Powerpoint Templates and Google slides for Cyber Threat
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Concerns And Solutions Of Implementing Cyber Threat Intelligence
Concerns And Solutions Of Implementing Cyber Threat IntelligenceThis slide showcases the problems and related solutions of implementing cyber threat intelligence which include overloaded data, complicated integration, etc. Deliver an outstanding presentation on the topic using this Concerns And Solutions Of Implementing Cyber Threat Intelligence. Dispense information and present a thorough explanation of Data Overload, Complicated Integration Process, Potential Sense Of Uncertainty, Compatibility Issues using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Threat Intelligence Case Study
Cyber Threat Intelligence Case StudyThis slide represents the cyber threat intelligence case study at Fintech industry including the challenges faced and the solutions provided. Present the topic in a bit more detail with this Cyber Threat Intelligence Case Study. Use it as a tool for discussion and navigation on Conduct Penetration Testing, Perform Thorough Assessments, Vulnerabilities In Registered Domains. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 K160 Cyber Threat Intelligence Life Cycle
K160 Cyber Threat Intelligence Life CycleThis slide represents the process phases of cyber threat intelligence lifecycle such as establishing roadmap, collecting data, etc. Introducing K160 Cyber Threat Intelligence Life Cycle to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Threat, Intelligence Life Cycle, Collect Data To Fulfill Goals, Dissemination, using this template. Grab it now to reap its full benefits.
-
 Cyber Threat Intelligence Operationalize Framework
Cyber Threat Intelligence Operationalize FrameworkThis slide represents cyber threat intelligence operationalize framework with factors such as alerts for monitoring, threat intelligence, etc. Present the topic in a bit more detail with this Cyber Threat Intelligence Operationalize Framework. Use it as a tool for discussion and navigation on Situational Awareness, Threat Intelligence, Alerts For Monitoring, Strategic Reports. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Threat Intelligence Training Schedule
Cyber Threat Intelligence Training ScheduleThis slide outlines the training schedule of cyber threat intelligence which includes three days with different time slots for various learnings. Deliver an outstanding presentation on the topic using this Cyber Threat Intelligence Training Schedule. Dispense information and present a thorough explanation of Setting Up And Configuring, Threat Hunting, Operationalizing Threat Intelligence, Cyber Threat Intelligence using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Elements Of Cyber Threat Intelligence Program
Elements Of Cyber Threat Intelligence ProgramThis slide outlines the various elements of cyber threat intelligence which include people, process, technology, budgeting, etc. Introducing Elements Of Cyber Threat Intelligence Program to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Threat Intelligence Platforms, Budgeting, Technology, Cyber Threat Intelligence Program, using this template. Grab it now to reap its full benefits.
-
 Features Of Cyber Threat Intelligence Platforms
Features Of Cyber Threat Intelligence PlatformsThis slide highlights the characteristic of cyber threat intelligence platform which includes dynamic intelligence feed, smart data virtualization, etc. Increase audience engagement and knowledge by dispensing information using Features Of Cyber Threat Intelligence Platforms. This template helps you present information on five stages. You can also present information on Dynamic Intelligence Feed, Automated Workflows, Smart Data Visualization, Cyber Threat Intelligence Platforms using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Features Of Cyber Threat Intelligence Tools
Features Of Cyber Threat Intelligence ToolsThis slide showcases the various characteristics of cyber threat intelligence tools such as data-driven, flexibility, comprehensiveness, etc. Introducing Features Of Cyber Threat Intelligence Tools to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on External Focused, Cyber Threat Intelligence Tools, Comprehensive, using this template. Grab it now to reap its full benefits.
-
 Features Of Strategic Cyber Threat Intelligence
Features Of Strategic Cyber Threat IntelligenceThis slide discusses the characteristics of strategic cyber threat intelligence which includes the features and objectives. Increase audience engagement and knowledge by dispensing information using Features Of Strategic Cyber Threat Intelligence. This template helps you present information on five stages. You can also present information on Analyzes Geopolitics And Cybersecurity, Aids Decision Making, Guides Cybersecurity Investments using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Features Of Tactical Cyber Threat Intelligence
Features Of Tactical Cyber Threat IntelligenceThis slide showcases the characteristics of tactical cyber threat intelligence which includes its features such as machine readable, automated, etc. Introducing Features Of Tactical Cyber Threat Intelligence to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Threat Intelligence, Easily Generated, Mostly Automated, Machine Readable, using this template. Grab it now to reap its full benefits.
