Powerpoint Templates and Google slides for Data Security Business
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Business Benefits Flexibility Data Security Resource Sharing Agility
Business Benefits Flexibility Data Security Resource Sharing AgilityKeep your audience glued to their seats with professionally designed PPT slides. This deck comprises of total of twelve slides. It has PPT templates with creative visuals and well researched content. Not just this, our PowerPoint professionals have crafted this deck with appropriate diagrams, layouts, icons, graphs, charts and more. This content ready presentation deck is fully editable. Just click the DOWNLOAD button below. Change the colour, text and font size. You can also modify the content as per your need. Get access to this well crafted complete deck presentation and leave your audience stunned.
-
 Data management maturity information security business growth architecture
Data management maturity information security business growth architectureDeliver a credible and compelling presentation by deploying this Data Management Maturity Information Security Business Growth Architecture. Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The twelve slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Data Management Maturity Information Security Business Growth Architecture PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.
-
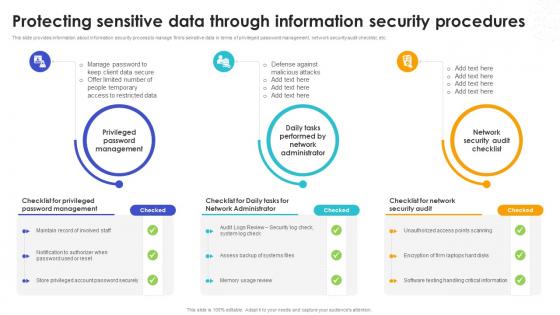 Protecting Sensitive Data Through Information Security Safeguarding Business With Data Loss Cybersecurity SS
Protecting Sensitive Data Through Information Security Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information about information security process to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc.Introducing Protecting Sensitive Data Through Information Security Safeguarding Business With Data Loss Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Network Security Audit, Privileged Password Management, Network Administrator, using this template. Grab it now to reap its full benefits.
-
 Data Breach Prevention 30 60 90 Days Plan To Secure Businesses From Data Breaches
Data Breach Prevention 30 60 90 Days Plan To Secure Businesses From Data BreachesThis slide represents 30-60-90 plan to protect companies and their employees from data breach attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month. Increase audience engagement and knowledge by dispensing information using Data Breach Prevention 30 60 90 Days Plan To Secure Businesses From Data Breaches. This template helps you present information on three stages. You can also present information on Strengthen Access Controls, Implement Continuous Monitoring, Implement Data Encryption, Continue Employee Awareness Training using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Breach Prevention Security Software To Protect Business From Data Breach
Data Breach Prevention Security Software To Protect Business From Data BreachThe purpose of this slide is to highlight the available security tools to stay safe from data breaches. The popular security software are access control solutions, Security Information And Event Management SIEM tools, and antivirus software. Increase audience engagement and knowledge by dispensing information using Data Breach Prevention Security Software To Protect Business From Data Breach. This template helps you present information on three stages. You can also present information on Security Information And Event Management, Amends Permissions As Needed, Security Software To Protect Business using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
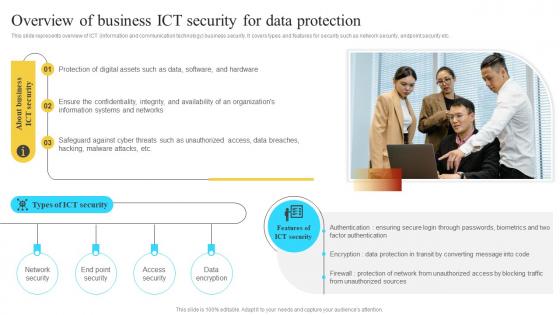
 Overview Of Business ICT Security For Data Elivering ICT Services For Enhanced Business Strategy SS V
Overview Of Business ICT Security For Data Elivering ICT Services For Enhanced Business Strategy SS VThis slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc. Increase audience engagement and knowledge by dispensing information using Overview Of Business ICT Security For Data Elivering ICT Services For Enhanced Business Strategy SS V. This template helps you present information on three stages. You can also present information on Authentication, Encryption, Firewall using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Implementation Of Information Overview Of Business Ict Security For Data Protection Strategy SS V
Implementation Of Information Overview Of Business Ict Security For Data Protection Strategy SS VThis slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc. Introducing Implementation Of Information Overview Of Business Ict Security For Data Protection Strategy SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Protection Of Digital, Safeguard Against Cyber, using this template. Grab it now to reap its full benefits.
