Powerpoint Templates and Google slides for Cybersecurity Strategy
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Agenda Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SS
Agenda Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SSIntroducing Agenda Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Network Security Loopholes, Security Vulnerabilities, Vulnerabilities Mitigation Strategies, using this template. Grab it now to reap its full benefits.
-
 Best Practices For Deploying Patch Management Implementing Strategies For Mitigating Cybersecurity SS
Best Practices For Deploying Patch Management Implementing Strategies For Mitigating Cybersecurity SSThis slide provides best practices for integrating patch management. It includes automating patch management, setting clear expectations, and scheduling auto-deployments.Increase audience engagement and knowledge by dispensing information using Best Practices For Deploying Patch Management Implementing Strategies For Mitigating Cybersecurity SS. This template helps you present information on three stages. You can also present information on Set Clear Expectations, Automate Patch Management, Schedule Auto Deployments using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Comparative Analysis Of End To End Encryption Tools Implementing Strategies For Mitigating Cybersecurity SS
Comparative Analysis Of End To End Encryption Tools Implementing Strategies For Mitigating Cybersecurity SSThis slide compares the best end-to-end encryption software solutions based on different parameters such as password management, on-the-fly decryption, and enterprise-grade decryption.Deliver an outstanding presentation on the topic using this Comparative Analysis Of End To End Encryption Tools Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Offers Support, Password Management, Enterprise Grade Decryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cost Benefit Analysis For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SS
Cost Benefit Analysis For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SSThis slide shows the cost-benefit analysis of implementing network vulnerability management strategies, including the costs incurred in end-to-end encryption and phishing awareness training, etc.Deliver an outstanding presentation on the topic using this Cost Benefit Analysis For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Costs, Benefits, Description, Initial Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 First Line Of Defense Device Attestation Implementing Strategies For Mitigating Cybersecurity SS
First Line Of Defense Device Attestation Implementing Strategies For Mitigating Cybersecurity SSThis slide represents details related to first line of defense offered by implemented end to end encryption solution. It includes details related to process for device attestation.Introducing First Line Of Defense Device Attestation Implementing Strategies For Mitigating Cybersecurity SS to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Mobile Device Management, Certificate Authority, Automatic Certificate Management Environment, using this template. Grab it now to reap its full benefits.
-
 Icons Slide Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SS
Icons Slide Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SSPresenting our well crafted Icons Slide Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SS set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly.
-
 Implementing Strategies For Mitigating Network Vulnerabilities Table Of Contents Cybersecurity SS
Implementing Strategies For Mitigating Network Vulnerabilities Table Of Contents Cybersecurity SSIntroducing Implementing Strategies For Mitigating Network Vulnerabilities Table Of Contents Cybersecurity SS to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Objectives, Best Practices, Training Plan For Identification, using this template. Grab it now to reap its full benefits.
-
 Investment Plan For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SS
Investment Plan For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SSThis slide details the costs associated with deploying network vulnerability management solutions for an enterprise. It includes expenses for implementing E2E software, IT talent acquisition costs etc.Deliver an outstanding presentation on the topic using this Investment Plan For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Parameters, Forecasted Budget, Actual Costs, Variance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Factors For Selecting Robust Encryption Solution Implementing Strategies For Mitigating Cybersecurity SS
Key Factors For Selecting Robust Encryption Solution Implementing Strategies For Mitigating Cybersecurity SSThis slide presents essential considerations for choosing an E2EE solution, including asymmetric encryption, key verification, complex cryptography, and ephemeral messaging.Introducing Key Factors For Selecting Robust Encryption Solution Implementing Strategies For Mitigating Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Asymmetric Encryption, Key Verification, Complex Cryptography, Ephemeral Messaging, using this template. Grab it now to reap its full benefits.
