Powerpoint Templates and Google slides for Cybersecurity
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Mdr Framework To Optimize Business Cybersecurity
Mdr Framework To Optimize Business CybersecurityThis slide represents framework that assists IT companies in understanding workflow of MDR solutions to enhance their data cybersecurity and risk management. It includes various components such as data lake, SIEM, SOAR, playbooks, ITSM, etc. Presenting our well structured Mdr Framework To Optimize Business Cybersecurity. The topics discussed in this slide are Business, Cybersecurity, Framework. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Mdr Icon To Enhance Cybersecurity For Information Protection
Mdr Icon To Enhance Cybersecurity For Information ProtectionIntroducing our Mdr Icon To Enhance Cybersecurity For Information Protection set of slides. The topics discussed in these slides are Cybersecurity, Information, Protection. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Rationales Of Implementing Mdr Cybersecurity In Smbs
Rationales Of Implementing Mdr Cybersecurity In SmbsThis slide represents various rationales of MDR cybersecurity that assist small and medium-sized businesses to enhance their data protection effectively. It includes rationales such as incident investigation, alert triage, remediation, etc. Presenting our set of slides with Rationales Of Implementing Mdr Cybersecurity In Smbs. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Incident Investigation, Remediation, Proactive Threat Hunting.
-
 Trends In Mdr Cybersecurity For Optimizing Threat Intelligence
Trends In Mdr Cybersecurity For Optimizing Threat IntelligenceThis slide represents various trends in MDR cybersecurity that assist companies to enhance their data protection against online threats. It includes trends such as Multi-cloud MDR, Digital risk protection services, and API security monitoring. Introducing our Trends In Mdr Cybersecurity For Optimizing Threat Intelligence set of slides. The topics discussed in these slides are Intelligence, Cybersecurity, Digital Risk Protection Services. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Use Cases Of Mdr For Enhancing Cybersecurity In Businesses
Use Cases Of Mdr For Enhancing Cybersecurity In BusinessesThis slide represents various use cases of MDR that assist companies to mitigate various cybersecurity attacks enhancing data and system protection. It includes various use cases such as network attack detection, cloud attack detection, etc. Presenting our well structured Use Cases Of Mdr For Enhancing Cybersecurity In Businesses. The topics discussed in this slide are Network Attack Detection, Cloud Attack Detection, Ransomware Malware Infections. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Agenda For Mobile Device Security For Data Protection Cybersecurity SS
Agenda For Mobile Device Security For Data Protection Cybersecurity SSIntroducing Agenda For Mobile Device Security For Data Protection Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Agenda using this template. Grab it now to reap its full benefits.
-
 Best Practices To Ensure Mobile Application Security Mobile Device Security Cybersecurity SS
Best Practices To Ensure Mobile Application Security Mobile Device Security Cybersecurity SSThis slide showcases best practices that can help to improve mobile application security. Its key elements are data encryption, security containers and secure KPIs Increase audience engagement and knowledge by dispensing information using Best Practices To Ensure Mobile Application Security Mobile Device Security Cybersecurity SS This template helps you present information on Three stages. You can also present information on Data Encryption, Secure Apis, Security Containers using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Budget Distribution For Mobile Security Implementation Mobile Device Security Cybersecurity SS
Budget Distribution For Mobile Security Implementation Mobile Device Security Cybersecurity SSThis slide showcases budget distribution that can help to implement mobile security solutions. Its key elements are biometric solution, virtual private network, employee training, data encryption etc. Introducing Budget Distribution For Mobile Security Implementation Mobile Device Security Cybersecurity SS to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Biometric Solution, Virtual Private Network, Employee Training using this template. Grab it now to reap its full benefits.
