Powerpoint Templates and Google slides for Encryption
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Encryption For Data Annual IT Budget Focused On Encryption Costs Cybersecurity SS
Encryption For Data Annual IT Budget Focused On Encryption Costs Cybersecurity SSThis slide showcases encryption costs under an annual information technology budget, helping companies adjust their expenses. It provides details about software, hardware, training, license, etc. Present the topic in a bit more detail with this Encryption For Data Annual IT Budget Focused On Encryption Costs Cybersecurity SS. Use it as a tool for discussion and navigation on Encryption Software, Hardware Infrastructure, Training Programs, Software Updates. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Caesar Algorithm Implementation For Basic Encryption Cybersecurity SS
Encryption For Data Caesar Algorithm Implementation For Basic Encryption Cybersecurity SSThis slide showcases caesar algorithm deployment which can help employees learn basic techniques for basic encryption. It provides details about shift, displacement, shift value, decryption, etc. Introducing Encryption For Data Caesar Algorithm Implementation For Basic Encryption Cybersecurity SS to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Pre-Implementation Stage, Implementation Steps, Potential Benefit, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Choose Right Data Encryption Solution Cybersecurity SS
Encryption For Data Choose Right Data Encryption Solution Cybersecurity SSThis slide showcases encryption best practice focused on ensuring right selection of tools and solutions. It provides details about database, application, on-premises, cloud, automated lifecycle, etc. Present the topic in a bit more detail with this Encryption For Data Choose Right Data Encryption Solution Cybersecurity SS. Use it as a tool for discussion and navigation on Encryption At Multiple Levels, Centralized Management Dashboard, Data Encryption. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Classify Data For Organizational Encryption Solution Cybersecurity SS
Encryption For Data Classify Data For Organizational Encryption Solution Cybersecurity SSThis slide showcases encryption best practice focused on classifying organizational data. It provides details about sensitivity checks, regulations, clerical errors, etc. Introducing Encryption For Data Classify Data For Organizational Encryption Solution Cybersecurity SS to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Financial Data, Customer Details, Business, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Comparative Assessment Of Top Encryption Tools Cybersecurity SS
Encryption For Data Comparative Assessment Of Top Encryption Tools Cybersecurity SSThis slide showcases comparative analysis of major encryption software, helping companies choose according to their needs. It provides details about platform, integration, cost, user experience, etc. Present the topic in a bit more detail with this Encryption For Data Comparative Assessment Of Top Encryption Tools Cybersecurity SS. Use it as a tool for discussion and navigation on Encryption Type, Platform, Integration, User Experience. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Define Security Requirements For Encryption Strategy Cybersecurity SS
Encryption For Data Define Security Requirements For Encryption Strategy Cybersecurity SSThis slide showcases encryption best practice focused on defining security requirements. It provides details about threat assessment, system vulnerabilities, business decisions, etc. Introducing Encryption For Data Define Security Requirements For Encryption Strategy Cybersecurity SS to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Conduct Threat Assessment, Learn Of Any Business Decisions, System Vulnerabilities, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Encryption Awareness Training Implementation Plan Cybersecurity SS
Encryption For Data Encryption Awareness Training Implementation Plan Cybersecurity SSThis slide showcases training plan focused on building key encryption skills amongst organizations employees. It provides details about retention of training, backdoor access, internet society, etc. Introducing Encryption For Data Encryption Awareness Training Implementation Plan Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Existing Training Scenario, Details, Modules, Training Initiatives, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Encryption Key Management Best Practices Cybersecurity SS
Encryption For Data Encryption Key Management Best Practices Cybersecurity SSThis slide showcases encryption key management best practices which can help companies increase security. It provides details about secure key stores, access, backup, recovery, etc. Present the topic in a bit more detail with this Encryption For Data Encryption Key Management Best Practices Cybersecurity SS. Use it as a tool for discussion and navigation on Secure Key Stores, Access To Key Stores, Key Backup And Recoverability. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Financial Impact Of Poor Encryption Practices Cybersecurity SS
