Powerpoint Templates and Google slides for Cyberterrorism
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyberterrorism it powerpoint presentation slides
Cyberterrorism it powerpoint presentation slidesEnthrall your audience with this Cyberterrorism IT Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising seventy four slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Strategic Guide To Implement Strategies To Prevent Cyberterrorism Strategy CD
Strategic Guide To Implement Strategies To Prevent Cyberterrorism Strategy CDStep up your game with our enchanting Strategic Guide To Implement Strategies To Prevent Cyberterrorism Strategy CD deck, guaranteed to leave a lasting impression on your audience. Crafted with a perfect balance of simplicity, and innovation, our deck empowers you to alter it to your specific needs. You can also change the color theme of the slide to mold it to your companys specific needs. Save time with our ready-made design, compatible with Microsoft versions and Google Slides. Additionally, it's available for download in various formats including JPG, JPEG, and PNG. Outshine your competitors with our fully editable and customized deck.
-
 Introduction To Types Of Attacks In Cyberterrorism Strategic Guide To Implement Strategy SS
Introduction To Types Of Attacks In Cyberterrorism Strategic Guide To Implement Strategy SSThis slide showcases the different types of attacks in cyber terrorism. It includes attacks such as DoS and DDoS attack, Man-in-the-Middle MITM attack, Phishing attack, Whale phishing attack, Spear phishing attack and Ransomware attack.Increase audience engagement and knowledge by dispensing information using Introduction To Types Of Attacks In Cyberterrorism Strategic Guide To Implement Strategy SS. This template helps you present information on six stages. You can also present information on Whale Phishing Attack, Spear Phishing Attack, Ransomware Attack, Phishing Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyberterrorism Framework In Digital Age Strategic Guide To Implement Strategy SS
Cyberterrorism Framework In Digital Age Strategic Guide To Implement Strategy SSIncrease audience engagement and knowledge by dispensing information using Cyberterrorism Framework In Digital Age Strategic Guide To Implement Strategy SS. This template helps you present information on one stages. You can also present information on Threat Actors, Targeted Servers, Legitimate User, Obfuscate Their Identities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Dark Web And Encrypted Communications In Cyberterrorism Strategic Guide To Implement Strategy SS
Dark Web And Encrypted Communications In Cyberterrorism Strategic Guide To Implement Strategy SSThis slide showcases the Dark web and encrypted communications in cyber terrorism. It includes elements such as definition, characteristics, implications and use cases.Introducing Dark Web And Encrypted Communications In Cyberterrorism Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Privacy Implications, Use Cases, Characteristics, Define, using this template. Grab it now to reap its full benefits.
-
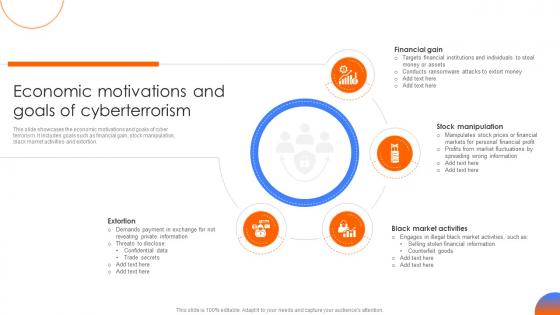 Economic Motivations And Goals Of Cyberterrorism Strategic Guide To Implement Strategy SS
Economic Motivations And Goals Of Cyberterrorism Strategic Guide To Implement Strategy SSThis slide showcases the economic motivations and goals of cyber terrorism. It includes goals such as financial gain, stock manipulation, black market activities and extortion.Introducing Economic Motivations And Goals Of Cyberterrorism Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Financial Gain, Stock Manipulation, Black Market Activities, Extortion, using this template. Grab it now to reap its full benefits.
