Powerpoint Templates and Google slides for Encryption
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Training Plan For Cloud Data Encryption Implementation Cloud Data Encryption
Training Plan For Cloud Data Encryption Implementation Cloud Data EncryptionThis slide represents the composition of a training plan for cloud data encryption implementation. The key components include the training module, expected learning, mode of training, training hours, and expected completion date. Present the topic in a bit more detail with this Training Plan For Cloud Data Encryption Implementation Cloud Data Encryption. Use it as a tool for discussion and navigation on Training Module, Expected Learning. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Zero Knowledge Cloud Storage Services Cloud Data Encryption
Zero Knowledge Cloud Storage Services Cloud Data EncryptionThis slide discusses zero knowledge cloud encryption services to secure data stored in the cloud. The purpose of this slide is to outline the scenarios where zero knowledge encryption implementation is suitable. Deliver an outstanding presentation on the topic using this Zero Knowledge Cloud Storage Services Cloud Data Encryption. Dispense information and present a thorough explanation of Scrambles Data Using, Service Provider using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Corporate Email Encryption In Powerpoint And Google Slides Cpb
Corporate Email Encryption In Powerpoint And Google Slides CpbPresenting Corporate Email Encryption In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Corporate Email Encryption. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Confidential Computing System Technology What Is Fully Homomorphic Encryption Fhe
Confidential Computing System Technology What Is Fully Homomorphic Encryption FheThis slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security. Deliver an outstanding presentation on the topic using this Confidential Computing System Technology What Is Fully Homomorphic Encryption Fhe. Dispense information and present a thorough explanation of Improved Privacy, Strict Regulatory Compliance, Enhanced Cloud Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Email Best Practices Privacy Encryption In Powerpoint And Google Slides Cpb
Email Best Practices Privacy Encryption In Powerpoint And Google Slides CpbPresenting our Email Best Practices Privacy Encryption In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Email Best Practices Privacy Encryption This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cloud Access Security Broker CASB V2 And Encryption Ppt Gallery Design Templates
Cloud Access Security Broker CASB V2 And Encryption Ppt Gallery Design TemplatesThis slide describes the improved encryption with CASB version 2.0. The purpose of this slide is to showcase the various encryption features of Cloud Access Security Broker version 2.0, including security that follows the data, content access that can be revoked at any time, and multi-platform compatibility. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 And Encryption Ppt Gallery Design Templates. Dispense information and present a thorough explanation of Detecting Sensitive Information, Personally Identifiable Information, Personal Health Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Opposite Types In Powerpoint And Google Slides Cpb
Encryption Opposite Types In Powerpoint And Google Slides CpbPresenting Encryption Opposite Types In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Encryption Opposite Types. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Agenda Encryption Implementation Strategies Ppt Ideas Design Templates
Agenda Encryption Implementation Strategies Ppt Ideas Design TemplatesIntroducing Agenda Encryption Implementation Strategies Ppt Ideas Design Templates to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Encryption Implementation Strategies, Data Encryption Techniques, Security Protocol, using this template. Grab it now to reap its full benefits.
