Powerpoint Templates and Google slides for End Encrypted
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 End To End Encryption Powerpoint PPT Template Bundles
End To End Encryption Powerpoint PPT Template BundlesDeliver a lucid presentation by utilizing this End To End Encryption Powerpoint PPT Template Bundles. Use it to present an overview of the topic with the right visuals, themes, shapes, and graphics. This is an expertly designed complete deck that reinforces positive thoughts and actions. Use it to provide visual cues to your audience and help them make informed decisions. A wide variety of discussion topics can be covered with this creative bundle such as End-To-End Encryption, Chat Privacy, Whatsapp Encryption, Encryption Challenges Solutions, Business Trends Encryption, Encryption Backup Systems. All the Twenty slides are available for immediate download and use. They can be edited and modified to add a personal touch to the presentation. This helps in creating a unique presentation every time. Not only that, with a host of editable features, this presentation can be used by any industry or business vertical depending on their needs and requirements. The compatibility with Google Slides is another feature to look out for in the PPT slideshow.
-
 Encryption Implementation Strategies Data Confidentiality Using End To End Encryption
Encryption Implementation Strategies Data Confidentiality Using End To End EncryptionThis slide illustrates the use of end-to-end encryption mechanism to maintain data confidentiality and secure digital ecosystems. The purpose of this slide is to demonstrate how data can be transformed into an encrypted format to transmit it over a network. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Data Confidentiality Using End To End Encryption. Dispense information and present a thorough explanation of Data Confidentiality, Encryption Mechanism, Demonstrate, Digital Ecosystems using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Public And Private Keys For End To End Encryption
Encryption Implementation Strategies Public And Private Keys For End To End EncryptionThis slide discusses the utilization of asymmetric public key encryption technique to provide E2EE. The purpose of this slide is to explain how client-side encryption employs public and private keys to encrypt the message before transmission. Present the topic in a bit more detail with this Encryption Implementation Strategies Public And Private Keys For End To End Encryption. Use it as a tool for discussion and navigation on Public And Private Keys, Encryption Employs, Encryption Technique, Server Transmitting And Storing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 End To End Encryption Colored Icon In Powerpoint Pptx Png And Editable Eps Format
End To End Encryption Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is a visual representation of end to end encryption, a secure method of communication that ensures data is kept safe from interception. It is an effective way to protect confidential information and is ideal for businesses and organisations.
-
 End To End Encryption Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
End To End Encryption Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMonotone PowerPoint icon on End to end encryption is a simple yet powerful graphic that conveys the message of secure data transmission. It is perfect for presentations and documents that require a visual representation of the encryption process. The icon is easy to use and customize to fit any design needs.
-
 Advantages Of End To End Encryption Methodology Encryption For Data Privacy In Digital Age It
Advantages Of End To End Encryption Methodology Encryption For Data Privacy In Digital Age ItThis slide represents the various benefits of client side encryption. The purpose of this slide is to outline the benefits of end to end encryption such as security in transit, tamper-proof, compliance, protects data from hacking and privacy of the user. Present the topic in a bit more detail with this Advantages Of End To End Encryption Methodology Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Protects Data From Hacking, Security In Transit, Compliance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparison End To End Encryption And Transport Layer Encryption For Data Privacy In Digital Age It
Comparison End To End Encryption And Transport Layer Encryption For Data Privacy In Digital Age ItThis slide demonstrates the differences between End-to-end encryption E2EE and Transport Layer Security TLS. The purpose of this slide is to compare these two security paradigms based on different factors such as endpoint protection, examples, etc. Present the topic in a bit more detail with this Comparison End To End Encryption And Transport Layer Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Comparison, Protection, Demonstrates. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Confidentiality Using End To End Encryption Encryption For Data Privacy In Digital Age It
Data Confidentiality Using End To End Encryption Encryption For Data Privacy In Digital Age ItThis slide illustrates the use of end to end encryption mechanism to maintain data confidentiality. The steps involved are client browser to web browser, web server to Siebel server, Siebel server to database, storing data into a storage system, etc. Deliver an outstanding presentation on the topic using this Data Confidentiality Using End To End Encryption Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Data Confidentiality, Encryption, Database using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Disadvantages Of End To End Encryption Technology Encryption For Data Privacy In Digital Age It
