Powerpoint Templates and Google slides for Cyber Security Threat
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Develop RACI Chart For Team Collaboration Implementing Strategies To Mitigate Cyber Security Threats
Develop RACI Chart For Team Collaboration Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the RACI accountable, consulted, responsible, informed plan to facilitate and ensure speedy communication during cyber issue management. It includes activities such as overall coordination, media messaging, internal communication, technical assistance etc. Present the topic in a bit more detail with this Develop RACI Chart For Team Collaboration Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Accountable, Consulted, Responsible This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encrypt And Create Backup Of Useful Data Implementing Strategies To Mitigate Cyber Security Threats
Encrypt And Create Backup Of Useful Data Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide illustrates various methods to encrypt and back up key data to avoid information loss and improved accessibility. It includes elements such as network attached storage, cloud storage services, flat backup system, details, advantages, disadvantages, cost, Deliver an outstanding presentation on the topic using this Encrypt And Create Backup Of Useful Data Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Network Attached Storage, Cloud Storage Services, Flat Backup System using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Global Cyber Security Trend Analysis Implementing Strategies To Mitigate Cyber Security Threats
Global Cyber Security Trend Analysis Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the key statistics about cyber security trends to project future performance. It mainly includes elements such as increase in ransomware attacks, average data breach costs, approximate number of businesses prone to cyber attacks etc. Increase audience engagement and knowledge by dispensing information using Global Cyber Security Trend Analysis Implementing Strategies To Mitigate Cyber Security Threats This template helps you present information on six stages. You can also present information on Attack, Data Breaches, Cyber Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide Implementing Strategies To Mitigate Cyber Security Threats
Icons Slide Implementing Strategies To Mitigate Cyber Security ThreatsIntroducing our well researched set of slides titled Icons Slide Implementing Strategies To Mitigate Cyber Security Threats It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Identifying Impact Of Cyber Attack On Business Implementing Strategies To Mitigate Cyber Security Threats
Identifying Impact Of Cyber Attack On Business Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the negative impact of cyber crimes on business to build control actions and strategies. It includes key elements such as rising costs, reputational damage, operational disruption, loss of revenue etc. Introducing Identifying Impact Of Cyber Attack On Business Implementing Strategies To Mitigate Cyber Security Threats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Rising Cost, Reputational Damage, Operational Disruption using this template. Grab it now to reap its full benefits.
-
 Impact Of Cyber Safety Security Measures Implementing Strategies To Mitigate Cyber Security Threats
Impact Of Cyber Safety Security Measures Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the projected consequences of implementing cyber security preventive measures. It includes data about number of cyber attracts pre and post adopting latest strategies Present the topic in a bit more detail with this Impact Of Cyber Safety Security Measures Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Cyber Attack Type, Malware, Ransomware This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Of Cyber Security Policies And Practices Implementing Strategies To Mitigate Cyber Security Threats
Impact Of Cyber Security Policies And Practices Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions, Deliver an outstanding presentation on the topic using this Impact Of Cyber Security Policies And Practices Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Inadequate Security Guidelines, Inappropriate Privacy Policies, Insufficient Background Check using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implement Automated Patch Management Solution Implementing Strategies To Mitigate Cyber Security Threats
Implement Automated Patch Management Solution Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the automated patch management process to fix software vulnerabilities and ensure smooth functioning of systems. It includes activities such as scanning of systems, requesting to take back up etc. Present the topic in a bit more detail with this Implement Automated Patch Management Solution Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Vulnerability Assessment, Request Cancelled, Asset Inventory This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Strategies To Mitigate Cyber Security Threats Table Of Content
Implementing Strategies To Mitigate Cyber Security Threats Table Of ContentIncrease audience engagement and knowledge by dispensing information using Implementing Strategies To Mitigate Cyber Security Threats Table Of Content This template helps you present information on one stages. You can also present information on Cyber Security, Cyber Risk using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 KPIs To Evaluate Cyber Security Risk Management Implementing Strategies To Mitigate Cyber Security Threats
KPIs To Evaluate Cyber Security Risk Management Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide highlights some key performance indicators to measure the impact of cyber security risk administration to assess its effectiveness and take improved decisions. It includes elements such as level of preparedness, mean time to detect, success rating etc. Present the topic in a bit more detail with this KPIs To Evaluate Cyber Security Risk Management Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Level Of Preparedness, Mean Time To Detect, Mean Time To Resolve This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Leverage Strong And Complex Password Management Implementing Strategies To Mitigate Cyber Security Threats
Leverage Strong And Complex Password Management Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide illustrates some practices to ensure strong password management and restrict access to data. It includes activities such as avoiding weak passwords, encryption, multi factor authentication, conducting test etc. Introducing Leverage Strong And Complex Password Management Implementing Strategies To Mitigate Cyber Security Threats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Conduct Password Test, Password Encryption, Multi Factor Authentication using this template. Grab it now to reap its full benefits.
