Powerpoint Templates and Google slides for Data Algorithms
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Working Of Rivest Shamir Adleman Algorithm Encryption For Data Privacy In Digital Age It
Working Of Rivest Shamir Adleman Algorithm Encryption For Data Privacy In Digital Age ItThis slide discusses the procedure of RSA asymmetric encryption algorithm. The purpose of this slide is to outline the two steps of Rivest Shamir Adleman RSA algorithm, named as key generation, and function of encryption and decryption. Deliver an outstanding presentation on the topic using this Working Of Rivest Shamir Adleman Algorithm Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Algorithm, Ciphered Data, Decrypted Plaintext Data using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
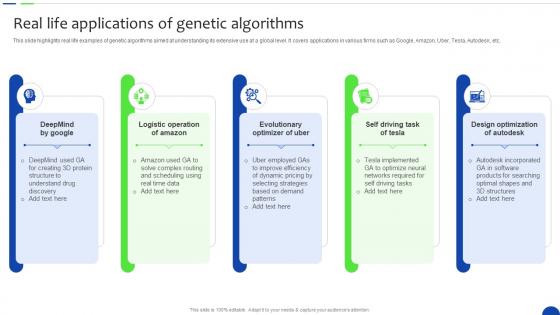 Real Life Applications Of Genetic Algorithms Unlocking The Power Of Prescriptive Data Analytics SS
Real Life Applications Of Genetic Algorithms Unlocking The Power Of Prescriptive Data Analytics SSThis slide highlights real life examples of genetic algorithms aimed at understanding its extensive use at a global level. It covers applications in various firms such as Google, Amazon, Uber, Tesla, Autodesk, etc. Increase audience engagement and knowledge by dispensing information using Real Life Applications Of Genetic Algorithms Unlocking The Power Of Prescriptive Data Analytics SS. This template helps you present information on five stages. You can also present information on Logistic Operation Of Amazon, Evolutionary Optimizer Of Uber, Self Driving Task Of Tesla using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Algorithms Computer Science Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Algorithms Computer Science Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful PowerPoint icon is perfect for any computer science presentation. It features a laptop with a blue and white background, representing the digital world of technology. It is a great way to add a professional touch to your presentation.
-
 Data Algorithms Computer Science Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Algorithms Computer Science Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone PowerPoint icon is perfect for any presentation on computer science. It features a simple, black-and-white design with a computer monitor and keyboard, symbolizing the world of technology. It is a great way to add a professional touch to your presentation.
-
 Data Design Algorithm Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Design Algorithm Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis Design Algorithm PowerPoint Icon is a vibrant, multi coloured vector graphic that can be used to illustrate complex algorithms in a visually appealing way. It is a perfect addition to any presentation or document, adding a touch of colour and energy to your work.
-
 Data Design Algorithm Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Design Algorithm Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone PowerPoint icon is a perfect addition to your design algorithm. It features an abstract shape with a black and white color scheme, making it a great choice for presentations and other projects. Its easy to customize and is sure to add a professional touch to your work.
-
 Data Structures Design Algorithm Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Structures Design Algorithm Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis Design Algorithm PowerPoint Icon is a vibrant, multi coloured vector graphic that can be used to illustrate complex algorithms in a visually appealing way. It is a perfect addition to any presentation or document, adding a touch of colour and energy to your work.
-
 Data Structures Design Algorithm Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Structures Design Algorithm Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone PowerPoint icon is a perfect addition to your design algorithm. It features an abstract shape with a black and white color scheme, making it a great choice for presentations and other projects. Its easy to customize and is sure to add a professional touch to your work.
-
 Data Mining A Complete Guide Types Of Machine Algorithms In Data Mining AI SS
Data Mining A Complete Guide Types Of Machine Algorithms In Data Mining AI SSThis slide showcases various types of machine learning algorithms often used by experts in the field of data mining. It provides information about supervised and un-supervised machine learning ML algorithms. Increase audience engagement and knowledge by dispensing information using Data Mining A Complete Guide Types Of Machine Algorithms In Data Mining AI SS. This template helps you present information on three stages. You can also present information on Supervised Ml Algorithms, Un Supervised Ml Algorithms, Unlabeled Data Sets using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Encryption Algorithms Data Encryption Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Encryption Algorithms Data Encryption Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis high quality coloured PowerPoint icon depicts Data Encryption Technology, with a bright and vibrant design. Perfect for presentations, brochures, and other digital projects. Easily add to your project to illustrate the importance of data security.