Encryption For Data Financial Impact Of Poor Encryption Practices Cybersecurity SSThis slide showcases financial impact of poor practices relating to encryption. Its purpose is to make businesses aware of major and potential vulnerabilities. It provides information about data breach, downtime, lost business, wages, etc. Present the topic in a bit more detail with this Encryption For Data Financial Impact Of Poor Encryption Practices Cybersecurity SS. Use it as a tool for discussion and navigation on Data Breach, Lost Business, Idle Employees And Wages, Regulatory Fines. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Homomorphic Cryptography For Data Base Security Cybersecurity SS
Encryption For Data Homomorphic Cryptography For Data Base Security Cybersecurity SSThis slide showcases homomorphic cryptography deployment which can help employees increase data privacy and outsourcing security. It provides details about private key, plaintext, decryption, etc. Introducing Encryption For Data Homomorphic Cryptography For Data Base Security Cybersecurity SS to increase your presentation threshold. Encompassed with Eight stages, this template is a great option to educate and entice your audience. Dispence information on Homomorphic Encryption, Classified Plaintext, Decrypted Results, Data Owner Organization, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Implementing Encryption Gap Analysis For Organization Cybersecurity SS
Encryption For Data Implementing Encryption Gap Analysis For Organization Cybersecurity SSThis slide showcases gap analysis relating to encryption running in the organization. Its purpose is to make businesses aware of major and potential vulnerabilities. It provides information about sensitive data, employee awareness, key management, etc. Introducing Encryption For Data Implementing Encryption Gap Analysis For Organization Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Current State, Desired State, Action Items, Priority, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Importance Of Encryption In Todays Business Cybersecurity SS
Encryption For Data Importance Of Encryption In Todays Business Cybersecurity SSThis slide showcases significant role of encryption technology, focused on improving data privacy. It provides details about data integrity, cost savings, backup authentication, customer trust, etc. Introducing Encryption For Data Importance Of Encryption In Todays Business Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Protects Data Integrity, Saves Costs, Authenticates Backups, Increases Customer Trust, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Introduction To Cybersecurity Awareness Cybersecurity SS
Encryption For Data Introduction To Cybersecurity Awareness Cybersecurity SSIntroducing Encryption For Data Introduction To Cybersecurity Awareness Cybersecurity SS to increase your presentation threshold. Encompassed with One stages, this template is a great option to educate and entice your audience. Dispence information on General Overview, Business, Data Security, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Key Management Algorithms And Dedicated Protocols Cybersecurity SS
Encryption For Data Key Management Algorithms And Dedicated Protocols Cybersecurity SSThis slide showcases key management protocols which can help companies increase efficiency and generation time. It provides details about hash functions, authentication, symmetric, etc. Introducing Encryption For Data Key Management Algorithms And Dedicated Protocols Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Cryptographic Hash Functions, Symmetric-Key Algorithms, Asymmetric-Key Algorithms, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Key Management And Strength Improvement Techniques Cybersecurity SS
Encryption For Data Key Management And Strength Improvement Techniques Cybersecurity SSThis slide showcases key management and strength improvement techniques which can help companies increase security. It provides details about elliptic, organization strategy, data exposure, etc. Introducing Encryption For Data Key Management And Strength Improvement Techniques Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Establishing Key Strength, Encrypting Keys Securely, Elliptic Curve Algorithms, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Multi Staged Process Of Encryption Technology Cybersecurity SS
Encryption For Data Multi Staged Process Of Encryption Technology Cybersecurity SSThis slide showcases general overview of encryption technology process, focused on improving data privacy. It provides details about plaintext, ciphertext, decryption, etc. Introducing Encryption For Data Multi Staged Process Of Encryption Technology Cybersecurity SS to increase your presentation threshold. Encompassed with Eight stages, this template is a great option to educate and entice your audience. Dispence information on Plaintext Becomes Ciphertext, Encryption Keys And Algorithms Used, Ciphertext Sent Though Insecure Channels, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data One Time Pad OTP Encryption Method Cybersecurity SS
Encryption For Data One Time Pad OTP Encryption Method Cybersecurity SSThis slide showcases one time pad OTP encryption deployment which can help employees secure their communication protocols. It provides details about plaintext, ciphertext, binary, exclusive OR XOR , etc. Introducing Encryption For Data One Time Pad OTP Encryption Method Cybersecurity SS to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Encryption Process, Decryption Process, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Organizational Chart Of Cyber Security Department Cybersecurity SS