-
 Encryption Implementation Strategies About Bring Your Own Encryption Overview And Benefits
Encryption Implementation Strategies About Bring Your Own Encryption Overview And BenefitsThis slide discusses about widely used encryption method known as Bring Your Own Encryption BYOE. The purpose of this slide is to elaborate the meaning of BYOE. This slide also outlines the benefits of Bring Your Own Keys BYOK method. Increase audience engagement and knowledge by dispensing information using Encryption Implementation Strategies About Bring Your Own Encryption Overview And Benefits. This template helps you present information on eight stages. You can also present information on Bring Your Own Encryption, Bring Your Own Keys, Control And Monitoring using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Encryption Implementation Strategies About Encryption Introduction And Key Benefits
Encryption Implementation Strategies About Encryption Introduction And Key BenefitsThis slide discusses encryption technique to transform data into an unreadable format using a cryptographic key. The purpose of this slide is to outline various benefits of encryption, such as data confidentiality, integrity, regulatory compliance, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies About Encryption Introduction And Key Benefits. Use it as a tool for discussion and navigation on Encryption Technique, Cryptographic Key, Data Confidentiality, Integrity, Regulatory Compliance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies About File Level Encryption Overview And Types
Encryption Implementation Strategies About File Level Encryption Overview And TypesThe purpose of this slide is to compare the administration and security levels of the various types of file-level encryption. The kinds of file-level encryption discussed in this slide are application level, file-system level, volume, partition, etc. Introducing Encryption Implementation Strategies About File Level Encryption Overview And Types to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Administration And Security Levels, File Level Encryption, Application Level, File System Level, using this template. Grab it now to reap its full benefits.
-
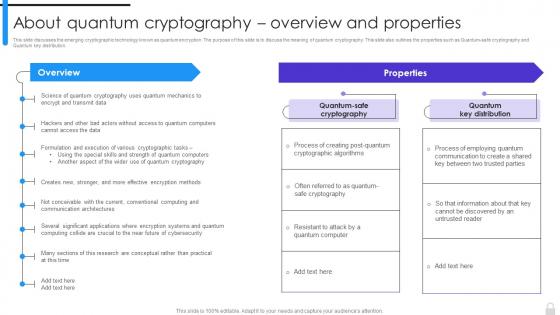 Encryption Implementation Strategies About Quantum Cryptography Overview And Properties
Encryption Implementation Strategies About Quantum Cryptography Overview And PropertiesThis slide discusses the emerging cryptographic technology known as quantum encryption. The purpose of this slide is to discuss the meaning of quantum cryptography. This slide also outlines the properties such as Quantum-safe cryptography and Quantum key distribution. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies About Quantum Cryptography Overview And Properties. Dispense information and present a thorough explanation of Quantum Safe Cryptography, Quantum Key Distribution, Quantum Cryptography using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Apple Full Disk Encryption Filevault
Encryption Implementation Strategies Apple Full Disk Encryption FilevaultThis slide discusses the full disk encryption technique provided by apple to secure the data of computer disk, known as the FileVault software. The purpose of this slide is to outline the steps to enable the FileVault encryption in computer system. Increase audience engagement and knowledge by dispensing information using Encryption Implementation Strategies Apple Full Disk Encryption Filevault. This template helps you present information on two stages. You can also present information on Full Disk Encryption Technique, Data Of Computer Disk, Macintosh Operating System, System Preferences using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Encryption Implementation Strategies Applications Of Encryption As A Service In Organizations
Encryption Implementation Strategies Applications Of Encryption As A Service In OrganizationsThe purpose of this slide is to outline the major uses of Encryption-as-Service method in different domains. The key applications discussed in this slide are all-time security assurance, secure sensitive information and maintaining regulatory compliance, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Applications Of Encryption As A Service In Organizations. Use it as a tool for discussion and navigation on Secure Sensitive Information, Maintaining Regulatory Compliance, Relevant Tools And Resources. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Architecture Of Cloud Storage Encryption Management
Encryption Implementation Strategies Architecture Of Cloud Storage Encryption ManagementThis slide represents the architecture of cloud cryptography technique. The purpose of this slide is to describe the security features and encryption methods employed by IBM Cloud and default encryption of data in motion and at rest using TLS. Introducing Encryption Implementation Strategies Architecture Of Cloud Storage Encryption Management to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Cryptography Technique, Encryption Of Data, Key Management, Cloud Storage Encryption, using this template. Grab it now to reap its full benefits.
