Powerpoint Templates and Google slides for Data Breaches
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Data Breach Response Plan Implementation Budget For Organization
Data Breach Response Plan Implementation Budget For OrganizationThis slide represents the estimated and actual cost of implementing data breach response plan in an organization. The cost categories are personnel, technology and tools, communication, legal and compliance, operational costs, and training and education. Present the topic in a bit more detail with this Data Breach Response Plan Implementation Budget For Organization. Use it as a tool for discussion and navigation on Technology And Tools, Communication, Legal Compliance, Operational Cost, Training And Education. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Response Plan Implementation Fix Vulnerabilities
Data Breach Response Plan Implementation Fix VulnerabilitiesThis slide represents actions to be taken, the responsible team, the deadline, and tasks for fixing vulnerabilities after a data breach. The action items include assessing Service Providers access privileges, reviewing network segmentation, monitoring, etc. Deliver an outstanding presentation on the topic using this Data Breach Response Plan Implementation Fix Vulnerabilities. Dispense information and present a thorough explanation of Review Network Segmentation, Communicate Transparently, Collaborate With Forensics Experts using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Response Plan Implementation Impact Assessment
Data Breach Response Plan Implementation Impact AssessmentThis slide represents the various aspects of the data breach impact assessment process. These are data type and sensitivity, data context and quality, the potential for individual identification from breached data, and circumstances of the breach. Present the topic in a bit more detail with this Data Breach Response Plan Implementation Impact Assessment. Use it as a tool for discussion and navigation on Data Type And Sensitivity, Data Context And Quality, Potential For Individual Identification. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Response Plan Implementation Notify Appropriate Parties
Data Breach Response Plan Implementation Notify Appropriate PartiesThis slide represents steps, actions, timeline, and responsible party for sending notifications to affected parties after a data breach. The measures include determining legal requirements, notifying law enforcement, notifying affected businesses, notifying individuals, etc. Deliver an outstanding presentation on the topic using this Data Breach Response Plan Implementation Notify Appropriate Parties. Dispense information and present a thorough explanation of Determine Legal Requirements, Notify Law Enforcement, Notify Affected Businesses using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Response Plan Implementation Secure Operations
Data Breach Response Plan Implementation Secure OperationsThis slide represents actions to be taken, the responsible team, the deadline, and tasks for securing operations after a data breach. The action items include secure physical areas, assemble expert team, consult with legal counsel, secure website and contact search engines, etc. Present the topic in a bit more detail with this Data Breach Response Plan Implementation Secure Operations. Use it as a tool for discussion and navigation on Secure Physical Areas, Assemble Expert Team, Consult With Legal Counsel, Secure Website. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Response Plan Information Included In Data Breach Notification
Data Breach Response Plan Information Included In Data Breach NotificationThis slide outlines the key points to be included in data breach notification. These are descriptions of the compromise, information stolen, actions taken to handle the situation, actions to protect individuals, relevant points of contacts in the organization, etc. Deliver an outstanding presentation on the topic using this Data Breach Response Plan Information Included In Data Breach Notification. Dispense information and present a thorough explanation of Actions To Protect Individuals, Data Breach Notification, Personal Data Compromised using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Response Plan Overview And Phases Ppt Ideas Example File
Data Breach Response Plan Overview And Phases Ppt Ideas Example FileThe purpose of this slide is to discuss the data breach response strategy and its different phases. The pre breach phases of data breach response plan are prepare and identify. The post breach phases include contain, eradicate, recover and review. Present the topic in a bit more detail with this Data Breach Response Plan Overview And Phases Ppt Ideas Example File. Use it as a tool for discussion and navigation on Containment, Assessment, Management, Data Breach Response Plan. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Response Plan Possible Causes Of Data Breach Attack
Data Breach Response Plan Possible Causes Of Data Breach AttackThis slide highlights the reasons behind the success of data breach attack. These include phishing attacks, unpatched software, malware, insider threats, third-party vulnerabilities, SQL Structured Query Language injections, unsecured APIs, etc. Deliver an outstanding presentation on the topic using this Data Breach Response Plan Possible Causes Of Data Breach Attack. Dispense information and present a thorough explanation of Phishing Attacks, Unpatched Software, Third Party Vulnerabilities, Structured Query Language using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Response Plan Possible Impact Of Data Security Breach
