Powerpoint Templates and Google slides for Data For Protection
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Mobile Device Security For Data Protection Powerpoint Presentation Slides Cybersecurity CD
Mobile Device Security For Data Protection Powerpoint Presentation Slides Cybersecurity CDDitch the Dull templates and opt for our engaging Mobile Device Security For Data Protection Powerpoint Presentation Slides Cybersecurity CD deck to attract your audience. Our visually striking design effortlessly combines creativity with functionality, ensuring your content shines through. Compatible with Microsoft versions and Google Slides, it offers seamless integration of presentation. Save time and effort with our pre-designed PPT layout, while still having the freedom to customize fonts, colors, and everything you ask for. With the ability to download in various formats like JPG, JPEG, and PNG, sharing your slides has never been easier. From boardroom meetings to client pitches, this deck can be the secret weapon to leaving a lasting impression.
-
 Datafication Of HR Measures Taken For Data Protection In Cloud Globally
Datafication Of HR Measures Taken For Data Protection In Cloud GloballyThis slide represents the measures taken for data protection in the cloud worldwide, covering multi-factor authentication, cloud backup, encryption, employee training, auditing of user activity, review of access rights, data classification, and removing sensitive data from the cloud. Deliver an outstanding presentation on the topic using this Datafication Of HR Measures Taken For Data Protection In Cloud Globally. Dispense information and present a thorough explanation of Measures, Protection, Authentication using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Datafication Framework Measures Taken For Data Protection In Cloud Globally
Datafication Framework Measures Taken For Data Protection In Cloud GloballyThis slide represents the measures taken for data protection in the cloud worldwide, covering multi-factor authentication, cloud backup, encryption, employee training, auditing of user activity, review of access rights, data classification, and removing sensitive data from the cloud. Present the topic in a bit more detail with this Datafication Framework Measures Taken For Data Protection In Cloud Globally. Use it as a tool for discussion and navigation on Measures, Information, Enterprises. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Datafication In Data Science Measures Taken For Data Protection In Cloud Globally
Datafication In Data Science Measures Taken For Data Protection In Cloud GloballyThis slide represents the measures taken for data protection in the cloud worldwide, covering multi factor authentication, cloud backup, encryption, employee training, auditing of user activity, review of access rights, data classification, and removing sensitive data from the cloud.Deliver an outstanding presentation on the topic using this Datafication In Data Science Measures Taken For Data Protection In Cloud Globally. Dispense information and present a thorough explanation of Digital Platforms, Encryption Features, Security Measures using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Deception Dashboard For Modern Data Protection
Cyber Deception Dashboard For Modern Data ProtectionThe purpose of this slide is to introduce a cyber deception dashboard for modern data protection, providing visual insights into threat activity by analyzing traps data, events timelines, etc. Introducing our Cyber Deception Dashboard For Modern Data Protection set of slides. The topics discussed in these slides are Statistics For Threat, Trap Events, Network Intelligence Events. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 US Cyber Security Solution Market Trend For Data Protection
US Cyber Security Solution Market Trend For Data ProtectionThis slide graphically represents market trend of US cyber security solutions for enhancing data protection and mitigating cyber attacks. It includes various growth drivers of solutions such as rising remote work culture, increasing cyber threats, etc. Introducing our US Cyber Security Solution Market Trend For Data Protection set of slides. The topics discussed in these slides are Key Insights, Market Size, Cybersecurity Solutions. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Dashboard For Supply Chain Attack Management For Data Protection
Dashboard For Supply Chain Attack Management For Data ProtectionThis slide represents dashboard that helps companies to manage supply chain attacks for improving security management measures. It includes various components such a policy and compliance, resource security hygiene, and threat protection. Presenting our well structured Dashboard For Supply Chain Attack Management For Data Protection. The topics discussed in this slide are Policy And Compliance, Resource Security Hygiene, Threat Protection. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Tools To Address Supply Chain Cybersecurity Attacks For Data Protection
Tools To Address Supply Chain Cybersecurity Attacks For Data ProtectionThis slide graphically represents use of various tools and approaches that assist companies in addressing various supply chain cybersecurity attacks and optimizing data protection. It includes tools such as IT vendor risk management tools, supply chain risk management tools, etc. Presenting our well structured Tools To Address Supply Chain Cybersecurity Attacks For Data Protection. The topics discussed in this slide are Audits Of Suppliers, Manufacturers, Logistics Partners. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Network Security Challenges And Solution For Protecting Data
Network Security Challenges And Solution For Protecting DataThis slide showcase solution and challenges for network security. The main purpose for this template is to save company data from getting into hands of rival businesses. This includes data theft, insider threat, password attack, etc. Presenting our set of slides with Network Security Challenges And Solution For Protecting Data. This exhibits information on two stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Challenges, Solution.
