Powerpoint Templates and Google slides for Cybersecurity Threat
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Insider Threats Awareness Training Program IT Security Awareness Training Cybersecurity SS
Insider Threats Awareness Training Program IT Security Awareness Training Cybersecurity SSThis slide represents details related to training program for mitigating threats that arises from within the targeted organization. It includes details related to mode of training, key learnings etc. Introducing Insider Threats Awareness Training Program IT Security Awareness Training Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Insider Threats Awareness, Training Program, Key Learnings, Mitigating Threats, using this template. Grab it now to reap its full benefits.
-
 IT Security Awareness Training Defense Against Cyber Threats Cybersecurity SS
IT Security Awareness Training Defense Against Cyber Threats Cybersecurity SSThis slide represents details related to ways security awareness training helps in preventing and mitigating common threats faced by organization such as data breaches, phishing attacks etc. Deliver an outstanding presentation on the topic using this IT Security Awareness Training Defense Against Cyber Threats Cybersecurity SS. Dispense information and present a thorough explanation of Data Breaches, Phishing Attacks, Insider Threats, Social Engineering using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Objectives Of Insider Threats Awareness Training IT Security Awareness Training Cybersecurity SS
Objectives Of Insider Threats Awareness Training IT Security Awareness Training Cybersecurity SSThis slide represents objectives of providing training for mitigating treats that originates from within the targeted organization. It includes objectives such as identify and report behaviors of insider threats etc. Increase audience engagement and knowledge by dispensing information using Objectives Of Insider Threats Awareness Training IT Security Awareness Training Cybersecurity SS. This template helps you present information on four stages. You can also present information on Unintentional Insider Threats, Malicious Or Unintentional Insider, Public And National Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Deploying Edr For Advanced Threat Protection Building Next Generation Endpoint Security Cybersecurity SS
Deploying Edr For Advanced Threat Protection Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases deploying endpoint detection and response EDR for advanced threat protection. It provides details about alert triage, containment, incident data search, etc.Deliver an outstanding presentation on the topic using this Deploying Edr For Advanced Threat Protection Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Advanced Threat Detection, Incident Data Search, Alert Triage using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Siem Tool To Address Potential Security Threats Building Next Generation Endpoint Security Cybersecurity SS
Siem Tool To Address Potential Security Threats Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases security information and event management SIEM tools which can help endpoint security teams detect and address potential security threats.Present the topic in a bit more detail with this Siem Tool To Address Potential Security Threats Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Collection, Detection, Investigation, Response. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Gantt Chart To Implement Mdr Cybersecurity Services For Threat Protection
Gantt Chart To Implement Mdr Cybersecurity Services For Threat ProtectionThis slide represents Gantt chart that assist companies to implement MDR cybersecurity services to enhance their data protection management. It includes steps such as defining needs, market research, budget consideration, comparison, etc. Introducing our Gantt Chart To Implement Mdr Cybersecurity Services For Threat Protection set of slides. The topics discussed in these slides are Cybersecurity, Services, Threat Protection. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Mdr Architecture To Mitigate Cybersecurity Threats Effectively
Mdr Architecture To Mitigate Cybersecurity Threats EffectivelyThis slide represents MDR architecture that assists companies in mitigating cybersecurity threats to enhance data protection effectively. It includes elements such as company infrastructure, MDR platforms, D and R teams, customers, etc. Presenting our well structured Mdr Architecture To Mitigate Cybersecurity Threats Effectively. The topics discussed in this slide are Architecture, Cybersecurity, Threats Effectively. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Mdr Cybersecurity Icon To Detect Data Threats
Mdr Cybersecurity Icon To Detect Data ThreatsPresenting our well structured Mdr Cybersecurity Icon To Detect Data Threats. The topics discussed in this slide are Cybersecurity, Data Threats. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Trends In Mdr Cybersecurity For Optimizing Threat Intelligence
