Powerpoint Templates and Google slides for Cybersecurity
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Vulnerability Rating For Risk Identification Cybersecurity Risk Analysis And Management Plan
Vulnerability Rating For Risk Identification Cybersecurity Risk Analysis And Management PlanThis slide showcases table for allocating vulnerability rating to different class of information assets. Its shows information about severity, vulnerability score and description Deliver an outstanding presentation on the topic using this Vulnerability Rating For Risk Identification Cybersecurity Risk Analysis And Management Plan. Dispense information and present a thorough explanation of Vulnerability, Identification, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Difference Data Privacy Cybersecurity In Powerpoint And Google Slides Cpb
Difference Data Privacy Cybersecurity In Powerpoint And Google Slides CpbPresenting our Difference Data Privacy Cybersecurity In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Difference Data Privacy Cybersecurity This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cybersecurity Risks Of An Escalating Russia Ukraine Conflict String Of Cyber Attacks Against
Cybersecurity Risks Of An Escalating Russia Ukraine Conflict String Of Cyber Attacks AgainstThis slide represents the cybersecurity risks associated with russia and ukraine conflict that are the most serious cyber threat, and many organizations are advised to take precautions. Introducing Cybersecurity Risks Of An Escalating Russia Ukraine Conflict String Of Cyber Attacks Against to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Capabilities, Economic Warfare, Cybersecurity, using this template. Grab it now to reap its full benefits.
-
 How To Protect Yourself From Ongoing Cybersecurity Attacks String Of Cyber Attacks
How To Protect Yourself From Ongoing Cybersecurity Attacks String Of Cyber AttacksThis slide talks about how to protect yourself from ongoing russian cybersecurity attacks, including being on high alert, choosing a strong password, keeping antivirus software up to data, etc. Introducing How To Protect Yourself From Ongoing Cybersecurity Attacks String Of Cyber Attacks to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Choose A Strong Password, Check Your Credit, Unique Password, using this template. Grab it now to reap its full benefits.
-
 Quarterly Cybersecurity Awareness Training Program Plan
Quarterly Cybersecurity Awareness Training Program PlanThis slide covers quarterly cybersecurity awareness training program plan. It involves activities such as cybersecurity knowledge and survey, compliance training, phishing simulation etc. Introducing our Quarterly Cybersecurity Awareness Training Program Plan set of slides. The topics discussed in these slides are Responsible Person, Budget, Key Message, Core Awareness Activities. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Best Practices For Effective Cybersecurity Awareness Training Program
Best Practices For Effective Cybersecurity Awareness Training ProgramThis slide covers best practices for effective cybersecurity awareness training program. It involves best practices such as getting into compliance, including everyone, establishing basics and making training engaging and entertaining. Presenting our set of slides with name Best Practices For Effective Cybersecurity Awareness Training Program. This exhibits information on four stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Getting Into Compliance, Establishing Basics, Including Everyone.
-
 Cybersecurity Attack Vector Analysis For Effective Awareness Training
Cybersecurity Attack Vector Analysis For Effective Awareness TrainingThis slide covers cybersecurity attack vector analysis for effective awareness training. It involves malware, phishing, denial of service, poor encryption, device misconfiguration and cross site scripting. Introducing our premium set of slides with Cybersecurity Attack Vector Analysis For Effective Awareness Training. Elucidate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Attack Vector, Examples, Objective, Problem Identifier. So download instantly and tailor it with your information.
-
 Cybersecurity Awareness Topics To Considered For Effective Training
Cybersecurity Awareness Topics To Considered For Effective TrainingThis slide covers cybersecurity awareness topics to considered for effective training. It involves topics such as removable media, cloud security, public wi fi and physical security. Presenting our set of slides with name Cybersecurity Awareness Topics To Considered For Effective Training. This exhibits information on four stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Removable Media, Cloud Security, Physical Security, Public Wi Fi.