-
 Icons Slide For Cyber Threat Intelligence
Icons Slide For Cyber Threat IntelligenceIntroducing our well researched set of slides titled Icons Slide For Cyber Threat Intelligence. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
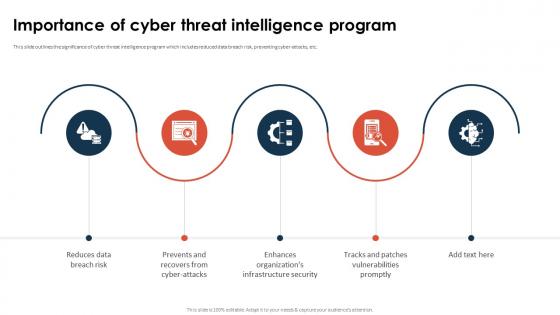 Importance Of Cyber Threat Intelligence Program
Importance Of Cyber Threat Intelligence ProgramThis slide outlines the significance of cyber threat intelligence program which includes reduced data breach risk, preventing cyber-attacks, etc. Increase audience engagement and knowledge by dispensing information using Importance Of Cyber Threat Intelligence Program. This template helps you present information on five stages. You can also present information on Tracks And Patches Vulnerabilities Promptly, Reduces Data Breach Risk, Prevents And Recovers From Cyber Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Introduction Of Cyber Threat Intelligence For Data Security
Introduction Of Cyber Threat Intelligence For Data SecurityThis slide discusses the overview of cyber threat intelligence for proactively blocking attacks and security purpose. Introducing Introduction Of Cyber Threat Intelligence For Data Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Evolving Threats Demand Intelligence, Vital For Security Architecture, Proactively Blocks Attacks, using this template. Grab it now to reap its full benefits.
-
 Key Objectives Of Cyber Threat Intelligence
Key Objectives Of Cyber Threat IntelligenceThis slide discusses the various goals of cyber threat intelligence which includes efficient incident response, powerful vulnerability management, etc. Increase audience engagement and knowledge by dispensing information using Key Objectives Of Cyber Threat Intelligence. This template helps you present information on five stages. You can also present information on Robust Fraud Prevention, Powerful Vulnerability Management, Effective Security Operations, Efficient Incident Response using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Main Benefits Of Cyber Threat Intelligence
Main Benefits Of Cyber Threat IntelligenceThis slide highlights the advantages of cyber threat intelligence which include early identification of threats, danger awareness, etc. Introducing Main Benefits Of Cyber Threat Intelligence to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Early Identification Of Threats, Precise Danger Awareness, Autonomous Reactions, Cyber Threat Intelligence, using this template. Grab it now to reap its full benefits.
-
 Objectives Of Technical Cyber Threat Intelligence
Objectives Of Technical Cyber Threat IntelligenceThis slide outlines the goals of technical cyber threat intelligence which includes security against malicious properties, prevent data theft, etc. Increase audience engagement and knowledge by dispensing information using Objectives Of Technical Cyber Threat Intelligence. This template helps you present information on five stages. You can also present information on Secures Against Malicious Properties, Protects Against Control Of Systems, Block Access To Threat Actors using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Primary Tools For Cyber Threat Intelligence
Primary Tools For Cyber Threat IntelligenceThis slide represents the various tools used for cyber threat intelligence along with their features and cost. Present the topic in a bit more detail with this Primary Tools For Cyber Threat Intelligence. Use it as a tool for discussion and navigation on Cyber Threat Intelligence, Isolated Browser, Data Collection Capabilities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Primary Types Of Cyber Threat Intelligence
Primary Types Of Cyber Threat IntelligenceThis slide highlights the various types if cyber threat intelligence which include strategic, operational, technical, and tactical. Introducing Primary Types Of Cyber Threat Intelligence to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Threat Intelligence, Strategic, Operational, Technical, using this template. Grab it now to reap its full benefits.