Data Breach Response Plan Possible Impact Of Data Security BreachThis slide outlines the immediate and longstanding expenses associated with data breaches. The direct business costs include government fines, public relations costs, attorney fees, cybersecurity investigations, operational disruption, etc. Present the topic in a bit more detail with this Data Breach Response Plan Possible Impact Of Data Security Breach. Use it as a tool for discussion and navigation on Customer Breach Notifications, Loss Of Customer Relationships, Operational Disruption, Damaged Brand Reputation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Response Plan Raci Matrix For Implementation Of Data Breach Response Plan
Data Breach Response Plan Raci Matrix For Implementation Of Data Breach Response PlanThis slide shows the matrix to assign multiple responsibilities to the different teams for the data breach response plan implementation. The responsibilities include alert and verification, impact assessment, rectification and notification. Deliver an outstanding presentation on the topic using this Data Breach Response Plan Raci Matrix For Implementation Of Data Breach Response Plan. Dispense information and present a thorough explanation of Assign Multiple Responsibilities, Data Breach Response Plan, Rectification And Notification using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Response Plan Responsibility Matrix For Fix Vulnerabilities Phase
Data Breach Response Plan Responsibility Matrix For Fix Vulnerabilities PhaseThis slide shows the matrix to assign multiple responsibilities to the different teams for the fix vulnerabilities phase of data breach response plan. The responsibilities include assess Service Providers access privileges, collaborate with forensic experts, etc. Present the topic in a bit more detail with this Data Breach Response Plan Responsibility Matrix For Fix Vulnerabilities Phase. Use it as a tool for discussion and navigation on Responsibilities, Customer Support Team, Review Network Segmentation, Fix Vulnerabilities Phase. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Response Plan Responsibility Matrix For Notify Appropriate Parties Phase
Data Breach Response Plan Responsibility Matrix For Notify Appropriate Parties PhaseThis slide shows the matrix to assign multiple responsibilities to the different teams for notifications phase of data breach response plan. The responsibilities include determine legal requirements, notify law enforcement, notify affected businesses, etc. Deliver an outstanding presentation on the topic using this Data Breach Response Plan Responsibility Matrix For Notify Appropriate Parties Phase. Dispense information and present a thorough explanation of Responsibility Matrix, Legal Requirements, Notify Law Enforcement, Notify Affected Businesses using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Response Plan Responsibility Matrix For Secure Operations Phase
Data Breach Response Plan Responsibility Matrix For Secure Operations PhaseThis slide shows the matrix to assign multiple responsibilities to the different teams for the secure operations phase of data breach response plan. The responsibilities include secure physical area, contact search engines, document investigation, etc. Present the topic in a bit more detail with this Data Breach Response Plan Responsibility Matrix For Secure Operations Phase. Use it as a tool for discussion and navigation on Secure Physical Area, Contact Search Engines, Document Investigation, Responsibility Matrix. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Response Plan Risks And Mitigation Strategies For Data Breach Response Plan
Data Breach Response Plan Risks And Mitigation Strategies For Data Breach Response PlanThe purpose of this slide is to discuss the challenges faced while handling data breaches. The critical components of this slide are the description of the risk, probability of occurrence, impact on system infrastructure, and possible mitigation strategies. Deliver an outstanding presentation on the topic using this Data Breach Response Plan Risks And Mitigation Strategies For Data Breach Response Plan. Dispense information and present a thorough explanation of Inadequate Employee Training, Weak Network Security, Regulatory Non Compliance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Response Plan Types Of Information Leaked In Data Breach
Data Breach Response Plan Types Of Information Leaked In Data BreachThis slide outlines the different forms of information loss in a data security breach. The major types of data leaked are customer personal data, payment information, purchase history, login credentials, personal preferences, social media links, etc. Deliver an outstanding presentation on the topic using this Data Breach Response Plan Types Of Information Leaked In Data Breach. Dispense information and present a thorough explanation of Customer Personal Data, Payment Information, Personal Preferences, Social Media Links using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Different Phases Of Data Breach Response Plan Implementation
Different Phases Of Data Breach Response Plan ImplementationThis slide outlines the steps involved in data breach response plan implementation. These are alert and verification, impact assessment, secure operations, fix vulnerabilities, notify appropriate parties, etc. Introducing Different Phases Of Data Breach Response Plan Implementation to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Alert And Verification, Impact Assessment, Secure Operations, Fix Vulnerabilities, using this template. Grab it now to reap its full benefits.