-
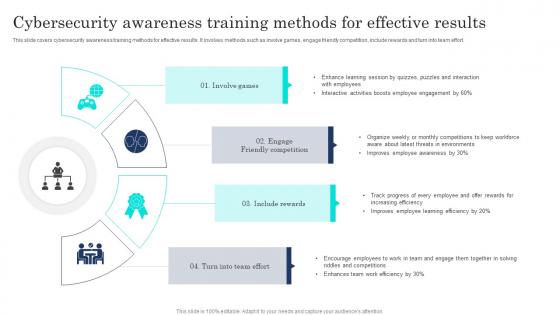 Cybersecurity Awareness Training Methods For Effective Results
Cybersecurity Awareness Training Methods For Effective ResultsThis slide covers cybersecurity awareness training methods for effective results. It involves methods such as involve games, engage friendly competition, include rewards and turn into team effort. Introducing our premium set of slides with Cybersecurity Awareness Training Methods For Effective Results. Elucidate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cybersecurity Awareness Training, Methods, Effective Results. So download instantly and tailor it with your information.
-
 Cybersecurity Awareness Training Program Process To Ensure Effectiveness
Cybersecurity Awareness Training Program Process To Ensure EffectivenessThis slide covers cybersecurity awareness training program process to ensure effectiveness. It involves steps such as identify training need, determine type of training, identify goals and objectives, implement and evaluate program. Presenting our set of slides with name Cybersecurity Awareness Training Program Process To Ensure Effectiveness. This exhibits information on five stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Implement Training, Evaluate Training Program, Determine Type Of Training, Identify Training Need.
-
 Cybersecurity Awareness Training To Enhance Effectiveness Of Employees
Cybersecurity Awareness Training To Enhance Effectiveness Of EmployeesThis slide covers cybersecurity awareness training to enhance effectiveness of employees. It involves document management, passwords and authentication and social engineering and phishing. Introducing our premium set of slides with Cybersecurity Awareness Training To Enhance Effectiveness Of Employees. Elucidate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Document Management, Passwords And Authentication, Social Engineering And Phishing. So download instantly and tailor it with your information.
-
 Employee Questionnaire To Assess Cybersecurity Awareness Training Effectiveness
Employee Questionnaire To Assess Cybersecurity Awareness Training EffectivenessThis slide covers employee questionnaire to assess cybersecurity training program effectiveness. It involves questions to determine trainer effectiveness in teaching, knowledge and skills of trainer and details about training organization. Introducing our Employee Questionnaire To Assess Cybersecurity Awareness Training Effectiveness set of slides. The topics discussed in these slides are Employee Questionnaire, Cybersecurity Awareness Training, Effectiveness. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Framework Of Cybersecurity Awareness Training Program
Framework Of Cybersecurity Awareness Training ProgramThis slide covers framework of cybersecurity awareness training program. It involves five steps such as analyse, plan, deploy, measure and optimize. Presenting our set of slides with name Framework Of Cybersecurity Awareness Training Program. This exhibits information on five stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Analyze, Plan, Deploy, Measure, Optimize.
-
 Key Elements Of Cybersecurity Awareness Training Program
Key Elements Of Cybersecurity Awareness Training ProgramThis slide covers key elements of cybersecurity awareness training program. It involves elements such as make message relevant, use real world examples, common language, present small messages and use continued reinforcement. Introducing our premium set of slides with Key Elements Of Cybersecurity Awareness Training Program. Elucidate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Make Message Relevant, Use Examples, Use Common Language, Present Small Messages . So download instantly and tailor it with your information.
-
 Monthly Cybersecurity Awareness Training Program Timeline
Monthly Cybersecurity Awareness Training Program TimelineThis slide covers monthly cybersecurity awareness training program timeline. It involves activities such as passwords training, phishing exercise, remote access testing and conduct internal tabletop exercises. Introducing our Monthly Cybersecurity Awareness Training Program Timeline set of slides. The topics discussed in these slides are Monthly, Cybersecurity Awareness Training, Program Timeline. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Phases Of Information Cybersecurity Awareness Training Program
Phases Of Information Cybersecurity Awareness Training ProgramThis slide covers phases of information cybersecurity awareness training program. It involves four phases such as design, development, execution and continual improvement. Presenting our well-structured Phases Of Information Cybersecurity Awareness Training Program. The topics discussed in this slide are Design, Development, Execution, Continual Improvement. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cybersecurity Risks In Powerpoint And Google Slides Cpb
Cybersecurity Risks In Powerpoint And Google Slides CpbPresenting Cybersecurity Risks In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cybersecurity Risks. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Agenda Formulating Cybersecurity Plan To Safeguard Information Assets
Agenda Formulating Cybersecurity Plan To Safeguard Information AssetsIntroducing Agenda Formulating Cybersecurity Plan To Safeguard Information Assets to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Current Information, Organization, Formulating Cybersecurity, using this template. Grab it now to reap its full benefits.
