Powerpoint Templates and Google slides for Cybersecurity
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Various Types Of IoT Password Attack Improving IoT Device Cybersecurity IoT SS
Various Types Of IoT Password Attack Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to delineate multiple types of Internet of Things IoT password attack. Phishing, Dictionary Attack, Credential Stuffing, and Keyloggers are the major attacks which are mentioned in slide. Present the topic in a bit more detail with this Various Types Of IoT Password Attack Improving IoT Device Cybersecurity IoT SS. Use it as a tool for discussion and navigation on Phishing, Dictionary, Credential. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Blockchain And Cybersecurity Quarterly Loss Incurred Due To Blockchain Frauds BCT SS V
Blockchain And Cybersecurity Quarterly Loss Incurred Due To Blockchain Frauds BCT SS VThe following slide depicts the amount of loss incurred due to blockchain frauds and scams to securely encrypt financial transactions. It includes elements such as loss amount, number of incidents along with key insights, etc. Deliver an outstanding presentation on the topic using this Blockchain And Cybersecurity Quarterly Loss Incurred Due To Blockchain Frauds BCT SS V Dispense information and present a thorough explanation of Number Of Cybersecurity, Web3 Market, Blockchain Frauds using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Blockchain And Cybersecurity Top Ten Cryptocurrency Thefts Incidents By Amount BCT SS V
Blockchain And Cybersecurity Top Ten Cryptocurrency Thefts Incidents By Amount BCT SS VThe following slide represents the number of cryptocurrencies theft incidents by total amount to prevent attackers from unauthorized access. It includes elements such as ronin, poly network, wormhole, bitmart, venus, cream finance, along with key insights, etc. Present the topic in a bit more detail with this Blockchain And Cybersecurity Top Ten Cryptocurrency Thefts Incidents By Amount BCT SS V Use it as a tool for discussion and navigation on Top Cryptocurrency Threat, Loss Amount, Incidents By Amount This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Blockchain And Cybersecurity Total Cryptocurrency Stolen By Victim Type BCT SS V
Blockchain And Cybersecurity Total Cryptocurrency Stolen By Victim Type BCT SS VThe following slide depicts the total amount of cryptocurrencies stolen. It includes elements such as centralized exchange, decentralized finance protocol, etc. Deliver an outstanding presentation on the topic using this Blockchain And Cybersecurity Total Cryptocurrency Stolen By Victim Type BCT SS V Dispense information and present a thorough explanation of Major Instances, Defi Platform, Stealing Of Funds using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Blockchain And Cybersecurity Various Types Of Crypto Phishing Attacks BCT SS V
Blockchain And Cybersecurity Various Types Of Crypto Phishing Attacks BCT SS VThe following slide illustrates various types of phishing attacks to analyze how cryptocurrency funds are stolen from blockchain network. It includes elements such as spear, whaling, clone, spoof emails, accessibility to personal details, replacing original link with fake one, etc. Introducing Blockchain And Cybersecurity Various Types Of Crypto Phishing Attacks BCT SS V to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Spear Phishing, Whaling Phishing, Clone Phishing using this template. Grab it now to reap its full benefits.
-
 Blockchain And Cybersecurity Various Types Of Honeypot Technologies In Blockchain BCT SS V
Blockchain And Cybersecurity Various Types Of Honeypot Technologies In Blockchain BCT SS VThe following slide depicts some honeypot technologies to identify and reduce hacking attempts. It includes elements such as clients, malware, honeynets, database, honeypots, etc. Introducing Blockchain And Cybersecurity Various Types Of Honeypot Technologies In Blockchain BCT SS V to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Client Honeyspot, Malware Honeypots using this template. Grab it now to reap its full benefits.
