Powerpoint Templates and Google slides for Cyberattack
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Implementing Organizational Security Training To Prevent Cyberattacks Complete Deck
Implementing Organizational Security Training To Prevent Cyberattacks Complete DeckDitch the Dull templates and opt for our engaging Implementing Organizational Security Training To Prevent Cyberattacks Complete Deck deck to attract your audience. Our visually striking design effortlessly combines creativity with functionality, ensuring your content shines through. Compatible with Microsoft versions and Google Slides, it offers seamless integration of presentation. Save time and effort with our pre-designed PPT layout, while still having the freedom to customize fonts, colors, and everything you ask for. With the ability to download in various formats like JPG, JPEG, and PNG, sharing your slides has never been easier. From boardroom meetings to client pitches, this deck can be the secret weapon to leaving a lasting impression.
-
 Security Controls Management Cyberattacks Organization Infrastructure Investments
Security Controls Management Cyberattacks Organization Infrastructure InvestmentsIf you require a professional template with great design, then this Security Controls Management Cyberattacks Organization Infrastructure Investments is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using twelve slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Cyberattacks Framework Network Security Platforms Through
Cyberattacks Framework Network Security Platforms ThroughEngage buyer personas and boost brand awareness by pitching yourself using this prefabricated set. This Cyberattacks Framework Network Security Platforms Through is a great tool to connect with your audience as it contains high-quality content and graphics. This helps in conveying your thoughts in a well-structured manner. It also helps you attain a competitive advantage because of its unique design and aesthetics. In addition to this, you can use this PPT design to portray information and educate your audience on various topics. With twelve slides, this is a great design to use for your upcoming presentations. Not only is it cost-effective but also easily pliable depending on your needs and requirements. As such color, font, or any other design component can be altered. It is also available for immediate download in different formats such as PNG, JPG, etc. So, without any further ado, download it now.
-
 EDR Graphical Insights For Detecting Cyberattacks
EDR Graphical Insights For Detecting CyberattacksThis slide demonstrates EDR insights into cyberattacks and includes reasons for detecting cyberattacks. Introducing our EDR Graphical Insights For Detecting Cyberattacks set of slides. The topics discussed in these slides are EDR Graphical Insights, Detecting Cyberattacks, Resource Constraints, Incident Complexity. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
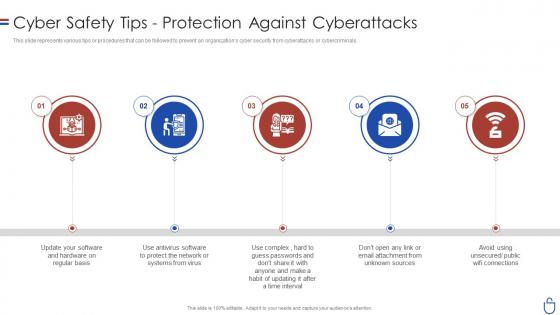 Data security it cyber safety tips protection against cyberattacks
Data security it cyber safety tips protection against cyberattacksThis slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. Increase audience engagement and knowledge by dispensing information using Data Security IT Cyber Safety Tips Protection Against Cyberattacks. This template helps you present information on five stages. You can also present information on Sources, Public Wifi Connections, Time Interval, Protect Network using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
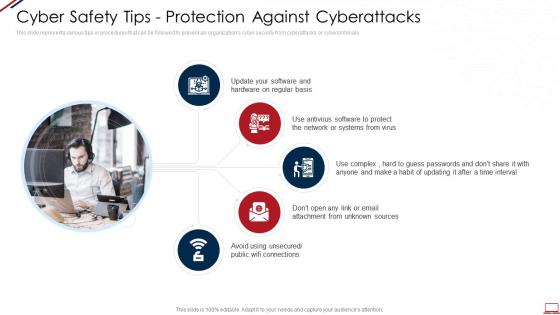 Cyber safety tips protection against cyberattacks computer system security
Cyber safety tips protection against cyberattacks computer system securityThis slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. Increase audience engagement and knowledge by dispensing information using Cyber Safety Tips Protection Against Cyberattacks Computer System Security. This template helps you present information on five stages. You can also present information on Cyber Safety Tips Protection Against Cyberattacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Potential Cyberattack Sources To Breach Mobile Devices E Wallets As Emerging Payment Method Fin SS V
