Powerpoint Templates and Google slides for Cybersecurity Strategy
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity CD
Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity CDStep up your game with our enchanting Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity CD deck, guaranteed to leave a lasting impression on your audience. Crafted with a perfect balance of simplicity, and innovation, our deck empowers you to alter it to your specific needs. You can also change the color theme of the slide to mold it to your companys specific needs. Save time with our ready-made design, compatible with Microsoft versions and Google Slides. Additionally, it is available for download in various formats including JPG, JPEG, and PNG. Outshine your competitors with our fully editable and customized deck.
-
 Backup Strategy In Cybersecurity Training Ppt
Backup Strategy In Cybersecurity Training PptPresenting Backup Strategy in Cybersecurity. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Network Vulnerabilities Logged Off In Previous Years Implementing Strategies For Mitigating Cybersecurity SS
Network Vulnerabilities Logged Off In Previous Years Implementing Strategies For Mitigating Cybersecurity SSThis slide represents network vulnerabilities faced by the organization, which led to the theft of confidential and sensitive information due to opening of infected email attachments etc.Deliver an outstanding presentation on the topic using this Network Vulnerabilities Logged Off In Previous Years Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Phishing Attacks, Malware Attacks, Reasons, Key Insights using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
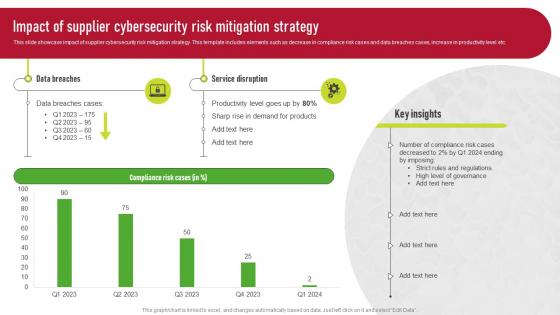 Impact Of Supplier Cybersecurity Risk Mitigation Strategy Supplier Risk Management
Impact Of Supplier Cybersecurity Risk Mitigation Strategy Supplier Risk ManagementThis slide showcase impact of supplier cybersecurity risk mitigation strategy. This template includes elements such as decrease in compliance risk cases and data breaches cases, increase in productivity level etc. Present the topic in a bit more detail with this Impact Of Supplier Cybersecurity Risk Mitigation Strategy Supplier Risk Management. Use it as a tool for discussion and navigation on Data Breaches, Service Disruption, Risk Mitigation Strategy. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IoT Password Attack Prevention Strategies Improving IoT Device Cybersecurity IoT SS
IoT Password Attack Prevention Strategies Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to highlight Internet of Things IoT password attack prevention measures. The techniques outlined in slide are limit public information, verifying the source, and no sharing of password. Deliver an outstanding presentation on the topic using this IoT Password Attack Prevention Strategies Improving IoT Device Cybersecurity IoT SS. Dispense information and present a thorough explanation of Information, Verify, Password using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategies To Improve IoT Security Improving IoT Device Cybersecurity IoT SS
Strategies To Improve IoT Security Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to highlight various techniques through which companies can increase Internet of Things IoT cyber security awareness level. The strategies mentioned in slide are getting top level management involved, building robust security awareness plan, etc. Present the topic in a bit more detail with this Strategies To Improve IoT Security Improving IoT Device Cybersecurity IoT SS. Use it as a tool for discussion and navigation on Management, Develop, Guidelines. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Analysis Of IoT Security Strategies Internet Of Things IoT Security Cybersecurity SS
Impact Analysis Of IoT Security Strategies Internet Of Things IoT Security Cybersecurity SSThis slide showcases impact analysis for deployed internet of things IoT security tools and strategies. It provides details about IoT ransomware, user privacy, insecure interfaces, remote work attacks, etc. Present the topic in a bit more detail with this Impact Analysis Of IoT Security Strategies Internet Of Things IoT Security Cybersecurity SS. Use it as a tool for discussion and navigation on Internet Of Things, Security Tools And Strategies, IoT Ransomware, Remote Work Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Impact Analysis Of Comprehensive Encryption Strategies Cybersecurity SS
