Powerpoint Templates and Google slides for Cybersecurity Systems
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Implementing Intrusion Prevention System For Effective Network Security Cybersecurity CD
Implementing Intrusion Prevention System For Effective Network Security Cybersecurity CDWhile your presentation may contain top-notch content, if it lacks visual appeal, you are not fully engaging your audience. Introducing our Implementing Intrusion Prevention System For Effective Network Security Cybersecurity CD deck, designed to engage your audience. Our complete deck boasts a seamless blend of Creativity and versatility. You can effortlessly customize elements and color schemes to align with your brand identity. Save precious time with our pre-designed template, compatible with Microsoft versions and Google Slides. Plus, it is downloadable in multiple formats like JPG, JPEG, and PNG. Elevate your presentations and outshine your competitors effortlessly with our visually stunning 100 percent editable deck.
-
 Cybersecurity System Powerpoint PPT Template Bundles
Cybersecurity System Powerpoint PPT Template BundlesEngage buyer personas and boost brand awareness by pitching yourself using this prefabricated set. This Cybersecurity System Powerpoint PPT Template Bundles is a great tool to connect with your audience as it contains high quality content and graphics. This helps in conveying your thoughts in a well structured manner. It also helps you attain a competitive advantage because of its unique design and aesthetics. In addition to this, you can use this PPT design to portray information and educate your audience on various topics. With twelve slides, this is a great design to use for your upcoming presentations. Not only is it cost effective but also easily pliable depending on your needs and requirements. As such color, font, or any other design component can be altered. It is also available for immediate download in different formats such as PNG, JPG, etc. So, without any further ado, download it now.
-
 Implementing Intrusion Prevention Gap Analysis For Intrusion Prevention System Cybersecurity SS
Implementing Intrusion Prevention Gap Analysis For Intrusion Prevention System Cybersecurity SSThis slide represents the gap analysis to help organizations understand the gaps so that they can build effective strategies to eliminate these gaps and achieve desired results. Present the topic in a bit more detail with this Implementing Intrusion Prevention Gap Analysis For Intrusion Prevention System Cybersecurity SS. Use it as a tool for discussion and navigation on Proactive Security Measures, Average Incident Response, Network Traffic Monitored. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
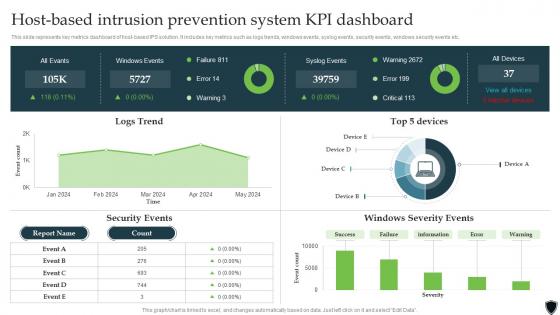 Implementing Intrusion Prevention Host Based Intrusion Prevention System KPI Cybersecurity SS
Implementing Intrusion Prevention Host Based Intrusion Prevention System KPI Cybersecurity SSThis slide represents key metrics dashboard of host-based IPS solution. It includes key metrics such as logs trends, windows events, syslog events, security events, windows security events etc. Present the topic in a bit more detail with this Implementing Intrusion Prevention Host Based Intrusion Prevention System Kpi Cybersecurity SS. Use it as a tool for discussion and navigation on Success, Failure, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
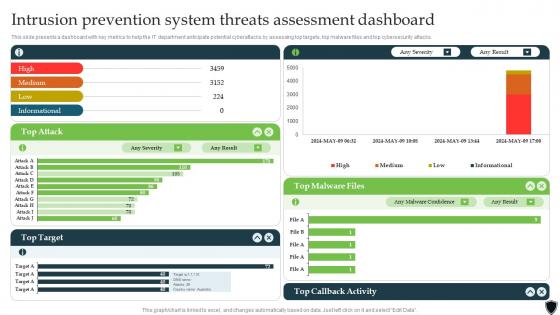 Implementing Intrusion Prevention Intrusion Prevention System Threats Assessment Cybersecurity SS
Implementing Intrusion Prevention Intrusion Prevention System Threats Assessment Cybersecurity SSThis slide presents a dashboard with key metrics to help the IT department anticipate potential cyberattacks by assessing top targets, top malware files and top cybersecurity attacks. Present the topic in a bit more detail with this Implementing Intrusion Prevention Intrusion Prevention System Threats Assessment Cybersecurity SS. Use it as a tool for discussion and navigation on Callback Activity, Malware Files, Target. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
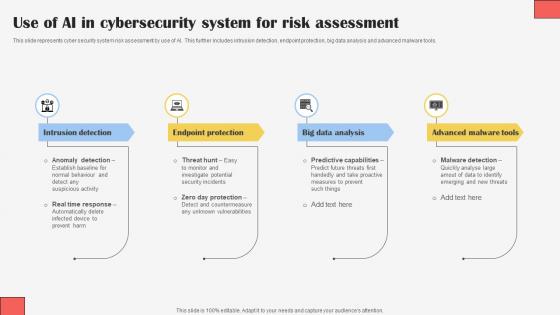 Use Of AI In Cybersecurity System For Risk Assessment
Use Of AI In Cybersecurity System For Risk AssessmentThis slide represents cyber security system risk assessment by use of AI. This further includes intrusion detection, endpoint protection, big data analysis and advanced malware tools. Presenting our set of slides with Use Of AI In Cybersecurity System For Risk Assessment. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Intrusion Detection, Endpoint Protection, Big Data Analysis.