Potential Cyberattack Sources To Breach Mobile Devices E Wallets As Emerging Payment Method Fin SS VThis slide shows diagram which can be used to understand the potential sources of cyberattacks used by hackers to get through users mobile devices. It is further categorized in four parts which are via browser, system, phone or SMS or applications. Increase audience engagement and knowledge by dispensing information using Potential Cyberattack Sources To Breach Mobile Devices E Wallets As Emerging Payment Method Fin SS V. This template helps you present information on four stages. You can also present information on Potential,Cyberattack,Sources using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Blockchain Cyberattack Identification Workflow Model Hands On Blockchain Security Risk BCT SS V
Blockchain Cyberattack Identification Workflow Model Hands On Blockchain Security Risk BCT SS VThe following slide depicts blockchain attack identification workflow. It includes elements such as recording blockchain fingerprints, determining data breaches, aiming to deliver data to manufacturer, stealing and corrupting data, etc. Present the topic in a bit more detail with this Blockchain Cyberattack Identification Workflow Model Hands On Blockchain Security Risk BCT SS V. Use it as a tool for discussion and navigation on Blockchain Fingerprints, Data Ownership, Data And Corrupt. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 NEO Banks For Digital Funds Potential Cyberattack Sources To Breach Mobile Devices Fin SS V
NEO Banks For Digital Funds Potential Cyberattack Sources To Breach Mobile Devices Fin SS VThis slide shows diagram which can be used to understand the potential sources of cyberattacks used by hackers to get through users mobile devices. It is further categorized in four parts which are via browser, system, phone or SMS or applications. Increase audience engagement and knowledge by dispensing information using NEO Banks For Digital Funds Potential Cyberattack Sources To Breach Mobile Devices Fin SS V. This template helps you present information on four stages. You can also present information on Improper SSL Validation, Config Manipulation, Dynamic Runtime Injection, Unintended Permissions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Blockchain And Cybersecurity Blockchain Cyberattack Identification Workflow Model BCT SS V
Blockchain And Cybersecurity Blockchain Cyberattack Identification Workflow Model BCT SS VThe following slide depicts blockchain attack identification workflow. It includes elements such as recording blockchain fingerprints, determining data breaches, aiming to deliver data to manufacturer, stealing and corrupting data, etc. Present the topic in a bit more detail with this Blockchain And Cybersecurity Blockchain Cyberattack Identification Workflow Model BCT SS V Use it as a tool for discussion and navigation on Designer, Blockchain, Bad Actor This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Threats In Blockchain Blockchain Cyberattack Identification Workflow Model BCT SS V
Cyber Threats In Blockchain Blockchain Cyberattack Identification Workflow Model BCT SS VThe following slide depicts blockchain attack identification workflow. It includes elements such as recording blockchain fingerprints, determining data breaches, aiming to deliver data to manufacturer, stealing and corrupting data, etc. Present the topic in a bit more detail with this Cyber Threats In Blockchain Blockchain Cyberattack Identification Workflow Model BCT SS V Use it as a tool for discussion and navigation on Designer, Blockchain, BAD Actor This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 4Ps Of 5G Network Visibility To Prevent Cyberattacks
4Ps Of 5G Network Visibility To Prevent CyberattacksThis slide shows the 4 Ps for establishing 5 G network visibility in order to prevent cyber attacks. The purpose of this slide is to help the business improve its visibility by eliminating the risk of cyber attacks. It includes packets, permissions, perimeters and partners Presenting our set of slides with 4Ps Of 5G Network Visibility To Prevent Cyberattacks. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Application, Services, Network.
-
 Components Of 5G Security Architecture To Prevent Cyberattacks
Components Of 5G Security Architecture To Prevent CyberattacksThis slide depicts the components of a 5 G security architecture utilized for preventing cyber attacks. The purpose of this slide is to help the business safeguard its networks through proper implementation of critical components such as network security, scaling security, etc. Presenting our set of slides with Components Of 5G Security Architecture To Prevent Cyberattacks. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network, Hardware, Security.