-
 Blockchain And Cybersecurity Year Over Year Blockchain Fraud Trends BCT SS V
Blockchain And Cybersecurity Year Over Year Blockchain Fraud Trends BCT SS VThe following slide depicts change in blockchain frauds over years to analyze trends and minimize frauds. It includes elements such as hacks, thefts, frauds, misappropriation along with key insights, etc. Present the topic in a bit more detail with this Blockchain And Cybersecurity Year Over Year Blockchain Fraud Trends BCT SS V Use it as a tool for discussion and navigation on Blockchain Cybersecurity, Hacks And Thefts This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 5G Cybersecurity Market Analysis By Component
5G Cybersecurity Market Analysis By ComponentThis slide highlights the component wise market analysis for 5G cyber security. The purpose of this slide is to forecast the 5G cyber security market for the future by observing historic trends. Introducing our 5G Cybersecurity Market Analysis By Component set of slides. The topics discussed in these slides are Increased, Solutions, Services. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Global 5G Cybersecurity Market Forecast
Global 5G Cybersecurity Market ForecastThis slide depicts the global 5G cybersecurity market forecast. The purpose of this slide is to help the business observe historic trends and adopt suitable techniques in order to safeguard its 5G network. Presenting our well structured Global 5G Cybersecurity Market Forecast. The topics discussed in this slide are Increased, Digital, Market. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Implementing Robust Cybersecurity Elevating Small And Medium Enterprises Digital Transformation DT SS
Implementing Robust Cybersecurity Elevating Small And Medium Enterprises Digital Transformation DT SSThis slide presents various cybersecurity measures to safeguard organization in the digital era. It includes measures such as continuous vulnerability management, secure configurations, data protection, data recovery, proactive monitoring and detection, and boundary defence. Present the topic in a bit more detail with this Implementing Robust Cybersecurity Elevating Small And Medium Enterprises Digital Transformation DT SS. Use it as a tool for discussion and navigation on Organization Networks, Data Protection, Controlled Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview Cybersecurity And Data Protection Elevating Small And Medium Enterprises Digital Transformation DT SS
Overview Cybersecurity And Data Protection Elevating Small And Medium Enterprises Digital Transformation DT SSThis slide presents an overview into the landscape of cybersecurity and data protection with its advantages. It also presents a survey analysis on share of SMEs that have implemented essential and basic IT security initiatives. Deliver an outstanding presentation on the topic using this Overview Cybersecurity And Data Protection Elevating Small And Medium Enterprises Digital Transformation DT SS. Dispense information and present a thorough explanation of Digital Technologies, Organizations Digital, Digital Transformation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Solutions To Multiple Cybersecurity Comprehensive Guide On Investment Banking Concepts Fin SS
Solutions To Multiple Cybersecurity Comprehensive Guide On Investment Banking Concepts Fin SSThis slide shows information which can be used by individuals or investment bankers to get the right solution for cybersecurity challenges. These solutions include cybersecurity framework, training, data encryption, etc. Deliver an outstanding presentation on the topic using this Solutions To Multiple Cybersecurity Comprehensive Guide On Investment Banking Concepts Fin SS. Dispense information and present a thorough explanation of Solutions, Cybersecurity, Cybersecurity Framework using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
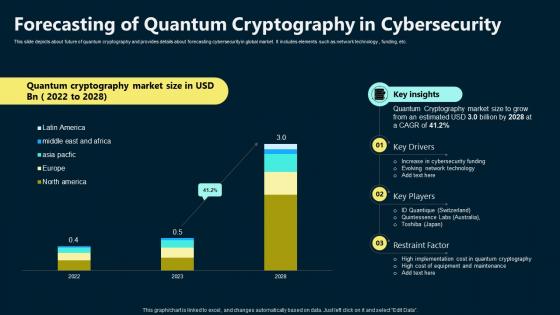 Forecasting Of Quantum Cryptography In Cybersecurity
Forecasting Of Quantum Cryptography In CybersecurityThis slide depicts about future of quantum cryptography and provides details about forecasting cybersecurity in global market. It includes elements such as network technology , funding, etc. Presenting our well structured Forecasting Of Quantum Cryptography In Cybersecurity. The topics discussed in this slide are Forecasting, Cryptography, Cybersecurity. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Triage Security Dashboard To Detect Cybersecurity Issues
Triage Security Dashboard To Detect Cybersecurity IssuesThis slide represents triage cyber security dashboard to detect cybersecurity issues which is utilized by organizations to investigate its endpoints and detect cyber threats. It includes key components such as total incidents count, level of threat, etc Introducing our Triage Security Dashboard To Detect Cybersecurity Issues set of slides. The topics discussed in these slides are Incident Trend By Level, Classification Of Incidents, Top Attackers. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cybersecurity Breach Incident Response Dashboard