-
 Global Historical Evolution Of Cyberterrorism Strategic Guide To Implement Strategy SS
Global Historical Evolution Of Cyberterrorism Strategic Guide To Implement Strategy SSThis slide showcases the global historical evolution od cyber terrorism. It includes some events such as start of hacking era, 414s group arrested, worm spread globally, WannaCry and NotPetya ransom ware attacks.Increase audience engagement and knowledge by dispensing information using Global Historical Evolution Of Cyberterrorism Strategic Guide To Implement Strategy SS. This template helps you present information on six stages. You can also present information on Supply Chain Attacks, Cyber Threats, University Systems, Hacking Activities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide For Strategic Guide To Implement Strategies To Prevent Cyberterrorism Strategy SS
Icons Slide For Strategic Guide To Implement Strategies To Prevent Cyberterrorism Strategy SSIntroducing our well researched set of slides titled Icons Slide For Strategic Guide To Implement Strategies To Prevent Cyberterrorism Strategy SS. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Ideological Motivations And Goals Of Cyberterrorism Strategic Guide To Implement Strategy SS
Ideological Motivations And Goals Of Cyberterrorism Strategic Guide To Implement Strategy SSThis slide showcases the Ideological motivations and goals of cyber terrorism. It includes goals such as anti-globalization, environmental activism, extremist ideologies and anti-corporate movements.Introducing Ideological Motivations And Goals Of Cyberterrorism Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Environmental Activism, Extremist Ideologies, Anti Corporate Movements, using this template. Grab it now to reap its full benefits.
-
 International Agreements And Treaties Of Cyberterrorism Strategic Guide To Implement Strategy SS
International Agreements And Treaties Of Cyberterrorism Strategic Guide To Implement Strategy SSThis slide showcases the International Agreements and Treaties of cyberterrorism. It includes agreements and treaties such as Budapest convention on cybercrime, united nations GGE reports, Tallinn manual, CCDCOE and US-EU privacy shield.Present the topic in a bit more detail with this International Agreements And Treaties Of Cyberterrorism Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Tallinn Manual, Budapest Convention, Privacy Shield, Addressing Cyber Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Major Categories Of Cyberterrorism For Data Protection Strategic Guide To Implement Strategy SS
Major Categories Of Cyberterrorism For Data Protection Strategic Guide To Implement Strategy SSThis slide showcases the major categories of cyber terrorism for data protection. It includes categories such as simple and unstructured, advanced-structure and complex-coordinated.Present the topic in a bit more detail with this Major Categories Of Cyberterrorism For Data Protection Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Advanced Structure, Complex Coordinated, Categories, Description. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Man In The Middle Mitm Attacks In Cyberterrorism Strategic Guide To Implement Strategy SS
Man In The Middle Mitm Attacks In Cyberterrorism Strategic Guide To Implement Strategy SSThis slide showcases the Man-in-the-Middle MITM Attacks in cyber terrorism. It includes mitigation startegies such as encryption, PKI, network security, 2FA and secure Wi-Fi.Introducing Man In The Middle Mitm Attacks In Cyberterrorism Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Mitigation Strategies, Account Security, Network Security, Encryption, using this template. Grab it now to reap its full benefits.
-
 Ongoing Threat Of Cyberterrorism In Digital Age Strategic Guide To Implement Strategy SS
Ongoing Threat Of Cyberterrorism In Digital Age Strategic Guide To Implement Strategy SSThis slide showcases the Ongoing Threat of Cyber terrorism in digital age. It includes key aspects such as constant evolution of tactics, wide-ranging targets, legislation and regulation and future perspectives.Deliver an outstanding presentation on the topic using this Ongoing Threat Of Cyberterrorism In Digital Age Strategic Guide To Implement Strategy SS. Dispense information and present a thorough explanation of Wide Ranging Targets, Legislation And Regulation, Future Perspectives using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Political Motivations And Goals Of Cyberterrorism Strategic Guide To Implement Strategy SS
Political Motivations And Goals Of Cyberterrorism Strategic Guide To Implement Strategy SSThis slide showcases the political motivation and goals of cyber terrorism. It includes goals such as nationalism and separatism, conflict and warfare, influence elections and revenge and retaliation.Increase audience engagement and knowledge by dispensing information using Political Motivations And Goals Of Cyberterrorism Strategic Guide To Implement Strategy SS. This template helps you present information on four stages. You can also present information on Conflict And Warfare, Nationalism And Separatism, Influence Elections using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Psychological Factors Of Cyberterrorism Identify Potential Risks Strategic Guide To Implement Strategy SS
Psychological Factors Of Cyberterrorism Identify Potential Risks Strategic Guide To Implement Strategy SSThis slide showcases the Psychological Factors of cyber terrorism identify potential risks. It includes goals such as revenge and grudges, mental helath isuues, desire for power and frustration and alienation.Present the topic in a bit more detail with this Psychological Factors Of Cyberterrorism Identify Potential Risks Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Mental Health Issues, Frustration And Alienation, Revenge And Grudges. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Role Of Interpol And Europol In Cyberterrorism Strategic Guide To Implement Strategy SS
Role Of Interpol And Europol In Cyberterrorism Strategic Guide To Implement Strategy SSThis slide showcases the Role of Interpol and Europol in cyber terrorism. It also includes role such as global network, digital forensics, coordination and EC3, investigation support, operational coordination and public awareness.Introducing Role Of Interpol And Europol In Cyberterrorism Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Global Network, Capacity Building, Digital Forensics, Coordination, using this template. Grab it now to reap its full benefits.