-
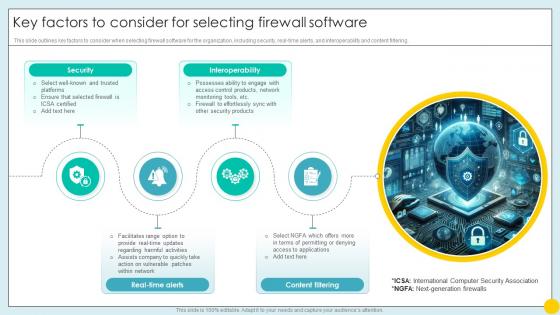 Key Factors To Consider For Selecting Firewall Software Implementing Strategies For Mitigating Cybersecurity SS
Key Factors To Consider For Selecting Firewall Software Implementing Strategies For Mitigating Cybersecurity SSThis slide outlines key factors to consider when selecting firewall software for the organization, including security, real-time alerts, and interoperability and content filtering.Increase audience engagement and knowledge by dispensing information using Key Factors To Consider For Selecting Firewall Software Implementing Strategies For Mitigating Cybersecurity SS. This template helps you present information on four stages. You can also present information on Security, Interoperability, Real Time Alerts, Content Filtering using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
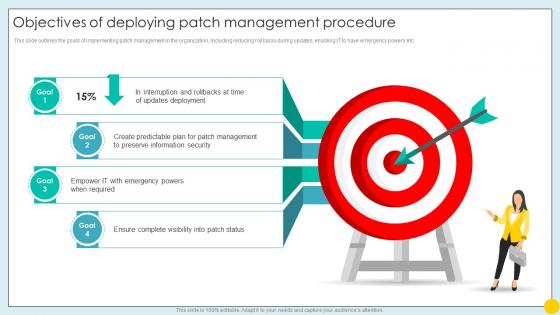 Objectives Of Deploying Patch Management Implementing Strategies For Mitigating Cybersecurity SS
Objectives Of Deploying Patch Management Implementing Strategies For Mitigating Cybersecurity SSThis slide outlines the goals of implementing patch management in the organization, including reducing rollbacks during updates, enabling IT to have emergency powers etc.Introducing Objectives Of Deploying Patch Management Implementing Strategies For Mitigating Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Updates Deployment, Preserve Information Security, Ensure Complete Visibility, using this template. Grab it now to reap its full benefits.
-
 Overview Strategies For Mitigating Network Vulnerabilities Cybersecurity SS
Overview Strategies For Mitigating Network Vulnerabilities Cybersecurity SSThis slide presents effective techniques for mitigating network vulnerabilities, including anti-phishing training, end-to-end encryption, patch management, strong password policies and authentication protocols.Introducing Overview Strategies For Mitigating Network Vulnerabilities Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Provide Anti Phishing Training, Authentication Protocols, Patch Management, using this template. Grab it now to reap its full benefits.
-
 Password Authentication To Mitigate Threats Posed By Implementing Strategies For Mitigating Cybersecurity SS
Password Authentication To Mitigate Threats Posed By Implementing Strategies For Mitigating Cybersecurity SSThis slide outlines strategies to implement password authentication and mitigate threats from large-scale breaches. It includes strategies such as password hashing and salting.Introducing Password Authentication To Mitigate Threats Posed By Implementing Strategies For Mitigating Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Problem, Consequence, Reasons, Password Authentication, using this template. Grab it now to reap its full benefits.
-
 Password Authentication To Mitigate Threats Posed Implementing Strategies For Mitigating Cybersecurity SS
Password Authentication To Mitigate Threats Posed Implementing Strategies For Mitigating Cybersecurity SSThis slide outlines strategies for IT teams to implement secure password authentication, including deploying multi-factor authentication systems, scanning all newly created passwords etc.Present the topic in a bit more detail with this Password Authentication To Mitigate Threats Posed Implementing Strategies For Mitigating Cybersecurity SS. Use it as a tool for discussion and navigation on Add Additional Layers, Compromised Credentials, Lower Case Letters, Symbols. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
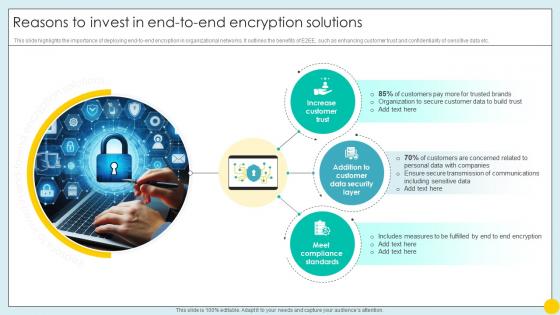 Reasons To Invest In End To End Encryption Solutions Implementing Strategies For Mitigating Cybersecurity SS
Reasons To Invest In End To End Encryption Solutions Implementing Strategies For Mitigating Cybersecurity SSThis slide highlights the importance of deploying end-to-end encryption in organizational networks. It outlines the benefits of E2EE, such as enhancing customer trust and confidentiality of sensitive data etc.Introducing Reasons To Invest In End To End Encryption Solutions Implementing Strategies For Mitigating Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Increase Customer Trust, Meet Compliance Standards, Customer Data Security Layer, using this template. Grab it now to reap its full benefits.