Cybersecurity Breach Incident Response DashboardThis dashboard enables real-time monitoring for swift cybersecurity incident response, minimizing damage and enhancing overall cyber resilience. Presenting our well structured Cybersecurity Breach Incident Response Dashboard. The topics discussed in this slide are Cybersecurity Breach, Incident Response Dashboard, Overall Cyber Resilience. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Effective Technologies For Cybersecurity Incident Response
Effective Technologies For Cybersecurity Incident ResponseThis slide explores effective security technology for cybersecurity incident response, optimizing response times, minimizing impact, and strengthening overall defense against evolving cyber threats. Introducing our Effective Technologies For Cybersecurity Incident Response set of slides. The topics discussed in these slides are Effective Technologies, Cybersecurity Incident Response, Minimizing Impact, Strengthening. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Next Generation Cybersecurity Firewall Market Snapshot
Next Generation Cybersecurity Firewall Market SnapshotThis slide showcases the next generation cybersecurity firewall market size referable for users, investors and business owners for making relevant decisions. It include details such as increase in the demand of internet of things implementation and rise in internal and external threats. Introducing our Next Generation Cybersecurity Firewall Market Snapshot set of slides. The topics discussed in these slides are Generation Cybersecurity, Market Snapshot. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Introduction To Cybersecurity Using Decoding The Future Of Blockchain Technology BCT SS
Introduction To Cybersecurity Using Decoding The Future Of Blockchain Technology BCT SSThis slide provides an overview of enhancing cybersecurity using blockchain technology integration and its key facts. Facts include reduction in costs, key enablers and influence on smart contracts. Deliver an outstanding presentation on the topic using this Introduction To Cybersecurity Using Decoding The Future Of Blockchain Technology BCT SS. Dispense information and present a thorough explanation of Reducing Identity Theft Risks, Cybersecurity, Cybersecurity Using Blockchain using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Score Metrics Evaluation Of Cybersecurity Training Dashboard
Security Score Metrics Evaluation Of Cybersecurity Training DashboardThis slide demonstrates cybersecurity training metrics KPI dashboard to measure risk rating and include security score, security score category breakdown, high risk participants, etc. Introducing our Security Score Metrics Evaluation Of Cybersecurity Training Dashboard set of slides. The topics discussed in these slides are Security Score Metrics Evaluation, Cybersecurity Training Dashboard This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Statistics Associated With Retail Cybersecurity Threats
Statistics Associated With Retail Cybersecurity ThreatsThis slide highlights stats data for vulnerabilities affecting retail cybersecurity. The purpose of this template is to provide businesses with quantitative for fostering strategic defences and risk management. It includes elements such as credential phishing, ransomware, etc. Introducing our Statistics Associated With Retail Cybersecurity Threats set of slides. The topics discussed in these slides are Statistics Associated, Retail Cybersecurity Threats This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Types Of Cybersecurity Attacks In Education
Types Of Cybersecurity Attacks In EducationThis slide depicts the types of cybersecurity attacks in education. This slide aims to help education businesses adopt suitable measures to prevent cyberattacks. It includes a graphical analysis and key insights Introducing our Types Of Cybersecurity Attacks In Education set of slides. The topics discussed in these slides are Cyberattacks In Education, Education Is Phishing. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Graph Showing Incident Response Cybersecurity Challenges
Graph Showing Incident Response Cybersecurity ChallengesThis slide highlights cybersecurity challenges for establishing effective framework to manage incidents, protecting assets, and ensuring business resilience. It includes bases such as growth drivers and opportunities available. Presenting our well structured Graph Showing Incident Response Cybersecurity Challenges The topics discussed in this slide are Growth Drivers, Opportunities Available This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Top Cybersecurity Challenges Faced By Business Firms
Top Cybersecurity Challenges Faced By Business FirmsThis slide demonstrates cybersecurity challenges in business for safeguarding sensitive information, protecting business operations, and maintaining customer trust. It includes bases such as growth drivers and opportunities available. Introducing our Top Cybersecurity Challenges Faced By Business Firms set of slides. The topics discussed in these slides are Growth Drivers, Opportunities Available This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Avoid Unnecessary Data Access Storage And Transmission Internet Of Things IoT Security Cybersecurity SS
