Powerpoint Templates and Google slides for Data security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
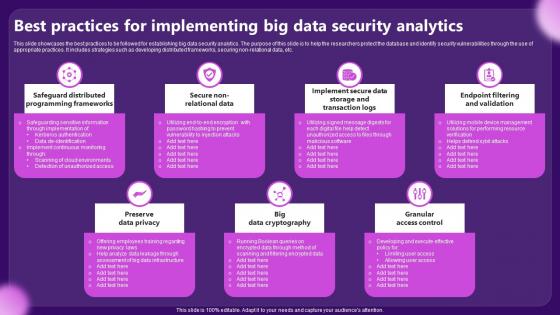 Best Practices For Implementing Big Data Security Analytics
Best Practices For Implementing Big Data Security AnalyticsThis slide showcases the best practices to be followed for establishing big data security analytics. The purpose of this slide is to help the researchers protect the database and identify security vulnerabilities through the use of appropriate practices. It includes strategies such as developing distributed frameworks, securing non relational data, etc. Presenting our set of slides with Best Practices For Implementing Big Data Security Analytics. This exhibits information on seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Preserve Data Privacy, Granular Access Control.
-
 Big Data Analytics Security Icon
Big Data Analytics Security IconIntroducing our Big Data Analytics Security Icon set of slides. The topics discussed in these slides are Big Data Analytics Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Big Data Security Analytics Ppt Powerpoint Presentation Infographics Format
Big Data Security Analytics Ppt Powerpoint Presentation Infographics FormatPresenting our well structured Big Data Security Analytics Ppt Powerpoint Presentation Infographics Format. The topics discussed in this slide are Big Data Security Analytics.This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Challenges And Solutions To Big Data Analytics Security
Challenges And Solutions To Big Data Analytics SecurityThis slide highlights the various challenges faced while safeguarding big data analytics. This slide aims to help business analysts in determining issues with the security of big data analytics and overcome them through the solutions provided. Introducing our Challenges And Solutions To Big Data Analytics Security set of slides. The topics discussed in these slides are Difficulty Storing Data, Presence Of Fake Data. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
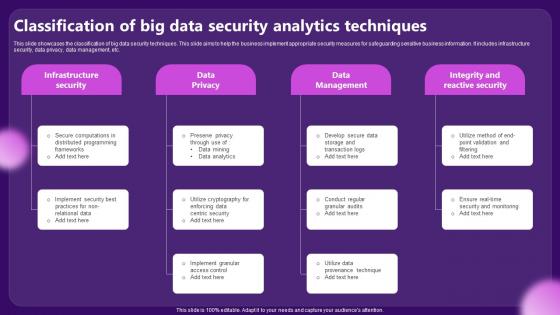 Classification Of Big Data Security Analytics Techniques
Classification Of Big Data Security Analytics TechniquesThis slide showcases the classification of big data security techniques. This slide aims to help the business implement appropriate security measures for safeguarding sensitive business information. It includes infrastructure security, data privacy, data management, etc. Presenting our set of slides with Classification Of Big Data Security Analytics Techniques. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Infrastructure Security, Data Management.
-
 Encryption Techniques Icon For Securing Big Data Analytics
Encryption Techniques Icon For Securing Big Data AnalyticsIntroducing our Encryption Techniques Icon For Securing Big Data Analytics set of slides. The topics discussed in these slides are Encryption Techniques, Securing Big Data Analytics. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
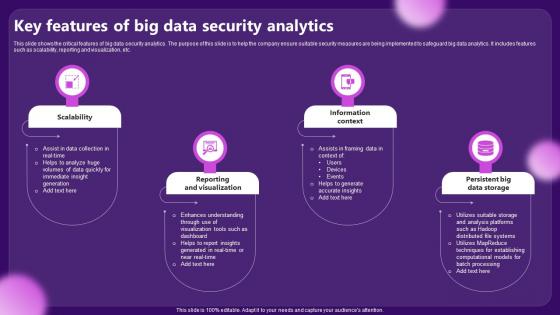 Key Features Of Big Data Security Analytics
Key Features Of Big Data Security AnalyticsThis slide shows the critical features of big data security analytics. The purpose of this slide is to help the company ensure suitable security measures are being implemented to safeguard big data analytics. It includes features such as scalability, reporting and visualization, etc. Presenting our set of slides with Key Features Of Big Data Security Analytics. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Scalability, Information Context.