-
 Second Line Of Defense Certificate Authentication Implementing Strategies For Mitigating Cybersecurity SS
Second Line Of Defense Certificate Authentication Implementing Strategies For Mitigating Cybersecurity SSThis slide represents details related to second line of defense offered by implemented end to end encryption solution. It includes details related to process for certificate authentication.Increase audience engagement and knowledge by dispensing information using Second Line Of Defense Certificate Authentication Implementing Strategies For Mitigating Cybersecurity SS. This template helps you present information on five stages. You can also present information on Certificate Authority, Client, Server using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Statistics Highlighting Importance Of Patch Implementing Strategies For Mitigating Cybersecurity SS
Statistics Highlighting Importance Of Patch Implementing Strategies For Mitigating Cybersecurity SSThis slide presents statistical data highlighting the importance of patch management in organizational operations. It includes statistics related to breach detection time, prevention of cyber attacks, etc.Introducing Statistics Highlighting Importance Of Patch Implementing Strategies For Mitigating Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Organizations Possess, Documented Process, Patch Management, using this template. Grab it now to reap its full benefits.
-
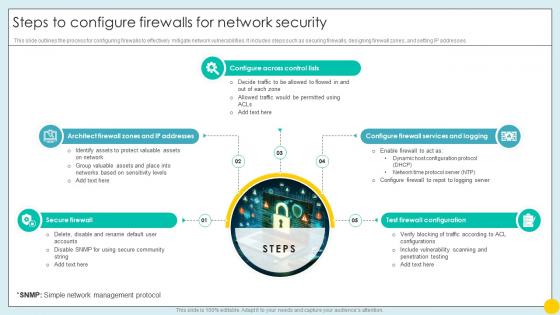 Steps To Configure Firewalls For Network Security Implementing Strategies For Mitigating Cybersecurity SS
Steps To Configure Firewalls For Network Security Implementing Strategies For Mitigating Cybersecurity SSThis slide outlines the process for configuring firewalls to effectively mitigate network vulnerabilities. It includes steps such as securing firewalls, designing firewall zones, and setting IP addresses.Increase audience engagement and knowledge by dispensing information using Steps To Configure Firewalls For Network Security Implementing Strategies For Mitigating Cybersecurity SS. This template helps you present information on five stages. You can also present information on Secure Firewall, Configure Across Control Lists, Test Firewall Configuration using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
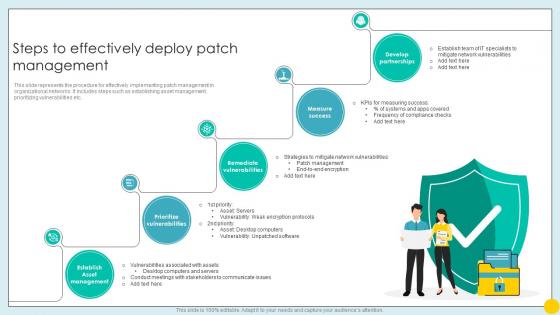 Steps To Effectively Deploy Patch Management Implementing Strategies For Mitigating Cybersecurity SS
Steps To Effectively Deploy Patch Management Implementing Strategies For Mitigating Cybersecurity SSThis slide represents the procedure for effectively implementing patch management in organizational networks. It includes steps such as establishing asset management, prioritizing vulnerabilities etc.Introducing Steps To Effectively Deploy Patch Management Implementing Strategies For Mitigating Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Prioritize Vulnerabilities, Remediate Vulnerabilities, Measure Success, Develop Partnerships, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SS
Table Of Contents Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SSIncrease audience engagement and knowledge by dispensing information using Table Of Contents Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SS. This template helps you present information on eight stages. You can also present information on Gap Analysis, Patch Management, Dashboard Tracking, Additional Slides using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Training Plan For Detecting Phishing Attacks Implementing Strategies For Mitigating Cybersecurity SS
Training Plan For Detecting Phishing Attacks Implementing Strategies For Mitigating Cybersecurity SSThis slide provides details about the training plan designed to help employees detect phishing attacks. It covers training topics such as identifying general signs of phishing attacks, signs of phishing in email etc.Present the topic in a bit more detail with this Training Plan For Detecting Phishing Attacks Implementing Strategies For Mitigating Cybersecurity SS. Use it as a tool for discussion and navigation on Training Sessions, Timeline, Trainer, Training Topic. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Training Plan For Identifying Different Types Of Implementing Strategies For Mitigating Cybersecurity SS