-
 Encryption Implementation Strategies Architecture Of Homomorphic Encryption In Healthcare Industry
Encryption Implementation Strategies Architecture Of Homomorphic Encryption In Healthcare IndustryThe purpose of this slide is to emphasize the need for secure transmission of data in healthcare departments. The key components included are smart watch, patient health information, homomorphic encryption, ciphertext, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Architecture Of Homomorphic Encryption In Healthcare Industry. Dispense information and present a thorough explanation of Architecture Of Homomorphic, Encryption In Healthcare Industry, Patient Health Information, Healthcare Departments using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Before Vs After Adopting Data Encryption Techniques
Encryption Implementation Strategies Before Vs After Adopting Data Encryption TechniquesThis slide compares the scenario after integrating encryption protocols in organizational network. The purpose of this slide is to represent before and after situation based on several parameters. The factors used to do the comparison are data protection, insider threat protection, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Before Vs After Adopting Data Encryption Techniques. Use it as a tool for discussion and navigation on Data Protection, Security Breach Impact, Regulatory Compliance, Data Sharing And Collaboration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Best Practices To Implement Suitable Security Protocol Into Network
Encryption Implementation Strategies Best Practices To Implement Suitable Security Protocol Into NetworkThe purpose of this slide is to outline the steps involved in implementing a security protocol into a network. These are access network requirements, plan and design, select the right protocol, prepare the network infrastructure, configure devices, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Best Practices To Implement Suitable Security Protocol Into Network. Dispense information and present a thorough explanation of Assess Network Requirements, Implement User Authentication, Suitable Security Protocol using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Business Applications Of Homomorphic Encryption Technology
Encryption Implementation Strategies Business Applications Of Homomorphic Encryption TechnologyThe purpose of this slide is to demonstrate the key uses of homomorphic encryption in different domains. The main business applications of this technology are supply chain security, regulatory compliance management and sensitive data analytics. Increase audience engagement and knowledge by dispensing information using Encryption Implementation Strategies Business Applications Of Homomorphic Encryption Technology. This template helps you present information on three stages. You can also present information on Supply Chain Security, Regulatory Compliance, Sensitive Data Analytics, Homomorphic Encryption Technology using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Encryption Implementation Strategies Challenges Of Data At Rest Encryption And Solutions
Encryption Implementation Strategies Challenges Of Data At Rest Encryption And SolutionsThis slide outlines the various limitations of data at rest protection and their possible solutions. These are scattered documentation, sensitive data stored on personal mobile devices, lack of control over data stored in cloud, compliance with data protection regulations in different verticals, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Challenges Of Data At Rest Encryption And Solutions. Use it as a tool for discussion and navigation on Data At Rest Protection, Scattered Documentation, Sensitive Data Stored, Personal Mobile Devices, Data Protection Regulations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Challenges Of Data In Transit Encryption And Solutions
Encryption Implementation Strategies Challenges Of Data In Transit Encryption And SolutionsThis slide outlines the various limitations of data in transit protection and their possible solutions. These are infinite number of channels for communication, protection of an infinite number of cloud applications, loss of control at the receiving end, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Challenges Of Data In Transit Encryption And Solutions. Dispense information and present a thorough explanation of Data In Transit, Encryption And Solutions, Cloud Applications, Channels For Communication using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Challenges Of Data In Use Protection And Solutions
Encryption Implementation Strategies Challenges Of Data In Use Protection And SolutionsThis slide outlines the various limitations of data in use protection and their possible solutions. These include limited control after data access, unauthorized copying or sharing of data, limitations of collaboration platforms, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Challenges Of Data In Use Protection And Solutions. Use it as a tool for discussion and navigation on Limitations Of Collaboration Platforms, Unauthorized Copying Or Sharing Of Data, Limited Control After Data Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Checklist To Implement Data Encryption Technology