Trends In Mdr Cybersecurity For Optimizing Threat IntelligenceThis slide represents various trends in MDR cybersecurity that assist companies to enhance their data protection against online threats. It includes trends such as Multi-cloud MDR, Digital risk protection services, and API security monitoring. Introducing our Trends In Mdr Cybersecurity For Optimizing Threat Intelligence set of slides. The topics discussed in these slides are Intelligence, Cybersecurity, Digital Risk Protection Services. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Global Mobile Security Threats Statistics Mobile Device Security Cybersecurity SS
Global Mobile Security Threats Statistics Mobile Device Security Cybersecurity SSThis side showcases statistics about global mobile threat and security. It highlights stats related to zero-day vulnerabilities, new malwares detected, phishing emails etc. Increase audience engagement and knowledge by dispensing information using Global Mobile Security Threats Statistics Mobile Device Security Cybersecurity SS This template helps you present information on Five stages. You can also present information on Mobile Devices, Malware Attack, SamplesWere Detected using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Mobile Threats Faced By Different Departments Mobile Device Security Cybersecurity SS
Mobile Threats Faced By Different Departments Mobile Device Security Cybersecurity SSThis slide showcases mobile security threats faced in different departments. Its key components are department, number of mobile threats and type of attacks Increase audience engagement and knowledge by dispensing information using Mobile Threats Faced By Different Departments Mobile Device Security Cybersecurity SS This template helps you present information on Three stages. You can also present information on Compliance, Incident Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Implementing Intrusion Prevention Fine Tune Detection Rules To Align With Threat Cybersecurity SS
Implementing Intrusion Prevention Fine Tune Detection Rules To Align With Threat Cybersecurity SSThis slide represents details related to fine-tuning threat detection rules for the implemented IPS software to effectively align with the organizations threat landscape. Present the topic in a bit more detail with this Implementing Intrusion Prevention Fine Tune Detection Rules To Align With Threat Cybersecurity SS. Use it as a tool for discussion and navigation on Preprocessor Rule, Standard Text Rule, Shared Object Rule. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Intrusion Prevention Identified Critical Assets And Threats Of Enterprise Cybersecurity SS
Implementing Intrusion Prevention Identified Critical Assets And Threats Of Enterprise Cybersecurity SSThis slide presents critical assets and associated threats, such as data breaches, information manipulation, data corruption, identity theft, etc., identified by the IT team. Present the topic in a bit more detail with this Implementing Intrusion Prevention Identified Critical Assets And Threats Of Enterprise Cybersecurity SS. Use it as a tool for discussion and navigation on Critical Assets, Network Infrastructure, Application Infrastructure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Password Authentication To Mitigate Threats Posed By Implementing Strategies For Mitigating Cybersecurity SS
Password Authentication To Mitigate Threats Posed By Implementing Strategies For Mitigating Cybersecurity SSThis slide outlines strategies to implement password authentication and mitigate threats from large-scale breaches. It includes strategies such as password hashing and salting.Introducing Password Authentication To Mitigate Threats Posed By Implementing Strategies For Mitigating Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Problem, Consequence, Reasons, Password Authentication, using this template. Grab it now to reap its full benefits.
-
 Password Authentication To Mitigate Threats Posed Implementing Strategies For Mitigating Cybersecurity SS
Password Authentication To Mitigate Threats Posed Implementing Strategies For Mitigating Cybersecurity SSThis slide outlines strategies for IT teams to implement secure password authentication, including deploying multi-factor authentication systems, scanning all newly created passwords etc.Present the topic in a bit more detail with this Password Authentication To Mitigate Threats Posed Implementing Strategies For Mitigating Cybersecurity SS. Use it as a tool for discussion and navigation on Add Additional Layers, Compromised Credentials, Lower Case Letters, Symbols. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Abs healthcare company records infected by minimize cybersecurity threats in healthcare company