Training Plan For Identifying Different Types Of Implementing Strategies For Mitigating Cybersecurity SSThis slide outlines a comprehensive training plan to help employees effectively identify various types of phishing attacks, including deceptive phishing, spear phishing, whaling, vishing and smishing.Deliver an outstanding presentation on the topic using this Training Plan For Identifying Different Types Of Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Training Topics, Training Sessions, Training Hours, Trainer using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Training Plan For Preventing Phishing Attacks Implementing Strategies For Mitigating Cybersecurity SS
Training Plan For Preventing Phishing Attacks Implementing Strategies For Mitigating Cybersecurity SSThis slide outlines a training plan to help employees effectively prevent phishing attacks. It covers topics such as email communication, blocking popups and ads, report phishing attempts etc.Deliver an outstanding presentation on the topic using this Training Plan For Preventing Phishing Attacks Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Training Topics, Training Method, Expected Completion Date, Trainer using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
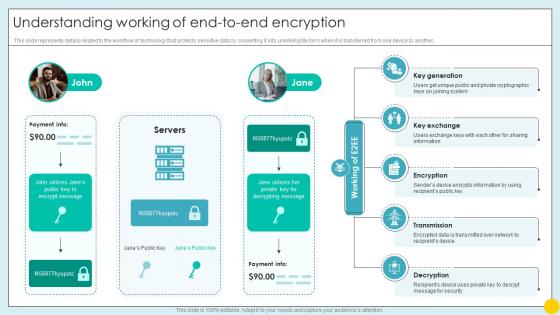 Understanding Working Of End To End Encryption Implementing Strategies For Mitigating Cybersecurity SS
Understanding Working Of End To End Encryption Implementing Strategies For Mitigating Cybersecurity SSThis slide represents details related to the workflow of technology that protects sensitive data by converting it into unintelligible form when it is transferred from one device to another. Increase audience engagement and knowledge by dispensing information using Understanding Working Of End To End Encryption Implementing Strategies For Mitigating Cybersecurity SS. This template helps you present information on five stages. You can also present information on Key Exchange, Encryption, Transmission, Decryption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cost estimation for strategy minimize cybersecurity threats in healthcare company
Cost estimation for strategy minimize cybersecurity threats in healthcare companyThe slide shows the estimation of major cost involved in the next four years 2021 to 2025 for implementing the strategies. The strategies are implementing Data Encryption, Increase Employee Awareness, Restricting Access to Physical Devices etc. Present the topic in a bit more detail with this Cost Estimation For Strategy Minimize Cybersecurity Threats In Healthcare Company. Use it as a tool for discussion and navigation on Data Encryption, Market Research, Software Installation, Employee Awareness. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risks involved and mitigation strategies minimize cybersecurity threats in healthcare company
Risks involved and mitigation strategies minimize cybersecurity threats in healthcare companyThe slide shows the risks associated with the implementation of strategy. Also, it provides the level of the risk low, medium or high, Potential Risk Impact on the Company and Key Strategies Measures for mitigating the risk. Present the topic in a bit more detail with this Risks Involved And Mitigation Strategies Minimize Cybersecurity Threats In Healthcare Company. Use it as a tool for discussion and navigation on Intellectual Property Risk, Malware Infection Risk, Customer Churn Risk. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategy to be adopted 3 restrict access to minimize cybersecurity threats in healthcare company
Strategy to be adopted 3 restrict access to minimize cybersecurity threats in healthcare companyThis slide shows the strategy to be adopted by the company i.e. restricting the access of Physical devices to authorized personnel only in order to avoid data misuse data leakage, security breach etc. along with the need of such strategy and how it is to be implemented that will give benefit to the company. Introducing Strategy To Be Adopted 3 Restrict Access To Minimize Cybersecurity Threats In Healthcare Company to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Data Security, Hardware, Mobile Device Management, Security Policies, using this template. Grab it now to reap its full benefits.