-
 Change Management Agents Driving Case Study On Implementing Cybersecurity System CM SS
Change Management Agents Driving Case Study On Implementing Cybersecurity System CM SSThis slide defines the case study of an IT Information technology professional implementing a new company-wide cybersecurity system. It consists of details related to a case study that reflects the importance of change agents in an organization. Introducing Change Management Agents Driving Case Study On Implementing Cybersecurity System CM SS to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Preventing Cyberattacks, Risk Of Cyberattacks, Cybersecurity System, Adequately Trained, using this template. Grab it now to reap its full benefits.
-
 Icon For Ensuring Cybersecurity In Automatic Control System
Icon For Ensuring Cybersecurity In Automatic Control SystemIntroducing our premium set of slides with Icon For Ensuring Cybersecurity In Automatic Control System. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon Ensuring Cybersecurity, Automatic Control System. So download instantly and tailor it with your information.
-
 Blockchain And Cybersecurity Discovery Identifying Potential Vulnerabilities In System BCT SS V
Blockchain And Cybersecurity Discovery Identifying Potential Vulnerabilities In System BCT SS VThe following slide showcases key phases of penetration testing to identify potential flaws and malware. It includes elements of discovery phase such as architecture, compliance readiness, readiness analysis, etc. Introducing Blockchain And Cybersecurity Discovery Identifying Potential Vulnerabilities In System BCT SS V to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Architecture Of Blockchain, Compliance Readiness, Readiness Analysis using this template. Grab it now to reap its full benefits.
-
 AUP Cybersecurity Icon For Establishing System Performance
AUP Cybersecurity Icon For Establishing System PerformancePresenting our set of slides with AUP Cybersecurity Icon For Establishing System Performance This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on AUP Cybersecurity, Icon For Establishing, System Performance
-
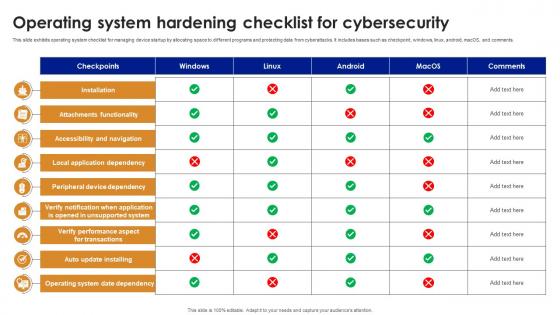 Operating System Hardening Checklist For Cybersecurity
Operating System Hardening Checklist For CybersecurityThis slide exhibits operating system checklist for managing device startup by allocating space to different programs and protecting data from cyberattacks. It includes bases such as checkpoint, windows, linux, android, macOS, and comments. Introducing our Operating System Hardening Checklist For Cybersecurity set of slides. The topics discussed in these slides are Attachments Functionality, Accessibility And Navigation, Local Application Dependency. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
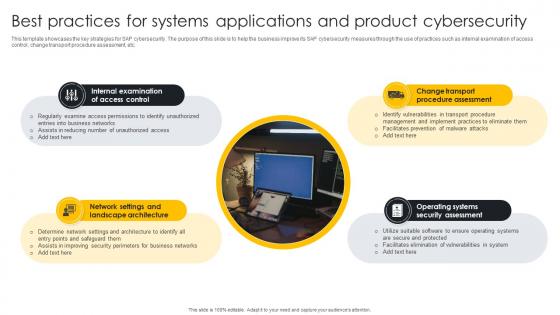 Best Practices For Systems Applications And Product Cybersecurity
Best Practices For Systems Applications And Product CybersecurityThis template showcases the key strategies for SAP cybersecurity. The purpose of this slide is to help the business improve its SAP cybersecurity measures through the use of practices such as internal examination of access control, change transport procedure assessment, etc. Introducing our premium set of slides with Best Practices For Systems Applications And Product Cybersecurity. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Internal Examination, Operating Systems Security Assessment, Change Transport Procedure Assessment. So download instantly and tailor it with your information.