Encryption For Data Impact Analysis Of Comprehensive Encryption Strategies Cybersecurity SSThis slide showcases post implementation analysis of encryption strategies. Its purpose is to make businesses aware of major and potential improvements. It provides information about vulnerabilities, costs, responsiveness, etc. Present the topic in a bit more detail with this Encryption For Data Impact Analysis Of Comprehensive Encryption Strategies Cybersecurity SS. Use it as a tool for discussion and navigation on Costs, Responsiveness Speed, Vulnerabilities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Network Vulnerabilities Assessment KPI Dashboard Implementing Strategies For Mitigating Cybersecurity SS
Network Vulnerabilities Assessment KPI Dashboard Implementing Strategies For Mitigating Cybersecurity SSThis dashboard tracks and assesses the network vulnerabilities faced by the organization. It includes KPIs such as critical vulnerabilities, new vulnerabilities, and unresolved vulnerabilities etc.Present the topic in a bit more detail with this Network Vulnerabilities Assessment KPI Dashboard Implementing Strategies For Mitigating Cybersecurity SS. Use it as a tool for discussion and navigation on New Vulnerabilities, Unresolved Vulnerabilities, Activity, Insecure Libraries. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
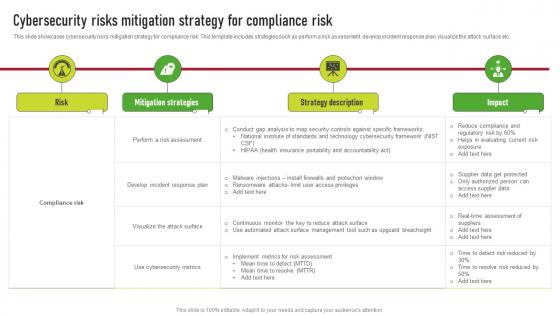 Cybersecurity Risks Mitigation Strategy For Compliance Risk Supplier Risk Management
Cybersecurity Risks Mitigation Strategy For Compliance Risk Supplier Risk ManagementThis slide showcases cybersecurity risks mitigation strategy for compliance risk. This template includes strategies such as perform a risk assessment, develop incident response plan, visualize the attack surface etc. Deliver an outstanding presentation on the topic using this Cybersecurity Risks Mitigation Strategy For Compliance Risk Supplier Risk Management. Dispense information and present a thorough explanation of Mitigation Strategies, Strategy Description, Risk using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
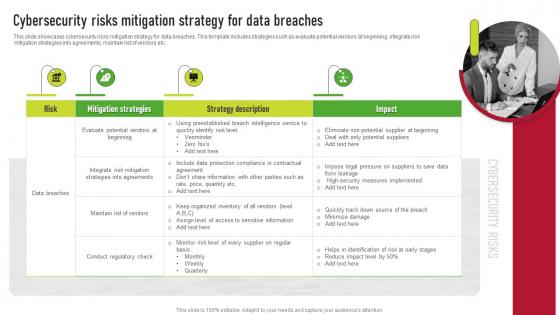 Cybersecurity Risks Mitigation Strategy For Data Breaches Supplier Risk Management
Cybersecurity Risks Mitigation Strategy For Data Breaches Supplier Risk ManagementThis slide showcases cybersecurity risks mitigation strategy for data breaches. This template includes strategies such as evaluate potential vendors at beginning, integrate risk mitigation strategies into agreements, maintain list of vendors etc. Introducing Cybersecurity Risks Mitigation Strategy For Data Breaches Supplier Risk Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Mitigation Strategies, Strategy Description, Risk, using this template. Grab it now to reap its full benefits.
-
 Cybersecurity Risks Mitigation Strategy For Service Disruptions Supplier Risk Management
Cybersecurity Risks Mitigation Strategy For Service Disruptions Supplier Risk ManagementThis slide showcases cybersecurity risks mitigation strategy for service disruptions. This template includes strategies such as see suppliers as partner, keep systems and software updated, use strong passwords etc. Present the topic in a bit more detail with this Cybersecurity Risks Mitigation Strategy For Service Disruptions Supplier Risk Management. Use it as a tool for discussion and navigation on Mitigation Strategies, Strategy Description, Service Disruptions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Unlocking The Impact Of Technology Steps For Building Business Cybersecurity Strategy
Unlocking The Impact Of Technology Steps For Building Business Cybersecurity StrategyThis slide showcases process for creating cybersecurity strategy. This template focuses on measuring protection against cyberthreats which disrupts employee productivity. It includes information related to assessing maturity, documenting strategy, etc. Introducing Unlocking The Impact Of Technology Steps For Building Business Cybersecurity Strategy to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Understand Cybersecurity Threat, Assess Maturity, Cybersecurity Awareness, Training Initiatives, using this template. Grab it now to reap its full benefits.
