Powerpoint Templates and Google slides for Cyber Security Attacks
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Analyse Impact Of Cyber Attack On Valuable Implementing Strategies To Mitigate Cyber Security Threats
Analyse Impact Of Cyber Attack On Valuable Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the consequences of data breach threats to prevent information leakage. It mainly includes elements such as impact on revenue, protection cost, liability if lost, weightage criteria, asset importance etc. Deliver an outstanding presentation on the topic using this Analyse Impact Of Cyber Attack On Valuable Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Criteria, Impact On Revenue, Protection Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices To Prevent Cyber Attacks Implementing Strategies To Mitigate Cyber Security Threats
Best Practices To Prevent Cyber Attacks Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide illustrates some activities to minimize the probability of cybercrimes within the organization. It includes elements such as utilizing anti virus, preventing to open suspicious emails, keeping systems up to date etc. Introducing Best Practices To Prevent Cyber Attacks Implementing Strategies To Mitigate Cyber Security Threats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Leverage Firewalls, Prevent Opening Suspicious Emails using this template. Grab it now to reap its full benefits.
-
 Classify Assets Vulnerable To Cyber Attack Implementing Strategies To Mitigate Cyber Security Threats
Classify Assets Vulnerable To Cyber Attack Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts some major assets that are more prone to cyber attack. It mainly includes elements such as sales record, sales lead record, company internal database, customer and product information etc. Present the topic in a bit more detail with this Classify Assets Vulnerable To Cyber Attack Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Sales Record, Customer Database, Product Database This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identifying Impact Of Cyber Attack On Business Implementing Strategies To Mitigate Cyber Security Threats
Identifying Impact Of Cyber Attack On Business Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the negative impact of cyber crimes on business to build control actions and strategies. It includes key elements such as rising costs, reputational damage, operational disruption, loss of revenue etc. Introducing Identifying Impact Of Cyber Attack On Business Implementing Strategies To Mitigate Cyber Security Threats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Rising Cost, Reputational Damage, Operational Disruption using this template. Grab it now to reap its full benefits.
-
 Types Of Cyber Attacks Encountered By Employees Implementing Strategies To Mitigate Cyber Security Threats
Types Of Cyber Attacks Encountered By Employees Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the various types of cyber attacks faced by staff to determine and formulate action plan. It includes elements such as malware, ransomware, man in the middle, phishing, denial of service tec. Introducing Types Of Cyber Attacks Encountered By Employees Implementing Strategies To Mitigate Cyber Security Threats to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Malware, Ransomware, Phishing using this template. Grab it now to reap its full benefits.
-
 Big Data Attack Detection Model In Cyber Security
Big Data Attack Detection Model In Cyber SecurityThis slide visualises the detection models used in defending cyber security in big data. Its aim is to detect any malicious attack. This slide includes training data, data preparation, testing, attack detection model, etc. Introducing our Big Data Attack Detection Model In Cyber Security set of slides. The topics discussed in these slides are Network, Activity, Application. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Using Big Data In Cyber Security Against Attacks
Using Big Data In Cyber Security Against AttacksThis slide informs about using big data again cyber security attacks. Its aim is to protect against cyber attacks and provide solutions to the company. This slide includes access control, encryption based attack, DDoS, false data, etc. Presenting our well structured Using Big Data In Cyber Security Against Attacks. The topics discussed in this slide are Security, Cyber, Attacks. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Implementing Strategies To Mitigate Cyber Security Reduce Attack Surface With Privilege Access Management
Implementing Strategies To Mitigate Cyber Security Reduce Attack Surface With Privilege Access ManagementThe following slide depicts the privilege access management PAM workflow to protect against suspicious events. It includes elements such as user access request, password retrieval, session proxy, record sessions, audit logs, servers etc. Present the topic in a bit more detail with this Implementing Strategies To Mitigate Cyber Security Reduce Attack Surface With Privilege Access Management Use it as a tool for discussion and navigation on Access Request, Approval Rules, Session Proxy This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Prevention Techniques For Cyber Security Data Attacks
Prevention Techniques For Cyber Security Data AttacksThe highlighted slide identifies critical types of cybersecurity attacks on data, including malware, phishing, password attacks, man in the middle attacks, and SQL injection. This information is essential for understanding and preparing against various threats, contributing to a more robust defense strategy for safeguarding data. Introducing our Prevention Techniques For Cyber Security Data Attacks set of slides. The topics discussed in these slides are Malware Attack, Phishing Attack, Password Attack. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 ATP Cyber Security Attack Process
ATP Cyber Security Attack ProcessThis slide depicts the ATP cyber security attack process. Its aim is to monitor the cyber security attack and prevent them. This slide includes brute force attacker, unfamiliar location, lateral movement, sensitive data, etc. Presenting our set of slides with name ATP Cyber Security Attack Process. This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Integrate Security, Measures In The System, Prevents Attack Automatically, Access Of Sensitive Data.