-
 Everything About Mobile Banking Potential Cyberattack Sources To Breach Mobile Devices Fin SS V
Everything About Mobile Banking Potential Cyberattack Sources To Breach Mobile Devices Fin SS VThis slide shows diagram which can be used to understand the potential sources of cyberattacks used by hackers to get through users mobile devices. It is further categorized in four parts which are via browser, system, phone or SMS or applications. Increase audience engagement and knowledge by dispensing information using Everything About Mobile Banking Potential Cyberattack Sources To Breach Mobile Devices Fin SS V. This template helps you present information on four stages. You can also present information on Sensitive Data Storage, Unintended Permissions, Escalated Privileges, Config Manipulation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Potential Cyberattack Sources To Breach Smartphone Banking For Transferring Funds Digitally Fin SS V
Potential Cyberattack Sources To Breach Smartphone Banking For Transferring Funds Digitally Fin SS VThis slide shows diagram which can be used to understand the potential sources of cyberattacks used by hackers to get through users mobile devices. It is further categorized in four parts which are via browser, system, phoneSMS or applications. Increase audience engagement and knowledge by dispensing information using Potential Cyberattack Sources To Breach Smartphone Banking For Transferring Funds Digitally Fin SS V. This template helps you present information on one stages. You can also present information on Phishing, Framing, Clickjacking, Man Middle using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Banking Solutions For Improving Customer Potential Cyberattack Sources To Breach Mobile Devices Fin SS V
Banking Solutions For Improving Customer Potential Cyberattack Sources To Breach Mobile Devices Fin SS VIncrease audience engagement and knowledge by dispensing information using Banking Solutions For Improving Customer Potential Cyberattack Sources To Breach Mobile Devices Fin SS V. This template helps you present information on four stages. You can also present information on Config Manipulation, Dynamic Runtime Injection, Unintended Permissions, Escalated Privileges using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Blockchain Cyberattack Identification Workflow Model Guide For Blockchain BCT SS V
Blockchain Cyberattack Identification Workflow Model Guide For Blockchain BCT SS VThe following slide depicts blockchain attack identification workflow. It includes elements such as recording blockchain fingerprints, determining data breaches, aiming to deliver data to manufacturer, stealing and corrupting data, etc. Present the topic in a bit more detail with this Blockchain Cyberattack Identification Workflow Model Guide For Blockchain BCT SS V Use it as a tool for discussion and navigation on Designer, Blockchain, Manufacturer This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Blockchain Cyberattack Securing Blockchain Transactions A Beginners Guide BCT SS V
Blockchain Cyberattack Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide depicts blockchain attack identification workflow. It includes elements such as recording blockchain fingerprints, determining data breaches, aiming to deliver data to manufacturer, stealing and corrupting data, etc. Present the topic in a bit more detail with this Blockchain Cyberattack Securing Blockchain Transactions A Beginners Guide BCT SS V. Use it as a tool for discussion and navigation on Designer, Blockchain, Bad Actor. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Potential Cyberattack Sources To Breach Digital Wallets For Making Hassle Fin SS V
Potential Cyberattack Sources To Breach Digital Wallets For Making Hassle Fin SS VThis slide shows diagram which can be used to understand the potential sources of cyberattacks used by hackers to get through users mobile devices. It is further categorized in four parts which are via browser, system, phone SMS or applications. Introducing Potential Cyberattack Sources To Breach Digital Wallets For Making Hassle Fin SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Browser, System, Storage, using this template. Grab it now to reap its full benefits.
-
 Website Server Security Audit Checklist For Reducing Cyberattacks
Website Server Security Audit Checklist For Reducing CyberattacksFollowing slide highlights checklist for website server security audit to reduce cyberattacks, also including description such as set up essential website framework, incorporate outside services, etc. Introducing our Website Server Security Audit Checklist For Reducing Cyberattacks set of slides. The topics discussed in these slides are Data Safely, Outside Services, Website Extensions. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Computer System Virus Icon For Prevention In DOS Cyberattack
Computer System Virus Icon For Prevention In DOS CyberattackIntroducing our premium set of slides with name Computer System Virus Icon For Prevention In DOS Cyberattack. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Computer System, Virus Icon, Prevention DOS Cyberattack. So download instantly and tailor it with your information.
-
 Network To Limit Cyberattack Damage Business Recovery Plan To Overcome Cyber Security Threat
Network To Limit Cyberattack Damage Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about the implementation of a network segmentation strategy to reduce cyber damage. It further includes key benefits of network segmentation such as improved performance, protect vulnerable devices, and limit damage. Present the topic in a bit more detail with this Network To Limit Cyberattack Damage Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Improve Performance, Protect Devices, Reduce Damage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Mobile Banking Applications Potential Cyberattack Sources To Breach Mobile Fin SS V
Mobile Banking Applications Potential Cyberattack Sources To Breach Mobile Fin SS VThis slide shows diagram which can be used to understand the potential sources of cyberattacks used by hackers to get through users mobile devices. It is further categorized in four parts which are via browser, system, phone or SMS or applications. Introducing Mobile Banking Applications Potential Cyberattack Sources To Breach Mobile Fin SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Browser, System, Phone Sms, Apps, using this template. Grab it now to reap its full benefits.