Disadvantages Of End To End Encryption Technology Encryption For Data Privacy In Digital Age ItThis slide represents the various drawbacks of client side encryption. The purpose of this slide is to outline the disadvantages of end to end encryption such as difficulty in identifying endpoints, surplus of privacy, transparent metadata, endpoint security, etc. Present the topic in a bit more detail with this Disadvantages Of End To End Encryption Technology Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Disadvantages, Encryption, Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 End To End Encryption To Secure Digital Ecosystems Encryption For Data Privacy In Digital Age It
End To End Encryption To Secure Digital Ecosystems Encryption For Data Privacy In Digital Age ItThis slide discusses about the end to end encryption methodology. It secures the communication between sender and receiver. The purpose of this slide is to show the data flow between two users using end to end encryption technique. Present the topic in a bit more detail with this End To End Encryption To Secure Digital Ecosystems Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Encryption, Digital Ecosystems, Communication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Limitations Of End To End Encryption And Solutions Encryption For Data Privacy In Digital Age It
Limitations Of End To End Encryption And Solutions Encryption For Data Privacy In Digital Age ItThis slide demonstrates the challenges faced by client side encryption such as metadata, compromised endpoints and risky intermediaries. The purpose of this slide is to outline the solutions of various limitations of end to end encryption mechanism. Deliver an outstanding presentation on the topic using this Limitations Of End To End Encryption And Solutions Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Encryption, Solutions, Limitations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 List Of Communication Apps Using End To End Encryption Encryption For Data Privacy In Digital Age It
List Of Communication Apps Using End To End Encryption Encryption For Data Privacy In Digital Age ItThis slide demonstrates different texting apps utilizing end to end encryption to secure data transmission. The purpose of this slide is to outline the communication apps with default or optional end to end encryption such as Signal, WhatsApp, etc. Increase audience engagement and knowledge by dispensing information using List Of Communication Apps Using End To End Encryption Encryption For Data Privacy In Digital Age It. This template helps you present information on five stages. You can also present information on Encryption, Communication, Conversations using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Mathematical Function Used In End To End Encryption Encryption For Data Privacy In Digital Age It
Mathematical Function Used In End To End Encryption Encryption For Data Privacy In Digital Age ItThis slide represents the calculative theory behind key generation in end-to-end encryption. The purpose of this slide is to illustrate the working of one-way mathematical function which uses a large integer to compute the key by using two prime numbers. Deliver an outstanding presentation on the topic using this Mathematical Function Used In End To End Encryption Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Mathematical, Processing, Calculative using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Public And Private Keys For End To End Encryption Encryption For Data Privacy In Digital Age It
Public And Private Keys For End To End Encryption Encryption For Data Privacy In Digital Age ItThis slide discusses the utilization of asymmetric public key encryption technique to provide E2EE. The purpose of this slide is to explain how client side encryption employs public and private keys to encrypt the message before transmission. Deliver an outstanding presentation on the topic using this Public And Private Keys For End To End Encryption Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Encryption, Utilization, Technique using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Working Of End To End Encryption Mechanism Encryption For Data Privacy In Digital Age It
Working Of End To End Encryption Mechanism Encryption For Data Privacy In Digital Age ItThis slide outlines the steps involved in working of end to end encrypted communication between sender and the recipient. The purpose of this slide is to demonstrate the encryption and decryption procedure with the help of data flow diagram. Deliver an outstanding presentation on the topic using this Working Of End To End Encryption Mechanism Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Encryption, Mechanism, Demonstrate using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Backup Systems In End To End Encryption
Backup Systems In End To End EncryptionThis slide covers the working of end-to-end encryption backups. The purpose of this template is to educate the audience on how end-to-end encryption functions in the context of data backups. It includes secure data storage, user-controlled keys, additional authentication measures, backup compatibility, and the potential performance impact.Introducing Backup Systems In End To End Encryption to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Secure Data Storage, Additional Authentication, Backup Compatibility, using this template. Grab it now to reap its full benefits.
