Powerpoint Templates and Google slides for Enterprise Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Enterprise Risk Management And Information Technology Security Table Of Contents
Enterprise Risk Management And Information Technology Security Table Of ContentsIncrease audience engagement and knowledge by dispensing information using Enterprise Risk Management And Information Technology Security Table Of Contents. This template helps you present information on one stages. You can also present information on Security Criteria, Control Measures, IT System Vulnerabilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Enterprise Risk Management Detection And Prevention Of Management Security Controls
Enterprise Risk Management Detection And Prevention Of Management Security ControlsThe following slide highlights the management security controls which includes preventive management security controls showcasing IT security polices and guidelines with detection management security controls. Increase audience engagement and knowledge by dispensing information using Enterprise Risk Management Detection And Prevention Of Management Security Controls. This template helps you present information on two stages. You can also present information on Preventive Management, Security Controls, Detection Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Enterprise Risk Management Financial Burden To Company From IT Security Breaches
Enterprise Risk Management Financial Burden To Company From IT Security BreachesThis slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Deliver an outstanding presentation on the topic using this Enterprise Risk Management Financial Burden To Company From IT Security Breaches. Dispense information and present a thorough explanation of Professional Services, Lost Business Opportunities, Total Damage using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enterprise Risk Management IT Security Residual Risk Matrix With Response Actions
Enterprise Risk Management IT Security Residual Risk Matrix With Response ActionsThis slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. Present the topic in a bit more detail with this Enterprise Risk Management IT Security Residual Risk Matrix With Response Actions. Use it as a tool for discussion and navigation on Control Topic, Evaluation Question, Response Action, Threat. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enterprise Risk Management Prioritized Cyber Security Threats With Risk Mitigation Plan
Enterprise Risk Management Prioritized Cyber Security Threats With Risk Mitigation PlanThis slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Present the topic in a bit more detail with this Enterprise Risk Management Prioritized Cyber Security Threats With Risk Mitigation Plan. Use it as a tool for discussion and navigation on Threat, Risk, Risk Priority, Risk Reduction Timeline. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enterprise Risk Management Security Criteria And Control Measures For IT System Vulnerabilities
Enterprise Risk Management Security Criteria And Control Measures For IT System VulnerabilitiesThis slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Introducing Enterprise Risk Management Security Criteria And Control Measures For IT System Vulnerabilities to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Management Security, Operational Security, Technical Security, using this template. Grab it now to reap its full benefits.
-
 Enterprise Risk Management Technical Security Control Model With Supporting Function
Enterprise Risk Management Technical Security Control Model With Supporting FunctionThe following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Introducing Enterprise Risk Management Technical Security Control Model With Supporting Function to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Identify, Cryptographic Administration, Security Management, System Protection, using this template. Grab it now to reap its full benefits.
-
 Icons Slide For Enterprise Risk Management And Information Technology Security
Icons Slide For Enterprise Risk Management And Information Technology SecurityIntroducing our well researched set of slides titled Icons Slide For Enterprise Risk Management And Information Technology Security. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Table Of Contents For Enterprise Risk Management And Information Technology Security
Table Of Contents For Enterprise Risk Management And Information Technology SecurityIntroducing Table Of Contents For Enterprise Risk Management And Information Technology Security to increase your presentation threshold. Encompassed with eleven stages, this template is a great option to educate and entice your audience. Dispence information on IT Risks, Threat Evaluation, IT Risk Management, Cost Estimation, using this template. Grab it now to reap its full benefits.
-
 Enterprise Architecture Security In Powerpoint And Google Slides Cpb
Enterprise Architecture Security In Powerpoint And Google Slides CpbPresenting Enterprise Architecture Security In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Enterprise Architecture Security. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Enterprise Network It Security Automation Enabling Automation In Cyber Security Operations
Enterprise Network It Security Automation Enabling Automation In Cyber Security OperationsThis slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps. Deliver an outstanding presentation on the topic using this Enterprise Network It Security Automation Enabling Automation In Cyber Security Operations. Dispense information and present a thorough explanation of Orchestrating Network Security, Troubleshooting, Integrating Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Addressing Mobile Device Management Approach Enterprise Mobile Security For On Device
Addressing Mobile Device Management Approach Enterprise Mobile Security For On DeviceThis slide provides information regarding different mobile device management approach such as container and platform approach that can be selected by vendor based on requirement. Introducing Addressing Mobile Device Management Approach Enterprise Mobile Security For On Device to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Critical Information, Ensuring Corporate, Legal Consideration, using this template. Grab it now to reap its full benefits.