-
 Strategy 3 Establish Cybersecurity Digital Transformation In A Banking Financial Services Company
Strategy 3 Establish Cybersecurity Digital Transformation In A Banking Financial Services CompanyThe slide explains the establish cybersecurity strategy of the company. It provides key points such as what to do in the strategy, major reason behind the strategy and key steps required for the strategy Present the topic in a bit more detail with this Strategy 3 Establish Cybersecurity Digital Transformation In A Banking Financial Services Company. Use it as a tool for discussion and navigation on Strategy, Cybersecurity, Development. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Digital Transformation In A Banking Financial Services Company Strategy 3 Establish Cybersecurity
Digital Transformation In A Banking Financial Services Company Strategy 3 Establish CybersecurityThe slide explains the establish cybersecurity strategy of the company. It provides key points such as what to do in the strategy, major reason behind the strategy and key steps required for the strategy Present the topic in a bit more detail with this Digital Transformation In A Banking Financial Services Company Strategy 3 Establish Cybersecurity. Use it as a tool for discussion and navigation on Strategy, Cybersecurity, Development. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 It Professional Upskilling For Cybersecurity It Strategy For Digitalization In Business
It Professional Upskilling For Cybersecurity It Strategy For Digitalization In BusinessThis slide displays the upskilling for cybersecurity which covers chief information security officer, cloud security architect, etc. Present the topic in a bit more detail with this It Professional Upskilling For Cybersecurity It Strategy For Digitalization In Business. Use it as a tool for discussion and navigation on Information, Management, Architect. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategy 3 Establish Cybersecurity In The Banking Digitalization In Retail Banking Company
Strategy 3 Establish Cybersecurity In The Banking Digitalization In Retail Banking CompanyThe slide explains the establish cybersecurity strategy of the company. It provides key points such as what to do in the strategy, major reason behind the strategy and key steps required for the strategy.Increase audience engagement and knowledge by dispensing information using Strategy 3 Establish Cybersecurity In The Banking Digitalization In Retail Banking Company This template helps you present information on three stages. You can also present information on Safeguard Customers, Protect Customer Assets, Establish An Integrated using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Implementation Latest Technologies Strategy 3 Establish Cybersecurity In The Banking
Implementation Latest Technologies Strategy 3 Establish Cybersecurity In The BankingThe slide explains the establish cybersecurity strategy of the company. It provides key points such as what to do in the strategy, major reason behind the strategy and key steps required for the strategy. Introducing Implementation Latest Technologies Strategy 3 Establish Cybersecurity In The Banking to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Driven Protection, Technology, Measures, Customers, Research And Development, using this template. Grab it now to reap its full benefits.
-
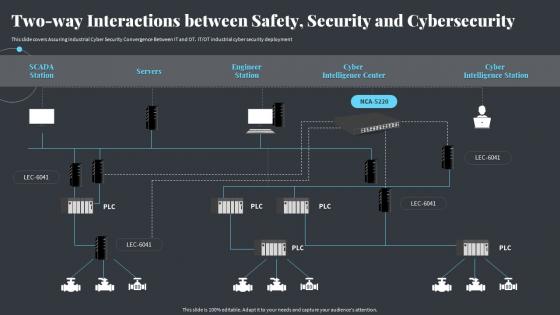
 It Ot Convergence Strategy Two Way Interactions Between Safety Security And Cybersecurity
It Ot Convergence Strategy Two Way Interactions Between Safety Security And CybersecurityThis slide covers Assuring Industrial Cyber Security Convergence Between IT and OT. IT or OT industrial cyber security deployment Present the topic in a bit more detail with this It Ot Convergence Strategy Two Way Interactions Between Safety Security And Cybersecurity. Use it as a tool for discussion and navigation on Interactions, Security, Cybersecurity This template is free to edit as deemed fit for your organization. Therefore download it now.
-
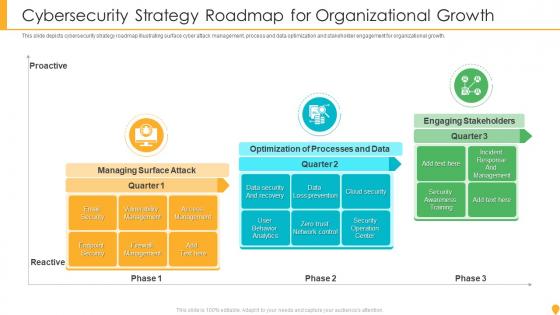 Cybersecurity Strategy Roadmap For Organizational Growth
Cybersecurity Strategy Roadmap For Organizational GrowthThis slide depicts cybersecurity strategy roadmap illustrating surface cyber attack management, process and data optimization and stakeholder engagement for organizational growth. Presenting our set of slides with name Cybersecurity Strategy Roadmap For Organizational Growth. This exhibits information on three stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Managing Surface Attack, Optimization Processes Data, Engaging Stakeholders.