-
 Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security Threats
Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Present the topic in a bit more detail with this Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Information Security And Privacy, Physical Assets And Data Security, Web Application Security This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Organize Cyber Security Training For Employees Implementing Strategies To Mitigate Cyber Security Threats
Organize Cyber Security Training For Employees Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the staff cyber security training plan to educate them regarding technology threats and practices. It mainly includes elements such as topics to be covered, target audience, trainer name, mode, proposed date, timings etc. Deliver an outstanding presentation on the topic using this Organize Cyber Security Training For Employees Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Document Management, Target Audience, Proposed Date using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Plan Useful Data Backup Schedule Implementing Strategies To Mitigate Cyber Security Threats
Plan Useful Data Backup Schedule Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the monthly calendar for data backup to advance cybersecurity protection and loss of information. It mainly includes techniques such as fully and incremental data backup etc. Increase audience engagement and knowledge by dispensing information using Plan Useful Data Backup Schedule Implementing Strategies To Mitigate Cyber Security Threats This template helps you present information on one stages. You can also present information on Time Consuming Process, Speedy Process, Incremental Backup using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Run Penetration Testing To Review Risk Implementing Strategies To Mitigate Cyber Security Threats
Run Penetration Testing To Review Risk Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases various methods to review cyber risks to determine probability and impact of risks. It includes elements such as penetration, red team and risk based testing along with objectives, features, cost, outcomes, duration etc. Present the topic in a bit more detail with this Run Penetration Testing To Review Risk Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Objectives, Features, Duration This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Select Cybersecurity Training Program Courses Implementing Strategies To Mitigate Cyber Security Threats
Select Cybersecurity Training Program Courses Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the best cybersecurity training courses to educate employees and minimize the possibility of cyber attacks. It includes cloud, disaster recovery, hardware, information security programs, duration, mode and cost Deliver an outstanding presentation on the topic using this Select Cybersecurity Training Program Courses Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Cloud Security, Information Security, Disaster Recovery using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Select Tools To Reduce Cyber Security Failure Implementing Strategies To Mitigate Cyber Security Threats
Select Tools To Reduce Cyber Security Failure Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide highlights some best tools to track and minimize the impact of cyber risks. It includes elements such as tool anme, features, trial period, cost and reviews etc. Present the topic in a bit more detail with this Select Tools To Reduce Cyber Security Failure Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Features, Free Trial, Cost This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents Implementing Strategies To Mitigate Cyber Security Threats
Table Of Contents Implementing Strategies To Mitigate Cyber Security ThreatsIncrease audience engagement and knowledge by dispensing information using Table Of Contents Implementing Strategies To Mitigate Cyber Security Threats This template helps you present information on one stages. You can also present information on Industry Overview, Current Scenario Analysis, Cyber Security Plan using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Types Of Cyber Attacks Encountered By Employees Implementing Strategies To Mitigate Cyber Security Threats
Types Of Cyber Attacks Encountered By Employees Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the various types of cyber attacks faced by staff to determine and formulate action plan. It includes elements such as malware, ransomware, man in the middle, phishing, denial of service tec. Introducing Types Of Cyber Attacks Encountered By Employees Implementing Strategies To Mitigate Cyber Security Threats to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Malware, Ransomware, Phishing using this template. Grab it now to reap its full benefits.
-
 Firewall Security Icon Protecting From Cyber Threats
Firewall Security Icon Protecting From Cyber ThreatsIntroducing our Firewall Security Icon Protecting From Cyber Threats set of slides. The topics discussed in these slides are Firewall Security, Protecting. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Advantages Of Utilizing Advanced Threat Protection In Cyber Security
Advantages Of Utilizing Advanced Threat Protection In Cyber SecurityThe following slide highlights the possible benefits of implementing advanced threat protection against sophisticated cyber threats and attacks. Presenting our set of slides with Advantages Of Utilizing Advanced Threat Protection In Cyber Security. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security, Analytics, Protection.