-
 Addressing Mobile Device Management Model Enterprise Mobile Security For On Device
Addressing Mobile Device Management Model Enterprise Mobile Security For On DeviceThis slide provides information regarding various mobile device management models such as BYOD, COPE, COBO, COSU that can be selected by vendor based on requirement.Increase audience engagement and knowledge by dispensing information using Addressing Mobile Device Management Model Enterprise Mobile Security For On Device. This template helps you present information on four stages. You can also present information on Professional Purpose, Owned Personally, Permitted Tasks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Addressing Staff Training Schedule With Cost Enterprise Mobile Security For On Device
Addressing Staff Training Schedule With Cost Enterprise Mobile Security For On DeviceThe employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Present the topic in a bit more detail with this Addressing Staff Training Schedule With Cost Enterprise Mobile Security For On Device. Use it as a tool for discussion and navigation on Fundamentals Information, Coaching Sessions, Supplier Relationship. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Addressing Timeframe For Incident Management At Enterprise Mobile Security For On Device
Addressing Timeframe For Incident Management At Enterprise Mobile Security For On DeviceThis slide provides information regarding entire duration of incident handling process which occur in various phases.Introducing Addressing Timeframe For Incident Management At Enterprise Mobile Security For On Device to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Incident Categorization, Incident Prioritization, Incident Resolution, using this template. Grab it now to reap its full benefits.
-
 Analyzing Budget For Effective Mobile Device Enterprise Mobile Security For On Device
Analyzing Budget For Effective Mobile Device Enterprise Mobile Security For On DeviceFirm has prepared a budget for managing mobile device security by optimizing various functional areas. It also provides information about the software used and the duration required for implementation.Deliver an outstanding presentation on the topic using this Analyzing Budget For Effective Mobile Device Enterprise Mobile Security For On Device. Dispense information and present a thorough explanation of Risk Management, Document Management, Information Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 B132 Table Of Contents For Enterprise Mobile Security For On Device Threat Detection
B132 Table Of Contents For Enterprise Mobile Security For On Device Threat DetectionIntroducing B132 Table Of Contents For Enterprise Mobile Security For On Device Threat Detection to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Determine Standard, Various Configuration, Features Associated, using this template. Grab it now to reap its full benefits.
-
 Determine Incident Reporting By Mobile Devices In Enterprise Mobile Security For On Device
Determine Incident Reporting By Mobile Devices In Enterprise Mobile Security For On DeviceThis slide will help in providing an overview of the various reported incidents, average cost per incident and number of people involved in the various incidents across different IT departments. Present the topic in a bit more detail with this Determine Incident Reporting By Mobile Devices In Enterprise Mobile Security For On Device. Use it as a tool for discussion and navigation on Person Involved, Average Cost, Description. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Mobile Device Maintenance Checklist Enterprise Mobile Security For On Device
Determine Mobile Device Maintenance Checklist Enterprise Mobile Security For On DeviceThis slide provides information regarding mobile device maintenance checklist that is prepared, and essential activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver an outstanding presentation on the topic using this Determine Mobile Device Maintenance Checklist Enterprise Mobile Security For On Device. Dispense information and present a thorough explanation of Backup Monitoring, Preventive Maintenance, Virus Scanning using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine Various Configuration Profiles Using Enterprise Mobile Security For On Device
Determine Various Configuration Profiles Using Enterprise Mobile Security For On DeviceThis slide provides information regarding various configuration profiles using MDM technology such as basics, email accounts, internet and additional settings. Present the topic in a bit more detail with this Determine Various Configuration Profiles Using Enterprise Mobile Security For On Device. Use it as a tool for discussion and navigation on Internet Settings, Virtual Private, Access Point. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Various Mobile Device Management Enterprise Mobile Security For On Device
Determine Various Mobile Device Management Enterprise Mobile Security For On DeviceThis slide provides information regarding various mobile device management deployment methods such as device enrollment program, configurator, user initiated through URL that can be selected by vendor based on requirement. Deliver an outstanding presentation on the topic using this Determine Various Mobile Device Management Enterprise Mobile Security For On Device. Dispense information and present a thorough explanation of Device Enrollment, Configurator, Enrollment Through using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine Various Mobile Devices Existing At Workplace Enterprise Mobile Security For On Device