-
 Allocating Budget For Information Security Risk Management Formulating Cybersecurity Plan
Allocating Budget For Information Security Risk Management Formulating Cybersecurity PlanThis slide showcase budget to be allocated for conducting training for information security risk management. It showcases budget for areas like cybersecurity awareness, threat detection and risk management. Increase audience engagement and knowledge by dispensing information using Allocating Budget For Information Security Risk Management Formulating Cybersecurity Plan. This template helps you present information on two stages. You can also present information on Cybersecurity Awareness, Incident Management, Threat Detection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Analysing The Impact Of Security Threats On Organization Formulating Cybersecurity Plan
Analysing The Impact Of Security Threats On Organization Formulating Cybersecurity PlanPresent the topic in a bit more detail with this Analysing The Impact Of Security Threats On Organization Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Organization, Average Financial, Analysing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Analysing The Impact On Assets Due To Information Breach Formulating Cybersecurity Plan
Analysing The Impact On Assets Due To Information Breach Formulating Cybersecurity PlanThis slide showcases impact of information breach on different assets which can help organization in formulating risk monitoring policy. Its key components are criterion, criterion weight and information assets. Deliver an outstanding presentation on the topic using this Analysing The Impact On Assets Due To Information Breach Formulating Cybersecurity Plan. Dispense information and present a thorough explanation of Sales Records, Customers Database, Products Database using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Asset Identification For Information Security Risk Management Formulating Cybersecurity Plan
Asset Identification For Information Security Risk Management Formulating Cybersecurity PlanThis slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help to monitor the asset in real time for any data breach or cyber attack. Deliver an outstanding presentation on the topic using this Asset Identification For Information Security Risk Management Formulating Cybersecurity Plan. Dispense information and present a thorough explanation of Sales Records, Customers Database, Products Database using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Assigning Criticality Rating To Information Assets Formulating Cybersecurity Plan
Assigning Criticality Rating To Information Assets Formulating Cybersecurity PlanThis slide showcases criticality rating that can be allocated to assets for identifying critical assets. Its key elements are asset, failure cost, failure impact and criticality rating. Present the topic in a bit more detail with this Assigning Criticality Rating To Information Assets Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Sales Records, Customers Database, Products Database. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Budget For Information Security Risk Management Formulating Cybersecurity Plan
Budget For Information Security Risk Management Formulating Cybersecurity PlanThis slide showcases budget that can should be allocated for different information security risk management activities. It provides information about employees training, software implementation, risk monitoring and data backup. Deliver an outstanding presentation on the topic using this Budget For Information Security Risk Management Formulating Cybersecurity Plan. Dispense information and present a thorough explanation of Training Of Employees, Software Implementation, Risk Monitoring using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Challenges And Solutions In Information Security Formulating Cybersecurity Plan
Challenges And Solutions In Information Security Formulating Cybersecurity PlanThis slide showcases challenges involved in formulating risk management program for information security. It also shows solutions to tackle the challenges and impact of implementing them. Introducing Challenges And Solutions In Information Security Formulating Cybersecurity Plan to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Fighting Frauds, Internal Vulnerabilities, Employee Awareness, using this template. Grab it now to reap its full benefits.
-
 Checklist For Information Security Risk Management Formulating Cybersecurity Plan
Checklist For Information Security Risk Management Formulating Cybersecurity PlanThis slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status. Present the topic in a bit more detail with this Checklist For Information Security Risk Management Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Identifying Potential, Different Vulnerabilities, Risk Management Plan. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Current Information And Data Security Capabilities Of Firm Formulating Cybersecurity Plan
Current Information And Data Security Capabilities Of Firm Formulating Cybersecurity PlanThis slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating. Deliver an outstanding presentation on the topic using this Current Information And Data Security Capabilities Of Firm Formulating Cybersecurity Plan. Dispense information and present a thorough explanation of Identify, Protect, Detect, Response using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Current Information Security Issues Faced By Organization Formulating Cybersecurity Plan
Current Information Security Issues Faced By Organization Formulating Cybersecurity PlanIntroducing Current Information Security Issues Faced By Organization Formulating Cybersecurity Plan to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Untrained Employees, Frequent Data Breaches, Risk Management Policy, using this template. Grab it now to reap its full benefits.