-
 Future Strategic Approach In Cybersecurity FIO SS
Future Strategic Approach In Cybersecurity FIO SSThe following slide showcases the key strategic approaches to be followed in cybersecurity to assist in shaping industry evolution. It includes pointers such provide firewall security, train employees, creating backup copies etc.Introducing our Future Strategic Approach In Cybersecurity FIO SS set of slides. The topics discussed in these slides are Provide Firewall Security, Protect Information, Train Employees. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Strategies For Big Data Cybersecurity Analytics
Strategies For Big Data Cybersecurity AnalyticsThe following slide highlights key points like data collection, data normalization, expansion, enrichment, automation, standardization, and advanced detection to show strategies for big data analytics cybersecurity. It helps organizations to proactively defend against cyber threats and enhance overall security posture. Presenting our set of slides with Strategies For Big Data Cybersecurity Analytics. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Collection, Expansion, Enrichment.
-
 Mitigation Strategies To Overcome Improving IoT Device Cybersecurity IoT SS
Mitigation Strategies To Overcome Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to outline various techniques which can be used to mitigate botnet attack. It covers information about strong password, network segmentation, cloud based security, and traffic filtering. Increase audience engagement and knowledge by dispensing information using Mitigation Strategies To Overcome Improving IoT Device Cybersecurity IoT SS. This template helps you present information on four stages. You can also present information on Strong, Security, Network using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Mitigation Strategies To Overcome IoT Improving IoT Device Cybersecurity IoT SS
Mitigation Strategies To Overcome IoT Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to showcase multiple techniques which can be used to overcome security breach caused by Verkada hack. The strategies mentioned in slide are regular security audit, secure authentication, firmware update, and encryption. Introducing Mitigation Strategies To Overcome IoT Improving IoT Device Cybersecurity IoT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Continuous, Authentication, Encryption, using this template. Grab it now to reap its full benefits.
-
 Mitigation Strategies To Overcome Jeep Hack Improving IoT Device Cybersecurity IoT SS
Mitigation Strategies To Overcome Jeep Hack Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to outline various mitigation techniques which can be used to overcome IoT cyber attack. The techniques outlined in slide are patch update, secure development practices, network segmentation, and strong authentication. Increase audience engagement and knowledge by dispensing information using Mitigation Strategies To Overcome Jeep Hack Improving IoT Device Cybersecurity IoT SS. This template helps you present information on four stages. You can also present information on Patch, Segmentation, Authentication using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Mitigation Strategies To Overcome Stuxnet Improving IoT Device Cybersecurity IoT SS
Mitigation Strategies To Overcome Stuxnet Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to highlight different mitigation techniques which can be used by companies to Internet of Things IoT security vulnerability. It covers information about strong access controls, security testing, user training, and robust security response plan. Introducing Mitigation Strategies To Overcome Stuxnet Improving IoT Device Cybersecurity IoT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Strong, Security, Incident, using this template. Grab it now to reap its full benefits.
-
 Strategic Model For IoT Cyber Security Improving IoT Device Cybersecurity IoT SS
Strategic Model For IoT Cyber Security Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to outline strategic framework for Internet of Things IoT cyber security. Information covered in this slide is related to IoT security elements and major principles such as edge processing, device intelligence, messaging control, device initiated connections, etc. Deliver an outstanding presentation on the topic using this Strategic Model For IoT Cyber Security Improving IoT Device Cybersecurity IoT SS. Dispense information and present a thorough explanation of Elements, Security, Device using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Various Strategies To Successfully Improving IoT Device Cybersecurity IoT SS
Various Strategies To Successfully Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to showcase different techniques through which companies can overcome Internet of Things IoT botnet attack. The strategies highlighted in slide are sender policy framework SPF, strong password policy, and string process for wire transfers. Present the topic in a bit more detail with this Various Strategies To Successfully Improving IoT Device Cybersecurity IoT SS. Use it as a tool for discussion and navigation on Policy, Strong, Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Strategies in Finance AI Image PowerPoint Presentation PPT ECS
Cybersecurity Strategies in Finance AI Image PowerPoint Presentation PPT ECSIntroducing a Visual PPT on Cybersecurity Strategies in Finance. Our design team have meticulously designed every PowerPoint Slide. Tailor the PPT content effortlessly. Additionally, the PPT Template is compatible with all monitor sizes and as well as Google Slides. Download the PPT, make the needed adjustments, and showcase with conviction.
