Powerpoint Templates and Google slides for Factor Authentication
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Multi Factor Authentication Powerpoint Ppt Template Bundles
Multi Factor Authentication Powerpoint Ppt Template BundlesDeliver a credible and compelling presentation by deploying this Multi Factor Authentication Powerpoint Ppt Template Bundles. Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The Twenty two slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Multi Factor Authentication Powerpoint Ppt Template Bundles PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.
-
 Multi Factor Authentication To Prevent Password Attacks Training Ppt
Multi Factor Authentication To Prevent Password Attacks Training PptPresenting Multi Factor Authentication to Prevent Password Attacks. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Multi factor authentication secure access process application server through
Multi factor authentication secure access process application server throughDeliver a lucid presentation by utilizing this Multi Factor Authentication Secure Access Process Application Server Through. Use it to present an overview of the topic with the right visuals, themes, shapes, and graphics. This is an expertly designed complete deck that reinforces positive thoughts and actions. Use it to provide visual cues to your audience and help them make informed decisions. A wide variety of discussion topics can be covered with this creative bundle such as Multi Factor Authentication, Secure, Access, Process, Application. All the twelve slides are available for immediate download and use. They can be edited and modified to add a personal touch to the presentation. This helps in creating a unique presentation every time. Not only that, with a host of editable features, this presentation can be used by any industry or business vertical depending on their needs and requirements. The compatibility with Google Slides is another feature to look out for in the PPT slideshow.
-
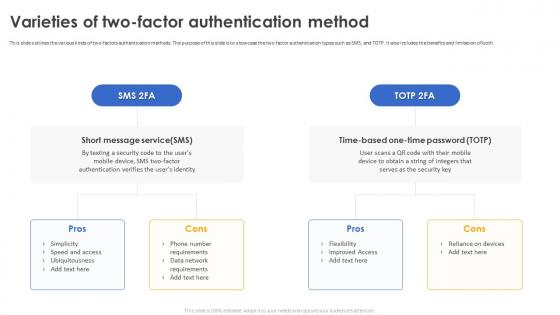 Secure Your Digital Assets Varieties Of Two Factor Authentication Method
Secure Your Digital Assets Varieties Of Two Factor Authentication MethodThis slide outlines the various kinds of two-factors authentication methods. The purpose of this slide is to showcase the two factor authentication types such as SMS, and TOTP. It also includes the benefits and limitation of both. Increase audience engagement and knowledge by dispensing information using Secure Your Digital Assets Varieties Of Two Factor Authentication Method. This template helps you present information on two stages. You can also present information on Phone Number Requirements, Data Network Requirements, Time Based One Time Password using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
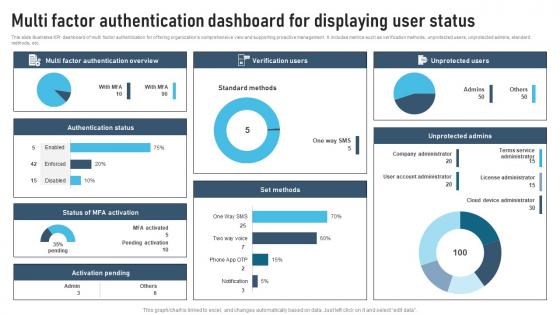 Multi Factor Authentication Dashboard For Displaying User Status
Multi Factor Authentication Dashboard For Displaying User StatusThis slide illustrates KPI dashboard of multi factor authentication for offering organizations comprehensive view and supporting proactive management. It includes metrics such as verification methods, unprotected users, unprotected admins, standard methods, etc. Introducing our Multi Factor Authentication Dashboard For Displaying User Status set of slides. The topics discussed in these slides are Overview, Status, Activation. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Multi Factor Authentication Global Market Dynamics Forecast
Multi Factor Authentication Global Market Dynamics ForecastThis slide illustrates multi factor authentication valuable tool for providing insights contributing to strategic planning, investment decisions, risk management and overall market trends. It includes basis such as growth drivers, opportunities available and key factors. Introducing our Multi Factor Authentication Global Market Dynamics Forecast set of slides. The topics discussed in these slides are Growth, Opportunities, Partnerships. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Multi Factor Dashboard For Adaptive Authentication Insights
Multi Factor Dashboard For Adaptive Authentication InsightsThis slide illustrates multi factor authentication KPI dashboard for serving visual interface to provide insights based on deployment and user status. It includes metrics such as registered devices, compliance status, device reset requests, device allocation, marked users, etc. Introducing our Multi Factor Dashboard For Adaptive Authentication Insights set of slides. The topics discussed in these slides are Communication, Allocation, Marked. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Two Factor Authentication Login Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Two Factor Authentication Login Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is perfect for making your presentation stand out. It features a login symbol in bright and vivid colours that will draw the attention of your audience. It is easy to use and can be resized to fit your needs. Get creative and make your presentation memorable with this powerpoint icon.