Encryption Implementation Strategies Checklist To Implement Data Encryption TechnologyThis slide outlines the steps to be taken to protect the organizations data using encryption. The key approaches include identify sensitive data, assess requirements, select method, implement encryption, test functionality, establish monitoring, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Checklist To Implement Data Encryption Technology. Dispense information and present a thorough explanation of Assess Requirements, Implement Encryption, Establish Monitoring, Test Functionality using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Column Level Data Encryption In SQL Servers
Encryption Implementation Strategies Column Level Data Encryption In SQL ServersThis slide discusses the encryption hierarchy in column level data encryption. The purpose of this slide is to represent different tiers of encryption hierarchy such as windows level, SQL server level, user database level, instance level, and master database level. Present the topic in a bit more detail with this Encryption Implementation Strategies Column Level Data Encryption In SQL Servers. Use it as a tool for discussion and navigation on Encrypts Service Key, Master Database, Encrypts Database Encryption Key. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Comparison Between Column Level And Whole Database Encryption
Encryption Implementation Strategies Comparison Between Column Level And Whole Database EncryptionThe purpose of this slide is to outline the differences between column level and whole database encryption technologies. This slide compares the mentioned techniques based on several parameters such as scope, level of encryption, flexibility, compliance, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Comparison Between Column Level And Whole Database Encryption. Dispense information and present a thorough explanation of Whole Database Encryption, Flexibility, Compliance, Mentioned Techniques, Encryption Technologies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Comparison Between Digital Rights Management Software
Encryption Implementation Strategies Comparison Between Digital Rights Management SoftwareThis slide outlines the available Digital Rights Management DRM software for several industries, such as information technology and services, marketing and advertising, consumer goods, automotive, civil engineering, architecture and planning, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Comparison Between Digital Rights Management Software. Use it as a tool for discussion and navigation on Marketing And Advertising, Architecture And Planning, Information Technology And Services. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Comparison Between Full Disk And File Level Encryption
Encryption Implementation Strategies Comparison Between Full Disk And File Level EncryptionThis slide discusses the two main types of encryption used for computers, known as full-disk encryption FDE and file-level encryption FLE. The purpose of this slide is to compare both encryption techniques based on different parameters. Increase audience engagement and knowledge by dispensing information using Encryption Implementation Strategies Comparison Between Full Disk And File Level Encryption. This template helps you present information on two stages. You can also present information on Full Disk Encryption, File Level Encryption, Operating System And System Files using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Encryption Implementation Strategies Comparison Between Information Rights Management And Digital
Encryption Implementation Strategies Comparison Between Information Rights Management And DigitalThis slide highlights the differences between Information Rights Management IRM and Digital Rights Management DRM. The comparison is carried out based on several factors, such as purpose, focus, application scope, legal framework, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Comparison Between Information Rights Management And Digital. Dispense information and present a thorough explanation of Information Rights Management, Digital Rights Management, Controversy And Criticisms using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Comparison Between Various VPN Protocols
Encryption Implementation Strategies Comparison Between Various VPN ProtocolsThis slide discusses different Virtual Private Network VPN protocols based on several factors, such as encryption, algorithms used, security level and speed. These protocols are IKEv2, OpenVPN, L2TP, WireGuard, SSTP Secure Socket Tunnelling Protocol, and PPTP. Present the topic in a bit more detail with this Encryption Implementation Strategies Comparison Between Various VPN Protocols. Use it as a tool for discussion and navigation on Virtual Private Network, Algorithms Used, Security Level And Speed, Secure Socket Tunnelling Protocol. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Criteria To Select Best Data Storage Encryption Method
Encryption Implementation Strategies Criteria To Select Best Data Storage Encryption MethodThis slide represents a guide to analyze the need for data protection in an organization. The criteria used to select the best data storage encryption method involves several factors such as security strength, performance impact, key management, compatibility, compliance, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Criteria To Select Best Data Storage Encryption Method. Dispense information and present a thorough explanation of Security Strength, Performance Impact, Key Management, Compatibility And Compliance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Data Confidentiality Using End To End Encryption
