Powerpoint Templates and Google slides for Cybersecurity
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Agenda Building Next Generation Endpoint Security Cybersecurity SS
Agenda Building Next Generation Endpoint Security Cybersecurity SSIntroducing Agenda Building Next Generation Endpoint Security Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Malicious Cyberattacks, Enhanced Security, Key Organizational Kpis, using this template. Grab it now to reap its full benefits.
-
 Ai And Ml Endpoint Security Architecture Building Next Generation Endpoint Security Cybersecurity SS
Ai And Ml Endpoint Security Architecture Building Next Generation Endpoint Security Cybersecurity SSDeliver an outstanding presentation on the topic using this Ai And Ml Endpoint Security Architecture Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Process, Output, Input using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Building Next Generation Endpoint Security Table Of Contents Cybersecurity SS
Building Next Generation Endpoint Security Table Of Contents Cybersecurity SSIncrease audience engagement and knowledge by dispensing information using Building Next Generation Endpoint Security Table Of Contents Cybersecurity SS. This template helps you present information on one stages. You can also present information on Antivirus Enhancement, Smart Endpoint Application Control, Least Privilege Approach using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Business Gap Analysis For Endpoint Security Building Next Generation Endpoint Security Cybersecurity SS
Business Gap Analysis For Endpoint Security Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases gap analysis which can help companies realize their need assessment position by calculating current and desired state, assisting them plan action items. Present the topic in a bit more detail with this Business Gap Analysis For Endpoint Security Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Parameters, Current State, Impact, Importance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Analysis Of Multiple Edr Tools Building Next Generation Endpoint Security Cybersecurity SS
Comparative Analysis Of Multiple Edr Tools Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases comparative assessment of various endpoint detection and response EDR tools. It provides details about multi level views, forensics breakdown, ransomware detection, etc.Deliver an outstanding presentation on the topic using this Comparative Analysis Of Multiple Edr Tools Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Product, Features, Pricing, Rating using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparative Assessment Of Endpoint Security Building Next Generation Endpoint Security Cybersecurity SS
Comparative Assessment Of Endpoint Security Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases comparative analysis for endpoint security tools. It provides details about endpoint firewall, compatibility, data loss prevention, regulatory compliance, etc.Present the topic in a bit more detail with this Comparative Assessment Of Endpoint Security Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Regulatory Compliance, Data Loss Prevention, Endpoint Firewall. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Crucial Ways To Avoid Malicious Code Building Next Generation Endpoint Security Cybersecurity SS
Crucial Ways To Avoid Malicious Code Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases major ways to prevent malicious code infections. This can help developers avoid attacks from public networks, verify sources and avoid harmless links code.Introducing Crucial Ways To Avoid Malicious Code Building Next Generation Endpoint Security Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Public Networks, Legitimacy Of Sources, Harmless Links, using this template. Grab it now to reap its full benefits.