-
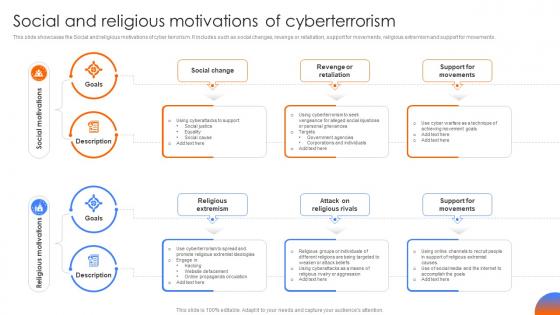 Social And Religious Motivations Of Cyberterrorism Strategic Guide To Implement Strategy SS
Social And Religious Motivations Of Cyberterrorism Strategic Guide To Implement Strategy SSThis slide showcases the Social and religious motivations of cyber terrorism. It includes such as social changes, revenge or retaliation, support for movements, religious extremism and support for movements.Present the topic in a bit more detail with this Social And Religious Motivations Of Cyberterrorism Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Description, Goals, Social Change, Social Motivations, Religious Motivations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents For Strategic Guide To Implement Strategies To Prevent Cyberterrorism Strategy SS
Table Of Contents For Strategic Guide To Implement Strategies To Prevent Cyberterrorism Strategy SSIncrease audience engagement and knowledge by dispensing information using Table Of Contents For Strategic Guide To Implement Strategies To Prevent Cyberterrorism Strategy SS. This template helps you present information on eight stages. You can also present information on Motivations And Goals, Cyberterrorist Actors, Conclusion, Future Trends using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Contents Strategic Guide To Implement Strategies To Prevent Cyberterrorism Strategy SS
Table Of Contents Strategic Guide To Implement Strategies To Prevent Cyberterrorism Strategy SSIntroducing Table Of Contents Strategic Guide To Implement Strategies To Prevent Cyberterrorism Strategy SS to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Intelligence Agencies, Cyber Security Initiatives, International Agreements, using this template. Grab it now to reap its full benefits.
-
 Cyberterrorism it average loss to firms in european countries ppt slides example
Cyberterrorism it average loss to firms in european countries ppt slides exampleThis slide depicts the average loss to firms in European countries, representing Germany as the most affected country. Present the topic in a bit more detail with this Cyberterrorism IT Average Loss To Firms In European Countries Ppt Slides Example. Use it as a tool for discussion and navigation on Cyber Terrorists Attacks, German Businesses, Damages Worth, Dollars. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyberterrorism it cyber terrorism faced by companies in us ppt slides deck
Cyberterrorism it cyber terrorism faced by companies in us ppt slides deckThis slide depicts the cyber terrorism faced by the companies in the US, and the graph represents the financial losses in the last five years. Deliver an outstanding presentation on the topic using this Cyberterrorism IT Cyber Terrorism Faced By Companies In US Ppt Slides Deck. Dispense information and present a thorough explanation of Financial Loss Million, Cyber Terrorism using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyberterrorism it cyber terrorism faced by various industries ppt slides model
Cyberterrorism it cyber terrorism faced by various industries ppt slides modelThis slide describes the cyber terrorism various industries face, including health, finance, media, transportation and education. Present the topic in a bit more detail with this Cyberterrorism IT Cyber Terrorism Faced By Various Industries Ppt Slides Model. Use it as a tool for discussion and navigation on Education, Transportation, Media, Healthcare, Government. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyberterrorism it dashboard for threat tracking of cyber terrorism
Cyberterrorism it dashboard for threat tracking of cyber terrorismThis slide depicts the dashboard for threat tracking of cyber terrorism by covering top threats, threats by class name, etc. Deliver an outstanding presentation on the topic using this Cyberterrorism IT Dashboard For Threat Tracking Of Cyber Terrorism. Dispense information and present a thorough explanation of Threats Per Month, Top Threat, Average Threats Detection Per Day using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyberterrorism it distributed denial of service ddos as cyber terrorism too
Cyberterrorism it distributed denial of service ddos as cyber terrorism tooThis slide explains the distributed denial of services DDOS as a cyber terrorism tool and the common types of DDOS attacks. Deliver an outstanding presentation on the topic using this Cyberterrorism IT Distributed Denial Of Service DDOS As Cyber Terrorism Too. Dispense information and present a thorough explanation of Service Denial, Disrupting Services, Ceasing Sites, 2019 To 2020 using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyberterrorism it impact of implementing cyber security measures in the company