-
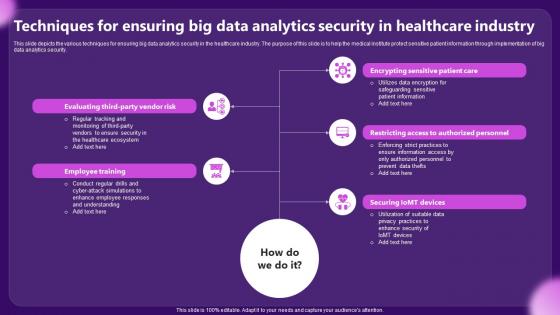 Techniques For Ensuring Big Data Analytics Security In Healthcare Industry
Techniques For Ensuring Big Data Analytics Security In Healthcare IndustryThis slide depicts the various techniques for ensuring big data analytics security in the healthcare industry. The purpose of this slide is to help the medical institute protect sensitive patient information through implementation of big data analytics security. Presenting our set of slides with Techniques For Ensuring Big Data Analytics Security In Healthcare Industry. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Employee Training, Securing Iomt Devices.
-
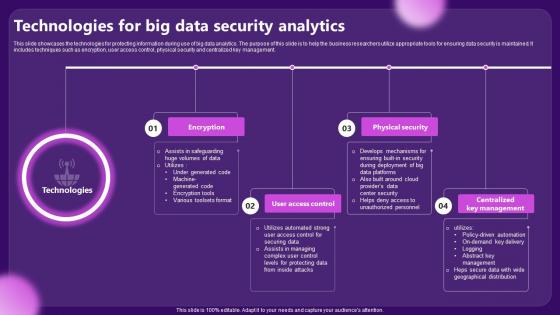 Technologies For Big Data Security Analytics
Technologies For Big Data Security AnalyticsThis slide showcases the technologies for protecting information during use of big data analytics. The purpose of this slide is to help the business researchers utilize appropriate tools for ensuring data security is maintained. It includes techniques such as encryption, user access control, physical security and centralized key management. Introducing our premium set of slides with Technologies For Big Data Security Analytics. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Encryption, Physical Security. So download instantly and tailor it with your information.
-
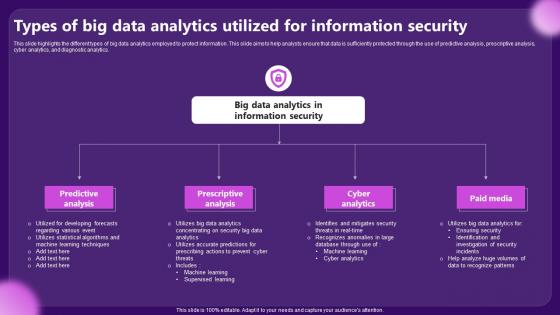 Types Of Big Data Analytics Utilized For Information Security
Types Of Big Data Analytics Utilized For Information SecurityThis slide highlights the different types of big data analytics employed to protect information. This slide aims to help analysts ensure that data is sufficiently protected through the use of predictive analysis, prescriptive analysis, cyber analytics, and diagnostic analytics. Presenting our set of slides with Types Of Big Data Analytics Utilized For Information Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Predictive Analysis, Prescriptive Analysis.
-
 Types Of Encryption For Securing Big Data Analytics
Types Of Encryption For Securing Big Data AnalyticsThis slide highlights the various types of encryption techniques utilized for protecting big data analytics. The purpose of this slide is to help the business safeguard sensitive information for preventing data breaches and information thefts. It includes quantum proof encryption, homomorphic encryption, etc. Introducing our premium set of slides with Types Of Encryption For Securing Big Data Analytics. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Homomorphic Encryption, Differential Privacy. So download instantly and tailor it with your information.