-
 Case Study 1 Mobile Application Security Mobile Device Security Cybersecurity SS
Case Study 1 Mobile Application Security Mobile Device Security Cybersecurity SSThis slide showcases case study regarding implementation of mobile application security solutions. Its key elements are objectives, challenges, solutions and impact Increase audience engagement and knowledge by dispensing information using Case Study 1 Mobile Application Security Mobile Device Security Cybersecurity SS This template helps you present information on Three stages. You can also present information on Enhanced Mobile Security, Objectives, Solution Implemented using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Case Study 2 Mobile Ransomware Solution Mobile Device Security Cybersecurity SS
Case Study 2 Mobile Ransomware Solution Mobile Device Security Cybersecurity SSThis slide showcases case study regarding implementation of mobile ransomware solutions. Its key elements are challenges, solutions and impact Introducing Case Study 2 Mobile Ransomware Solution Mobile Device Security Cybersecurity SS to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Challenges Faced, Solutions Implemented using this template. Grab it now to reap its full benefits.
-
 Checklist To Ensure Mobile Application Security Mobile Device Security Cybersecurity SS
Checklist To Ensure Mobile Application Security Mobile Device Security Cybersecurity SSThis slide showcases checklist that can help to improve mobile application security. It can help to safeguard data in organization and protect confidential information. Present the topic in a bit more detail with this Checklist To Ensure Mobile Application Security Mobile Device Security Cybersecurity SS Use it as a tool for discussion and navigation on Update Devices In Organization, Conduct Security Training For Users This template is free to edit as deemed fit for your organization. Therefore download it now.
-
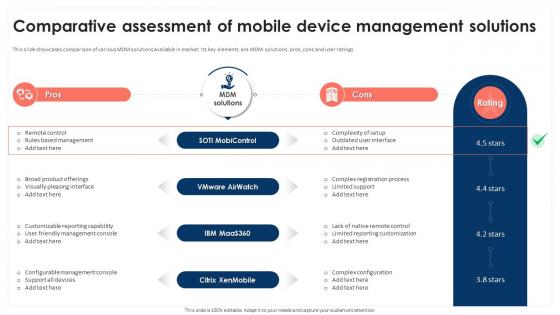 Comparative Assessment Of Mobile Device Management Solutions Mobile Device Security Cybersecurity SS
Comparative Assessment Of Mobile Device Management Solutions Mobile Device Security Cybersecurity SSThis slide showcases comparison of various MDM solutions available in market. Its key elements are MDM solutions, pros, cons and user ratings Increase audience engagement and knowledge by dispensing information using Comparative Assessment Of Mobile Device Management Solutions Mobile Device Security Cybersecurity SS This template helps you present information on Two stages. You can also present information on SOTI Mobicontrol, Vmware Airwatch, Citrix Xenmobile using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Factors To Consider Before Purchasing Mobile Device Management Mobile Device Security Cybersecurity SS
Factors To Consider Before Purchasing Mobile Device Management Mobile Device Security Cybersecurity SSThis slide showcases factors to be considered before buying MDM solutions. Its key elements are supported operating systems, budget and feature requirements Introducing Factors To Consider Before Purchasing Mobile Device Management Mobile Device Security Cybersecurity SS to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Biometrics, Mobile VPN, Encryption using this template. Grab it now to reap its full benefits.
-
 Global Mobile Security Threats Statistics Mobile Device Security Cybersecurity SS
Global Mobile Security Threats Statistics Mobile Device Security Cybersecurity SSThis side showcases statistics about global mobile threat and security. It highlights stats related to zero-day vulnerabilities, new malwares detected, phishing emails etc. Increase audience engagement and knowledge by dispensing information using Global Mobile Security Threats Statistics Mobile Device Security Cybersecurity SS This template helps you present information on Five stages. You can also present information on Mobile Devices, Malware Attack, SamplesWere Detected using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How Different Biometric Technique Can Enhance Mobile Device Security Cybersecurity SS
How Different Biometric Technique Can Enhance Mobile Device Security Cybersecurity SSThis slide showcases use cases of different biometric techniques for enhancing mobile security. Biometric techniques used are fingerprint scanner, facial recognition, voice recognition etc. Introducing How Different Biometric Technique Can Enhance Mobile Device Security Cybersecurity SS to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Company Financial Loss, Operational Disruption using this template. Grab it now to reap its full benefits.