-
 Encryption Algorithms Data Encryption Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Encryption Algorithms Data Encryption Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon is a great visual representation of Data Encryption Technology. It is a simple and modern design that easily conveys the concept of secure data transmission. It is perfect for presentations on data security and encryption technology.
-
 Cryptographic Algorithms Used In Data Security Cloud Cryptography
Cryptographic Algorithms Used In Data Security Cloud CryptographyThis slide talks about algorithms used for implementing cryptography in data security. The purpose of this slide is to explain the different implementation steps. The techniques discussed are RSA Rivest, Shamir, Adleman cryptographic algorithm and Data Encryption Standard algorithm. Deliver an outstanding presentation on the topic using this Cryptographic Algorithms Used In Data Security Cloud Cryptography. Dispense information and present a thorough explanation of Cryptographic, Algorithms, Data Encryption Standard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Working Of Common Data Encryption Des Algorithm Cloud Cryptography
Working Of Common Data Encryption Des Algorithm Cloud CryptographyThis slide represents the working flow of Common Data Encryption DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc. Deliver an outstanding presentation on the topic using this Working Of Common Data Encryption Des Algorithm Cloud Cryptography. Dispense information and present a thorough explanation of Pseudorandom, Initialization, Independent using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 About Triple Data Encryption Algorithm Tdea Encryption For Data Privacy In Digital Age It
About Triple Data Encryption Algorithm Tdea Encryption For Data Privacy In Digital Age ItThis slide discusses the Triple data Encryption Algorithm TDEA which utilizes three keys. The purpose of this slide is to provide simplified illustration of the procedure to demonstrate how the TDEA encrypts plain text data into unreadable ciphertext. Present the topic in a bit more detail with this About Triple Data Encryption Algorithm Tdea Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Computational, Processing, Illustration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Advantages Of Rivest Shamir Adleman Encryption Algorithm Encryption For Data Privacy In Digital Age It
Advantages Of Rivest Shamir Adleman Encryption Algorithm Encryption For Data Privacy In Digital Age ItThis slide demonstrates the benefits of utilizing Rivest Shamir Adleman technique for data encryption. The advantages outlines in this slide are no key sharing, proof of authenticity, faster encryption, and no data modification. Increase audience engagement and knowledge by dispensing information using Advantages Of Rivest Shamir Adleman Encryption Algorithm Encryption For Data Privacy In Digital Age It. This template helps you present information on four stages. You can also present information on Proof Of Authenticity, Faster Encryption, Data Modification using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Algorithms Based On Elliptic Curve Cryptography Encryption For Data Privacy In Digital Age It
Algorithms Based On Elliptic Curve Cryptography Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to explain the applications of elliptic curve cryptography ECC in digital signatures, encryption, and key agreement. The algorithms discussed are ECDSA Elliptic Curve Digital Signature Algorithm, ECDH Elliptic Curve Diffie-Hellman, etc. Introducing Algorithms Based On Elliptic Curve Cryptography Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Digital Signatures, Minimal Computational Power, Fast Key Generation, using this template. Grab it now to reap its full benefits.
-
 Applications Of Elliptic Curve Cryptography Algorithm Encryption For Data Privacy In Digital Age It
Applications Of Elliptic Curve Cryptography Algorithm Encryption For Data Privacy In Digital Age ItThis slide outlines the various fields which employ Elliptic Curve Cryptography algorithm to provide security. The applications of ECC discussed in this slide are Tor, National Security Agency NSA, blockchain, iMessage and Secure Sockets Layer SSL. Introducing Applications Of Elliptic Curve Cryptography Algorithm Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Blockchain, Cryptography Algorithm, Applications, using this template. Grab it now to reap its full benefits.