-
 Two Factor Authentication Login Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Two Factor Authentication Login Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMonotone Powerpoint Icon on Login is a high-quality vector icon designed to be used in presentations, websites, and other digital projects. It features a simple, minimalistic design with a monotone color palette, making it perfect for modern and professional designs.
-
 Comprehensive Guide To Understand Two Factor Authentication For Improved Security Fin SS
Comprehensive Guide To Understand Two Factor Authentication For Improved Security Fin SSThis slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Present the topic in a bit more detail with this Comprehensive Guide To Understand Two Factor Authentication For Improved Security Fin SS. Use it as a tool for discussion and navigation on Possession Verification, Biometric Verification, Enter Username And Password. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Two Factor Authentication Process Flow For Enhanced Security E Wallets As Emerging Payment Method Fin SS V
Two Factor Authentication Process Flow For Enhanced Security E Wallets As Emerging Payment Method Fin SS VThis slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Present the topic in a bit more detail with this Two Factor Authentication Process Flow For Enhanced Security E Wallets As Emerging Payment Method Fin SS V. Use it as a tool for discussion and navigation on Authentication, Process, Possession Verification. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tools Factor Authentication In Powerpoint And Google Slides Cpb
Tools Factor Authentication In Powerpoint And Google Slides CpbPresenting Tools Factor Authentication In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Tools Factor Authentication. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Adopt Two Factor Authentication To Reduce Hacking Hands On Blockchain Security Risk BCT SS V
Adopt Two Factor Authentication To Reduce Hacking Hands On Blockchain Security Risk BCT SS VThe following slide illustrates some tips and practices to ensure two factor authentication and safeguard blockchain network. It includes elements such as restricting unauthorized access, safeguarding personal keys, sending unique codes, extending user authentication, etc. Increase audience engagement and knowledge by dispensing information using Adopt Two Factor Authentication To Reduce Hacking Hands On Blockchain Security Risk BCT SS V. This template helps you present information on four stages. You can also present information on Restricts Unauthorized Access, Extends User Authentication, Safeguards Personal Key using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 NEO Banks For Digital Funds Two Factor Authentication Process Flow For Enhanced Security Fin SS V
NEO Banks For Digital Funds Two Factor Authentication Process Flow For Enhanced Security Fin SS VThis slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Deliver an outstanding presentation on the topic using this NEO Banks For Digital Funds Two Factor Authentication Process Flow For Enhanced Security Fin SS V. Dispense information and present a thorough explanation of Authentication Process Flow, Enhanced Security, Verify Biometrics, Authentication Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Blockchain And Cybersecurity Adopt Two Factor Authentication To Reduce Hacking BCT SS V
Blockchain And Cybersecurity Adopt Two Factor Authentication To Reduce Hacking BCT SS VThe following slide illustrates some tips and practices to ensure two factor authentication and safeguard blaockchain network. It includes elements such as restricting unauthorized access, safeguarding personal keys, sending unique codes, extending user authentication, etc. Introducing Blockchain And Cybersecurity Adopt Two Factor Authentication To Reduce Hacking BCT SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Restricts Unauthorized Access, Extends User Authentication, Sending Unique Codes using this template. Grab it now to reap its full benefits.