-
 Access Management Techniques To Prevent Cyberattacks Strategic Guide To Implement Strategy SS
Access Management Techniques To Prevent Cyberattacks Strategic Guide To Implement Strategy SSThis slide showcases Access management techniques to prevent cyber attacks. It includes strategies such as Single sign-On, password management, biometric authentication and access control lists ACLs.Introducing Access Management Techniques To Prevent Cyberattacks Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Password Management, Biometric Authentication, Access Control Lists, using this template. Grab it now to reap its full benefits.
-
 Hacking it reputational damage due to cyberattacks
Hacking it reputational damage due to cyberattacksThis slide represents the reputational damage caused by continuous cyberattacks faced by the company in recent years and the fall of the company in the stock market. Present the topic in a bit more detail with this Hacking It Reputational Damage Due To Cyberattacks. Use it as a tool for discussion and navigation on Reputational Damage Due To Cyberattacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Hacker Reputational Damage Due To Cyberattacks Ppt Pictures Portfolio
Security Hacker Reputational Damage Due To Cyberattacks Ppt Pictures PortfolioThis slide represents the reputational damage caused by continuous cyberattacks faced by the company in recent years and the fall of the company in the stock market. Deliver an outstanding presentation on the topic using this Security Hacker Reputational Damage Due To Cyberattacks Ppt Pictures Portfolio. Dispense information and present a thorough explanation of Cyberattacks, Reputational Damage Due using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
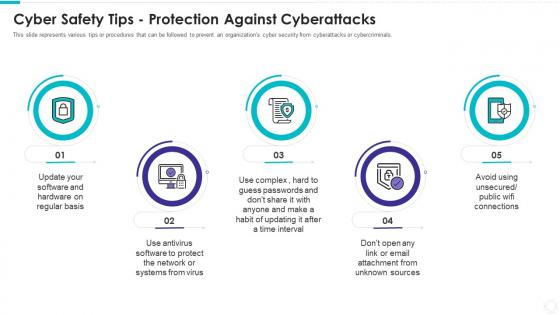 Electronic information security cyber safety tips protection against cyberattacks
Electronic information security cyber safety tips protection against cyberattacksThis slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. Introducing Electronic Information Security Cyber Safety Tips Protection Against Cyberattacks to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Regular Basis, Protect Network, Systems Virustime Interval, Email Attachment Unknown Sources, using this template. Grab it now to reap its full benefits.
-
 Types of cyberattacks waf is designed web application firewall waf it
Types of cyberattacks waf is designed web application firewall waf itThis slide represents the key cyberattacks that a WAF is designed to stop. It includes DDoS attacks, zero day threats, cross site scripting XSS, cookie poisoning, web scrapping, parameter tampering, and SQL injection. Increase audience engagement and knowledge by dispensing information using Types Of Cyberattacks Waf Is Designed Web Application Firewall Waf It. This template helps you present information on eight stages. You can also present information on Parameter Tampering, Vulnerabilities, Service using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Web application firewall waf how waf will protect client company from cyberattacks
Web application firewall waf how waf will protect client company from cyberattacksThis slide depicts what the will WAF mechanism will do to protect information from cyberattacks. It includes session block, IP address block, request block, user block, generating admin alerts, and creating history logs. Introducing Web Application Firewall Waf How Waf Will Protect Client Company From Cyberattacks to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Information, Cyberattacks, Unauthorized, using this template. Grab it now to reap its full benefits.
-
 How can we protect ourselves from cyberattacks ukraine and russia cyber warfare it
How can we protect ourselves from cyberattacks ukraine and russia cyber warfare itThis slide depicts cyberattacks protection methods to follow throughout the country, such as multi factor authentication, data backup, to keep a copy of all the backup information. Increase audience engagement and knowledge by dispensing information using How Can We Protect Ourselves From Cyberattacks Ukraine And Russia Cyber Warfare It. This template helps you present information on three stages. You can also present information on How CAN We Protect Ourselves FROM Cyberattacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ukraine and russia cyber warfare it continued impact of ongoing cyberattacks on internet providers
Ukraine and russia cyber warfare it continued impact of ongoing cyberattacks on internet providersThis slide shows the continued impact of ongoing cyberattacks on Ukrainian internet providers and how these cyberattacks are causing internet outages throughout the country. Introducing Ukraine And Russia Cyber Warfare It Continued Impact Of Ongoing Cyberattacks On Internet Providers to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Continued, Cyberattacks, Providers, using this template. Grab it now to reap its full benefits.
