Powerpoint Templates and Google slides for Cybersecurity
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Solutions To Challenges Associated With Big Data Analytics For Cybersecurity
Solutions To Challenges Associated With Big Data Analytics For CybersecurityThis slide highlights solutions of big data analytics for cybersecurity challenges. This includes challenges such as combining big data from all sources and huge data storage used, real time insights of time taken between data extractions and analysis along with solutions. Presenting our well structured Solutions To Challenges Associated With Big Data Analytics For Cybersecurity. The topics discussed in this slide are Big Data Analytics, Cybersecurity Challenges, Huge Data Storage Used, Real Time Insights. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Transforming Ai And Big Data Analytics With Cybersecurity
Transforming Ai And Big Data Analytics With CybersecurityThis slide showcases big data analytics and AI transformation with cybersecurity. This includes healthcare follow ups, malicious software diagnosis and uproot security factors. Presenting our set of slides with name Transforming Ai And Big Data Analytics With Cybersecurity. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Malicious Software Diagnosis, Uproot Security Factor, Healthcare Follow Ups.
-
 Web Cybersecurity Icon For Big Data Anaytics
Web Cybersecurity Icon For Big Data AnayticsIntroducing our premium set of slides with name Web Cybersecurity Icon For Big Data Anaytics. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Web Cybersecurity Icon, Big Data Analytics. So download instantly and tailor it with your information.
-
 Operation Continuity Plan For Cybersecurity Threats
Operation Continuity Plan For Cybersecurity ThreatsThis slide represents an operation continuity plan for businesses including cybersecurity threats such as injections, broken authentication, and cross-site scripting. Presenting our well structured Operation Continuity Plan For Cybersecurity Threats. The topics discussed in this slide are Supervisors, Broken Authentication, Cross-Site Scripting. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cybersecurity Tips While Using Open AI ChatGPT Impact Of Generative AI SS V
Cybersecurity Tips While Using Open AI ChatGPT Impact Of Generative AI SS VThis slide showcases various cybersecurity tips that can be used while using ChatGPT for generating responses. Its key elements are avoid inserting sensitive data, awareness of potential bias and beware of fake applications. Increase audience engagement and knowledge by dispensing information using Cybersecurity Tips While Using Open AI ChatGPT Impact Of Generative AI SS V. This template helps you present information on three stages. You can also present information on Avoid Inserting, Awareness Of Potential Bias, Fake Applications using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How ChatGPT Can Help In Cybersecurity Penetration Testing Impact Of Generative AI SS V
How ChatGPT Can Help In Cybersecurity Penetration Testing Impact Of Generative AI SS VThis slide showcases various ChatGPT use cases for penetration testing which can help to prevent cyber attacks in organization. Its key elements are establish penetration testing environment, gain knowledge about testing tools, writing code for testing etc. Introducing How ChatGPT Can Help In Cybersecurity Penetration Testing Impact Of Generative AI SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Establish Penetration, Testing Tools, Testing Activities, using this template. Grab it now to reap its full benefits.
-
 Icons Slide Impact Of Generative AI On Organizational Cybersecurity AI SS V
Icons Slide Impact Of Generative AI On Organizational Cybersecurity AI SS VIntroducing our well researched set of slides titled Icons Slide Impact Of Generative AI On Organizational Cybersecurity AI SS V. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Impact Of Generative AI On Organizational Cybersecurity Table Of Content AI SS V
Impact Of Generative AI On Organizational Cybersecurity Table Of Content AI SS VIncrease audience engagement and knowledge by dispensing information using Impact Of Generative AI On Organizational Cybersecurity Table Of Content AI SS V. This template helps you present information on one stages. You can also present information on Applications In Cybersecurity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key Statistics Highlighting Importance Of Cybersecurity Impact Of Generative AI SS V
Key Statistics Highlighting Importance Of Cybersecurity Impact Of Generative AI SS VThis slide showcases various statistics that highlights the importance of cybersecurity in organization. It highlights stats related to malware attacks, DDos attacks, cybersecurity spending, ransomware attacks, malicious mining software etc. Introducing Key Statistics Highlighting Importance Of Cybersecurity Impact Of Generative AI SS V to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Mining Software, Reported Ransomware, Faced Per Day, using this template. Grab it now to reap its full benefits.