-
 Network Security Highlighting Important Steps For Protecting Data
Network Security Highlighting Important Steps For Protecting DataThis slide showcase steps of network security. The main reason for this slide is showcasing management of network without any uninterrupted operations. This includes internal networks, protection security, cyber security, etc. Presenting our well structured Network Security Highlighting Important Steps For Protecting Data. The topics discussed in this slide are Internal Network, Protected Payment.This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Network Security Icon For Protecting Data From Theft
Network Security Icon For Protecting Data From TheftIntroducing our Network Security Icon For Protecting Data From Theft set of slides. The topics discussed in these slides are Network Security Protecting Data. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Network Security Tips For Protecting Important Data
Network Security Tips For Protecting Important DataThese slide showcase ways of protecting network security. The main purpose of this template is how to keep office data safe from any kind of theft, this includes careful grant access, strong password, secure servers, text security. Presenting our set of slides with Network Security Tips For Protecting Important Data. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Careful Grant Access, Strong Password.
-
 Guidelines For Implementing Data Protection Regulations Strategies To Comply Strategy SS V
Guidelines For Implementing Data Protection Regulations Strategies To Comply Strategy SS VThis slide presents data protection policies and procedures to ensure data compliance in the company. It includes information about data classification, access control, incident response and data privacy policy. Present the topic in a bit more detail with this Guidelines For Implementing Data Protection Regulations Strategies To Comply Strategy SS V. Use it as a tool for discussion and navigation on Data Classification Policy, Access Control Policy, Incident Response Policy. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
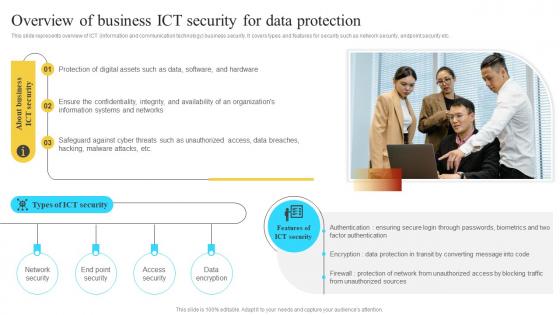 Implementation Of Information Overview Of Business Ict Security For Data Protection Strategy SS V
Implementation Of Information Overview Of Business Ict Security For Data Protection Strategy SS VThis slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc. Introducing Implementation Of Information Overview Of Business Ict Security For Data Protection Strategy SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Protection Of Digital, Safeguard Against Cyber, using this template. Grab it now to reap its full benefits.
-
 Guidelines For Implementing Data Protection Corporate Regulatory Compliance Strategy SS V
Guidelines For Implementing Data Protection Corporate Regulatory Compliance Strategy SS VThis slide presents data protection policies and procedures to ensure data compliance in the company. It includes information about data classification, access control, incident response and data privacy policy. Present the topic in a bit more detail with this Guidelines For Implementing Data Protection Corporate Regulatory Compliance Strategy SS V. Use it as a tool for discussion and navigation on Data Classification Policy, Access Control Policy. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Icon For Ensuring Data Protection In Digital Transformation For Local Government
Icon For Ensuring Data Protection In Digital Transformation For Local GovernmentIntroducing our Icon For Ensuring Data Protection In Digital Transformation For Local Government set of slides. The topics discussed in these slides are Icon Ensuring, Data Protection, Digital Transformation. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Secured Data Protection For Online Security System Icon
Secured Data Protection For Online Security System IconPresenting our set of slides with Secured Data Protection For Online Security System Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Secured Data Protection, Online Security System Icon.
-
 Corporate Compliance Strategy Guidelines For Implementing Data Protection Regulations Strategy SS V
Corporate Compliance Strategy Guidelines For Implementing Data Protection Regulations Strategy SS VThis slide presents data protection policies and procedures to ensure data compliance in the company. It includes information about data classification, access control, incident response and data privacy policy. Introducing Corporate Compliance Strategy Guidelines For Implementing Data Protection Regulations Strategy SS V to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Workplace Safety Compliance, Recordkeeping Compliance, Employment Law Compliance using this template. Grab it now to reap its full benefits.
