Powerpoint Templates and Google slides for Engineer.
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Overview Engineering Ide Tools Prompt Engineering How To Communicate With Ai AI SS
Overview Engineering Ide Tools Prompt Engineering How To Communicate With Ai AI SSThis slide showcases basic overview to prompt engineering integrated development environments IDEs which developers can refer to gain knowledge about this technology. It provides details about language model, refining prompts, etc. Deliver an outstanding presentation on the topic using this Overview Engineering Ide Tools Prompt Engineering How To Communicate With Ai AI SS. Dispense information and present a thorough explanation of Overview, Engineering, Promptbase using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Overview Prompt Engineering Ai Methodology Prompt Engineering How To Communicate With Ai AI SS
Overview Prompt Engineering Ai Methodology Prompt Engineering How To Communicate With Ai AI SSThis slide showcases a basic introduction to prompt engineering technology and skill which are necessary for development and functioning of AI systems. It provides details about biasness, ethical concerns, etc. Present the topic in a bit more detail with this Overview Prompt Engineering Ai Methodology Prompt Engineering How To Communicate With Ai AI SS. Use it as a tool for discussion and navigation on Methodology, Engineering, Interaction. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Practical Illustration Of Good And Bad Prompts Prompt Engineering How To Communicate With Ai AI SS
Practical Illustration Of Good And Bad Prompts Prompt Engineering How To Communicate With Ai AI SSThis slide showcases practical examples of good and bad prompts, referable by users and multiple businesses harnessing this technology. It provides information about summary request, coherence evaluation, accuracy testing, etc. Deliver an outstanding presentation on the topic using this Practical Illustration Of Good And Bad Prompts Prompt Engineering How To Communicate With Ai AI SS. Dispense information and present a thorough explanation of Illustration, Requesting A Summary, Evaluating Coherence using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Prompt Engineering How To Communicate With Ai Table Of Contents AI SS
Prompt Engineering How To Communicate With Ai Table Of Contents AI SSPresent the topic in a bit more detail with this Prompt Engineering How To Communicate With Ai Table Of Contents AI SS. Use it as a tool for discussion and navigation on Communicate, Comparative, Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Prompt Engineering Techniques General Prompt Engineering How To Communicate With Ai AI SS
Prompt Engineering Techniques General Prompt Engineering How To Communicate With Ai AI SSThis slide showcases general introduction to prompt engineering techniques. It provides details about iterative refinement, fine tuning alignment, negative phrasing, evaluation, validation, etc. Deliver an outstanding presentation on the topic using this Prompt Engineering Techniques General Prompt Engineering How To Communicate With Ai AI SS. Dispense information and present a thorough explanation of Techniques, Overview, Instructions using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Question Answering Using Prompt Engineering Prompt Engineering How To Communicate With Ai AI SS
Question Answering Using Prompt Engineering Prompt Engineering How To Communicate With Ai AI SSThis slide showcases use cases and illustration of prompt engineering for question answering, which prompt engineers and users increase efficiency of their tasks. It provides information about responses, knowledge, etc. Present the topic in a bit more detail with this Question Answering Using Prompt Engineering Prompt Engineering How To Communicate With Ai AI SS. Use it as a tool for discussion and navigation on Illustration, Answering, Productivity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 React Prompting Prompt Engineering Technique Prompt Engineering How To Communicate With Ai AI SS
React Prompting Prompt Engineering Technique Prompt Engineering How To Communicate With Ai AI SSThis slide showcases overview and explanation of ReAct prompting, which prompt engineers and users can refer to increase accuracy of prompts. It provides information about reasoning, acting, interaction, etc. Deliver an outstanding presentation on the topic using this React Prompting Prompt Engineering Technique Prompt Engineering How To Communicate With Ai AI SS. Dispense information and present a thorough explanation of Engineering, Technique, Interaction using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Self Consistency Prompt Prompt Engineering Prompt Engineering How To Communicate With Ai AI SS
Self Consistency Prompt Prompt Engineering Prompt Engineering How To Communicate With Ai AI SSThis slide showcases overview and explanation of self consistency prompting, which prompt engineers and users can refer to increase accuracy of prompts. It provides information about internally coherent, logical coherence, etc. Present the topic in a bit more detail with this Self Consistency Prompt Prompt Engineering Prompt Engineering How To Communicate With Ai AI SS. Use it as a tool for discussion and navigation on Statements, Consistency, Technique. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Step By Step Process Prompt Engineering Prompt Engineering How To Communicate With Ai AI SS