-
 Strategies To Reduce Cybersecurity Concerns Comprehensive Guide On IoT Enabled IoT SS
Strategies To Reduce Cybersecurity Concerns Comprehensive Guide On IoT Enabled IoT SSThis slide exhibits key cybersecurity concerns solving methods for IoT enabled smart grid. These strategies include multiple authentication, employee training, password strength, and operating system protection.Introducing Strategies To Reduce Cybersecurity Concerns Comprehensive Guide On IoT Enabled IoT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Transmission Line Management, Safety Management, Corrective Maintenance, using this template. Grab it now to reap its full benefits.
-
 Cybersecurity Issues Overview And Key Statistics Strategic Guide For Web Design Company
Cybersecurity Issues Overview And Key Statistics Strategic Guide For Web Design CompanyMentioned slide provides introduction about cyber security issues. It includes key elements such as description, types of security issue, key facts, and negative impact on business. Present the topic in a bit more detail with this Cybersecurity Issues Overview And Key Statistics Strategic Guide For Web Design Company. Use it as a tool for discussion and navigation on Service, Authentication, Injection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
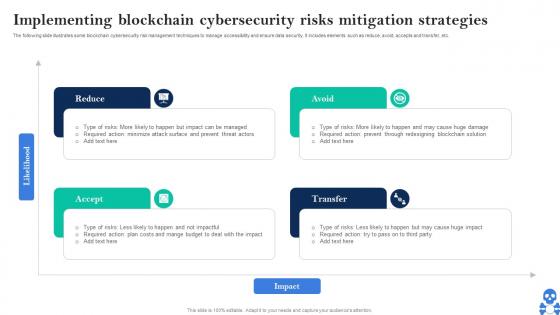
 Blockchain And Cybersecurity Implementing Blockchain Cybersecurity Risks Mitigation Strategies BCT SS V
Blockchain And Cybersecurity Implementing Blockchain Cybersecurity Risks Mitigation Strategies BCT SS VThe following slide illustrates some blockchain cybersecurity risk management techniques to manage accessibility and ensure data security. It includes elements such as reduce, avoid, accepts and transfer, etc. Increase audience engagement and knowledge by dispensing information using Blockchain And Cybersecurity Implementing Blockchain Cybersecurity Risks Mitigation Strategies BCT SS V This template helps you present information on Two stages. You can also present information on Reduce, Avoid, Transfer, Accept using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Enforcing AUP Cybersecurity Strategies For Network Monitoring
Enforcing AUP Cybersecurity Strategies For Network MonitoringThis slide covers AUP cybersecurity ways for providing clear expectations for using technology safely and appropriately in organization. It includes strategies such as understandable policies, corrective action plan, employee monitoring software, etc. Introducing our premium set of slides with Enforcing AUP Cybersecurity Strategies For Network Monitoring Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Understandable Policies, Corrective Action Plan So download instantly and tailor it with your information.
-
 Cyber Threats In Blockchain Implementing Blockchain Cybersecurity Risks Mitigation Strategies BCT SS V
Cyber Threats In Blockchain Implementing Blockchain Cybersecurity Risks Mitigation Strategies BCT SS VThe following slide illustrates some blockchain cybersecurity risk management techniques to manage accessibility and ensure data security. It includes elements such as reduce, avoid, accepts and transfer, etc. Introducing Cyber Threats In Blockchain Implementing Blockchain Cybersecurity Risks Mitigation Strategies BCT SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Reduce, Avoid, Transfer, Accept using this template. Grab it now to reap its full benefits.
-
 Cybersecurity Strategies To Safeguard It Infrastructure
Cybersecurity Strategies To Safeguard It InfrastructureThis slide showcases the cybersecurity tactics to secure IT infrastructure. This slide aims to help the business ensure its IT infrastructure is protected. It includes strategies such as segmented networks, utilization of encryption, monitoring networks and removing old devices and software. Introducing our premium set of slides with Cybersecurity Strategies To Safeguard It Infrastructure Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Segment Network, Utilize Encryption, Monitor Networks So download instantly and tailor it with your information.