-
 Openai ChatGPT Usage In Organization Cybersecurity Impact Of Generative AI SS V
Openai ChatGPT Usage In Organization Cybersecurity Impact Of Generative AI SS VThis slide showcases various use cases of ChatGPT for cybersecurity in organization. Various use cases are incident management, penetration testing, security operations, threat intelligence, vulnerability assessment and security training. Introducing Openai ChatGPT Usage In Organization Cybersecurity Impact Of Generative AI SS V to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Incident Management, Threat Intelligence, Vulnerability Assessment, using this template. Grab it now to reap its full benefits.
-
 Overview And Cybersecurity Importance For Organization Impact Of Generative AI SS V
Overview And Cybersecurity Importance For Organization Impact Of Generative AI SS VThis slide showcases cybersecurity overview that can help organization to safeguard data from different types of cyber attacks. It also highlights various benefits of cybersecurity such as safeguard data, timely incident response, reduce monetary damage etc. Increase audience engagement and knowledge by dispensing information using Overview And Cybersecurity Importance For Organization Impact Of Generative AI SS V. This template helps you present information on two stages. You can also present information on Overview Of Cybersecurity, Importance Of Cybersecurity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview And Importance Of Cybersecurity Incident Management Impact Of Generative AI SS V
Overview And Importance Of Cybersecurity Incident Management Impact Of Generative AI SS VThis slide showcases overview of incident management that can help organization in tackling cyber attacks. It also highlights various importance of incident management that are reduction in cyber attacks, decrease in system downtime, improved incident response etc. Introducing Overview And Importance Of Cybersecurity Incident Management Impact Of Generative AI SS V to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Incident Management, Practices Of Incident Management, using this template. Grab it now to reap its full benefits.
-
 Potential ChatGPT Impact On Cybersecurity Functions Impact Of Generative AI SS V
Potential ChatGPT Impact On Cybersecurity Functions Impact Of Generative AI SS VThis slide showcases potential impact of ChatGPT on cybersecurity functions of organization in future. Various impacts are improved threat detection, enhanced incident response, automated security operations and threat intelligence. Increase audience engagement and knowledge by dispensing information using Potential ChatGPT Impact On Cybersecurity Functions Impact Of Generative AI SS V. This template helps you present information on four stages. You can also present information on Improved Threat Detection, Enhanced Incident Response, Automated Security Operations using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Potential Impact Of ChatGPT On Cybersecurity Jobs Impact Of Generative AI SS V
Potential Impact Of ChatGPT On Cybersecurity Jobs Impact Of Generative AI SS VThis slide showcases potential impact of ChatGPT on cybersecurity jobs in future. Its key elements are demand for specialized roles, evolving skill requirements, human machine collaboration and automation of routine tasks. Introducing Potential Impact Of ChatGPT On Cybersecurity Jobs Impact Of Generative AI SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Specialized Roles, Evolving Skill Requirements, Human Machine Collaboration, using this template. Grab it now to reap its full benefits.
-
 Table Of Content Impact Of Generative AI On Organizational Cybersecurity AI SS V
Table Of Content Impact Of Generative AI On Organizational Cybersecurity AI SS VIncrease audience engagement and knowledge by dispensing information using Table Of Content Impact Of Generative AI On Organizational Cybersecurity AI SS V. This template helps you present information on five stages. You can also present information on Cybersecurity, Applications In Cybersecurity, Poses To Cybersecurity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Use Cases Of Artificial Intelligence In Cybersecurity Impact Of Generative AI SS V
Use Cases Of Artificial Intelligence In Cybersecurity Impact Of Generative AI SS VThis slide showcases various use cases of Artificial intelligence in cybersecurity operations of organization. Its key elements are threat reporting, guided investigation writing detection rules, threat hunting, threat modelling etc. Present the topic in a bit more detail with this Use Cases Of Artificial Intelligence In Cybersecurity Impact Of Generative AI SS V. Use it as a tool for discussion and navigation on Task Automation, Reactive. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Current Trends In Cybersecurity Management Program
Current Trends In Cybersecurity Management ProgramFollowing slide showcases cybersecurity management program current trends for business continuity. It further covers trends such as responsive ecosystem, restructuring approaches, and rebalancing practices etc. Introducing our premium set of slides with Current Trends In Cybersecurity Management Program. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Responsive Ecosystem, Restructuring Approaches, Rebalancing Practice. So download instantly and tailor it with your information.