-
 IoT Cyber Security Technologies For Advanced Threat Protection
IoT Cyber Security Technologies For Advanced Threat ProtectionThe purpose of this slide is to showcase various types of Internet of Things IoT security technologies that assists in safeguarding cyber threats. Introducing our premium set of slides with IoT Cyber Security Technologies For Advanced Threat Protection. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Architecture, Security, Computing. So download instantly and tailor it with your information.
-
 Saas Cyber Security Icon For Threat Mitigation
Saas Cyber Security Icon For Threat MitigationIntroducing our premium set of slides with Saas Cyber Security Icon For Threat Mitigation Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Saas Cyber Security Icon, Threat Mitigation. So download instantly and tailor it with your information.
-
 Impact Of Cyber Security Threats On Organisational Policy
Impact Of Cyber Security Threats On Organisational PolicyThis slide covers the negative impacts of prevalent cybersecurity threats. This template aims to highlight two key negative impacts of threats, including DNS Attacks, SQL Injection, Malware, Phishing, and Ransomware. Presenting our set of slides with Impact Of Cyber Security Threats On Organisational Policy This exhibits information on Six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Malware, DNS Attack, SQL Injection
-
 Implementing Strategies To Mitigate Cyber Security Threats Prioritize Cyber Security Risk With Severity Matrix
Implementing Strategies To Mitigate Cyber Security Threats Prioritize Cyber Security Risk With Severity MatrixThe following slide depicts cyber security risk assessment grid to prioritize and eliminate occurrence of threats. It includes elements such as moderate, severe, minor, negligible, rate, possible, likely, unlikely etc. Introducing Implementing Strategies To Mitigate Cyber Security Threats Prioritize Cyber Security Risk With Severity Matrix to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Very Severe, Severe, Moderate using this template. Grab it now to reap its full benefits.
-
 ATP Cyber Security Threat Detection System
ATP Cyber Security Threat Detection SystemThis slide depicts the ATP cyber security detection system. Its aim is to use various approach to kill off any threats during cyber attack. This slide includes multilayer approach, behavioural analysis, machine learning, sand boxing, threat intelligence, etc. Presenting our set of slides with name ATP Cyber Security Threat Detection System. This exhibits information on Nine stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Multilayered Approach, Behavioural Analysis, Machine Learning, Threat Intelligence, Endpoint Detection.
-
 Cyber Security Threat Icon To Prevent Gap
Cyber Security Threat Icon To Prevent GapPresenting our set of slides with name Cyber Security Threat Icon To Prevent Gap. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security Threat, Icon Prevent Gap.
-
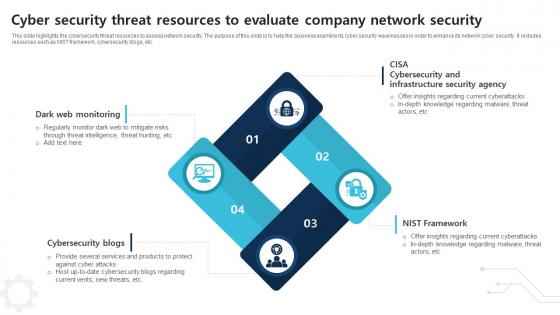 Cyber Security Threat Resources To Evaluate Company Network Security
Cyber Security Threat Resources To Evaluate Company Network SecurityThis slide highlights the cybersecurity threat resources to assess network security. The purpose of this slide is to help the business examine its cyber security weaknesses in order to enhance its network cyber security. It includes resources such as NIST framework, cybersecurity blogs, etc. Introducing our premium set of slides with Cyber Security Threat Resources To Evaluate Company Network Security Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Dark Web Monitoring, Cybersecurity Blogs, Nist Framework So download instantly and tailor it with your information.