Encryption For Data Organizational Chart Of Cyber Security Department Cybersecurity SSThis slide showcases hierarchy chart focused on building cybersecurity teams to help improve business data encryption. It provides details about DevOps, CISO, encryption specialist, engineer, etc. Present the topic in a bit more detail with this Encryption For Data Organizational Chart Of Cyber Security Department Cybersecurity SS. Use it as a tool for discussion and navigation on Organizational Chart, Cyber Security Department. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Password Encryption Strategy For Maximum Security Cybersecurity SS
Encryption For Data Password Encryption Strategy For Maximum Security Cybersecurity SSThis slide showcases password encryption policies which can help organizations achieve maximum data security. It provides details about salting, SHA-2, Bcrypt, passcode age, auto-lock, etc. Present the topic in a bit more detail with this Encryption For Data Password Encryption Strategy For Maximum Security Cybersecurity SS. Use it as a tool for discussion and navigation on Require Alphanumeric Value, Maximum Passcode Age, Grace Period For Device Lock. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
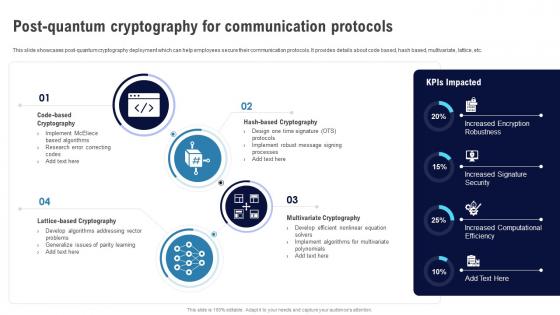 Encryption For Data Post Quantum Cryptography For Communication Protocols Cybersecurity SS
Encryption For Data Post Quantum Cryptography For Communication Protocols Cybersecurity SSThis slide showcases post-quantum cryptography deployment which can help employees secure their communication protocols. It provides details about code based, hash based, multivariate, lattice, etc. Introducing Encryption For Data Post Quantum Cryptography For Communication Protocols Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Code-Based Cryptography, Lattice-Based Cryptography, Hash-Based Cryptography, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Public Key Cryptography For Secure Access Cybersecurity SS
Encryption For Data Public Key Cryptography For Secure Access Cybersecurity SSThis slide showcases public key cryptography deployment which can help employees increased speed and user experience of their platforms. It provides details about private key, key generation, decryption, etc. Present the topic in a bit more detail with this Encryption For Data Public Key Cryptography For Secure Access Cybersecurity SS. Use it as a tool for discussion and navigation on Potential Impact, Increased Speed, Improved User Experience. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Roles And Responsibilities Of Cyber Security Department Cybersecurity SS
Encryption For Data Roles And Responsibilities Of Cyber Security Department Cybersecurity SSThis slide showcases roles and responsibilities of cybersecurity teams which can help improve business data encryption. It provides details about CTO, key management, encryption specialist and engineer, etc. Introducing Encryption For Data Roles And Responsibilities Of Cyber Security Department Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Key Management, Encryption Engineer, Chief Technology Officer, Encryption Specialist, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Security Defense Arsenal For Data Encryption Cybersecurity SS
Encryption For Data Security Defense Arsenal For Data Encryption Cybersecurity SSThis slide showcases encryption best practice focused on implementing security defense arsenal for data protection. It provides details about firewall, antimalware, authentication, encryption, etc. Introducing Encryption For Data Security Defense Arsenal For Data Encryption Cybersecurity SS to increase your presentation threshold. Encompassed with Seven stages, this template is a great option to educate and entice your audience. Dispence information on Firewall, Anti Malware, Authentication, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Timeline For Implementing Encryption Best Practices Cybersecurity SS
Encryption For Data Timeline For Implementing Encryption Best Practices Cybersecurity SSThis slide showcases timeline of encryption to be implemented in the organization. Its purpose is to make businesses ready for future plans of cyber security. It provides information about foundation, rollout, secure communication, etc. Introducing Encryption For Data Timeline For Implementing Encryption Best Practices Cybersecurity SS to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Foundation And Training, Asymmetric Encryption Rollout, Additional Security Measures, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data What Is Encryption General Overview Cybersecurity SS
Encryption For Data What Is Encryption General Overview Cybersecurity SSThis slide showcases general overview of encryption technology which acts as a cornerstone of data privacy. It provides details about plaintext, ciphertext, data privacy, integrity, compliance issues, etc. Introducing Encryption For Data What Is Encryption General Overview Cybersecurity SS to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Benefits, Overview, Increase Consumer Trust, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents Encryption For Data Security Cybersecurity SS
Table Of Contents Encryption For Data Security Cybersecurity SSIntroducing Table Of Contents Encryption For Data Security Cybersecurity SS to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Cybersecurity Team For Encryption, Encryption Costs Analysis, Pre Implementation Best Practices, using this template. Grab it now to reap its full benefits.
