Powerpoint Templates and Google slides for Eliminating Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Effective security monitoring plan to eliminate cyber threats and data breaches complete deck
Effective security monitoring plan to eliminate cyber threats and data breaches complete deckEnthrall your audience with this Effective Security Monitoring Plan To Eliminate Cyber Threats And Data Breaches Complete Deck. Increase your presentation threshold by deploying this well crafted template. It acts as a great communication tool due to its well researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention grabber. Comprising fourty four slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Opsec Cyber Security To Eliminate Business Risks
Opsec Cyber Security To Eliminate Business RisksThis slide showcases the multiple threats eliminated by opsec cybersecurity measures. This slide aims to help the business understand the importance of opsec security measures. It includes elements such as third party risks, social engineering, etc. Introducing our premium set of slides with Opsec Cyber Security To Eliminate Business Risks. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Social Engineering,Patch Management,Malware And Ransomware. So download instantly and tailor it with your information.
-
 Threats Eliminated By Hids Cyber Security
Threats Eliminated By Hids Cyber SecurityThis slide represents threats eliminated by HIDS cyber security which detects suspicious activities and generates alerts when they are detected. It includes threats eliminated by HIDS cyber security such as malicious attacks, asymmetric routing, etc. Presenting our set of slides with Threats Eliminated By Hids Cyber Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Malicious Attacks, Asymmetric Routing, Buffer Overflow Attacks.
-
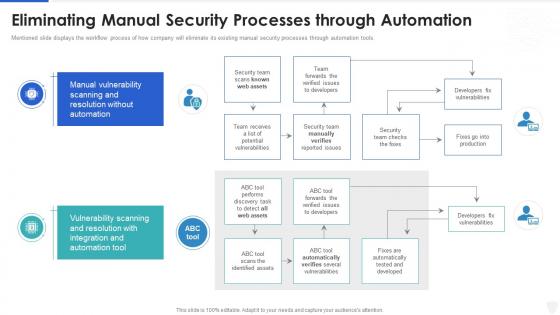
 Eliminating manual security processes managing cyber risk in a digital age
Eliminating manual security processes managing cyber risk in a digital ageMentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Present the topic in a bit more detail with this Eliminating Manual Security Processes Managing Cyber Risk In A Digital Age. Use it as a tool for discussion and navigation on Vulnerability, Scanning, Resolution, Team. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Program Eliminating Manual Security Processes Through Automation
Information Security Program Eliminating Manual Security Processes Through AutomationMentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Deliver an outstanding presentation on the topic using this Information Security Program Eliminating Manual Security Processes Through Automation. Dispense information and present a thorough explanation of Processes, Automation, Vulnerabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Eliminating Manual Security Processes Through Automation Risk Based Methodology To Cyber
Eliminating Manual Security Processes Through Automation Risk Based Methodology To CyberMentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools.Present the topic in a bit more detail with this Eliminating Manual Security Processes Through Automation Risk Based Methodology To Cyber Use it as a tool for discussion and navigation on Manual Vulnerability, Scanning And Resolution, Vulnerability Scanning This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Eliminating Manual Security Introducing A Risk Based Approach To Cyber Security
Eliminating Manual Security Introducing A Risk Based Approach To Cyber SecurityMentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools.Present the topic in a bit more detail with this Eliminating Manual Security Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on Manual Vulnerability, Scanning And Resolution, Automation Vulnerability This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity and digital business risk management eliminating manual security processes
Cybersecurity and digital business risk management eliminating manual security processesMentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Present the topic in a bit more detail with this Cybersecurity And Digital Business Risk Management Eliminating Manual Security Processes. Use it as a tool for discussion and navigation on Processes, Resolution, Automation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Infra Security Icon For Eliminating Cyber Threats
Infra Security Icon For Eliminating Cyber ThreatsIncrease audience engagement and knowledge by dispensing information using Infra Security Icon For Eliminating Cyber Threats. This template helps you present information on four stages. You can also present information on Infra Security, Icon Eliminating, Cyber Threats using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 It Infra Security Model To Eliminate Unauthorized User Access
It Infra Security Model To Eliminate Unauthorized User AccessThe following slide exhibits model for IT infrastructure security in order to determine tools that provide in depth defence. It presents information related to perimeter, endpoint, visibility, etc. Introducing It Infra Security Model To Eliminate Unauthorized User Access to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Perimeter, Application, Identify, using this template. Grab it now to reap its full benefits.
-
 Worker Participation To Eliminate Safety Risks Best Practices For Workplace Security
Worker Participation To Eliminate Safety Risks Best Practices For Workplace SecurityThis slide highlights the worker participation to remove safety risks which includes motivate workers for participation, report safety concerns, provide information access to workers and eliminate participation barrier.Increase audience engagement and knowledge by dispensing information using Worker Participation To Eliminate Safety Risks Best Practices For Workplace Security. This template helps you present information on four stages. You can also present information on Eliminate Participation, Provide Information, Report Safety Concerns using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Smart Home Security Steps To Eliminate Threat
Smart Home Security Steps To Eliminate ThreatThis side showcase the steps to reduce the threats of smart home by creating solid defense for burglary and provides cybersecurity. It includes key elements such as door security, window reinforcement, save energy, garage protection and cybersecurity.Presenting our set of slides with Smart Home Security Steps To Eliminate Threat. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Door Security, Garage Protection, Customized Security.
-
 Secured debt elimination ppt powerpoint presentation layouts shapes cpb
Secured debt elimination ppt powerpoint presentation layouts shapes cpbPresenting this set of slides with name Secured Debt Elimination Ppt Powerpoint Presentation Layouts Shapes Cpb. This is an editable Powerpoint seven stages graphic that deals with topics like Secured Debt Elimination to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Blockchain security system framework for eliminating vulnerabilities
Blockchain security system framework for eliminating vulnerabilitiesIntroducing our premium set of slides with Blockchain Security System Framework For Eliminating Vulnerabilities. Elucidate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Security, Risk Control Mechanisms, Application System Security. So download instantly and tailor it with your information.
-
 Use cases of blockchain security for threat elimination
Use cases of blockchain security for threat eliminationPresenting our set of slides with name Use Cases Of Blockchain Security For Threat Elimination. This exhibits information on six stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Decentralized Data Storage, Security Alerts, Distribution.
-
 Icons slide for effective security monitoring plan to eliminate cyber threats and data breaches
Icons slide for effective security monitoring plan to eliminate cyber threats and data breachesIntroducing our well researched set of slides titled Icons Slide For Effective Security Monitoring Plan To Eliminate Cyber Threats And Data Breaches. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Strategic Solutions To Eliminate Prevailing Implementing Organizational Security Training
Strategic Solutions To Eliminate Prevailing Implementing Organizational Security TrainingThe slide showcases strategic solutions used by various companies to eliminate cyber attacks or cloud security attacks in the organization. It includes reporting of attacks, software engineer training, etc. Present the topic in a bit more detail with this Strategic Solutions To Eliminate Prevailing Implementing Organizational Security Training. Use it as a tool for discussion and navigation on Employee Security Awareness Training, Incident Evaluation Team, Identify And Mitigate Risks. This template is free to edit as deemed fit for your organization. Therefore download it now.