Determine Various Mobile Devices Existing At Workplace Enterprise Mobile Security For On DeviceThe employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Present the topic in a bit more detail with this Determine Various Mobile Devices Existing At Workplace Enterprise Mobile Security For On Device. Use it as a tool for discussion and navigation on Technology Allowed, Employees Request, Mixed Environment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determining Firm Current Capabilities In Devices Enterprise Mobile Security For On Device
Determining Firm Current Capabilities In Devices Enterprise Mobile Security For On DeviceThis slide portrays information regarding assessment of current mobile device security framework on certain standards. Deliver an outstanding presentation on the topic using this Determining Firm Current Capabilities In Devices Enterprise Mobile Security For On Device. Dispense information and present a thorough explanation of Safeguarding Critical, Infrastructure, Occurrence Identification using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determining Roles And Responsibilities For Risk Handling Enterprise Mobile Security For On Device
Determining Roles And Responsibilities For Risk Handling Enterprise Mobile Security For On DeviceThis slide provides information regarding the roles and responsibilities of management in handling mobile device security risks. Key people involved in risk handling are chief risk officer, chief information security officer, senior management and executives and line managers. Increase audience engagement and knowledge by dispensing information using Determining Roles And Responsibilities For Risk Handling Enterprise Mobile Security For On Device. This template helps you present information on five stages. You can also present information on Security Program, Information Resources, Management Activities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Effective Mobile Device Security Management Enterprise Mobile Security For On Device
Effective Mobile Device Security Management Enterprise Mobile Security For On DeviceThis slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events associated to mobile device. Present the topic in a bit more detail with this Effective Mobile Device Security Management Enterprise Mobile Security For On Device. Use it as a tool for discussion and navigation on Incidents Damaging, Access Violations, Security Incidents. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ensuring Mobile Device Compliance Enforcement Enterprise Mobile Security For On Device
Ensuring Mobile Device Compliance Enforcement Enterprise Mobile Security For On DeviceThis slide provides information regarding mobile device compliance and policy enforcement with automated device setup, dynamic workflows and policies, etc.Present the topic in a bit more detail with this Ensuring Mobile Device Compliance Enforcement Enterprise Mobile Security For On Device. Use it as a tool for discussion and navigation on Automated Device, Corporate Policies, Essential Business. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Icons Slide For Enterprise Mobile Security For On Device Threat Detection
Icons Slide For Enterprise Mobile Security For On Device Threat DetectionPresenting our well crafted Icons Slide For Enterprise Mobile Security For On Device Threat Detection set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly
-
 Implementing Mobile Device Security Roadmap Enterprise Mobile Security For On Device
Implementing Mobile Device Security Roadmap Enterprise Mobile Security For On DeviceThis slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Present the topic in a bit more detail with this Implementing Mobile Device Security Roadmap Enterprise Mobile Security For On Device. Use it as a tool for discussion and navigation on Risk Management, Implement Security, Control Environment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Steps Involved In Mobile Device Deployment Enterprise Mobile Security For On Device
Key Steps Involved In Mobile Device Deployment Enterprise Mobile Security For On DeviceThis slide provides information regarding key steps involved in deploying mobile device management system.Increase audience engagement and knowledge by dispensing information using Key Steps Involved In Mobile Device Deployment Enterprise Mobile Security For On Device. This template helps you present information on four stages. You can also present information on Associated Device, Profile Configuration, Device Purchase using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Mobile Device Management Action Plan Enterprise Mobile Security For On Device
Mobile Device Management Action Plan Enterprise Mobile Security For On DeviceThe risk management action plan will help in keeping the track of various potential risks that are existing in the firm in context to mobile device management. The person responsible in handling the risk will keep track of the duration in which risk is resolved.Deliver an outstanding presentation on the topic using this Mobile Device Management Action Plan Enterprise Mobile Security For On Device. Dispense information and present a thorough explanation of Implement Receivables, Develop Implement, Compliance Monitoring using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Mobile Device Management Employees Enterprise Mobile Security For On Device