-
 Current Challenges With Traditional Endpoint Building Next Generation Endpoint Security Cybersecurity SS
Current Challenges With Traditional Endpoint Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases current scenario of roadblocks faced by business w.r.t traditional endpoint security. It includes challenges such as false positives, privileges, anti-virus, etc.Increase audience engagement and knowledge by dispensing information using Current Challenges With Traditional Endpoint Building Next Generation Endpoint Security Cybersecurity SS. This template helps you present information on six stages. You can also present information on Modern Attacks Missed, Challenges, Vulnerabilities Highlighted using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity Endpoint Security Architecture Building Next Generation Endpoint Security Cybersecurity SS
Cybersecurity Endpoint Security Architecture Building Next Generation Endpoint Security Cybersecurity SSPresent the topic in a bit more detail with this Cybersecurity Endpoint Security Architecture Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Management, Contact Distribution, Endpoint Protection Clients. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Deploying Edr For Advanced Threat Protection Building Next Generation Endpoint Security Cybersecurity SS
Deploying Edr For Advanced Threat Protection Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases deploying endpoint detection and response EDR for advanced threat protection. It provides details about alert triage, containment, incident data search, etc.Deliver an outstanding presentation on the topic using this Deploying Edr For Advanced Threat Protection Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Advanced Threat Detection, Incident Data Search, Alert Triage using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Deploying Enhanced Anti Virus For Endpoint Building Next Generation Endpoint Security Cybersecurity SS
Deploying Enhanced Anti Virus For Endpoint Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases enhanced antivirus platform for endpoint security. It includes details about attack surface reduction, centralized configuration, zero-day attacks, etc.Present the topic in a bit more detail with this Deploying Enhanced Anti Virus For Endpoint Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Our Platform Capabilities, Potential Impact, Centralized Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Endpoint Cyber Security General Overview Building Next Generation Endpoint Security Cybersecurity SS
Endpoint Cyber Security General Overview Building Next Generation Endpoint Security Cybersecurity SSIntroducing Endpoint Cyber Security General Overview Building Next Generation Endpoint Security Cybersecurity SS to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Overview, Computer Viruses, Smartphones And Tablets, Servers, using this template. Grab it now to reap its full benefits.
-
 Endpoint Data Loss Prevention Tool Building Next Generation Endpoint Security Cybersecurity SS
Endpoint Data Loss Prevention Tool Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases endpoint data loss prevention DLP tool process. It includes stages such as identification, assistance and tracking of endpoint data.Increase audience engagement and knowledge by dispensing information using Endpoint Data Loss Prevention Tool Building Next Generation Endpoint Security Cybersecurity SS. This template helps you present information three stages. You can also present information on Identify, Assist, Track, Potential Impact using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Endpoint Security Least Privilege Approach Building Next Generation Endpoint Security Cybersecurity SS
Endpoint Security Least Privilege Approach Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases least privilege approach for endpoint security. It includes steps such as granular access control, regular access reviews, whitelisting, etc.Introducing Endpoint Security Least Privilege Approach Building Next Generation Endpoint Security Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Granular Access Control, Regular Access Reviews, App Control And Whitelisting, using this template. Grab it now to reap its full benefits.
-
 Endpoint Security Process With Key Stages Building Next Generation Endpoint Security Cybersecurity SS
Endpoint Security Process With Key Stages Building Next Generation Endpoint Security Cybersecurity SSIntroducing Endpoint Security Process With Key Stages Building Next Generation Endpoint Security Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Gather Information, Choose Security Solutions, Implement Chosen Solutions, using this template. Grab it now to reap its full benefits.
-
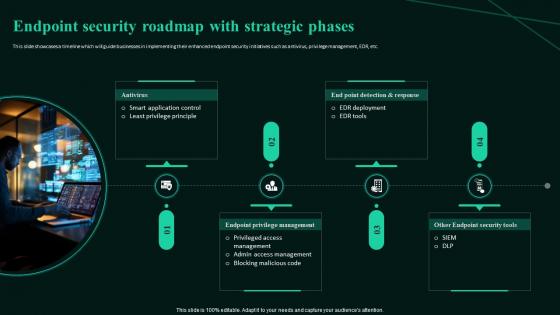 Endpoint Security Roadmap With Strategic Building Next Generation Endpoint Security Cybersecurity SS
Endpoint Security Roadmap With Strategic Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases a timeline which will guide businesses in implementing their enhanced endpoint security initiatives such as antivirus, privilege management, EDR, etc.Increase audience engagement and knowledge by dispensing information using Endpoint Security Roadmap With Strategic Building Next Generation Endpoint Security Cybersecurity SS. This template helps you present information on one stages. You can also present information on Other Endpoint Security Tools, Endpoint Privilege Management, Antivirus, End Point Detection And Response using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Endpoint Security Team Training Plan Building Next Generation Endpoint Security Cybersecurity SS
Endpoint Security Team Training Plan Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases endpoint security team training plan. It provides details about endpoint detection and response, network security, applied threat hunting, etc.Present the topic in a bit more detail with this Endpoint Security Team Training Plan Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Training Provider, Duration, Modules, Sessions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Establishing Endpoint Privilege Management Building Next Generation Endpoint Security Cybersecurity SS
Establishing Endpoint Privilege Management Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases endpoint privilege management for maximum security. It includes details about admin rights, application privileges, just in time access, etcIntroducing Establishing Endpoint Privilege Management Building Next Generation Endpoint Security Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Current Scenario, Remedial Solutions, Potential Impact, using this template. Grab it now to reap its full benefits.