-
 Cyber Security Online Threat Control Icon
Cyber Security Online Threat Control IconPresenting our set of slides with Cyber Security Online Threat Control Icon This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security Online Threat Control Icon
-
 Types Of Web Security Technologies To Prevent Cyber Threats
Types Of Web Security Technologies To Prevent Cyber ThreatsThis slide covers various types of web security technologies. The purpose of this slide is to help businesses in preventing cyber threats to ensure business protection and compliance. It covers technologies such as web application firewalls, vulnerability scanners, password cracking technologies, etc. Presenting our set of slides with Types Of Web Security Technologies To Prevent Cyber Threats This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Web Application Firewalls, Vulnerability Scanners, Password Cracking Technologies
-
 Cyber Security Management Strategies To Mitigate Threats
Cyber Security Management Strategies To Mitigate ThreatsThis slide highlights different strategies that can help businesses in reducing cyber security threats. It further covers attributes such as priority level, description, mitigating strategies, etc. Presenting our well structured Cyber Security Management Strategies To Mitigate Threats. The topics discussed in this slide are Information Disclosure, Service Denial, Tampering. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Impact Analysis Of Cyber Security Threats In Automotive Industry
Impact Analysis Of Cyber Security Threats In Automotive IndustryThis slide highlights influence assessment cyber security risks in automobile industry. The purpose of this slide is to aid businesses in evaluating potential consequences of digital factors. It includes elements such as data privacy, supply chain disruption, etc. Introducing our premium set of slides with Impact Analysis Of Cyber Security Threats In Automotive Industry Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Privacy, Intellectual Property, Supply Chain Disruption So download instantly and tailor it with your information.
-
 Threats Eliminated By Hids Cyber Security
Threats Eliminated By Hids Cyber SecurityThis slide represents threats eliminated by HIDS cyber security which detects suspicious activities and generates alerts when they are detected. It includes threats eliminated by HIDS cyber security such as malicious attacks, asymmetric routing, etc. Presenting our set of slides with Threats Eliminated By Hids Cyber Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Malicious Attacks, Asymmetric Routing, Buffer Overflow Attacks.
-
 Cyber Threat Intelligence Security Control Solutions
Cyber Threat Intelligence Security Control SolutionsThis slide showcases cyber threat intelligence security control which helps managers improve threat detection and organizational defence capabilities. It includes elements such as strategic, tactical, operational, technical, high level, low level, short term use and long term use. Introducing our premium set of slides with name Cyber Threat Intelligence Security Control Solutions. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Strategic, Tactical, Operational, Technical. So download instantly and tailor it with your information.
-
 Cyber Threat Intelligence Security Icon
Cyber Threat Intelligence Security IconPresenting our set of slides with name Cyber Threat Intelligence Security Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Threat, Intelligence Security.
-
 Access With Cloud Storage Solution Business Recovery Plan To Overcome Cyber Security Threat
Access With Cloud Storage Solution Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about access management with a cloud storage solution. It includes file sharing with cloud platforms and selection criteria such as storage space, privacy and security, and other benefits. Present the topic in a bit more detail with this Access With Cloud Storage Solution Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Storage Space, Privacy And Security, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Agenda Business Recovery Plan To Overcome Cyber Security Threat
Agenda Business Recovery Plan To Overcome Cyber Security ThreatIntroducing Agenda Business Recovery Plan To Overcome Cyber Security Threat to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Business, Financial, Operations, using this template. Grab it now to reap its full benefits.
-
 Alternative For Managing Cyber Threats Business Recovery Plan To Overcome Cyber Security Threat
Alternative For Managing Cyber Threats Business Recovery Plan To Overcome Cyber Security ThreatIncrease audience engagement and knowledge by dispensing information using Alternative For Managing Cyber Threats Business Recovery Plan To Overcome Cyber Security Threat. This template helps you present information on five stages. You can also present information on Staff Training, End Point Protection, Wifi Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Automated Patch Management Process Business Recovery Plan To Overcome Cyber Security Threat
Automated Patch Management Process Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about system patch management to determine vulnerabilities after cyber attack. It includes key process of automated patch management and best practices such as schedule patching, prioritization, and patch testing. Deliver an outstanding presentation on the topic using this Automated Patch Management Process Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Management, Process, Vulnerability using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Business Goals Achievement Duration Business Recovery Plan To Overcome Cyber Security Threat
Business Goals Achievement Duration Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about time-based goals achieved for cyber attack management. It includes goals such as mean time to detect incidents, containment time, resolution time, and recovery time. Present the topic in a bit more detail with this Business Goals Achievement Duration Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Mean Time To Recover, Mean Time To Resolve, Mean Time To Contain. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Business Plan Implementation Roadmap Business Recovery Plan To Overcome Cyber Security Threat
Business Plan Implementation Roadmap Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about business cyber security attack recovery plan. It includes key steps such as setting time based recovery goals, impact and risk assessment, build recovery team, communication plan, recovery strategies implementation, etc. Introducing Business Plan Implementation Roadmap Business Recovery Plan To Overcome Cyber Security Threat to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Assessment, Communication Plan, Recovery Strategies Implementation, using this template. Grab it now to reap its full benefits.