-
 Roadmap To Deploy Cyber Threat Intelligence
Roadmap To Deploy Cyber Threat IntelligenceThis slide showcases the steps that an organization should take while deploying cyber threat intelligence such as recognizing needs, assembling data, etc. Increase audience engagement and knowledge by dispensing information using Roadmap To Deploy Cyber Threat Intelligence. This template helps you present information on seven stages. You can also present information on Assemble Data Sources, Recognize Needs And Goals, Gathering And Analyzing Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Steps To Build Cyber Threat Intelligence Framework
Steps To Build Cyber Threat Intelligence FrameworkThis slide outlines the process phases to construct cyber threat intelligence framework such as threat vector identification, compiling intelligence, etc. Introducing Steps To Build Cyber Threat Intelligence Framework to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Threat Vector Identification, Compile Intelligence, Cyber Threat Intelligence Framework, using this template. Grab it now to reap its full benefits.
-
 Strategic Cyber Threat Intelligence Reports
Strategic Cyber Threat Intelligence ReportsThis slide represents what all is included in strategic cyber threat intelligence reports such as policy documents, research reports, etc. Increase audience engagement and knowledge by dispensing information using Strategic Cyber Threat Intelligence Reports. This template helps you present information on five stages. You can also present information on Policy Documents, Whitepaper And Research Reports, Data Loss Statistics using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Contents Cyber Threat Intelligence
Table Of Contents Cyber Threat IntelligenceIntroducing Table Of Contents Cyber Threat Intelligence to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Introduction, Importance, Benefits, Objectives, Cyber Threat Intelligence, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents For Cyber Threat Intelligence
Table Of Contents For Cyber Threat IntelligenceIncrease audience engagement and knowledge by dispensing information using Table Of Contents For Cyber Threat Intelligence. This template helps you present information on twelve stages. You can also present information on Cyber Threat Intelligence Overview, Framework And Deployment, Training And Budget, Relevant Use Cases using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Use Cases Of Cyber Threat Intelligence
Use Cases Of Cyber Threat IntelligenceThis slide discusses the various use cases of cyber threat analysis which include cyber threat feeds, real time alerts, patch prioritization, etc. Introducing Use Cases Of Cyber Threat Intelligence to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Threat Monitoring, Patch Prioritization, Strategic Intelligence Reporting, Operational Intelligence Reporting, using this template. Grab it now to reap its full benefits.
-
 Various Platform Of Cyber Threat Intelligence
Various Platform Of Cyber Threat IntelligenceThis slide discusses the different platforms of cyber threat intelligence which include Anomali ThreatStream, Dataminr Pulse, etc. Deliver an outstanding presentation on the topic using this Various Platform Of Cyber Threat Intelligence. Dispense information and present a thorough explanation of Visualizes Real Time Information, Automatically Updates Data Feeds, Cyber Threat Intelligence using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Emergency Preparedness Icon For Cyber Threat
Emergency Preparedness Icon For Cyber ThreatPresenting our set of slides with Emergency Preparedness Icon For Cyber Threat. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Emergency, Preparedness, Cyber Threat.
-
 Threats Faced In Fintech Cyber Security
Threats Faced In Fintech Cyber SecurityThis slide showcases the threats faced in fintech cyber security. Its use is to face threats in fintech cyber security and help protect against zero day attacks. This slide includes spoofing, ransomware, organisation, malware, etc. Introducing our premium set of slides with name Threats Faced In Fintech Cyber Security. Ellicudate the nine stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like DDOS, Advanced Threats, Phishing, Sniffing, Malware. So download instantly and tailor it with your information.
-
 Solutions For Threat Of Cyber Security In Digital Banking
Solutions For Threat Of Cyber Security In Digital BankingThis slide represents remedies to cyber security problem in internet banking. It aims to adopt holistic and proactive approach to cyber security that encompasses technology, processes, and people. It includes various solutions such as integrated security, protecting information, etc. Introducing our premium set of slides with Solutions For Threat Of Cyber Security In Digital Banking. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Integrated Security, Security Integration, Spent Money. So download instantly and tailor it with your information.
-
 IT Security Awareness Training Defense Against Cyber Threats Cybersecurity SS
IT Security Awareness Training Defense Against Cyber Threats Cybersecurity SSThis slide represents details related to ways security awareness training helps in preventing and mitigating common threats faced by organization such as data breaches, phishing attacks etc. Deliver an outstanding presentation on the topic using this IT Security Awareness Training Defense Against Cyber Threats Cybersecurity SS. Dispense information and present a thorough explanation of Data Breaches, Phishing Attacks, Insider Threats, Social Engineering using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Crisis Management Icon For Threat Mitigation
Cyber Crisis Management Icon For Threat MitigationIntroducing our premium set of slides with name Cyber Crisis Management Icon For Threat Mitigation. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Crisis Management, Threat Mitigation. So download instantly and tailor it with your information.