-
 Ukraine and russia cyber warfare it should we be concerned about russian cyberattacks
Ukraine and russia cyber warfare it should we be concerned about russian cyberattacksIncrease audience engagement and knowledge by dispensing information using Ukraine And Russia Cyber Warfare It Should We Be Concerned About Russian Cyberattacks. This template helps you present information on five stages. You can also present information on Should We Be Concerned About Russian Cyberattacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ukraine and russia cyber warfare it steps to prepare for cyberattacks by russia
Ukraine and russia cyber warfare it steps to prepare for cyberattacks by russiaThis slide represents the steps to take right now to prepare for cyberattacks by Russia, including access exposure, minimizing attack surface, executing the basics, and so on. Deliver an outstanding presentation on the topic using this Ukraine And Russia Cyber Warfare It Steps To Prepare For Cyberattacks By Russia. Dispense information and present a thorough explanation of Steps To Prepare For Cyberattacks By Russia using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ukraine and russia cyber warfare it triolan suffers severe cyberattacks during russian invasion
Ukraine and russia cyber warfare it triolan suffers severe cyberattacks during russian invasionThis slide describes the severe cyberattacks and infrastructure destruction experienced by major internet provider Triolan during the Russian Invasion. Increase audience engagement and knowledge by dispensing information using Ukraine And Russia Cyber Warfare It Triolan Suffers Severe Cyberattacks During Russian Invasion. This template helps you present information on six stages. You can also present information on Disruptions, Service, Providers using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security Safety Tips Protection Against Cyberattacks
Information Security Safety Tips Protection Against CyberattacksThis slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. Introducing Information Security Safety Tips Protection Against Cyberattacks to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Safety Tips Protection Against Cyberattacks, using this template. Grab it now to reap its full benefits.
-
 Cyber Attacks On Ukraine Continued Impact Of Ongoing Cyberattacks
Cyber Attacks On Ukraine Continued Impact Of Ongoing CyberattacksThis slide shows the continued impact of ongoing cyberattacks on Ukrainian internet providers and how these cyberattacks are causing internet outages throughout the country. Increase audience engagement and knowledge by dispensing information using Cyber Attacks On Ukraine Continued Impact Of Ongoing Cyberattacks. This template helps you present information on six stages. You can also present information on Disruptions, Assaults, Internet Service, Unsuccessful using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Attacks On Ukraine How Can We Protect Ourselves From Cyberattacks
Cyber Attacks On Ukraine How Can We Protect Ourselves From CyberattacksThis slide depicts cyberattacks protection methods to follow throughout the country, such as multi factor authentication, data backup, to keep a copy of all the backup information. Introducing Cyber Attacks On Ukraine How Can We Protect Ourselves From Cyberattacks to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on How Can We Protect Ourselves From Cyberattacks, using this template. Grab it now to reap its full benefits.
-
 Cyber Attacks On Ukraine Should We Be Concerned About Russian Cyberattacks
Cyber Attacks On Ukraine Should We Be Concerned About Russian CyberattacksThis slide shows that US citizens should not be concerned about Russian cyberattacks as nothing has happened so far. However, the US Department of Homeland Security issued a warning to organizations to look for Russian cyberattacks. Introducing Cyber Attacks On Ukraine Should We Be Concerned About Russian Cyberattacks to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Should We Be Concerned About Russian Cyberattacks, using this template. Grab it now to reap its full benefits.