-
 Asymmetric Cryptography Using Digital Signature Algorithm Encryption For Data Privacy In Digital Age It
Asymmetric Cryptography Using Digital Signature Algorithm Encryption For Data Privacy In Digital Age ItThis slide demonstrates the working of Digital Signature Algorithm. The purpose of this slide is to outline the benefits of DSA asymmetric cryptography. The advantages of DSA are message authentication, identity verification and non-repudiation. Present the topic in a bit more detail with this Asymmetric Cryptography Using Digital Signature Algorithm Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Message Authentication, Integrity Verification, Non Repudiation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Benefits Of Data Encryption Standard Algorithm Encryption For Data Privacy In Digital Age It
Benefits Of Data Encryption Standard Algorithm Encryption For Data Privacy In Digital Age ItThis slide demonstrates the advantages and disadvantages of Data Encryption Standard DES algorithm. The benefits include secure against brute-force attacks, robust level of encryption, suitable for resource-constrained devices and applications, etc. Present the topic in a bit more detail with this Benefits Of Data Encryption Standard Algorithm Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Data Encryption, Demonstrates, Applications. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Benefits Of Elliptic Curve Cryptography Algorithm Encryption For Data Privacy In Digital Age It
Benefits Of Elliptic Curve Cryptography Algorithm Encryption For Data Privacy In Digital Age ItThis slide represents the advantages of Elliptic Curve Cryptography algorithm ECC. The benefits discussed in this slide are shorter key lengths, minimal computational power, faster key generation and incredibly fast generation of digital signatures. Increase audience engagement and knowledge by dispensing information using Benefits Of Elliptic Curve Cryptography Algorithm Encryption For Data Privacy In Digital Age It. This template helps you present information on four stages. You can also present information on Shorter Key Lengths, Minimal Computational Power, Fast Key Generation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Benefits Of Standard For Advanced Encryption Algorithm Encryption For Data Privacy In Digital Age It
Benefits Of Standard For Advanced Encryption Algorithm Encryption For Data Privacy In Digital Age ItThis slide demonstrates the advantages and disadvantages of Standard for Advanced Encryption AES algorithm. The benefits include most reliable security protocol, longer key sizes, used for commercial and open-source solutions for many businesses, etc. Present the topic in a bit more detail with this Benefits Of Standard For Advanced Encryption Algorithm Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Encryption, Algorithm, Commercial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Benefits Of Triple Data Encryption Standard Algorithm Encryption For Data Privacy In Digital Age It
Benefits Of Triple Data Encryption Standard Algorithm Encryption For Data Privacy In Digital Age ItThis slide represents the advantages and disadvantages of Triple Data Encryption Standard TDES algorithm. The benefits include strong security, compatibility, simplicity and disadvantages are performance, key length limitation, vulnerability to attacks etc. Deliver an outstanding presentation on the topic using this Benefits Of Triple Data Encryption Standard Algorithm Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Data Encryption, Compatibility, Performance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparison Aes And Des Symmetric Algorithm Encryption For Data Privacy In Digital Age It
Comparison Aes And Des Symmetric Algorithm Encryption For Data Privacy In Digital Age ItThis slide represents the differences between Standard for Advanced Encryption AES and Data Encryption Standard DES algorithm. The comparison is carried out based on different factors such as algorithm type, key size, security strength, key expansion, etc. Deliver an outstanding presentation on the topic using this Comparison Aes And Des Symmetric Algorithm Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Comparison, Key Expansion, Symmetric Algorithm using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparison Rsa And Dsa Asymmetric Algorithm Encryption For Data Privacy In Digital Age It
Comparison Rsa And Dsa Asymmetric Algorithm Encryption For Data Privacy In Digital Age ItThis slide represents the differences between RSA Rivest-Shamir-Adleman and DSA Digital Signature Algorithm. The comparison is carried out based on different factors such as algorithm type, key size, security strength, key generation, performance, etc. Present the topic in a bit more detail with this Comparison Rsa And Dsa Asymmetric Algorithm Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Asymmetric Algorithm, Comparison, Performance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Standard Algorithm Overview And Applications Encryption For Data Privacy In Digital Age It