-
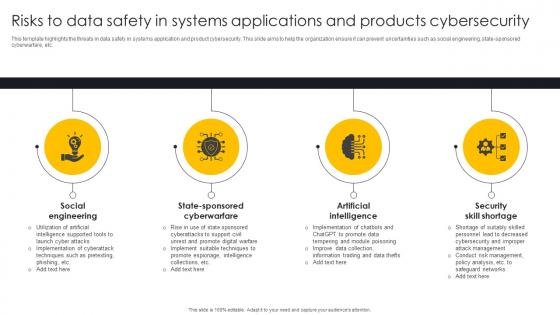 Risks To Data Safety In Systems Applications And Products Cybersecurity
Risks To Data Safety In Systems Applications And Products CybersecurityThis template highlights the threats in data safety in systems application and product cybersecurity. This slide aims to help the organization ensure it can prevent uncertainties such as social engineering, state sponsored cyberwarfare, etc. Presenting our set of slides with Risks To Data Safety In Systems Applications And Products Cybersecurity. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Social Engineering, State Sponsored Cyberwarfare, Artificial Intelligence.
-
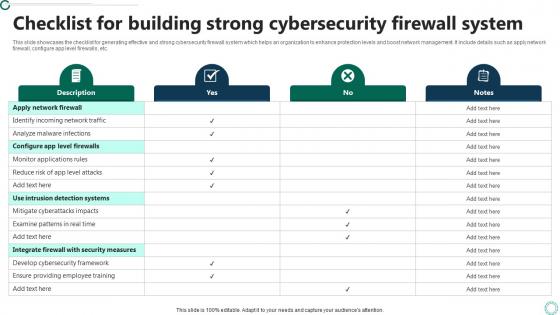 Checklist For Building Strong Cybersecurity Firewall System
Checklist For Building Strong Cybersecurity Firewall SystemThis slide showcases the checklist for generating effective and strong cybersecurity firewall system which helps an organization to enhance protection levels and boost network management. It include details such as apply network firewall, configure app level firewalls, etc. Introducing our Checklist For Building Strong Cybersecurity Firewall System set of slides. The topics discussed in these slides are Cybersecurity, Firewall System, Checklist. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
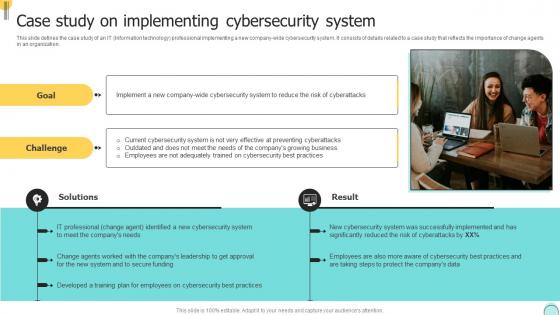 Q101 Changemakers Catalysts Organizational Case Study On Implementing Cybersecurity System CM SS V
Q101 Changemakers Catalysts Organizational Case Study On Implementing Cybersecurity System CM SS VThis slide defines the case study of an IT Information technology professional implementing a new company-wide cybersecurity system. It consists of details related to a case study that reflects the importance of change agents in an organization. Introducing Q101 Changemakers Catalysts Organizational Case Study On Implementing Cybersecurity System CM SS V to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Goal, Challenge, Solutions, using this template. Grab it now to reap its full benefits.
-
 Key Components Of Maritime Cybersecurity System
Key Components Of Maritime Cybersecurity SystemThis slide showcases major components of maritime. The main purpose of this template is to develop cargo management. This includes cybersecurity infrastructure, supply chain integration, environmental monitoring, etc. Presenting our set of slides with Key Components Of Maritime Cybersecurity System. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cybersecurity Infrastructure, Environmental Monitoring, Supply Chain Integration.
-
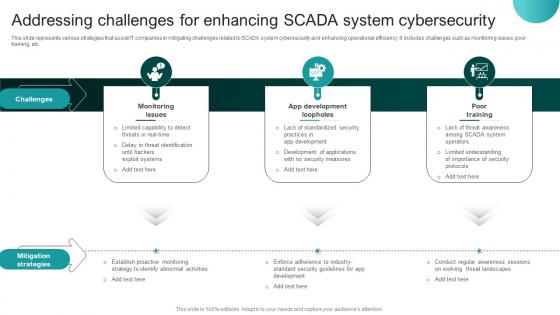 Addressing Challenges For Enhancing SCADA System Cybersecurity
Addressing Challenges For Enhancing SCADA System CybersecurityThis slide represents various strategies that assist IT companies in mitigating challenges related to SCADA system cybersecurity and enhancing operational efficiency. It includes challenges such as monitoring issues, poor training, etc. Presenting our set of slides with Addressing Challenges For Enhancing SCADA System Cybersecurity This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on This slide represents various strategies that assist IT companies in mitigating challenges related to SCADA system cybersecurity and enhancing operational efficiency. It includes challenges such as monitoring issues, poor training, etc.