-
 Cyber Threat Detection Data Encryption Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Threat Detection Data Encryption Colored Icon In Powerpoint Pptx Png And Editable Eps FormatSecure your digital assets with our Cloud-based endpoint cyber security icon for PowerPoint. Featuring a bold and vibrant design, this icon represents the protection and peace of mind offered by our cutting-edge security solutions. Perfect for presentations on cloud security, data protection, and cyber threats. Download now and enhance your slides.
-
 Cyber Threat Detection Data Encryption Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Threat Detection Data Encryption Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon represents a cloud-based endpoint cyber security solution. It is designed to protect your digital assets from external threats, providing real-time monitoring and threat detection. With its user-friendly interface and advanced features, it offers a comprehensive and reliable solution for safeguarding your data and devices.
-
 Cyber Threats Digital Resilience Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Threats Digital Resilience Colored Icon In Powerpoint Pptx Png And Editable Eps FormatEnhance your digital transformation journey with our vibrant cyber security PowerPoint icon. This eye-catching icon features a lock symbol in bold colors, representing the importance of protecting your digital assets. Perfect for presentations and reports on cyber security, this icon will add a professional touch to your content.
-
 Cyber Threats Digital Resilience Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Threats Digital Resilience Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone PowerPoint icon is designed to represent cyber security in the context of digital transformation. It features a simple yet impactful design, making it perfect for use in presentations, reports, and other digital materials related to cyber security and its role in modern technology.
-
 Automated Cyber Threat Hunting Overview
Automated Cyber Threat Hunting OverviewThis slide gives an overview of an automated cyber threat-hunting process that uses artificial intelligence and machine learning algorithms for threat detection. Increase audience engagement and knowledge by dispensing information using Automated Cyber Threat Hunting Overview. This template helps you present information on four stages. You can also present information on Automated Cyber, Threat Hunting Overview, Machine Learning Algorithms, Threat Detection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Benefits Of Threat Hunting In Cyber Security
Benefits Of Threat Hunting In Cyber SecurityThis slide outlines the advantages of cyber threat hunting, such as early detection of threats, reducing false alarms, shortening incident investigation time, etc. Increase audience engagement and knowledge by dispensing information using Benefits Of Threat Hunting In Cyber Security. This template helps you present information on four stages. You can also present information on Threat Hunting, Cyber Security, Incident Investigation Time, Early Detection Of Threats using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices To Improve Cyber Threat Hunting
Best Practices To Improve Cyber Threat HuntingThis slide showcases various best practices for effective cyber threat hunting, including utilizing external tools when necessary, recording methods and code, etc. Introducing Best Practices To Improve Cyber Threat Hunting to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Foster Collaboration, Avoid Isolation, Improve Coding Skills, Record The Methods And Code, using this template. Grab it now to reap its full benefits.
-
 Core Cyber Threat Hunting Techniques
Core Cyber Threat Hunting TechniquesThis slide outlines the main cyber threat hunting techniques, such as baseline, attack-specific hunts, time sensitivity, and third-party sources. Increase audience engagement and knowledge by dispensing information using Core Cyber Threat Hunting Techniques. This template helps you present information on four stages. You can also present information on Attack Specific Hunts, Baselining, Time Sensitivity, Third Party Sources using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Threat Hunting Case Study
Cyber Threat Hunting Case StudyThis slide outlines the case study for cyber threat hunting in North Haven, Connecticut, including background, problems, solutions and impact. Introducing Cyber Threat Hunting Case Study to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Threat Hunting Case Study, Problems, Solutions And Impact, using this template. Grab it now to reap its full benefits.
