Powerpoint Templates and Google slides for Data security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Icon Showing Data Security Through Blockchain Technology In Supply Chain
Icon Showing Data Security Through Blockchain Technology In Supply ChainPresenting our well structured Icon Showing Data Security Through Blockchain Technology In Supply Chain. The topics discussed in this slide are Icon Showing Data Security, Blockchain Technology, Supply Chain. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Best Work From Home Data Security Practices Security Incident Response Playbook
Best Work From Home Data Security Practices Security Incident Response PlaybookPurpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc. Introducing Best Work From Home Data Security Practices Security Incident Response Playbook to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on System Update, Communication, External Devices, using this template. Grab it now to reap its full benefits.
-
 Data Backup Evaluation Sheet Security Incident Response Playbook Ppt Slides Background Image
Data Backup Evaluation Sheet Security Incident Response Playbook Ppt Slides Background ImageMentioned slide addresses evaluation sheet which can be used for assessing data backup activities. Sections covered in the sheet are backup testing frequency, type of backup solution and responsible person details. Present the topic in a bit more detail with this Data Backup Evaluation Sheet Security Incident Response Playbook Ppt Slides Background Image. Use it as a tool for discussion and navigation on Evaluation, Responsible, Solution. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Incident Response Playbook Checklist For Work From Home Data Security
Security Incident Response Playbook Checklist For Work From Home Data SecurityDeliver an outstanding presentation on the topic using this Security Incident Response Playbook Checklist For Work From Home Data Security. Dispense information and present a thorough explanation of Remote, Workstations, Encryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Security Handled By Cdn Cdn Edge Server Ppt Styles Graphics Design
Data Security Handled By Cdn Cdn Edge Server Ppt Styles Graphics DesignThis slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. Present the topic in a bit more detail with this Data Security Handled By Cdn Cdn Edge Server Ppt Styles Graphics Design. Use it as a tool for discussion and navigation on Certificates, Server, Resources. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Components Of Data Security And Privacy Policies
Key Components Of Data Security And Privacy PoliciesThe following slide depicts some elements of data security and privacy policies to communicate the relevance and purpose of collected data. It includes elements such as scan vulnerabilities, manage patches, response to incidents, monitor compliance etc. Presenting our set of slides with name Key Components Of Data Security And Privacy Policies. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Scan Vulnerabilities, Manage Patches, Response To Incidents.
-
 Key Strategies For Data Security And Privacy
Key Strategies For Data Security And PrivacyThe following slide showcases some techniques to ensure data security and privacy. It includes elements such as authentication, data encryption, network security, access controls etc. Introducing our premium set of slides with name Key Strategies For Data Security And Privacy. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Authentication, Network Security, Data Encryption, Access Controls. So download instantly and tailor it with your information.
-
 Online Data Security And Privacy Icon
Online Data Security And Privacy IconPresenting our set of slides with name Online Data Security And Privacy Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security And Privacy Icon, Online Data.
-
 Steps To Build Data Security And Privacy Plan
Steps To Build Data Security And Privacy PlanThe following slide showcases some steps to draft data safety and protection plan to gain user trust and confidence. It includes elements such as creating internal and external policy, implementation, responsibility, security vulnerabilities etc. Presenting our well structured Steps To Build Data Security And Privacy Plan. The topics discussed in this slide are Collect Relevant Information, Train Employees, New Policies. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Technologies To Ensure Data Security And Privacy
Technologies To Ensure Data Security And PrivacyThe following slide showcases some technologies to administer organizational data privacy and security concerns. It includes elements such as data encryption, change management and auditing, user and behavior analytics UEBA, backup and recovery etc. Introducing our premium set of slides with name Technologies To Ensure Data Security And Privacy. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Encryption, Change Management And Auditing, Backup And Recovery. So download instantly and tailor it with your information.
-
 Cloud Architecture And Security Review Data Complexity Slows Down The Business Process Multi Cloud
Cloud Architecture And Security Review Data Complexity Slows Down The Business Process Multi CloudThis slide covers the current complex multi cloud architecture with all their inherent complexity, fragility, and limitations that slow down the business process. Introducing Cloud Architecture And Security Review Data Complexity Slows Down The Business Process Multi Cloud to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Data Complexity, Slows Down The Business, Multi Cloud Architecture, using this template. Grab it now to reap its full benefits.