-
 Encryption Secure Communication In Powerpoint And Google Slides Cpp
Encryption Secure Communication In Powerpoint And Google Slides CppPresenting Encryption Secure Communication In Powerpoint And Google Slides Cpp slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Encryption Secure Communication. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Email Dlp And Encryption Prevent Potential Data Safeguarding Business With Data Loss Cybersecurity SS
Email Dlp And Encryption Prevent Potential Data Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding email data loss prevention with exact data matching, email fraud prevention, deep analysis, fingerprinting, and automate regulatory compliance.Deliver an outstanding presentation on the topic using this Email Dlp And Encryption Prevent Potential Data Safeguarding Business With Data Loss Cybersecurity SS. Dispense information and present a thorough explanation of Focus Areas, Activities Performed, Overall Impact using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Services Type In Powerpoint And Google Slides Cpp
Encryption Services Type In Powerpoint And Google Slides CppPresenting our Encryption Services Type In Powerpoint And Google Slides Cpp PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Encryption Services Type This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Confidential Information Encrypt File In Powerpoint And Google Slides Cpp
Confidential Information Encrypt File In Powerpoint And Google Slides CppPresenting our Confidential Information Encrypt File In Powerpoint And Google Slides Cpp PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Confidential Information Encrypt File This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Information Encryption Icon For Effective Data Loss Prevention
Information Encryption Icon For Effective Data Loss PreventionPresenting our well structured Information Encryption Icon For Effective Data Loss Prevention. The topics discussed in this slide are Loss Prevention, Information, Encryption. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Fintech Encryption Cyber Security Icon
Fintech Encryption Cyber Security IconIntroducing our premium set of slides with name Fintech Encryption Cyber Security Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Fintech Encryption, Cyber Security. So download instantly and tailor it with your information.
-
 End To End Encryption Icon For Chatbot Security
End To End Encryption Icon For Chatbot SecurityPresenting our set of slides with End To End Encryption Icon For Chatbot Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on End To End, Encryption Icon, Chatbot Security.
-
 Email Security Best Practices Types Of Email Encryption For Secure Communication
Email Security Best Practices Types Of Email Encryption For Secure CommunicationThe purpose of this slide is to outline the different types of email encryption protocols used to secure business communication. These techniques are Pretty Good Privacy PGP , Secure Multi-purpose Internet Mail Extension S or MIME, etc. Introducing Email Security Best Practices Types Of Email Encryption For Secure Communication to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Pretty Good Privacy, Secure Multi-Purpose Internet Mail Extension, Transport Layer Security, using this template. Grab it now to reap its full benefits.
-
 Comparative Assessment Of Encryption Algorithms For Organizational Data Security
Comparative Assessment Of Encryption Algorithms For Organizational Data SecurityThis slide provides a comparative assessment of various data encryption algorithms on different parameters. The multiple parameters used for assessment are encryption standard and use cases. Introducing our premium set of slides with Comparative Assessment Of Encryption Algorithms For Organizational Data Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Aes, Tdes, Twofish, Blowfish. So download instantly and tailor it with your information.