-
 Business Trends To Strengthen End To End Encryption In Future
Business Trends To Strengthen End To End Encryption In FutureThis slide covers five future trends in end-to-end encryption. The purpose of this template is to inform the audience about the evolving landscape of end-to-end encryption and its potential impact on data security and privacy. It includes Homomorphic Encryption, Quantum-Resistant Encryption, Decentralized Encryption, AI-powered Threat Detection, and Collaborative Encryption Standards. Increase audience engagement and knowledge by dispensing information using Business Trends To Strengthen End To End Encryption In Future This template helps you present information on Five stages. You can also present information on Homomorphic Encryption, Decentralized Encryption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Creating And Restoring End To End Encryption Backup
Creating And Restoring End To End Encryption BackupThis slide highlights the process for establishing an end-to-end encryption backup. The purpose of this slide is to highlight the workings of an encryption backup. It includes manually saving the 64-digit key, generating the encryption key, and retrieving the encryption key. Present the topic in a bit more detail with this Creating And Restoring End To End Encryption Backup Use it as a tool for discussion and navigation on 64 Digit Format, Encrypts The Backup, Uploaded To Cloud. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 End To End Encryption Challenges With Action Steps
End To End Encryption Challenges With Action StepsThis slide covers the challenges associated with implementing end-to-end encryption. The purpose of this template is to enlighten stakeholders on key issues such as key management complexity, cross-platform compatibility, user experience impact, data recovery challenges, and regulatory compliance complexity. Deliver an outstanding presentation on the topic using this End To End Encryption Challenges With Action Steps Dispense information and present a thorough explanation of Key Management Complexity, User Experience Impact using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 End To End Encryption Icon For Mobile Texting
End To End Encryption Icon For Mobile TextingIntroducing End To End Encryption Icon For Mobile Texting to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on End To End Encryption, Icon For Mobile Texting, using this template. Grab it now to reap its full benefits.
-
 End To End Encryption Icon For User Data Protection
End To End Encryption Icon For User Data ProtectionIncrease audience engagement and knowledge by dispensing information using End To End Encryption Icon For User Data Protection This template helps you present information on Three stages. You can also present information on End To End Encryption, Icon For User Data Protection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 End To End Encryption Icon Showing Messaging Privacy
End To End Encryption Icon Showing Messaging PrivacyPresent the topic in a bit more detail with this End To End Encryption Icon Showing Messaging Privacy Use it as a tool for discussion and navigation on End To End Encryption, Icon Showing Messaging Privacy This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 End To End Encryption Provided By Social App
End To End Encryption Provided By Social AppThis slide covers key points related to social apps implementation of end-to-end encryption. The purpose of this template is to inform the audience about WhatsApps commitment to privacy and security through end-to-end encryption. It includes personal messaging, business messaging, Metas involvement, and secure payments on WhatsApp. Introducing End To End Encryption Provided By Social App to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Personal Messaging Encryption, Business Messaging Encryption, using this template. Grab it now to reap its full benefits.