Cyberterrorism it impact of implementing cyber security measures in the companyThis slide represents the current state of cyber assaults in a business after implementing the cyber security model. Present the topic in a bit more detail with this Cyberterrorism IT Impact Of Implementing Cyber Security Measures In The Company. Use it as a tool for discussion and navigation on Number Attacks, Cyber Terrorists Attacks 2021, Cyber Terrorists Attacks 2022. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyberterrorism it implement strong it guidelines in the company
Cyberterrorism it implement strong it guidelines in the companyThis slide depicts the strong IT guidelines which should be implemented in the company, such as security software, backups, fraud detection. Deliver an outstanding presentation on the topic using this Cyberterrorism IT Implement Strong IT Guidelines In The Company. Dispense information and present a thorough explanation of Requirements Regularly Updating Computers, Report Security Incidents, Required Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyberterrorism it installation and update of antivirus software
Cyberterrorism it installation and update of antivirus softwareThis slide represents the companys installation and update of antivirus software and the different antivirus software available in the market with the share of usage. Present the topic in a bit more detail with this Cyberterrorism IT Installation And Update Of Antivirus Software. Use it as a tool for discussion and navigation on Usage Antivirus, Bitdefender, Malwarebtyes Corporation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyberterrorism it agenda for cyber terrorism ppt slides diagrams
Cyberterrorism it agenda for cyber terrorism ppt slides diagramsIntroducing Cyberterrorism IT Agenda For Cyber Terrorism Ppt Slides Diagrams to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Terrorism, Current Situation, Globe And Tools, using this template. Grab it now to reap its full benefits.
-
 Cyberterrorism it assessment matrix of cyber terrorism ppt slides picture
Cyberterrorism it assessment matrix of cyber terrorism ppt slides pictureThis slide demonstrate cyber terrorism in terms of cybercriminal actors, as well as the financial impact of successful cyber terrorists attacks. Present the topic in a bit more detail with this Cyberterrorism IT Assessment Matrix Of Cyber Terrorism Ppt Slides Picture. Use it as a tool for discussion and navigation on Organized Criminals, Financial Theft Froud, Business Destruction. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyberterrorism it checklist to deal with cyber terrorism threats ppt slides templates
Cyberterrorism it checklist to deal with cyber terrorism threats ppt slides templatesThis slide represents the checklist to deal with cyber terrorism threats which involve 24 7 monitoring, employee training, keeping software updated. Increase audience engagement and knowledge by dispensing information using Cyberterrorism IT Checklist To Deal With Cyber Terrorism Threats Ppt Slides Templates. This template helps you present information on one stages. You can also present information on Incident Response Plan, Limited Access Privileges, Evaluating Risk Third Party Vendor, Cyber Security Assessment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyberterrorism it confidential data should be backup ppt slides clipart
Cyberterrorism it confidential data should be backup ppt slides clipartThis slide emphasizes the significance of backing up private data, which enables for data recovery in the event of an attack. Introducing Cyberterrorism IT Confidential Data Should Be Backup Ppt Slides Clipart to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Allow Data, Time, Business, Data Damage, Malicious Assaults, using this template. Grab it now to reap its full benefits.
-
 Cyberterrorism it cyber terrorism awareness programme for employees
Cyberterrorism it cyber terrorism awareness programme for employeesThis slide depicts the cyber terrorism awareness programm for employees, including the name of the participants and what modules would be covered under training. Present the topic in a bit more detail with this Cyberterrorism IT Cyber Terrorism Awareness Programme For Employees. Use it as a tool for discussion and navigation on Frontline Staff, IT Teams, Project Managers, Senior Executives. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyberterrorism it cyber terrorism issues faced by the company ppt slides styles
Cyberterrorism it cyber terrorism issues faced by the company ppt slides stylesThis slide represents the cyber terrorism issues faced by the company, such as increased costs, reputational damage, loss in revenue. Introducing Cyberterrorism IT Cyber Terrorism Issues Faced By The Company Ppt Slides Styles to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Increased Costs, Reputational Damage, Lost Revenue, Intellectual Property Theft, using this template. Grab it now to reap its full benefits.