-
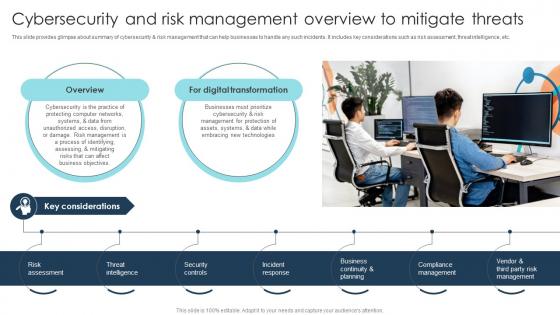 Cybersecurity And Risk Management Overview Digital Transformation Strategies To Integrate DT SS
Cybersecurity And Risk Management Overview Digital Transformation Strategies To Integrate DT SSThis slide provides glimpse about summary of cybersecurity and risk management that can help businesses to handle any such incidents. It includes key considerations such as risk assessment, threat intelligence, etc. Increase audience engagement and knowledge by dispensing information using Cybersecurity And Risk Management Overview Digital Transformation Strategies To Integrate DT SS. This template helps you present information on seven stages. You can also present information on Overview, Digital Transformation, Key Considerations using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Use Case Cybersecurity And Risk Management Digital Transformation Strategies To Integrate DT SS
Use Case Cybersecurity And Risk Management Digital Transformation Strategies To Integrate DT SSThis slide provides glimpse about business case that help businesses take various cybersecurity measures and mitigate risks. It includes introduction, challenges, initiatives, etc. Introducing Use Case Cybersecurity And Risk Management Digital Transformation Strategies To Integrate DT SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Data Protection, Industry Standards, Global Technology, using this template. Grab it now to reap its full benefits.
-
 Blackberry Compliance Considerations For Cybersecurity Strategies
Blackberry Compliance Considerations For Cybersecurity StrategiesThis slide showcases blackberry legal considerations for cybersecurity planning. The purpose of this slide is to assist businesses in aligning their strategies with industry standards for maintaining data integrity. It includes elements such as GDPR, SOX act, etc. Introducing our Blackberry Compliance Considerations For Cybersecurity Strategies set of slides. The topics discussed in these slides are Considerations, Strategies, Cybersecurity. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Implementing Blockchain Cybersecurity Risks Mitigation Strategies Guide For Blockchain BCT SS V
Implementing Blockchain Cybersecurity Risks Mitigation Strategies Guide For Blockchain BCT SS VThe following slide illustrates some blockchain cybersecurity risk management techniques to manage accessibility and ensure data security. It includes elements such as reduce, avoid, accepts and transfer, etc. Increase audience engagement and knowledge by dispensing information using Implementing Blockchain Cybersecurity Risks Mitigation Strategies Guide For Blockchain BCT SS V This template helps you present information on four stages. You can also present information on Reduce, Avoid, Transfer, Accept using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategies To Model Uncertainties For Opsec Cybersecurity
Strategies To Model Uncertainties For Opsec CybersecurityThis slide depicts the tactics to model uncertainties for opsec cybersecurity. The purpose of this slide is to help the business ensure it is able to accurately model threats dangers in order to eliminate them. It includes outlining potential threats, analyzing security vulnerabilities, etc. Introducing our premium set of slides with Strategies To Model Uncertainties For Opsec Cybersecurity. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Potential Threats, Analyze Security, Risk Level. So download instantly and tailor it with your information.
-
 Strategic Response Plan For Managing Financial Impact Of Cybersecurity Incidents
Strategic Response Plan For Managing Financial Impact Of Cybersecurity IncidentsThis slide provides a strategic framework for managing cybersecurity incident financial impact, helping organizations mitigate losses and maintain fiscal resilience amid evolving threats. Introducing our Strategic Response Plan For Managing Financial Impact Of Cybersecurity Incidents set of slides. The topics discussed in these slides are Customer Trust And Reputation Damage, Business Interruption, Loss Of Intellectual Property, Future Security Investments. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Select Cybersecurity Training Program Courses Implementing Strategies To Mitigate Cyber Security Threats
Select Cybersecurity Training Program Courses Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the best cybersecurity training courses to educate employees and minimize the possibility of cyber attacks. It includes cloud, disaster recovery, hardware, information security programs, duration, mode and cost Deliver an outstanding presentation on the topic using this Select Cybersecurity Training Program Courses Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Cloud Security, Information Security, Disaster Recovery using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategies To Select Accurate Cybersecurity Firewall
Strategies To Select Accurate Cybersecurity FirewallThis slide showcases the potential ways for choosing right cybersecurity firewall which helps an organization to customize protection and specify network management. It include details such as identify organizational needs, ensure scalability and verify maximum protection level. Introducing our Strategies To Select Accurate Cybersecurity Firewall set of slides. The topics discussed in these slides are Identify Organizational Needs, Ensure Scalability, Verify Maximum Protection Level . This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cybersecurity Incident Response Mitigation Strategies
Cybersecurity Incident Response Mitigation StrategiesThis slide showcases various approaches to mitigate cybersecurity incidents for securing business IT systems. The purpose of this slide is to help organizations in ensuring network security controls. It covers strategies such as multi-factor authentication, strengthening user apllications, application whitelisting and daily backups. Presenting our set of slides with Cybersecurity Incident Response Mitigation Strategies This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Strengthen User Applications, Daily Backups, Application Whitelisting.