-
 Cyber Attacks Faced By Different Departments Formulating Cybersecurity Plan
Cyber Attacks Faced By Different Departments Formulating Cybersecurity PlanThis slide showcase information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks. Present the topic in a bit more detail with this Cyber Attacks Faced By Different Departments Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Marketing Department, Operations Department, Accounts Department. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Estimated Impact Of Information Security Risk Management Plan Formulating Cybersecurity Plan
Estimated Impact Of Information Security Risk Management Plan Formulating Cybersecurity PlanThis slide showcases capabilities of organization regarding information and data security after risk management plan. Its key components are risk management functions, required standard rating and actual standard rating. Deliver an outstanding presentation on the topic using this Estimated Impact Of Information Security Risk Management Plan Formulating Cybersecurity Plan. Dispense information and present a thorough explanation of Identify, Protect, Detect, Response using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Financial Impact Of Information Security Attacks Formulating Cybersecurity Plan
Financial Impact Of Information Security Attacks Formulating Cybersecurity PlanThis slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type. Present the topic in a bit more detail with this Financial Impact Of Information Security Attacks Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Financial Impact, Information, Security Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Framework For Information Security Risk Management Formulating Cybersecurity Plan
Framework For Information Security Risk Management Formulating Cybersecurity PlanThis slide showcases framework that can help organization to formulate plan for information security risk management. Its key elements are identify risks, analyze risks, evaluate and treat risks. Deliver an outstanding presentation on the topic using this Framework For Information Security Risk Management Formulating Cybersecurity Plan. Dispense information and present a thorough explanation of Establish The Context, Identify Risks, Analyze Risks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 G14 Table Of Contents Formulating Cybersecurity Plan To Safeguard Information Assets
G14 Table Of Contents Formulating Cybersecurity Plan To Safeguard Information AssetsIntroducing G14 Table Of Contents Formulating Cybersecurity Plan To Safeguard Information Assets to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Process, Risk Management Plan, Formulate Information, using this template. Grab it now to reap its full benefits.
-
 Gap Assessment Of Organization Information Security Formulating Cybersecurity Plan
Gap Assessment Of Organization Information Security Formulating Cybersecurity PlanThis slide showcases gap assessment of information security capabilities of organization. It also provides solutions to tackle the problems faced by company like frequent malware attacks and lack of awareness among employee. Increase audience engagement and knowledge by dispensing information using Gap Assessment Of Organization Information Security Formulating Cybersecurity Plan. This template helps you present information on three stages. You can also present information on Security Programme, Vulnerabilities In Software, Organization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide For Formulating Cybersecurity Plan To Safeguard Information Assets
Icons Slide For Formulating Cybersecurity Plan To Safeguard Information AssetsIntroducing our well researched set of slides titled Icons Slide For Formulating Cybersecurity Plan To Safeguard Information Assets. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Identifying Employees For Information Security Training Formulating Cybersecurity Plan
Identifying Employees For Information Security Training Formulating Cybersecurity PlanThis slide showcases plan that can help organization to conduct training for employees for information security risk management. It will enable employees to monitor risks and resolve them in timely manner. Deliver an outstanding presentation on the topic using this Identifying Employees For Information Security Training Formulating Cybersecurity Plan. Dispense information and present a thorough explanation of Threat Scanning, Report Formulation, Training Programme using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Identifying Information Security Threats And Impact Formulating Cybersecurity Plan
Identifying Information Security Threats And Impact Formulating Cybersecurity PlanThis slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization. Introducing Identifying Information Security Threats And Impact Formulating Cybersecurity Plan to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Errors And Omissions, Fraud And Theft, Employee Sabotage, using this template. Grab it now to reap its full benefits.