-
 Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS V
Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS VThis slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc. Introducing Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS V to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Incident Management, Request Fulfillment using this template. Grab it now to reap its full benefits.
-
 Business Expansion And Data Security Strategy Icon
Business Expansion And Data Security Strategy IconIntroducing our premium set of slides with Business Expansion And Data Security Strategy Icon. Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Business Expansion, Data Security Strategy Icon. So download instantly and tailor it with your information.
-
 Key Strategies To Secure Business Data
Key Strategies To Secure Business DataThis slide showcase strategies that can be used for securing cyberattacks and target organizational data security and access. It includes updating devices, secure iot technology, track cloud storage, train employees and secure network access. Introducing our premium set of slides with Key Strategies To Secure Business Data. Ellicudate the Five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Updated Devices, Track Cloud Storage, Train Employees. So download instantly and tailor it with your information.
-
 Significant Data Security Measures For Business
Significant Data Security Measures For BusinessThis slide showcase different type of risk measure that are used by the organization for securing valuable data. It include strong password access, backup, technology updating and antivirus installation. Presenting our set of slides with Significant Data Security Measures For Business. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Strong Password Access, Antivirus Installation, Backups.
-
 Overview Of Business Ict Security For Data Comprehensive Guide For Deployment Strategy SS V
Overview Of Business Ict Security For Data Comprehensive Guide For Deployment Strategy SS VThis slide represents overview of ICT information and communication technology business security It covers types and features for security such as network security, endpoint security etc Present the topic in a bit more detail with this Overview Of Business Ict Security For Data Comprehensive Guide For Deployment Strategy SS V Use it as a tool for discussion and navigation on Unauthorized Sources, Factor Authentication, Organizations Information This template is free to edit as deemed fit for your organization Therefore download it now
-
 Privacy Framework Icon For Securing Business Data
Privacy Framework Icon For Securing Business DataPresenting our well structured Privacy Framework Icon For Securing Business Data. The topics discussed in this slide are Privacy Framework Icon, Securing Business Data. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Data Breach Response Plan 30 60 90 Days Plan To Secure Businesses From Data Breaches
Data Breach Response Plan 30 60 90 Days Plan To Secure Businesses From Data BreachesThis slide represents 30-60-90 plan to protect companies and their employees from data breach attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month. Increase audience engagement and knowledge by dispensing information using Data Breach Response Plan 30 60 90 Days Plan To Secure Businesses From Data Breaches. This template helps you present information on three stages. You can also present information on Strengthen Access Controls, Conduct Regular Security Audits, Provide Data Security Training using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Business Impact Of Data Classification On Information Security
Business Impact Of Data Classification On Information SecurityThis slide shows key benefits of data classification for improving information security. The purpose of this slide is to help organizations in reducing burden of security teams by enhancing data protection strategies. It covers benefits such as risk evaluation, data backup, access control, compliance standards. Presenting our set of slides with Business Impact Of Data Classification On Information Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on General Data Protection Regulation, Compliance Standard, Protected Storage.
-
 Different Encryption Methods To Secure Business Data
Different Encryption Methods To Secure Business DataThis slide represents various types of encryption method which assists businesses to protect data and maintain regulatory compliances. It includes different encryption methods to secure business data such as advance encryption standards, rivest shamir adleman, etc. Introducing our premium set of slides with name Different Encryption Methods To Secure Business Data. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Format Preserving Encryption, Blowfish, Advance Encryption Standards. So download instantly and tailor it with your information.