Step By Step Process Prompt Engineering Prompt Engineering How To Communicate With Ai AI SSThis slide showcases prompt engineering step by step guide through which users can understand working methodology of this technology. It provides details about understanding, problem, initial prompt, model response, etc. Increase audience engagement and knowledge by dispensing information using Step By Step Process Prompt Engineering Prompt Engineering How To Communicate With Ai AI SS. This template helps you present information on six stages. You can also present information on Understanding The Problem, Crafting Initial Prompt, Iterating And Refining using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Contents Prompt Engineering How To Communicate With Ai AI SS
Table Of Contents Prompt Engineering How To Communicate With Ai AI SSDeliver an outstanding presentation on the topic using this Table Of Contents Prompt Engineering How To Communicate With Ai AI SS. Dispense information and present a thorough explanation of Prompt Engineering Techniques, Prompt Engineering Use Cases, Introduction To Prompt Engineering using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Text Classification Through Prompt Engineering Prompt Engineering How To Communicate With Ai AI SS
Text Classification Through Prompt Engineering Prompt Engineering How To Communicate With Ai AI SSThis slide showcases use cases and illustration of prompt engineering for text classification, through which prompt engineers and users can increase efficiency of their tasks. It provides information about AI, diverse interactions, etc. Present the topic in a bit more detail with this Text Classification Through Prompt Engineering Prompt Engineering How To Communicate With Ai AI SS. Use it as a tool for discussion and navigation on Classification, Interactions, Interviewer. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Text Summarization Through Prompt Engineering Prompt Engineering How To Communicate With Ai AI SS
Text Summarization Through Prompt Engineering Prompt Engineering How To Communicate With Ai AI SSThis slide showcases use cases and illustration of prompt engineering for text summarization, which prompt engineers and users increase efficiency of their tasks. It provides information about sentence breaking, etc. Deliver an outstanding presentation on the topic using this Text Summarization Through Prompt Engineering Prompt Engineering How To Communicate With Ai AI SS. Dispense information and present a thorough explanation of Summarization, Biodiversity, Characterized using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Types Audio And Transcription Based Prompts Prompt Engineering How To Communicate With Ai AI SS
Types Audio And Transcription Based Prompts Prompt Engineering How To Communicate With Ai AI SSThis slide showcases overview and illustration of transcribed audio prompting, which prompt engineers and users can refer to increase accuracy of prompts. It provides information about audio inputs, speech analysis, etc. Deliver an outstanding presentation on the topic using this Types Audio And Transcription Based Prompts Prompt Engineering How To Communicate With Ai AI SS. Dispense information and present a thorough explanation of Interactions, Introduce, Illustration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Types Multi Modal Prompt Engineering Prompt Engineering How To Communicate With Ai AI SS
Types Multi Modal Prompt Engineering Prompt Engineering How To Communicate With Ai AI SSThis slide showcases overview and illustration of multi modal prompting, which prompt engineers and users can refer to increase accuracy of prompts. It provides information about text, image, audio, etc. Present the topic in a bit more detail with this Types Multi Modal Prompt Engineering Prompt Engineering How To Communicate With Ai AI SS. Use it as a tool for discussion and navigation on Interactions, Illustrating, Engineering. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Types Natural Language Based Prompts Prompt Engineering How To Communicate With Ai AI SS
Types Natural Language Based Prompts Prompt Engineering How To Communicate With Ai AI SSThis slide showcases overview and illustration of natural language prompting, which prompt engineers and users can refer to increase accuracy of prompts. It provides information about communication, accessibility, interactions, etc. Deliver an outstanding presentation on the topic using this Types Natural Language Based Prompts Prompt Engineering How To Communicate With Ai AI SS. Dispense information and present a thorough explanation of Services, Businesses, Producers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Types Programming Language And Prompts Prompt Engineering How To Communicate With Ai AI SS
Types Programming Language And Prompts Prompt Engineering How To Communicate With Ai AI SSThis slide showcases overview and illustration of programming language and coding prompting, which prompt engineers and users can refer to increase accuracy of prompts. It provides information about software, automation, etc. Present the topic in a bit more detail with this Types Programming Language And Prompts Prompt Engineering How To Communicate With Ai AI SS. Use it as a tool for discussion and navigation on Services, Businesses, Producers. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Types Visual And Image Based Prompts Prompt Engineering How To Communicate With Ai AI SS