Abs healthcare company records infected by minimize cybersecurity threats in healthcare companyThis slide shows the percentage of ABS Healthcare Company Records that are infected by Malware in the past 5 years. Deliver an outstanding presentation on the topic using this ABS Healthcare Company Records Infected By Minimize Cybersecurity Threats In Healthcare Company. Dispense information and present a thorough explanation of Abs Healthcare Company Records Infected By Malware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Challenge and solutions 1 malware and minimize cybersecurity threats in healthcare company
Challenge and solutions 1 malware and minimize cybersecurity threats in healthcare companyThis slide shows the problem that the company is facing related to malware and ransomware attacks on company softwares. Also, some solutions are provided to solve the problem. Present the topic in a bit more detail with this Challenge And Solutions 1 Malware And Minimize Cybersecurity Threats In Healthcare Company. Use it as a tool for discussion and navigation on Data Loss, Low Accessibility, Management, Security Softwares. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Challenge and solutions 2 cloud threats and minimize cybersecurity threats in healthcare company
Challenge and solutions 2 cloud threats and minimize cybersecurity threats in healthcare companyThis slide shows the problem that the company is facing related to cloud threats and security issues due to improper encryption and password protection. Additionally, the slide covers the key majors solutions which the company needs to follow. Deliver an outstanding presentation on the topic using this Challenge And Solutions 2 Cloud Threats And Minimize Cybersecurity Threats In Healthcare Company. Dispense information and present a thorough explanation of Encryption, Risk Of Infiltration, Data Encryption Techniques using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Challenge and solutions 3 employee error minimize cybersecurity threats in healthcare company
Challenge and solutions 3 employee error minimize cybersecurity threats in healthcare companyThis slide shows the problem that the company is facing related to improper and unaware employee behavior leading to data loss and misuse. Also, some solutions are provided to solve the problem. Present the topic in a bit more detail with this Challenge And Solutions 3 Employee Error Minimize Cybersecurity Threats In Healthcare Company. Use it as a tool for discussion and navigation on Data Security, Security Training Programs, Knowledge And Awareness. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Costs incurred to process faulty minimize cybersecurity threats in healthcare company
Costs incurred to process faulty minimize cybersecurity threats in healthcare companyThis slide shows the amount of costs that is incurred by the company to process and rectify faulty cybersecurity transactions for the past 5 years. Deliver an outstanding presentation on the topic using this Costs Incurred To Process Faulty Minimize Cybersecurity Threats In Healthcare Company. Dispense information and present a thorough explanation of Costs Incurred To Process Faulty Cybersecurity Transactions using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.v
-
 Estimated five year targets of company minimize cybersecurity threats in healthcare company
Estimated five year targets of company minimize cybersecurity threats in healthcare companyThis slide shows the estimated future trends of ABS Healthcare Company for 5 years after the implementation of Strategies. These targets are related to number of Cybersecurity Cases, Client Satisfaction Rate, Company Revenue etc. Present the topic in a bit more detail with this Estimated Five Year Targets Of Company Minimize Cybersecurity Threats In Healthcare Company. Use it as a tool for discussion and navigation on Cybersecurity Cases, Patient Satisfaction Rate, Company Revenue. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact on revenue due to increasing minimize cybersecurity threats in healthcare company
Impact on revenue due to increasing minimize cybersecurity threats in healthcare companyThis slide shows the reveanue trends of ABS Healthcare Company for the past 5 years. The revenue is constantly declining due to extra spend on faulty cybersecurity transactions. Deliver an outstanding presentation on the topic using this Impact On Revenue Due To Increasing Minimize Cybersecurity Threats In Healthcare Company. Dispense information and present a thorough explanation of Healthcare Company, Revenue, Revenue Trend using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
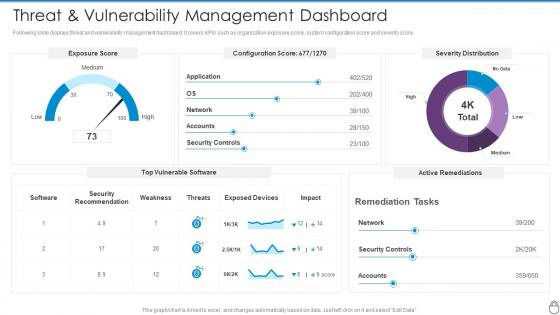 Cybersecurity Risk Management Framework Threat And Vulnerability Management Dashboard
Cybersecurity Risk Management Framework Threat And Vulnerability Management DashboardFollowing slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Present the topic in a bit more detail with this Cybersecurity Risk Management Framework Threat And Vulnerability Management Dashboard. Use it as a tool for discussion and navigation on Exposure Score, Configuration Score, Severity Distribution, Weakness, Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Threat Management Activities Tracking Dashboard Managing IT Threats At Workplace Overview