-
 Impact Of Information Security Loss On Organization Formulating Cybersecurity Plan
Impact Of Information Security Loss On Organization Formulating Cybersecurity PlanIncrease audience engagement and knowledge by dispensing information using Impact Of Information Security Loss On Organization Formulating Cybersecurity Plan. This template helps you present information on four stages. You can also present information on Financial Loss, Organization, Business Continuity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security And Risk Management User Spending Formulating Cybersecurity Plan
Information Security And Risk Management User Spending Formulating Cybersecurity PlanThis slide showcases expenses done by organization in different segments of information security and risk management. Key segments include application security, cloud security, data security, identify access management, infrastructure protection, integrated risk management, security services etc. Deliver an outstanding presentation on the topic using this Information Security And Risk Management User Spending Formulating Cybersecurity Plan. Dispense information and present a thorough explanation of Application Security, Identity Access Management, Integrated Risk Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Attacks Faced By Organization Formulating Cybersecurity Plan
Information Security Attacks Faced By Organization Formulating Cybersecurity PlanThis slide showcases most common information attacks faced by organization. It includes malware, phishing, man in the middle attack, SQL injection, zero day exploit and DNS attack. Present the topic in a bit more detail with this Information Security Attacks Faced By Organization Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Malware, Phishing, Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 KPIS To Measure Information Security Risk Management Formulating Cybersecurity Plan
KPIS To Measure Information Security Risk Management Formulating Cybersecurity PlanThis slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan. Deliver an outstanding presentation on the topic using this KPIS To Measure Information Security Risk Management Formulating Cybersecurity Plan. Dispense information and present a thorough explanation of Intrusion Attempts, Mean Time Between Failures, Mean Time To Resolve using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Matrix For Threat Solution And Risk Management Formulating Cybersecurity Plan
Matrix For Threat Solution And Risk Management Formulating Cybersecurity PlanThis slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack. Deliver an outstanding presentation on the topic using this Matrix For Threat Solution And Risk Management Formulating Cybersecurity Plan. Dispense information and present a thorough explanation of Block Malicious, Monitor Database Activity, Validate Database Protocols using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Mitigation Plan For Resolving Encountered Threat Formulating Cybersecurity Plan
Mitigation Plan For Resolving Encountered Threat Formulating Cybersecurity PlanMentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. Present the topic in a bit more detail with this Mitigation Plan For Resolving Encountered Threat Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Risk Mitigation Plan, Expected Resolution Time, Mitigation Plan. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Mitigation Strategies To Avoid Information Breach Formulating Cybersecurity Plan
Mitigation Strategies To Avoid Information Breach Formulating Cybersecurity PlanThis slide showcases startegies that can help organization to avoid information breach. Key strategies include impelment antivirus software, monitor network traffic, incident reponse plan, patch management schedule and establish network access controls. Introducing Mitigation Strategies To Avoid Information Breach Formulating Cybersecurity Plan to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Implement Antivirus, Monitor Network Traffic, Incident Response Plan, using this template. Grab it now to reap its full benefits.
-
 Mitigation Strategies To Tackle Information Security Threats Formulating Cybersecurity Plan
Mitigation Strategies To Tackle Information Security Threats Formulating Cybersecurity PlanThis slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help organization to minimize the financial loss and maintain reputation of business. Increase audience engagement and knowledge by dispensing information using Mitigation Strategies To Tackle Information Security Threats Formulating Cybersecurity Plan. This template helps you present information on five stages. You can also present information on Malware, Phishing, Mitigation Strategies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Probability Assessment Matrix For Risk Management Formulating Cybersecurity Plan
Probability Assessment Matrix For Risk Management Formulating Cybersecurity PlanThis slide showcase matrix that can help organization to identify the probability of different information security attacks and formulate mitigation strategy in advance. It can help organization to manage the major risks and safeguard the information. Present the topic in a bit more detail with this Probability Assessment Matrix For Risk Management Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Probability, Assessment Matrix, Risk Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Process For Information Security Risk Assessment Formulating Cybersecurity Plan
Process For Information Security Risk Assessment Formulating Cybersecurity PlanThis slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets. Introducing Process For Information Security Risk Assessment Formulating Cybersecurity Plan to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Identifying Internal, Information Security Threats, Information Assets, using this template. Grab it now to reap its full benefits.
-
 Reporting Structure For Information Security Risk Management Formulating Cybersecurity Plan
Reporting Structure For Information Security Risk Management Formulating Cybersecurity PlanThis slide showcases plan that can help to communicate the major risks report on regular intervals. Its key components are risk, reported by, frequency, likelihood, criticality and impact. Present the topic in a bit more detail with this Reporting Structure For Information Security Risk Management Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Reporting Structure, Information Security, Risk Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Assessment Matrix With Vulnerability And Threat Level Formulating Cybersecurity Plan
Risk Assessment Matrix With Vulnerability And Threat Level Formulating Cybersecurity PlanThis slide showcases assessment matrix to identify risk associated with different class of information assists. It calculates severity of risk on the basis of threat and vulnerability level. Present the topic in a bit more detail with this Risk Assessment Matrix With Vulnerability And Threat Level Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Risk Assessment Matrix, Vulnerability Level. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Roles And Responsibilities In Information Security Formulating Cybersecurity Plan
Roles And Responsibilities In Information Security Formulating Cybersecurity PlanThis slide showcases challenges involved in formulating risk management program for information security. It also shows solutions to tackle the challenges and impact of implementing them. Introducing Roles And Responsibilities In Information Security Formulating Cybersecurity Plan to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Information Security Manager, Risk Management Officer, Chief Information Officer, using this template. Grab it now to reap its full benefits.