Encryption Implementation Strategies Data Confidentiality Using End To End EncryptionThis slide illustrates the use of end-to-end encryption mechanism to maintain data confidentiality and secure digital ecosystems. The purpose of this slide is to demonstrate how data can be transformed into an encrypted format to transmit it over a network. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Data Confidentiality Using End To End Encryption. Dispense information and present a thorough explanation of Data Confidentiality, Encryption Mechanism, Demonstrate, Digital Ecosystems using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Data Protection Technologies To Secure Information In Use
Encryption Implementation Strategies Data Protection Technologies To Secure Information In UseThis slide compares different data in use protection methods, and their working and associated cost. These methods are IDM Identity and Access Management, RBAC Role Based Access and conditional access, IRM Information Rights Management, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Data Protection Technologies To Secure Information In Use. Use it as a tool for discussion and navigation on Identity Management Tools, Digital Rights Protection, Data Protection Technologies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Data Security Concerns Faced By Company
Encryption Implementation Strategies Data Security Concerns Faced By CompanyThis slide discusses the security issues faced by the organization due to a lack of encryption and data protection technologies. These concerns are unauthorized access, data breaches, insider threats, malware and ransomware, phishing attacks, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Data Security Concerns Faced By Company. Dispense information and present a thorough explanation of Data Security Concerns, Phishing Attacks, Data Protection Technologies, Compliance And Regulations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Database Encryption Methods For Business Security
Encryption Implementation Strategies Database Encryption Methods For Business SecurityThis slide discusses the database encryption methods used to encrypt the data of different departments, such as finance, sales, and human resources. The database encryption levels are application-level encryption, plug-in method, TDE, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Database Encryption Methods For Business Security. Use it as a tool for discussion and navigation on Database Encryption Methods, Business Security, Sales And Human Resources. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Different States Of Data Which Requires Protection
Encryption Implementation Strategies Different States Of Data Which Requires ProtectionThis slide discusses various customer demands to ensure data privacy and authenticity. The purpose of this slide is to highlight the various states of data that require encryption, such as data-at-rest, data-in-transit, and data-in-use. Introducing Encryption Implementation Strategies Different States Of Data Which Requires Protection to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Customer Demands, Data Privacy And Authenticity, Require Encryption, Collaboration Software, using this template. Grab it now to reap its full benefits.
-
 Encryption Implementation Strategies Encryption As A Service Overview And Features
Encryption Implementation Strategies Encryption As A Service Overview And FeaturesThis slide discusses the Encryption-as-a-Service model of securing data using cryptographic techniques. This slide also outlines the characteristics of Encryption-as-a-Service, such as confidentiality, authentication, integrity, nonrepudiation, etc. Increase audience engagement and knowledge by dispensing information using Encryption Implementation Strategies Encryption As A Service Overview And Features. This template helps you present information on six stages. You can also present information on Text Message Encoding, Encryption Services, Subscription Packages, Data Encryption Security Solutions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Encryption Implementation Strategies Encryption As A Service Providers To Safeguard Network
Encryption Implementation Strategies Encryption As A Service Providers To Safeguard NetworkThis slide outlines the companies which provide EaaS services to secure data in a network. The purpose of this slide is to demonstrate the services and benefits of several EaaS providers such as CloudHesive, FortKnoxter, Hashicrop, Identos, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Encryption As A Service Providers To Safeguard Network. Dispense information and present a thorough explanation of Encryption As A Service, Safeguard Network Communication, Internal Revocation System using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Encryption Key Management Software For Byoe
Encryption Implementation Strategies Encryption Key Management Software For ByoeThe purpose of this slide is to demonstrate the importance of encryption key management EKM software. The key components included are encryption algorithm, customer master key, plaintext data key, encrypted data key, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Encryption Key Management Software For Byoe. Use it as a tool for discussion and navigation on Encryption Algorithm, Customer Master Key, Encrypted Data Key, Key Management Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Encryption Technologies To Secure Data At Rest