Cybersecurity Threat Management Activities Tracking Dashboard Managing IT Threats At Workplace OverviewThis slide provides details regarding cybersecurity threat management activities tracking dashboard in terms of breach risk trends, risk issues by owner, breach likelihood, etc. Present the topic in a bit more detail with this Cybersecurity Threat Management Activities Tracking Dashboard Managing IT Threats At Workplace Overview. Use it as a tool for discussion and navigation on Cybersecurity, Management, Tracking. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IoT Cybersecurity Technology Threat Management
IoT Cybersecurity Technology Threat ManagementThe below slide provides the data regarding the number of malware attacks detected and mitigated with the help of IoT security technology. The data is represented for past five years. Presenting our well structured IoT Cybersecurity Technology Threat Management. The topics discussed in this slide are Cybersecurity, Technology, Management. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Abs healthcare company overview minimize cybersecurity threats in healthcare company
Abs healthcare company overview minimize cybersecurity threats in healthcare companyThis slide shows details about ABC Carbonated Drink Company such as company type, employees, headquarters, annual revenue, CEO, founding year etc. Present the topic in a bit more detail with this ABS Healthcare Company Overview Minimize Cybersecurity Threats In Healthcare Company. Use it as a tool for discussion and navigation on Abs Healthcare Company Overview. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cost estimation for strategy minimize cybersecurity threats in healthcare company
Cost estimation for strategy minimize cybersecurity threats in healthcare companyThe slide shows the estimation of major cost involved in the next four years 2021 to 2025 for implementing the strategies. The strategies are implementing Data Encryption, Increase Employee Awareness, Restricting Access to Physical Devices etc. Present the topic in a bit more detail with this Cost Estimation For Strategy Minimize Cybersecurity Threats In Healthcare Company. Use it as a tool for discussion and navigation on Data Encryption, Market Research, Software Installation, Employee Awareness. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity dashboard for abs minimize cybersecurity threats in healthcare company
Cybersecurity dashboard for abs minimize cybersecurity threats in healthcare companyThis slide shows a cybersecurity dashboard with KPIs such as total cybersecurity cases in company in 2021, total records stoles, malware cases resolved, operational efficiency, mean time to resolve threats etc. Deliver an outstanding presentation on the topic using this Cybersecurity Dashboard For Abs Minimize Cybersecurity Threats In Healthcare Company. Dispense information and present a thorough explanation of Cybersecurity Cases, Phishing Attacks, Records Stolen, Operational Efficiency, Hacking Incidents using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Minimize cybersecurity threats in healthcare company for icons slide ppt infographic
Minimize cybersecurity threats in healthcare company for icons slide ppt infographicIntroducing our well researched set of slides titled Minimize Cybersecurity Threats In Healthcare Company For Icons Slide Ppt Infographic. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Risks involved and mitigation strategies minimize cybersecurity threats in healthcare company
Risks involved and mitigation strategies minimize cybersecurity threats in healthcare companyThe slide shows the risks associated with the implementation of strategy. Also, it provides the level of the risk low, medium or high, Potential Risk Impact on the Company and Key Strategies Measures for mitigating the risk. Present the topic in a bit more detail with this Risks Involved And Mitigation Strategies Minimize Cybersecurity Threats In Healthcare Company. Use it as a tool for discussion and navigation on Intellectual Property Risk, Malware Infection Risk, Customer Churn Risk. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategy to be adopted 3 restrict access to minimize cybersecurity threats in healthcare company
Strategy to be adopted 3 restrict access to minimize cybersecurity threats in healthcare companyThis slide shows the strategy to be adopted by the company i.e. restricting the access of Physical devices to authorized personnel only in order to avoid data misuse data leakage, security breach etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Introducing Strategy To Be Adopted 3 Restrict Access To Minimize Cybersecurity Threats In Healthcare Company to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Data Security, Hardware, Mobile Device Management, Security Policies, using this template. Grab it now to reap its full benefits.