-
 Secure Your Digital Assets Overview And Working Of Two Factor Authentication
Secure Your Digital Assets Overview And Working Of Two Factor AuthenticationThis slide represents an overview and working of 2-factor authentication 2FA. The purpose of this slide is to outline a 2FA overview, how it works, and why we need 2FA. 2FA is a two-step verification for protection and security, it is user-friendly, etc. Deliver an outstanding presentation on the topic using this Secure Your Digital Assets Overview And Working Of Two Factor Authentication. Dispense information and present a thorough explanation of Phishing, Social Engineering, Password Brute Force Attacks, Prevents Attackers, Stolen Credentials using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Threats In Blockchain Adopt Two Factor Authentication To Reduce Hacking BCT SS V
Cyber Threats In Blockchain Adopt Two Factor Authentication To Reduce Hacking BCT SS VThe following slide illustrates some tips and practices to ensure two factor authentication and safeguard blaockchain network. It includes elements such as restricting unauthorized access, safeguarding personal keys, sending unique codes, extending user authentication, etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain Adopt Two Factor Authentication To Reduce Hacking BCT SS V This template helps you present information on Four stages. You can also present information on Restricts, Unauthorized Access, Extends User Authentication, Safeguards Personal Key using this PPT design. This layout is completely editable so personaize it now
-
 Crypto Wallets Types And Applications Factors And Need For Two Factor Authentication
Crypto Wallets Types And Applications Factors And Need For Two Factor AuthenticationThis slide represents the need and factors for two-factor authentication. The purpose of this slide is to outline the factors such as knowledge, inherence, time factor, etc. The need for 2FA to prevent unwanted access to the wallets each time a different code is provided serves as a powerful deterrent to protect money. Increase audience engagement and knowledge by dispensing information using Crypto Wallets Types And Applications Factors And Need For Two Factor Authentication. This template helps you present information on four stages. You can also present information on Two Factor Authentication, Online Risks, Knowledge, Inherence using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Crypto Wallets Types And Applications Overview And Working Of Two Factor Authentication
Crypto Wallets Types And Applications Overview And Working Of Two Factor AuthenticationThis slide represents an overview and working of 2-factor authentication2FA. The purpose of this slide is to outline a 2FA overview, how it works, and why we need 2FA. 2FA is a two-step verification for protection and security, it is user-friendly, etc. Increase audience engagement and knowledge by dispensing information using Crypto Wallets Types And Applications Overview And Working Of Two Factor Authentication. This template helps you present information on four stages. You can also present information on Phishing, Social Engineering, Password Brute Force Attacks, Stolen Credentials using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Crypto Wallets Types And Applications Risks Two Factor Authentication 2fa Mitigates
Crypto Wallets Types And Applications Risks Two Factor Authentication 2fa MitigatesThis slide discusses the risk that two-factor authentication has reduced. The purpose of this slide is to outline the risks being held off by 2FA, such as stolen passwords, social engineering, keylogging, phishing attempts, etc. Increase audience engagement and knowledge by dispensing information using Crypto Wallets Types And Applications Risks Two Factor Authentication 2fa Mitigates. This template helps you present information on six stages. You can also present information on Social Engineering, Stolen Passwords, Phishing Attempts, Risks Two Factor Authentication using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Implementing Byod Policy To Enhance Use Two Factor Authentication For Mitigating Risks
Implementing Byod Policy To Enhance Use Two Factor Authentication For Mitigating RisksThis slide shows major risks in BYOD policy that can be mitigated with the help of two factor authentication. It include various risks along with mechanism of overcoming it, etc. Introducing Implementing Byod Policy To Enhance Use Two Factor Authentication For Mitigating Risks to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Authentication For Mitigating Risks, Mechanism Of Overcoming, BYOD Policy, Stops Unauthorized Data, using this template. Grab it now to reap its full benefits.
