is to showcase the two main ways of confidential computing, such as hardware and hypervisor. It also includes the components of confidential computing covering applications, operating systems, hypervisors, and hardware. Deliver an outstanding presentation on the topic using this Confidential Computing Hardware Primary Approaches To Obtain Confidential Computing. Dispense information and present a thorough explanation of Operating System, Hypervisor, Restrict Local Administrator, Cloud Administrator using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Hardware Process Of Using Intel SGX Based Trusted Applications
Confidential Computing Hardware Process Of Using Intel SGX Based Trusted ApplicationsThis slide outlines the process of using Intel SGX-based trusted applications. The purpose of this slide is to demonstrate the procedure of utilizing Intel SGX-based trusted applications. The main components include applying for a key, installing the environment, developing, computing and building, and executing. Introducing Confidential Computing Hardware Process Of Using Intel SGX Based Trusted Applications to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on SGX Based Trusted Applications, Installing The Environment, Developing, Computing And Building, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing Hardware Public And Retail And CPG Sector Scenario Case Analysis
Confidential Computing Hardware Public And Retail And CPG Sector Scenario Case AnalysisThis slide discusses the comparative analysis between the public, retail and consumer packaged goods sectors based on the best, median and worst-case scenarios. The purpose of this slide is to showcase the change agents for the best and worst-case scenarios of both sectors. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Public And Retail And CPG Sector Scenario Case Analysis. This template helps you present information on four stages. You can also present information on Restrictive Government Expenditure, Persisting Epidemic Impacts, Delayed Economic Recovery, Technologies Utilizing Public Funds using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.