-
 Swot analysis of abs healthcare company opportunity minimize cybersecurity threats in healthcare company
Swot analysis of abs healthcare company opportunity minimize cybersecurity threats in healthcare companyThis slide shows some opportunities of ABS Healthcare Company that that can lead to growth in future such as Technological Developments , Business Expansion, Easy Online Accessibility and Sales Opportunity etc. Increase audience engagement and knowledge by dispensing information using Swot Analysis Of Abs Healthcare Company Opportunity Minimize Cybersecurity Threats In Healthcare Company. This template helps you present information on four stages. You can also present information on Technological, Business Expansion, Online Accessibility, Opportunity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Swot analysis of abs healthcare company threats minimize cybersecurity threats in healthcare company
Swot analysis of abs healthcare company threats minimize cybersecurity threats in healthcare companyThis slide shows some threats that may effect the company in future course of time and impact the company profits. Some potential threats are High Cybersecurity Risks , Intense Competition Level , Government Regulations and Currency Fluctuations etc. Increase audience engagement and knowledge by dispensing information using Swot Analysis Of Abs Healthcare Company Threats Minimize Cybersecurity Threats In Healthcare Company. This template helps you present information on four stages. You can also present information on Cybersecurity Risks, Intense Competition, Government Regulations, Threat using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table of contents minimize cybersecurity threats in healthcare company ppt show templates
Table of contents minimize cybersecurity threats in healthcare company ppt show templatesDeliver an outstanding presentation on the topic using this Table Of Contents Minimize Cybersecurity Threats In Healthcare Company Ppt Show Templates. Dispense information and present a thorough explanation of Company Challenges, Competitive Analysis, Healthcare Company, Cybersecurity Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Agenda for advanced security monitoring plan to remove cybersecurity threat and data infraction
Agenda for advanced security monitoring plan to remove cybersecurity threat and data infractionIncrease audience engagement and knowledge by dispensing information using Agenda For Advanced Security Monitoring Plan To Remove Cybersecurity Threat And Data Infraction. This template helps you present information on seven stages. You can also present information on Agenda using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons slide for advanced security monitoring plan to remove cybersecurity threat and data infraction
Icons slide for advanced security monitoring plan to remove cybersecurity threat and data infractionIntroducing our well researched set of slides titled Icons Slide For Advanced Security Monitoring Plan To Remove Cybersecurity Threat And Data Infraction. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Table of contents advanced security monitoring plan to remove cybersecurity threat and data infraction
Table of contents advanced security monitoring plan to remove cybersecurity threat and data infractionPresent the topic in a bit more detail with this Table Of Contents Advanced Security Monitoring Plan To Remove Cybersecurity Threat And Data Infraction. Use it as a tool for discussion and navigation on Cybersecurity Monitoring Tools To Be Implemented, Essential Elements Of Security Monitoring Plan, Cybersecurity Monitoring Best Practices To Be Followed By The Company. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Program Cybersecurity Management Threat Vulnerability Asset Matrix
Information Security Program Cybersecurity Management Threat Vulnerability Asset MatrixMentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver an outstanding presentation on the topic using this Information Security Program Cybersecurity Management Threat Vulnerability Asset Matrix. Dispense information and present a thorough explanation of Threat Vulnerability Asset Matrix using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity Risk Management Framework Mitigation Plan For Resolving Encountered Threat
Cybersecurity Risk Management Framework Mitigation Plan For Resolving Encountered ThreatMentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Management Framework Mitigation Plan For Resolving Encountered Threat. Dispense information and present a thorough explanation of Security Breach, Data Backup Team, Asset Manager, Operational Downtime using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