-
 Use Cases Of Big Data Security Analytics
Use Cases Of Big Data Security AnalyticsThis slide depicts the use cases of utilizing bug data security analytics. This slide aims to help the business utilize security analytics to safeguard information and prevent data thefts and information leaks. It includes instances like cloud security monitoring, user behavior analysis, etc. Presenting our set of slides with Use Cases Of Big Data Security Analytics. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cloud Security Monitoring, Insider Threat Detection.
-
 Key Components Of Data Security Breach Management Plan
Key Components Of Data Security Breach Management PlanThis slide showcases the critical components of a business security breach management plan. This slide aims to help the business effectively manage a data security breach to prevent financial loss, market share loss, or reputational damage.Introducing our premium set of slides with Key Components Of Data Security Breach Management Plan. Ellicudate the seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Prevent Identity, Credit Report Monitoring, Review Security Measures. So download instantly and tailor it with your information.
-
 Cyber Security Data Capture Plan Icon
Cyber Security Data Capture Plan IconIntroducing our premium set of slides with Cyber Security Data Capture Plan Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data, Capture, Security. So download instantly and tailor it with your information.
-
 Corporate Data Security Policy In Powerpoint And Google Slides Cpb
Corporate Data Security Policy In Powerpoint And Google Slides CpbPresenting our Corporate Data Security Policy In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Corporate Data Security Policy This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Impact Of Encryption Implementation On Cloud Security Cloud Data Encryption
Impact Of Encryption Implementation On Cloud Security Cloud Data EncryptionThis slide represents the various factors that showcase the improvement of application security after adopting encryption. The parameters discussed are unauthorized access, data breaches, malware and ransomware, phishing attacks, etc. Deliver an outstanding presentation on the topic using this Impact Of Encryption Implementation On Cloud Security Cloud Data Encryption. Dispense information and present a thorough explanation of Unauthorized Access, Data Breaches using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Timeline For Cloud Data Security Implementation Cloud Data Encryption
Timeline For Cloud Data Security Implementation Cloud Data EncryptionThis slide represents the timeline to implement cloud data encryption in an organization. The main components included are determine sensitive data and required encryption technique, choose a cloud service provider, implement encryption solution in cloud, etc. Introducing Timeline For Cloud Data Security Implementation Cloud Data Encryption to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Test Encryption Solutions, Implement Encryptions Solution, using this template. Grab it now to reap its full benefits.
-
 Secured Data Protection For Online Security System Icon
Secured Data Protection For Online Security System IconPresenting our set of slides with Secured Data Protection For Online Security System Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Secured Data Protection, Online Security System Icon.
-
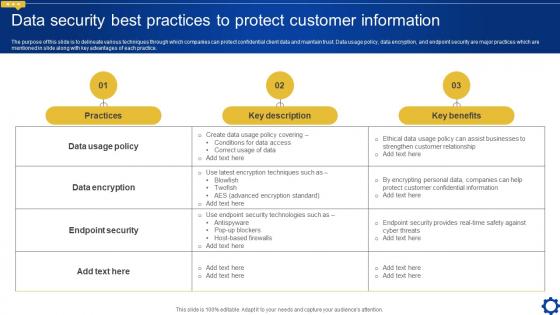 Data Security Best Practices To Protect Customer Creating Personalized Marketing Messages MKT SS V
Data Security Best Practices To Protect Customer Creating Personalized Marketing Messages MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Present the topic in a bit more detail with this Data Security Best Practices To Protect Customer Creating Personalized Marketing Messages MKT SS V. Use it as a tool for discussion and navigation on Practices, Key Description, Key Benefits. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Security Best Practices To Developing Targeted Marketing Campaign MKT SS V
Data Security Best Practices To Developing Targeted Marketing Campaign MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Increase audience engagement and knowledge by dispensing information using Data Security Best Practices To Developing Targeted Marketing Campaign MKT SS V. This template helps you present information on four stages. You can also present information on Policy, Encryption, Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Data Security Software In Powerpoint And Google Slides Cpb
Cloud Data Security Software In Powerpoint And Google Slides CpbPresenting Cloud Data Security Software In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cloud Data Security Software. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