Data Standard Algorithm Overview And Applications Encryption For Data Privacy In Digital Age ItThis slide discusses about Data Encryption Standard DES algorithm. The purpose of this slide is to demonstrate the various applications of DES algorithm such as secure data transmission, Automated teller machines, smart cards, etc. Present the topic in a bit more detail with this Data Standard Algorithm Overview And Applications Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Overview, Applications, Data Transmission. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Different Key Encryption Algorithms Encryption For Data Privacy In Digital Age It
Different Key Encryption Algorithms Encryption For Data Privacy In Digital Age ItThis slide demonstrates the various algorithms used to achieve asymmetric key cryptography to secure data transmission. The algorithms outlined are Elliptic Curve Cryptography ECC, RSA Rivest Shamir Adleman, Digital Signature Standard DSS, etc. Present the topic in a bit more detail with this Different Key Encryption Algorithms Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Asymmetric, Encryption, Algorithms. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Different Symmetric Key Encryption Algorithms Encryption For Data Privacy In Digital Age It
Different Symmetric Key Encryption Algorithms Encryption For Data Privacy In Digital Age ItThis slide demonstrates the various algorithms used to achieve symmetric key encryption to secure data transmission. The algorithms outlined are AES Advanced Encryption Standard, DES Data Encryption Standard, IDEA International Data Encryption Algorithm, Blowfish, etc. Deliver an outstanding presentation on the topic using this Different Symmetric Key Encryption Algorithms Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Symmetric, Encryption, Algorithms using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Disadvantages Of Elliptic Curve Cryptography Algorithm Encryption For Data Privacy In Digital Age It
Disadvantages Of Elliptic Curve Cryptography Algorithm Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to outline the drawbacks of using Elliptic Curve Cryptography ECC algorithm. The disadvantages of ECC algorithm are complicated implementation, random number generator, patents, signature verification, etc. Deliver an outstanding presentation on the topic using this Disadvantages Of Elliptic Curve Cryptography Algorithm Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Cryptography, Algorithm, Disadvantages using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Drawbacks Of Using Symmetric Algorithms For Data Encryption For Data Privacy In Digital Age It
Drawbacks Of Using Symmetric Algorithms For Data Encryption For Data Privacy In Digital Age ItThis slide demonstrates the flaws of existing symmetric encryption techniques. The purpose of this slide is to explain the various disadvantages of symmetric cryptography. These include key leakage risk, lack of attribution data, no management system, etc. Increase audience engagement and knowledge by dispensing information using Drawbacks Of Using Symmetric Algorithms For Data Encryption For Data Privacy In Digital Age It. This template helps you present information on four stages. You can also present information on Key Leakage Risk, Lack Of Attribution Data, No Management System using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Elliptic Curve Cryptography Ecc Asymmetric Algorithm Encryption For Data Privacy In Digital Age It
Elliptic Curve Cryptography Ecc Asymmetric Algorithm Encryption For Data Privacy In Digital Age ItThis slide discusses the Elliptic Curve Cryptography algorithm. The purpose of this slide is to elaborate the different uses of ECC algorithm. The uses of this algorithm are key agreement, mobile devices, cryptocurrency, etc. Present the topic in a bit more detail with this Elliptic Curve Cryptography Ecc Asymmetric Algorithm Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Algorithms, Asymmetric, Cryptography. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Features Affecting Working Of Des Algorithm Encryption For Data Privacy In Digital Age It
Key Features Affecting Working Of Des Algorithm Encryption For Data Privacy In Digital Age ItThis slide demonstrates the various properties of Data Encryption Standard DES algorithm. The characteristics outlined in this slide are block cyphers, several encryption cycles, 64-bit key, permutation and replacement, and backward compatibility. Introducing Key Features Affecting Working Of Des Algorithm Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Several Encryption Cycles, Permutation And Replacement, Backward Compatibility, using this template. Grab it now to reap its full benefits.