-
 Effective Cybersecurity Program Management Framework
Effective Cybersecurity Program Management FrameworkFollowing slide showcases cybersecurity program management with customized methodology for early threat detection. It further covers directions, experience, culture and technology such as strategic roadmap, data driven innovation, defined audience, etc. Introducing our Effective Cybersecurity Program Management Framework set of slides. The topics discussed in these slides are Scalable Architecture, Integrated Systems, Data Driven Innovation. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Effective Cybersecurity Risk Management Process Flow
Effective Cybersecurity Risk Management Process FlowFollowing slide highlights process flow of cyber security risk management for enhanced efficiency. It further covers data sources, cyber security communities, private organizations, government organizations, continuous monitoring and threat modelling, etc. Presenting our well structured Effective Cybersecurity Risk Management Process Flow. The topics discussed in this slide are Cyber Security Communities, Private Organizations, Governative Organization. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Employee Training Program Focusing On Cybersecurity Management
Employee Training Program Focusing On Cybersecurity ManagementFollowing slide showcases cybersecurity management training plan for employees to provide them with essential knowledge and skills. It further covers training topics, date, durations, responsible person, mode, etc. Introducing our Employee Training Program Focusing On Cybersecurity Management set of slides. The topics discussed in these slides are Introduction To Cyber Security, Managing Network Security Management, Cyber Security Risk Management. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Key Strategies For Cybersecurity Risk Management
Key Strategies For Cybersecurity Risk ManagementFollowing slide highlights various risk management strategies to boost cyber security and sensitive data protection. It further covers capability assessments, program design, strategy, risk management, compliance, etc. Introducing our premium set of slides with Key Strategies For Cybersecurity Risk Management. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Third Party Risk Management, Capability Assessments, Risk Management. So download instantly and tailor it with your information.
-
 Cybersecurity Automation Tools To Enhance Data Protection
Cybersecurity Automation Tools To Enhance Data ProtectionThis slide represents various cybersecurity automation tools that help companies to enhance data protection from threats and vulnerabilities. It includes various tools such as sprint, quals, splunk, logpoint, etc. Introducing our premium set of slides with Cybersecurity Automation Tools To Enhance Data Protection Ellicudate the seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Features, Cybersecurity Automation, Data Protection So download instantly and tailor it with your information.
-
 4 Threats To Cybersecurity In Automobile Industry
4 Threats To Cybersecurity In Automobile IndustryThis slide highlights cyber safety concerns in automotive sector. The purpose of this slide is to provide businesses with the required knowledge regarding various malware attacks in vehicles. It includes elements such as software, unauthorized access, etc. Presenting our set of slides with 4 Threats To Cybersecurity In Automobile Industry This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Unauthorized Access, Supply Chain, Software
-
 Core Responsibilities Of Cybersecurity Engineer In Automotive Sector
Core Responsibilities Of Cybersecurity Engineer In Automotive SectorThis slide highlights cyber security obligations of technicians in?retail sector. The purpose of this slide is to help businesses in managing security protocols by implementing preventive measures for maintaining integrity of systems. It includes elements such as threat analysis, awareness training, etc. Introducing our premium set of slides with Core Responsibilities Of Cybersecurity Engineer In Automotive Sector Ellicudate the seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Vehicle Security Assessment, Threat Analysis, Awareness Training So download instantly and tailor it with your information.