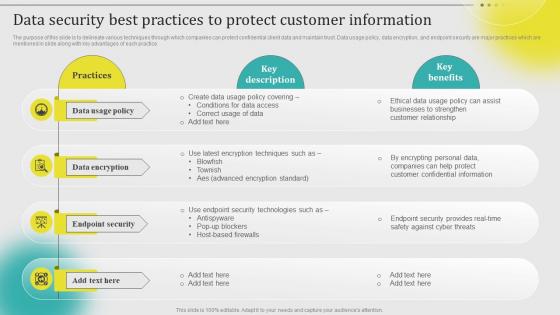 Data Security Best Practices To Protect Customer Information Leveraging Customer Data MKT SS V
Data Security Best Practices To Protect Customer Information Leveraging Customer Data MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Introducing Data Security Best Practices To Protect Customer Information Leveraging Customer Data MKT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Data Usage Policy, Data Encryption, Endpoint Security, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB V2 Comparison Between CASB And Data Loss Prevention DLP
Cloud Access Security Broker CASB V2 Comparison Between CASB And Data Loss Prevention DLPThis slide describes the difference between Cloud Access Security Broker and data loss prevention. This slide highlights the main comparisons between CASB and DLP systems based on their purpose, focus area, use cases, key features, implementation and relationship. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Comparison Between CASB And Data Loss Prevention DLP. Dispense information and present a thorough explanation of Content Inspection, Data Classification, Encryption, Access Control using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 Pillar Data Security Ppt Icon Backgrounds
Cloud Access Security Broker CASB V2 Pillar Data Security Ppt Icon BackgroundsThis slide talks about the data security pillar of the Cloud Access Security Broker pillar. This slide highlights how CASB data security can help organizations improve their IT requirements and business operations and detect security breaches before they happen. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Pillar Data Security Ppt Icon Backgrounds. This template helps you present information on four stages. You can also present information on Document Fingerprinting, Data Security Pillar, Cloud Access Security Broker Pillar using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Employee Data Security Compliance Icon
Employee Data Security Compliance IconPresenting our set of slides with Employee Data Security Compliance Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Employee Data, Security Compliance.
-
 Data Security Best Practices To Protect Complete Introduction To Database MKT SS V
Data Security Best Practices To Protect Complete Introduction To Database MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Increase audience engagement and knowledge by dispensing information using Data Security Best Practices To Protect Complete Introduction To Database MKT SS V. This template helps you present information on four stages. You can also present information on Policy, Encryption, Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Encryption Implementation Strategies Data Protection Technologies To Secure Information In Use
Encryption Implementation Strategies Data Protection Technologies To Secure Information In UseThis slide compares different data in use protection methods, and their working and associated cost. These methods are IDM Identity and Access Management, RBAC Role Based Access and conditional access, IRM Information Rights Management, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Data Protection Technologies To Secure Information In Use. Use it as a tool for discussion and navigation on Identity Management Tools, Digital Rights Protection, Data Protection Technologies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Data Security Concerns Faced By Company
Encryption Implementation Strategies Data Security Concerns Faced By CompanyThis slide discusses the security issues faced by the organization due to a lack of encryption and data protection technologies. These concerns are unauthorized access, data breaches, insider threats, malware and ransomware, phishing attacks, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Data Security Concerns Faced By Company. Dispense information and present a thorough explanation of Data Security Concerns, Phishing Attacks, Data Protection Technologies, Compliance And Regulations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Encryption Technologies To Secure Data At Rest
Encryption Implementation Strategies Encryption Technologies To Secure Data At RestThis slide compares different data protection methods, highlighting their advantages and limitations. These methods are full disk encryption, file-level encryption, database encryption, information rights management IRM, data leak prevention DLP,etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Encryption Technologies To Secure Data At Rest. Dispense information and present a thorough explanation of Information Rights Management, Data Leak Prevention, Full Disk Encryption, Cloud Access Security Brokers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Overview Of Encryption For Securing Data In Use