-
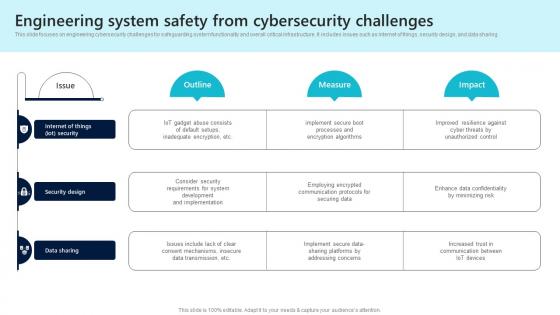 Engineering System Safety From Cybersecurity Challenges
Engineering System Safety From Cybersecurity ChallengesThis slide focuses on engineering cybersecurity challenges for safeguarding system functionality and overall critical infrastructure. It includes issues such as internet of things, security design, and data sharing. Presenting our well structured Engineering System Safety From Cybersecurity Challenges The topics discussed in this slide are Security Design, Data Sharing, Security This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
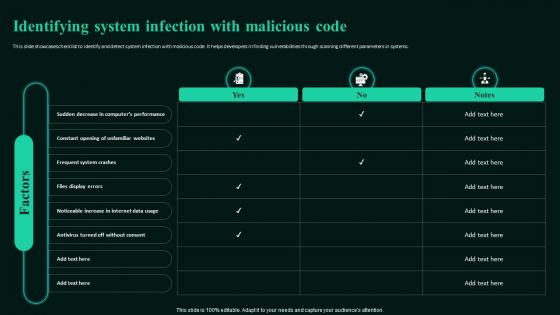 Identifying System Infection With Malicious Building Next Generation Endpoint Security Cybersecurity SS
Identifying System Infection With Malicious Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases checklist to identify and detect system infection with malicious code. It helps developers in finding vulnerabilities through scanning different parameters in systems.Deliver an outstanding presentation on the topic using this Identifying System Infection With Malicious Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Frequent System Crashes, Files Display Errors, Unfamiliar Websites using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Suspicious Activities And Prevent Threats, Protect Organizations Networks, Filter Out Malicious Activities, Security Devices Or Controls, using this template. Grab it now to reap its full benefits.
-
 Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing our well researched set of slides titled Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
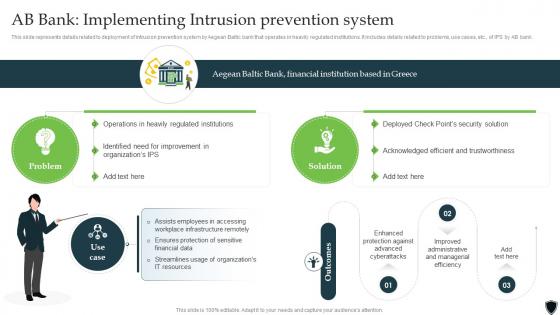 Implementing Intrusion Prevention Ab Bank Implementing Intrusion Prevention System Cybersecurity SS
Implementing Intrusion Prevention Ab Bank Implementing Intrusion Prevention System Cybersecurity SSThis slide represents details related to deployment of intrusion prevention system by Aegean Baltic bank that operates in heavily regulated institutions. It includes details related to problems, use cases, etc., of IPS by AB bank. Introducing Implementing Intrusion Prevention Ab Bank Implementing Intrusion Prevention System Cybersecurity SS to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Problem, Solution, Enhanced Protection Against Advanced Cyberattacks, using this template. Grab it now to reap its full benefits.
-
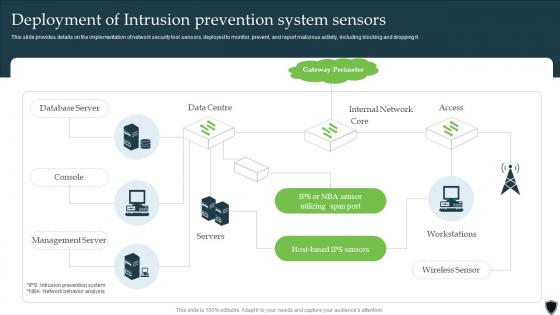 Implementing Intrusion Prevention Deployment Of Intrusion Prevention System Cybersecurity SS
Implementing Intrusion Prevention Deployment Of Intrusion Prevention System Cybersecurity SSThis slide provides details on the implementation of network security tool sensors, deployed to monitor, prevent, and report malicious activity, including blocking and dropping it. Introducing Implementing Intrusion Prevention Deployment Of Intrusion Prevention System Cybersecurity SS to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Database Server, Gateway Perimeter, Workstations, Management Server, using this template. Grab it now to reap its full benefits.