-
 Encryption Implementation Strategies Top Regulatory Compliance Frameworks For Data Protection
Encryption Implementation Strategies Top Regulatory Compliance Frameworks For Data ProtectionThe purpose of this slide is to summarize several relevant regulations. These are GDPR General Data Protection Regulation, CCPA California Consumer Privacy Act, PCI DSS Payment Card Industry Data Security Standard, NIST, and HIPAA, along with their descriptions and scopes. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Top Regulatory Compliance Frameworks For Data Protection. Dispense information and present a thorough explanation of General Data Protection Regulation, California Consumer Privacy Act, Health Insurance Portability And Accountability Act using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Employee And Workplace Guidelines For Implementing Data Protection Regulations Strategy SS V
Employee And Workplace Guidelines For Implementing Data Protection Regulations Strategy SS VThis slide presents data protection policies and procedures to ensure data compliance in the company. It includes information about data classification, access control, incident response and data privacy policy.Increase audience engagement and knowledge by dispensing information using Employee And Workplace Guidelines For Implementing Data Protection Regulations Strategy SS V This template helps you present information on Four stages. You can also present information on Internal Review, External Audit, Compliance Surveys using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Guidelines For Implementing Data Protection Regulations Effective Business Risk Strategy SS V
Guidelines For Implementing Data Protection Regulations Effective Business Risk Strategy SS VThis slide presents data protection policies and procedures to ensure data compliance in the company. It includes information about data classification, access control, incident response and data privacy policy. Increase audience engagement and knowledge by dispensing information using Guidelines For Implementing Data Protection Regulations Effective Business Risk Strategy SS V. This template helps you present information on four stages. You can also present information on Purpose, Data Classification Policy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS V
Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS VThis slide represents overview of ICT information and communication technology business security. It covers types and features for security such as network security, endpoint security etc. Introducing Strategic Plan To Implement Overview Of Business Ict Security For Data Protection Strategy SS V to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Incident Management, Request Fulfillment using this template. Grab it now to reap its full benefits.
-
 Information Security Management Framework For Organization Data Protection
Information Security Management Framework For Organization Data ProtectionThis slide represents framework that assists organizations in developing information security management to enhance data protection. This model sets information security at tactical level, strategic level, and operational level. Introducing our Information Security Management Framework For Organization Data Protection set of slides. The topics discussed in these slides are Information Security Plan, Consciousness Management, Risk Analysis. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Information Security Management Icon For Data Protection
Information Security Management Icon For Data ProtectionPresenting our set of slides with Information Security Management Icon For Data Protection. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Information Security Management Icon, Data Protection.
-
 Extensive Business Strategy Cyber Strategies For KPMG For Client Data Protection Strategy SS V
Extensive Business Strategy Cyber Strategies For KPMG For Client Data Protection Strategy SS VThis slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory. Introducing Extensive Business Strategy Cyber Strategies For KPMG For Client Data Protection Strategy SS V to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on People, Process, Regulatory, using this template. Grab it now to reap its full benefits.
-
 Extensive Business Strategy Other Cyber Strategies Of KPMG For Client Data Protection Strategy SS V
Extensive Business Strategy Other Cyber Strategies Of KPMG For Client Data Protection Strategy SS VThis slide covers cyber strategies to protect KPMG customer data protection. The purpose of this template is to provide an overview on top techniques to be implemented to save clients data. It includes strategies such as developing comprehensive understanding of cyber threat landscape, implementing risk based approach, establishing robust security governance framework, etc. Increase audience engagement and knowledge by dispensing information using Extensive Business Strategy Other Cyber Strategies Of KPMG For Client Data Protection Strategy SS V. This template helps you present information on five stages. You can also present information on Threat Landscape, Cyber Security, Governance Framework using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Implementing Byod Policy To Enhance Develop Security Policies For Data Protection
Implementing Byod Policy To Enhance Develop Security Policies For Data ProtectionThis slide shows major data protection policies for handling sensitive data of corporate. It include policies such as device security, network and data handling, etc. Introducing Implementing Byod Policy To Enhance Develop Security Policies For Data Protection to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Network Security, Data Handling, Device Security, Data Protection, using this template. Grab it now to reap its full benefits.
