Powerpoint Templates and Google slides for Cyber Threat Prevention
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Threats In Blockchain Techniques To Prevent Eclipse Attack And Secure Funds BCT SS V
Cyber Threats In Blockchain Techniques To Prevent Eclipse Attack And Secure Funds BCT SS VThe following slide illustrates some methods to minimize the adverse impact of eclipse attack on blockchain network and facilitate security features. It includes elements such as random node selection, deterministic node selection, increased node connections, new node restrictions, etc. Introducing Cyber Threats In Blockchain Techniques To Prevent Eclipse Attack And Secure Funds BCT SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Mining Capability, Mining Capabilities, Much Faster Rate using this template. Grab it now to reap its full benefits.
-
 Cyber Threats In Blockchain Ways To Prevent Blockchain Routing Attacks BCT SS V
Cyber Threats In Blockchain Ways To Prevent Blockchain Routing Attacks BCT SS VThe following slide illustrates some methods to minimize blockchain routing attacks to safeguard network from wrong routing table. It includes elements such as strong passwords, updating firmware, managing access control lists, monitoring logs, etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain Ways To Prevent Blockchain Routing Attacks BCT SS V This template helps you present information on Four stages. You can also present information on Blockchain Routing Attacks, Strong Passwords, Manage Access Control List using this PPT design. This layout is completely editable so personaize it now
-
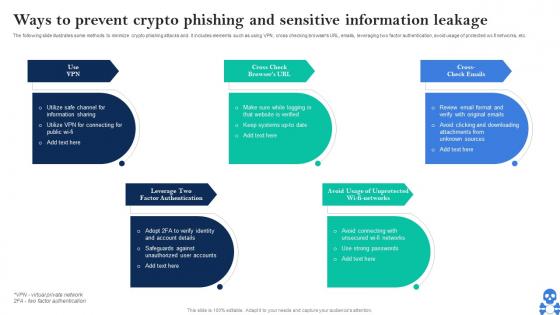 Cyber Threats In Blockchain Ways To Prevent Crypto Phishing And Sensitive Information Leakage BCT SS V
Cyber Threats In Blockchain Ways To Prevent Crypto Phishing And Sensitive Information Leakage BCT SS VThe following slide illustrates some methods to minimize crypto phishing attacks and. it includes elements such as using VPN, cross checking browsers URL, emails, leveraging two factor authentication, avoid usage of protected wi-fi networks, etc. Introducing Cyber Threats In Blockchain Ways To Prevent Crypto Phishing And Sensitive Information Leakage BCT SS V to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Use VPN, Factor Authentication, Avoid Usage Of Unprotected using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Understanding The Cyber Threats Prevented By Waf
Firewall Network Security Understanding The Cyber Threats Prevented By WafThis slide represents the many cyberattacks that a WAF is designed to stop. The purpose of this slide is to showcase the various cyber attacks that can avoided with the help of WAF, such as DDoS attacks, zero-day threats, cross-site scripting XSS, cookie poisoning, web scrapping, parameter tampering, and SQL injection. Introducing Firewall Network Security Understanding The Cyber Threats Prevented By Waf to increase your presentation threshold. Encompassed with Eight stages, this template is a great option to educate and entice your audience. Dispence information on Cookie Poisoning, Sql Injection, Parameter Tampering using this template. Grab it now to reap its full benefits.
-
 Best Practices To Prevent Cyber Attacks Implementing Strategies To Mitigate Cyber Security Threats
Best Practices To Prevent Cyber Attacks Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide illustrates some activities to minimize the probability of cybercrimes within the organization. It includes elements such as utilizing anti virus, preventing to open suspicious emails, keeping systems up to date etc. Introducing Best Practices To Prevent Cyber Attacks Implementing Strategies To Mitigate Cyber Security Threats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Leverage Firewalls, Prevent Opening Suspicious Emails using this template. Grab it now to reap its full benefits.
-
 Cyber Security Threat Icon To Prevent Gap
Cyber Security Threat Icon To Prevent GapPresenting our set of slides with name Cyber Security Threat Icon To Prevent Gap. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security Threat, Icon Prevent Gap.