-
 How Mobile Vpn Help In Organization Security Mobile Device Security Cybersecurity SS
How Mobile Vpn Help In Organization Security Mobile Device Security Cybersecurity SSThis slides showcases various use cases of VPN in enhancing mobile security. Its key components are encrypted communication, secure remote access, data privacy etc. Increase audience engagement and knowledge by dispensing information using How Mobile Vpn Help In Organization Security Mobile Device Security Cybersecurity SS This template helps you present information on Three stages. You can also present information on Company Data Loss, Data Breaches, Unauthorized Access using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide For Mobile Device Security For Data Protection Cybersecurity SS
Icons Slide For Mobile Device Security For Data Protection Cybersecurity SSIntroducing our well researched set of slides titled Icons Slide For Mobile Device Security For Data Protection Cybersecurity SS It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Kpis To Track Mobile Security Management Plan Mobile Device Security Cybersecurity SS
Kpis To Track Mobile Security Management Plan Mobile Device Security Cybersecurity SSThis slide showcases metrics that can help to track the effectiveness of mobile security management plan. Various KPIs are mobile threat detection rate, incident response time etc. Deliver an outstanding presentation on the topic using this Kpis To Track Mobile Security Management Plan Mobile Device Security Cybersecurity SS Dispense information and present a thorough explanation of Phase, Key Tasks, Estimated Duration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Mobile Application Security Techniques Mobile Device Security Cybersecurity SS
Mobile Application Security Techniques Mobile Device Security Cybersecurity SSThis slide showcases plan that can help to implement mobile device application techniques. Its key elements are risk assessment, security policies, Wi-Fi configurations etc. Introducing Mobile Application Security Techniques Mobile Device Security Cybersecurity SS to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Global Mobile Cyber Attacks, Telegram And Twitter using this template. Grab it now to reap its full benefits.
-
 Mobile Device Encryption Plan For Data Security Mobile Device Security Cybersecurity SS
Mobile Device Encryption Plan For Data Security Mobile Device Security Cybersecurity SSThis slide showcases data encryption plan that can help to enhance mobile security. Its key elements are target devices, employees, encryption technique used, software used, authentication method etc. Introducing Mobile Device Encryption Plan For Data Security Mobile Device Security Cybersecurity SS to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Encrypted Communication, Secure Remote Access, Data Privacy using this template. Grab it now to reap its full benefits.
-
 Mobile Device Encryption Policy To Safeguard Data Mobile Device Security Cybersecurity SS
Mobile Device Encryption Policy To Safeguard Data Mobile Device Security Cybersecurity SSThis slide showcases mobile encryption policy that can help in data privacy. Its key components are purpose of policy, scope and encryption policy Increase audience engagement and knowledge by dispensing information using Mobile Device Encryption Policy To Safeguard Data Mobile Device Security Cybersecurity SS This template helps you present information on Three stages. You can also present information on Geographical Region, Detected Globally, Mobile Cyber Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Mobile Device Security For Data Protection Table Of Contents Cybersecurity SS
Mobile Device Security For Data Protection Table Of Contents Cybersecurity SSIntroducing Mobile Device Security For Data Protection Table Of Contents Cybersecurity SS to increase your presentation threshold. Encompassed with One stages, this template is a great option to educate and entice your audience. Dispence information on Target Devices, Target Employees, Encryption Technique Used using this template. Grab it now to reap its full benefits.
-
 Mobile Threats Faced By Different Departments Mobile Device Security Cybersecurity SS
Mobile Threats Faced By Different Departments Mobile Device Security Cybersecurity SSThis slide showcases mobile security threats faced in different departments. Its key components are department, number of mobile threats and type of attacks Increase audience engagement and knowledge by dispensing information using Mobile Threats Faced By Different Departments Mobile Device Security Cybersecurity SS This template helps you present information on Three stages. You can also present information on Compliance, Incident Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Plan To Implement Different Mobile Biometric Techniques Mobile Device Security Cybersecurity SS
Plan To Implement Different Mobile Biometric Techniques Mobile Device Security Cybersecurity SSThis slide showcases plan that can help company to implement mobile biometric solutions. Its key components are biometric technique, team responsible, expected benefits, progress and budget allocated. Deliver an outstanding presentation on the topic using this Plan To Implement Different Mobile Biometric Techniques Mobile Device Security Cybersecurity SS Dispense information and present a thorough explanation of Policy Development, Choose Solution, Train Users using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Positive Impact Due To Mobile Security Techniques Mobile Device Security Cybersecurity SS
Positive Impact Due To Mobile Security Techniques Mobile Device Security Cybersecurity SSThis slides showcases impact of implementing mobile security techniques. It highlights starts regarding company loses, operational disruption, cybersecurity expenses etc. Introducing Positive Impact Due To Mobile Security Techniques Mobile Device Security Cybersecurity SS to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on VPN Technology Selection, Assessment And Planning, Deployment And Training using this template. Grab it now to reap its full benefits.