-
 Cyber Attacks On Ukraine Steps To Prepare For Cyberattacks By Russia
Cyber Attacks On Ukraine Steps To Prepare For Cyberattacks By RussiaThis slide represents the steps to take right now to prepare for cyberattacks by Russia, including access exposure, minimizing attack surface, executing the basics, and so on. Deliver an outstanding presentation on the topic using this Cyber Attacks On Ukraine Steps To Prepare For Cyberattacks By Russia. Dispense information and present a thorough explanation of Steps To Prepare For Cyberattacks By Russia using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
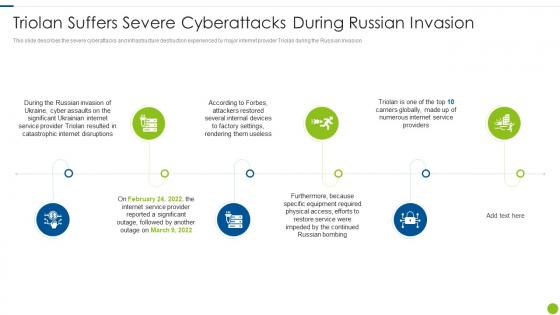 Cyber Attacks On Ukraine Triolan Suffers Severe Cyberattacks During Russian Invasion
Cyber Attacks On Ukraine Triolan Suffers Severe Cyberattacks During Russian InvasionThis slide describes the severe cyberattacks and infrastructure destruction experienced by major internet provider Triolan during the Russian Invasion. Introducing Cyber Attacks On Ukraine Triolan Suffers Severe Cyberattacks During Russian Invasion to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Internet Service, Significant, Equipment, Disruptions, Service, using this template. Grab it now to reap its full benefits.
-
 Wiper Malware Attack Continued Impact Of Ongoing Cyberattacks
Wiper Malware Attack Continued Impact Of Ongoing CyberattacksThis slide shows the continued impact of ongoing cyberattacks on Ukrainian internet providers and how these cyberattacks are causing internet outages throughout the country. Increase audience engagement and knowledge by dispensing information using Wiper Malware Attack Continued Impact Of Ongoing Cyberattacks. This template helps you present information on six stages. You can also present information on Internet Disruptions, Internal Sources, Resilience, Disruptions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Wiper Malware Attack How Can We Protect Ourselves From Cyberattacks
Wiper Malware Attack How Can We Protect Ourselves From CyberattacksThis slide depicts cyberattacks protection methods to follow throughout the country, such as multi factor authentication, data backup, to keep a copy of all the backup information. Introducing Wiper Malware Attack How Can We Protect Ourselves From Cyberattacks to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Technology, Security, Administration, Authentication, using this template. Grab it now to reap its full benefits.
-
 Wiper Malware Attack Should We Be Concerned About Russian Cyberattacks
Wiper Malware Attack Should We Be Concerned About Russian CyberattacksThis slide shows that US citizens should not be concerned about Russian cyberattacks as nothing has happened so far. However, the US Department of Homeland Security issued a warning to organizations to look for Russian cyberattacks. Introducing Wiper Malware Attack Should We Be Concerned About Russian Cyberattacks to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Security, Speculated, Cyberattacks, Unstoppable, using this template. Grab it now to reap its full benefits.
-
 Wiper Malware Attack Steps To Prepare For Cyberattacks By Russia
Wiper Malware Attack Steps To Prepare For Cyberattacks By RussiaThis slide represents the steps to take right now to prepare for cyberattacks by Russia, including access exposure, minimizing attack surface, executing the basics, and so on.Present the topic in a bit more detail with this Wiper Malware Attack Steps To Prepare For Cyberattacks By Russia. Use it as a tool for discussion and navigation on Steps To Prepare For Cyberattacks By Russia. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
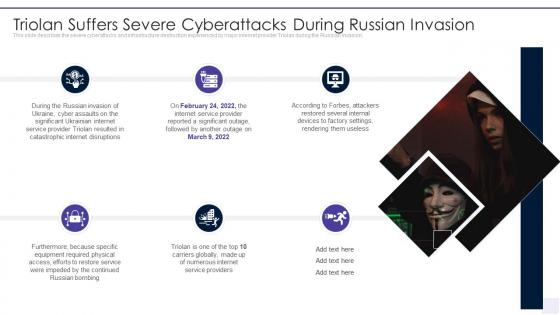 Wiper Malware Attack Triolan Suffers Severe Cyberattacks During Russian Invasion
Wiper Malware Attack Triolan Suffers Severe Cyberattacks During Russian InvasionThis slide describes the severe cyberattacks and infrastructure destruction experienced by major internet provider Triolan during the Russian Invasion. Increase audience engagement and knowledge by dispensing information using Wiper Malware Attack Triolan Suffers Severe Cyberattacks During Russian Invasion. This template helps you present information on six stages. You can also present information on Triolan Suffers Severe Cyberattacks During Russian Invasion using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Technology Security Safety Tips Protection Against Cyberattacks
Information Technology Security Safety Tips Protection Against CyberattacksThis slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. Increase audience engagement and knowledge by dispensing information using Information Technology Security Safety Tips Protection Against Cyberattacks. This template helps you present information on five stages. You can also present information on Cyber Safety Tips Protection Against Cyberattacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Application Firewall How WAF will Protect Client Company from Cyberattacks
Application Firewall How WAF will Protect Client Company from CyberattacksThis slide depicts what the will WAF mechanism will do to protect information from cyberattacks. It includes session block, IP address block, request block, user block, generating admin alerts, and creating history logs. Introducing Application Firewall How WAF will Protect Client Company from Cyberattacks to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Client Company, Cyberattacks, using this template. Grab it now to reap its full benefits.