-
 Business Plan To Overcome Cyber Security Threat Table Of Contents
Business Plan To Overcome Cyber Security Threat Table Of ContentsIncrease audience engagement and knowledge by dispensing information using Business Plan To Overcome Cyber Security Threat Table Of Contents. This template helps you present information on one stages. You can also present information on Business, Communication, External Stakeholders using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Case Study Construction Management Company Business Recovery To Overcome Cyber Security Threat
Case Study Construction Management Company Business Recovery To Overcome Cyber Security ThreatMentioned slide provides information about a case study related to a ransomware attack on the construction company. It includes key elements such as situation detail, adopted strategies, and outcomes. Deliver an outstanding presentation on the topic using this Case Study Construction Management Company Business Recovery To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Construction, Management, Ransomware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Case Study Continuity Disaster Recovery Business Recovery Plan To Overcome Cyber Security Threat
Case Study Continuity Disaster Recovery Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about case study related to business recovery by Automotive company after a water outbreak. It includes challenges faced, goals, adopted approaches, and results. Present the topic in a bit more detail with this Case Study Continuity Disaster Recovery Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Business Continuity, Disaster Recovery, Approach. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Case Study Data Breach Incident Recovery Business Recovery Plan To Overcome Cyber Security Threat
Case Study Data Breach Incident Recovery Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about a case study related to data breach recovery. It includes key elements such as incident date, challenges faced, LinkedIn response plan, and results. Deliver an outstanding presentation on the topic using this Case Study Data Breach Incident Recovery Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Regain Customer Trust, Rebuilding Business Reputation, Linkedin Response using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Conducting Of Business Recovery Plan Business Recovery Plan To Overcome Cyber Security Threat
Conducting Of Business Recovery Plan Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about cybercrime cost growth and various cybercrime attacks on leading companies such as LinkedIn, Facebook, Microsoft Exchange email servers, and real estate wealth networks. Present the topic in a bit more detail with this Conducting Of Business Recovery Plan Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Assessment, Business, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attack Restriction Plan Checklist Business Recovery Plan To Overcome Cyber Security Threat
Cyber Attack Restriction Plan Checklist Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information on various cyber attack containment strategies that can be implemented to prevent further data breaches such as restraining lateral movements, and data breach evident collection. Deliver an outstanding presentation on the topic using this Cyber Attack Restriction Plan Checklist Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Containment, Strategies, Implemented using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Communication Different Stakeholders Business Recovery Plan To Overcome Cyber Security Threat
Cyber Communication Different Stakeholders Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about various stakeholders to be taken care of during and after the business recovery periods such as customers, internal stakeholders, external agencies, and recovery team. Introducing Cyber Communication Different Stakeholders Business Recovery Plan To Overcome Cyber Security Threat to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Customer, Government, Recovery Team, using this template. Grab it now to reap its full benefits.