-
 Risk Assessment And Mitigation In Automotive Cybersecurity
Risk Assessment And Mitigation In Automotive CybersecurityThis slide highlights risk evaluation and minimization strategies in automotive cybersecurity. The purpose of this slide is to aid businesses in identifying vulnerabilities associated with cybersecurity of systems. It includes elements such as malware, human factors, etc. Introducing our Risk Assessment And Mitigation In Automotive Cybersecurity set of slides. The topics discussed in these slides are Unauthorized Access, Supply Chain Security, Incident Response This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cybersecurity Strategies For It Business Development
Cybersecurity Strategies For It Business DevelopmentThe purpose of this slide is to showcase cyber security development strategies like assurance framework and to encourage open standards, which helps bolster overall business resilience. Presenting our well structured Cybersecurity Strategies For It Business Development The topics discussed in this slide are Assurance Framework, Secure Cyber Ecosystem, Business Development This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Agenda Encryption For Data Security Cybersecurity SS
Agenda Encryption For Data Security Cybersecurity SSIntroducing Agenda Encryption For Data Security Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on General Overview, Concepts And Global Significance, Key Management, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data AES Algorithm Deployment For Data Encryption Cybersecurity SS
Encryption For Data AES Algorithm Deployment For Data Encryption Cybersecurity SSThis slide showcases advanced encryption standard AES algorithm deployment which can help employees learn basic techniques for data encryption. It provides details about AES engine, wireless communication, etc. Present the topic in a bit more detail with this Encryption For Data AES Algorithm Deployment For Data Encryption Cybersecurity SS. Use it as a tool for discussion and navigation on Controller, Organization, Potential Benefits. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Annual IT Budget Focused On Encryption Costs Cybersecurity SS
Encryption For Data Annual IT Budget Focused On Encryption Costs Cybersecurity SSThis slide showcases encryption costs under an annual information technology budget, helping companies adjust their expenses. It provides details about software, hardware, training, license, etc. Present the topic in a bit more detail with this Encryption For Data Annual IT Budget Focused On Encryption Costs Cybersecurity SS. Use it as a tool for discussion and navigation on Encryption Software, Hardware Infrastructure, Training Programs, Software Updates. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Caesar Algorithm Implementation For Basic Encryption Cybersecurity SS
Encryption For Data Caesar Algorithm Implementation For Basic Encryption Cybersecurity SSThis slide showcases caesar algorithm deployment which can help employees learn basic techniques for basic encryption. It provides details about shift, displacement, shift value, decryption, etc. Introducing Encryption For Data Caesar Algorithm Implementation For Basic Encryption Cybersecurity SS to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Pre-Implementation Stage, Implementation Steps, Potential Benefit, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Choose Right Data Encryption Solution Cybersecurity SS
Encryption For Data Choose Right Data Encryption Solution Cybersecurity SSThis slide showcases encryption best practice focused on ensuring right selection of tools and solutions. It provides details about database, application, on-premises, cloud, automated lifecycle, etc. Present the topic in a bit more detail with this Encryption For Data Choose Right Data Encryption Solution Cybersecurity SS. Use it as a tool for discussion and navigation on Encryption At Multiple Levels, Centralized Management Dashboard, Data Encryption. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Classify Data For Organizational Encryption Solution Cybersecurity SS
Encryption For Data Classify Data For Organizational Encryption Solution Cybersecurity SSThis slide showcases encryption best practice focused on classifying organizational data. It provides details about sensitivity checks, regulations, clerical errors, etc. Introducing Encryption For Data Classify Data For Organizational Encryption Solution Cybersecurity SS to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Financial Data, Customer Details, Business, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Comparative Assessment Of Top Encryption Tools Cybersecurity SS
Encryption For Data Comparative Assessment Of Top Encryption Tools Cybersecurity SSThis slide showcases comparative analysis of major encryption software, helping companies choose according to their needs. It provides details about platform, integration, cost, user experience, etc. Present the topic in a bit more detail with this Encryption For Data Comparative Assessment Of Top Encryption Tools Cybersecurity SS. Use it as a tool for discussion and navigation on Encryption Type, Platform, Integration, User Experience. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Define Security Requirements For Encryption Strategy Cybersecurity SS
Encryption For Data Define Security Requirements For Encryption Strategy Cybersecurity SSThis slide showcases encryption best practice focused on defining security requirements. It provides details about threat assessment, system vulnerabilities, business decisions, etc. Introducing Encryption For Data Define Security Requirements For Encryption Strategy Cybersecurity SS to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Conduct Threat Assessment, Learn Of Any Business Decisions, System Vulnerabilities, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Encryption Awareness Training Implementation Plan Cybersecurity SS