-
 Data Protection Multi Cloud Data Encryption Cloud Architecture And Security Review
Data Protection Multi Cloud Data Encryption Cloud Architecture And Security ReviewThis slide covers data protection and encryption framework in multi cloud with multi layer protection and data management. Increase audience engagement and knowledge by dispensing information using Data Protection Multi Cloud Data Encryption Cloud Architecture And Security Review. This template helps you present information on one stages. You can also present information on Object Store Appliance, Spectrum Protect, Multi Cloud Data Encryption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Protection And Information Security Policy And Procedure Staff Induction Training Guide
Data Protection And Information Security Policy And Procedure Staff Induction Training GuideThis slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. Present the topic in a bit more detail with this Data Protection And Information Security Policy And Procedure Staff Induction Training Guide. Use it as a tool for discussion and navigation on Applicable, Enforcement, Organization Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Security And Storage Environment Icon
Data Security And Storage Environment IconPresenting our set of slides with Data Security And Storage Environment Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Security, Storage Environment Icon.
-
 Data Security Threats Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security Threats Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Data security threats colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Data Security Threats Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security Threats Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Data security threats monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Data Folder Security Threats Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Folder Security Threats Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Data folder security threats colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Data Folder Security Threats Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Folder Security Threats Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Data folder security threats monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Data Security Lock Threats Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security Lock Threats Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Data security lock threats colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Data Security Lock Threats Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security Lock Threats Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Data security lock threats monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Enterprise Data Warehouse Framework To Ensure Data Security
Enterprise Data Warehouse Framework To Ensure Data SecurityThis slide covers enterprise data warehouse framework to ensure data security. It involves four steps such as data extraction, cleaning, conversion and storing of data. Presenting our well structured Enterprise Data Warehouse Framework To Ensure Data Security. The topics discussed in this slide are Extraction Of Data, Cleaning Of Data, Conversion Of Data. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Enterprise Data Warehouse To Ensure Security Icon
Enterprise Data Warehouse To Ensure Security IconPresenting our set of slides with Enterprise Data Warehouse To Ensure Security Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Enterprise Data Warehouse, Ensure Security Icon.
-
 Data Security And Protection Policy Framework
Data Security And Protection Policy FrameworkThis slide showcases policies covered in data protection and information security. The policies includes are BYOD, system security, information rights, PCI DSS, network security, etc. Presenting our well structured Data Security And Protection Policy Framework. The topics discussed in this slide are Data Policy Framework, Data Protection Policy, Information Security Policy. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Data Warehouse Security Policy And Procedure Icon
Data Warehouse Security Policy And Procedure IconIntroducing our Data Warehouse Security Policy And Procedure Icon set of slides. The topics discussed in these slides are Data Warehouse Security Policy, Procedure Icon. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data Security Handled By CDN Content Distribution Network Ppt Powerpoint Presentation File Example
Data Security Handled By CDN Content Distribution Network Ppt Powerpoint Presentation File ExampleThis slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults.Present the topic in a bit more detail with this Data Security Handled By CDN Content Distribution Network Ppt Powerpoint Presentation File Example. Use it as a tool for discussion and navigation on Defending Against, Perfect For Stopping, Dispersed Architecture. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Privacy Vs Data Security Information Privacy Ppt Powerpoint Presentation Summary Grid
Data Privacy Vs Data Security Information Privacy Ppt Powerpoint Presentation Summary GridThis slide compares data privacy with data security, indicating that security is concerned with safeguarding data, and privacy is about responsible data usage.Introducing Data Privacy Vs Data Security Information Privacy Ppt Powerpoint Presentation Summary Grid to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Privacy Concerned, Sensitive Information, Security Concerned, using this template. Grab it now to reap its full benefits.
-
 Cyber Data Security Risk Management Response
Cyber Data Security Risk Management ResponseThis slide covers the basic guidelines to mitigate cyber data security risks. It includes techniques such as no one size fits all solution, top management commitment and involvement of every member to identify loopholes in security processes. Introducing our premium set of slides with name Cyber Data Security Risk Management Response. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Top Management, Commitment, Legal Aspects, Organisation Workforce. So download instantly and tailor it with your information.