-
 Overview Of Different Data Encryption Algorithm Types Encryption For Data Privacy In Digital Age It
Overview Of Different Data Encryption Algorithm Types Encryption For Data Privacy In Digital Age ItThis slide outlines the several data encryption algorithms. The purpose of this slide is to divide all available cryptographic algorithms into two types of encryption, namely symmetric and asymmetric. These algorithms are 3DES encryption, Twofish encryption, etc. Introducing Overview Of Different Data Encryption Algorithm Types Encryption For Data Privacy In Digital Age It to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Encryption, Algorithm, Overview, using this template. Grab it now to reap its full benefits.
-
 Rivest Shamir Adleman Rsa Asymmetric Algorithm Encryption For Data Privacy In Digital Age It
Rivest Shamir Adleman Rsa Asymmetric Algorithm Encryption For Data Privacy In Digital Age ItThis slide discusses the Rivest Shamir Adleman RSA asymmetric algorithm. The purpose of this slide is to represent the benefits and applications of RSA algorithm. The uses of RSA algorithm includes hybrid encryption, digital signatures, etc. Present the topic in a bit more detail with this Rivest Shamir Adleman Rsa Asymmetric Algorithm Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Overview, Asymmetric, Algorithm. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Working For Advanced Encryption Aes Algorithm Encryption For Data Privacy In Digital Age It
Working For Advanced Encryption Aes Algorithm Encryption For Data Privacy In Digital Age ItThis slide demonstrates the functioning of Standard for Advanced Encryption AES algorithm. The purpose of this slide is to outline the different steps involved in the working of AES algorithm such as add round key, sub-bytes, shift rows, etc. Deliver an outstanding presentation on the topic using this Working For Advanced Encryption Aes Algorithm Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Algorithm, Encryption, Demonstrates using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Working Of Common Data Encryption Des Algorithm Encryption For Data Privacy In Digital Age It
Working Of Common Data Encryption Des Algorithm Encryption For Data Privacy In Digital Age ItThis slide represents the working flow of Data Encryption Standard DES algorithm. The purpose of this slide is to outline the algorithm steps. This slide also explains the DES modes of operation, which include Digital Codebook, Cipher Block Chaining, etc. Present the topic in a bit more detail with this Working Of Common Data Encryption Des Algorithm Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Data Encryption, Independent, Initialization Vector. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Working Steps Of Triple Data Encryption Algorithm Tdea Encryption For Data Privacy In Digital Age It
Working Steps Of Triple Data Encryption Algorithm Tdea Encryption For Data Privacy In Digital Age ItThis slide discusses the procedure of Triple Data Encryption Algorithm TDEA. The purpose of this slide is to explain the TDES encryption and decryption process using Data Encryption algorithm DEA and three keys named as K1, K2 and K3. Present the topic in a bit more detail with this Working Steps Of Triple Data Encryption Algorithm Tdea Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Encryption, Algorithm, Decryption. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Algorithm Data Processing And Analysis Icon
Algorithm Data Processing And Analysis IconIntroducing our Algorithm Data Processing And Analysis Icon set of slides. The topics discussed in these slides are Algorithm, Data Processing, Analysis Icon This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data Science Algorithms Course In Powerpoint And Google Slides Cpb
Data Science Algorithms Course In Powerpoint And Google Slides CpbPresenting our Data Science Algorithms Course In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Data Science Algorithms Course. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Introduction To Genetic Algorithms Description Unlocking The Power Of Prescriptive Data Analytics SS
Introduction To Genetic Algorithms Description Unlocking The Power Of Prescriptive Data Analytics SSThis slide provides an introduction to genetic algorithms aimed at stimulating natural selection to find optimal solutions . It covers description and operators of genetic algorithms. Introducing Introduction To Genetic Algorithms Description Unlocking The Power Of Prescriptive Data Analytics SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Selection Operator, Crossover Operator, Mutation Operator, using this template. Grab it now to reap its full benefits.