-
 IOT Data Encryption Security Icon
IOT Data Encryption Security IconIntroducing our premium set of slides with name IOT Data Encryption Security Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like IOT, Data Encryption, Security. So download instantly and tailor it with your information.
-
 Encryption Data Protection Illustration
Encryption Data Protection IllustrationThis colourful PowerPoint icon showcases the relationship between BYOE Bring Your Own Encryption and Hardware Security Module HSM. It represents the seamless integration and collaboration between these two important components in ensuring robust data security. Perfect for presentations and educational materials on data encryption and HSM technology.
-
 Cyber Threat Detection Data Encryption Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Threat Detection Data Encryption Colored Icon In Powerpoint Pptx Png And Editable Eps FormatSecure your digital assets with our Cloud-based endpoint cyber security icon for PowerPoint. Featuring a bold and vibrant design, this icon represents the protection and peace of mind offered by our cutting-edge security solutions. Perfect for presentations on cloud security, data protection, and cyber threats. Download now and enhance your slides.
-
 Cyber Threat Detection Data Encryption Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Threat Detection Data Encryption Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon represents a cloud-based endpoint cyber security solution. It is designed to protect your digital assets from external threats, providing real-time monitoring and threat detection. With its user-friendly interface and advanced features, it offers a comprehensive and reliable solution for safeguarding your data and devices.
-
 Encryption Phishing Prevention Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Encryption Phishing Prevention Colored Icon In Powerpoint Pptx Png And Editable Eps FormatUpgrade your email security with our vibrant PowerPoint icon. This eye-catching design showcases the importance of safeguarding your emails from cyber threats. With enhanced protection features, our icon serves as a visual reminder to prioritize email security in your daily communications. Perfect for presentations, reports, and more.
-
 Encryption Phishing Prevention Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Encryption Phishing Prevention Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatIntroducing our Monotone PowerPoint icon for Email Security, designed to enhance protection for your emails. This sleek and modern icon is perfect for presentations and documents related to email security and will add a professional touch to your materials. Keep your emails safe and secure with our Monotone PowerPoint icon.
-
 Mobile Device Encryption Plan For Data Security Mobile Device Security Cybersecurity SS
Mobile Device Encryption Plan For Data Security Mobile Device Security Cybersecurity SSThis slide showcases data encryption plan that can help to enhance mobile security. Its key elements are target devices, employees, encryption technique used, software used, authentication method etc. Introducing Mobile Device Encryption Plan For Data Security Mobile Device Security Cybersecurity SS to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Encrypted Communication, Secure Remote Access, Data Privacy using this template. Grab it now to reap its full benefits.
-
 Mobile Device Encryption Policy To Safeguard Data Mobile Device Security Cybersecurity SS
Mobile Device Encryption Policy To Safeguard Data Mobile Device Security Cybersecurity SSThis slide showcases mobile encryption policy that can help in data privacy. Its key components are purpose of policy, scope and encryption policy Increase audience engagement and knowledge by dispensing information using Mobile Device Encryption Policy To Safeguard Data Mobile Device Security Cybersecurity SS This template helps you present information on Three stages. You can also present information on Geographical Region, Detected Globally, Mobile Cyber Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Adopting Homomorphic Encryption To Secure Cloud Computing Implementing Digital Transformation And Ai DT SS
Adopting Homomorphic Encryption To Secure Cloud Computing Implementing Digital Transformation And Ai DT SSThis slide provides glimpse about utilizing homomorphic encryption approach that can help businesses in privacy preservation. It includes stages such as encryption, computation, decryption, etc. Increase audience engagement and knowledge by dispensing information using Adopting Homomorphic Encryption To Secure Cloud Computing Implementing Digital Transformation And Ai DT SS. This template helps you present information on three stages. You can also present information on Privacy Preservation, Secure Cloud Computing, Model Owner using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Dark Web And Encrypted Communications In Cyberterrorism Strategic Guide To Implement Strategy SS
Dark Web And Encrypted Communications In Cyberterrorism Strategic Guide To Implement Strategy SSThis slide showcases the Dark web and encrypted communications in cyber terrorism. It includes elements such as definition, characteristics, implications and use cases.Introducing Dark Web And Encrypted Communications In Cyberterrorism Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Privacy Implications, Use Cases, Characteristics, Define, using this template. Grab it now to reap its full benefits.