-
 Cyber Data Security Risk Management Response Process
Cyber Data Security Risk Management Response ProcessThis slide covers process to respond towards cyber data security risk. It includes steps such as preparation of incident response plan, detection of data compromises, analyse use of malicious tools, eradicate network threats, data recovery as the final step. Presenting our set of slides with name Cyber Data Security Risk Management Response Process. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Threats, Compromised Data, Data Compromises.
-
 Four Steps Of Cyber Security Data Breach Risk Process
Four Steps Of Cyber Security Data Breach Risk ProcessThis slide covers steps utilised to breach data. It includes stages such as probing, performing initial attack, expansion of attacks and data lifting. Introducing our premium set of slides with name Four Steps Of Cyber Security Data Breach Risk Process. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Initial Attack, Expanded Attack, Breach Risk Process. So download instantly and tailor it with your information.
-
 Data Protection And Information Security Policy And Procedure Corporate Induction Program For New Staff
Data Protection And Information Security Policy And Procedure Corporate Induction Program For New StaffThis slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. Introducing Data Protection And Information Security Policy And Procedure Corporate Induction Program For New Staff to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Protection, Information, Procedure, using this template. Grab it now to reap its full benefits.
-
 Business Data Security Management Model
Business Data Security Management ModelThis slide covers business data security management model which includes Defining, executing and measuring security controls. Introducing our Business Data Security Management Model set of slides. The topics discussed in these slides are Business Data, Security, Management Model. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Information System Security And Risk Administration Current Information And Data Security Capabilities Of Firm
Information System Security And Risk Administration Current Information And Data Security Capabilities Of FirmThis slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating. Deliver an outstanding presentation on the topic using this Information System Security And Risk Administration Current Information And Data Security Capabilities Of Firm. Dispense information and present a thorough explanation of Risk Management Functions, Required Standard Rating, Actual Standard Rating using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Protection And Information Security Policy New Employee Induction Programme
Data Protection And Information Security Policy New Employee Induction ProgrammeThis slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy.Increase audience engagement and knowledge by dispensing information using Data Protection And Information Security Policy New Employee Induction Programme. This template helps you present information on two stages. You can also present information on Information Confidentiality, Security Program, Ensure Necessary using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Securities Trading Platform Data Flow Diagram
Securities Trading Platform Data Flow DiagramThis slide displays a thorough data flow diagram that graphically illustrates the operations of a securities trading platform, as well as the sources and recipients of the information. It includes five processes such as open account, verify transaction, deposit cash, withdraw cash and place order. Presenting our well-structured Securities Trading Platform Data Flow Diagram. The topics discussed in this slide are Client, Broker, Place Order, Withdraw Cash. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Data In Powerpoint And Google Slides Cpb
Cyber Security Data In Powerpoint And Google Slides CpbPresenting Cyber Security Data In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cyber Security Data. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Data Protection And Information Security Policy Company Policies And Procedures Manual
Data Protection And Information Security Policy Company Policies And Procedures ManualThis slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. Increase audience engagement and knowledge by dispensing information using Data Protection And Information Security Policy Company Policies And Procedures Manual. This template helps you present information on one stage. You can also present information on Applicable, Enforcement, Policy And Procedures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Architecture Data Security In Powerpoint And Google Slides Cpb
Data Architecture Data Security In Powerpoint And Google Slides CpbPresenting our Data Architecture Data Security In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Data Architecture Data Security. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Enterprise Data Security Operation Center System
Enterprise Data Security Operation Center SystemThis slide covers enterprise data security operation center system to ensure better safety. It involves six stages collection, transmission, storage, processing, exchange and destruction. Presenting our set of slides with Enterprise Data Security Operation Center System. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Collection, Transmission, Processing .
-
 Threat Modeling Process For Secure Data Assets
Threat Modeling Process For Secure Data AssetsThis slide shows threat modeling to protect business assets from risks. It contains two phases discovery and implementation that includes steps such as identify assets, analyze attack surface, attack vectors, analyze, prioritize and develop controls. Introducing our premium set of slides with name Threat Modeling Process For Secure Data Assets. Ellicudate the two stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Hackers Path, Identified Assets, Threat Routes. So download instantly and tailor it with your information.