Encryption Implementation Strategies Overview Of Encryption For Securing Data In UseThe purpose of this slide is to outline the different possible ways of protecting data in use. The methods include IDM Identity and Access Management, RBAC Role Based Access and conditional access, IRM Information Rights Management, etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Overview Of Encryption For Securing Data In Use. Dispense information and present a thorough explanation of Information Rights Management, Encryption For Securing Data, Role Based Access using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Technologies To Secure Data In Transit Encryption Implementation Strategies
Encryption Technologies To Secure Data In Transit Encryption Implementation StrategiesThis slide compares different data in transit protection methods, including their working and associated cost. These methods are email encryption, Managed File Transfer MFT, Data Leak Prevention DLP, Cloud Access Security Brokers CASB, etc. Deliver an outstanding presentation on the topic using this Encryption Technologies To Secure Data In Transit Encryption Implementation Strategies. Dispense information and present a thorough explanation of Managed File Transfer, Cloud Access Security Brokers, Email Encryption, Encryption Technologies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Overview Of Encryption For Securing Data At Rest Encryption Implementation Strategies
Overview Of Encryption For Securing Data At Rest Encryption Implementation StrategiesThis slide represents the different possible ways of protecting data at rest. The storage methods include file servers, network shares, document management systems, external storage, databases, endpoint devices, mobile devices, cloud storage, etc. Present the topic in a bit more detail with this Overview Of Encryption For Securing Data At Rest Encryption Implementation Strategies. Use it as a tool for discussion and navigation on Database Encryption, Information Rights Management, Data Leak Prevention, Mobile Device Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview Of Encryption For Securing Data In Transit Encryption Implementation Strategies
Overview Of Encryption For Securing Data In Transit Encryption Implementation StrategiesThis slide represents the different possible ways of protecting data in transit. The methods include email encryption, MFT Managed File Transfer, IRM Information Rights Management, CASB Cloud Access Security Brokers, and DLP Data Leak Prevention. Deliver an outstanding presentation on the topic using this Overview Of Encryption For Securing Data In Transit Encryption Implementation Strategies. Dispense information and present a thorough explanation of Information Rights Management, Data Leak Prevention, Cloud Access Security Brokers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Security Best Practices To Protect Customer Database Marketing Strategies MKT SS V
Data Security Best Practices To Protect Customer Database Marketing Strategies MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Introducing Data Security Best Practices To Protect Customer Database Marketing Strategies MKT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Data Usage Policy, Data Encryption, using this template. Grab it now to reap its full benefits.
-
 IT Audit Evaluation Icon For Data Security
IT Audit Evaluation Icon For Data SecurityIntroducing our premium set of slides with IT Audit Evaluation Icon For Data Security. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like IT Audit, Evaluation Icon, Data Security. So download instantly and tailor it with your information.
-
 Use Case Of Splunk Big Data For Security Intelligence
Use Case Of Splunk Big Data For Security IntelligenceFollowing slide showcases uses of splunk big data for security management. The purpose of this slide is to help businesses in investigating threats and improving compliance. It includes elements such as security monitoring, incident reporting, etc. Presenting our set of slides with Use Case Of Splunk Big Data For Security Intelligence This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Monitoring, Compliance.
-
 Blockchain Technology For Securing IoT Data How IoT Technology Is Transforming IoT SS
Blockchain Technology For Securing IoT Data How IoT Technology Is Transforming IoT SSThe following slide showcases solutions to overcome Internet of Things IoT security challenges faced by mining companies. Information covered in this slide is related to secure data sharing, improved compliance and safety, secure transactions and payments.Introducing Blockchain Technology For Securing IoT Data How IoT Technology Is Transforming IoT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Secure Data Sharing, Blockchain Technology, Enables Execution, using this template. Grab it now to reap its full benefits.