Encryption For Data Encryption Awareness Training Implementation Plan Cybersecurity SSThis slide showcases training plan focused on building key encryption skills amongst organizations employees. It provides details about retention of training, backdoor access, internet society, etc. Introducing Encryption For Data Encryption Awareness Training Implementation Plan Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Existing Training Scenario, Details, Modules, Training Initiatives, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Encryption Key Management Best Practices Cybersecurity SS
Encryption For Data Encryption Key Management Best Practices Cybersecurity SSThis slide showcases encryption key management best practices which can help companies increase security. It provides details about secure key stores, access, backup, recovery, etc. Present the topic in a bit more detail with this Encryption For Data Encryption Key Management Best Practices Cybersecurity SS. Use it as a tool for discussion and navigation on Secure Key Stores, Access To Key Stores, Key Backup And Recoverability. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Financial Impact Of Poor Encryption Practices Cybersecurity SS
Encryption For Data Financial Impact Of Poor Encryption Practices Cybersecurity SSThis slide showcases financial impact of poor practices relating to encryption. Its purpose is to make businesses aware of major and potential vulnerabilities. It provides information about data breach, downtime, lost business, wages, etc. Present the topic in a bit more detail with this Encryption For Data Financial Impact Of Poor Encryption Practices Cybersecurity SS. Use it as a tool for discussion and navigation on Data Breach, Lost Business, Idle Employees And Wages, Regulatory Fines. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Homomorphic Cryptography For Data Base Security Cybersecurity SS
Encryption For Data Homomorphic Cryptography For Data Base Security Cybersecurity SSThis slide showcases homomorphic cryptography deployment which can help employees increase data privacy and outsourcing security. It provides details about private key, plaintext, decryption, etc. Introducing Encryption For Data Homomorphic Cryptography For Data Base Security Cybersecurity SS to increase your presentation threshold. Encompassed with Eight stages, this template is a great option to educate and entice your audience. Dispence information on Homomorphic Encryption, Classified Plaintext, Decrypted Results, Data Owner Organization, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Implementing Encryption Gap Analysis For Organization Cybersecurity SS
Encryption For Data Implementing Encryption Gap Analysis For Organization Cybersecurity SSThis slide showcases gap analysis relating to encryption running in the organization. Its purpose is to make businesses aware of major and potential vulnerabilities. It provides information about sensitive data, employee awareness, key management, etc. Introducing Encryption For Data Implementing Encryption Gap Analysis For Organization Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Current State, Desired State, Action Items, Priority, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Importance Of Encryption In Todays Business Cybersecurity SS
Encryption For Data Importance Of Encryption In Todays Business Cybersecurity SSThis slide showcases significant role of encryption technology, focused on improving data privacy. It provides details about data integrity, cost savings, backup authentication, customer trust, etc. Introducing Encryption For Data Importance Of Encryption In Todays Business Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Protects Data Integrity, Saves Costs, Authenticates Backups, Increases Customer Trust, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Introduction To Cybersecurity Awareness Cybersecurity SS
Encryption For Data Introduction To Cybersecurity Awareness Cybersecurity SSIntroducing Encryption For Data Introduction To Cybersecurity Awareness Cybersecurity SS to increase your presentation threshold. Encompassed with One stages, this template is a great option to educate and entice your audience. Dispence information on General Overview, Business, Data Security, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Key Management Algorithms And Dedicated Protocols Cybersecurity SS
Encryption For Data Key Management Algorithms And Dedicated Protocols Cybersecurity SSThis slide showcases key management protocols which can help companies increase efficiency and generation time. It provides details about hash functions, authentication, symmetric, etc. Introducing Encryption For Data Key Management Algorithms And Dedicated Protocols Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Cryptographic Hash Functions, Symmetric-Key Algorithms, Asymmetric-Key Algorithms, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Key Management And Strength Improvement Techniques Cybersecurity SS
Encryption For Data Key Management And Strength Improvement Techniques Cybersecurity SSThis slide showcases key management and strength improvement techniques which can help companies increase security. It provides details about elliptic, organization strategy, data exposure, etc. Introducing Encryption For Data Key Management And Strength Improvement Techniques Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Establishing Key Strength, Encrypting Keys Securely, Elliptic Curve Algorithms, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Multi Staged Process Of Encryption Technology Cybersecurity SS