Avoid Unnecessary Data Access Storage And Transmission Internet Of Things IoT Security Cybersecurity SSThis slide showcases avoiding unnecessary resources on internet of things IoT devices, helping developers avoid transmission and storage costs. It provides details about data classification, compliance, etc. Deliver an outstanding presentation on the topic using this Avoid Unnecessary Data Access Storage And Transmission Internet Of Things IoT Security Cybersecurity SS. Dispense information and present a thorough explanation of Privacy And Compliance Considerations, Data Privacy And Compliance, Data Access Storage using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Business Survey Highlighting Common IoT Security Threats Internet Of Things IoT Security Cybersecurity SS
Business Survey Highlighting Common IoT Security Threats Internet Of Things IoT Security Cybersecurity SSThis slide showcases common internet of things IoT threats in the company, referable for related businesses. It provides details about network scan, command injection, SQL, zero-day, etc. Present the topic in a bit more detail with this Business Survey Highlighting Common IoT Security Threats Internet Of Things IoT Security Cybersecurity SS. Use it as a tool for discussion and navigation on Cyber Security Awareness, Quality Threat Modeling Tools, Weak Passwords, Authentication Practices. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Dashboard Showcasing Security Status Of IoT Devices Internet Of Things IoT Security Cybersecurity SS
Dashboard Showcasing Security Status Of IoT Devices Internet Of Things IoT Security Cybersecurity SSThis slide showcases dashboard for security status of deployed internet of things IoT devices. It provides details about connected sites, IP address, vulnerabilities, critical firmware, etc. Deliver an outstanding presentation on the topic using this Dashboard Showcasing Security Status Of IoT Devices Internet Of Things IoT Security Cybersecurity SS. Dispense information and present a thorough explanation of Dashboard, Security Status, IoT Devices, Vulnerabilities, Critical Firmware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Impact Analysis Of IoT Security Strategies Internet Of Things IoT Security Cybersecurity SS
Impact Analysis Of IoT Security Strategies Internet Of Things IoT Security Cybersecurity SSThis slide showcases impact analysis for deployed internet of things IoT security tools and strategies. It provides details about IoT ransomware, user privacy, insecure interfaces, remote work attacks, etc. Present the topic in a bit more detail with this Impact Analysis Of IoT Security Strategies Internet Of Things IoT Security Cybersecurity SS. Use it as a tool for discussion and navigation on Internet Of Things, Security Tools And Strategies, IoT Ransomware, Remote Work Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IoT Cyber Security Budget Plan Internet Of Things IoT Security Cybersecurity SS
IoT Cyber Security Budget Plan Internet Of Things IoT Security Cybersecurity SSThis slide showcases security budget plan for internet of things IoT operations. It provides details about secure data transmission, reduce attack surface, add features from gateways, understand data, etc. Present the topic in a bit more detail with this IoT Cyber Security Budget Plan Internet Of Things IoT Security Cybersecurity SS. Use it as a tool for discussion and navigation on IoT Cyber Security, Budget Plan, Reduce Attack Surface, Internet Of Things. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IoT Security Market Size Analysis Internet Of Things IoT Security Cybersecurity SS
IoT Security Market Size Analysis Internet Of Things IoT Security Cybersecurity SSThis slide showcases internet of things IoT security market analysis snapshot, referable for related businesses and investors. It provides details about industry 4.0, vulnerabilities, cyber resilience, etc. Present the topic in a bit more detail with this IoT Security Market Size Analysis Internet Of Things IoT Security Cybersecurity SS. Use it as a tool for discussion and navigation on IoT Security, Market Size Analysis, Internet Of Things, Vulnerabilities, Cyber Resilience. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Minimize The Attack Surface Of Your IoT Ecosystem Internet Of Things IoT Security Cybersecurity SS
Minimize The Attack Surface Of Your IoT Ecosystem Internet Of Things IoT Security Cybersecurity SSThis slide showcases application of attack surface minimization on internet of things IoT devices, referable for businesses in developing mitigation process. It provides details about unused points, configuration, etc. Deliver an outstanding presentation on the topic using this Minimize The Attack Surface Of Your IoT Ecosystem Internet Of Things IoT Security Cybersecurity SS. Dispense information and present a thorough explanation of Eliminate Unused Points, System Security, Exploitation Opportunities, Probability Of Unauthorized Access using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Training Budget For Seamless Integration Of Cybersecurity Frameworks
Training Budget For Seamless Integration Of Cybersecurity FrameworksThis slide showcases the breakdown cost for training of cyber security frameworks for seamless integration based on instructors costs, training material cost. Present the topic in a bit more detail with this Training Budget For Seamless Integration Of Cybersecurity Frameworks. Use it as a tool for discussion and navigation on Training Budget, Seamless Integration, Cybersecurity Frameworks, Training Material Cost. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Analyzing Barriers To Entry In The Cybersecurity Industry Global Cybersecurity Industry Outlook