-
 Implementing Byod Policy To Enhance Security Considerations For Data Protection Under Byod Policy
Implementing Byod Policy To Enhance Security Considerations For Data Protection Under Byod PolicyThis slide shows essential considerations for protecting crucial data of company in organization. It include security areas such as device security, network security and software updates, etc. Increase audience engagement and knowledge by dispensing information using Implementing Byod Policy To Enhance Security Considerations For Data Protection Under Byod Policy. This template helps you present information on five stages. You can also present information on Device Security, Mobile Device Management, Network Security, Malware Protection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Blackberry Cybersecurity Approach For Protecting Data
Blackberry Cybersecurity Approach For Protecting DataThis slide showcases blackberry cybersecurity strategy for data protection. The purpose of this slide is to aid IT teams aids in effective protection and maintenance of sensitive information. It includes elements such as continuous monitoring, data loss prevention, etc. Presenting our set of slides with Blackberry Cybersecurity Approach For Protecting Data. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Monitoring, Access, Prevention.
-
 Cloning In Cyber Security For Data Protection
Cloning In Cyber Security For Data ProtectionThis slide shows benefits of cloning for cyber protection. It aims to prevent cloning security risks to mitigate unauthorized access to technical assets. It covers four cyber security measures such as data protection, integrity, loss prevention and transfers. Presenting our set of slides with name Cloning In Cyber Security For Data Protection. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Protection, Data Integrity, Data Transfers.
-
 Implementation Stats Of Big Data Analytics For Cyber Protection
Implementation Stats Of Big Data Analytics For Cyber ProtectionThe following slide highlights key points like prioritizing, training, improving, and security infrastructure to show implementation stats of big data analytics for cybersecurity. It helps organizations to enhance cyber threat detection and response capabilities. Presenting our set of slides with Implementation Stats Of Big Data Analytics For Cyber Protection. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Implementation, Data Analytics, Cybersecurity.
-
 Strategies For Big Data Cyber Protection Analytics
Strategies For Big Data Cyber Protection AnalyticsThe following slide highlights key points like data collection, data normalization, expansion, enrichment, automation, standardization, and advanced detection to show strategies for big data analytics cybersecurity. It helps organizations to proactively defend against cyber threats and enhance overall security posture. Introducing our premium set of slides with Strategies For Big Data Cyber Protection Analytics. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Collection, Data Normalization, Expansion. So download instantly and tailor it with your information.
-
 Types Of Wireless Internet Security For Data Protection
Types Of Wireless Internet Security For Data ProtectionThe following slide highlights key points such as WEP, WPA, WPA2, and WPA3 protocols to show types of wireless internet security for privacy protection. It helps in understanding and comparing different safety procedures for effective data protection. Introducing our premium set of slides with Types Of Wireless Internet Security For Data Protection. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Protection, Wireless Internet. So download instantly and tailor it with your information.
-
 Csirt Cyber Security Icon For Protecting Data
Csirt Cyber Security Icon For Protecting DataIntroducing our premium set of slides with Csirt Cyber Security Icon For Protecting Data. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Csirt Cyber Security, Protecting Data. So download instantly and tailor it with your information.
-
 Cybersecurity Incident Response Icon For Data Protection
Cybersecurity Incident Response Icon For Data ProtectionIntroducing our premium set of slides with name Cybersecurity Incident Response Icon For Data Protection. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cybersecurity Incident, Response Icon, Data Protection. So download instantly and tailor it with your information.
-
 Data Encryption For Mobile Protection Icon
Data Encryption For Mobile Protection IconPresenting our set of slides with name Data Encryption For Mobile Protection Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Encryption, Mobile Protection, Icon.