-
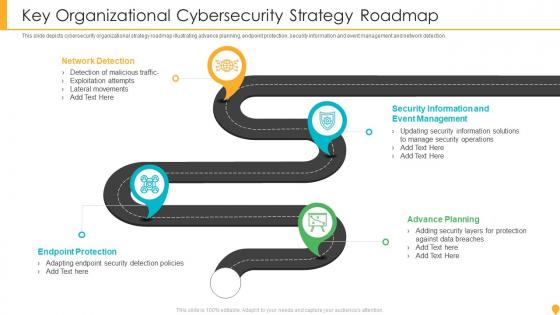 Key Organizational Cybersecurity Strategy Roadmap
Key Organizational Cybersecurity Strategy RoadmapThis slide depicts cybersecurity organizational strategy roadmap illustrating advance planning, endpoint protection, security information and event management and network detection. Presenting our set of slides with name Key Organizational Cybersecurity Strategy Roadmap. This exhibits information on four stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Detection, Endpoint Protection, Advance Planning, Security Information.
-
 Cybersecurity Risk Assessment And Strategic Mitigation Plan
Cybersecurity Risk Assessment And Strategic Mitigation PlanThis slide represents the identified cyber security risks to help the organizations in identifying and prioritizing areas to improve cybersecurity program. It includes details related to cyber security threats, risks, risk priority, mitigation plan, risk owner and risk deduction timeline. Presenting our well structured Cybersecurity Risk Assessment And Strategic Mitigation Plan. The topics discussed in this slide are Risk, Risk Priority, Risk Mitigation Plan . This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Two Way Interactions Between Safety Security And Cybersecurity Strategies Ot And It Modern Pi System
Two Way Interactions Between Safety Security And Cybersecurity Strategies Ot And It Modern Pi SystemThis slide covers Assuring Industrial Cyber Security Convergence Between IT and OT. IT or OT industrial cyber security deployment Deliver an outstanding presentation on the topic using this Two Way Interactions Between Safety Security And Cybersecurity Strategies Ot And It Modern Pi System. Dispense information and present a thorough explanation of Cybersecurity, Interactions, Intelligence Station using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Reduction Strategies Stakeholders Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company
Risk Reduction Strategies Stakeholders Approaches To Overcome Cybersecurity Risk Faced By Real Estate CompanyThe following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti-phishing add-ons, using a customized web application firewall etc. Deliver an outstanding presentation on the topic using this Risk Reduction Strategies Stakeholders Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company. Dispense information and present a thorough explanation of Approaches, Cybersecurity, Ransomware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 F857 Mitigation Strategies To Avoid Information Breach Cybersecurity Risk Analysis And Management Plan
F857 Mitigation Strategies To Avoid Information Breach Cybersecurity Risk Analysis And Management PlanThis slide showcases strategies that can help organization to avoid information breach. Key strategies include implement antivirus software, monitor network traffic, incident response plan, patch management schedule and establish network access controls Increase audience engagement and knowledge by dispensing information using F857 Mitigation Strategies To Avoid Information Breach Cybersecurity Risk Analysis And Management Plan. This template helps you present information on five stages. You can also present information on Mitigation, Strategies, Information Breach using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Mitigation Strategies To Tackle Information Security Cybersecurity Risk Analysis And Management Plan
Mitigation Strategies To Tackle Information Security Cybersecurity Risk Analysis And Management PlanThis slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help organization to minimize the financial loss and main reputation of business Introducing Mitigation Strategies To Tackle Information Security Cybersecurity Risk Analysis And Management Plan to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Mitigation, Strategies, Information, using this template. Grab it now to reap its full benefits.
-
 Mitigation Strategies To Avoid Information Breach Formulating Cybersecurity Plan
Mitigation Strategies To Avoid Information Breach Formulating Cybersecurity PlanThis slide showcases startegies that can help organization to avoid information breach. Key strategies include impelment antivirus software, monitor network traffic, incident reponse plan, patch management schedule and establish network access controls. Introducing Mitigation Strategies To Avoid Information Breach Formulating Cybersecurity Plan to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Implement Antivirus, Monitor Network Traffic, Incident Response Plan, using this template. Grab it now to reap its full benefits.