-
 Establishing Privilege Access Management Building Next Generation Endpoint Security Cybersecurity SS
Establishing Privilege Access Management Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases how to establish privilege access management process. It provides details about prepare, protect, operate, monitor, etc.Present the topic in a bit more detail with this Establishing Privilege Access Management Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Prepare, Protect, Operate, Monitor. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Icons Slide For Building Next Generation Endpoint Security Cybersecurity SS
Icons Slide For Building Next Generation Endpoint Security Cybersecurity SSPresenting our premium Icons Slide For Building Next Generation Endpoint Security Cybersecurity SS set of slides with flexible icons. The icons are designed by our group of professionals. Add these XXXXXXXXXXXXXXXXXXXX to your presentation to make it visually appealing. Also, edit them according to your requirement. Download it and captive your audience.
-
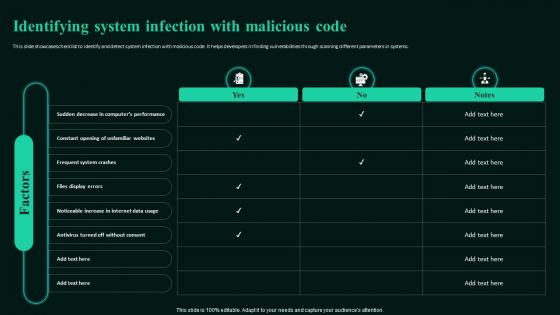 Identifying System Infection With Malicious Building Next Generation Endpoint Security Cybersecurity SS
Identifying System Infection With Malicious Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases checklist to identify and detect system infection with malicious code. It helps developers in finding vulnerabilities through scanning different parameters in systems.Deliver an outstanding presentation on the topic using this Identifying System Infection With Malicious Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Frequent System Crashes, Files Display Errors, Unfamiliar Websites using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Impact Analysis Of Endpoint Security Building Next Generation Endpoint Security Cybersecurity SS
Impact Analysis Of Endpoint Security Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases current scenario of improvements w.r.t traditional endpoint security. It includes details such as false positives, privileges, anti-virus, etc.Introducing Impact Analysis Of Endpoint Security Building Next Generation Endpoint Security Cybersecurity SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Improvements, Vulnerabilities Solved, Modern Attacks Missed, using this template. Grab it now to reap its full benefits.
-
 Least Privilege Implementation For Accidental Building Next Generation Endpoint Security Cybersecurity SS
Least Privilege Implementation For Accidental Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases implementation of least privilege principle for avoiding accidental misuses. It provides details about security controls, data discovery, etc.Deliver an outstanding presentation on the topic using this Least Privilege Implementation For Accidental Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Action Steps, Real Problem Solved, Layering Security Controls using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Least Privilege Implementation For Segregation Building Next Generation Endpoint Security Cybersecurity SS
Least Privilege Implementation For Segregation Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases implementation of least privilege principle for segregation of duties. It provides details about time limits, certain access, etc.Introducing Least Privilege Implementation For Segregation Building Next Generation Endpoint Security Cybersecurity SS to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Action Steps, Real Problem Solved, Financial Data, using this template. Grab it now to reap its full benefits.