-
 Cyberterrorism it cyber terrorist attacks experienced by company in previous financial year
Cyberterrorism it cyber terrorist attacks experienced by company in previous financial yearThis slide describes the number of cyber-terrorist attacks experienced by the company in the previous financial year 2020. Present the topic in a bit more detail with this Cyberterrorism IT Cyber Terrorist Attacks Experienced By Company In Previous Financial Year. Use it as a tool for discussion and navigation on Cyber Crime, Lowest Cyber Crimes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyberterrorism it disaster recovery plan for the business ppt summary graphics
Cyberterrorism it disaster recovery plan for the business ppt summary graphicsThis slide illustrates the elements that will be taken into account when establishing a recovery plan for company to go back to business swiftly and successfully. Increase audience engagement and knowledge by dispensing information using Cyberterrorism IT Disaster Recovery Plan For The Business Ppt Summary Graphics. This template helps you present information on three stages. You can also present information on Inventory Assets, Risk Assessment, Determine Importance Assets using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyberterrorism it employee access control protocols ppt slides files
Cyberterrorism it employee access control protocols ppt slides filesThis slide highlights how it is critical to limit employee rights and access in order to keep data safe and prevent it from being deleted or manipulated. Increase audience engagement and knowledge by dispensing information using Cyberterrorism IT Employee Access Control Protocols Ppt Slides Files. This template helps you present information on one stages. You can also present information on Physical Access Control, Proximity Card, Buildings, And Other Physical Assets, Access Control, Cyber Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyberterrorism it employee awareness training budget against cyber terrorism fy2020
Cyberterrorism it employee awareness training budget against cyber terrorism fy2020This slide demonstrates the employee awareness training budget against cyber-terrorism by a graph that includes the training date, and the degree of capacity. Present the topic in a bit more detail with this Cyberterrorism IT Employee Awareness Training Budget Against Cyber Terrorism FY2020. Use it as a tool for discussion and navigation on Provider, Training Date, Duration, Budget, Capability Level. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyberterrorism it financial loss faced by the business ppt slides idea
Cyberterrorism it financial loss faced by the business ppt slides ideaThis slide depicts the average financial loss faced by the business when projects of different scales are attacked. Increase audience engagement and knowledge by dispensing information using Cyberterrorism IT Financial Loss Faced By The Business Ppt Slides Idea. This template helps you present information on two stages. You can also present information on Average Financial Loss Per Cyber Attack, Small Project, Medium Project, Large Project using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyberterrorism it how to prevent ddos attacks in the company
Cyberterrorism it how to prevent ddos attacks in the companyThis slide represents the ways to prevent DDoS attacks in the company, which include network monitoring, updating security elements, etc. Introducing Cyberterrorism IT How To Prevent Ddos Attacks In The Company to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Service Providers, Cloud Services, Network Monitoring, Combat Cybercrime, using this template. Grab it now to reap its full benefits.
-
 Cyberterrorism it how to protect company from trojan attacks
Cyberterrorism it how to protect company from trojan attacksThis slide explains how to protect the company from trojan attacks which include procedures such as installing advanced antivirus software. Deliver an outstanding presentation on the topic using this Cyberterrorism IT How To Protect Company From Trojan Attacks. Dispense information and present a thorough explanation of Install Good Antivirus Programm, Web Application Firewall, Stick To Reliable Sources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyberterrorism it implementing least privilege administrative model
Cyberterrorism it implementing least privilege administrative modelThis slide depicts that administration and employees should have limited access to the information and confidential data. Introducing Cyberterrorism IT Implementing Least Privilege Administrative Model to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Employees Still, Phishing Emails, Limited Access, Control Risk Levels, Prevent Cybercriminals, using this template. Grab it now to reap its full benefits.