-
 Reducing Attack Surface By Cyber Security Mesh Icon
Reducing Attack Surface By Cyber Security Mesh IconIntroducing our premium set of slides with Reducing Attack Surface By Cyber Security Mesh Icon Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Reducing Attack Surface, Cyber Security Mesh Icon. So download instantly and tailor it with your information.
-
 Cyber Security Attack Control Icon
Cyber Security Attack Control IconIntroducing our premium set of slides with Cyber Security Attack Control Icon Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Security Attack Control Icon So download instantly and tailor it with your information.
-
 Web Security Icon To Prevent Cyber Attacks
Web Security Icon To Prevent Cyber AttacksPresenting our set of slides with Web Security Icon To Prevent Cyber Attacks This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Web Security Icon, Prevent Cyber Attacks
-
 Cyber Attack Vulnerability Icon For Security Management
Cyber Attack Vulnerability Icon For Security ManagementPresenting our set of slides with Cyber Attack Vulnerability Icon For Security Management This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Attack Vulnerability, Security Management
-
 Potential Consistent Cyber Security Attacks Business Recovery Plan To Overcome Cyber Security Threat
Potential Consistent Cyber Security Attacks Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about various solutions that can be adopted for business cyber-attack management. It includes key solutions such as staff training, collaboration with experts, and develop business recovery plan. Deliver an outstanding presentation on the topic using this Potential Consistent Cyber Security Attacks Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Solution Scope, Solution Duration, Requisites using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Setting Goals For Cyber Attack Management Business Recovery Plan To Overcome Cyber Security Threat
Setting Goals For Cyber Attack Management Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about time-based goals set for cyber attack management. It includes goals such as mean time to detect incidents, containment time, resolution time, and recovery time. Introducing Setting Goals For Cyber Attack Management Business Recovery Plan To Overcome Cyber Security Threat to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Mean Time To Contain, Mean Time To Resolve, Mean Time To Recover, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Attacks In Blockchain Technology
Cyber Security Attacks In Blockchain TechnologyPresenting our set of slides with Cyber Security Attacks In Blockchain Technology. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Interception, Floods Networks, False Identities.
-
 Impact Of Cyber Attacks On Organizational Operations IT Security Awareness Training Cybersecurity SS
Impact Of Cyber Attacks On Organizational Operations IT Security Awareness Training Cybersecurity SSThis slide represents impact of attacks that are attempted to steal sensitive information in the form of user names, credit card numbers etc. on organizational operations. Increase audience engagement and knowledge by dispensing information using Impact Of Cyber Attacks On Organizational Operations IT Security Awareness Training Cybersecurity SS. This template helps you present information on four stages. You can also present information on Reputational Damage, Stolen Intellectual Property, Operational Disruption, Increased Costs using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Chatbot Security Icon To Reduce Cyber Attacks
Chatbot Security Icon To Reduce Cyber AttacksIntroducing our premium set of slides with Chatbot Security Icon To Reduce Cyber Attacks. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Chatbot Security, Icon To Reduce, Cyber Attacks. So download instantly and tailor it with your information.