Mobile Device Management Employees Enterprise Mobile Security For On DeviceThis slide provides information regarding mobile device management technology assistance to employees and to IT department associated to firm.Increase audience engagement and knowledge by dispensing information using Mobile Device Management Employees Enterprise Mobile Security For On Device. This template helps you present information on one stage. You can also present information on Business Processes, Enforce Security, Rendering Appropriate using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Mobile Device Management For Android Platform Enterprise Mobile Security For On Device
Mobile Device Management For Android Platform Enterprise Mobile Security For On DeviceThis slide provides information regarding mobile device management for android platform with device settings policy, device security settings, etc. Present the topic in a bit more detail with this Mobile Device Management For Android Platform Enterprise Mobile Security For On Device. Use it as a tool for discussion and navigation on Device Security, Theft Protection, Remote Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Mobile Device Management For IOS Platform Enterprise Mobile Security For On Device
Mobile Device Management For IOS Platform Enterprise Mobile Security For On DeviceThis slide provides information regarding mobile device management for iOS platform with device enrollment program, anti theft protection, etc.Deliver an outstanding presentation on the topic using this Mobile Device Management For IOS Platform Enterprise Mobile Security For On Device. Dispense information and present a thorough explanation of Enrollment Program, Remote Management, Managing Notifications using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Role Of Management In Effective Enterprise Mobile Security For On Device
Role Of Management In Effective Enterprise Mobile Security For On DeviceThis slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief information security office in order to ensure the effective information security governance. Present the topic in a bit more detail with this Role Of Management In Effective Enterprise Mobile Security For On Device. Use it as a tool for discussion and navigation on Strategic Alignment, Integrate Business, Impact Assessments. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Selecting Suitable Mobile Device Management Solutions Enterprise Mobile Security For On Device
Selecting Suitable Mobile Device Management Solutions Enterprise Mobile Security For On DeviceThis slide provides information regarding selection of suitable mobile device management solution with various features such as user self registration, remote lock, remote wipe, mobile experience management. Deliver an outstanding presentation on the topic using this Selecting Suitable Mobile Device Management Solutions Enterprise Mobile Security For On Device. Dispense information and present a thorough explanation of Experience Management, Self Registration, Remote Wipe using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents For Enterprise Mobile Security For On Device Threat Detection
Table Of Contents For Enterprise Mobile Security For On Device Threat DetectionPresent the topic in a bit more detail with this Table Of Contents For Enterprise Mobile Security For On Device Threat Detection. Use it as a tool for discussion and navigation on Impact Assessment, Dashboard Assessment, Device Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enterprise Network It Security Automation Security Automation To Investigate And Remediate Cyberthreats
Enterprise Network It Security Automation Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps. Increase audience engagement and knowledge by dispensing information using Enterprise Network It Security Automation Security Automation To Investigate And Remediate Cyberthreats. This template helps you present information on six stages. You can also present information on Automation, Security Infrastructure, Troubleshooting using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Enterprise Network It Security Automation Security Automation In Information Technology
Enterprise Network It Security Automation Security Automation In Information TechnologyThis slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps. Increase audience engagement and knowledge by dispensing information using Enterprise Network It Security Automation Security Automation In Information Technology. This template helps you present information on six stages. You can also present information on Orchestrating Network Security, Security Policy Automation, Infrastructure using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Enterprise Data Warehouse Framework To Ensure Data Security
Enterprise Data Warehouse Framework To Ensure Data SecurityThis slide covers enterprise data warehouse framework to ensure data security. It involves four steps such as data extraction, cleaning, conversion and storing of data. Presenting our well structured Enterprise Data Warehouse Framework To Ensure Data Security. The topics discussed in this slide are Extraction Of Data, Cleaning Of Data, Conversion Of Data. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Enterprise Data Warehouse To Ensure Security Icon
Enterprise Data Warehouse To Ensure Security IconPresenting our set of slides with Enterprise Data Warehouse To Ensure Security Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Enterprise Data Warehouse, Ensure Security Icon.