-
 Ethical Considerations Related To End To End Encryption
Ethical Considerations Related To End To End EncryptionThis slide covers the ethical considerations surrounding end-to-end encryption. The purpose of this template is to inform stakeholders about the importance of preserving user privacy, safeguarding against unauthorized surveillance, striking a balance between security and accessibility, addressing potential misuse for criminal activities, and promoting transparency and accountability. Increase audience engagement and knowledge by dispensing information using Ethical Considerations Related To End To End Encryption This template helps you present information on Five stages. You can also present information on Preserving User Privacy, Unauthorized Surveillance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Five Step Process To Implement End To End Encryption
Five Step Process To Implement End To End EncryptionThis slide covers a 5-stage process for implementing end-to-end encryption. The purpose of this template is to provide a comprehensive roadmap for effectively working on end-to-end encryption, including defining requirements, selecting encryption algorithms, testing, deploying, and monitoring the solution.Introducing Five Step Process To Implement End To End Encryption to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Select Encryption Algorithms, Testing And Validation, using this template. Grab it now to reap its full benefits.
-
 How Does End To End Encryption Work
How Does End To End Encryption WorkThis slide highlights an example of end-to-end encryption. The purpose of this slide is to show the working of end-to-end encryption, including encrypting and decrypting keys of both receiver and sender. Deliver an outstanding presentation on the topic using this How Does End To End Encryption Work Dispense information and present a thorough explanation of Adam Encrypted Message, Decrypt Message using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implications Of End To End Encryption For User Safety
Implications Of End To End Encryption For User SafetyThis slide covers the fundamental reasons behind WhatsApps implementation of end-to-end encryption. This template aims to articulate the significance of end-to-end encryption in safeguarding privacy, enhancing security, building user trust, data privacy, and securing the communication process. Introducing Implications Of End To End Encryption For User Safety to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Protecting Privacy, Preventing Data Breaches, using this template. Grab it now to reap its full benefits.
-
 Importance Of End To End Encryption To Business
Importance Of End To End Encryption To BusinessThis slide covers the importance of end-to-end encryption for businesses. The purpose of this template is to underscore the critical role of end-to-end encryption in enhancing data privacy and security for businesses. It includes data privacy, customer trust, regulatory compliance, competitive advantage, and reducing costs. Increase audience engagement and knowledge by dispensing information using Importance Of End To End Encryption To Business This template helps you present information on Five stages. You can also present information on Enhanced Data Privacy, Customer Trust And Loyalty using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Procedure To Create End To End Encryption Model
Procedure To Create End To End Encryption ModelThis slide covers process to create end-to-end encryption. The purpose of this template is to guide and inform the audience about the fundamental steps involved in establishing robust end-to-end encryption for secure communication. It includes key generation, public key exchange, encryption with public keys, decryption with private keys, and integrity verification. Introducing Procedure To Create End To End Encryption Model to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Key Generation, Public Key Exchange, Encryption With Public Keys, using this template. Grab it now to reap its full benefits.
-
 Real World Applications Of End To End Encryption
Real World Applications Of End To End EncryptionThis slide covers the real-life applications of end-to-end encryption. The purpose of this template is to illustrate how end-to-end encryption is employed in everyday scenarios, ensuring data security and privacy. It includes secure messaging apps, cloud storage services, password managers, and encrypted email services. Increase audience engagement and knowledge by dispensing information using Real World Applications Of End To End Encryption This template helps you present information on Four stages. You can also present information on Secure Messaging Apps, Cloud Storage Services, Encrypted Email Services using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 User Statistics On End To End Encryption
User Statistics On End To End EncryptionThis slide covers key statistics related to cloud data analytics. The purpose of this template is to highlight the effectiveness and impact of cloud data analytics on businesses. It includes factual statistics that demonstrate the profitability, usage, and benefits of adopting cloud-based analytics solutions. Introducing User Statistics On End To End Encryption to increase your presentation threshold. Encompassed with Seven stages, this template is a great option to educate and entice your audience. Dispence information on Specific Types Of Data, User Trust And Confidence, Encryption Services By 2030, using this template. Grab it now to reap its full benefits.