-
 Impact Of Encryption On Various Industries For Data Protection
Impact Of Encryption On Various Industries For Data ProtectionThis slide represents impact of encryption in various industries which assists organization to protect their financial data and customers information. It includes impact of encryption in various industries such as financial services, government, manufacturing, etc. Presenting our well structured Impact Of Encryption On Various Industries For Data Protection. The topics discussed in this slide are Financial Services, Government, Manufacturing. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Security Management Framework For Enhancing Data Protection
Security Management Framework For Enhancing Data ProtectionThis slide presents the framework that helps businesses to manage data security against modern attack vectors and network vulnerabilities. It includes various elements such as govern, discover, insights, protect and monitor. Presenting our well structured Security Management Framework For Enhancing Data Protection. The topics discussed in this slide are Privacy Readiness, Risk And Security Analytics, Data Driven Outcomes. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cybersecurity Measures For Protecting Sensitive Data
Cybersecurity Measures For Protecting Sensitive DataThe highlighted slide underscores essential elements such as organized information, encryption, assessment, masking, and authentication setup. These measures collectively contribute to effective cybersecurity, enhancing the protection of sensitive data. Introducing our Cybersecurity Measures For Protecting Sensitive Data set of slides. The topics discussed in these slides are Enable Data Encryption, Data Obfuscation, Organize And Classify Data. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Process To Develop Cybersecurity Strategy For Data Protection
Process To Develop Cybersecurity Strategy For Data ProtectionIntroducing our premium set of slides with Process To Develop Cybersecurity Strategy For Data Protection. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Threat Landscape, Cybersecurity Maturity, Cybersecurity Program Improvement. So download instantly and tailor it with your information.
-
 Privacy Project Icon For Data Protection
Privacy Project Icon For Data ProtectionPresenting our set of slides with name Privacy Project Icon For Data Protection. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Privacy Project Icon, Data Protection.
-
 BCP Icon For Enhancing Data Protection And Cybersecurity
BCP Icon For Enhancing Data Protection And CybersecurityPresenting our set of slides with BCP Icon For Enhancing Data Protection And Cybersecurity This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on BCP Icon For Enhancing, Data Protection, Cybersecurity
-
 Best Practices To Improve Cybersecurity In BCP For Data Protection
Best Practices To Improve Cybersecurity In BCP For Data ProtectionThis slide represents various best practices that helps businesses in improving cybersecurity against online data threats affecting business continuity. It includes practices such as using VPN, Training employees, backing up companies data, etc. Presenting our set of slides with Best Practices To Improve Cybersecurity In BCP For Data Protection This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Continuity Software, Backup Company, Train Employees
-
 Applications Of SCADA Cybersecurity Tools For Data Protection
Applications Of SCADA Cybersecurity Tools For Data ProtectionThis slide represents various applications of SCADA cybersecurity tools that assist IT companies to enhance their data protection effectively. It includes various applications such as data encryption, vulnerability assessment, etc. Introducing our premium set of slides with Applications Of SCADA Cybersecurity Tools For Data Protection Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Intrusion Detection Systems, Firewalls And Network Segmentation, Encryption And Secure Protocols. So download instantly and tailor it with your information.
-
 Working Model Of SCADA Cybersecurity For Data Protection
Working Model Of SCADA Cybersecurity For Data ProtectionThis slide represents working model of SCADA cybersecurity that assists IT companies to secure their data from vulnerable attacks. It includes various components such as impact analysis, mitigation strategies, etc. Presenting our well structured Working Model Of SCADA Cybersecurity For Data Protection The topics discussed in this slide are Remedial, Prevention, Decision Making. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Significance Of Cloud Storage Management For Data Protection
Significance Of Cloud Storage Management For Data ProtectionThis slide highlights importance of online storage management techniques. The purpose of this slide is to enable organizations in understanding the derived benefits from using cloud storage for ensuring efficient operations. It includes elements such as security, compliance, etc. Introducing our premium set of slides with Significance Of Cloud Storage Management For Data Protection. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security, Compliance, Data Governance. So download instantly and tailor it with your information.
-
 Virtual Private Network VPN Using VPN For Healthcare Data Protection
Virtual Private Network VPN Using VPN For Healthcare Data ProtectionThis slide discusses the use of virtual private network for protection of data in healthcare and security. Increase audience engagement and knowledge by dispensing information using Virtual Private Network VPN Using VPN For Healthcare Data Protection. This template helps you present information on seven stages. You can also present information on Transforms Sensitive Data, Unreadable Ciphertext, Robust Protection, Healthcare Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Authentication In Application Security For Data Protection
Authentication In Application Security For Data ProtectionThis slide discusses about the overview of authentication in application security and the various elements of MFA. Increase audience engagement and knowledge by dispensing information using Authentication In Application Security For Data Protection. This template helps you present information on five stages. You can also present information on Knowledge Factor, Possession Factor, Biometric Factor, Data Protection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 End To End Encryption Icon For User Data Protection
End To End Encryption Icon For User Data ProtectionIncrease audience engagement and knowledge by dispensing information using End To End Encryption Icon For User Data Protection This template helps you present information on Three stages. You can also present information on End To End Encryption, Icon For User Data Protection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SaaS Security Icon For Protecting Confidential Data
SaaS Security Icon For Protecting Confidential DataPresenting our set of slides with SaaS Security Icon For Protecting Confidential Data. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on SaaS Security, Protecting Confidential Data.