-
 Addressing Mobile Device Management Model For Enterprise Unified Endpoint Security
Addressing Mobile Device Management Model For Enterprise Unified Endpoint SecurityThis slide provides information regarding various mobile device management models such as BYOD, COPE, COBO, COSU that can be selected by vendor based on requirement. Increase audience engagement and knowledge by dispensing information using Addressing Mobile Device Management Model For Enterprise Unified Endpoint Security. This template helps you present information on four stages. You can also present information on Equipment Personal, Devices Professional, Employees Personal using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
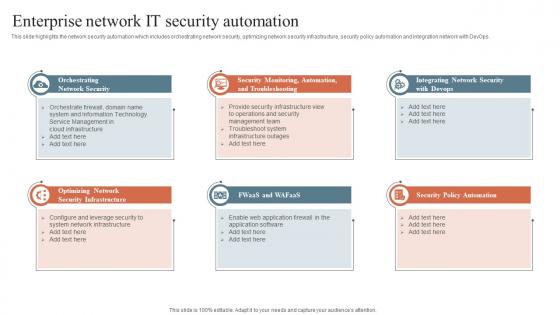 Enterprise Network It Security Automation Security Orchestration Automation And Response Guide
Enterprise Network It Security Automation Security Orchestration Automation And Response GuideThis slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps. Introducing Enterprise Network It Security Automation Security Orchestration Automation And Response Guide to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Network Security, Security Infrastructure, Security Policy Automation, using this template. Grab it now to reap its full benefits.
-
 Enterprise Risk Management Plan For Cyber Security
Enterprise Risk Management Plan For Cyber SecurityThis slide displays the steps that helps to stay away from the threats of cyber security and makes clients feel safe from the cyber attacks. The steps includes Identifying digital assets, audit data, perform assessments, analyze risk level, establish committee, etc. Presenting our set of slides with name Enterprise Risk Management Plan For Cyber Security. This exhibits information on eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify Digital, Perform Risk, Establish Risk.
-
 Automated Enterprise Security Operation Icon
Automated Enterprise Security Operation IconPresenting our set of slides with Automated Enterprise Security Operation Icon. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Automated Enterprise, Security Operation Icon.
-
 Comparison Assessment Of Enterprise Security Operations Tools
Comparison Assessment Of Enterprise Security Operations ToolsThis slide covers comparison assessment of enterprise security operations tools. It involves features such as vulnerability management, penetration testing and privacy standard compliance. Introducing our Comparison Assessment Of Enterprise Security Operations Tools set of slides. The topics discussed in these slides are Features, Cost Involved, User Rating. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Enterprise Cyber Security Operation Icon
Enterprise Cyber Security Operation IconIntroducing our premium set of slides with Enterprise Cyber Security Operation Icon. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Enterprise Cyber Security, Operation Icon. So download instantly and tailor it with your information.
-
 Enterprise Data Security Operation Center System
Enterprise Data Security Operation Center SystemThis slide covers enterprise data security operation center system to ensure better safety. It involves six stages collection, transmission, storage, processing, exchange and destruction. Presenting our set of slides with Enterprise Data Security Operation Center System. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Collection, Transmission, Processing .
-
 Enterprise Security Operation Center Audit Checklist
Enterprise Security Operation Center Audit ChecklistThis slide covers enterprise security operation center audit checklist. It involves vulnerability scan, employee cyber training, security provisions, asset management policy and network segmentation procedures. Introducing our Enterprise Security Operation Center Audit Checklist set of slides. The topics discussed in these slides are Employee Cyber Training Guide, Vulnerability Scan And Analysis, Incident Response Policy. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Enterprise Security Operation Center Best Practices
Enterprise Security Operation Center Best PracticesThis slide covers enterprise security operation center best practices. It involves practices such as setting up right time, align strategy with business goals, leverage best tools and continuously monitor network. Presenting our well structured Enterprise Security Operation Center Best Practices. The topics discussed in this slide are Leverage Best Tools, Continuously Monitor Network, Business Goals. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Enterprise Security Operation Center Icon
Enterprise Security Operation Center IconIntroducing our premium set of slides with Enterprise Security Operation Center Icon. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Enterprise Security Operation, Center Icon. So download instantly and tailor it with your information.