-
 Using End To End Encryption For Chat Privacy
Using End To End Encryption For Chat PrivacyThis slide covers the use cases of end-to-end encryption. The purpose of this template is to educate and emphasize the critical roles of end-to-end encryption in various scenarios. It includes secure messaging, protects passwords from unauthorized access, and safeguards data storage against potential compromises. Increase audience engagement and knowledge by dispensing information using Using End To End Encryption For Chat Privacy This template helps you present information on Three stages. You can also present information on Secure Communications, Password Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Various Types Of End To End Encryption
Various Types Of End To End EncryptionThis slide covers four types of end-to-end encryption. The purpose of this template is to educate the audience on the diverse approaches to implementing end-to-end encryption, including Symmetric Encryption, Asymmetric Encryption, Hybrid Encryption, and Multi-Party Computation MPC.Introducing Various Types Of End To End Encryption to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Symmetric Encryption, Asymmetric Encryption, Hybrid Encryption, using this template. Grab it now to reap its full benefits.
-
 End To End Encryption Icon For Chatbot Security
End To End Encryption Icon For Chatbot SecurityPresenting our set of slides with End To End Encryption Icon For Chatbot Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on End To End, Encryption Icon, Chatbot Security.
-
 Comparative Analysis Of End To End Encryption Tools Implementing Strategies For Mitigating Cybersecurity SS
Comparative Analysis Of End To End Encryption Tools Implementing Strategies For Mitigating Cybersecurity SSThis slide compares the best end-to-end encryption software solutions based on different parameters such as password management, on-the-fly decryption, and enterprise-grade decryption.Deliver an outstanding presentation on the topic using this Comparative Analysis Of End To End Encryption Tools Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Offers Support, Password Management, Enterprise Grade Decryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implementing End To End Encryption To Communication Channels Cybersecurity SS
Implementing End To End Encryption To Communication Channels Cybersecurity SSThis slide provides information about implementing end-to-end encryption E2EE to secure an organizations communication channels, including email communication, instant messaging, software and programs.Deliver an outstanding presentation on the topic using this Implementing End To End Encryption To Communication Channels Cybersecurity SS. Dispense information and present a thorough explanation of Communication Channels, Description, Impact using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
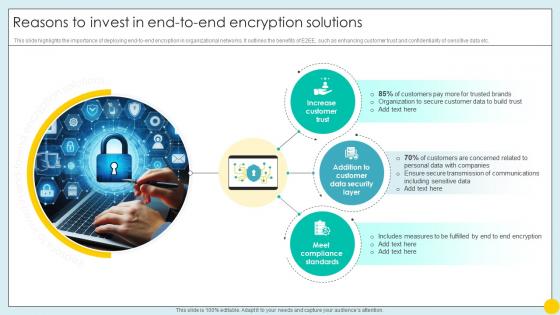 Reasons To Invest In End To End Encryption Solutions Implementing Strategies For Mitigating Cybersecurity SS
Reasons To Invest In End To End Encryption Solutions Implementing Strategies For Mitigating Cybersecurity SSThis slide highlights the importance of deploying end-to-end encryption in organizational networks. It outlines the benefits of E2EE, such as enhancing customer trust and confidentiality of sensitive data etc.Introducing Reasons To Invest In End To End Encryption Solutions Implementing Strategies For Mitigating Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Increase Customer Trust, Meet Compliance Standards, Customer Data Security Layer, using this template. Grab it now to reap its full benefits.