Types Visual And Image Based Prompts Prompt Engineering How To Communicate With Ai AI SSThis slide showcases overview and illustration of image based visual prompting, which prompt engineers and users can refer to increase accuracy of prompts. It provides information about description, interpretation, etc. Deliver an outstanding presentation on the topic using this Types Visual And Image Based Prompts Prompt Engineering How To Communicate With Ai AI SS. Dispense information and present a thorough explanation of Interpretation, Descriptive, Expressions using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Using Chatgpt Prompts Effectively For Business Prompt Engineering How To Communicate With Ai AI SS
Using Chatgpt Prompts Effectively For Business Prompt Engineering How To Communicate With Ai AI SSThis slide showcases ChatGPT prompt engineerings effective usage for corporates, referable by users and multiple businesses harnessing this technology. It provides information about linked prompts, priming, sample prompts, etc. Present the topic in a bit more detail with this Using Chatgpt Prompts Effectively For Business Prompt Engineering How To Communicate With Ai AI SS. Use it as a tool for discussion and navigation on Business, Effectively, Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Role Of Prompt Engineering In Achieving ChatGPT OpenAI Conversation AI Chatbot ChatGPT CD V
Role Of Prompt Engineering In Achieving ChatGPT OpenAI Conversation AI Chatbot ChatGPT CD VThis slide provides information regarding the importance of prompt engineering in gaining desired results. This approach helps in assessing fed inputs and showcase relevant and contextual results across ChatGPT model. Present the topic in a bit more detail with this Role Of Prompt Engineering In Achieving ChatGPT OpenAI Conversation AI Chatbot ChatGPT CD V. Use it as a tool for discussion and navigation on Relevant And Contextual, Prompt Engineering, Natural Language Processing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Online Search Engine Marketing Training Course
Online Search Engine Marketing Training CourseThis slide covers the online marketing training course for planning website, optimising search engine, app campaign and social media tools. Introducing our Online Search Engine Marketing Training Course set of slides. The topics discussed in these slides are Content, Module, Impact This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Aerospace Engineering Icon For Spacecraft Testing
Aerospace Engineering Icon For Spacecraft TestingPresenting our set of slides with Aerospace Engineering Icon For Spacecraft Testing This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Aerospace Engineering Icon, Spacecraft Testing
-
 Four Major Domains Of Aerospace Engineering
Four Major Domains Of Aerospace EngineeringThe purpose of this slide is to assist aerospace engineers in choosing their field of specialization followed by rigorous research and development. Presenting our well structured Four Major Domains Of Aerospace Engineering The topics discussed in this slide are Aerodynamics, Thermodynamics, Celestial Mechanics This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Agenda For Social Engineering Methods And Mitigation Strategies
Agenda For Social Engineering Methods And Mitigation StrategiesIntroducing Agenda For Social Engineering Methods And Mitigation Strategies to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Impersonation, Tailgating, Pretexting, Scareware, Mitigation Strategies, using this template. Grab it now to reap its full benefits.
-
 Icons Slide For Social Engineering Methods And Mitigation Strategies
Icons Slide For Social Engineering Methods And Mitigation StrategiesIntroducing our well researched set of slides titled Icons Slide For Social Engineering Methods And Mitigation Strategies. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Preventive Measures To Stay Safe From Quid Pro Quo Scams Social Engineering Methods And Mitigation
Preventive Measures To Stay Safe From Quid Pro Quo Scams Social Engineering Methods And MitigationThis slide represents the methods to avoid quid pro quo social engineering scams. These include verify identity, analyze unsolicited and unexpected offers, update anti-malware and anti-virus software, protect login information, provide employee cybersecurity awareness training, etc. Present the topic in a bit more detail with this Preventive Measures To Stay Safe From Quid Pro Quo Scams Social Engineering Methods And Mitigation. Use it as a tool for discussion and navigation on Protect Login Information, Anti Virus Software, Quid Pro Quo Scams. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Methods And Mitigation 30 60 90 Days Plan To Implement Social Engineering Prevention
Social Engineering Methods And Mitigation 30 60 90 Days Plan To Implement Social Engineering PreventionThis slide represents 30-60-90 plan to protect companies and their employees from social engineering attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month. Introducing Social Engineering Methods And Mitigation 30 60 90 Days Plan To Implement Social Engineering Prevention to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Social Engineering, Prevention Strategies, Protect Companies, Social Engineering Attacks, using this template. Grab it now to reap its full benefits.