-
 Cyberterrorism it managing cyber terrorim 30 days plan
Cyberterrorism it managing cyber terrorim 30 days planThis slide demonstrates how the cyber security model would operate in the first 30 days and the duties that the company should concentrate on. Present the topic in a bit more detail with this Cyberterrorism IT Managing Cyber Terrorim 30 Days Plan. Use it as a tool for discussion and navigation on Phishing Awareness, Phishing Reporting, Phishing Repeat Offende, Facility Physical Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyberterrorism it managing cyber terrorism 60 days plan
Cyberterrorism it managing cyber terrorism 60 days planThis slide depicts the plan for the next 60 days after the firm has implemented the cyber security model to tackle cyber terrorism. Deliver an outstanding presentation on the topic using this Cyberterrorism IT Managing Cyber Terrorism 60 Days Plan. Dispense information and present a thorough explanation of Data Loss Incidents, Infected Computers, Policy Violations, Measures using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyberterrorism it managing cyber terrorism 90 days plan
Cyberterrorism it managing cyber terrorism 90 days planThis slide demonstrates the cyber security models 90 day strategy in an enterprise, as well as training compliance and communication strategies. Present the topic in a bit more detail with this Cyberterrorism IT Managing Cyber Terrorism 90 Days Plan. Use it as a tool for discussion and navigation on Training Completion, Communication Methods, Measured. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyberterrorism it peroration of cyber terrorism ppt slides layout
Cyberterrorism it peroration of cyber terrorism ppt slides layoutThis slide explains the conclusion or peroration of cyber terrorism and how it is different from information warfare as it targets civilians rather than operations. Increase audience engagement and knowledge by dispensing information using Cyberterrorism IT Peroration Of Cyber Terrorism Ppt Slides Layout. This template helps you present information on six stages. You can also present information on Cyber Terrorism, Information Warfare, Except IT Targets, Cyber Terrorism using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyberterrorism it phishing cyber terrorism tool ppt slides graphics
Cyberterrorism it phishing cyber terrorism tool ppt slides graphicsThis slide describes phishing in which an attacker tricks a victim to open an email, provide card credentials or any sensitive information. Introducing Cyberterrorism IT Phishing Cyber Terrorism Tool Ppt Slides Graphics to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Obtain Sensitive Information, Credit Card Details, Business, Consumer Confidence, using this template. Grab it now to reap its full benefits.
-
 Cyberterrorism it phishing techniques misused for cyber assault
Cyberterrorism it phishing techniques misused for cyber assaultThis slide represents phishing techniques used for cyber assaults or cyber terrorism, such as email phishing scams and whaling. Increase audience engagement and knowledge by dispensing information using Cyberterrorism IT Phishing Techniques Misused For Cyber Assault. This template helps you present information on four stages. You can also present information on Spear Phishing, Smishing And Vishing, Whaling, Email Phishing Scams using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyberterrorism it reputational loss faced by the company
Cyberterrorism it reputational loss faced by the companyThis slide demonstrates the reputational loss of the company due to cyber terrorism, which leads to the customers leaving and a decline in sales. Introducing Cyberterrorism IT Reputational Loss Faced By The Company to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Assaults Harm, Brand And Diminish, Resolved Claims, using this template. Grab it now to reap its full benefits.
-
 Cyberterrorism it roadmap to implement cyber security to mitigate cyber terrorism
Cyberterrorism it roadmap to implement cyber security to mitigate cyber terrorismThis slide depicts the roadmap to implement strategies to mitigate cyber terrorism such as training employees about cyber terrorism, creating personal accounts. Increase audience engagement and knowledge by dispensing information using Cyberterrorism IT Roadmap To Implement Cyber Security To Mitigate Cyber Terrorism. This template helps you present information on four stages. You can also present information on Creating Personal Accounts, Awareness Training Employees, Keep Hardware And Software Updated using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyberterrorism it scada system misused for cyber terrorism
Cyberterrorism it scada system misused for cyber terrorismThis slide describes the SCADA system as a tool misused for cyberterrorism and any damage to the SCADA can cause a major physical damage. Introducing Cyberterrorism IT SCADA System Misused For Cyber Terrorism to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on SCADA Operator Terminal, Alarm Monitor, Radio Cellular Telemetry, Control System Adjustments, Instrumentation Inputs, using this template. Grab it now to reap its full benefits.