-
 Maritime Cybersecurity Strategies For Risk Management
Maritime Cybersecurity Strategies For Risk ManagementThis slide showcases strategies for maritime cybersecurity. The main purpose of this template is to analyze vulnerable assets. This includes maritime assets, risk mitigation strategy, regulatory compliance, etc. Introducing our premium set of slides with Maritime Cybersecurity Strategies For Risk Management. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Maritime Assets, Risk Mitigation Strategy, Regulatory Compliance. So download instantly and tailor it with your information.
-
 Process To Develop Cybersecurity Strategy For Data Protection
Process To Develop Cybersecurity Strategy For Data ProtectionIntroducing our premium set of slides with Process To Develop Cybersecurity Strategy For Data Protection. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Threat Landscape, Cybersecurity Maturity, Cybersecurity Program Improvement. So download instantly and tailor it with your information.
-
 Strategies For Enhancing Cybersecurity In BCP And Disaster Recovery
Strategies For Enhancing Cybersecurity In BCP And Disaster RecoveryThis slide represents multiple strategies that helps businesses to enhance their cybersecurity in business continuity planning BCP for and disaster recovery. It includes strategies such as data replication, disaster recovery, and zero trust data security. Introducing our Strategies For Enhancing Cybersecurity In BCP And Disaster Recovery set of slides. The topics discussed in these slides are Data Replication, Disaster Recovery, Trust Data Security This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Strategies To Mitigate SCADA Network Cybersecurity Threats
Strategies To Mitigate SCADA Network Cybersecurity ThreatsThis slide represents various strategies that assist companies to mitigate various SCADA network threats for enhancing data cybersecurity. It includes various threats such as hackers, malware, and employees. In Presenting our well structured Strategies To Mitigate SCADA Network Cybersecurity Threats The topics discussed in this slide are Hackers, Malware, Employees. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Strategies To Implement Cybersecurity In Education
Strategies To Implement Cybersecurity In EducationThis slide showcases the strategies to implement cybersecurity in education. The purpose of this slide is to help the business manage and ensure cybersecurity is correctly established in an educational institute. It includes strategies such as conducting audits, immediate response to cyber attacks, etc. Introducing our premium set of slides with Strategies To Implement Cybersecurity In Education. Ellicudate the Five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Rules And Regulations, Technical Control Methods, Cyber Attacks. So download instantly and tailor it with your information.
-
 Timeline For Implementing IoT Security Strategy Internet Of Things IoT Security Cybersecurity SS
Timeline For Implementing IoT Security Strategy Internet Of Things IoT Security Cybersecurity SSThis slide showcases internet of things IoT security strategy timeline, referable for developers and businesses in protection of connected devices. It provides details about credentials, authentication, cryptography, etc. Introducing Timeline For Implementing IoT Security Strategy Internet Of Things IoT Security Cybersecurity SS to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Avoid Unnecessary Data Handling, Cryptographic Network Protocol Usage, Enforce Authentication Controls, using this template. Grab it now to reap its full benefits.
-
 Strategies And Recommendations For Cybersecurity Industry Global Cybersecurity Industry Outlook
Strategies And Recommendations For Cybersecurity Industry Global Cybersecurity Industry OutlookThe purpose of the slide is to provide valuable recommendations and effective strategies for cybersecurity industry players to succeed in a dynamic and competitive market. It covers strategies such as. Increase audience engagement and knowledge by dispensing information using Strategies And Recommendations For Cybersecurity Industry Global Cybersecurity Industry Outlook. This template helps you present information on five stages. You can also present information on Innovation And Research, Tailored Solutions, Education And Awareness using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key Strategies For Cybersecurity Risk Management
Key Strategies For Cybersecurity Risk ManagementFollowing slide highlights various risk management strategies to boost cyber security and sensitive data protection. It further covers capability assessments, program design, strategy, risk management, compliance, etc. Introducing our premium set of slides with Key Strategies For Cybersecurity Risk Management. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Third Party Risk Management, Capability Assessments, Risk Management. So download instantly and tailor it with your information.