-
 Social Engineering Methods And Mitigation About Angler Phishing Working And Example
Social Engineering Methods And Mitigation About Angler Phishing Working And ExampleThis slide talks about the angler phishing attacks conducted on internet using social media platforms. The purpose of this slide is to illustrate how fraudulent tweets or texts containing malicious links and misleading information, can be used by scammers to trick individuals. Deliver an outstanding presentation on the topic using this Social Engineering Methods And Mitigation About Angler Phishing Working And Example. Dispense information and present a thorough explanation of Angler Phishing Attacks, Social Media Platforms, Fraudulent Tweets, Texts Containing Malicious using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Methods And Mitigation About Baiting Attack Overview And Techniques
Social Engineering Methods And Mitigation About Baiting Attack Overview And TechniquesThis slide discusses baiting technique of social engineering attacks. The purpose of this slide is to outline the methods used by attackers to conduct baiting scam. These are online downloads, malware-infected devices and tempting offers. Present the topic in a bit more detail with this Social Engineering Methods And Mitigation About Baiting Attack Overview And Techniques. Use it as a tool for discussion and navigation on Online Downloads, Malware Infected Devices, Baiting Attack, Malicious Attachment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Methods And Mitigation About Impersonation Attacks Overview And Examples
Social Engineering Methods And Mitigation About Impersonation Attacks Overview And ExamplesThis slide discusses social engineering attacks using impersonation method. The purpose of this slide is to outline various examples of impersonation scams, such as email spoofing attack, cousin domain, account takeover, forged header or envelope, etc. Deliver an outstanding presentation on the topic using this Social Engineering Methods And Mitigation About Impersonation Attacks Overview And Examples. Dispense information and present a thorough explanation of Email Spoofing Attack, Cousin Domain, Fraudulent Applications, Impersonation Attacks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Methods And Mitigation About Phishing Attacks Overview And Impact
Social Engineering Methods And Mitigation About Phishing Attacks Overview And ImpactThis slide demonstrates the overview of cyber phishing attacks. The purpose of this slide is to talk about the effectiveness of phishing scams. This slide also outlines the issues which can be caused by phishing attacks such as disclosure of private data, etc. Increase audience engagement and knowledge by dispensing information using Social Engineering Methods And Mitigation About Phishing Attacks Overview And Impact. This template helps you present information on five stages. You can also present information on Compromised Accounts, Malware Injections, Financial Penalties, Financial Access using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Methods And Mitigation About Pretexting Technique Overview And Examples
Social Engineering Methods And Mitigation About Pretexting Technique Overview And ExamplesThis slide discusses the pretexting technique of social engineering and its examples. Different pretexting scam methods include business email compromise, account update scams, grandparent scams, romance scams, cryptocurrency scams, government scams, etc. Present the topic in a bit more detail with this Social Engineering Methods And Mitigation About Pretexting Technique Overview And Examples. Use it as a tool for discussion and navigation on Business Email Compromise, Grandparent Scams, Cryptocurrency Scams, Pretexting Technique. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Methods And Mitigation About Smishing Attacks Overview And Types
Social Engineering Methods And Mitigation About Smishing Attacks Overview And TypesThis slide talks about the smishing cyber attacks conducted by sending text messages to the targets. The purpose of this slide is to illustrate how fraudulent texts are sent to the users which contains malicious links and other mis-leading information. Introducing Social Engineering Methods And Mitigation About Smishing Attacks Overview And Types to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Smishing Scams, Financial Services Smishing, Gift Smishing, Customer Support Smishing, using this template. Grab it now to reap its full benefits.