-
 Current Information And Data Security Cybersecurity Risk Analysis And Management Plan
Current Information And Data Security Cybersecurity Risk Analysis And Management PlanThis slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating Present the topic in a bit more detail with this Current Information And Data Security Cybersecurity Risk Analysis And Management Plan. Use it as a tool for discussion and navigation on Information, Capabilities, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Applications Of Data Masking Security Technology
Applications Of Data Masking Security TechnologyThis slide illustrates the multiple applications of data masking technology which helps to protect sensitive data by providing a functional alternative. Major elements include encryption, scrambling, nulling out, substitution, shuffling etc. Introducing our premium set of slides with Applications Of Data Masking Security Technology. Elucidate the seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Date Aging, Encryption, Scrambling, Nulling Out, Substitution. So download instantly and tailor it with your information.
-
 Business Data Encryption Security Technology
Business Data Encryption Security TechnologyThis slide highlights the role of encryption technology which is used by business and organisation to protect the confidentiality of digital data storage and transmission. Key components are authentication, privacy, regulatory compliance and security. Presenting our set of slides with name Business Data Encryption Security Technology. This exhibits information on four stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Privacy, Authentication, Regulatory Compliance, Security.
-
 Firewall Data Network Security Technology
Firewall Data Network Security TechnologyThe below slide highlights the benefit of using firewall security technology to ensure the safe connection over internet. Key elements include packet filtering, proxy service, unified threat management UTM, stateful inspection and next-generation firewall. Introducing our premium set of slides with Firewall Data Network Security Technology. Elucidate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Packet Filtering, Proxy Service, UTM, Stateful Inspection, Next Gen Firewall. So download instantly and tailor it with your information.
-
 Current Information And Data Security Capabilities Of Firm Formulating Cybersecurity Plan
Current Information And Data Security Capabilities Of Firm Formulating Cybersecurity PlanThis slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating. Deliver an outstanding presentation on the topic using this Current Information And Data Security Capabilities Of Firm Formulating Cybersecurity Plan. Dispense information and present a thorough explanation of Identify, Protect, Detect, Response using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best It And Data Security Practices
Best It And Data Security PracticesThe following slide highlights the best practices to protect the business from security threats. It includes activities such as installing and upgrading protective software, adopting strong password policy, applying multi layer authentication etc. Presenting our set of slides with Best It And Data Security Practices. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Make Regular Backups, Strong Password Policy, Protective Software.
-
 It Security And Data Safety Elements Icon
It Security And Data Safety Elements IconIntroducing our premium set of slides with It Security And Data Safety Elements Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security, Data Safety. So download instantly and tailor it with your information.
-
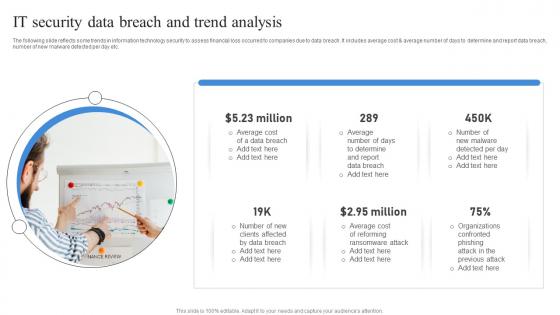 It Security Data Breach And Trend Analysis
It Security Data Breach And Trend AnalysisThe following slide reflects some trends in information technology security to assess financial loss occurred to companies due to data breach. It includes average cost and average number of days to determine and report data breach, number of new malware detected per day etc. Presenting our set of slides with It Security Data Breach And Trend Analysis. This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Data, Breach, Analysis.
-
 Key Statistics Of It Security And Data Breach
Key Statistics Of It Security And Data BreachThe following slide depicts some statistical insights of IT security to prevent data breaches and financial loss. It includes facts such as annual cost incurred due to malware, threats due to ransomware, previous year records of data breach etc. Presenting our well structured Key Statistics Of It Security And Data Breach. The topics discussed in this slide are Mobile, Data, Breach. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Secured Transactional Data Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Secured Transactional Data Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Secured transactional data colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Secured Transactional Data Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Secured Transactional Data Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Secured transactional data monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Best Work From Home Data Security Practices Cybersecurity Incident And Vulnerability
Best Work From Home Data Security Practices Cybersecurity Incident And VulnerabilityPurpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc. Introducing Best Work From Home Data Security Practices Cybersecurity Incident And Vulnerability to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Configure WIFI Encryption, Avoid Using External Devices, System Update, using this template. Grab it now to reap its full benefits.