-
 Cyber Containment Action Plan Checklist Business Recovery Plan To Overcome Cyber Security Threat
Cyber Containment Action Plan Checklist Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information various cyber-attack containment strategies that can be implemented to prevent further data breach such as affected system isolation, and securing credential and accounts. Deliver an outstanding presentation on the topic using this Cyber Containment Action Plan Checklist Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Affected System Isolation, Secure Credential And Accounts, Determine Compromised Devices using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Impact And Risk Assessment Matrix Business Recovery Plan To Overcome Cyber Security Threat
Cyber Impact And Risk Assessment Matrix Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about the cyber security attack risk assessment matrix which can be leveraged to determine the severity of cyber threats, the likelihood of occurrence, and future action plan. Present the topic in a bit more detail with this Cyber Impact And Risk Assessment Matrix Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Assessment Matrix, Occurrence, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Incident Channels For Customers Business Recovery Plan To Overcome Cyber Security Threat
Cyber Incident Channels For Customers Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about various communication channels that can be used by company to inform customers about cyber security such as social media, website blogs, and text message. Present the topic in a bit more detail with this Cyber Incident Channels For Customers Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Communication, Incident Information, Grammatical. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Incident Response Budget Allocation Business Recovery Plan To Overcome Cyber Security Threat
Cyber Incident Response Budget Allocation Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide demonstrates business cyber security management budget plan. It includes key allocation areas such as software and hardware solutions, managed services, training, and education. Deliver an outstanding presentation on the topic using this Cyber Incident Response Budget Allocation Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Antivirus Solution, Intrusion Prevention System, Encryption Software using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Meeting With Recovery Team Business Recovery Plan To Overcome Cyber Security Threat
Cyber Meeting With Recovery Team Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about communication plan for the recovery team. It includes key elements such as meeting agenda, meeting coordinator, things to communicate, meeting mode, and target audience. Present the topic in a bit more detail with this Cyber Meeting With Recovery Team Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Incident Details, Impact Assessment, Recovery Plan. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Designated Business Recovery Team Structure Business Recovery Plan To Overcome Cyber Security Threat
Designated Business Recovery Team Structure Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about recovery team structure and number of members across different team for business recovery. It includes teams such as executive, communication, crisis management, impact assessment, etc. Present the topic in a bit more detail with this Designated Business Recovery Team Structure Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Business Continuity Expert, Assessment, Communication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Email Strategy For External Stakeholders Business Recovery Plan To Overcome Cyber Security Threat
Email Strategy For External Stakeholders Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide demonstrates a sample email template that can be used by the company to inform stakeholders about security incidents. It includes key elements such as incident details, impacted data, potential impact, and our actions. Present the topic in a bit more detail with this Email Strategy For External Stakeholders Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Government, Executives, Stakeholders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Evaluating Hacking Impact On Business Business Recovery Plan To Overcome Cyber Security Threat
Evaluating Hacking Impact On Business Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about the impact of cyber hacking incidents on business key areas such as financial, operational area, company reputation, and market value. Introducing Evaluating Hacking Impact On Business Business Recovery Plan To Overcome Cyber Security Threat to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Financial Impact, Operational Impact, Legal Impact, using this template. Grab it now to reap its full benefits.
-
 Forecasted Cyber Business Performance Business Recovery Plan To Overcome Cyber Security Threat
Forecasted Cyber Business Performance Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about the impact of cyber response plan applications on business performance. It includes key areas of impact such as reputation, operations, and market value of company Increase audience engagement and knowledge by dispensing information using Forecasted Cyber Business Performance Business Recovery Plan To Overcome Cyber Security Threat. This template helps you present information on three stages. You can also present information on Operational Impact, Reputation Impact, Legal Impact using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide For Business Recovery Plan To Overcome Cyber Security Threat
Icons Slide For Business Recovery Plan To Overcome Cyber Security ThreatDeliver an outstanding presentation on the topic using this Icons Slide For Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Icons using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Elements Security Response Plan Business Recovery Plan To Overcome Cyber Security Threat
Key Elements Security Response Plan Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about the key components of cyber security threat response plan. It includes key elements such as identify attack source, limit damage, damage scope assessment, consulting, clean up system, and future action plan. Increase audience engagement and knowledge by dispensing information using Key Elements Security Response Plan Business Recovery Plan To Overcome Cyber Security Threat. This template helps you present information on six stages. You can also present information on Identify The Attack Source, Limit Additional Damage, Damage Scope Assessment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Major Incident Details Related To It Failure Business Recovery Plan To Overcome Cyber Security Threat
Major Incident Details Related To It Failure Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about cyber attack incidents. It includes information about incident date, impact, and incident information comprising loss of customer name, address, phone number, birth date, etc. Increase audience engagement and knowledge by dispensing information using Major Incident Details Related To It Failure Business Recovery Plan To Overcome Cyber Security Threat. This template helps you present information on three stages. You can also present information on Ransomware, Information, Cyber Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.