-
 Social Engineering Methods And Mitigation About Tailgating Attacks Overview And Techniques
Social Engineering Methods And Mitigation About Tailgating Attacks Overview And TechniquesThis slide demonstrates the procedure of tailgating attack with the help of an illustrative example. The purpose of this slide is to provide the overview of tailgating social engineering attack and the techniques used to implement it in organizations. Deliver an outstanding presentation on the topic using this Social Engineering Methods And Mitigation About Tailgating Attacks Overview And Techniques. Dispense information and present a thorough explanation of Procedure Of Tailgating Attack, Tailgating Social Engineering Attack, Subcontractors Identity using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Methods And Mitigation About Vishing Attacks Overview And Identification
Social Engineering Methods And Mitigation About Vishing Attacks Overview And IdentificationThis slide talks about the vishing cyber attacks. The purpose of this slide is to explain the vishing technique used by phishers to scam victims. This slide also outlines the signs of vishing attack such as call from unknown number, act as an authority, etc. Present the topic in a bit more detail with this Social Engineering Methods And Mitigation About Vishing Attacks Overview And Identification. Use it as a tool for discussion and navigation on Vishing Cyber Attacks, Vishing Technique, Phishers To Scam Victims, Internal Revenue Service. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Methods And Mitigation About Whale Phishing CEO Fraud Overview And Example
Social Engineering Methods And Mitigation About Whale Phishing CEO Fraud Overview And ExampleThis slide talks about the whaling phishing attack which is also known as CEO fraud. The purpose of this slide is to explain how attackers target senior executives of organizations to conduct whale phishing cyber attacks by sending fraud mails to the employees. Deliver an outstanding presentation on the topic using this Social Engineering Methods And Mitigation About Whale Phishing CEO Fraud Overview And Example. Dispense information and present a thorough explanation of Whaling Phishing Attack, Attackers Target Senior Executives, Phishing Cyber Attacks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Methods And Mitigation Checklist To Secure Organizations From Social Engineering
Social Engineering Methods And Mitigation Checklist To Secure Organizations From Social EngineeringThis slide outlines the steps to be taken to protect the organization and its employees from social engineering attacks. The key approaches include provide staff training, update software, enable MFA and spam filters, implement real-time monitoring and develop an incident plan. Deliver an outstanding presentation on the topic using this Social Engineering Methods And Mitigation Checklist To Secure Organizations From Social Engineering. Dispense information and present a thorough explanation of Social Engineering Attacks, Real Time Monitoring, Develop An Incident Plan using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Methods And Mitigation Classification Of Different Social Engineering Attacks
Social Engineering Methods And Mitigation Classification Of Different Social Engineering AttacksThis slide represents the different types of social engineering attacks based on technology and human interaction. These include impersonation, tailgating, baiting, pretexting, scareware, quid pro quo, reverse social engineering, phishing, email phishing, spear phishing, whaling, etc. Increase audience engagement and knowledge by dispensing information using Social Engineering Methods And Mitigation Classification Of Different Social Engineering Attacks. This template helps you present information on two stages. You can also present information on Human Based Attacks, Social Engineering Attacks, Technology Based Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Methods And Mitigation Common Tactics Used In Scareware Attacks
Social Engineering Methods And Mitigation Common Tactics Used In Scareware AttacksThe purpose of this slide is to outline the several techniques used in scareware scams. The major points discussed in this slide are fake virus scans, fake tech support, Malvertising using legitimate advertisements and online law enforcement scams. Present the topic in a bit more detail with this Social Engineering Methods And Mitigation Common Tactics Used In Scareware Attacks. Use it as a tool for discussion and navigation on Fake Virus Scams, Malvertising, Law Enforcement Scams, Fake Tech Support. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Methods And Mitigation Comparison Between Different Types Of Email Based Phishing