-
 Mitigation Plan For Malicious Code Protection Building Next Generation Endpoint Security Cybersecurity SS
Mitigation Plan For Malicious Code Protection Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases mitigation plan for protection against malicious code. It can help detect malware, adware, etc. and plan action items accordingly.Present the topic in a bit more detail with this Mitigation Plan For Malicious Code Protection Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Malware Infection, Unauthorized Access, Adware Intrusion, Phishing Attack. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Raci Matrix For Effective Endpoint Security Building Next Generation Endpoint Security Cybersecurity SS
Raci Matrix For Effective Endpoint Security Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases endpoint security team responsible, accountable, consulted and informed RACI matrix. It provides details about endpoint detection and response, network security, etc.Deliver an outstanding presentation on the topic using this Raci Matrix For Effective Endpoint Security Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Monitor Security, Identity Strategic Risk, Perform Business Impact Assessments using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Removing Admin Rights For Endpoint Security Building Next Generation Endpoint Security Cybersecurity SS
Removing Admin Rights For Endpoint Security Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases process to remove admin rights for increased endpoint security. It includes details about discover, analyze, remediate, etc. Introducing Removing Admin Rights For Endpoint Security Building Next Generation Endpoint Security Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Analyze, Remediate, Discover, Improves Risk Mitigation, using this template. Grab it now to reap its full benefits.
-
 Siem Tool To Address Potential Security Threats Building Next Generation Endpoint Security Cybersecurity SS
Siem Tool To Address Potential Security Threats Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases security information and event management SIEM tools which can help endpoint security teams detect and address potential security threats.Present the topic in a bit more detail with this Siem Tool To Address Potential Security Threats Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Collection, Detection, Investigation, Response. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Smart Endpoint Application Control For Reduced Building Next Generation Endpoint Security Cybersecurity SS
Smart Endpoint Application Control For Reduced Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases smart endpoint app control process. It can help developers reduce attacks through blocklist rules, risk assessment, recommendation engine, etc.Deliver an outstanding presentation on the topic using this Smart Endpoint Application Control For Reduced Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Symantec Application Control, Symantec Application Control, Recommendation Engine using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents Building Next Generation Endpoint Security Cybersecurity SS
Table Of Contents Building Next Generation Endpoint Security Cybersecurity SSIntroducing Table Of Contents Building Next Generation Endpoint Security Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Endpoint Security Strategies, Endpoint Security Team, Current Endpoint Security Scenario, using this template. Grab it now to reap its full benefits.
-
 Types Of Endpoint Cyber Security Tools Building Next Generation Endpoint Security Cybersecurity SS
Types Of Endpoint Cyber Security Tools Building Next Generation Endpoint Security Cybersecurity SSPresent the topic in a bit more detail with this Types Of Endpoint Cyber Security Tools Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Mobile Threat Defense, Endpoint Protection Platform, Advanced Threat Protection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Blockchain Technology Working For Organizational Cybersecurity
Blockchain Technology Working For Organizational CybersecurityThe below slide provides the working process for blockchain security technology used by organizations to enhance transaction privacy. The process involves steps such as initiation, validation, verification, etc. Presenting our set of slides with Blockchain Technology Working For Organizational Cybersecurity. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Transaction Initiated, Transaction Completed, Benefits Received.
-
 Organizational Cybersecurity Risk Prevention Icon
Organizational Cybersecurity Risk Prevention IconIntroducing our premium set of slides with Organizational Cybersecurity Risk Prevention Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Organizational Cybersecurity, Risk Prevention, Icon. So download instantly and tailor it with your information.