-
 Mitigation Strategies To Tackle Information Security Threats Formulating Cybersecurity Plan
Mitigation Strategies To Tackle Information Security Threats Formulating Cybersecurity PlanThis slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help organization to minimize the financial loss and maintain reputation of business. Increase audience engagement and knowledge by dispensing information using Mitigation Strategies To Tackle Information Security Threats Formulating Cybersecurity Plan. This template helps you present information on five stages. You can also present information on Malware, Phishing, Mitigation Strategies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity Defense Strategy In Powerpoint And Google Slides Cpb
Cybersecurity Defense Strategy In Powerpoint And Google Slides CpbPresenting our Cybersecurity Defense Strategy In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Cybersecurity Defense Strategy. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cultural Shift Toward A Technology Strategy 3 Establish Cybersecurity In The Banking Company
Cultural Shift Toward A Technology Strategy 3 Establish Cybersecurity In The Banking CompanyThe slide explains the establish cybersecurity strategy of the company. It provides key points such as what to do in the strategy, major reason behind the strategy and key steps required for the strategy. Increase audience engagement and knowledge by dispensing information using Cultural Shift Toward A Technology Strategy 3 Establish Cybersecurity In The Banking Company. This template helps you present information on three stages. You can also present information on Safeguard Vulnerable Customers, Protect Customer Assets, Research And Development, Cybersecurity Tools using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategy To Minimize Cyber Attacks Framework For Cybersecurity Risk Management
Strategy To Minimize Cyber Attacks Framework For Cybersecurity Risk ManagementThis slide indicates the framework for cybersecurity risk management. The major sub components of model are data sources, cyber intelligence and monitoring, threat and vulnerabilities, executive board and IT governance. Present the topic in a bit more detail with this Strategy To Minimize Cyber Attacks Framework For Cybersecurity Risk Management. Use it as a tool for discussion and navigation on Information Sharing, Components Of Framework, Framework For Cybersecurity, Risk Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategy To Minimize Cyber Attacks Multistep Approach To Conduct Cybersecurity Risk Assessment
Strategy To Minimize Cyber Attacks Multistep Approach To Conduct Cybersecurity Risk AssessmentThis slide indicates the multistep approach to conduct cybersecurity risk assessment in business organization. The major steps of process are risk identification, quantification, evaluation, mitigation and monitoring. Introducing Strategy To Minimize Cyber Attacks Multistep Approach To Conduct Cybersecurity Risk Assessment to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Risk Identification, Risk Mapping, Risk Evaluation, Risk Mitigation And Monitoring, using this template. Grab it now to reap its full benefits.
-
 Strategy To Minimize Cyber Attacks Need Of Cybersecurity Program For Organization
Strategy To Minimize Cyber Attacks Need Of Cybersecurity Program For OrganizationThis slide depicts the value that a cybersecurity program with risk assessment module add to organization in terms of increased awareness of organization security landscape, identification of system vulnerabilities, actionable and prioritized list of cybersecurity risks and mitigation plan to tackle future threats. Increase audience engagement and knowledge by dispensing information using Strategy To Minimize Cyber Attacks Need Of Cybersecurity Program For Organization. This template helps you present information on four stages. You can also present information on Organization Security Landscape, Actionable And Prioritized, List Of Cybersecurity Risks, Identification Of System Vulnerabilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategy To Minimize Cyber Attacks NIST Cybersecurity Framework With Subcategories
Strategy To Minimize Cyber Attacks NIST Cybersecurity Framework With SubcategoriesThis slide represents the NIST cybersecurity framework with subcategories. It also contains information regarding the software which fulfill multiple compliance requirements of NIST cybersecurity framework. Introducing Strategy To Minimize Cyber Attacks NIST Cybersecurity Framework With Subcategories to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on NIST Cybersecurity, Framework With Subcategories, Contains Information, Compliance Requirements, using this template. Grab it now to reap its full benefits.
-
 Strategic Risk Assessment Framework For Cybersecurity Management
Strategic Risk Assessment Framework For Cybersecurity ManagementThis slide showcases flow diagram to plan efficient management of cybersecurity risks for the organization for threat reduction. It includes steps such as understanding company strategies, data gathering, preliminary risk profiling, action plan, etc. Presenting our set of slides with name Strategic Risk Assessment Framework For Cybersecurity Management. This exhibits information on seven stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Strategic, Assessment, Framework.