-
 Icons Slide For Data Breach Response Plan For Businesses Ppt Icon Microsoft
Icons Slide For Data Breach Response Plan For Businesses Ppt Icon MicrosoftIntroducing our well researched set of slides titled Icons Slide For Data Breach Response Plan For Businesses Ppt Icon Microsoft. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
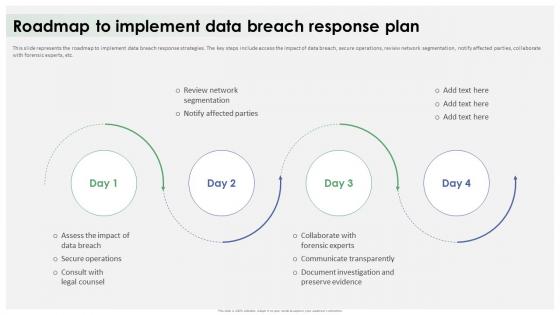 Roadmap To Implement Data Breach Response Plan Ppt Icon Information
Roadmap To Implement Data Breach Response Plan Ppt Icon InformationThis slide represents the roadmap to implement data breach response strategies. The key steps include access the impact of data breach, secure operations, review network segmentation, notify affected parties, collaborate with forensic experts, etc. Increase audience engagement and knowledge by dispensing information using Roadmap To Implement Data Breach Response Plan Ppt Icon Information. This template helps you present information on four stages. You can also present information on Data Breach Response Strategies, Secure Operations, Review Network Segmentation, Collaborate With Forensic Experts using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Steps For Developing A Data Breach Response Plan Ppt Icon Graphics Design
Steps For Developing A Data Breach Response Plan Ppt Icon Graphics DesignThis slide demonstrates the working of the data breach response plan. The steps involved in developing a response plan are preplanning exercises, define response teams and members, create a contact list, create a communication plan and perform incident response. Introducing Steps For Developing A Data Breach Response Plan Ppt Icon Graphics Design to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Preplanning Exercises, Perform Incident Response, Data Breach Response Plan, Create A Communications Plan, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents For Data Breach Response Plan For Businesses
Table Of Contents For Data Breach Response Plan For BusinessesIncrease audience engagement and knowledge by dispensing information using Table Of Contents For Data Breach Response Plan For Businesses. This template helps you present information on ten stages. You can also present information on Response Plan Creation, Response Team, Plan Execution Budget, Training Program, Response Plan Implementation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Team Structure For Data Breach Response Plan Implementation
Team Structure For Data Breach Response Plan ImplementationThis slide represents the team structure for the implementation of data breach response plan. The team members are legal and compliance representative, IT and technical representative, communication lead, forensic analyst, incident coordinator, etc. Introducing Team Structure For Data Breach Response Plan Implementation to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Team Structure, Data Breach Response Plan, Legal And Compliance Representative, Forensic Analyst, using this template. Grab it now to reap its full benefits.