-
 Data Security People In Powerpoint And Google Slides Cpb
Data Security People In Powerpoint And Google Slides CpbPresenting our Data Security People In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Data Security People This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Strategic Plan To Implement Data Encryption Model For Effective Information Security Strategy SS V
Strategic Plan To Implement Data Encryption Model For Effective Information Security Strategy SS VThis slide represents data encryption model for effective information security. It includes data encoding, data decoding, backup repository etc. Present the topic in a bit more detail with this Strategic Plan To Implement Data Encryption Model For Effective Information Security Strategy SS V Use it as a tool for discussion and navigation on Employee Headcount, Average Employee Age, Gender Diversity Ratio This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS V
Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS VThis slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc. Introducing Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS V to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Incident Management, Request Fulfillment using this template. Grab it now to reap its full benefits.
-
 Secure Crime Data File Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Secure Crime Data File Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful PowerPoint icon is perfect for any presentation on crime. It features a magnifying glass and a fingerprint, representing the investigative process. It is ideal for law enforcement, legal and security topics, as well as any discussion on crime.
-
 Secure Crime Data File Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Secure Crime Data File Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone powerpoint icon is perfect for presentations on crime files. It features a magnifying glass and a fingerprint, representing the investigative process. It is a high quality vector graphic, making it ideal for use in any professional setting.
-
 Data Encryption Secure Computer Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Encryption Secure Computer Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is a visual representation of secure computer. It is a modern, vibrant and eye catching icon that will help to create an impactful presentation. It is a great way to emphasize the importance of data security and safety.
-
 Data Encryption Secure Computer Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Encryption Secure Computer Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon is perfect for presentations on secure computer systems. It features a black and white design depicting a computer with a padlock, symbolizing the safety of your data. Use this icon to emphasize the importance of secure computing.
-
 Data Flow Diagram Of IoT Cyber Security Improving IoT Device Cybersecurity IoT SS
Data Flow Diagram Of IoT Cyber Security Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to display visual representation of internet of Things IoT security. The slide covers information about various IoT sensors, cloud for data collection, administration level, etc. Deliver an outstanding presentation on the topic using this Data Flow Diagram Of IoT Cyber Security Improving IoT Device Cybersecurity IoT SS. Dispense information and present a thorough explanation of Data, Security, Cyber using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IoT Cyber Security Technologies For Data Improving IoT Device Cybersecurity IoT SS
IoT Cyber Security Technologies For Data Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to showcase various types of Internet of Things IoT security technologies which can assist companies in safeguarding customer data. Blockchain, IoT security analytics, Zero Trust Architecture, and Edge Computing are the most trending technologies which are outlined in slide. Increase audience engagement and knowledge by dispensing information using IoT Cyber Security Technologies For Data Improving IoT Device Cybersecurity IoT SS. This template helps you present information on four stages. You can also present information on Devices, Architecture, Computing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Financial Data Security Services AI Image PowerPoint Presentation PPT ECS
Financial Data Security Services AI Image PowerPoint Presentation PPT ECSIntroducing a Visual PPT on Financial Data Security Services Each PPT Slide is a testament to the expertise of our Design Teams Craftsmen. Personalize the Google Slides compatible PowerPoint Slide with ease. Download the PPT, modify as you desire, and showcase it with poise.
-
 Secure Financial Data Management AI Image PowerPoint Presentation PPT ECS
Secure Financial Data Management AI Image PowerPoint Presentation PPT ECSIntroducing a Visual PPT on Secure Financial Data Management. Our Presentation Specialists have taken great care in designing each slide in this PowerPoint. Feel free to tailor the content. The PPT Template fits well with any screen size, and its also compatible with Google Slides. Download the PPT, and present it confidently.