-
 Cyberterrorism it simple advanced and complex types of cyber terrorism
Cyberterrorism it simple advanced and complex types of cyber terrorismThis slide explains the simple advanced and complex types of cyber terrorism i.e. simple structure, advanced structure, and complex coordinated around the 128 countries of the world. Increase audience engagement and knowledge by dispensing information using Cyberterrorism IT Simple Advanced And Complex Types Of Cyber Terrorism. This template helps you present information on three stages. You can also present information on Simple Structured, Advanced Structured, Complex Coordinated using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyberterrorism it structure of malicious code misused for cyber terrorism
Cyberterrorism it structure of malicious code misused for cyber terrorismThis slide depicts the structure of malicious code or malware and the four steps of the structure i.e. Probe, Program, Expose and Execute. Increase audience engagement and knowledge by dispensing information using Cyberterrorism IT Structure Of Malicious Code Misused For Cyber Terrorism. This template helps you present information on four stages. You can also present information on Prob, Program, Expose, Execute using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyberterrorism it table of contents for cyber terrorism ppt slides sample
Cyberterrorism it table of contents for cyber terrorism ppt slides samplePresent the topic in a bit more detail with this Cyberterrorism IT Table Of Contents For Cyber Terrorism Ppt Slides Sample. Use it as a tool for discussion and navigation on Assessment Matrix, Cyber Terrorism, Timeline, Dashboard, Threat Tracking. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyberterrorism it techniques to protect scada systems from cyber attacks
Cyberterrorism it techniques to protect scada systems from cyber attacksThis slide depicts the techniques to protect SCADA from cyber-attacks which include security training of employees, strict firewalls. Deliver an outstanding presentation on the topic using this Cyberterrorism IT Techniques To Protect SCADA Systems From Cyber Attacks. Dispense information and present a thorough explanation of Security Training, Employee, Access Controls, Strict Firewalls, Network Security Procedures using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyberterrorism it three major forms of cyber terrorism ppt slides tips
Cyberterrorism it three major forms of cyber terrorism ppt slides tipsThis slide describes the three major forms of cyber terrorism such as privacy violation, networks damage, and disruptions, and distribution denial of service attack. Introducing Cyberterrorism IT Three Major Forms Of Cyber Terrorism Ppt Slides Tips to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Privacy Violation, Networks Damage And Disruptions, Distributed Denial Service Attack, Cause Networks Damage And Their Disruptions, using this template. Grab it now to reap its full benefits.
-
 Cyberterrorism it timeline for implementation of cyber security in the company
Cyberterrorism it timeline for implementation of cyber security in the companyThis slide shows the timeframe for implementing a cyber security model in a business and the monthly activities that must be completed to fight cyber terrorism. Present the topic in a bit more detail with this Cyberterrorism IT Timeline For Implementation Of Cyber Security In The Company. Use it as a tool for discussion and navigation on Changes System, Network Passwords, Penetration Test. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyberterrorism it trojans as cyber terrorism tool ppt slides aids
Cyberterrorism it trojans as cyber terrorism tool ppt slides aidsThis slide depicts the Trojans as a cyber terrorism tool in which phishing is used to manipulate a user into executing the infected file. Deliver an outstanding presentation on the topic using this Cyberterrorism IT Trojans As Cyber Terrorism Tool Ppt Slides Aids. Dispense information and present a thorough explanation of Attacker Owned, Compromise Site, Downloader Trojan using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyberterrorism it types of ddos attacks in the company ppt slides show
Cyberterrorism it types of ddos attacks in the company ppt slides showThis slide demonstrates the types of DDoS attacks happening in the company, which include volume based attacks, protocol based attacks, and application layer attacks. Present the topic in a bit more detail with this Cyberterrorism IT Types Of Ddos Attacks In The Company Ppt Slides Show. Use it as a tool for discussion and navigation on Ddos Attack Volume, Based Attacks, Protocol Based Attacks, Application Layer Attacks, Volume Based Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyberterrorism it types of trojans misused in cyber terrorism ppt slides tips
Cyberterrorism it types of trojans misused in cyber terrorism ppt slides tipsThis slide describes the types of trojans misused in cyber terrorism, such as downloader trojan, spyware, backdoor trojan, and rootkit trojans. Introducing Cyberterrorism IT Types Of Trojans Misused In Cyber Terrorism Ppt Slides Tips to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Downloader Trojan, Backdoor Trojan, Spyware, Rootkit Trojans, using this template. Grab it now to reap its full benefits.
-
 Cyberterrorism it updating hardware and software in company
Cyberterrorism it updating hardware and software in companyThis slide describes the updating of hardware and software in the company, including upgrading operating systems. Increase audience engagement and knowledge by dispensing information using Cyberterrorism IT Updating Hardware And Software In Company. This template helps you present information on three stages. You can also present information on Peripheral Devices, Security Necessitates, Data Transport using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.