Analyzing Barriers To Entry In The Cybersecurity Industry Global Cybersecurity Industry OutlookThe slide exhibits significant barriers to cybersecurity market entry, providing valuable insights for entrepreneurs, investors, and policymakers. These barriers make it difficult for new companies to compete with established players in the industry. Barriers include technical knowledge, regulatory compliance, High RandD cost, legal and ethical challenges. Increase audience engagement and knowledge by dispensing information using Analyzing Barriers To Entry In The Cybersecurity Industry Global Cybersecurity Industry Outlook. This template helps you present information on four stages. You can also present information on Technical Expertise, Regulatory Compliance, Rapid Technological Advancements using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity Industry Competitor Analysis With Attributes Global Cybersecurity Industry Outlook
Cybersecurity Industry Competitor Analysis With Attributes Global Cybersecurity Industry OutlookThe slide presents the key players in the cybersecurity industry. The purpose of the slide is to provide glimpse and competitor analysis of major players in the cybersecurity industry to gain insight into their products, services, and sales. It covers companies such as Palo alto networks, Inc, Fortinet, CrowdStrike, Checkpoint, and Zscaler, Inc. Introducing Cybersecurity Industry Competitor Analysis With Attributes Global Cybersecurity Industry Outlook to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Palo Alto Networks, Inc, Crowdstrike, Checkpoint, using this template. Grab it now to reap its full benefits.
-
 Emerging Threat Trends In Cybersecurity Industry Global Cybersecurity Industry Outlook
Emerging Threat Trends In Cybersecurity Industry Global Cybersecurity Industry OutlookThe slide presents the latest threat trends in the global cybersecurity industry. The purpose of the slide is to raise awareness about the evolving landscape of cyber threats, which is crucial for individuals and organizations to stay protected. It covers threat such as automotive hacking, cloud services attacks, social engineering attacks, 5g network threats, and ransomware attacks. Increase audience engagement and knowledge by dispensing information using Emerging Threat Trends In Cybersecurity Industry Global Cybersecurity Industry Outlook. This template helps you present information on three stages. You can also present information on Automotive Hacking, Attacks Against Cloud Services, Social Engineering Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Major Market Trends Impacting Cybersecurity Industry Global Cybersecurity Industry Outlook
Major Market Trends Impacting Cybersecurity Industry Global Cybersecurity Industry OutlookThe slide highlights the market trends in the global cybersecurity industry. These trends are having a significant impact on the way the industry operates, and they are likely to continue in the coming years. It cover trends such as artificial intelligence, real-time data monitoring, managed services, users as an attack surface, and quantum cryptography. Introducing Major Market Trends Impacting Cybersecurity Industry Global Cybersecurity Industry Outlook to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Rise Of Artificial Intelligence, Real Time Data Monitoring, Increase In Managed Services, using this template. Grab it now to reap its full benefits.
-
 PESTLE Analysis Of Global Cybersecurity Industry Global Cybersecurity Industry Outlook
PESTLE Analysis Of Global Cybersecurity Industry Global Cybersecurity Industry OutlookThe slide depicts PESTLE analysis which companies can use to evaluate the external factors that impact the industrys growth and profitability. It enables companies to make informed decisions and strategic planning in a dynamic business environment. Key components include political, legal, economic, social, technological and environmental aspects. Increase audience engagement and knowledge by dispensing information using PESTLE Analysis Of Global Cybersecurity Industry Global Cybersecurity Industry Outlook. This template helps you present information on three stages. You can also present information on Political Factors, Economic Factors, Social Factors using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Kpi Dashboard Showcasing Cybersecurity In Big Data Analytics
Kpi Dashboard Showcasing Cybersecurity In Big Data AnalyticsThis slide highlights big data analytics cybersecurity threats showcasing KPI dashboard for user awareness against insecure systems. It further covers risk and compliance, threat detection, top threat by class, security control table, etc. Presenting our well structured Kpi Dashboard Showcasing Cybersecurity In Big Data Analytics. The topics discussed in this slide are KPI Dashboard, Showcasing Cybersecurity, Big Data Analytics, Security Control Table. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Encryption For Data Encrypted Email Practices For Secure Messaging Cybersecurity SS