Social Engineering Methods And Mitigation Comparison Between Different Types Of Email Based PhishingThis slide talks about several email-based phishing attacks such as spear phishing and whaling. The purpose of this slide is to compare these phishing types based on several factors such as target, attack method, deception, goal, example, etc. Deliver an outstanding presentation on the topic using this Social Engineering Methods And Mitigation Comparison Between Different Types Of Email Based Phishing. Dispense information and present a thorough explanation of Email Based Phishing Attacks, Goal, Target, Spear Phishing And Whaling using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Methods And Mitigation Defensive Strategies Against Tailgating Attacks
Social Engineering Methods And Mitigation Defensive Strategies Against Tailgating AttacksThis slide highlights the best practices to avoid tailgating social engineering attacks. These include beware of surroundings, implement biometric scanners, issue smart badges or cards with RFID technology, install AI-based video surveillance, etc. Present the topic in a bit more detail with this Social Engineering Methods And Mitigation Defensive Strategies Against Tailgating Attacks. Use it as a tool for discussion and navigation on Implement Biometric Scanners, Be Aware Of Surroundings, Unique Physical Features. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Methods And Mitigation Difference Between Baiting And Phishing Attacks
Social Engineering Methods And Mitigation Difference Between Baiting And Phishing AttacksThis slide compares the two major techniques of social engineering attacks, known as baiting and phishing. The comparison is based on several factors such as impersonation, communication, malware, identity theft, presentation, etc. Deliver an outstanding presentation on the topic using this Social Engineering Methods And Mitigation Difference Between Baiting And Phishing Attacks. Dispense information and present a thorough explanation of Impersonation, Communication, Identity Theft, Presentation, Malware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Methods And Mitigation Different Techniques Of Quid Pro Quo Scams
Social Engineering Methods And Mitigation Different Techniques Of Quid Pro Quo ScamsThis slide outlines the different methods used by attackers to implement quid pro quo scams. The major tactics involved in these attacks are related to employment opportunities, charity, investment services, tech support and healthcare departments. Present the topic in a bit more detail with this Social Engineering Methods And Mitigation Different Techniques Of Quid Pro Quo Scams. Use it as a tool for discussion and navigation on Employment Scams, Charity Scams, Investment Scams, Tech Support Scams, Healthcare Scams. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Methods And Mitigation Different Types Of Vishing Cyber Attacks
Social Engineering Methods And Mitigation Different Types Of Vishing Cyber AttacksThis slide talks about the various types of vishing cyber attacks. The purpose of this slide is to briefly explain different techniques of vishing scams used by the attackers to scam users. These are caller ID spoofing, dumpster diving, wardialing, etc. Introducing Social Engineering Methods And Mitigation Different Types Of Vishing Cyber Attacks to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Vishing Cyber Attacks, Dumpster Diving, Wardialing, Techniques Of Vishing Scams, using this template. Grab it now to reap its full benefits.
-
 Social Engineering Methods And Mitigation Execution Of Man In The Middle Cyber Attacks
Social Engineering Methods And Mitigation Execution Of Man In The Middle Cyber AttacksThis slide illustrates the process of executing man-in-the-middle cyber attacks. The purpose of this slide is to outline the two stages of execution of MITM scams. These stages are interception and decryption. Deliver an outstanding presentation on the topic using this Social Engineering Methods And Mitigation Execution Of Man In The Middle Cyber Attacks. Dispense information and present a thorough explanation of Cyber Attacks, Intercepting User Traffic, Malicious Wi Fi Hotspots using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Methods And Mitigation Guidelines To Stay Safe From Phishing Scams
Social Engineering Methods And Mitigation Guidelines To Stay Safe From Phishing ScamsThis slide outlines the various preventive measures to stay safe from phishing attacks. These include know how to spot phishing scams, avoid clicking that link, install free anti-phishing extensions, change passwords regularly, install firewalls, never miss updates, etc. Increase audience engagement and knowledge by dispensing information using Social Engineering Methods And Mitigation Guidelines To Stay Safe From Phishing Scams. This template helps you present information on seven stages. You can also present information on Install Firewalls, Change Passwords Regularly, Avoid Clicking That Link, Stay Safe From Phishing Scams using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Methods And Mitigation How To Protect Users From Vishing Attacks