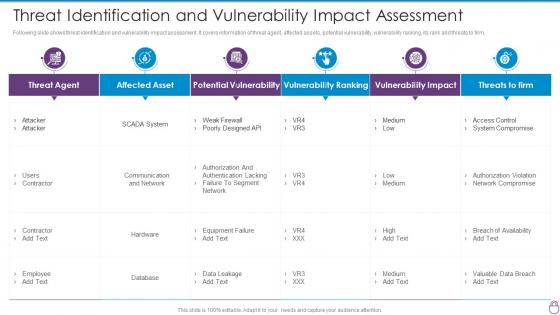 Cybersecurity Risk Management Framework Threat Identification And Vulnerability Impact
Cybersecurity Risk Management Framework Threat Identification And Vulnerability ImpactFollowing slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Management Framework Threat Identification And Vulnerability Impact. Dispense information and present a thorough explanation of Threat Agent, Affected Asset, Potential Vulnerability, Vulnerability Ranking, Vulnerability Impact using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Insider threat cybersecurity ppt powerpoint presentation summary outfit cpb
Insider threat cybersecurity ppt powerpoint presentation summary outfit cpbPresenting our Insider Threat Cybersecurity Ppt Powerpoint Presentation Summary Outfit Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Insider Threat Cybersecurity. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
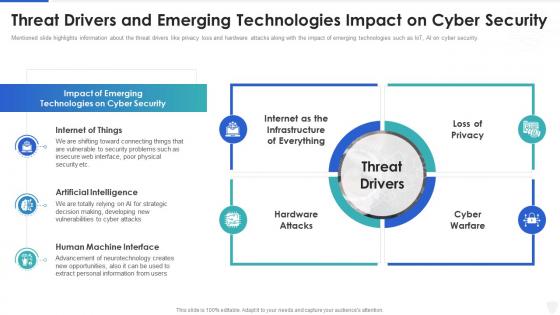 Cybersecurity and digital business risk management threat drivers and emerging technologies
Cybersecurity and digital business risk management threat drivers and emerging technologiesMentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. Deliver an outstanding presentation on the topic using this Cybersecurity And Digital Business Risk Management Threat Drivers And Emerging Technologies. Dispense information and present a thorough explanation of Internet Of Things, Artificial Intelligence, Human Machine Interface using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
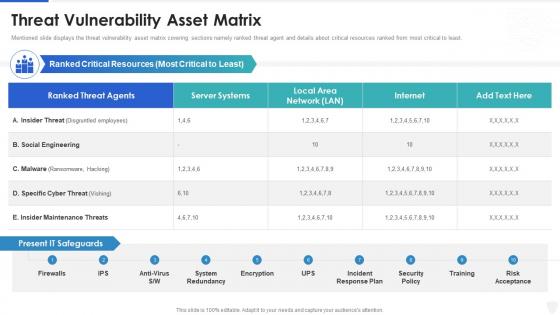 Cybersecurity and digital business risk management threat vulnerability asset matrix
Cybersecurity and digital business risk management threat vulnerability asset matrixMentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver an outstanding presentation on the topic using this Cybersecurity And Digital Business Risk Management Threat Vulnerability Asset Matrix. Dispense information and present a thorough explanation of Threat Vulnerability Asset Matrix using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Five Step Cybersecurity Threat Management Roadmap
Five Step Cybersecurity Threat Management RoadmapThis slide depicts cybersecurity roadmap for threat management illustrating five steps such as identification, analyzing, evaluation, responding and monitoring for identifying and analyzing potential cyber risk. Presenting our set of slides with name Five Step Cybersecurity Threat Management Roadmap. This exhibits information on five stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Analyzing, Identification, Responding, Monitoring, Evaluation.
-
 Major Indicators Of Cybersecurity Insider Threat
Major Indicators Of Cybersecurity Insider ThreatThis slide shows major indicators of cybersecurity insider threat along with mitigation strategies. It contains information about behavioral, information technology IT sabotage and data theft. Introducing our premium set of slides with Major Indicators Of Cybersecurity Insider Threat. Elucidate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Indicators, Potential Attack Probability, Mitigation Strategy. So download instantly and tailor it with your information.
-
 Top Cybersecurity Threats In Internet Banking
Top Cybersecurity Threats In Internet BankingThe following slide highlights major cybersecurity threats in banking sector while making digital transactions. It includes unencrypted data, malware, third part vendor, spoofing, phishing etc. Introducing our premium set of slides with Top Cybersecurity Threats In Internet Banking. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Third Party Services, Unencrypted Data, Phishing. So download instantly and tailor it with your information.
-
 Cybersecurity Insider Threat Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cybersecurity Insider Threat Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Cybersecurity insider threat colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Cybersecurity Insider Threat Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cybersecurity Insider Threat Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Cybersecurity insider threat monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Risk And Threats Landscape In Business Cybersecurity
Risk And Threats Landscape In Business CybersecurityThis slide showcases risk and threats landscape which can be referred by businesses to be aware of cybersecurity issues and attacks. It contains information about phishing, malware and blackmail hacking. Presenting our set of slides with Risk And Threats Landscape In Business Cybersecurity. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Phishing, Malware, Blackmail Hacking.