-
 Process To Implement Mobile Device Management Mobile Device Security Cybersecurity SS
Process To Implement Mobile Device Management Mobile Device Security Cybersecurity SSThis slide showcases procedure that can help organization to implement mobile device management solution. Its key steps are current scenario assessment, policy development, choose solution etc. Increase audience engagement and knowledge by dispensing information using Process To Implement Mobile Device Management Mobile Device Security Cybersecurity SS This template helps you present information on Five stages. You can also present information on Estimated Budget, Phase Duration using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Process To Implement Mobile Vpn In Organization Mobile Device Security Cybersecurity SS
Process To Implement Mobile Vpn In Organization Mobile Device Security Cybersecurity SSThis slide showcases procedure that can help organization to implement VPN for mobile security. Its key steps are assessment, VPN technology selection, infrastructure setup etc. Introducing Process To Implement Mobile Vpn In Organization Mobile Device Security Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Rating, Ideal, Softwares using this template. Grab it now to reap its full benefits.
-
 Roadmap For Mobile Security Solutions Implementation Mobile Device Security Cybersecurity SS
Roadmap For Mobile Security Solutions Implementation Mobile Device Security Cybersecurity SSThis slide showcases roadmap that can help to implement mobile security solutions. Its key elements are estimated budget, duration of different phases etc. Present the topic in a bit more detail with this Roadmap For Mobile Security Solutions Implementation Mobile Device Security Cybersecurity SS Use it as a tool for discussion and navigation on Device Security Budget, Device Security Solutions, Techniques Effectiveness This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents For Mobile Device Security For Data Protection Cybersecurity SS
Table Of Contents For Mobile Device Security For Data Protection Cybersecurity SSIncrease audience engagement and knowledge by dispensing information using Table Of Contents For Mobile Device Security For Data Protection Cybersecurity SS This template helps you present information on Five stages. You can also present information on Financial Companies, Million Phishing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Virtual Private Network Software Comparison Mobile Device Security Cybersecurity SS
Virtual Private Network Software Comparison Mobile Device Security Cybersecurity SSThis slide showcases comparison of various VPN solutions available in market. Its key elements are mobile VPN, simultaneous connections, ratings, free trial and starting price Introducing Virtual Private Network Software Comparison Mobile Device Security Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Simultaneous Connections, Free Trial, Starting Price using this template. Grab it now to reap its full benefits.
-
 Assessing Multiple Cybersecurity Challenges In Digital Age Implementing Digital Transformation And Ai DT SS
Assessing Multiple Cybersecurity Challenges In Digital Age Implementing Digital Transformation And Ai DT SSThis slide provides glimpse about various cybersecurity challenges that allow businesses in identification of digital transformation road blocks. It includes challenges such as ransomware attacks, blockchain evolution, etc. Introducing Assessing Multiple Cybersecurity Challenges In Digital Age Implementing Digital Transformation And Ai DT SS to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Blockchain Evolution, Ransomware Attacks, Insider Attacks, Software Vulnerabilities, Phishing Attacks, using this template. Grab it now to reap its full benefits.