-
 Everything About Mobile Banking Two Factor Authentication Process Flow For Enhanced Fin SS V
Everything About Mobile Banking Two Factor Authentication Process Flow For Enhanced Fin SS VThis slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Deliver an outstanding presentation on the topic using this Everything About Mobile Banking Two Factor Authentication Process Flow For Enhanced Fin SS V. Dispense information and present a thorough explanation of Biometric Verification, Possession Verification, Two Factor Authentication Process, Flow For Enhanced Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Factor Authentication Not Working In Powerpoint And Google Slides Cpb
Factor Authentication Not Working In Powerpoint And Google Slides CpbPresenting Factor Authentication Not Working In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Factor Authentication Not Working. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Two Factor Authentication Process Flow Smartphone Banking For Transferring Funds Digitally Fin SS V
Two Factor Authentication Process Flow Smartphone Banking For Transferring Funds Digitally Fin SS VThis slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Increase audience engagement and knowledge by dispensing information using Two Factor Authentication Process Flow Smartphone Banking For Transferring Funds Digitally Fin SS V. This template helps you present information on one stages. You can also present information on Biometric Verification, Possession Verification, Access Denied using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Banking Solutions For Improving Customer Two Factor Authentication Process Flow For Enhanced Fin SS V
Banking Solutions For Improving Customer Two Factor Authentication Process Flow For Enhanced Fin SS VThis slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Deliver an outstanding presentation on the topic using this Banking Solutions For Improving Customer Two Factor Authentication Process Flow For Enhanced Fin SS V. Dispense information and present a thorough explanation of Security Feature Works, Verify Biometrics Or Enter OTP, Possession Verification using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Compare Different Multi Factor Authentication Token For Risk Mitigation
Compare Different Multi Factor Authentication Token For Risk MitigationThis slide focuses on multi factor authentication tokens for enhancing security of user processes, reducing unauthorized risk with robust defense system. It includes basis such as growth drivers and opportunities available. Introducing our Compare Different Multi Factor Authentication Token For Risk Mitigation set of slides. The topics discussed in these slides are Security, Requirements, Technology. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Contributing Factors Affecting Multi Factor Authentication
Contributing Factors Affecting Multi Factor AuthenticationThis slide highlights multi factor authentication factors for effective implementation, balanced security requirements with user experience and organizational needs, it includes components such as knowledge, possession, inherence, time and location factor. Introducing our premium set of slides with Contributing Factors Affecting Multi Factor Authentication. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Knowledge, Possession, Location. So download instantly and tailor it with your information.
-
 Ensure Secure Access Icon Using Multi Factor Authentication Tool
Ensure Secure Access Icon Using Multi Factor Authentication ToolPresenting our set of slides with Ensure Secure Access Icon Using Multi Factor Authentication Tool. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Secure, Factor, Authentication.
-
 Identity Verification Icon Using Multi Factor Authentication
Identity Verification Icon Using Multi Factor AuthenticationIntroducing our premium set of slides with Identity Verification Icon Using Multi Factor Authentication. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Authentication, Verification, Using. So download instantly and tailor it with your information.
-
 Key Difference Between Two And Multi Factor Authentication
Key Difference Between Two And Multi Factor AuthenticationThis slide highlights contrasting variation between two and multi factor authentication depending on specific security needs and use cases of organization. It includes basis such as authentication criteria, security strength, implementation complexity, regulatory compliance, etc. Presenting our well structured Key Difference Between Two And Multi Factor Authentication. The topics discussed in this slide are Security, Complexity, Flexibility. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Mitigate Credential Risk Protection Icon Using Multi Factor Authentication
Mitigate Credential Risk Protection Icon Using Multi Factor AuthenticationIntroducing our premium set of slides with Mitigate Credential Risk Protection Icon Using Multi Factor Authentication. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Protection, Authentication, Credential. So download instantly and tailor it with your information.