-
 Cyber Security Measures To Protect Business Data
Cyber Security Measures To Protect Business DataThe highlighted slide underscores essential measures, including robust passwords, regular software updates, antivirus protection, multi factor authentication, and access control. These steps collectively enhance cybersecurity, fortifying defenses to safeguard critical business data against potential threats. Presenting our set of slides with Cyber Security Measures To Protect Business Data. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Strong And Complex Passwords, Software Updates, Enhance Security.
-
 Tokenization For Improved Data Security Budget Allocation To Implement Tokenization In Business
Tokenization For Improved Data Security Budget Allocation To Implement Tokenization In BusinessThis slide showcases the breakdown cost for conducting tokenization for data security. The purpose of this slide is to showcase the technology cost breakdown for different components such as test infrastructure, staff training, etc. Present the topic in a bit more detail with this Tokenization For Improved Data Security Budget Allocation To Implement Tokenization In Business. Use it as a tool for discussion and navigation on Tokenization Solution, Integration And Customization, Infrastructure And Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tokenization For Improved Data Security Future Trends Of Tokenization On Business And Technology
Tokenization For Improved Data Security Future Trends Of Tokenization On Business And TechnologyThis slide highlights the anticipated developments in tokenizations impact on the realms of business and technology. The purpose of this slide is to outline the future trends of tokenization. Introducing Tokenization For Improved Data Security Future Trends Of Tokenization On Business And Technology to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Anticipated Developments, Business And Technology, Future Trends Of Tokenization, using this template. Grab it now to reap its full benefits.
-
 Tokenization For Improved Data Security Selecting Appropriate Tokenization Solution For Business Needs
Tokenization For Improved Data Security Selecting Appropriate Tokenization Solution For Business NeedsThis slide discusses about choosing right tokenization solution for business needs. The purpose of this slide is to highlight the ways of selecting which include applicability to business, data elements, etc. Introducing Tokenization For Improved Data Security Selecting Appropriate Tokenization Solution For Business Needs to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Consistency Requirement, Data Elements For Tokenization, Applicability To Business, using this template. Grab it now to reap its full benefits.
-
 Case Study Data Breach Incident Recovery Business Recovery Plan To Overcome Cyber Security Threat
Case Study Data Breach Incident Recovery Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about a case study related to data breach recovery. It includes key elements such as incident date, challenges faced, LinkedIn response plan, and results. Deliver an outstanding presentation on the topic using this Case Study Data Breach Incident Recovery Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Regain Customer Trust, Rebuilding Business Reputation, Linkedin Response using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Multi Factor A For Business Data Protection Business Recovery Plan To Overcome Cyber Security Threat
Multi Factor A For Business Data Protection Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information leveraging multifactor authentication to increase cyber security. It includes key points such as failed login, geographic location, time of login, operating system, IP address, etc. Deliver an outstanding presentation on the topic using this Multi Factor A For Business Data Protection Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Time Of Login Attempt, Operating System, Source Of IP Address using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
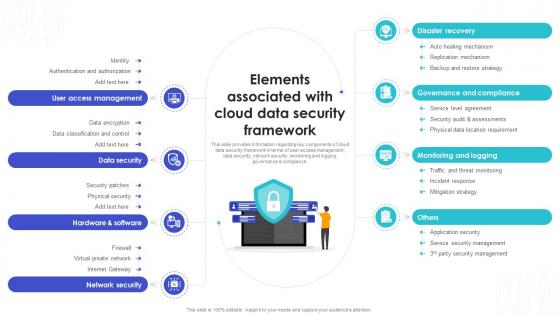 Elements Associated With Cloud Data Security Safeguarding Business With Data Loss Cybersecurity SS
Elements Associated With Cloud Data Security Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding key components of cloud data security framework in terms of user access management, data security, network security, monitoring and logging, governance and compliance.Increase audience engagement and knowledge by dispensing information using Elements Associated With Cloud Data Security Safeguarding Business With Data Loss Cybersecurity SS. This template helps you present information on eight stages. You can also present information on Disaster Recovery, User Access Management, Data Security, Network Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security Training Program For Workforce Safeguarding Business With Data Loss Cybersecurity SS