Encryption Implementation Strategies Encryption Technologies To Secure Data At RestThis slide compares different data protection methods, highlighting their advantages and limitations. These methods are full disk encryption, file-level encryption, database encryption, information rights management IRM, data leak prevention DLP,etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Encryption Technologies To Secure Data At Rest. Dispense information and present a thorough explanation of Information Rights Management, Data Leak Prevention, Full Disk Encryption, Cloud Access Security Brokers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Estimated Budget Of Data Encryption Implementation
Encryption Implementation Strategies Estimated Budget Of Data Encryption ImplementationThis slide represents the budget for securing data using encryption techniques. The purpose of this slide is to showcase the estimated and actual cost for installing cryptographic solutions. The components include hardware and software, maintenance and support, training, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Estimated Budget Of Data Encryption Implementation. Use it as a tool for discussion and navigation on Maintenance And Support, Deployment Team, Data Encryption, Estimated Cost. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies For Table Of Contents Ppt Ideas Templates
Encryption Implementation Strategies For Table Of Contents Ppt Ideas TemplatesIntroducing Encryption Implementation Strategies For Table Of Contents Ppt Ideas Templates to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Safeguard Network Communication, Encryption Key Management Software, Applications Of Encryption As A Service, using this template. Grab it now to reap its full benefits.
-
 Encryption Implementation Strategies Hardware And Software Tools For Full Disk Encryption
Encryption Implementation Strategies Hardware And Software Tools For Full Disk EncryptionThis slide demonstrates the two tools available for full disk encryption. These are hardware based full disk encryption such as self-encrypting drives SEDs and software based full disk encryption, which include Microsoft BitLocker or Apple FileVault. Increase audience engagement and knowledge by dispensing information using Encryption Implementation Strategies Hardware And Software Tools For Full Disk Encryption. This template helps you present information on two stages. You can also present information on Hardware And Software Tools, Full Disk Encryption, Microsoft Bitlocker, Apple Filevault using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Encryption Implementation Strategies High Level View Of Symmetric And Asymmetric Cle
Encryption Implementation Strategies High Level View Of Symmetric And Asymmetric CleThis slide demonstrates the enhanced view of symmetric and asymmetric column level encryption techniques. The key components of diagram illustrated in this slide are database master key, certificates, symmetric keys, asymmetric keys, data, etc. Introducing Encryption Implementation Strategies High Level View Of Symmetric And Asymmetric Cle to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Symmetric Method, Asymmetric Method, Asymmetric Column Level Encryption, Symmetric Column Level Encryption, using this template. Grab it now to reap its full benefits.
-
 Encryption Implementation Strategies Impact Of Encryption Implementation On Application Security
Encryption Implementation Strategies Impact Of Encryption Implementation On Application SecurityThis slide represents the various factors which showcase the improvement of application security after adopting encryption. The parameters discussed are data privacy, confidentiality, authentication, compliance, trust and reputation, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Impact Of Encryption Implementation On Application Security. Dispense information and present a thorough explanation of Confidentiality, Data Privacy, Trust And Reputation, Application Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Introduction To Fully Homomorphic Encryption Technology
Encryption Implementation Strategies Introduction To Fully Homomorphic Encryption TechnologyThe purpose of this slide is to provide a summary of the outcomes of regulatory compliance management strategies, such as avoid unnecessary legal issues, foster healthy competition, etc. It highlights their business impact and advantages to organizations. Present the topic in a bit more detail with this Encryption Implementation Strategies Introduction To Fully Homomorphic Encryption Technology. Use it as a tool for discussion and navigation on Encrypted Program Input Data, Encrypted Program Output, Decrypted Program Output, Trusted Data Storage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Key Components Of Internet Protocol Security
Encryption Implementation Strategies Key Components Of Internet Protocol SecurityThe purpose of this slide is to discuss the main components of internet protocol security IPsec architecture. These three components are encapsulating security payload ESP, authentication header AH, and internet key exchange IKE. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Key Components Of Internet Protocol Security. Dispense information and present a thorough explanation of Data Integrity, Encryption, Anti Replay, Payload Authentication using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Key Considerations For Selecting File Encryption Software