-
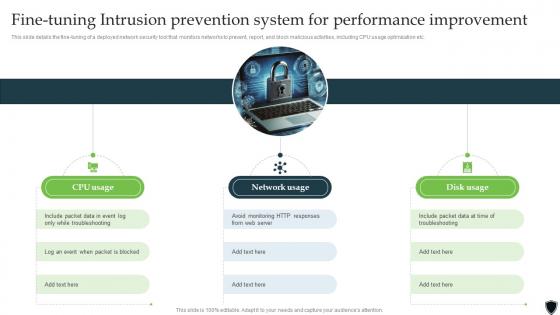 Implementing Intrusion Prevention Fine Tuning Intrusion Prevention System Cybersecurity SS
Implementing Intrusion Prevention Fine Tuning Intrusion Prevention System Cybersecurity SSThis slide details the fine-tuning of a deployed network security tool that monitors networks to prevent, report, and block malicious activities, including CPU usage optimization etc. Introducing Implementing Intrusion Prevention Fine Tuning Intrusion Prevention System Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on CPU Usage, Network Usage, Disk Usage, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Reasons To Invest In Intrusion Prevention System Cybersecurity SS
Implementing Intrusion Prevention Reasons To Invest In Intrusion Prevention System Cybersecurity SSThis slide presents reasons to invest in a network security tool that monitors the network to prevent malicious activities, protect against known and unknown threats, etc. Introducing Implementing Intrusion Prevention Reasons To Invest In Intrusion Prevention System Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Protection Against Known, Unknown Threats, Real-Time Detection, Blocking Of Malicious Traffic, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention System Intrusion Prevention System Training Plan Cybersecurity SS
Implementing Intrusion Prevention System Intrusion Prevention System Training Plan Cybersecurity SSThis slide details the training plan to facilitate the effective use of deployed IPS software by employees. It includes training topics such as traffic analysis, IPS signatures and analysis, web app attacks etc. Present the topic in a bit more detail with this Implementing Intrusion Prevention System Intrusion Prevention System Training Plan Cybersecurity SS. Use it as a tool for discussion and navigation on Training Method, Traffic Analysis, Anomaly Detection Systems, Web Application Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Budget Plan, Impact Assessment, Dashboards, Case Study Analysis, using this template. Grab it now to reap its full benefits.
-
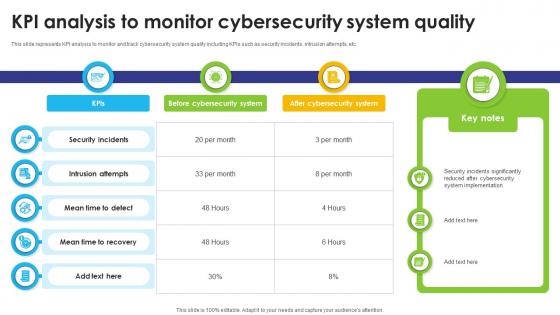 KPI Analysis To Monitor Cybersecurity System Quality
KPI Analysis To Monitor Cybersecurity System QualityThis slide represents KPI analysis to monitor and track cybersecurity system quality including KPIs such as security incidents, intrusion attempts, etc. Presenting our well structured KPI Analysis To Monitor Cybersecurity System Quality The topics discussed in this slide are Before Cybersecurity System, After Cybersecurity SystemThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cybersecurity monitoring plan steps in detail fine tune monitoring system
Cybersecurity monitoring plan steps in detail fine tune monitoring systemThis slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Fine Tune Monitoring System. Introducing Cybersecurity Monitoring Plan Steps In Detail Fine Tune Monitoring System to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cybersecurity Monitoring Plan, using this template. Grab it now to reap its full benefits.