-
 Cybersecurity Best Practices Essential For Government Strategic Guide To Implement Strategy SS
Cybersecurity Best Practices Essential For Government Strategic Guide To Implement Strategy SSThis slide showcases the Cyber security Best Practices essential for government. It includes best practices such as Investment in cyber security, International Cooperation, Public-Private Partnerships and Capacity Building.Introducing Cybersecurity Best Practices Essential For Government Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Public Private Partnerships, International Cooperation, Investment In Cybersecurity, Capacity Building, using this template. Grab it now to reap its full benefits.
-
 Cybersecurity Best Practices Essential For Individual Strategic Guide To Implement Strategy SS
Cybersecurity Best Practices Essential For Individual Strategic Guide To Implement Strategy SSThis slide showcases Cyber security Best Practices essential for individual. It includes best practices such as strong passwords, public Wi-Fi, device security and social media privacy. Increase audience engagement and knowledge by dispensing information using Cybersecurity Best Practices Essential For Individual Strategic Guide To Implement Strategy SS. This template helps you present information on four stages. You can also present information on Strong Passwords, Device Security, Social Media Privacy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity Best Practices Essential For Organizations Strategic Guide To Implement Strategy SS
Cybersecurity Best Practices Essential For Organizations Strategic Guide To Implement Strategy SSThis slide showcases the Cyber security Best Practices essential for organizations. It includes strategies such as Network Security, Access control, Patch Management and Vendor Security.Present the topic in a bit more detail with this Cybersecurity Best Practices Essential For Organizations Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Access Controls, Network Security, Patch Management, Vendor Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Need For Vigilance And Adaptation In Cybersecurity Strategic Guide To Implement Strategy SS
Need For Vigilance And Adaptation In Cybersecurity Strategic Guide To Implement Strategy SSThis slide showcases the Need for vigilance and adaptation in cyber security. It includes key points such as evolving threat landscape, pervasive cyber attacks, data as a target, adaptive strategies and resilience building.Present the topic in a bit more detail with this Need For Vigilance And Adaptation In Cybersecurity Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Pervasive Cyberattacks, Adaptive Strategies, Resilience Building, Evolving Threat Landscape. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Dlp Approaches Enterprise Vs Integrated Data Loss Safeguarding Business With Data Loss Cybersecurity SS
Dlp Approaches Enterprise Vs Integrated Data Loss Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding the comparison of DLP approaches namely enterprise and integrated data loss prevention on various parameters such as deployment, policy management, use case, etc.Deliver an outstanding presentation on the topic using this Dlp Approaches Enterprise Vs Integrated Data Loss Safeguarding Business With Data Loss Cybersecurity SS. Dispense information and present a thorough explanation of Deployment, Policy Management, Management, Vendor Ecosystem using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Suspicious Activities And Prevent Threats, Protect Organizations Networks, Filter Out Malicious Activities, Security Devices Or Controls, using this template. Grab it now to reap its full benefits.
-
 Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing our well researched set of slides titled Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
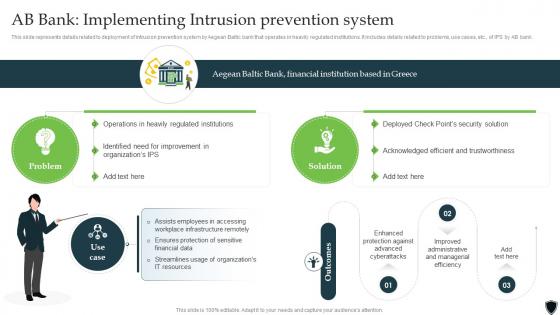 Implementing Intrusion Prevention Ab Bank Implementing Intrusion Prevention System Cybersecurity SS
Implementing Intrusion Prevention Ab Bank Implementing Intrusion Prevention System Cybersecurity SSThis slide represents details related to deployment of intrusion prevention system by Aegean Baltic bank that operates in heavily regulated institutions. It includes details related to problems, use cases, etc., of IPS by AB bank. Introducing Implementing Intrusion Prevention Ab Bank Implementing Intrusion Prevention System Cybersecurity SS to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Problem, Solution, Enhanced Protection Against Advanced Cyberattacks, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Alerting Configuration For Implemented Intrusion Cybersecurity SS