Encryption Implementation Strategies Key Considerations For Selecting File Encryption SoftwareThis slide represents a guide for selecting a file encryption software based on several key factors. These considerations are threat analysis, encryption layers, training needs, compatibility, encryption scope, vendors incident response plan, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Key Considerations For Selecting File Encryption Software. Use it as a tool for discussion and navigation on Encryption Software, Training Needs, Compatibility, Encryption Scope, Training Timelines. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies List Of Symmetric And Asymmetric Encryption Algorithms
Encryption Implementation Strategies List Of Symmetric And Asymmetric Encryption AlgorithmsThis slide outlines several data encryption algorithms. The purpose of this slide is to divide all available cryptographic algorithms into two types of encryption, namely symmetric and asymmetric. These algorithms are 3DES encryption, Twofish encryption, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies List Of Symmetric And Asymmetric Encryption Algorithms. Dispense information and present a thorough explanation of Data Encryption Standard, Triple Data Encryption Standard, Digital Signature Algorithm, Elliptic Curve Cryptography using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Microsoft Full Disk Encryption Bitlocker
Encryption Implementation Strategies Microsoft Full Disk Encryption BitlockerThis slide discusses the full disk windows encryption technique provided by Microsoft, known as BitLocker. The purpose of this slide is to outline the step-by-step process to enable the BitLocker encryption in computer system. Increase audience engagement and knowledge by dispensing information using Encryption Implementation Strategies Microsoft Full Disk Encryption Bitlocker. This template helps you present information on nine stages. You can also present information on Microsoft Full Disk Encryption, Disc Characteristics, Trusted Platform Module, Automatically Be Encrypted using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Encryption Implementation Strategies Organizational Compliance Regulations For Information Security
Encryption Implementation Strategies Organizational Compliance Regulations For Information SecurityThe purpose of this slide is to summarize the most common regulations that organizations need to comply with, and their requirements. These regulations are HIPAA Health Insurance Portability and Accountability Act, SOX, PCI DSS, breach laws in all US states, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Organizational Compliance Regulations For Information Security. Use it as a tool for discussion and navigation on Health Insurance Portability, Accountability Act, Payment Card Industry, Data Security Standard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Outcomes Of Regulatory Compliance Management Strategies
Encryption Implementation Strategies Outcomes Of Regulatory Compliance Management StrategiesThe purpose of this slide is to provide a summary of the outcomes of regulatory compliance management strategies, such as avoid unnecessary legal issues, foster healthy competition, etc. It highlights their business impact and advantages to organizations. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Outcomes Of Regulatory Compliance Management Strategies. Dispense information and present a thorough explanation of Foster Healthy Competition, Gain Better Branding, Regulatory Compliance, Management Strategies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Overview Of Encryption For Securing Data In Use
Encryption Implementation Strategies Overview Of Encryption For Securing Data In UseThe purpose of this slide is to outline the different possible ways of protecting data in use. The methods include IDM Identity and Access Management, RBAC Role Based Access and conditional access, IRM Information Rights Management, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Overview Of Encryption For Securing Data In Use. Dispense information and present a thorough explanation of Information Rights Management, Encryption For Securing Data, Role Based Access using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Public And Private Keys For End To End Encryption
Encryption Implementation Strategies Public And Private Keys For End To End EncryptionThis slide discusses the utilization of asymmetric public key encryption technique to provide E2EE. The purpose of this slide is to explain how client-side encryption employs public and private keys to encrypt the message before transmission. Present the topic in a bit more detail with this Encryption Implementation Strategies Public And Private Keys For End To End Encryption. Use it as a tool for discussion and navigation on Public And Private Keys, Encryption Employs, Encryption Technique, Server Transmitting And Storing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Roadmap To Encrypt Application Data Of Organization
Encryption Implementation Strategies Roadmap To Encrypt Application Data Of OrganizationThis slide represents the roadmap to implement encryption security in an organization. The main components included are are identify sensitive data, assess encryption requirements, choose encryption algorithms, implement data encryption at rest, etc. Introducing Encryption Implementation Strategies Roadmap To Encrypt Application Data Of Organization to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Encryption Security, Identify Sensitive Data, Assess Encryption Requirements, Encryption Algorithms, Implement Data Encryption, using this template. Grab it now to reap its full benefits.