-
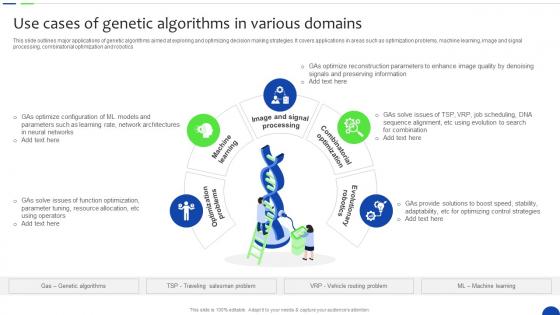 Use Cases Of Genetic Algorithms In Various Unlocking The Power Of Prescriptive Data Analytics SS
Use Cases Of Genetic Algorithms In Various Unlocking The Power Of Prescriptive Data Analytics SSThis slide outlines major applications of genetic algorithms aimed at exploring and optimizing decision making strategies. It covers applications in areas such as optimization problems, machine learning, image and signal processing, combinatorial optimization and robotics. Increase audience engagement and knowledge by dispensing information using Use Cases Of Genetic Algorithms In Various Unlocking The Power Of Prescriptive Data Analytics SS. This template helps you present information on five stages. You can also present information on Optimization Problems, Volution Combinatorial, Image And Signal Processing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Integrating Algorithms For Encrypting Data Securely Data Lifecycle Management To Enhance Flow
Integrating Algorithms For Encrypting Data Securely Data Lifecycle Management To Enhance FlowThis slide presents algorithms for encrypting data to ensure its protection and security. It includes types such as, AES advanced encryption standard and RSA rivest-shamir-adleman and ECC elliptic curve cryptography. Present the topic in a bit more detail with this Integrating Algorithms For Encrypting Data Securely Data Lifecycle Management To Enhance Flow. Use it as a tool for discussion and navigation on Encryption Algorithm, Key Characteristics, Implementation In Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data AES Algorithm Deployment For Data Encryption Cybersecurity SS
Encryption For Data AES Algorithm Deployment For Data Encryption Cybersecurity SSThis slide showcases advanced encryption standard AES algorithm deployment which can help employees learn basic techniques for data encryption. It provides details about AES engine, wireless communication, etc. Present the topic in a bit more detail with this Encryption For Data AES Algorithm Deployment For Data Encryption Cybersecurity SS. Use it as a tool for discussion and navigation on Controller, Organization, Potential Benefits. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Caesar Algorithm Implementation For Basic Encryption Cybersecurity SS
Encryption For Data Caesar Algorithm Implementation For Basic Encryption Cybersecurity SSThis slide showcases caesar algorithm deployment which can help employees learn basic techniques for basic encryption. It provides details about shift, displacement, shift value, decryption, etc. Introducing Encryption For Data Caesar Algorithm Implementation For Basic Encryption Cybersecurity SS to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Pre-Implementation Stage, Implementation Steps, Potential Benefit, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Key Management Algorithms And Dedicated Protocols Cybersecurity SS
Encryption For Data Key Management Algorithms And Dedicated Protocols Cybersecurity SSThis slide showcases key management protocols which can help companies increase efficiency and generation time. It provides details about hash functions, authentication, symmetric, etc. Introducing Encryption For Data Key Management Algorithms And Dedicated Protocols Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Cryptographic Hash Functions, Symmetric-Key Algorithms, Asymmetric-Key Algorithms, using this template. Grab it now to reap its full benefits.
-
 Comparative Assessment Of Encryption Algorithms For Organizational Data Security
Comparative Assessment Of Encryption Algorithms For Organizational Data SecurityThis slide provides a comparative assessment of various data encryption algorithms on different parameters. The multiple parameters used for assessment are encryption standard and use cases. Introducing our premium set of slides with Comparative Assessment Of Encryption Algorithms For Organizational Data Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Aes, Tdes, Twofish, Blowfish. So download instantly and tailor it with your information.