Implementing Intrusion Prevention Alerting Configuration For Implemented Intrusion Cybersecurity SSThis slide outlines the steps to configure an alerting system for a network security tool implemented to monitor networks to prevent, report, and block malicious activities. Introducing Implementing Intrusion Prevention Alerting Configuration For Implemented Intrusion Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Automate Monitoring For Intrusions, Cyber Security Data Breaches, Deploy Alarms For Detected, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Best Practices To Configure Span Ports Cybersecurity SS
Implementing Intrusion Prevention Best Practices To Configure Span Ports Cybersecurity SSThis slide represents tactics to effectively configure switched port analyzers such as focusing on filtering, checking logs, and not over-capturing and analyzing the organizational environment. Introducing Implementing Intrusion Prevention Best Practices To Configure Span Ports Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Environment, Focus On Filtering, Check Logs, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Challenges Experienced By Organization Due Cybersecurity SS
Implementing Intrusion Prevention Challenges Experienced By Organization Due Cybersecurity SSThis slide outlines the issues that enterprise face with outdated cybersecurity solutions, including limited threat visibility, inability to combat APTs, lack of granular control, and insufficient incident response capabilities. Introducing Implementing Intrusion Prevention Challenges Experienced By Organization Due Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Limited Threat Visibility, Inability To Combat Apts, Lack Of Granular Control, Insufficient Incident Response, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Cisco Data Centers Deploying Network Based Ips Cybersecurity SS
Implementing Intrusion Prevention Cisco Data Centers Deploying Network Based Ips Cybersecurity SSThis slide represents details related to deployment of intrusion prevention system by Cisco data centers . It includes details related to problems, solutions, use cases and outcomes of deploying IPS by Cisco data centers. Introducing Implementing Intrusion Prevention Cisco Data Centers Deploying Network Based Ips Cybersecurity SS to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Problem, Solution, Outcomes, Fewer Service Interruptions, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Comparative Analysis Of Intrusion Prevention Cybersecurity SS
Implementing Intrusion Prevention Comparative Analysis Of Intrusion Prevention Cybersecurity SSThis slide represents details related to deployment of intrusion prevention system by Cisco data centers . It includes details related to problems, solutions, use cases and outcomes of deploying IPS by Cisco data centers. Present the topic in a bit more detail with this Implementing Intrusion Prevention Comparative Analysis Of Intrusion Prevention Cybersecurity SS. Use it as a tool for discussion and navigation on Softwares, Features, USP, Pricing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
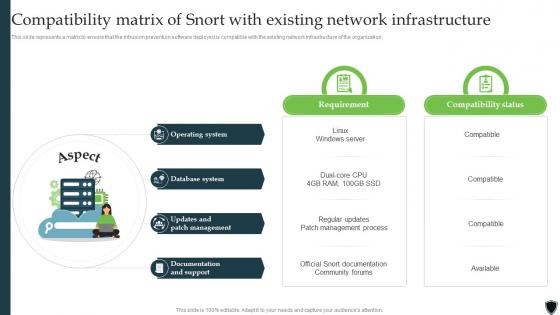 Implementing Intrusion Prevention Compatibility Matrix Of Snort With Existing Cybersecurity SS
Implementing Intrusion Prevention Compatibility Matrix Of Snort With Existing Cybersecurity SSThis slide represents a matrix to ensure that the intrusion prevention software deployed is compatible with the existing network infrastructure of the organization. Introducing Implementing Intrusion Prevention Compatibility Matrix Of Snort With Existing Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Operating System, Database System, Updates And Patch Management, Documentation And Support, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Configuring Alerts For Intrusion Prevention Cybersecurity SS
Implementing Intrusion Prevention Configuring Alerts For Intrusion Prevention Cybersecurity SSThis slide represents details related to the configuration of alerts for deployed network security tool that monitors networks for preventing, reporting, and blocking malicious activities. Introducing Implementing Intrusion Prevention Configuring Alerts For Intrusion Prevention Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on SNMP Alert Objects, Remote Syslog Alert Objects, Quarantine Response Objects, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Cost Benefit Analysis Of Intrusion Prevention Cybersecurity SS