-
 Encryption Implementation Strategies Secure Socket Layer SSL Security Technology
Encryption Implementation Strategies Secure Socket Layer SSL Security TechnologyThe purpose of this slide is to explain the role of HTTPS and the secure sockets layer SSL protocol for secure connections. This slide also discusses the incorporation of symmetric and asymmetric encryption during the SSL handshake process. Present the topic in a bit more detail with this Encryption Implementation Strategies Secure Socket Layer SSL Security Technology. Use it as a tool for discussion and navigation on Secure Socket Layer, Security Technology, Symmetric And Asymmetric Encryption, Protocol For Secure Connections. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Secure Socket Shell Encryption Protocol
Encryption Implementation Strategies Secure Socket Shell Encryption ProtocolThis slide represents the working process of SSH Secure Socket Shell protocol to secure data sharing between unsecured networks. This slide also illustrates the before and after scenario of using SSH protocol for data encryption. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Secure Socket Shell Encryption Protocol. Dispense information and present a thorough explanation of Secure Socket Shell, Encryption Protocol, Unsecured Networks, Protocol For Data Encryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Security Protocols Required According To Type Of Network
Encryption Implementation Strategies Security Protocols Required According To Type Of NetworkThe purpose of this slide is to outline different security protocols used in various types of networks, and their specific applications. These network types are wired, wireless networks, Local Area Networks LANs, Wide Area Networks WANs, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Security Protocols Required According To Type Of Network. Use it as a tool for discussion and navigation on Local Area Networks, Wide Area Networks, Wired Networks, Wireless Networks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Selecting VPN Protocols For Different Use Cases
Encryption Implementation Strategies Selecting VPN Protocols For Different Use CasesThe purpose of this slide is to demonstrate a reference guide for most suitable VPN protocol selection based on specific use cases and their corresponding requirements. These use cases are streaming, downloads, gaming and privacy. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Selecting VPN Protocols For Different Use Cases. Dispense information and present a thorough explanation of Demonstrate A Reference Guide, Corresponding Requirements, Streaming, Gaming And Privacy using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Steps Followed By Internet Protocol Security Connections
Encryption Implementation Strategies Steps Followed By Internet Protocol Security ConnectionsThe purpose of this slide is to outline the working steps of internet protocol security connections. These are key exchange, packet headers and trailers, packet authentication, encryption, data transmission and decryption of data packets. Present the topic in a bit more detail with this Encryption Implementation Strategies Steps Followed By Internet Protocol Security Connections. Use it as a tool for discussion and navigation on Protocol Security Connections, Packet Authentication, Encryption, Data Transmission, Decryption Of Data Packets. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Steps For Quantum Safe Certificate Migration
Encryption Implementation Strategies Steps For Quantum Safe Certificate MigrationThis slide demonstrates the process of replicating the old certificates with quantum-safe certificates. The steps included are quantum-safe PKI, update servers cryptography, update clients cryptography, install QS roots, install QS certificates, and deprecate old cryptography. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Steps For Quantum Safe Certificate Migration. Dispense information and present a thorough explanation of Quantum Safe Certificate Migration, Deprecate Old Cryptography, Support Recent Algorithms using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