-
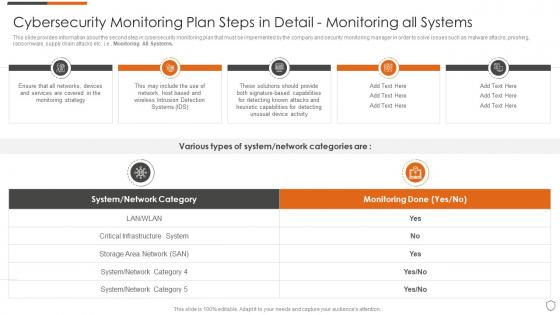 Cybersecurity monitoring plan steps in detail monitoring all systems
Cybersecurity monitoring plan steps in detail monitoring all systemsThis slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Monitoring All Systems. Increase audience engagement and knowledge by dispensing information using Cybersecurity Monitoring Plan Steps In Detail Monitoring All Systems. This template helps you present information on five stages. You can also present information on Critical Infrastructure System, Storage Area Network, System Network Category using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity Risk Management Framework Asset Criticality Of Identified System
Cybersecurity Risk Management Framework Asset Criticality Of Identified SystemFollowing slide demonstrates the asset criticality of identified system components. It covers details such as system name, component used, impact rating, criticality rating and failure cost. Present the topic in a bit more detail with this Cybersecurity Risk Management Framework Asset Criticality Of Identified System. Use it as a tool for discussion and navigation on Criticality Rating, Failure Cost, Moderate, High. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Risk Management Framework System Categorization Worksheet
Cybersecurity Risk Management Framework System Categorization WorksheetThis slide illustrates system categorization worksheet. It includes information about security system such as system name, its version, system location and other general information. Present the topic in a bit more detail with this Cybersecurity Risk Management Framework System Categorization Worksheet. Use it as a tool for discussion and navigation on Host Computer, System Location, System Accessibility, Asset Tag. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Risk Management Framework System Disposal Checklist
Cybersecurity Risk Management Framework System Disposal ChecklistMentioned slide shows system disposal checklist. It covers information such as system requirement, its compliance and remarks. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Management Framework System Disposal Checklist. Dispense information and present a thorough explanation of Stored Information, All Information, All Hardcopy Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity Risk Management Framework System Management Checklist
Cybersecurity Risk Management Framework System Management ChecklistFollowing slide displays system management checklist. It includes system management activities and frequency of performing them. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Management Framework System Management Checklist. Dispense information and present a thorough explanation of System Monitoring, Data Backup, Security Patches, Virus Scanning using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
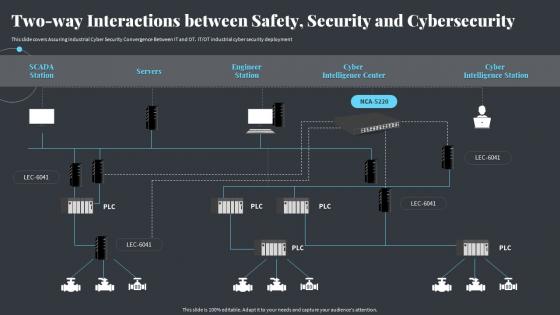 Two Way Interactions Between Safety Security And Cybersecurity Strategies Ot And It Modern Pi System
Two Way Interactions Between Safety Security And Cybersecurity Strategies Ot And It Modern Pi SystemThis slide covers Assuring Industrial Cyber Security Convergence Between IT and OT. IT or OT industrial cyber security deployment Deliver an outstanding presentation on the topic using this Two Way Interactions Between Safety Security And Cybersecurity Strategies Ot And It Modern Pi System. Dispense information and present a thorough explanation of Cybersecurity, Interactions, Intelligence Station using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
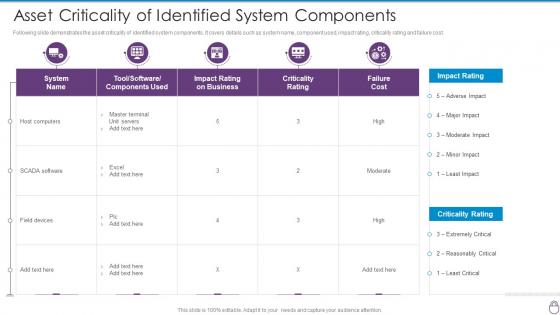
 Asset Criticality Of Identified System Components Cybersecurity Incident And Vulnerability
Asset Criticality Of Identified System Components Cybersecurity Incident And VulnerabilityMentioned slide demonstrates the asset criticality of identified system components. It includes information of system name, component used, impact rating, criticality rating and failure cost. Deliver an outstanding presentation on the topic using this Asset Criticality Of Identified System Components Cybersecurity Incident And Vulnerability. Dispense information and present a thorough explanation of Host Computers, SCADA Software, Field Devices using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Categorization Worksheet For System Components Cybersecurity Incident And Vulnerability