Encryption For Data Encrypted Email Practices For Secure Messaging Cybersecurity SSThis slide showcases public key cryptography deployment which can help employees increased speed and user experience of their platforms. It provides details about private key, key generation, decryption, etc. Present the topic in a bit more detail with this Encryption For Data Encrypted Email Practices For Secure Messaging Cybersecurity SS. Use it as a tool for discussion and navigation on Reduced Data Breaches, Reduced Email Compromises, Create Strong Passwords. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Endpoint Encryption Progress Monitoring Dashboard Cybersecurity SS
Encryption For Data Endpoint Encryption Progress Monitoring Dashboard Cybersecurity SSThis slide showcases endpoint encryption progress monitoring dashboard focused on tracking protection status of organizations computers. It provides details about warning period, managed, decrypted drives, etc. Present the topic in a bit more detail with this Encryption For Data Endpoint Encryption Progress Monitoring Dashboard Cybersecurity SS. Use it as a tool for discussion and navigation on Decrypting, Managed Computers, Non-Reporting Computers, Computer With Decrypted Drives. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Impact Analysis Of Comprehensive Encryption Strategies Cybersecurity SS
Encryption For Data Impact Analysis Of Comprehensive Encryption Strategies Cybersecurity SSThis slide showcases post implementation analysis of encryption strategies. Its purpose is to make businesses aware of major and potential improvements. It provides information about vulnerabilities, costs, responsiveness, etc. Present the topic in a bit more detail with this Encryption For Data Impact Analysis Of Comprehensive Encryption Strategies Cybersecurity SS. Use it as a tool for discussion and navigation on Costs, Responsiveness Speed, Vulnerabilities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Major Types Of Encryption For Data Security Cybersecurity SS
Encryption For Data Major Types Of Encryption For Data Security Cybersecurity SSThis slide major types of encryption technology, focused on improving data privacy and security of todays business. It provides details about symmetric, asymmetric, RSA, data encryption standard, etc. Introducing Encryption For Data Major Types Of Encryption For Data Security Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Symmetric Encryption, Asymmetric Encryption, RSA Encryption, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data SSL Protocol Deployment For Secure Communication Cybersecurity SS
Encryption For Data SSL Protocol Deployment For Secure Communication Cybersecurity SSThis slide showcases secure socket layer SSL deployment which can help employees perform secure communication within businesses. It provides details about certificate authority, webmaster, etc. Present the topic in a bit more detail with this Encryption For Data SSL Protocol Deployment For Secure Communication Cybersecurity SS. Use it as a tool for discussion and navigation on Reduced Message Forgery, Reduced Data Theft, Less Eavesdropping. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Global Market Research For AI And ML In Cybersecurity
Global Market Research For AI And ML In CybersecurityThis slide covers AI and ML market research in cybersecurity and includes growth drivers and key factors Presenting our well structured Global Market Research For AI And ML In Cybersecurity. The topics discussed in this slide are Growth Drivers, Cybersecurity Training, User Authentication. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 IT Cybersecurity Operation Reporting Dashboard
IT Cybersecurity Operation Reporting DashboardThis slide depicts the reporting dashboard to track companys IT and cybersecurity measures. The purpose of this slide is to help the business safeguard its networks through the analysis of its current measures. It includes elements such as intrusion attempts, mean detection time, etc. Introducing our IT Cybersecurity Operation Reporting Dashboard set of slides. The topics discussed in these slides are Cyber Security, Advanced, Average Resolution Time. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Major Impacts Of Public Policy On Cybersecurity
Major Impacts Of Public Policy On CybersecurityThis slide showcases the essential impacts of public policy on cybersecurity which helps an organization to gain relevant insights that ease operational tasks and provide protection against threats. Presenting our well structured Major Impacts Of Public Policy On Cybersecurity The topics discussed in this slide are Understand Issues, Policy Changes, Positive EffectsThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Global Cybersecurity Trends With Incident Volumes By Sectors
Global Cybersecurity Trends With Incident Volumes By SectorsThis slide graphically represents global cybersecurity trends that help businesses to understand and enhance data security against potential attacks. It includes trends such as common cyber attacks, top global frauds, and cybersecurity incident volume by sector. Presenting our well structured Global Cybersecurity Trends With Incident Volumes By Sectors. The topics discussed in this slide are Common Cyber Attacks, Companies Experienced, Top Global Frauds. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Best Practices For Data Loss Prevention Policy Safeguarding Business With Data Loss Cybersecurity SS