Information Security Training Program For Workforce Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding training program to ensure information security at workplace by considering focus areas such as data security and encryption, network security, incident response, etc.Deliver an outstanding presentation on the topic using this Information Security Training Program For Workforce Safeguarding Business With Data Loss Cybersecurity SS. Dispense information and present a thorough explanation of Duration, Delivery Method, Assessment, Cost, Modules using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phase 4 Of Dlp Success Focus On Proactive Security Safeguarding Business With Data Loss Cybersecurity SS
Phase 4 Of Dlp Success Focus On Proactive Security Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding focusing on proactive security for successful data loss prevention execution. It will include initiatives such as infiltration, exfiltration, automated protection, etc.Increase audience engagement and knowledge by dispensing information using Phase 4 Of Dlp Success Focus On Proactive Security Safeguarding Business With Data Loss Cybersecurity SS. This template helps you present information on one stages. You can also present information on Exhibited Behavior, Objective, Customization, High Risk Events using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Business Data Security And Privacy Assessment Survey Form Survey SS
Business Data Security And Privacy Assessment Survey Form Survey SSFollowing slides illustrates business data security survey form which can be used by data analyst to identify best data security tools. It includes key elements such as data security tools, budget allocation on tools, satisfaction level with tools, etc. Introducing our Business Data Security And Privacy Assessment Survey Form Survey SS set of slides. The topics discussed in these slides are Security Tools Used, Allocated For Tools, Security Software Solutions. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data security small businesses ppt powerpoint presentation pictures sample cpb
Data security small businesses ppt powerpoint presentation pictures sample cpbPresenting our Data Security Small Businesses Ppt Powerpoint Presentation Pictures Sample Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Data Security Small Businesses This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Enabling Data Security Risk Management Action Plan Building Business Analytics Architecture
Enabling Data Security Risk Management Action Plan Building Business Analytics ArchitectureThe data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Present the topic in a bit more detail with this Enabling Data Security Risk Management Action Plan Building Business Analytics Architecture. Use it as a tool for discussion and navigation on Potential Risk, Risk Level, Reason For Risk Rating, Communication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Unlocking Business Infrastructure Capabilities Enabling Data Security Risk Management Action Plan
Unlocking Business Infrastructure Capabilities Enabling Data Security Risk Management Action PlanThe data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver an outstanding presentation on the topic using this Unlocking Business Infrastructure Capabilities Enabling Data Security Risk Management Action Plan. Dispense information and present a thorough explanation of Enabling Data Security Risk Management Action Plan using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Computing Security How Does Cloud Security Work Data Retention And Business
Cloud Computing Security How Does Cloud Security Work Data Retention And BusinessThis slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan. Increase audience engagement and knowledge by dispensing information using Cloud Computing Security How Does Cloud Security Work Data Retention And Business. This template helps you present information on four stages. You can also present information on Impact Analysis, Recovery Strategies, Testing And Maintenance, Plan Development using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Business Data Security Analysis Icon With Shield
Business Data Security Analysis Icon With ShieldPresenting our set of slides with Business Data Security Analysis Icon With Shield. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Business, Data Security, Analysis, Icon Shield.
-
 Checklist To Implement Cloud Security In Business Cloud Data Protection
Checklist To Implement Cloud Security In Business Cloud Data ProtectionThis slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Introducing Checklist To Implement Cloud Security In Business Cloud Data Protection to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispense information on Logging And Monitoring, Networking, Data Encryption, using this template. Grab it now to reap its full benefits.