-
 Application Firewall Types of Cyberattacks WAF is Designed to Stop
Application Firewall Types of Cyberattacks WAF is Designed to StopThis slide represents the key cyberattacks that a WAF is designed to stop. It includes DDoS attacks, zero-day threats, cross-site scripting XSS, cookie poisoning, web scrapping, parameter tampering, and SQL injection. Increase audience engagement and knowledge by dispensing information using Application Firewall Types of Cyberattacks WAF is Designed to Stop. This template helps you present information on eight stages. You can also present information on Zero Day Threats, Web Scraping, Cookie Poisoning using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Continued Impact Of Ongoing Cyberattacks On Internet Providers
Continued Impact Of Ongoing Cyberattacks On Internet ProvidersThis slide shows the continued impact of ongoing cyberattacks on ukrainian internet providers and how these cyberattacks are causing internet outages throughout the country Increase audience engagement and knowledge by dispensing information using Continued Impact Of Ongoing Cyberattacks On Internet Providers. This template helps you present information on six stages. You can also present information on Internet Resilience, Internet Service, Internal Sources using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How Can We Protect Ourselves From Cyberattacks String Of Cyber Attacks Against
How Can We Protect Ourselves From Cyberattacks String Of Cyber Attacks AgainstThis slide depicts cyberattacks protection methods to follow throughout the country, such as multi factor authentication, data backup, to keep a copy of all the backup information. Increase audience engagement and knowledge by dispensing information using How Can We Protect Ourselves From Cyberattacks String Of Cyber Attacks Against. This template helps you present information on three stages. You can also present information on Governments, Backup Copy, Technology using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Should We Be Concerned About Russian Cyberattacks String Of Cyber Attacks Against Ukraine 2022
Should We Be Concerned About Russian Cyberattacks String Of Cyber Attacks Against Ukraine 2022This slide shows that US citizens should not be concerned about russian cyberattacks as nothing has happened so far. However, the US department of homeland security issued a warning to organizations to look for russian cyberattacks. Introducing Should We Be Concerned About Russian Cyberattacks String Of Cyber Attacks Against Ukraine 2022 to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cyberattacks, Online Cyber Fighters, Cyberattacks, using this template. Grab it now to reap its full benefits.
-
 Steps To Prepare For Cyberattacks By Russia String Of Cyber Attacks Against Ukraine 2022
Steps To Prepare For Cyberattacks By Russia String Of Cyber Attacks Against Ukraine 2022This slide represents the steps to take right now to prepare for cyberattacks by russia, including access exposure, minimizing attack surface, executing the basics, and so on. Present the topic in a bit more detail with this Steps To Prepare For Cyberattacks By Russia String Of Cyber Attacks Against Ukraine 2022. Use it as a tool for discussion and navigation on Minimize Your Attack Surface, Execute The Basics, Communicate. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
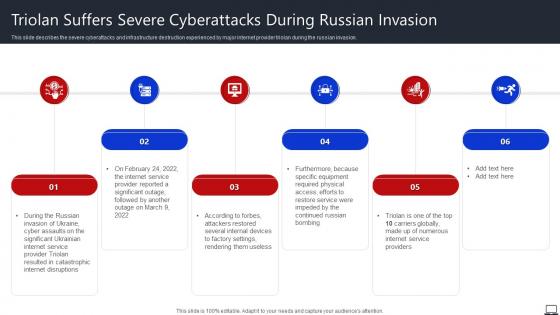 TRIOLAN Suffers Severe Cyberattacks During Russian Invasion String Of Cyber Attacks Against
TRIOLAN Suffers Severe Cyberattacks During Russian Invasion String Of Cyber Attacks AgainstThis slide describes the severe cyberattacks and infrastructure destruction experienced by major internet provider triolan during the russian invasion. Increase audience engagement and knowledge by dispensing information using TRIOLAN Suffers Severe Cyberattacks During Russian Invasion String Of Cyber Attacks Against. This template helps you present information on six stages. You can also present information on Cyber Assaults, Restored Several Internal Devices, Specific Equipment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ultimate Guide For Blockchain Blockchain Cyberattack Identification Workflow Model BCT SS