-
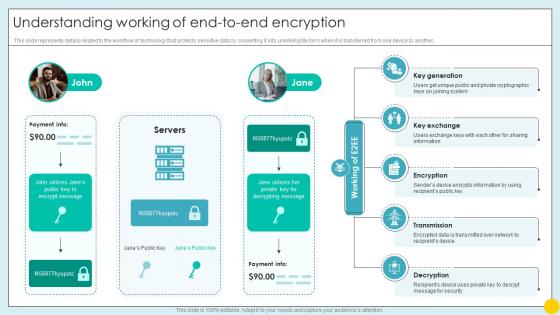 Understanding Working Of End To End Encryption Implementing Strategies For Mitigating Cybersecurity SS
Understanding Working Of End To End Encryption Implementing Strategies For Mitigating Cybersecurity SSThis slide represents details related to the workflow of technology that protects sensitive data by converting it into unintelligible form when it is transferred from one device to another. Increase audience engagement and knowledge by dispensing information using Understanding Working Of End To End Encryption Implementing Strategies For Mitigating Cybersecurity SS. This template helps you present information on five stages. You can also present information on Key Exchange, Encryption, Transmission, Decryption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 End To End Test Plan Icon For Message Encryption
End To End Test Plan Icon For Message EncryptionIntroducing our End To End Test Plan Icon For Message Encryption set of slides. The topics discussed in these slides are End To End Test Plan, Message Encryption This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 End encrypted cloud storage ppt powerpoint presentation infographic template format cpb
End encrypted cloud storage ppt powerpoint presentation infographic template format cpbPresenting this set of slides with name End Encrypted Cloud Storage Ppt Powerpoint Presentation Infographic Template Format Cpb. This is an editable Powerpoint six stages graphic that deals with topics like End Encrypted Cloud Storage to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 End to end encrypted ppt powerpoint presentation styles grid cpb
End to end encrypted ppt powerpoint presentation styles grid cpbPresenting this set of slides with name End To End Encrypted Ppt Powerpoint Presentation Styles Grid Cpb. This is an editable Powerpoint six stages graphic that deals with topics like End To End Encrypted to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 End encrypted ppt powerpoint presentation infographics visuals cpb
End encrypted ppt powerpoint presentation infographics visuals cpbPresenting this set of slides with name End Encrypted Ppt Powerpoint Presentation Infographics Visuals Cpb. This is an editable Powerpoint four stages graphic that deals with topics like End Encrypted to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 End to end encrypted data ppt powerpoint presentation summary portrait cpb
End to end encrypted data ppt powerpoint presentation summary portrait cpbPresenting this set of slides with name End To End Encrypted Data Ppt Powerpoint Presentation Summary Portrait Cpb. This is an editable Powerpoint three stages graphic that deals with topics like End To End Encrypted Data to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 End encrypted data ppt powerpoint presentation gallery display cpb
End encrypted data ppt powerpoint presentation gallery display cpbPresenting this set of slides with name End Encrypted Data Ppt Powerpoint Presentation Gallery Display Cpb. This is an editable Powerpoint five stages graphic that deals with topics like End Encrypted Data to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 End encrypted ppt powerpoint presentation show clipart cpb
End encrypted ppt powerpoint presentation show clipart cpbPresenting this set of slides with name End Encrypted Ppt Powerpoint Presentation Show Clipart Cpb. This is an editable Powerpoint three stages graphic that deals with topics like End Encrypted to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Implement end to end encryption ppt powerpoint presentation gallery backgrounds cpb
Implement end to end encryption ppt powerpoint presentation gallery backgrounds cpbPresenting this set of slides with name Implement End To End Encryption Ppt Powerpoint Presentation Gallery Backgrounds Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Implement End To End Encryption to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 End encryption app ppt powerpoint presentation slides influencers cpb
End encryption app ppt powerpoint presentation slides influencers cpbPresenting our End Encryption App Ppt Powerpoint Presentation Slides Influencers Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on End Encryption App,CPB This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 End encryption messaging ppt powerpoint presentation model show cpb
End encryption messaging ppt powerpoint presentation model show cpbPresenting our End Encryption Messaging Ppt Powerpoint Presentation Model Show Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on End Encryption Messaging,CPB This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 6 value slide for end to end encryption signal infographic template
6 value slide for end to end encryption signal infographic templateThis is a single slide titled 6 Value Slide For End To End Encryption Signal Infographic Template. It is crafted using high quality vector based visuals that are 100 percent editable and available for immediate download in standard and widescreen aspect ratios.