-
 Cyber Threat Hunting Challenges And Solutions
Cyber Threat Hunting Challenges And SolutionsThis slide outlines the challenges and solutions associated with the cyber threat hunting process, such as hiring experts, collecting data, and so on. Deliver an outstanding presentation on the topic using this Cyber Threat Hunting Challenges And Solutions. Dispense information and present a thorough explanation of Deploying Expert Threat Hunters, Collecting Comprehensive Data, Implement Data Aggregation Tools using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Threat Hunting Model Types
Cyber Threat Hunting Model TypesThis slide represents the various cyber threat hunting model types, such as intel-based hunting, hypothesis hunting, and custom hunting. Increase audience engagement and knowledge by dispensing information using Cyber Threat Hunting Model Types. This template helps you present information on three stages. You can also present information on Hypothesis Hunting, Custom Hunting, Intel Based Hunting using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Threat Hunting Training Program
Cyber Threat Hunting Training ProgramThis slide outlines the training program schedule for the cyber threat hunting process, including the time of training and the modules to be covered. Present the topic in a bit more detail with this Cyber Threat Hunting Training Program. Use it as a tool for discussion and navigation on Cyber Threat Hunting, Training Program, Time Of Training, Indicators Of Attack Investigation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective Cyber Threat Hunting Tools
Effective Cyber Threat Hunting ToolsThis slide enlists effective cyber threat hunting tools, including managed detection and response, security information and event management, security analysis, etc. Deliver an outstanding presentation on the topic using this Effective Cyber Threat Hunting Tools. Dispense information and present a thorough explanation of Managed Detection And Response, Security Information, Event Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Important Elements Of Cyber Threat Hunting
Important Elements Of Cyber Threat HuntingThis slide represents the critical elements required for cyber threat hunting, such as tools and technology, human hunters, data, organization model, etc. Introducing Important Elements Of Cyber Threat Hunting to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Human Hunters, Tools And Technology, Organizational Model, Threat Intelligence, using this template. Grab it now to reap its full benefits.
-
 Introduction To Threat Hunting In Cyber Security
Introduction To Threat Hunting In Cyber SecurityThis slide gives an overview of the cyber threat hunting process for network and data security. It detects threats that bypass the initial defenses. Increase audience engagement and knowledge by dispensing information using Introduction To Threat Hunting In Cyber Security. This template helps you present information on six stages. You can also present information on Threat Hunting In Cyber Security, Bypass The Initial Defenses, Cyber Threat Hunting Process using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Parties Involved In Cyber Threat Hunting
Parties Involved In Cyber Threat HuntingThis slide outlines the various parties involved in cyber threat hunting, such as clients, threat intelligence, forensics, SIEM experts, forensics, etc. Present the topic in a bit more detail with this Parties Involved In Cyber Threat Hunting. Use it as a tool for discussion and navigation on Advanced Hunting Procedures, Potential Breaches, Incidents Leads. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Steps Of Cyber Threat Hunting Process
Steps Of Cyber Threat Hunting ProcessThis slide outlines the main steps of the cyber threat hunting process, covering hypothesis, data collection, trigger, investigation, and response. Present the topic in a bit more detail with this Steps Of Cyber Threat Hunting Process. Use it as a tool for discussion and navigation on Hypothesis, Cyber Threat Hunting Process, Formulate Initial Ideas, Probe Potential Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Timeline For Conducting Cyber Threat Hunting
Timeline For Conducting Cyber Threat HuntingThis slide represents the implementation timeline for the cyber threat hunting process, including all the steps to be performed at different intervals. Increase audience engagement and knowledge by dispensing information using Timeline For Conducting Cyber Threat Hunting. This template helps you present information on six stages. You can also present information on Assessment And Planning, Tool Selection And Acquisition, Initial Implementation And Testing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Top Cyber Threat Hunting Frameworks
Top Cyber Threat Hunting FrameworksThis slide outlines the best cyber threat hunting frameworks, such as the Sqrrl threat hunting reference model, targeted hunting integrating threat intelligence, and peak. Deliver an outstanding presentation on the topic using this Top Cyber Threat Hunting Frameworks. Dispense information and present a thorough explanation of Hunting Reference Model, Targeted Hunting Integrating, Threat Intelligence, Cyber Threat Hunting using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Typical Cyber Threat Hunting Process