Best Practices For Data Loss Prevention Policy Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding best practices for data loss prevention in terms of identify and classify, regulatory compliance, and business information.Increase audience engagement and knowledge by dispensing information using Best Practices For Data Loss Prevention Policy Safeguarding Business With Data Loss Cybersecurity SS. This template helps you present information on three stages. You can also present information on Business Information DLP, Regulatory Compliance, Identify And Classify using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
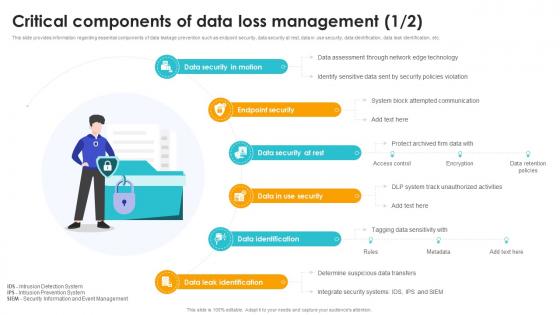 Critical Components Of Data Loss Management Safeguarding Business With Data Loss Cybersecurity SS
Critical Components Of Data Loss Management Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding essential components of data leakage prevention such as endpoint security, data security at rest, data in use security, data identification, data leak identification, etc.Introducing Critical Components Of Data Loss Management Safeguarding Business With Data Loss Cybersecurity SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Data Identification, Data Security At Rest, Endpoint Security, Data Leak Identification, using this template. Grab it now to reap its full benefits.
-
 Cyber Protection Dashboard To Track Data Loss Safeguarding Business With Data Loss Cybersecurity SS
Cyber Protection Dashboard To Track Data Loss Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding cybersecurity dashboard to track activities such as malware blocked, vulnerabilities detected, patches ready to install, protection status, active alerts, to ensure minimum data loss.Present the topic in a bit more detail with this Cyber Protection Dashboard To Track Data Loss Safeguarding Business With Data Loss Cybersecurity SS. Use it as a tool for discussion and navigation on Protection Status, Active Alerts Summary, Activities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Dashboard To Leverage Cybersecurity Across Workplace Safeguarding Business With Data Loss Cybersecurity SS
Dashboard To Leverage Cybersecurity Across Workplace Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding the dashboard to handle cybersecurity across firm by tracking patches applied, vulnerabilities detected, intrusion attempted, security score, etc.Deliver an outstanding presentation on the topic using this Dashboard To Leverage Cybersecurity Across Workplace Safeguarding Business With Data Loss Cybersecurity SS. Dispense information and present a thorough explanation of Intrusion Attempts, Successful Intrusions, Security Score using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Incidents At Global Scale Safeguarding Business With Data Loss Cybersecurity SS
Data Breach Incidents At Global Scale Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding data breach incidents across globe with rise in cyber attacks leading to substantial data loss.Deliver an outstanding presentation on the topic using this Data Breach Incidents At Global Scale Safeguarding Business With Data Loss Cybersecurity SS. Dispense information and present a thorough explanation of Business Growth, Global Level, Single Data Breach using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Global Data Loss Prevention Market Overview Safeguarding Business With Data Loss Cybersecurity SS
Global Data Loss Prevention Market Overview Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding global market scenario of data loss prevention in terms of prominent players, and growth drivers.Deliver an outstanding presentation on the topic using this Global Data Loss Prevention Market Overview Safeguarding Business With Data Loss Cybersecurity SS. Dispense information and present a thorough explanation of Growth Drivers, Prominent Players, Data Visibility And Control using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phase 5 Of Dlp Success Monitor Risk Reduction Outcomes Safeguarding Business With Data Loss Cybersecurity SS
Phase 5 Of Dlp Success Monitor Risk Reduction Outcomes Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding monitoring of risk reduction outcomes for successful data loss prevention execution. It includes tracking of data loss likelihood across platforms such as web, email, etc.Deliver an outstanding presentation on the topic using this Phase 5 Of Dlp Success Monitor Risk Reduction Outcomes Safeguarding Business With Data Loss Cybersecurity SS. Dispense information and present a thorough explanation of Marker Legend, Goals, Data Loss Likelihood using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
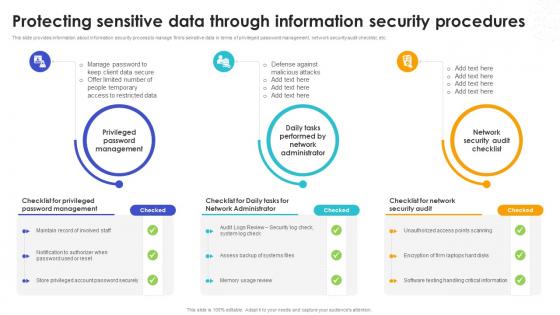 Protecting Sensitive Data Through Information Security Safeguarding Business With Data Loss Cybersecurity SS
Protecting Sensitive Data Through Information Security Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information about information security process to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc.Introducing Protecting Sensitive Data Through Information Security Safeguarding Business With Data Loss Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Network Security Audit, Privileged Password Management, Network Administrator, using this template. Grab it now to reap its full benefits.