-
 Enterprise Security Operation Center Process
Enterprise Security Operation Center ProcessThis slide covers enterprise security operation center process. It involves monitoring, basic investigation, mitigation, threat hunting, counter intelligence and advanced investigations. Introducing our Enterprise Security Operation Center Process set of slides. The topics discussed in these slides are Security Intelligence Platform, Help Desks, Monitoring. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Enterprise Security Operation Center System
Enterprise Security Operation Center SystemThis slide covers enterprise security operation center system. It involves business security, data security, infrastructure, office network and application security. Presenting our well structured Enterprise Security Operation Center System. The topics discussed in this slide are Business Security, Data Security, Application Security. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Enterprise Security Operation Center Team Roles And Responsibilities
Enterprise Security Operation Center Team Roles And ResponsibilitiesThis slide covers enterprise security operation center team roles and responsibilities. It involves key roles such as incident responder, security investigator, advanced security analyst and SOC manager. Introducing our Enterprise Security Operation Center Team Roles And Responsibilities set of slides. The topics discussed in these slides are Security Investigator, Incident Responder, Advanced Security Analyst. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Enterprise Security Operation Center To Enhance Safety
Enterprise Security Operation Center To Enhance SafetyThis slide covers enterprise security operation center to enhance safety. It involves log collection, reporting, research and development, threat intelligence and aggregation. Presenting our set of slides with Enterprise Security Operation Center To Enhance Safety. This exhibits information on eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Knowledge Base, Ticketing, Log Collection.
-
 Enterprise Security Operation Model To Build Secure Organization
Enterprise Security Operation Model To Build Secure OrganizationThis slide covers enterprise security operation model to build secure organization. It involves regulatory requirements, customer expectations, industry forums and internal business demands. Introducing our premium set of slides with Enterprise Security Operation Model To Build Secure Organization. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Regulatory Requirements, Customer Expectations, Industry Norms. So download instantly and tailor it with your information.
-
 Enterprise Security Operation System Icon
Enterprise Security Operation System IconPresenting our set of slides with Enterprise Security Operation System Icon. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Enterprise Security Operation, System Icon.
-
 Enterprise Security Operations Center Framework
Enterprise Security Operations Center FrameworkThis slide covers enterprise security operations center framework. It involves five stages such as discovery, preliminary investigation, triage, extended investigation and respond. Introducing our premium set of slides with Enterprise Security Operations Center Framework. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Preliminary Investigation, Extended Investigation, Triage. So download instantly and tailor it with your information.
-
 Evolution Of Enterprise Security Operation Center
Evolution Of Enterprise Security Operation CenterThis slide covers evolution of enterprise security operation center. It involves availability monitoring, reactive monitoring, proactive monitoring and monitoring with automation. Introducing our Evolution Of Enterprise Security Operation Center set of slides. The topics discussed in these slides are Reactive Monitoring, Availability Monitoring, Proactive Monitoring. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Inclusion Of Automation In Enterprise Security Operations
Inclusion Of Automation In Enterprise Security OperationsThis slide covers inclusion of automation in enterprise security operations. It involves key roles such as automation, security analysts, incident responder, threat hunter and security operation manager. Presenting our well structured Inclusion Of Automation In Enterprise Security Operations. The topics discussed in this slide are Security Analyst, Incident Responder, Security Operation Manager. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Key Strategies For Enhancing Enterprise Security Operations
Key Strategies For Enhancing Enterprise Security OperationsThis slide covers key strategies for enhancing enterprise security operations. It involves strategies such as detect endpoint threats, leverage advanced analytics and automate incident response. Introducing our premium set of slides with Key Strategies For Enhancing Enterprise Security Operations. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Detect Endpoint Threats, Leverage Advanced Analytics, Automate Incident Response. So download instantly and tailor it with your information.