-
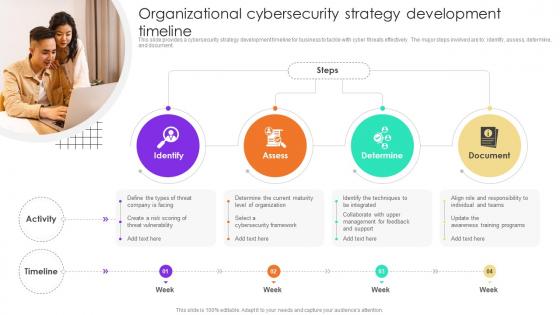 Organizational Cybersecurity Strategy Development Timeline
Organizational Cybersecurity Strategy Development TimelineThis slide provides a cybersecurity strategy development timeline for business to tackle with cyber threats effectively. The major steps involved are to identify, assess, determine, and document. Presenting our set of slides with Organizational Cybersecurity Strategy Development Timeline. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify, Assess, Determine, Document.
-
 Various Training Programs Cybersecurity Compliance Awareness Training Program DTE SS
Various Training Programs Cybersecurity Compliance Awareness Training Program DTE SSThe following slide depicts cybersecurity compliance training plan for employees. It includes elements such as courses, mode, duration, resources, start and end date, etc. Deliver an outstanding presentation on the topic using this Various Training Programs Cybersecurity Compliance Awareness Training Program DTE SS. Dispense information and present a thorough explanation of Cybersecurity Tools And Attacks, Disaster Recovery, Information Security And Awareness using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Assessment Of Operational And Cybersecurity Factors Global 3d Printing Industry Outlook IR SS
Risk Assessment Of Operational And Cybersecurity Factors Global 3d Printing Industry Outlook IR SSThe slide highlights major risks existing in 3D printing industry. It seeks to inform the audience of the need to effectively identify and manage risks in order to maintain stability and security. The main elements are risks related to operational, cybersecurity, legal and regulatory factors. Present the topic in a bit more detail with this Risk Assessment Of Operational And Cybersecurity Factors Global 3d Printing Industry Outlook IR SS. Use it as a tool for discussion and navigation on Operational Risks ,Legal Regulatory Risks, Cybersecurity Risks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building Cybersecurity Icon For Data Protection
Building Cybersecurity Icon For Data ProtectionPresenting our set of slides with Building Cybersecurity Icon For Data Protection. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Building Cybersecurity,Icon,Data Protection.
-
 Key Considerations For Building Cybersecurity Strategies
Key Considerations For Building Cybersecurity StrategiesThis slide showcases the major considerations for developing cybersecurity strategies which helps an organization to decrease attacks and data breaches by offering quick response time. It include details such as protect perimeter less technology,support zero trust,etc. Introducing our premium set of slides with Key Considerations For Building Cybersecurity Strategies. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Support Zero Trust,Provide Awareness Programs,Offer Security Knowledge. So download instantly and tailor it with your information.
-
 Timeline For Building Cybersecurity To Protect Organizational Data
Timeline For Building Cybersecurity To Protect Organizational DataThis slide showcases the roadmap for creating cybersecurity for encrypting organizational data which helps them to protect enterprise sensitive information and discourage suspicious activities. It include details such as secure virtual and physical assets,determine risks,etc. Presenting our well structured Timeline For Building Cybersecurity To Protect Organizational Data. The topics discussed in this slide are Ensure Performing,Correct Issues,Deploy Controls. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cybersecurity Emergency And Crisis Management Icon
Cybersecurity Emergency And Crisis Management IconIntroducing our premium set of slides with Cybersecurity Emergency And Crisis Management Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cybersecurity Emergency, Crisis Management, Icon. So download instantly and tailor it with your information.
-
 Cybersecurity Emergency And Crisis Management Services
Cybersecurity Emergency And Crisis Management ServicesThis slide represents the incident response management services for cybersecurity that helps to strengthen cyber resilience and prevent attacks. The service categories include on-demand, tier1, tier 2, and tier 3. Introducing our Cybersecurity Emergency And Crisis Management Services set of slides. The topics discussed in these slides are Service Category, Incident Response Services, Features. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cybersecurity Incident Management Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cybersecurity Incident Management Colored Icon In Powerpoint Pptx Png And Editable Eps FormatIntroducing our Emergency Response Plan for Cybersecurity Incidents PowerPoint icon. This vibrant and eye-catching icon is the perfect visual aid for your presentation on cybersecurity incident response strategies. With its bold colors and clear design, it will effectively convey the importance of having a plan in place to handle cyber threats.