-
 Email Security Best Practices Steps To Secure Email From Cyber Attacks
Email Security Best Practices Steps To Secure Email From Cyber AttacksThis slide outlines the steps for implementing email security policies to avoid cyber attacks. These include strong password, two-factor authentication, email encryption, software updating, choose a trustworthy email provider, etc. Present the topic in a bit more detail with this Email Security Best Practices Steps To Secure Email From Cyber Attacks. Use it as a tool for discussion and navigation on Two-Factor Authentication, Email Encryption, Virtual Private Network. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attacks Caused By IOT Security Vulnerabilities
Cyber Attacks Caused By IOT Security VulnerabilitiesThis slide showcases an overview of attacks that disrupt smooth functioning. Threats covered in the slide are IoT botnets and data exfiltration. Introducing our Cyber Attacks Caused By IOT Security Vulnerabilities set of slides. The topics discussed in these slides are Examples, Description, IOT Botnets, Data Exfiltration . This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Supply Chain Security Checklist To Prevent Cyber Attacks
Supply Chain Security Checklist To Prevent Cyber AttacksThis slide represents checklist that helps companies to enhance their supply chain security and prevent suppliers from potential cyberattacks effectively. It includes various parameters such as documenting supply chain security plan, conducting suppliers meeting, etc. Presenting our well structured Supply Chain Security Checklist To Prevent Cyber Attacks. The topics discussed in this slide are Supply Chain Security Plan, Network, Evaluation Processes. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Most Common Cyber Attack Building A Security Awareness Program
Most Common Cyber Attack Building A Security Awareness ProgramThe purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, IoT based attacks, malware, social engineering attack and business email compromise. Present the topic in a bit more detail with this Most Common Cyber Attack Building A Security Awareness Program. Use it as a tool for discussion and navigation on Ransomware, Password Attack, Cryptojacking. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Cyber Attacks Faced By The Company In Previous Year
Cyber Security Attacks Response Plan Cyber Attacks Faced By The Company In Previous YearThis slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Plan Cyber Attacks Faced By The Company In Previous Year. Dispense information and present a thorough explanation of Ransomware Attacks, Phishing Attacks, Post Pandemic using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Electronic information security cyber attacks experienced company previous
Electronic information security cyber attacks experienced company previousThis slide shows the impact on the organizations financial condition due to cyber attacks in the past financial year 2022. Deliver an outstanding presentation on the topic using this Electronic Information Security Cyber Attacks Experienced Company Previous. Dispense information and present a thorough explanation of Cyber Attacks, Massive Increase using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
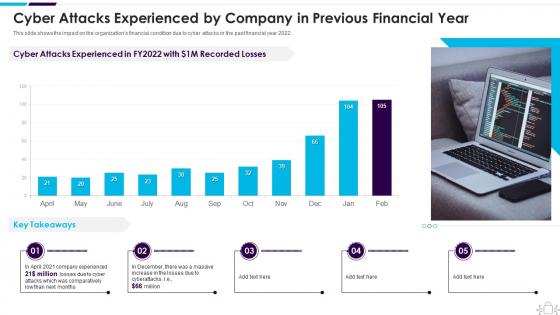 Cyber Attacks Experienced By Company In Previous Information Technology Security
Cyber Attacks Experienced By Company In Previous Information Technology SecurityThis slide shows the impact on the organizations financial condition due to cyber attacks in the past financial year 2022. Present the topic in a bit more detail with this Cyber Attacks Experienced By Company In Previous Information Technology Security. Use it as a tool for discussion and navigation on Experienced, Previous, Financial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Terrorism Attacks Impact Of Implementing Cyber Security
Cyber Terrorism Attacks Impact Of Implementing Cyber SecurityThis slide represents the current state of cyber assaults in a business after implementing the cyber security model. Deliver an outstanding presentation on the topic using this Cyber Terrorism Attacks Impact Of Implementing Cyber Security. Dispense information and present a thorough explanation of Impact Of Implementing Cyber Security Measures In The Company using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IT Infrastructure Cyber Security Budget Against Cyber Terrorism Attacks
IT Infrastructure Cyber Security Budget Against Cyber Terrorism AttacksThis slide depicts the IT infrastructure budget of incorporating cyber security, as well as the cost of each activity to the company. Present the topic in a bit more detail with this IT Infrastructure Cyber Security Budget Against Cyber Terrorism Attacks. Use it as a tool for discussion and navigation on It Infrastructure Cyber Security Budget Against Cyber Terrorism Fy19 20. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Hacker Loss Due To Different Cyber Attacks Ppt Powerpoint Presentation Slides