-
 Best Practices For Cybersecurity Incident Management Incident Response Strategies Deployment
Best Practices For Cybersecurity Incident Management Incident Response Strategies DeploymentThis slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as create cyber incident management plan etc. Increase audience engagement and knowledge by dispensing information using Best Practices For Cybersecurity Incident Management Incident Response Strategies Deployment. This template helps you present information on five stages. You can also present information on Cybersecurity, Incident, Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Five Phases Of Cybersecurity Incident Management Incident Response Strategies Deployment
Five Phases Of Cybersecurity Incident Management Incident Response Strategies DeploymentThis slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Increase audience engagement and knowledge by dispensing information using Five Phases Of Cybersecurity Incident Management Incident Response Strategies Deployment. This template helps you present information on five stages. You can also present information on Plan, Respond, Report using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Impact Of Cybersecurity Incidents On Organization Incident Response Strategies Deployment
Impact Of Cybersecurity Incidents On Organization Incident Response Strategies DeploymentThis slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Increase audience engagement and knowledge by dispensing information using Impact Of Cybersecurity Incidents On Organization Incident Response Strategies Deployment. This template helps you present information on six stages. You can also present information on Operational, Reputational, Revenue using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Incident Response Strategies Deployment Gap Analysis Representing Current Situation Of Cybersecurity
Incident Response Strategies Deployment Gap Analysis Representing Current Situation Of CybersecurityThis slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. Introducing Incident Response Strategies Deployment Gap Analysis Representing Current Situation Of Cybersecurity to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Current, Desired, Gap, using this template. Grab it now to reap its full benefits.
-
 Marketing Initiatives For Tech Segments Cybersecurity Develop Business Aligned IT Strategy
Marketing Initiatives For Tech Segments Cybersecurity Develop Business Aligned IT StrategyThis slide provides information regarding marketing initiatives for a technology firm across the cybersecurity segment. The slide includes goal and marketing initiatives such as prepare brand identity, etc. Increase audience engagement and knowledge by dispensing information using Marketing Initiatives For Tech Segments Cybersecurity Develop Business Aligned IT Strategy. This template helps you present information on three stages. You can also present information on Marketing Initiatives, Prepare Brand Identity, Formulate Thought Leadership using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Approaches To Overcome Cybersecurity Risk Faced Effective Risk Management Strategies
Approaches To Overcome Cybersecurity Risk Faced Effective Risk Management StrategiesThe following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti-phishing add ons, using a customized web application firewall etc. Present the topic in a bit more detail with this Approaches To Overcome Cybersecurity Risk Faced Effective Risk Management Strategies. Use it as a tool for discussion and navigation on Ransomware, Phishing, Business Email Compromise. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategic Management Plan For Cybersecurity Risk
Strategic Management Plan For Cybersecurity RiskThis slide deals with the formation of cyber security risk management program to identify, eliminate and minimize cyber threat. The steps involved are business alignment, defining program, program development, metrics, monitoring Presenting our set of slides with Strategic Management Plan For Cybersecurity Risk. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Business, Program, Development.
-
 Effective Cybersecurity Strategic Plan For Crisis Communication
Effective Cybersecurity Strategic Plan For Crisis CommunicationThis slide presents cybersecurity plan helpful in seamless communication during crisis within an organization and to deliver accurate and comprehensive messages to stakeholders. It includes plan for phishing attack, spy attack and denial of service. Introducing our Effective Cybersecurity Strategic Plan For Crisis Communication set of slides. The topics discussed in these slides are Phising Attack, Risk, Communication, Channel This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cybersecurity Risk Assessment Program Strategic Plan To Mitigate Cyber Attacks
Cybersecurity Risk Assessment Program Strategic Plan To Mitigate Cyber AttacksThe slide indicates the risk mitigation plan for the multiple cyber attacks. It also includes details of cost involved and implementation time required for each mitigation approach. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Assessment Program Strategic Plan To Mitigate Cyber Attacks. Dispense information and present a thorough explanation of Strategic Plan, Mitigate Cyber Attacks, Malware Attack, Recommended Mitigation Strategy using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Effective Cybersecurity Risk Mitigation Strategies
Effective Cybersecurity Risk Mitigation StrategiesThe following slide illustrates key risk mitigation strategies for cybersecurity to limit impact of potential threats. This covers five strategies risk assessment, data encryption, firewalls, employee training and incident response plan.Presenting our set of slides with Effective Cybersecurity Risk Mitigation Strategies. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Conduct Risk Assessment, Encryption Software, Incident Response.
-
 Marketing Initiatives Different Segments Cybersecurity Cios Guide For It Strategy Strategy SS V
Marketing Initiatives Different Segments Cybersecurity Cios Guide For It Strategy Strategy SS VThis slide provides information regarding marketing initiatives for a technology firm across the cybersecurity segment. The slide includes goal and marketing initiatives such as prepare brand identity, etc. Deliver an outstanding presentation on the topic using this Marketing Initiatives Different Segments Cybersecurity Cios Guide For It Strategy Strategy SS V. Dispense information and present a thorough explanation of Prepare Brand Identity, Formulate Thought Leadership, Investment In Paid Media using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