-
 Timeline To Implement Data Breach Response Plan Ppt Icon Graphic Images
Timeline To Implement Data Breach Response Plan Ppt Icon Graphic ImagesThis slide shows the timeline for implementing data breach response plan. The key steps include access the impact of data breach, secure operations, review network segmentation, notify affected parties, collaborate with forensic experts, etc. Increase audience engagement and knowledge by dispensing information using Timeline To Implement Data Breach Response Plan Ppt Icon Graphic Images. This template helps you present information on five stages. You can also present information on Data Breach Response Plan, Secure Operations, Review Network Segmentation, Collaborate With Forensic Experts using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 List Of Major Data Breaches Occurred Due To Lack Of Encryption Encryption For Data Privacy In Digital Age It
List Of Major Data Breaches Occurred Due To Lack Of Encryption Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to provide an organized overview of major data breaches that occurred due to a lack of encryption. The main components are year of the breach, the affected company, the number of records compromised, and impact. Present the topic in a bit more detail with this List Of Major Data Breaches Occurred Due To Lack Of Encryption Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Compromised, Encryption, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Icon For Insurancing Data Breaches
Cyber Security Icon For Insurancing Data BreachesPresenting our set of slides with Cyber Security Icon For Insurancing Data Breaches. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security Icon, Insurancing Data Breaches.
-
 Digital Forensic Tools For Data Breach Incident Investigation
Digital Forensic Tools For Data Breach Incident InvestigationThis slide represents various tools that assist IT companies in conducting digital forensics to analyze and investigate data breach incidents effectively. It includes various tools such as Cellebrite, magnet axiom, and velociraptor. Present the topic in a bit more detail with this Digital Forensic Tools For Data Breach Incident Investigation. Use it as a tool for discussion and navigation on Magnet Axiom, Velociraptor, Cellebrite. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Contingency Risk Icon For Data Breaches
Contingency Risk Icon For Data BreachesIntroducing our Contingency Risk Icon For Data Breaches set of slides. The topics discussed in these slides are Contingency Risk Icon For Data Breaches. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Privacy Project For Data Breach And Incident Response
Privacy Project For Data Breach And Incident ResponseThe purpose of this slide is to highlight how privacy project for data breach and incident response strengthens cybersecurity by proactively addressing, swiftly detecting, and effectively responding to potential data breaches and incidents. Introducing our Privacy Project For Data Breach And Incident Response set of slides. The topics discussed in these slides are Date Of Discovery, Response Actions, Impact Assessment, Quantified Data. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data Breaches Related To Smart Contracts Ppt Styles Graphics Example
Data Breaches Related To Smart Contracts Ppt Styles Graphics ExampleThe purpose of this slide is to explain the data breaches related to smart contracts these include polynetwork attacks, grim finance reentrancy attacks, etc. Deliver an outstanding presentation on the topic using this Data Breaches Related To Smart Contracts Ppt Styles Graphics Example. Dispense information and present a thorough explanation of Poly Network Attack, Grim Finance Re Entrancy Attack, Cream Finance Flash Loan using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Case Study Data Breach Incident Recovery Business Recovery Plan To Overcome Cyber Security Threat
Case Study Data Breach Incident Recovery Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about a case study related to data breach recovery. It includes key elements such as incident date, challenges faced, LinkedIn response plan, and results. Deliver an outstanding presentation on the topic using this Case Study Data Breach Incident Recovery Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Regain Customer Trust, Rebuilding Business Reputation, Linkedin Response using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Confidential Information In Powerpoint And Google Slides Cpp
Data Breach Confidential Information In Powerpoint And Google Slides CppPresenting Data Breach Confidential Information In Powerpoint And Google Slides Cpp slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Data Breach Confidential Information. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Confidential Information Data Breach In Powerpoint And Google Slides Cpp
Confidential Information Data Breach In Powerpoint And Google Slides CppPresenting Confidential Information Data Breach In Powerpoint And Google Slides Cpp slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Confidential Information Data Breach. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Review Of Major Healthcare Data Breaches Globally Revolutionizing Health Services With Blockchain BCT SS