Typical Cyber Threat Hunting ProcessThis slide showcases the typical cyber threat hunting process, such as creating a hypothesis, conducting a search, validating, adjusting, and broadening the scope. Present the topic in a bit more detail with this Typical Cyber Threat Hunting Process. Use it as a tool for discussion and navigation on Respond To Incidents, Generate New Detection Content, Adjust And Broaden Scope, Create A Hypothesis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Working Principles Of Cyber Threat Hunting
Working Principles Of Cyber Threat HuntingThis slide describes the main principles of the cyber threat hunting process, such as selecting a target, creating a hypothesis, collecting data, analyzing data, etc. Deliver an outstanding presentation on the topic using this Working Principles Of Cyber Threat Hunting. Dispense information and present a thorough explanation of Select Target, Form Hypothesis, Gather Data, Analyze Data, Draw Conclusions using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Working Process Of Cyber Threat Hunting
Working Process Of Cyber Threat HuntingThis slide outlines the working process model of cyber threat hunting, including layers such as IoC hunting, intelligence-based hunting, post-incident, etc. Present the topic in a bit more detail with this Working Process Of Cyber Threat Hunting. Use it as a tool for discussion and navigation on Indicators Of Compromise Hunting, Incident Hunting, Anomaly Detections, Infection Readiness. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Threat Analyst Jobs In Powerpoint And Google Slides Cpp
Cyber Threat Analyst Jobs In Powerpoint And Google Slides CppPresenting Cyber Threat Analyst Jobs In Powerpoint And Google Slides Cpp slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cyber Threat Analyst Jobs. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Education And Awareness Campaigns For Cyber Terrorism Strategic Guide To Implement Strategy SS
Education And Awareness Campaigns For Cyber Terrorism Strategic Guide To Implement Strategy SSThis slide showcases the Education and Awareness Campaigns for cyber terrorism. It includes best practices such as Government and Industry Partnership, Interactive Training, Public-Private Partnerships and Online Resources.Increase audience engagement and knowledge by dispensing information using Education And Awareness Campaigns For Cyber Terrorism Strategic Guide To Implement Strategy SS. This template helps you present information on four stages. You can also present information on Interactive Training, Government And Industry Partnerships, Public Private Partnerships, Online Resources using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Incident Response And Recovery Strategies For Cyber Terrorism Strategic Guide To Implement Strategy SS
Incident Response And Recovery Strategies For Cyber Terrorism Strategic Guide To Implement Strategy SSThis slide showcases the Incident Response and Recovery Strategies for cyber terrorism. It includes strategies such as Incident Identification, Containment and Mitigation, Data Restoration and Resilience.Present the topic in a bit more detail with this Incident Response And Recovery Strategies For Cyber Terrorism Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Containment And Mitigation, Incident Identification, Eradication, Forensics And Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Introduction To Cyber Terrorism And Its Impact Strategic Guide To Implement Strategy SS
Introduction To Cyber Terrorism And Its Impact Strategic Guide To Implement Strategy SSThis slide showcases the introduction to cyber terrorism. It includes its impact such as financial losses, economic impact, data breaches, political instability and social disruption.Deliver an outstanding presentation on the topic using this Introduction To Cyber Terrorism And Its Impact Strategic Guide To Implement Strategy SS. Dispense information and present a thorough explanation of Economic Impact, Data Breaches, Social Disruption, Political Instability using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Introduction To Types Of Cyber Threat Actors Strategic Guide To Implement Strategy SS
Introduction To Types Of Cyber Threat Actors Strategic Guide To Implement Strategy SSThis slide showcases the market scenario of global automobile industry. It includes elements such as top worlds vehicle producers, number of cars sold worldwide and preference for type of engine in next vehicle.Introducing Introduction To Types Of Cyber Threat Actors Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Thrill Seekers, Cybercriminal Actors, Insiders, Hacktivists Actors, using this template. Grab it now to reap its full benefits.
-
 Cyber Threats For Synthetic Biology In Powerpoint And Google Slides CPP
Cyber Threats For Synthetic Biology In Powerpoint And Google Slides CPPPresenting Cyber Threats For Synthetic Biology In Powerpoint And Google Slides CPP slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cyber Threats For Synthetic Biology. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Contingency Plan Icon For Cyber Threat Mitigation
Contingency Plan Icon For Cyber Threat MitigationIntroducing our Contingency Plan Icon For Cyber Threat Mitigation set of slides. The topics discussed in these slides areContingency Plan Icon, Cyber Threat Mitigation This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Pptx cyber terrorism cyber crime ppt background
Pptx cyber terrorism cyber crime ppt backgroundPresenting pptx cyber terrorism cyber crime ppt background. This is a cyber terrorism cyber crime ppt background. This is a five stage process. The stages in this process are security threats, cyber terrorism, cyber espionage, cyber war, cyber line.