-
 Multi Factor Authentication Architectural Framework By Using Azure
Multi Factor Authentication Architectural Framework By Using AzureThis slide showcases multi factor authentication framework for providing structured approach to deploy and manage cybersecurity threats by adaptable security strategy. It includes aspects such as remote desktop services infrastructure, azure multi factor authentication license, etc. Introducing our Multi Factor Authentication Architectural Framework By Using Azure set of slides. The topics discussed in these slides are Connected, Second, Validation. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Multi Factor Authentication Checklist For Quality Assurance Testing
Multi Factor Authentication Checklist For Quality Assurance TestingThis slide represents multi factor authentication checklist for addressing key aspects to strengthen security and protect against unauthorized access. It includes elements such as classification, statements, lead staff, checkpoints, status and remarks. Presenting our well structured Multi Factor Authentication Checklist For Quality Assurance Testing. The topics discussed in this slide are Quality, Testing, Assurance. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Multi Factor Authentication Flowchart For Online Banking
Multi Factor Authentication Flowchart For Online BankingThis slide demonstrates multi factor authentication for online banking to fortify, secure, protect user accounts and foster trust among customers. It includes basis such as onboarding and proof of identity, connecting and online verification. Presenting our well structured Multi Factor Authentication Flowchart For Online Banking. The topics discussed in this slide are Connecting, Verification, Result. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Multi Factor Authentication Methods For Analyzing User Behavior
Multi Factor Authentication Methods For Analyzing User BehaviorThis slide displays multi factor authentication methods based on security requirements, user preferences and system nature being protected. It includes aspects such as sms, email, hardware and software token authentication. Introducing our premium set of slides with Multi Factor Authentication Methods For Analyzing User Behavior. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Hardware, Software, Email. So download instantly and tailor it with your information.
-
 Multi Factor Authentication Solution Opportunities Available For Business
Multi Factor Authentication Solution Opportunities Available For BusinessThis slide represents multi factor authentication opportunities for enhancing cybersecurity, protecting user identities while balancing user experience and business continuity. It includes elements such as perimeter security, secure cloud applications, desktop services, etc. Presenting our set of slides with Multi Factor Authentication Solution Opportunities Available For Business. This exhibits information on nine stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security, Applications, Infrastructure.
-
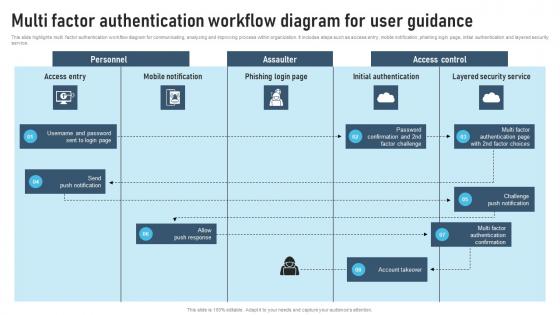 Multi Factor Authentication Workflow Diagram For User Guidance
Multi Factor Authentication Workflow Diagram For User GuidanceThis slide highlights multi factor authentication workflow diagram for communicating, analyzing and improving process within organization. It includes steps such as access entry, mobile notification, phishing login page, initial authentication and layered security service. Presenting our well structured Multi Factor Authentication Workflow Diagram For User Guidance. The topics discussed in this slide are Notification, Response, Account. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Prerequisites For Successful Multi Factor Authentication
Prerequisites For Successful Multi Factor AuthenticationThis slide represents multi factor authentication purpose for addressing username and password authentication by enhancing overall cybersecurity. It includes elements such as credential protection, reduced unauthorized access, user identity verification, adaptability, etc. Presenting our well structured Prerequisites For Successful Multi Factor Authentication. The topics discussed in this slide are Protection, Reduced, Verification. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Provide Adaptive Security Icon Based On Multi Factor Authentication
Provide Adaptive Security Icon Based On Multi Factor AuthenticationPresenting our set of slides with Provide Adaptive Security Icon Based On Multi Factor Authentication. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Adaptive, Factor, Security.
-
 Reinforce Multi Factor Authentication Security For Unauthorized Use
Reinforce Multi Factor Authentication Security For Unauthorized UseThis slide showcases multi factor authentication practices for mitigating common security risks associated with relying solely on passwords. It includes aspects such as detailed multi factor authentication plan, configurable authentication factors, forgotten password plans, etc. Introducing our premium set of slides with Reinforce Multi Factor Authentication Security For Unauthorized Use. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Authentication, Configurable, Compatibility. So download instantly and tailor it with your information.