-
 How Does Cloud Security Work Data Retention And Business Cloud Data Protection
How Does Cloud Security Work Data Retention And Business Cloud Data ProtectionThis slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan. Increase audience engagement and knowledge by dispensing information using How Does Cloud Security Work Data Retention And Business Cloud Data Protection. This template helps you present information on four stages. You can also present information on Impact Analysis, Business Continuity, Plan Development, Recovery Strategies using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Implementation Steps Enable Data Security Crm System Implementation Guide For Businesses
Implementation Steps Enable Data Security Crm System Implementation Guide For BusinessesThis slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Present the topic in a bit more detail with this Implementation Steps Enable Data Security Crm System Implementation Guide For Businesses. Use it as a tool for discussion and navigation on Implementation, Compliance, Authentication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encrypted Business Data Security Icon
Encrypted Business Data Security IconPresenting our well structured Encrypted Business Data Security Icon. The topics discussed in this slide are Encrypted Business, Data Security Icon. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Network Security Policy To Secure Business Data
Network Security Policy To Secure Business DataThis slide outlines the practice of protecting organizations crucial data in accordance with the companys law and industry standards. the respective policies include internet access, VPN, firewall rules, wireless LAN, and remote connection. Introducing our Network Security Policy To Secure Business Data set of slides. The topics discussed in these slides are Internet Access Policy, Proxy Server Policy, Remote Connection Policy. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cloud Architecture And Security Review Data Complexity Slows Down The Business Process Multi Cloud
Cloud Architecture And Security Review Data Complexity Slows Down The Business Process Multi CloudThis slide covers the current complex multi cloud architecture with all their inherent complexity, fragility, and limitations that slow down the business process. Introducing Cloud Architecture And Security Review Data Complexity Slows Down The Business Process Multi Cloud to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Data Complexity, Slows Down The Business, Multi Cloud Architecture, using this template. Grab it now to reap its full benefits.
-
 Business Data Security Management Model
Business Data Security Management ModelThis slide covers business data security management model which includes Defining, executing and measuring security controls. Introducing our Business Data Security Management Model set of slides. The topics discussed in these slides are Business Data, Security, Management Model. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Business Data Encryption Security Technology
Business Data Encryption Security TechnologyThis slide highlights the role of encryption technology which is used by business and organisation to protect the confidentiality of digital data storage and transmission. Key components are authentication, privacy, regulatory compliance and security. Presenting our set of slides with name Business Data Encryption Security Technology. This exhibits information on four stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Privacy, Authentication, Regulatory Compliance, Security.
-
 Overview Of Business Email Compromise Attack Preventing Data Breaches Through Cyber Security
Overview Of Business Email Compromise Attack Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to delineate an example of business email compromise attack. Information covered in this slide is related to the working of this attack and how it can result in loss of company reputation. Increase audience engagement and knowledge by dispensing information using Overview Of Business Email Compromise Attack Preventing Data Breaches Through Cyber Security. This template helps you present information on four stages. You can also present information on Email, Services, Account using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Various Techniques To Successfully Prevent Business Email Preventing Data Breaches Through Cyber Security
Various Techniques To Successfully Prevent Business Email Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to outline different techniques which can be used to protect organization from business email compromise attack. The techniques covered in the slide are sender policy framework SPF, using strong password policy and process for wire transfers. Increase audience engagement and knowledge by dispensing information using Various Techniques To Successfully Prevent Business Email Preventing Data Breaches Through Cyber Security. This template helps you present information on four stages. You can also present information on Sender Policy Framework, Strong Password Policy, Strong Process For Wire Transfers using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Access Security Measures For Businesses
Data Access Security Measures For BusinessesThis slide represents the security measures for data access within an organization. This template aims to demonstrate secure data access techniques and their benefits. The components include workforce training, implementing a data centric security plan, deploying a multi factor authentication policy, etc. Presenting our well structured Data Access Security Measures For Businesses. The topics discussed in this slide are Workforce Training, Data Centric Security, Stricter Permissions. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Data Security Business Key Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security Business Key Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis PowerPoint icon is a bright, eye catching symbol for business success. It features a key with a vibrant blue and yellow colour scheme, perfect for adding a modern touch to any presentation. Use it to highlight key points or to illustrate the importance of achieving success in business.
-
 Data Security Business Key Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security Business Key Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone PowerPoint icon depicts a key, representing the importance of unlocking success in business. It is a versatile graphic that can be used to illustrate a variety of concepts, from unlocking potential to opening doors to new opportunities.