-
 Selecting Suitable Software For Information Formulating Cybersecurity Plan
Selecting Suitable Software For Information Formulating Cybersecurity PlanThis slide showcases software that can help organization to monitor and manage the information security. It provides information about Cyber Risk Quantification, vvulnerability management, Ccentralized rrepository for aassets etc. Present the topic in a bit more detail with this Selecting Suitable Software For Information Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Issue Management, Vulnerability Management, Cyber Risk Quantification. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Steps For Information Security Risk Management Formulating Cybersecurity Plan
Steps For Information Security Risk Management Formulating Cybersecurity PlanThis slide showcase steps which can help organization to implement information security risk management program in organization. Its key steps are identify, protect, detect and respond. Deliver an outstanding presentation on the topic using this Steps For Information Security Risk Management Formulating Cybersecurity Plan. Dispense information and present a thorough explanation of Asset Identification, Risk Assessment, Awareness And Training using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents Formulating Cybersecurity Plan To Safeguard Information Assets
Table Of Contents Formulating Cybersecurity Plan To Safeguard Information AssetsIntroducing Table Of Contents Formulating Cybersecurity Plan To Safeguard Information Assets to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Current Scenario Assessment, Security Capabilities, Management Plan, using this template. Grab it now to reap its full benefits.
-
 Threat Identification And Vulnerability Assessment Formulating Cybersecurity Plan
Threat Identification And Vulnerability Assessment Formulating Cybersecurity PlanThis slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. Present the topic in a bit more detail with this Threat Identification And Vulnerability Assessment Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Vulnerability Severity, Threat Source, Likelihood. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Timeline For Information Security Risk Management Training Formulating Cybersecurity Plan
Timeline For Information Security Risk Management Training Formulating Cybersecurity PlanThis slide showcases timeline that can help organization to conduct training for information security risk management programme. It also showcases weekly and step progress. Deliver an outstanding presentation on the topic using this Timeline For Information Security Risk Management Training Formulating Cybersecurity Plan. Dispense information and present a thorough explanation of Cybersecurity Awareness, Malware Detection, Risk Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Vulnerability Rating For Risk Identification Formulating Cybersecurity Plan
Vulnerability Rating For Risk Identification Formulating Cybersecurity PlanThis slide showcases table for allocating vulnerability rating to different class of information assets. It shows information about severity, vulnerability score and description. Introducing Vulnerability Rating For Risk Identification Formulating Cybersecurity Plan to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Vulnerability Score, Risk Identification, using this template. Grab it now to reap its full benefits.
-
 Cybersecurity Dashboard In Powerpoint And Google Slides Cpb
Cybersecurity Dashboard In Powerpoint And Google Slides CpbPresenting our Cybersecurity Dashboard In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Cybersecurity Dashboard. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cybersecurity Risk In Powerpoint And Google Slides Cpb
Cybersecurity Risk In Powerpoint And Google Slides CpbPresenting our Cybersecurity Risk In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Cybersecurity Risk. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cybersecurity Defense Strategy In Powerpoint And Google Slides Cpb
Cybersecurity Defense Strategy In Powerpoint And Google Slides CpbPresenting our Cybersecurity Defense Strategy In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Cybersecurity Defense Strategy. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Addressing The Cyber Incident Logging Process Cybersecurity Incident And Vulnerability
Addressing The Cyber Incident Logging Process Cybersecurity Incident And VulnerabilityThis slide displays logging process for a cyber incident logging. It covers information about process ID, procedure, its description and owner details. Present the topic in a bit more detail with this Addressing The Cyber Incident Logging Process Cybersecurity Incident And Vulnerability. Use it as a tool for discussion and navigation on Create New Incident, Complete Incident Details, Category And Priority. This template is free to edit as deemed fit for your organization. Therefore download it now.