Security Hacker Loss Due To Different Cyber Attacks Ppt Powerpoint Presentation SlidesThis slide represents the different types of cyber attacks throughout the year, including the percentage of total loss caused by these attacks. Present the topic in a bit more detail with this Security Hacker Loss Due To Different Cyber Attacks Ppt Powerpoint Presentation Slides. Use it as a tool for discussion and navigation on Different Cyber Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determining The Actors Behind Most Significant Cyber Attack Developing Cyber Security Awareness
Determining The Actors Behind Most Significant Cyber Attack Developing Cyber Security AwarenessThe purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Present the topic in a bit more detail with this Determining The Actors Behind Most Significant Cyber Attack Developing Cyber Security Awareness. Use it as a tool for discussion and navigation on Determining The Actors, Behind Most Significant, Cyber Attack. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Most Common Cyber Attack Faced By Our Employees Developing Cyber Security Awareness Training Program
Most Common Cyber Attack Faced By Our Employees Developing Cyber Security Awareness Training ProgramThe purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, iot based attacks, malware, social engineering attack and business email compromise. Increase audience engagement and knowledge by dispensing information using Most Common Cyber Attack Faced By Our Employees Developing Cyber Security Awareness Training Program. This template helps you present information on eight stages. You can also present information on Ransomware, Password Attack, Social Engineering Attack, Business Email Compromise using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Attack Prevention Techniques Developing Cyber Security Awareness Training
Social Engineering Attack Prevention Techniques Developing Cyber Security Awareness TrainingThe purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no s haring of password. Deliver an outstanding presentation on the topic using this Social Engineering Attack Prevention Techniques Developing Cyber Security Awareness Training. Dispense information and present a thorough explanation of Limit Public Information, Verify The Source, No Sharing Of Password using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Attacks Faced By Organization In Previous Information Security Risk Management
Cyber Attacks Faced By Organization In Previous Information Security Risk ManagementThis slide showcases information security attacks faced by organization in past financial year. It can help company to assess different types of cyber attacks and formulate strategies to tackle them. Deliver an outstanding presentation on the topic using this Cyber Attacks Faced By Organization In Previous Information Security Risk Management. Dispense information and present a thorough explanation of Cyber Attacks Faced, Organization, Previous Financial Year using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 KPI Metrics Of Cyber Security For Attacks Dashboard
KPI Metrics Of Cyber Security For Attacks DashboardThis slide shows dashboard of cyber threats and attacks and predictions made for the same. It includes threats by class name and attacks by month. Introducing our KPI Metrics Of Cyber Security For Attacks Dashboard set of slides. The topics discussed in these slides are KPI Metrics, Cyber Security, Attacks Dashboard. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Determining The Actors Behind Most Significant Cyber Attack Conducting Security Awareness
Determining The Actors Behind Most Significant Cyber Attack Conducting Security AwarenessThe purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Deliver an outstanding presentation on the topic using this Determining The Actors Behind Most Significant Cyber Attack Conducting Security Awareness. Dispense information and present a thorough explanation of Online Criminals, Foreign Government Officials, Malicious Insiders using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Most Common Cyber Attack Faced By Our Employees Conducting Security Awareness
Most Common Cyber Attack Faced By Our Employees Conducting Security AwarenessThe purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, IoT-based attacks, malware, social engineering attack and business email compromise. Present the topic in a bit more detail with this Most Common Cyber Attack Faced By Our Employees Conducting Security Awareness. Use it as a tool for discussion and navigation on Ransomware, Password Attack, Cryptojacking. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Most Common Cyber Attack Faced By Our Employees Implementing Security Awareness Training
Most Common Cyber Attack Faced By Our Employees Implementing Security Awareness TrainingThe purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, IoT based attacks, malware, social engineering attack and business email compromise. Introducing Most Common Cyber Attack Faced By Our Employees Implementing Security Awareness Training to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Ransomware, Password Attack, Cryptojacking, Malware, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents Implementing Security Awareness Training To Prevent Cyber Attacks