Encryption For Data Multi Staged Process Of Encryption Technology Cybersecurity SSThis slide showcases general overview of encryption technology process, focused on improving data privacy. It provides details about plaintext, ciphertext, decryption, etc. Introducing Encryption For Data Multi Staged Process Of Encryption Technology Cybersecurity SS to increase your presentation threshold. Encompassed with Eight stages, this template is a great option to educate and entice your audience. Dispence information on Plaintext Becomes Ciphertext, Encryption Keys And Algorithms Used, Ciphertext Sent Though Insecure Channels, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data One Time Pad OTP Encryption Method Cybersecurity SS
Encryption For Data One Time Pad OTP Encryption Method Cybersecurity SSThis slide showcases one time pad OTP encryption deployment which can help employees secure their communication protocols. It provides details about plaintext, ciphertext, binary, exclusive OR XOR , etc. Introducing Encryption For Data One Time Pad OTP Encryption Method Cybersecurity SS to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Encryption Process, Decryption Process, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Organizational Chart Of Cyber Security Department Cybersecurity SS
Encryption For Data Organizational Chart Of Cyber Security Department Cybersecurity SSThis slide showcases hierarchy chart focused on building cybersecurity teams to help improve business data encryption. It provides details about DevOps, CISO, encryption specialist, engineer, etc. Present the topic in a bit more detail with this Encryption For Data Organizational Chart Of Cyber Security Department Cybersecurity SS. Use it as a tool for discussion and navigation on Organizational Chart, Cyber Security Department. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Password Encryption Strategy For Maximum Security Cybersecurity SS
Encryption For Data Password Encryption Strategy For Maximum Security Cybersecurity SSThis slide showcases password encryption policies which can help organizations achieve maximum data security. It provides details about salting, SHA-2, Bcrypt, passcode age, auto-lock, etc. Present the topic in a bit more detail with this Encryption For Data Password Encryption Strategy For Maximum Security Cybersecurity SS. Use it as a tool for discussion and navigation on Require Alphanumeric Value, Maximum Passcode Age, Grace Period For Device Lock. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
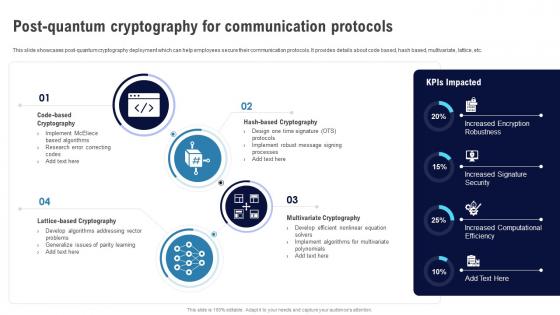 Encryption For Data Post Quantum Cryptography For Communication Protocols Cybersecurity SS
Encryption For Data Post Quantum Cryptography For Communication Protocols Cybersecurity SSThis slide showcases post-quantum cryptography deployment which can help employees secure their communication protocols. It provides details about code based, hash based, multivariate, lattice, etc. Introducing Encryption For Data Post Quantum Cryptography For Communication Protocols Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Code-Based Cryptography, Lattice-Based Cryptography, Hash-Based Cryptography, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Public Key Cryptography For Secure Access Cybersecurity SS
Encryption For Data Public Key Cryptography For Secure Access Cybersecurity SSThis slide showcases public key cryptography deployment which can help employees increased speed and user experience of their platforms. It provides details about private key, key generation, decryption, etc. Present the topic in a bit more detail with this Encryption For Data Public Key Cryptography For Secure Access Cybersecurity SS. Use it as a tool for discussion and navigation on Potential Impact, Increased Speed, Improved User Experience. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption For Data Roles And Responsibilities Of Cyber Security Department Cybersecurity SS
Encryption For Data Roles And Responsibilities Of Cyber Security Department Cybersecurity SSThis slide showcases roles and responsibilities of cybersecurity teams which can help improve business data encryption. It provides details about CTO, key management, encryption specialist and engineer, etc. Introducing Encryption For Data Roles And Responsibilities Of Cyber Security Department Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Key Management, Encryption Engineer, Chief Technology Officer, Encryption Specialist, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Security Defense Arsenal For Data Encryption Cybersecurity SS
Encryption For Data Security Defense Arsenal For Data Encryption Cybersecurity SSThis slide showcases encryption best practice focused on implementing security defense arsenal for data protection. It provides details about firewall, antimalware, authentication, encryption, etc. Introducing Encryption For Data Security Defense Arsenal For Data Encryption Cybersecurity SS to increase your presentation threshold. Encompassed with Seven stages, this template is a great option to educate and entice your audience. Dispence information on Firewall, Anti Malware, Authentication, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data Timeline For Implementing Encryption Best Practices Cybersecurity SS
Encryption For Data Timeline For Implementing Encryption Best Practices Cybersecurity SSThis slide showcases timeline of encryption to be implemented in the organization. Its purpose is to make businesses ready for future plans of cyber security. It provides information about foundation, rollout, secure communication, etc. Introducing Encryption For Data Timeline For Implementing Encryption Best Practices Cybersecurity SS to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Foundation And Training, Asymmetric Encryption Rollout, Additional Security Measures, using this template. Grab it now to reap its full benefits.