-
 Cybersecurity Strategies For It Business Development
Cybersecurity Strategies For It Business DevelopmentThe purpose of this slide is to showcase cyber security development strategies like assurance framework and to encourage open standards, which helps bolster overall business resilience. Presenting our well structured Cybersecurity Strategies For It Business Development The topics discussed in this slide are Assurance Framework, Secure Cyber Ecosystem, Business Development This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Encryption For Data Define Security Requirements For Encryption Strategy Cybersecurity SS
Encryption For Data Define Security Requirements For Encryption Strategy Cybersecurity SSThis slide showcases encryption best practice focused on defining security requirements. It provides details about threat assessment, system vulnerabilities, business decisions, etc. Introducing Encryption For Data Define Security Requirements For Encryption Strategy Cybersecurity SS to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Conduct Threat Assessment, Learn Of Any Business Decisions, System Vulnerabilities, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Password Encryption Strategy For Maximum Security Cybersecurity SS
Encryption For Data Password Encryption Strategy For Maximum Security Cybersecurity SSThis slide showcases password encryption policies which can help organizations achieve maximum data security. It provides details about salting, SHA-2, Bcrypt, passcode age, auto-lock, etc. Present the topic in a bit more detail with this Encryption For Data Password Encryption Strategy For Maximum Security Cybersecurity SS. Use it as a tool for discussion and navigation on Require Alphanumeric Value, Maximum Passcode Age, Grace Period For Device Lock. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comprehensive Training Program For Cybersecurity Deception Strategies
Comprehensive Training Program For Cybersecurity Deception StrategiesThe purpose of this slide is to present a training program that enables personnel to upskill to identify and respond to cyber threats effectively by attending the cyber deception detection workshop. Presenting our set of slides with Comprehensive Training Program For Cybersecurity Deception Strategies. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Existing Training Scenario, Schedule, Training Items.
-
 Case Study For Implementing Optimized OT Cybersecurity Strategy
Case Study For Implementing Optimized OT Cybersecurity StrategyThis slide represents case study for implementing effective OT cybersecurity approach to mitigate cyber threats and enhance infrastructure protection. It includes various elements such as overview, challenges, solutions, and benefits. Presenting our set of slides with Case Study For Implementing Optimized OT Cybersecurity Strategy This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Overview, Challenges, Solution, Benefits
-
 Gantt Chart To Implement Pam Strategy For Cybersecurity
Gantt Chart To Implement Pam Strategy For CybersecurityThis slide represents gantt chart that assist companies to implement PAM strategy for enhancing their data cybersecurity effectively. It includes various steps such as accountability, understanding vulnerabilities, securing cloud, etc. Presenting our well structured Gantt Chart To Implement Pam Strategy For Cybersecurity. The topics discussed in this slide are Accountability For Privileged Passwords, Implement Least Privileged Access, Understand Vulnerabilities. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Strategic Password Authentication Training Plan IT Security Awareness Training Cybersecurity SS
Strategic Password Authentication Training Plan IT Security Awareness Training Cybersecurity SSThis slide represents training plan for verifying identity of user accessing a digital system. It includes details related to password authentication methods, training sessions etc. Deliver an outstanding presentation on the topic using this Strategic Password Authentication Training Plan IT Security Awareness Training Cybersecurity SS. Dispense information and present a thorough explanation of Token Authentication, Biometric Authentication, Strategic Password, Authentication Training Plan using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
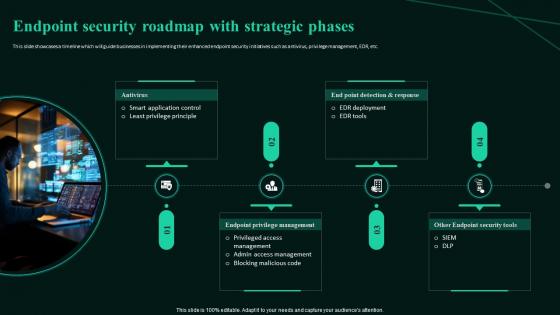 Endpoint Security Roadmap With Strategic Building Next Generation Endpoint Security Cybersecurity SS
Endpoint Security Roadmap With Strategic Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases a timeline which will guide businesses in implementing their enhanced endpoint security initiatives such as antivirus, privilege management, EDR, etc.Increase audience engagement and knowledge by dispensing information using Endpoint Security Roadmap With Strategic Building Next Generation Endpoint Security Cybersecurity SS. This template helps you present information on one stages. You can also present information on Other Endpoint Security Tools, Endpoint Privilege Management, Antivirus, End Point Detection And Response using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