Review Of Major Healthcare Data Breaches Globally Revolutionizing Health Services With Blockchain BCT SSThis slide covers incidents where healthcare data security was compromised on a large scale in different entities, states, entity types, individuals affected and reasons of breach. Present the topic in a bit more detail with this Review Of Major Healthcare Data Breaches Globally Revolutionizing Health Services With Blockchain BCT SS. Use it as a tool for discussion and navigation on Covered Entity Type, Individuals Affected, Cause Of Breach. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Customer Data Breach Emergency Preparedness Checklist
Customer Data Breach Emergency Preparedness ChecklistThis slide represents customer data breach checklist for emergency preparedness including steps such as preplanning exercise, define response team, etc. Introducing our Customer Data Breach Emergency Preparedness Checklist set of slides. The topics discussed in these slides are Define Response Teams, Preplanning Exercises, Create Acommunications Plan. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Risk Management Case Study Mitigating Data Breach Risks Optimizing Risk Management Practices Risk SS
Risk Management Case Study Mitigating Data Breach Risks Optimizing Risk Management Practices Risk SSThis slide defines a case study on mitigating data breach risks faced by an insurance company, along with details related to the problems faced, solutions taken, and the resulting outcome. Introducing Risk Management Case Study Mitigating Data Breach Risks Optimizing Risk Management Practices Risk SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Risk Management, Mitigating Data Breach Risks, Frameworks And Regulations, using this template. Grab it now to reap its full benefits.
-
 Contingency Plan To Mitigate Customer Data Breach
Contingency Plan To Mitigate Customer Data BreachThis slide represents contingency plan to mitigate customer data breach including elements such as event, trigger points, event response, etc. Presenting our set of slides with Contingency Plan To Mitigate Customer Data Breach This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Supervisor, Trigger Points, Contingency Plan
-
 Web application firewall waf it implementation decreased risk data breach in web apps
Web application firewall waf it implementation decreased risk data breach in web appsThis slide represents the current status of the cyber attacks in an organization after implementing the web application firewall mechanism. Deliver an outstanding presentation on the topic using this Web Application Firewall Waf It Implementation Decreased Risk Data Breach In Web Apps. Dispense information and present a thorough explanation of Implementation, Misconfiguration, Organization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Detail Impact Information Security Can Reduce Risk Data Breach Organization
Information Security Detail Impact Information Security Can Reduce Risk Data Breach OrganizationThis slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver an outstanding presentation on the topic using this Information Security Detail Impact Information Security Can Reduce Risk Data Breach Organization. Dispense information and present a thorough explanation of Organization, Information, Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Assessment And Management Plan For Information Security Information And Data Breach Impacting
Risk Assessment And Management Plan For Information Security Information And Data Breach ImpactingDeliver an outstanding presentation on the topic using this Risk Assessment And Management Plan For Information Security Information And Data Breach Impacting. Dispense information and present a thorough explanation of Information, Business, Financial using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information And Data Breach Impacting Customer Loyalty Information Security Risk Management
Information And Data Breach Impacting Customer Loyalty Information Security Risk ManagementDeliver an outstanding presentation on the topic using this Information And Data Breach Impacting Customer Loyalty Information Security Risk Management. Dispense information and present a thorough explanation of Information, Data Breach Impacting, Customer Loyalty using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Application Firewall WAF Implementation Decreased the Risk of Data Breach in Web Apps
Application Firewall WAF Implementation Decreased the Risk of Data Breach in Web AppsThis slide represents the current status of the cyber attacks in an organization after implementing the web application firewall mechanism. Present the topic in a bit more detail with this Application Firewall WAF Implementation Decreased the Risk of Data Breach in Web Apps. Use it as a tool for discussion and navigation on SQL Injection, Ddos Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Average Costing On Risk Management For Data Breach Incident