-
 Safeguarding User Identity Using Multi Factor Authentication Tools
Safeguarding User Identity Using Multi Factor Authentication ToolsThis slide displays multi factor tools for enhancing authentication processes by requiring users to provide multiple forms of identification before granting access to system. It includes basis such as software tools, outline, pricing and rating. Introducing our Safeguarding User Identity Using Multi Factor Authentication Tools set of slides. The topics discussed in these slides are Identity, Tools, Safeguarding. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Setting Up Multi Factor Authentication Process For Microsoft 365
Setting Up Multi Factor Authentication Process For Microsoft 365This slide demonstrates multi factor authentication process for enhancing security of user accounts and protecting sensitive data within microsoft 365 environment. It includes steps such as multi factor authentication, decision makers, authentication form and new device. Introducing our premium set of slides with Setting Up Multi Factor Authentication Process For Microsoft 365. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Decision, Device, Register. So download instantly and tailor it with your information.
-
 Adopt Two Factor Authentication To Reduce Hacking Guide For Blockchain BCT SS V
Adopt Two Factor Authentication To Reduce Hacking Guide For Blockchain BCT SS VThe following slide illustrates some tips and practices to ensure two factor authentication and safeguard blaockchain network. It includes elements such as restricting unauthorized access, safeguarding personal keys, sending unique codes, extending user authentication, etc. Introducing Adopt Two Factor Authentication To Reduce Hacking Guide For Blockchain BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Unauthorized Access, User Authentication, Safeguards Personal using this template. Grab it now to reap its full benefits.
-
 Adopt Two Factor Authentication Securing Blockchain Transactions A Beginners Guide BCT SS V
Adopt Two Factor Authentication Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide illustrates some tips and practices to ensure two factor authentication and safeguard blaockchain network. It includes elements such as restricting unauthorized access, safeguarding personal keys, sending unique codes, extending user authentication, etc. Introducing Adopt Two Factor Authentication Securing Blockchain Transactions A Beginners Guide BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Restricts Unauthorized Access, Extends User Authentication, Safeguards Personal Key, using this template. Grab it now to reap its full benefits.
-
 Two Factor Authentication Process Flow For Digital Wallets For Making Hassle Fin SS V
Two Factor Authentication Process Flow For Digital Wallets For Making Hassle Fin SS VThis slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Deliver an outstanding presentation on the topic using this Two Factor Authentication Process Flow For Digital Wallets For Making Hassle Fin SS V. Dispense information and present a thorough explanation of Verification, Prompt, Possession using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Mobile Security Two Factor Authentication Process
Mobile Security Two Factor Authentication ProcessThis slide showcases roadmap for 2FA mobile security and includes assessment, select solutions, planning and integration, implementation, etc. Presenting our set of slides with name Mobile Security Two Factor Authentication Process. This exhibits information on Six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Assessment, Select Solution, Implementation, Testing And Optimization.
-
 Two Factor Authentication For Mobile Security Icon
Two Factor Authentication For Mobile Security IconIntroducing our premium set of slides with name Two Factor Authentication For Mobile Security Icon. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Two Factor Authentication, Mobile Security Icon. So download instantly and tailor it with your information.
-
 IAM Process For Effective Access IAM Multi Factor Authentication Tool And System
IAM Process For Effective Access IAM Multi Factor Authentication Tool And SystemThis slide discusses the multi-factor authentication tool and system for the Identity and Access Management process. The purpose of this slide is to explain the multi-factor authentication that uses multiple authentication factors for user access. Introducing IAM Process For Effective Access IAM Multi Factor Authentication Tool And System to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Multi Factor Authentication Tool, Access Management Process, Risk Of Credential Based Attacks, using this template. Grab it now to reap its full benefits.
-
 Authenticator Multi Factor Authentication In Powerpoint And Google Slides Cpp
Authenticator Multi Factor Authentication In Powerpoint And Google Slides CppPresenting Authenticator Multi Factor Authentication In Powerpoint And Google Slides Cpp slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Authenticator Multi Factor Authentication. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Mobile Banking Applications Two Factor Authentication Process Flow For Enhanced Fin SS V
Mobile Banking Applications Two Factor Authentication Process Flow For Enhanced Fin SS VThis slide shows flow chart which can be used to understand how two factor authentication security feature works. It includes steps such as enter username and password, verify biometrics or enter OTP, etc. Introducing Mobile Banking Applications Two Factor Authentication Process Flow For Enhanced Fin SS V to increase your presentation threshold. Encompassed with One stages, this template is a great option to educate and entice your audience. Dispence information on Biometric Verification, Access Granted, Access Denied, using this template. Grab it now to reap its full benefits.