Categorization Worksheet For System Components Cybersecurity Incident And VulnerabilityThis slide illustrates categorization worksheet that can be used to categorize system components. It includes information about security system such as system name, its version, system location and other general information. Present the topic in a bit more detail with this Categorization Worksheet For System Components Cybersecurity Incident And Vulnerability. Use it as a tool for discussion and navigation on System Location, System Accessibility, IT Server Room. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
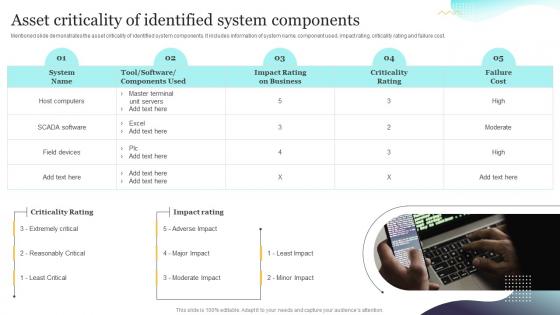 Asset Criticality Of Identified System Components Upgrading Cybersecurity With Incident Response Playbook
Asset Criticality Of Identified System Components Upgrading Cybersecurity With Incident Response PlaybookMentioned slide demonstrates the asset criticality of identified system components. It includes information of system name, component used, impact rating, criticality rating and failure cost. Present the topic in a bit more detail with this Asset Criticality Of Identified System Components Upgrading Cybersecurity With Incident Response Playbook. Use it as a tool for discussion and navigation on Criticality, Information, Demonstrates. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Categorization Worksheet For System Components Upgrading Cybersecurity With Incident Response Playbook
Categorization Worksheet For System Components Upgrading Cybersecurity With Incident Response PlaybookThis slide illustrates categorization worksheet that can be used to categorize system components. It includes information about security system such as system name, its version, system location and other general information. Present the topic in a bit more detail with this Categorization Worksheet For System Components Upgrading Cybersecurity With Incident Response Playbook. Use it as a tool for discussion and navigation on Categorization, Components, Worksheet. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
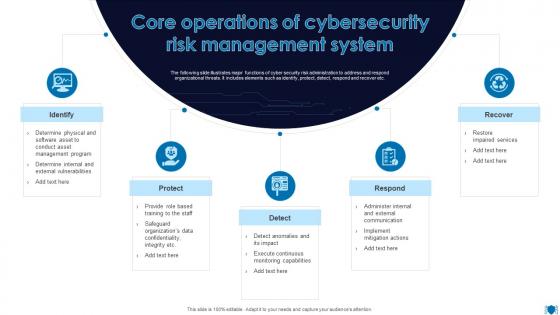 Core Operations Of Cybersecurity Risk Management System
Core Operations Of Cybersecurity Risk Management SystemThe following slide illustrates major functions of cyber security risk administration to address and respond organizational threats. It includes elements such as identify, protect, detect, respond and recover etc. Presenting our set of slides with Core Operations Of Cybersecurity Risk Management System. This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify, Protect, Respond.
-
 Cybersecurity And Data Protection System Icon
Cybersecurity And Data Protection System IconIntroducing our premium set of slides with Cybersecurity And Data Protection System Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cybersecurity, Data Protection, Framework Icon. So download instantly and tailor it with your information.
-
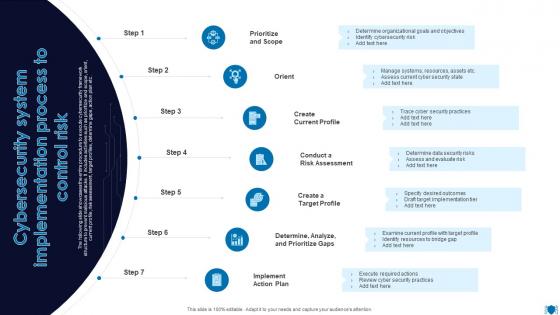 Cybersecurity System Implementation Process To Control Risk
Cybersecurity System Implementation Process To Control RiskThe following slide showcases the entire procedure to execute cybersecurity framework structure to prevent malicious attacks. It includes activities such as prioritize and scope, orient, current profile, risk assessment, target profiles, determine gaps, action plan etc. Presenting our set of slides with Cybersecurity System Implementation Process To Control Risk. This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Create Current Profile, Determine, Analyze, Prioritize Gaps.
-
 Cybersecurity System Implementation Timeline With Capability And Initiatives
Cybersecurity System Implementation Timeline With Capability And InitiativesThe following slide showcases the information security framework execution timeline to safeguard companys reputation and manage IT infrastructure. It includes elements such as capability, initiatives, deploying security cloud, assessing asset criticality, optimizing patching posture etc. Introducing our Cybersecurity System Implementation Timeline With Capability And Initiatives set of slides. The topics discussed in these slides are Identify, Protect, Detect. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cybersecurity Risk Assessment System Icon
Cybersecurity Risk Assessment System IconPresenting our set of slides with Cybersecurity Risk Assessment System Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cybersecurity, Risk Assessment, Framework Icon.