Social Engineering Methods And Mitigation How To Protect Users From Vishing AttacksThis slide talks about the ways to protect users from vishing attacks. These include avoid calls from robots, never respond to audio-automated calls, verify the identity of the caller, never share personal information over the call, use multi-factor authentication, etc. Present the topic in a bit more detail with this Social Engineering Methods And Mitigation Guidelines To Stay Safe From Phishing Scams. Use it as a tool for discussion and navigation on Facto Authentication, Government Organizations, Identity Of The Caller, Avoid Calls From Robots. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Methods And Mitigation Man In The Middlemitm Phishing Attack Diagram
Social Engineering Methods And Mitigation Man In The Middlemitm Phishing Attack DiagramThis slide demonstrates the working flow of man-in-the-middle phishing attacks using MITM phishing toolkit cloud server. This slide also elaborates the various real-world examples of MITM attacks such as Equifaxs mobile application, superfish and DigiNotar. Deliver an outstanding presentation on the topic using this Social Engineering Methods And Mitigation Man In The Middlemitm Phishing Attack Diagram. Dispense information and present a thorough explanation of Equifaxs Mobile Application, Superfish, Phishing Attack Diagram, Financial Data using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Methods And Mitigation Methods To Prevent Reverse Social Engineering Attacks
Social Engineering Methods And Mitigation Methods To Prevent Reverse Social Engineering AttacksThis slide outlines the strategies to avoid reverse social engineering scams. The methods discussed in this slide are identify technical support specialists, use separate internal identifiers, provide regular security awareness training to employees, etc. Increase audience engagement and knowledge by dispensing information using Social Engineering Methods And Mitigation Methods To Prevent Reverse Social Engineering Attacks. This template helps you present information on three stages. You can also present information on Identify Technical Support Specialists, Use Separate Internal Identifiers, Provide Regular Security Awareness Training using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Methods And Mitigation Precaution Measures Against Pretexting Attacks
Social Engineering Methods And Mitigation Precaution Measures Against Pretexting AttacksThis slide outlines the preventive measures to stay safe from pretexting attacks, These are Domain-based Message Authentication Reporting DMARC, AI-powered email filters, Endpoint Detection and Response EDR, and Network Detection and Response NDR. Present the topic in a bit more detail with this Social Engineering Methods And Mitigation Precaution Measures Against Pretexting Attacks. Use it as a tool for discussion and navigation on Endpoint Detection And Response, Network Detection And Response, Pretexting Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Methods And Mitigation Prevention Strategies To Safeguard Against Impersonation
Social Engineering Methods And Mitigation Prevention Strategies To Safeguard Against ImpersonationThis slide represents the effective strategies to stay safe from impersonation attacks. These are custom email domains, email security and solutions software, AI-driven and automated software, implementing dual-control transactions and taking false domains. Introducing Social Engineering Methods And Mitigation Prevention Strategies To Safeguard Against Impersonation to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Custom Email Domains, Taking Down False Domains, Dual Control Transactions, using this template. Grab it now to reap its full benefits.
-
 Social Engineering Methods And Mitigation Preventive Measures For Man In The Middle Cyber Attacks
Social Engineering Methods And Mitigation Preventive Measures For Man In The Middle Cyber AttacksThis slide outlines the various methods of preventing man-in-the-middle cyber attacks. The purpose of this slide is to explain how users can protect themselves from MITM scams. These include secure connections, avoid phishing emails, endpoint security, etc. Increase audience engagement and knowledge by dispensing information using Social Engineering Methods And Mitigation Preventive Measures For Man In The Middle Cyber Attacks. This template helps you present information on four stages. You can also present information on Secure Connections, Avoid Phishing Emails, Endpoint Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Methods And Mitigation Preventive Measures To Avoid Watering Hole Phishing
Social Engineering Methods And Mitigation Preventive Measures To Avoid Watering Hole PhishingThis slide outlines the various preventive measures to avoid watering hole phishing attacks. The purpose of this slide is to help in protecting users from watering hole scams. The key steps include vulnerability scanning, security patches, input validation, etc. Introducing Social Engineering Methods And Mitigation Preventive Measures To Avoid Watering Hole Phishing to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Vulnerability Scanning, Security Patches, Input Vulnerability, Bug Bounty Programs, using this template. Grab it now to reap its full benefits.