-
 Cybersecurity Threats Businesses In Powerpoint And Google Slides Cpb
Cybersecurity Threats Businesses In Powerpoint And Google Slides CpbPresenting our Cybersecurity Threats Businesses In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Cybersecurity Threats Businesses This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cybersecurity Risk Analysis And Management Plan Analysing The Impact Of Security Threats
Cybersecurity Risk Analysis And Management Plan Analysing The Impact Of Security ThreatsPresent the topic in a bit more detail with this Cybersecurity Risk Analysis And Management Plan Analysing The Impact Of Security Threats. Use it as a tool for discussion and navigation on Analysing, Organization, Security Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Risk Analysis And Management Plan Mitigation Plan For Resolving Encountered Threat
Cybersecurity Risk Analysis And Management Plan Mitigation Plan For Resolving Encountered ThreatMentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Analysis And Management Plan Mitigation Plan For Resolving Encountered Threat. Dispense information and present a thorough explanation of Encountered Threat, Description, Resources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Identifying Information Security Threats And Impact Cybersecurity Risk Analysis And Management Plan
Identifying Information Security Threats And Impact Cybersecurity Risk Analysis And Management PlanThis slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization Present the topic in a bit more detail with this Identifying Information Security Threats And Impact Cybersecurity Risk Analysis And Management Plan. Use it as a tool for discussion and navigation on Identifying, Information, Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Matrix For Threat Solution And Risk Management Cybersecurity Risk Analysis And Management Plan
Matrix For Threat Solution And Risk Management Cybersecurity Risk Analysis And Management PlanThis slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack Present the topic in a bit more detail with this Matrix For Threat Solution And Risk Management Cybersecurity Risk Analysis And Management Plan. Use it as a tool for discussion and navigation on Management, Solution, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat Identification And Vulnerability Assessment For Cybersecurity Risk Analysis And Management Plan
Threat Identification And Vulnerability Assessment For Cybersecurity Risk Analysis And Management PlanThis slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating Deliver an outstanding presentation on the topic using this Threat Identification And Vulnerability Assessment For Cybersecurity Risk Analysis And Management Plan. Dispense information and present a thorough explanation of Identification, Assessment, Vulnerability using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Analysing The Impact Of Security Threats On Organization Formulating Cybersecurity Plan
Analysing The Impact Of Security Threats On Organization Formulating Cybersecurity PlanPresent the topic in a bit more detail with this Analysing The Impact Of Security Threats On Organization Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Organization, Average Financial, Analysing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identifying Information Security Threats And Impact Formulating Cybersecurity Plan
Identifying Information Security Threats And Impact Formulating Cybersecurity PlanThis slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization. Introducing Identifying Information Security Threats And Impact Formulating Cybersecurity Plan to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Errors And Omissions, Fraud And Theft, Employee Sabotage, using this template. Grab it now to reap its full benefits.
-
 Matrix For Threat Solution And Risk Management Formulating Cybersecurity Plan
Matrix For Threat Solution And Risk Management Formulating Cybersecurity PlanThis slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack. Deliver an outstanding presentation on the topic using this Matrix For Threat Solution And Risk Management Formulating Cybersecurity Plan. Dispense information and present a thorough explanation of Block Malicious, Monitor Database Activity, Validate Database Protocols using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Mitigation Plan For Resolving Encountered Threat Formulating Cybersecurity Plan
Mitigation Plan For Resolving Encountered Threat Formulating Cybersecurity PlanMentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. Present the topic in a bit more detail with this Mitigation Plan For Resolving Encountered Threat Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Risk Mitigation Plan, Expected Resolution Time, Mitigation Plan. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Mitigation Strategies To Tackle Information Security Threats Formulating Cybersecurity Plan
Mitigation Strategies To Tackle Information Security Threats Formulating Cybersecurity PlanThis slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help organization to minimize the financial loss and maintain reputation of business. Increase audience engagement and knowledge by dispensing information using Mitigation Strategies To Tackle Information Security Threats Formulating Cybersecurity Plan. This template helps you present information on five stages. You can also present information on Malware, Phishing, Mitigation Strategies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.