-
 Encryption For Data What Is Encryption General Overview Cybersecurity SS
Encryption For Data What Is Encryption General Overview Cybersecurity SSThis slide showcases general overview of encryption technology which acts as a cornerstone of data privacy. It provides details about plaintext, ciphertext, data privacy, integrity, compliance issues, etc. Introducing Encryption For Data What Is Encryption General Overview Cybersecurity SS to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Benefits, Overview, Increase Consumer Trust, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents Encryption For Data Security Cybersecurity SS
Table Of Contents Encryption For Data Security Cybersecurity SSIntroducing Table Of Contents Encryption For Data Security Cybersecurity SS to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Cybersecurity Team For Encryption, Encryption Costs Analysis, Pre Implementation Best Practices, using this template. Grab it now to reap its full benefits.
-
 Comprehensive Training Program For Cybersecurity Deception Strategies
Comprehensive Training Program For Cybersecurity Deception StrategiesThe purpose of this slide is to present a training program that enables personnel to upskill to identify and respond to cyber threats effectively by attending the cyber deception detection workshop. Presenting our set of slides with Comprehensive Training Program For Cybersecurity Deception Strategies. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Existing Training Scenario, Schedule, Training Items.
-
 Cybersecurity Solution Development Project Description
Cybersecurity Solution Development Project DescriptionThis slide shows a template that can be used by organizations to represent the summary of a cybersecurity development project for packet sniffing. It includes multiple elements such as project duration, team, infrastructure requirements, etc. Introducing our premium set of slides with Cybersecurity Solution Development Project Description Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Additional Stakeholders, Description Template So download instantly and tailor it with your information.
-
 NIST Cybersecurity Maturity Framework To Evaluate Risk Management
NIST Cybersecurity Maturity Framework To Evaluate Risk ManagementThis slide represents the NIST cybersecurity maturity scale assisting companies to monitor and enhance their risk management plan. ITincludes various levels such as initial level, repeatable level, defined level, managed level, etc. Presenting our well structured NIST Cybersecurity Maturity Framework To Evaluate Risk Management The topics discussed in this slide are Protect, Detect, RepeatableThis is an instantly available PowerPoint presentation that can be edited conveniently. Download ITright away and captivate your audience.
-
 Benefits Of Using Blockchain Technology In Cybersecurity
Benefits Of Using Blockchain Technology In CybersecurityThis slide discusses the benefits of using blockchain technology in cybersecurity which include ensures user confidentiality, data transparency, etc. Presenting our set of slides with Benefits Of Using Blockchain Technology In Cybersecurity. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Ensures User Confidentiality, Safe Data Transfers, Data Transparency Traceability.
-
 Best Practices Of Cybersecurity Policy For Businesses
Best Practices Of Cybersecurity Policy For BusinessesThis slide showcases the effective approaches of cybersecurity policy for businesses which helps them to ensure compliance regulation and provide efficient employee training. It include details such as understand cybersecurity importance, analyze threats and risks, etc. Presenting our set of slides with Best Practices Of Cybersecurity Policy For Businesses This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cybersecurity Importance Analyze Threats And Risks, Establish Realistic Goals
-
 Comparative Analysis Of Cybersecurity Policies Used By Multiple Companies
Comparative Analysis Of Cybersecurity Policies Used By Multiple CompaniesThis slide showcases the comparison between cybersecurity policies applied by different organizations which help them to protect personal and company data and enhance productivity. It include details such as developmental reasons, priority in government, cyber force, etc. Introducing our Comparative Analysis Of Cybersecurity Policies Used By Multiple Companies set of slides. The topics discussed in these slides are Infrastructure Security, Major InfrastructureThis is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.