-
 Using AI ML Algorithms In Enhance Implementing Data Analytics To Enhance Telecom Data Analytics SS
Using AI ML Algorithms In Enhance Implementing Data Analytics To Enhance Telecom Data Analytics SSThis slide showcases trend of adoption of artificial intelligence solutions in telecom industry which helps in improving customer experience and drive innovation. It provides information regarding operational efficiency, network traffic, network error, decision making, service quality, service provisioning etc. Present the topic in a bit more detail with this Using AI ML Algorithms In Enhance Implementing Data Analytics To Enhance Telecom Data Analytics SS. Use it as a tool for discussion and navigation on Business Operational Efficiency, Effectively Predict Network Traffic, Identify Network Errors. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Encryption Algorithms For Security Solutions
Data Encryption Algorithms For Security SolutionsThe purpose of this slide is to demonstrate how data encryption algorithms for security solutions enhance protection. It encode data to prevent unauthorized access or manipulation. Introducing our Data Encryption Algorithms For Security Solutions set of slides. The topics discussed in these slides are Advanced Encryption Standard, Rivest Shamir Adleman, Elliptic Curve Cryptography. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Big Data And Algorithmic Biased In Powerpoint And Google Slides Cpp
Big Data And Algorithmic Biased In Powerpoint And Google Slides CppPresenting Big Data And Algorithmic Biased In Powerpoint And Google Slides Cpp slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Big Data And Algorithmic Biased. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Algorithm data compression diagram ppt powerpoint presentation portfolio graphics tutorials cpb
Algorithm data compression diagram ppt powerpoint presentation portfolio graphics tutorials cpbPresenting our Algorithm Data Compression Diagram Ppt Powerpoint Presentation Portfolio Graphics Tutorials Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Algorithm Data Compression Diagram This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Algorithms Data Structures Ppt Powerpoint Presentation Gallery Designs Cpb
Algorithms Data Structures Ppt Powerpoint Presentation Gallery Designs CpbPresenting our Algorithms Data Structures Ppt Powerpoint Presentation Gallery Designs Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Algorithms Data Structures. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Algorithm With Data Processing Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Algorithm With Data Processing Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Algorithm with data processing colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Algorithm With Data Processing Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Algorithm With Data Processing Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Algorithm with data processing monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Data Architecture And Program Algorithm Icon
Data Architecture And Program Algorithm IconIntroducing our Data Architecture And Program Algorithm Icon set of slides. The topics discussed in these slides are Data Architecture And Program, Algorithm Icon. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Big Data Algorithm Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Big Data Algorithm Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful PowerPoint icon is perfect for presentations on algorithms. It features a cog wheel with a series of arrows pointing inwards, representing the process of an algorithm. It is bright and eye-catching, making it ideal for any presentation.
-
 Big Data Algorithm Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Big Data Algorithm Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone powerpoint icon is a great visual representation of an algorithm. It features a simple, black and white design that is perfect for presentations, documents, and other projects. It is a great way to illustrate a complex concept in a simple and easy to understand way.
-
 Data Algorithms Hackers Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Algorithms Hackers Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis vibrant coloured PowerPoint icon is perfect for data hackers. It features a laptop with a magnifying glass, a chart, and a lightbulb, representing the creative and analytical process of data hacking.
-
 Data Algorithms Hackers Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Algorithms Hackers Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone powerpoint icon is perfect for data hackers. It features a silhouette of a person holding a laptop with a data chart projected onto a wall. Its a great way to represent the data hacking process and the power of data analysis.
-
 Data Driven Marketing Algorithm Structure Data Driven Decision Making To Build MKT SS V
Data Driven Marketing Algorithm Structure Data Driven Decision Making To Build MKT SS VThis slide represents the structure to effectively apply data driven marketing for effectively targeting most receptive customers and communicating relevant messages to them. It includes details related to procedure to apply data algorithm such as data collection culture, data collection etc. Increase audience engagement and knowledge by dispensing information using Data Driven Marketing Algorithm Structure Data Driven Decision Making To Build MKT SS V. This template helps you present information on four stages. You can also present information on Data, Collection, Elements using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Big Data Business Algorithm Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Big Data Business Algorithm Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is perfect for presentations on business algorithms. It features a colourful image of a graph, with a cog in the centre, representing the complex calculations of a business algorithm.
-
 Big Data Business Algorithm Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Big Data Business Algorithm Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone PowerPoint icon depicts a business algorithm. It is perfect for presentations and documents related to business processes, decision making, and strategy. It is a simple yet powerful image that conveys the complexity of modern business operations.