Implementing Intrusion Prevention Cost Benefit Analysis Of Intrusion Prevention Cybersecurity SSThis slide shows the cost-benefit analysis of deploying Intrusion prevention system, including the costs incurred in deploying IPS platform and providing training to employees. Present the topic in a bit more detail with this Implementing Intrusion Prevention Cost Benefit Analysis Of Intrusion Prevention Cybersecurity SS. Use it as a tool for discussion and navigation on Initial Cost, Costs, Training Costs. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Intrusion Prevention Costs Incurred In Deploying Intrusion Cybersecurity SS
Implementing Intrusion Prevention Costs Incurred In Deploying Intrusion Cybersecurity SSThis slide details the costs associated with deploying an Intrusion prevention system solution in an enterprise. It includes expenses for implementing IPS software, IT talent acquisition costs, training costs etc. Introducing Implementing Intrusion Prevention Costs Incurred In Deploying Intrusion Cybersecurity SS to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Intrusion Prevention Software, IT Talent Acquisition Costs, Training Costs, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Create Network Segmentation Zones Based Cybersecurity SS
Implementing Intrusion Prevention Create Network Segmentation Zones Based Cybersecurity SSThis slide represents details related to the first step of deploying a network security tool that monitors networks to prevent malicious activities including blocking, reporting or dropping it. Introducing Implementing Intrusion Prevention Create Network Segmentation Zones Based Cybersecurity SS to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Active Directory, IT Monitoring Servers, Public Servers, Database Servers, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Customize Deployed Intrusion Prevention Cybersecurity SS
Implementing Intrusion Prevention Customize Deployed Intrusion Prevention Cybersecurity SSThis slide represents details related to customization of implemented network security tool that monitors networks to prevent, report and block malicious activities to organizations IT environment. Introducing Implementing Intrusion Prevention Customize Deployed Intrusion Prevention Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Servers, Metric Performance, Values, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Cybersecurity Incident Response Plan Timeline Cybersecurity SS
Implementing Intrusion Prevention Cybersecurity Incident Response Plan Timeline Cybersecurity SSThis slide represents a strategic plan to effectively respond to cybersecurity incidents experienced by the organization, including action steps such as a cyber incident reports, verification of incidents, etc. Present the topic in a bit more detail with this Implementing Intrusion Prevention Cybersecurity Incident Response Plan Timeline Cybersecurity SS. Use it as a tool for discussion and navigation on Cyber Incident Report, Verification Of Incident, Response Arrives. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
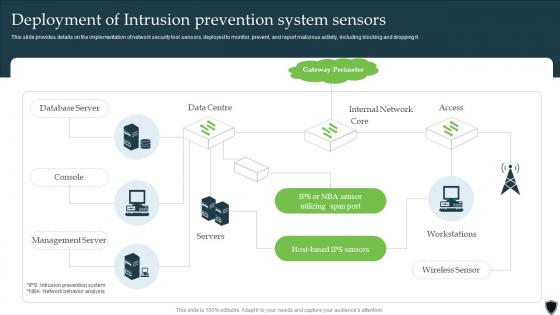 Implementing Intrusion Prevention Deployment Of Intrusion Prevention System Cybersecurity SS
Implementing Intrusion Prevention Deployment Of Intrusion Prevention System Cybersecurity SSThis slide provides details on the implementation of network security tool sensors, deployed to monitor, prevent, and report malicious activity, including blocking and dropping it. Introducing Implementing Intrusion Prevention Deployment Of Intrusion Prevention System Cybersecurity SS to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Database Server, Gateway Perimeter, Workstations, Management Server, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Fine Tune Detection Rules To Align With Threat Cybersecurity SS
Implementing Intrusion Prevention Fine Tune Detection Rules To Align With Threat Cybersecurity SSThis slide represents details related to fine-tuning threat detection rules for the implemented IPS software to effectively align with the organizations threat landscape. Present the topic in a bit more detail with this Implementing Intrusion Prevention Fine Tune Detection Rules To Align With Threat Cybersecurity SS. Use it as a tool for discussion and navigation on Preprocessor Rule, Standard Text Rule, Shared Object Rule. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