Ultimate Guide For Blockchain Blockchain Cyberattack Identification Workflow Model BCT SSThe following slide depicts blockchain attack identification workflow. It includes elements such as recording blockchain fingerprints, determining data breaches, aiming to deliver data to manufacturer, stealing and corrupting data, etc. Present the topic in a bit more detail with this Ultimate Guide For Blockchain Blockchain Cyberattack Identification Workflow Model BCT SS Use it as a tool for discussion and navigation on Blockchain Fingerprint, Data Ownership This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Malware Analysis Process To Prevent Future Cyberattacks
Malware Analysis Process To Prevent Future CyberattacksThis slide represents malware analysis insights which benefit organizations to mitigate threat and prevent future occurrences. Steps included in this slide are expanding malware sample size, utilizing automation and secure environment, analyzing malware, etc. Introducing our premium set of slides with name Malware Analysis Process To Prevent Future Cyberattacks. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Expand Malware Sample, Secure Environment, Image Snapshots. So download instantly and tailor it with your information.
-
 Potential Cyberattack Sources Devices Mobile Banking For Convenient And Secure Online Payments Fin SS
Potential Cyberattack Sources Devices Mobile Banking For Convenient And Secure Online Payments Fin SSThis slide shows diagram which can be used to understand the potential sources of cyberattacks used by hackers to get through users mobile devices. It is further categorized in four parts which are via browser, system, phone or SMS or applications. Present the topic in a bit more detail with this Potential Cyberattack Sources Devices Mobile Banking For Convenient And Secure Online Payments Fin SS. Use it as a tool for discussion and navigation on Potential, Cyberattack, Sources . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Security Tools To Prevent Against Cyberattacks
Cloud Security Tools To Prevent Against CyberattacksThe slide showcases top tools to protect business computing against cyberattacks. it highlights crowdstrike falcon, barracuda cloudgen firewall, cloudflare web application firewall, zerospam. Introducing our Cloud Security Tools To Prevent Against Cyberattacks set of slides. The topics discussed in these slides are Crowdstrike Falcon, Barracuda Cloudgen Firewall, Cloudflare, Web Application Firewall. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Potential Cyberattack Sources Comprehensive Guide For Mobile Banking Fin SS V
Potential Cyberattack Sources Comprehensive Guide For Mobile Banking Fin SS VThis slide shows diagram which can be used to understand the potential sources of cyberattacks used by hackers to get through users mobile devices. It is further categorized in four parts which are via browser, system, phone or SMS or applications. Increase audience engagement and knowledge by dispensing information using Potential Cyberattack Sources Comprehensive Guide For Mobile Banking Fin SS V. This template helps you present information on four stages. You can also present information on Browser, System using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyberattacks And Fraud Incidents Implementing Blockchain Security Solutions
Cyberattacks And Fraud Incidents Implementing Blockchain Security SolutionsThis slide outlines a few cyber attacks and fraud incidents that happened in the blockchain infrastructure. The purpose of this slide is to showcase the cyberattacks and fraud that occurred in the past, including code exploitation, stolen keys and employee computer hacking.Present the topic in a bit more detail with this Cyberattacks And Fraud Incidents Implementing Blockchain Security Solutions. Use it as a tool for discussion and navigation on Resulting In Substantial Financial, Bitcoins Belonging, Gain Unauthorized. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Web Application Firewall Introduction It Types Of Cyberattacks WAF Is Designed To Stop
Web Application Firewall Introduction It Types Of Cyberattacks WAF Is Designed To StopThis slide represents the key cyberattacks that a WAF is designed to stop. It includes ddos attacks, zero day threats, cross site scripting XSS, cookie poisoning, web scrapping, parameter tampering, and SQL injection. Introducing Web Application Firewall Introduction It Types Of Cyberattacks WAF Is Designed To Stop. to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Distributed Denial, Zero Day Threats, Cross Site Scripting Xss, using this template. Grab it now to reap its full benefits.