-
 Different Types Of Visualization Security For Protecting Data
Different Types Of Visualization Security For Protecting DataThis slides showcases various types of visualization data. The main purpose of this template is to showcase data encryption for shared data. This includes role based access control, encrypted file sharing, regular security audits, etc. Introducing our premium set of slides with Different Types Of Visualization Security For Protecting Data. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Access Methods, Regular Security Audits, Encrypted File Sharing. So download instantly and tailor it with your information.
-
 Visualization Security Icon For Data Protection
Visualization Security Icon For Data ProtectionPresenting our set of slides with Visualization Security Icon For Data Protection. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Visualization Security, Data Protection.
-
 Data Masking Workflow For Optimizing Sensitive Information Protection
Data Masking Workflow For Optimizing Sensitive Information ProtectionThis slide represents flowchart of data masking that assist IT companies to enhance security of their sensitive data improving operational efficiency. It includes various steps such as metadata collection, sensitive data discovery, etc. Introducing our Data Masking Workflow For Optimizing Sensitive Information Protection set of slides. The topics discussed in these slides are Data Masking Definition, Data Masking Process, Data Subsetting Definition.This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Fintech Icon For Customer Data Protection
Fintech Icon For Customer Data ProtectionIntroducing our Fintech Icon For Customer Data Protection set of slides. The topics discussed in these slides are Fintech Icon, Customer Data ProtectionThis is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Multi Factor A For Business Data Protection Business Recovery Plan To Overcome Cyber Security Threat
Multi Factor A For Business Data Protection Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information leveraging multifactor authentication to increase cyber security. It includes key points such as failed login, geographic location, time of login, operating system, IP address, etc. Deliver an outstanding presentation on the topic using this Multi Factor A For Business Data Protection Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Time Of Login Attempt, Operating System, Source Of IP Address using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 E Commerce Cybersecurity Trends For Customer Data Protection
E Commerce Cybersecurity Trends For Customer Data ProtectionThis slide represents various cybersecurity trends that helps ecommerce companies to enhance data protection improving customer satisfaction. It includes trends such as new payment options, AI adoption, blockchain systems, etc. Presenting our set of slides with E Commerce Cybersecurity Trends For Customer Data Protection. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on New Payment Options, AI Adoption, Blockchain Systems.
-
 Ethical Standards To Enhance Cybersecurity For Data Protection
Ethical Standards To Enhance Cybersecurity For Data ProtectionThis slide represents various ethical standards that assist companies to enhance their cybersecurity for effect data protection. It includes various ethical standards such as integrity, professionalism, and credibility. Introducing our premium set of slides with Ethical Standards To Enhance Cybersecurity For Data Protection. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Ethical Standards, Cyber Security, Integrity. So download instantly and tailor it with your information.
-
 NIDS Cyber Security Icon For Sensitive Data Protection
NIDS Cyber Security Icon For Sensitive Data ProtectionIntroducing our premium set of slides with NIDS Cyber Security Icon For Sensitive Data Protection. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Protection, Sensitive, Cyber Security. So download instantly and tailor it with your information.
-
 Pam Framework For Optimizing Cyber Security And Data Protection
Pam Framework For Optimizing Cyber Security And Data ProtectionThis slide represents framework that assists companies to implement PAM cybersecurity to enhance their data protection and risk management. It includes various components such as use cases, defining requirements, architecture development, etc. Presenting our well structured Pam Framework For Optimizing Cyber Security And Data Protection. The topics discussed in this slide are Determine Use Cases, Define Requirements, Develop Architecture. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Applications Of Cyber Security In Banking For Data Protection
Applications Of Cyber Security In Banking For Data ProtectionThis slide represents cyber security applications in banking for data protection. This template aims to safeguard data and systems, ensure variety of cyber security tools and methodologies at access. It includes different approaches such as network security surveillance, software security, etc. Introducing our Applications Of Cyber Security In Banking For Data Protection set of slides. The topics discussed in these slides are Network Security Surveillance, Software Security, Risk Management. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.