Average Costing On Risk Management For Data Breach IncidentThis slide covers total cost incurred on response of data breach incident. It includes four categories such as incident detection and escalation, notifications, post breach response, lost business cost ,etc. Presenting our well structured Average Costing On Risk Management For Data Breach Incident. The topics discussed in this slide are Average Costing On Risk, Management, Data Breach Incident. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Breakdown Of Malicious Data Breach Risk Root Cause By Threat
Breakdown Of Malicious Data Breach Risk Root Cause By ThreatThis slide depicts division of data breach with root cause. It includes risk categories such as compromised credentials, cloud misconfiguration, third party software vulnerability, phishing, security compromise, social engineering, business email compromise, etc. Introducing our Breakdown Of Malicious Data Breach Risk Root Cause By Threat set of slides. The topics discussed in these slides are Social Engineering, Business Email Compromise, Malicious Insider. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data Breach Risks Stats On Social Media Platforms And Incident Sources
Data Breach Risks Stats On Social Media Platforms And Incident SourcesThis slide covers trends on social media data breach incidents reported. It also includes various sources of data theft such as malicious outsider, accidental loss, malicious insider, hacker, etc. Introducing our Data Breach Risks Stats On Social Media Platforms And Incident Sources set of slides. The topics discussed in these slides are Data Breach Risks, Stats On Social Media, Platforms And Incident Sources. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data Theft And Breach Risk Monitoring Dashboard
Data Theft And Breach Risk Monitoring DashboardThis slide covers dashboard to monitor top data breaches and loss of confidential data in organization. It includes KPIs such percentage of data risks detected, number of data risks, data risk analysis, response progress for data risks, data risk ratings. Presenting our well structured Data Theft And Breach Risk Monitoring Dashboard. The topics discussed in this slide are Data Theft And Breach, Risk Monitoring, Dashboard. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Information System Security And Risk Administration Information And Data Breach Impacting Customer Loyalty
Information System Security And Risk Administration Information And Data Breach Impacting Customer LoyaltyDeliver an outstanding presentation on the topic using this Information System Security And Risk Administration Information And Data Breach Impacting Customer Loyalty. Dispense information and present a thorough explanation of Business, Financial Data, Data Breach using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Consequences Of Data Breaches Faced By Organization Implementing Cyber Security Ppt Diagrams
Consequences Of Data Breaches Faced By Organization Implementing Cyber Security Ppt DiagramsThis slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Deliver an outstanding presentation on the topic using this Consequences Of Data Breaches Faced By Organization Implementing Cyber Security Ppt Diagrams. Dispense information and present a thorough explanation of Data Breaches, Consequences, Organization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
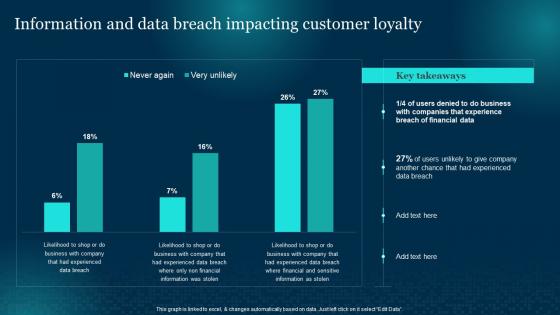 Cybersecurity Risk Analysis And Management Plan Information And Data Breach Impacting
Cybersecurity Risk Analysis And Management Plan Information And Data Breach ImpactingPresent the topic in a bit more detail with this Cybersecurity Risk Analysis And Management Plan Information And Data Breach Impacting. Use it as a tool for discussion and navigation on Information, Customer Loyalty, Financial Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information And Data Breach Impacting Customer Loyalty Formulating Cybersecurity Plan
Information And Data Breach Impacting Customer Loyalty Formulating Cybersecurity PlanPresent the topic in a bit more detail with this Information And Data Breach Impacting Customer Loyalty Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Information, Data Breach Impacting, Customer Loyalty. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Conducting Cyber Security Gap Analysis Of Organization Preventing Data Breaches Through Cyber Security
Conducting Cyber Security Gap Analysis Of Organization Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. Deliver an outstanding presentation on the topic using this Conducting Cyber Security Gap Analysis Of Organization Preventing Data Breaches Through Cyber Security. Dispense information and present a thorough explanation of Current State, Email, Business using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determining The Actors Behind Most Significant Cyber Attack Preventing Data Breaches Through Cyber Security
Determining The Actors Behind Most Significant Cyber Attack Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Present the topic in a bit more detail with this Determining The Actors Behind Most Significant Cyber Attack Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Online Criminals, Foreign Government Officials, Malicious Insiders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Statistics Showing The Impact Of Security Awarenesspreventing Data Breaches Through Cyber Security