-
 Checklist For Work From Home Data Security Cybersecurity Incident And Vulnerability
Checklist For Work From Home Data Security Cybersecurity Incident And VulnerabilityDeliver an outstanding presentation on the topic using this Checklist For Work From Home Data Security Cybersecurity Incident And Vulnerability. Dispense information and present a thorough explanation of Data Security, Reporting Process, Employees using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Agenda Preventing Data Breaches Through Cyber Security Awareness
Agenda Preventing Data Breaches Through Cyber Security AwarenessIntroducing Agenda Preventing Data Breaches Through Cyber Security Awareness to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Awareness Campaign, Security Threats, Employees, using this template. Grab it now to reap its full benefits.
-
 Assessment Test To Measure Effectiveness Of Training Preventing Data Breaches Through Cyber Security
Assessment Test To Measure Effectiveness Of Training Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to outline a comprehensive assessment test which can be used by the trainer to evaluate the effectiveness of cyber security training plan. The questions covered in the slide is related to spam, ways to protect from cyberbullying etc. Increase audience engagement and knowledge by dispensing information using Assessment Test To Measure Effectiveness Of Training Preventing Data Breaches Through Cyber Security. This template helps you present information on four stages. You can also present information on Cyberbullying, Confidential Data, Training Plan using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Comparative Assessment Of Security Awareness Online Preventing Data Breaches Through Cyber Security
Comparative Assessment Of Security Awareness Online Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase comparison of various advance cyber security training courses. The comparison is drawn on the basis of course description, level, duration, no. of companies enrolled for this course etc. Present the topic in a bit more detail with this Comparative Assessment Of Security Awareness Online Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Course Description, Instructor, Rating. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparison Of Various Security Awareness Training Software Preventing Data Breaches Through Cyber Security
Comparison Of Various Security Awareness Training Software Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. Deliver an outstanding presentation on the topic using this Comparison Of Various Security Awareness Training Software Preventing Data Breaches Through Cyber Security. Dispense information and present a thorough explanation of Security Reporting, Phishing Simulations, Deployment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Awareness Checklist To Ensure It Asset Preventing Data Breaches Through Cyber Security
Cyber Security Awareness Checklist To Ensure It Asset Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Introducing Cyber Security Awareness Checklist To Ensure It Asset Preventing Data Breaches Through Cyber Security to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Employees, Data Breach, Operating System, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Awareness Trends In 2023 Preventing Data Breaches Through Cyber Security
Cyber Security Awareness Trends In 2023 Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase security awareness trends which the organization has to look out for in 2023. increase in malware and ransomware attack, more employees will be targeted by mobile malware attack and advancement of phishing attack are some of the major trends mentioned in the slide. Increase audience engagement and knowledge by dispensing information using Cyber Security Awareness Trends In 2023 Preventing Data Breaches Through Cyber Security. This template helps you present information on four stages. You can also present information on Mobile Malware Attack, Get More Advanced, Ransomware Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Dos And Donts Of Prevention From Ransomware Attack Preventing Data Breaches Through Cyber Security
Dos And Donts Of Prevention From Ransomware Attack Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase the Dos and donts of ransomware prevention attack. The slide covers information about updating the software, installing a firewall software, using reliable website and sources etc. Introducing Dos And Donts Of Prevention From Ransomware Attack Preventing Data Breaches Through Cyber Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Online Criminals, Foreign Government Officials, Malicious Insiders, using this template. Grab it now to reap its full benefits.
-
 Evaluating It System Security Using Swot Analysis Preventing Data Breaches Through Cyber Security
Evaluating It System Security Using Swot Analysis Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Increase audience engagement and knowledge by dispensing information using Evaluating It System Security Using Swot Analysis Preventing Data Breaches Through Cyber Security. This template helps you present information on four stages. You can also present information on Strength, Threats, Weaknesses using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.