-
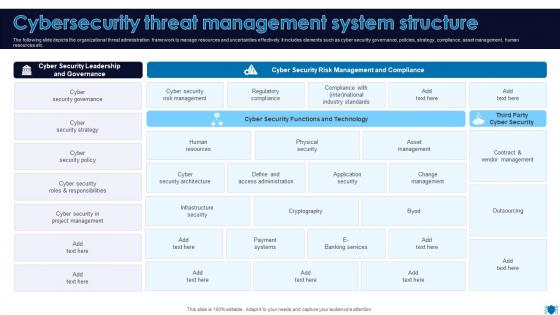 Cybersecurity Threat Management System Structure
Cybersecurity Threat Management System StructureThe following slide depicts the organizational threat administration framework to manage resources and uncertainties effectively. It includes elements such as cyber security governance, policies, strategy, compliance, asset management, human resources etc. Presenting our well structured Cybersecurity Threat Management System Structure. The topics discussed in this slide are Cyber Security Governance, Cyber Security Strategy, Cyber Security Policy. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Elements Of Cybersecurity Risk Administration System
Elements Of Cybersecurity Risk Administration SystemThe following slide showcases the components of cybersecurity framework to assess industry standards and manage risks. It includes elements namely, core, tiers and profile etc. Introducing our premium set of slides with Elements Of Elements Of Cybersecurity Risk Administration System. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Framework Core, Framework Tiers, Framework Profile. So download instantly and tailor it with your information.
-
 Executing Cybersecurity System With Target State
Executing Cybersecurity System With Target StateThe following slide showcases the process of implementing cybersecurity framework to prevent data breach. It includes elements such as current state, assessment, target state, roadmap along with continuous improvement etc. Presenting our set of slides with Executing Cybersecurity System With Target State. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Current State, Assessment, Target State.
-
 Impact Of Implementing Cybersecurity System Practices
Impact Of Implementing Cybersecurity System PracticesThe following slide highlights the various benefits of adopting cybersecurity framework to assess its success and ensure effective risk management. It includes key elements such as common language, collaboration, due diligence, compliance etc. Introducing our premium set of slides with Impact Of Implementing Cybersecurity System Practices. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Common Language, Collaboration, Due Diligence. So download instantly and tailor it with your information.
-
 Steps To Implement Cybersecurity Asset Management System
Steps To Implement Cybersecurity Asset Management SystemThe following slide illustrates some steps to execute cybersecurity framework for safety risk and performance management. It includes elements such as setting goals, drafting detailed profile, evaluating current position, assessing gaps, implementing plan etc. Presenting our set of slides with Steps To Implement Cybersecurity Asset Management System. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Evaluate Current Position, Execute Action Plan, Asses Gap.
-
 Cybersecurity Solution For IoT System Components
Cybersecurity Solution For IoT System ComponentsThe following slide illustrates a strategic proposed mechanism with the sequential process for IoT system components that ensures cybersecurity. The three major components are the IoT device, IoT gateway, and IoT server. Presenting our well structured Cybersecurity Solution For IoT System Components. The topics discussed in this slide are Format, Data, Transfer. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Hire business consultant cybersecurity business meeting planning system cpb
Hire business consultant cybersecurity business meeting planning system cpbPresenting this set of slides with name - Hire Business Consultant Cybersecurity Business Meeting Planning System Cpb. This is an editable three stages graphic that deals with topics like Hire Business Consultant, Cybersecurity, Business Meeting Planning System to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Cybersecurity incident response workflow system ppt powerpoint presentation infographics graphics tutorials cpb
Cybersecurity incident response workflow system ppt powerpoint presentation infographics graphics tutorials cpbPresenting this set of slides with name Cybersecurity Incident Response Workflow System Ppt Powerpoint Presentation Infographics Graphics Tutorials Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Cybersecurity Incident Response Workflow System to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Coder checking cybersecurity module to identify potential system risk
Coder checking cybersecurity module to identify potential system riskPresenting our set of slides with Coder Checking Cybersecurity Module To Identify Potential System Risk. This exhibits information on three stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Coder Checking Cybersecurity Module To Identify Potential System Risk.
-
 Cybersecurity monitoring system effective security monitoring plan ppt outline outfit
Cybersecurity monitoring system effective security monitoring plan ppt outline outfitThis slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Fine Tune Monitoring System. Introducing Cybersecurity Monitoring System Effective Security Monitoring Plan Ppt Outline Outfit to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Systems, Generate, Changes, Monitoring, using this template. Grab it now to reap its full benefits.