Key Statistics Showing The Impact Of Security Awarenesspreventing Data Breaches Through Cyber SecurityPresent the topic in a bit more detail with this Key Statistics Showing The Impact Of Security Awarenesspreventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Employees, Security, Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Kpi Dashboard To Monitor Cyber Security Performance Preventing Data Breaches Through Cyber Security
Kpi Dashboard To Monitor Cyber Security Performance Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to highlight key performance indicator KPI dashboard which can be used to track the performance of organization cyber security. The KPI metrics covered in the slide are asset type control, control issues by standard and regulation etc. Deliver an outstanding presentation on the topic using this Kpi Dashboard To Monitor Cyber Security Performance Preventing Data Breaches Through Cyber Security. Dispense information and present a thorough explanation of Control Review Status, Management, Cyber Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Kpi Metrics Dashboard To Effectively Track Cyber Threat Preventing Data Breaches Through Cyber Security
Kpi Metrics Dashboard To Effectively Track Cyber Threat Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Present the topic in a bit more detail with this Kpi Metrics Dashboard To Effectively Track Cyber Threat Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Risk By Threats, Threat Report, Current Risk Status. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Measuring The Impact Of Security Awareness Training Preventing Data Breaches Through Cyber Security
Measuring The Impact Of Security Awareness Training Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. Present the topic in a bit more detail with this Measuring The Impact Of Security Awareness Training Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Security Awareness, Social Engineering. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Most Common Cyber Attack Faced By Our Employees Preventing Data Breaches Through Cyber Security
Most Common Cyber Attack Faced By Our Employees Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, IoT-based attacks, malware, social engineering attack and business email compromise. Introducing Most Common Cyber Attack Faced By Our Employees Preventing Data Breaches Through Cyber Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Ransomware, Password Attack, Cryptojacking, using this template. Grab it now to reap its full benefits.
-
 Operational Outlook Of Security Awareness Training Software Preventing Data Breaches Through Cyber Security
Operational Outlook Of Security Awareness Training Software Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered etc. Present the topic in a bit more detail with this Operational Outlook Of Security Awareness Training Software Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Finished Training, Awareness Factors, Training Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Practices To Improve Security Awareness Level Amongst The Preventing Data Breaches Through Cyber Security
Practices To Improve Security Awareness Level Amongst The Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to outline multiple ways which can be used by the organization to improve the cyber security awareness level of employees. The key practices mentioned in the slide are involving top level management, developing robust policies, and setting guidelines. Increase audience engagement and knowledge by dispensing information using Practices To Improve Security Awareness Level Amongst The Preventing Data Breaches Through Cyber Security. This template helps you present information on four stages. You can also present information on Get Management Involved, Develop Robust Policies, Set Guidelines using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Awareness Training Program Challenges Preventing Data Breaches Through Cyber Security
Security Awareness Training Program Challenges Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Increase audience engagement and knowledge by dispensing information using Security Awareness Training Program Challenges Preventing Data Breaches Through Cyber Security. This template helps you present information on five stages. You can also present information on Outdated Content, Employees Lose Interest, Burden On Administrators using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Attack Prevention Techniques Preventing Data Breaches Through Cyber Security
Social Engineering Attack Prevention Techniques Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no sharing of password. Present the topic in a bit more detail with this Social Engineering Attack Prevention Techniques Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Limit Public Information, Verify The Source, No Sharing Of Password. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents For Preventing Data Breaches Through Cyber Security Awareness
Table Of Contents For Preventing Data Breaches Through Cyber Security AwarenessDeliver an outstanding presentation on the topic using this Table Of Contents For Preventing Data Breaches Through Cyber Security Awareness. Dispense information and present a thorough explanation of Cyber Security Awareness, Online Courses, Automation Tools using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