-
 Comparative Analysis Of End To End Encryption Tools Implementing Strategies For Mitigating Cybersecurity SS
Comparative Analysis Of End To End Encryption Tools Implementing Strategies For Mitigating Cybersecurity SSThis slide compares the best end-to-end encryption software solutions based on different parameters such as password management, on-the-fly decryption, and enterprise-grade decryption.Deliver an outstanding presentation on the topic using this Comparative Analysis Of End To End Encryption Tools Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Offers Support, Password Management, Enterprise Grade Decryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implementing End To End Encryption To Communication Channels Cybersecurity SS
Implementing End To End Encryption To Communication Channels Cybersecurity SSThis slide provides information about implementing end-to-end encryption E2EE to secure an organizations communication channels, including email communication, instant messaging, software and programs.Deliver an outstanding presentation on the topic using this Implementing End To End Encryption To Communication Channels Cybersecurity SS. Dispense information and present a thorough explanation of Communication Channels, Description, Impact using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Factors For Selecting Robust Encryption Solution Implementing Strategies For Mitigating Cybersecurity SS
Key Factors For Selecting Robust Encryption Solution Implementing Strategies For Mitigating Cybersecurity SSThis slide presents essential considerations for choosing an E2EE solution, including asymmetric encryption, key verification, complex cryptography, and ephemeral messaging.Introducing Key Factors For Selecting Robust Encryption Solution Implementing Strategies For Mitigating Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Asymmetric Encryption, Key Verification, Complex Cryptography, Ephemeral Messaging, using this template. Grab it now to reap its full benefits.
-
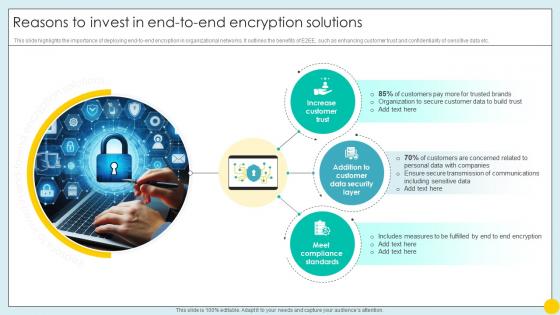 Reasons To Invest In End To End Encryption Solutions Implementing Strategies For Mitigating Cybersecurity SS
Reasons To Invest In End To End Encryption Solutions Implementing Strategies For Mitigating Cybersecurity SSThis slide highlights the importance of deploying end-to-end encryption in organizational networks. It outlines the benefits of E2EE, such as enhancing customer trust and confidentiality of sensitive data etc.Introducing Reasons To Invest In End To End Encryption Solutions Implementing Strategies For Mitigating Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Increase Customer Trust, Meet Compliance Standards, Customer Data Security Layer, using this template. Grab it now to reap its full benefits.