-
 Global Overview Of Pam Cybersecurity Solution Market Size
Global Overview Of Pam Cybersecurity Solution Market SizeThis slide graphically represents global market overview of PAM solutions that assist companies in enhancing their cybersecurity against online threats. It includes various growth drivers such as increasing cyber threats, increasing cloud technologies, etc. Introducing our Global Overview Of Pam Cybersecurity Solution Market Size set of slides. The topics discussed in these slides are Overview, Cybersecurity, Solution. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Analyzing High Risk Employees And Departments IT Security Awareness Training Cybersecurity SS
Analyzing High Risk Employees And Departments IT Security Awareness Training Cybersecurity SSThis slide represents report for analyzing high risk participants and departments that requires continuous IT security awareness training. It includes details related to high risk participants etc. Present the topic in a bit more detail with this Analyzing High Risk Employees And Departments IT Security Awareness Training Cybersecurity SS. Use it as a tool for discussion and navigation on Analyzing High Risk, Employees And Departments, Marketing Team, Operations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Security Awareness Training Program Outline IT Security Awareness Training Cybersecurity SS
Cloud Security Awareness Training Program Outline IT Security Awareness Training Cybersecurity SSThis slide represents overview of training program highlighting set of measures which protects data stored online from theft, leakage and detection. It includes details related to program overview, skills etc. Introducing Cloud Security Awareness Training Program Outline IT Security Awareness Training Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Security Awareness, Training Program Outline, Cloud Architecture And Design, Cloud Infrastructure Security, using this template. Grab it now to reap its full benefits.
-
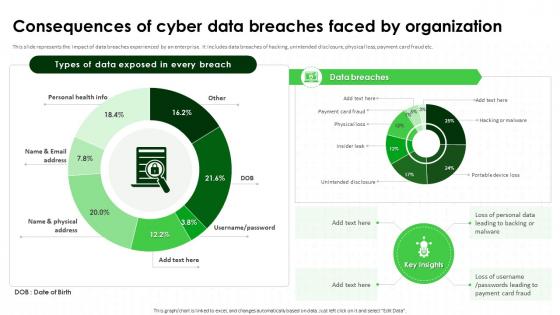 Consequences Of Cyber Data Breaches Faced IT Security Awareness Training Cybersecurity SS
Consequences Of Cyber Data Breaches Faced IT Security Awareness Training Cybersecurity SSThis slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Present the topic in a bit more detail with this Consequences Of Cyber Data Breaches Faced IT Security Awareness Training Cybersecurity SS. Use it as a tool for discussion and navigation on Consequences Of Cyber Data Breaches, Unintended Disclosure, Physical Loss, Payment Card Fraud. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Gap Analysis Representing Current Situation Of Cyber IT Security Awareness Training Cybersecurity SS
Gap Analysis Representing Current Situation Of Cyber IT Security Awareness Training Cybersecurity SSThis slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. Deliver an outstanding presentation on the topic using this Gap Analysis Representing Current Situation Of Cyber IT Security Awareness Training Cybersecurity SS. Dispense information and present a thorough explanation of Gap Analysis Representing, Current Situation Of Cyber Attacks, Employee Productivity Rates using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Impact Of IT Security Awareness Program On Organizational Kpis Cybersecurity SS
Impact Of IT Security Awareness Program On Organizational Kpis Cybersecurity SSThis slide represents impact of strategy deployed by IT and security professionals for preventing and mitigating cyber security risks on organizational KPIs such as annual revenue etc. Present the topic in a bit more detail with this Impact Of IT Security Awareness Program On Organizational Kpis Cybersecurity SS. Use it as a tool for discussion and navigation on Increase In Potential Annual Revenue, Increase In Employee Productivity Rates, Increase In Customer Satisfaction Rates. This template is free to edit as deemed fit for your organization. Therefore download it now.