-
 Benefits Of Using SMS In Two Factor Authentication Mobile Security
Benefits Of Using SMS In Two Factor Authentication Mobile SecurityThis slide represents the benefits of using SMS in two factor authentication in mobile security which includes security, speed and access and wide availability. Introducing Benefits Of Using SMS In Two Factor Authentication Mobile Security to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Security Policy, Mobile Security using this template. Grab it now to reap its full benefits.
-
 Common Threats Addressed By Two Factor Authentication Mobile Security
Common Threats Addressed By Two Factor Authentication Mobile SecurityThis slide discusses the common threats addressed by two factor authentication which includes stolen passwords, social engineering, key logging, etc. Increase audience engagement and knowledge by dispensing information using Common Threats Addressed By Two Factor Authentication Mobile Security This template helps you present information on Six stages. You can also present information on Sandbox Isolation, Robust Application using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key Factors Of Authentication In Mobile Security Mobile Security
Key Factors Of Authentication In Mobile Security Mobile SecurityThis slide highlights the key factors of authentication in mobile security which include knowledge factor, inherence factor, time factor and possession factor. Increase audience engagement and knowledge by dispensing information using Key Factors Of Authentication In Mobile Security Mobile Security This template helps you present information on Six stages. You can also present information on Security Broker, Email Security, Virtual Private Network using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Two Factor Authentication In Mobile Security Mobile Security
Two Factor Authentication In Mobile Security Mobile SecurityThis slide gives an overview of two factor authentication in mobile security and is defined as specific type of multi-factor authentication which strengthens access. Increase audience engagement and knowledge by dispensing information using Two Factor Authentication In Mobile Security Mobile Security This template helps you present information on Five stages. You can also present information on Spear Phishing, Voice Phishing, Credential Phishing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Types Of Two Factor Authentication In Mobile Security Mobile Security
Types Of Two Factor Authentication In Mobile Security Mobile SecurityThis slide discusses the types of two factor authentication in mobile security which includes SMS 2FA, push based 2FA, web authentication API and so on. Increase audience engagement and knowledge by dispensing information using Types Of Two Factor Authentication In Mobile Security Mobile Security This template helps you present information on Five stages. You can also present information on No Authentication, Hacker Access, Security Threats using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Two Factor Authentication To Enhance Chatbot Security
Two Factor Authentication To Enhance Chatbot SecurityThis slide shows a process that can be used to highlight how companies can use two-factor authentication to protect their chatbots against various security threats or vulnerabilities. It include three stages which are user enters credentials, OTP is sent to the user and user uses OTP to verify hi identity. Presenting our set of slides with Two Factor Authentication To Enhance Chatbot Security. This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Authentication Key, Username, Email.
-
 Single factor authentication pros cons ppt powerpoint presentation outline graphic tips cpb
Single factor authentication pros cons ppt powerpoint presentation outline graphic tips cpbPresenting Single Factor Authentication Pros Cons Ppt Powerpoint Presentation Outline Graphic Tips Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Single Factor Authentication Pros Cons. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Two factor authentication risk ppt powerpoint presentation infographic template cpb
Two factor authentication risk ppt powerpoint presentation infographic template cpbPresenting Two Factor Authentication Risk Ppt Powerpoint Presentation Infographic Template Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Two Factor Authentication Risk. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Multi factor authentication architecture ppt powerpoint presentation show grid cpb
Multi factor authentication architecture ppt powerpoint presentation show grid cpbPresenting our Multi Factor Authentication Architecture Ppt Powerpoint Presentation Show Grid Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Monetary Resources. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Factors Used Authentication Systems In Powerpoint And Google Slides Cpb
Factors Used Authentication Systems In Powerpoint And Google Slides CpbPresenting our Factors Used Authentication Systems In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Factors Used Authentication Systems This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.