-
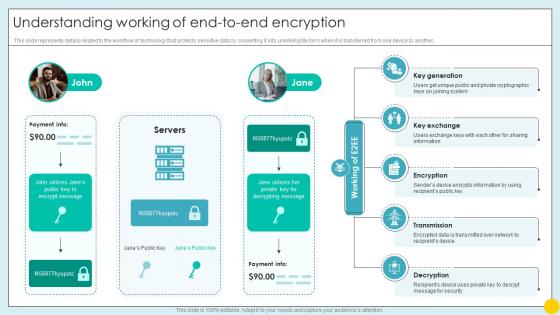 Understanding Working Of End To End Encryption Implementing Strategies For Mitigating Cybersecurity SS
Understanding Working Of End To End Encryption Implementing Strategies For Mitigating Cybersecurity SSThis slide represents details related to the workflow of technology that protects sensitive data by converting it into unintelligible form when it is transferred from one device to another. Increase audience engagement and knowledge by dispensing information using Understanding Working Of End To End Encryption Implementing Strategies For Mitigating Cybersecurity SS. This template helps you present information on five stages. You can also present information on Key Exchange, Encryption, Transmission, Decryption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Asymmetric Data Encryption For Secure Communication
Asymmetric Data Encryption For Secure CommunicationThe purpose of this slide is to elucidate how asymmetric data encryption enhances secure communication through the use of key pairs. It ensures robust protection against unauthorized access and interception. Introducing our Asymmetric Data Encryption For Secure Communication set of slides. The topics discussed in these slides are Device, Securing, Communication Channels, Cloud Server. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cloud Encryption Essentials For Robust Data Security
Cloud Encryption Essentials For Robust Data SecurityThe purpose of this slide is to highlight how cloud encryption essentials bolster robust data security. It safeguard sensitive information stored in cloud environments through cryptographic techniques. Presenting our set of slides with name Cloud Encryption Essentials For Robust Data Security. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Insider Threat Defense, Secure Data Transfers, Organizational Integrity.
-
 Cybersecurity Compliance Checklist For Data Encryption
Cybersecurity Compliance Checklist For Data EncryptionThe purpose of this slide is to present a cybersecurity compliance checklist for data encryption, offering a comprehensive guide. It ensures adherence to regulatory standards and best practices, ultimately fortifying data security against potential breaches and non-compliance risks. Presenting our set of slides with name Cybersecurity Compliance Checklist For Data Encryption. This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Encryption Algorithms, Homomorphic Encryption, Algorithms And Protocols.
-
 Data Encryption Algorithms For Security Solutions
Data Encryption Algorithms For Security SolutionsThe purpose of this slide is to demonstrate how data encryption algorithms for security solutions enhance protection. It encode data to prevent unauthorized access or manipulation. Introducing our Data Encryption Algorithms For Security Solutions set of slides. The topics discussed in these slides are Advanced Encryption Standard, Rivest Shamir Adleman, Elliptic Curve Cryptography. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data Encryption Checklist To Ensure Confidentiality
Data Encryption Checklist To Ensure ConfidentialityThe slides purpose is to guide organizations with a data encryption checklist. It ensures confidentiality through robust encryption measures and safeguarding sensitive information with data integrity. Presenting our set of slides with name Data Encryption Checklist To Ensure Confidentiality. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Implement Encryption In Transit, Implement Encryption At Rest, System Administrator.
-
 Data Encryption Hierarchy In SQL Sever
Data Encryption Hierarchy In SQL SeverThe slide illustrates how the data encryption hierarchy in SQL Server enhances security by implementing encryption methods at various levels. It ensures comprehensive data protection within the database. Presenting our set of slides with name Data Encryption Hierarchy In SQL Sever. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Service Master Key, Master Database Key, Database Level Key.
-
 Data Encryption Icon For Confidential Transactions
Data Encryption Icon For Confidential TransactionsPresenting our set of slides with name Data Encryption Icon For Confidential Transactions. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Encryption Icon, Confidential Transactions.
-
 Data Encryption Icon For Enhanced Privacy
Data Encryption Icon For Enhanced PrivacyPresenting our set of slides with name Data Encryption Icon For Enhanced Privacy. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Encryption Icon, Enhanced Privacy.
-
 Data Encryption Icon For Secure Messaging
Data Encryption Icon For Secure MessagingPresenting our set of slides with name Data Encryption Icon For Secure Messaging. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Encryption Icon, Secure Messaging.
-
 Data Encryption Tools Comparative Analysis
Data Encryption Tools Comparative AnalysisThe purpose of this slide is to facilitate a comparative analysis of data encryption tools. It aids in selection of most optimal solution through an evaluation of performance, security features, and compatibility. Introducing our Data Encryption Tools Comparative Analysis set of slides. The topics discussed in these slides are Encryption Algorithm, Key Management, Platform Support. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.