-
 Cryptographic Algorithms Used In Data Security Cloud Cryptography
Cryptographic Algorithms Used In Data Security Cloud CryptographyThis slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm. Deliver an outstanding presentation on the topic using this Cryptographic Algorithms Used In Data Security Cloud Cryptography. Dispense information and present a thorough explanation of Cryptographic, Algorithms, Data Encryption Standard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Security In Cloud Computing Architecture Cloud Cryptography
Data Security In Cloud Computing Architecture Cloud CryptographyThis slide talks about the key components of working of a cloud cryptography system. The purpose of this slide is to explain the main steps involved in functioning of cloud cryptography. The techniques explained are data-in-transit, data-at-rest and legal and regulatory issues. Present the topic in a bit more detail with this Data Security In Cloud Computing Architecture Cloud Cryptography. Use it as a tool for discussion and navigation on Architecture, Cryptographic, Data Encryption. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breaches Cyber Security In Powerpoint And Google Slides Cpb
Data Breaches Cyber Security In Powerpoint And Google Slides CpbPresenting our Data Breaches Cyber Security In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Data Breaches Cyber Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Plan Useful Data Backup Schedule Improving Cyber Security Risks Management
Plan Useful Data Backup Schedule Improving Cyber Security Risks ManagementThe following slide showcases the monthly calendar for data backup to advance cybersecurity protection and loss of information. It mainly includes techniques such as fully and incremental data backup etc. Present the topic in a bit more detail with this Plan Useful Data Backup Schedule Improving Cyber Security Risks Management. Use it as a tool for discussion and navigation on Incremental Backup, Plan Useful, Data Backup Schedule. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Business Expansion And Data Security Strategy Icon
Business Expansion And Data Security Strategy IconIntroducing our premium set of slides with Business Expansion And Data Security Strategy Icon. Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Business Expansion, Data Security Strategy Icon. So download instantly and tailor it with your information.
-
 Key Strategies To Secure Business Data
Key Strategies To Secure Business DataThis slide showcase strategies that can be used for securing cyberattacks and target organizational data security and access. It includes updating devices, secure iot technology, track cloud storage, train employees and secure network access. Introducing our premium set of slides with Key Strategies To Secure Business Data. Ellicudate the Five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Updated Devices, Track Cloud Storage, Train Employees. So download instantly and tailor it with your information.
-
 Significant Data Security Measures For Business
Significant Data Security Measures For BusinessThis slide showcase different type of risk measure that are used by the organization for securing valuable data. It include strong password access, backup, technology updating and antivirus installation. Presenting our set of slides with Significant Data Security Measures For Business. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Strong Password Access, Antivirus Installation, Backups.
-
 Data Security Safety Information Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security Safety Information Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is perfect for conveying safety information in a visually appealing way. It features a bright yellow background with a black image of a safety helmet, clearly indicating the importance of safety. It is sure to draw attention and help your audience understand the importance of safety in any situation.
-
 Data Security Safety Information Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security Safety Information Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is perfect for highlighting safety information in presentations. It features a figure in a safety vest and hardhat, with a warning sign in the background. The icon is a great visual aid to emphasize the importance of safety in the workplace.
-
 Overview Of Business Ict Security For Data Comprehensive Guide For Deployment Strategy SS V
Overview Of Business Ict Security For Data Comprehensive Guide For Deployment Strategy SS VThis slide represents overview of ICT information and communication technology business security It covers types and features for security such as network security, endpoint security etc Present the topic in a bit more detail with this Overview Of Business Ict Security For Data Comprehensive Guide For Deployment Strategy SS V Use it as a tool for discussion and navigation on Unauthorized Sources, Factor Authentication, Organizations Information This template is free to edit as deemed fit for your organization Therefore download it now
-
 Impacts Of Cyber Security Data Compliance
Impacts Of Cyber Security Data ComplianceThis slide shows benefits of cyber security compliance which helps in aiming to protect sensitive data and maintain the integrity of information systems. It further includes benefits such as strengthening data protection etc. Presenting our set of slides with Impacts Of Cyber Security Data Compliance. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Strengthening Data Protection, Regulatory Compliance.
-
 Hr Employee Security Data Icon
Hr Employee Security Data IconIntroducing our premium set of slides with Hr Employee Security Data Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Data Icon, HR Employee. So download instantly and tailor it with your information.