-
 Types Of Web Security Technologies To Prevent Cyber Threats
Types Of Web Security Technologies To Prevent Cyber ThreatsThis slide covers various types of web security technologies. The purpose of this slide is to help businesses in preventing cyber threats to ensure business protection and compliance. It covers technologies such as web application firewalls, vulnerability scanners, password cracking technologies, etc. Presenting our set of slides with Types Of Web Security Technologies To Prevent Cyber Threats This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Web Application Firewalls, Vulnerability Scanners, Password Cracking Technologies
-
 Kpi Metrics Dashboard To Effectively Track Cyber Threat Preventing Data Breaches Through Cyber Security
Kpi Metrics Dashboard To Effectively Track Cyber Threat Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. Present the topic in a bit more detail with this Kpi Metrics Dashboard To Effectively Track Cyber Threat Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Risk By Threats, Threat Report, Current Risk Status. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Terrorism Prevention Tools Comparative Analysis
Cyber Terrorism Prevention Tools Comparative AnalysisThis slide represents the comparison between various cyber terrorism prevention tools on the basis of their top features, bottom line and the free trials provided. It includes features such as multiple server support, breach severity insights, anti-exploit module etc. Introducing our Cyber Terrorism Prevention Tools Comparative Analysis set of slides. The topics discussed in these slides are Analysis Of Event Logs, Detection Of SQL Injection Attacks, Highly Automated, Comprehensive. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Business Cyber Security Program For Threat Prevention
Business Cyber Security Program For Threat PreventionThis slide covers business cyber security program for threat prevention which includes identify, protect, detect, respond and recover. Presenting our well structured Business Cyber Security Program For Threat Prevention. The topics discussed in this slide are Business Cyber, Security Program, Threat Prevention. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Threat Prevention And Security Process
Cyber Threat Prevention And Security ProcessThis slide shows four steps to provide and assure protection against cyber threats. It includes steps secure perimeter, protect users, network segmentation, determine and control risks. Introducing our premium set of slides with name Cyber Threat Prevention And Security Process. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Secure Perimeter, Smart Network Segmentation, Determine And Control. So download instantly and tailor it with your information.
-
 Cyber Intelligence Initiatives For Threat Prevention Icon
Cyber Intelligence Initiatives For Threat Prevention IconIntroducing our premium set of slides with Cyber Intelligence Initiatives For Threat Prevention Icon. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Intelligence, Initiatives, Threat Prevention Icon. So download instantly and tailor it with your information.
-
 Effective Secops Tools To Prevent Cyber Threats
Effective Secops Tools To Prevent Cyber ThreatsThis slide includes some SecOps tools that provide a more secure working environment to organisations by improving collaboration between operations and security teams. It includes elements such as tools, pricing, features, rating, free version, and free trial. Presenting our well structured Effective Secops Tools To Prevent Cyber Threats. The topics discussed in this slide are Features, Pricing, Tools. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Threat Prevention Detection Correction Icon
Cyber Threat Prevention Detection Correction IconIntroducing our premium set of slides with Cyber Threat Prevention Detection Correction Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Threat Prevention, Detection Correction Icon. So download instantly and tailor it with your information.
-
 Cyber Threat Prevention Detection Correction Plan
Cyber Threat Prevention Detection Correction PlanThis slide presents prevention, detection and correction plan for cybersecurity and management that helps in avoiding critical situations and data loss. It includes plan for technology, processes and human activity that takes place in organisation. Presenting our set of slides with Cyber Threat Prevention Detection Correction Plan. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Vulnerability, Prevention, Detection, Correction.
-
 Cyber threat prevention ppt powerpoint presentation infographics influencers cpb
Cyber threat prevention ppt powerpoint presentation infographics influencers cpbPresenting this set of slides with name Cyber Threat Prevention Ppt Powerpoint Presentation Infographics Influencers Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Cyber Threat Prevention to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Key security controls to prevent cyber threat
Key security controls to prevent cyber threatIntroducing our premium set of slides with Key Security Controls To Prevent Cyber Threat. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Access, Training, Prevention. So download instantly and tailor it with your information.