-
 Cybersecurity Incident Management Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cybersecurity Incident Management Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is the perfect visual aid for your Emergency Response Plan for Cybersecurity Incidents. It features a simple yet impactful design that will enhance your presentation and effectively communicate the importance of having a plan in place to handle potential cyber threats.
-
 Cybersecurity Risk Management Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cybersecurity Risk Management Colored Icon In Powerpoint Pptx Png And Editable Eps FormatEnhance the security of your web application with this comprehensive checklist icon for PowerPoint. Featuring a bold and vibrant colour, this icon serves as a visual reminder to ensure all necessary security measures are in place. Perfect for presentations and training materials on web application security.
-
 Cybersecurity Risk Management Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cybersecurity Risk Management Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint icon is perfect for any web application security checklist. With its sleek and minimalist design, it will add a professional touch to your presentation. Use it to highlight important points and emphasize the importance of web application security in a visually appealing way.
-
 Employee Training Calendar For Cybersecurity Skill Development
Employee Training Calendar For Cybersecurity Skill DevelopmentThis slide represents calendar for employee training to develop cybersecurity skills including sessions on e-mail scam, malware, password security, etc. Introducing our Employee Training Calendar For Cybersecurity Skill Development set of slides. The topics discussed in these slides are Online, Offline, Training Program. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cybersecurity Optimization Meeting Summary Icon
Cybersecurity Optimization Meeting Summary IconIntroducing our premium set of slides with Cybersecurity Optimization Meeting Summary Icon. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cybersecurity Optimization, Meeting Summary, Icon. So download instantly and tailor it with your information.
-
 Cybersecurity Project Improvement Plan For Organizational Security Improvement Plan SS
Cybersecurity Project Improvement Plan For Organizational Security Improvement Plan SSThe purpose of this slide is to present a cybersecurity project improvement plan focused on enhancing organizational security by targeted vulnerability mitigation. It includes objectives, action plan, and urgent problems, etc. Presenting our set of slides with Cybersecurity Project Improvement Plan For Organizational Security Improvement Plan SS This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Objective, Action Plan, Urgent Problems
-
 Cybersecurity Mentorship Program For Risk Management
Cybersecurity Mentorship Program For Risk ManagementThis slide represents mentorship program for effective cybersecurity including elements such as sessions, mentors, date, duration, department, etc. Introducing our Cybersecurity Mentorship Program For Risk Management set of slides. The topics discussed in these slides are Malware Attack, Encryption, Cloud Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Addressing Business Challenges For Effective Mdr Cybersecurity Adoption
Addressing Business Challenges For Effective Mdr Cybersecurity AdoptionThis slide represents various strategies that assist IT companies to mitigate challenges faced during MDR adoption for enhancing cybersecurity. It includes various challenges such as staffing, alert fatigue, and time to maturity. Introducing our Addressing Business Challenges For Effective Mdr Cybersecurity Adoption set of slides. The topics discussed in these slides are Mitigation, Strategies, Business. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Applications Of Mdr Solutions For Enhancing Healthcare Cybersecurity
Applications Of Mdr Solutions For Enhancing Healthcare CybersecurityThis slide represents various applications of MDR solutions that assist healthcare companies to enhance their cybersecurity for protecting patients data. It includes applications such as patient health data security, resilience of emergency services, etc. Presenting our set of slides with Applications Of Mdr Solutions For Enhancing Healthcare Cybersecurity. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Patient Health Data Security, Reducing Cybersecurity Workload, Third Party Vendor Risk Management.