-
 Social Engineering Methods And Mitigation Preventive Strategies For Baiting Cyber Attacks
Social Engineering Methods And Mitigation Preventive Strategies For Baiting Cyber AttacksThis slide outlines the methods to prevent baiting attacks. These are employee training, dont follow links blindly, use anti-virus and anti-malware software, avoid use of external devices without scanning and hold organized simulated attacks. Deliver an outstanding presentation on the topic using this Social Engineering Methods And Mitigation Preventive Strategies For Baiting Cyber Attacks. Dispense information and present a thorough explanation of Vulnerability Scanning, Security Patches, Input Vulnerability, Bug Bounty Programs using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Methods And Mitigation Quid Pro Quo Scams Overview And Warning Signs
Social Engineering Methods And Mitigation Quid Pro Quo Scams Overview And Warning SignsThis slide discusses the quid pro quo social engineering scams. The warning signs of this attack include unsolicited offers or requests, high-pressure tactics to decide quickly, requests for personal or financial information, and unclear or unrealistic promises of benefits. Increase audience engagement and knowledge by dispensing information using Social Engineering Methods And Mitigation Quid Pro Quo Scams Overview And Warning Signs. This template helps you present information on four stages. You can also present information on Quid Pro Quo Scams, Unrealistic Promises Of Benefits, Financial Information using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Methods And Mitigation Reverse Social Engineering Overview And Causes
Social Engineering Methods And Mitigation Reverse Social Engineering Overview And CausesThis slide discusses reverse social engineering scams. The purpose of this slide is to highlight the major reasons behind the successful reverse social engineering attacks. These are lack of security awareness, exploitation of human weaknesses, etc. Present the topic in a bit more detail with this Social Engineering Methods And Mitigation Reverse Social Engineering Overview And Causes. Use it as a tool for discussion and navigation on Lack Of Security Awareness, Exploitation Of Human Weaknesses, Untested Plans And Procedures. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Methods And Mitigation Roadmap To Implement Social Engineering Prevention Strategies
Social Engineering Methods And Mitigation Roadmap To Implement Social Engineering Prevention StrategiesThis slide represents the roadmap to prevent social engineering attacks in organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc. Introducing Social Engineering Methods And Mitigation Roadmap To Implement Social Engineering Prevention Strategies to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Employee Training, Implement Technical Controls, Social Engineering Prevention Strategies, using this template. Grab it now to reap its full benefits.
-
 Social Engineering Methods And Mitigation Scareware Technique Overview And Warning Signs
Social Engineering Methods And Mitigation Scareware Technique Overview And Warning SignsThis slide represents the scareware technique used by scammers to attempt social engineering attacks. The purpose of this slide is to demonstrate the various warning signs of scareware attack. Increase audience engagement and knowledge by dispensing information using Social Engineering Methods And Mitigation Scareware Technique Overview And Warning Signs. This template helps you present information on five stages. You can also present information on Scareware Technique, Scareware Attack, Social Engineering Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
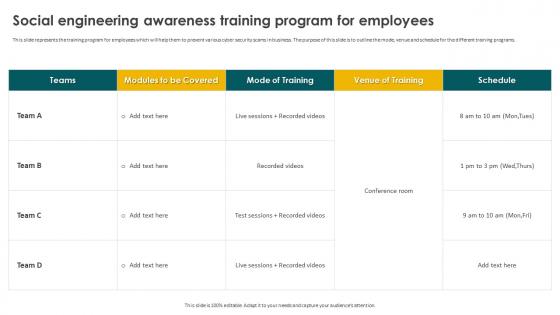 Social Engineering Methods And Mitigation Social Engineering Awareness Training Program For Employees
Social Engineering Methods And Mitigation Social Engineering Awareness Training Program For EmployeesThis slide represents the training program for employees which will help them to prevent various cyber security scams in business. The purpose of this slide is to outline the mode, venue and schedule for the different training programs. Present the topic in a bit more detail with this Social Engineering Methods And Mitigation Social Engineering Awareness Training Program For Employees. Use it as a tool for discussion and navigation on Social Engineering, Awareness Training, Program For Employees. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Methods And Mitigation Social Engineering Technique Dumpster Diving
Social Engineering Methods And Mitigation Social Engineering Technique Dumpster DivingThis slide discusses dumpster diving technique used to carry out social engineering attacks. The various types of information collected include passwords, access codes, organizational charts, calendars, credit card receipts, expense reports, phone numbers, etc. Introducing Social Engineering Methods And Mitigation Social Engineering Technique Dumpster Diving to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Organizational Charts, Network Or Application Diagrams, Dumpster Diving, Social Engineering Technique, using this template. Grab it now to reap its full benefits.
-
 Social Engineering Methods And Mitigation Steps To Identify Whaling Phishing Attacks
Social Engineering Methods And Mitigation Steps To Identify Whaling Phishing AttacksThis slide talks about the various methods of identifying whale phishing cyber attacks. The purpose of this slide is to help users identify CEO phishing scams. These include flag emails received from external domains, cross-verify sensitive requests, etc. Increase audience engagement and knowledge by dispensing information using Social Engineering Methods And Mitigation Steps To Identify Whaling Phishing Attacks. This template helps you present information on six stages. You can also present information on Phishing Cyber Attacks, Phishing Scams, External Domains, Cross Verify Sensitive Requests using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.