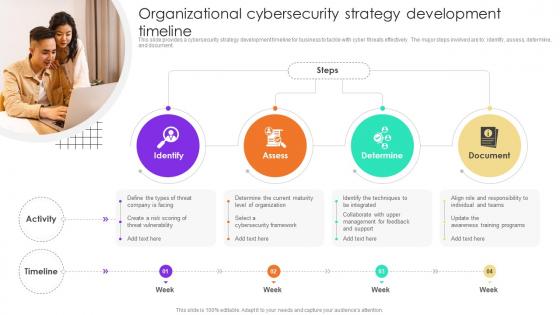 Organizational Cybersecurity Strategy Development Timeline
Organizational Cybersecurity Strategy Development TimelineThis slide provides a cybersecurity strategy development timeline for business to tackle with cyber threats effectively. The major steps involved are to identify, assess, determine, and document. Presenting our set of slides with Organizational Cybersecurity Strategy Development Timeline. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify, Assess, Determine, Document.
-
 Key Considerations For Building Cybersecurity Strategies
Key Considerations For Building Cybersecurity StrategiesThis slide showcases the major considerations for developing cybersecurity strategies which helps an organization to decrease attacks and data breaches by offering quick response time. It include details such as protect perimeter less technology,support zero trust,etc. Introducing our premium set of slides with Key Considerations For Building Cybersecurity Strategies. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Support Zero Trust,Provide Awareness Programs,Offer Security Knowledge. So download instantly and tailor it with your information.
-
 Cybersecurity Best Practices Essential For Government Strategic Guide To Implement Strategy SS
Cybersecurity Best Practices Essential For Government Strategic Guide To Implement Strategy SSThis slide showcases the Cyber security Best Practices essential for government. It includes best practices such as Investment in cyber security, International Cooperation, Public-Private Partnerships and Capacity Building.Introducing Cybersecurity Best Practices Essential For Government Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Public Private Partnerships, International Cooperation, Investment In Cybersecurity, Capacity Building, using this template. Grab it now to reap its full benefits.
-
 Cybersecurity Best Practices Essential For Individual Strategic Guide To Implement Strategy SS
Cybersecurity Best Practices Essential For Individual Strategic Guide To Implement Strategy SSThis slide showcases Cyber security Best Practices essential for individual. It includes best practices such as strong passwords, public Wi-Fi, device security and social media privacy. Increase audience engagement and knowledge by dispensing information using Cybersecurity Best Practices Essential For Individual Strategic Guide To Implement Strategy SS. This template helps you present information on four stages. You can also present information on Strong Passwords, Device Security, Social Media Privacy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity Best Practices Essential For Organizations Strategic Guide To Implement Strategy SS
Cybersecurity Best Practices Essential For Organizations Strategic Guide To Implement Strategy SSThis slide showcases the Cyber security Best Practices essential for organizations. It includes strategies such as Network Security, Access control, Patch Management and Vendor Security.Present the topic in a bit more detail with this Cybersecurity Best Practices Essential For Organizations Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Access Controls, Network Security, Patch Management, Vendor Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Need For Vigilance And Adaptation In Cybersecurity Strategic Guide To Implement Strategy SS
Need For Vigilance And Adaptation In Cybersecurity Strategic Guide To Implement Strategy SSThis slide showcases the Need for vigilance and adaptation in cyber security. It includes key points such as evolving threat landscape, pervasive cyber attacks, data as a target, adaptive strategies and resilience building.Present the topic in a bit more detail with this Need For Vigilance And Adaptation In Cybersecurity Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Pervasive Cyberattacks, Adaptive Strategies, Resilience Building, Evolving Threat Landscape. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Strategies For Small Business Network
Cybersecurity Strategies For Small Business NetworkThis slide highlights small business network security tactics including passwords and authentication, security training program and cyber insurance. Introducing our premium set of slides with name Cybersecurity Strategies For Small Business Network. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Passwords And Authentication, Security Training Program, Cyber Insurance. So download instantly and tailor it with your information.