-
 Best Practices For Mdr Utilization To Enhance Cybersecurity
Best Practices For Mdr Utilization To Enhance CybersecurityThis slide represents various best practices that assist companies to effectively utilize MDR solutions for enhancing their cybersecurity and data protection. It includes practices such as integration with SIEM, Internal team collaborations, etc. Presenting our well structured Best Practices For Mdr Utilization To Enhance Cybersecurity. The topics discussed in this slide are Best Practices, Actions Required, Integration With SIEM. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Case Study Of Implementing Mdr Cybersecurity For Aws
Case Study Of Implementing Mdr Cybersecurity For AwsThis slide represents case study that assist companies to understand applications of MDR cybersecurity solutions to enhance network protection, it includes various elements such as overview, challenges, solutions, and impact. Introducing our premium set of slides with Case Study Of Implementing Mdr Cybersecurity For Aws. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Overview, Challenges, Solutions. So download instantly and tailor it with your information.
-
 Comparison Analysis Of Mdr Cybersecurity With Edr And Xdr Solutions
Comparison Analysis Of Mdr Cybersecurity With Edr And Xdr SolutionsThis slide represents comparison analysis of MDR cybersecurity solution with EDR and XDR solutions to enhance data risk management and information security. It includes various aspects such as definition, capabilities, components, etc. Introducing our Comparison Analysis Of Mdr Cybersecurity With Edr And Xdr Solutions set of slides. The topics discussed in these slides are Comparison, Analysis, Cybersecurity. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Comparison Assessment Of Mdr Software For Enhancing Cybersecurity
Comparison Assessment Of Mdr Software For Enhancing CybersecurityThis slide represents comparison analysis of MDR software that assist IT companies to enhance their cybersecurity and information management. It includes various software such as Sophos MDR, Huntress, Alert logic MDR, Arctic wolf, etc. Presenting our well structured Comparison Assessment Of Mdr Software For Enhancing Cybersecurity. The topics discussed in this slide are Comparison, Assessment, Cybersecurity. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Gantt Chart To Implement Mdr Cybersecurity Services For Threat Protection
Gantt Chart To Implement Mdr Cybersecurity Services For Threat ProtectionThis slide represents Gantt chart that assist companies to implement MDR cybersecurity services to enhance their data protection management. It includes steps such as defining needs, market research, budget consideration, comparison, etc. Introducing our Gantt Chart To Implement Mdr Cybersecurity Services For Threat Protection set of slides. The topics discussed in these slides are Cybersecurity, Services, Threat Protection. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Key Considerations To Select Mdr Vendor For Effective Cybersecurity
Key Considerations To Select Mdr Vendor For Effective CybersecurityThis slide represents various considerations that assist companies to select best MDR vendor to enhance their data protection and cybersecurity effectively. It includes various considerations such as expertise, facilities, and methodology. Introducing our Key Considerations To Select Mdr Vendor For Effective Cybersecurity set of slides. The topics discussed in these slides are Key Considerations, Cybersecurity, Methodology. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Mdr Architecture To Mitigate Cybersecurity Threats Effectively
Mdr Architecture To Mitigate Cybersecurity Threats EffectivelyThis slide represents MDR architecture that assists companies in mitigating cybersecurity threats to enhance data protection effectively. It includes elements such as company infrastructure, MDR platforms, D and R teams, customers, etc. Presenting our well structured Mdr Architecture To Mitigate Cybersecurity Threats Effectively. The topics discussed in this slide are Architecture, Cybersecurity, Threats Effectively. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Mdr Cybersecurity Icon For Multi Cloud Data Protection
Mdr Cybersecurity Icon For Multi Cloud Data ProtectionIntroducing our Mdr Cybersecurity Icon For Multi Cloud Data Protection set of slides. The topics discussed in these slides are Cybersecurity, Data Protection. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Mdr Cybersecurity Icon To Detect Data Threats
Mdr Cybersecurity Icon To Detect Data ThreatsPresenting our well structured Mdr Cybersecurity Icon To Detect Data Threats. The topics discussed in this slide are Cybersecurity, Data Threats. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.