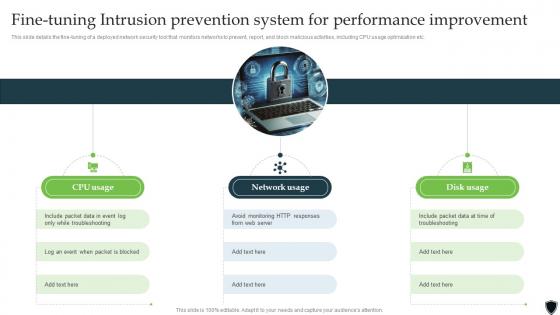 Implementing Intrusion Prevention Fine Tuning Intrusion Prevention System Cybersecurity SS
Implementing Intrusion Prevention Fine Tuning Intrusion Prevention System Cybersecurity SSThis slide details the fine-tuning of a deployed network security tool that monitors networks to prevent, report, and block malicious activities, including CPU usage optimization etc. Introducing Implementing Intrusion Prevention Fine Tuning Intrusion Prevention System Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on CPU Usage, Network Usage, Disk Usage, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Hardware Requirements For Effective Ips Cybersecurity SS
Implementing Intrusion Prevention Hardware Requirements For Effective Ips Cybersecurity SSThis slide outlines the hardware requirements to consider when selecting a network security tool to monitor and prevent malicious activities. These requirements include network interfaces etc. Introducing Implementing Intrusion Prevention Hardware Requirements For Effective Ips Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Network Interfaces, Storage, Redundancy, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Identified Critical Assets And Threats Of Enterprise Cybersecurity SS
Implementing Intrusion Prevention Identified Critical Assets And Threats Of Enterprise Cybersecurity SSThis slide presents critical assets and associated threats, such as data breaches, information manipulation, data corruption, identity theft, etc., identified by the IT team. Present the topic in a bit more detail with this Implementing Intrusion Prevention Identified Critical Assets And Threats Of Enterprise Cybersecurity SS. Use it as a tool for discussion and navigation on Critical Assets, Network Infrastructure, Application Infrastructure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Intrusion Prevention Impact Of Inefficient Network Security Cybersecurity SS
Implementing Intrusion Prevention Impact Of Inefficient Network Security Cybersecurity SSThis slide represents the impact of outdated cybersecurity solutions on organizational operations which leads to compromised data security, data leakage, and damage to the organizations reputation. Introducing Implementing Intrusion Prevention Impact Of Inefficient Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Compromised Data Integrity, Increase In Risk Of Data Leakage, Increase In Recovery Costs, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Monitor Real Time Intrusion Prevention Detection Cybersecurity SS
Implementing Intrusion Prevention Monitor Real Time Intrusion Prevention Detection Cybersecurity SSThis slide covers details related to real-time monitoring of system alerts provided by deployed network security tool that monitors networks for preventing, reporting and blocking malicious activities. Introducing Implementing Intrusion Prevention Monitor Real Time Intrusion Prevention Detection Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Pattern Recognition, Automated Response, Behavioral Analysis, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Patch Management Plan For Mitigating Cybersecurity SS
Implementing Intrusion Prevention Patch Management Plan For Mitigating Cybersecurity SSThis slide represents a strategic plan for protecting the organization against software vulnerabilities, including action steps such as establishing a regular patching schedule, successfully testing patches, etc. Introducing Implementing Intrusion Prevention Patch Management Plan For Mitigating Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Establish Regular Patching Schedule, Progress Status, Successfully Test Patches, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Potential Attacks Detected And Prevented Cybersecurity SS
Implementing Intrusion Prevention Potential Attacks Detected And Prevented Cybersecurity SSThis slide represents cybersecurity attacks detected and prevented by a network security tool that monitors the network for malicious activities, including DDoS attacks, ARP spoofing, and IP fragmentation. Introducing Implementing Intrusion Prevention Potential Attacks Detected And Prevented Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Distributed Denial Of Service, Address Resolution Protocol ARP Spoofing, IP Fragmentation, using this template. Grab it now to reap its full benefits.