-
 Improve Business Data Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Improve Business Data Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Improve business data security colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Improve Business Data Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Improve Business Data Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Improve business data security monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Enhance Business Data Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Enhance Business Data Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Enhance business data security colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Enhance Business Data Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Enhance Business Data Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Enhance business data security monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Overview Of Business ICT Security Data Protection Implementation ICT Strategic Plan Strategy SS
Overview Of Business ICT Security Data Protection Implementation ICT Strategic Plan Strategy SSThis slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc.Present the topic in a bit more detail with this Overview Of Business ICT Security Data Protection Implementation ICT Strategic Plan Strategy SS. Use it as a tool for discussion and navigation on Factor Authentication, Organizations Information, Ensure Confidentiality. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview Of Business ICT Security For Data Protection ICT Strategic Framework Strategy SS V
Overview Of Business ICT Security For Data Protection ICT Strategic Framework Strategy SS VThis slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc. Present the topic in a bit more detail with this Overview Of Business ICT Security For Data Protection ICT Strategic Framework Strategy SS V. Use it as a tool for discussion and navigation on Network Security, Access Security, Data Encryption. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data and business network security techniques ppt slides
Data and business network security techniques ppt slidesPresenting data and business network security techniques ppt slides. This is a data and business network security techniques ppt slides. This is a one stage process. The stages in this process are security.
-
 Securing business data powerpoint slide deck template
Securing business data powerpoint slide deck templatePresenting securing business data powerpoint slide deck template. This is a securing business data powerpoint slide deck template. This is a one stage process. The stages in this process are identify data, secure access, back up to the cloud, encrypt your data, control downloads.
-
 Enterprise security strategy roadmap data architecture business analytics
Enterprise security strategy roadmap data architecture business analyticsPresenting this set of slides with name - Enterprise Security Strategy Roadmap Data Architecture Business Analytics. This is an editable four stages graphic that deals with topics like Enterprise Security, Strategy Roadmap, Data Architecture, Business Analytics to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Finance business collaboration corporate business data security business strategy cpb
Finance business collaboration corporate business data security business strategy cpbPresenting this set of slides with name - Finance Business Collaboration Corporate Business Data Security Business Strategy Cpb. This is an editable three stages graphic that deals with topics like Finance, Business, Collaboration, Corporate, Business, Data, Security, Business, Strategy to help convey your message better graphically. This product is a premium product available for immediate download,and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Firewall setup for business data security icon
Firewall setup for business data security iconPresenting this set of slides with name Firewall Setup For Business Data Security Icon. This is a three stage process. The stages in this process are Firewall Setup, Business Data, Security Icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Why businesses should invest in data security ppt powerpoint presentation portfolio
Why businesses should invest in data security ppt powerpoint presentation portfolioPresenting this set of slides with name Why Businesses Should Invest In Data Security Ppt Powerpoint Presentation Portfolio. This is a four stage process. The stages in this process are Data Security, Strategies, Financially, Threat. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Data security business ppt powerpoint presentation icon aids cpb
Data security business ppt powerpoint presentation icon aids cpbPresenting this set of slides with name Data Security Business Ppt Powerpoint Presentation Icon Aids Cpb. This is an editable Powerpoint six stages graphic that deals with topics like Data Security Business to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Data security small business ppt powerpoint presentation model display cpb
Data security small business ppt powerpoint presentation model display cpbPresenting this set of slides with name Data Security Small Business Ppt Powerpoint Presentation Model Display Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Data Security Small Business to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Small business data security ppt powerpoint presentation show brochure cpb
Small business data security ppt powerpoint presentation show brochure cpbPresenting this set of slides with name Small Business Data Security Ppt Powerpoint Presentation Show Brochure Cpb. This is an editable Powerpoint six stages graphic that deals with topics like Small Business Data Security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Business data security dashboard snapshot of critical application
Business data security dashboard snapshot of critical applicationPresenting this set of slides with name Business Data Security Dashboard Snapshot Of Critical Application. The topics discussed in these slides are Business Data Security Dashboard Of Critical Application. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.