Table Of Contents Implementing Security Awareness Training To Prevent Cyber AttacksPresent the topic in a bit more detail with this Table Of Contents Implementing Security Awareness Training To Prevent Cyber Attacks. Use it as a tool for discussion and navigation on Security Awareness, Current Assessment, Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attacks Faced By Organization Previous Financial Year Information System Security And Risk Administration
Cyber Attacks Faced By Organization Previous Financial Year Information System Security And Risk AdministrationThis slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type of cyber attacks and formulate strategies to tackle them. Deliver an outstanding presentation on the topic using this Cyber Attacks Faced By Organization Previous Financial Year Information System Security And Risk Administration. Dispense information and present a thorough explanation of Organization Experienced, Increasing A Rapid Rate, Financial Year using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determining The Actors Behind Most Significant Cyber Attack Preventing Data Breaches Through Cyber Security
Determining The Actors Behind Most Significant Cyber Attack Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. Present the topic in a bit more detail with this Determining The Actors Behind Most Significant Cyber Attack Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Online Criminals, Foreign Government Officials, Malicious Insiders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Attack Prevention Techniques Preventing Data Breaches Through Cyber Security
Social Engineering Attack Prevention Techniques Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no sharing of password. Present the topic in a bit more detail with this Social Engineering Attack Prevention Techniques Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Limit Public Information, Verify The Source, No Sharing Of Password. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attack Analytics Dashboard With Level Of Security
Cyber Attack Analytics Dashboard With Level Of SecurityThe given slide depicts the cyber threat analytics to track the attacks. It includes the no. of incidents, open and solved tickets, category wise no. of incidents along with malware type etc. Introducing our Cyber Attack Analytics Dashboard With Level Of Security set of slides. The topics discussed in these slides are Cyber Attack Analytics, Dashboard, Level Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
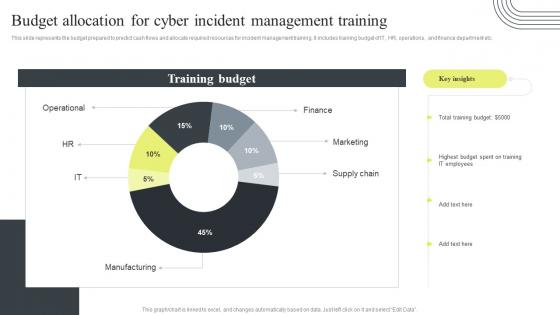 Cyber Security Attacks Response Plan Budget Allocation For Cyber Incident Management Training
Cyber Security Attacks Response Plan Budget Allocation For Cyber Incident Management TrainingThis slide represents the budget prepared to predict cash flows and allocate required resources for incident management training. It includes training budget of IT, HR, operations, and finance department etc. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Plan Budget Allocation For Cyber Incident Management Training. Dispense information and present a thorough explanation of Budget Allocation, Cyber Incident Management, Training using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Attacks Response Plan Consequences Of Data Breaches Faced By Organization
Cyber Security Attacks Response Plan Consequences Of Data Breaches Faced By OrganizationThis slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Consequences Of Data Breaches Faced By Organization. Use it as a tool for discussion and navigation on Consequences, Data Breaches, Unintended Disclosure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Cyber Security Risk Assessment And Management Dashboard
Cyber Security Attacks Response Plan Cyber Security Risk Assessment And Management DashboardThis slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Plan Cyber Security Risk Assessment And Management Dashboard. Dispense information and present a thorough explanation of Cyber Security, Risk Assessment, Management Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Attacks Response Plan Cyber Security Systems Monitoring Report
Cyber Security Attacks Response Plan Cyber Security Systems Monitoring ReportThis slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Cyber Security Systems Monitoring Report. Use it as a tool for discussion and navigation on Cyber Security Systems, Monitoring Report, Mean Detect And Resolve Time. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Cyber Supply Chain Risk Management Dashboard
Cyber Security Attacks Response Plan Cyber Supply Chain Risk Management DashboardThis slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Cyber Supply Chain Risk Management Dashboard. Use it as a tool for discussion and navigation on Cyber Supply Chain, Risk Management, Dashboard, Regulatory Compliance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Enterprise Cyber Risk Management Dashboard
Cyber Security Attacks Response Plan Enterprise Cyber Risk Management DashboardThis slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Plan Enterprise Cyber Risk Management Dashboard. Dispense information and present a thorough explanation of Enterprise Cyber, Risk Management, Dashboard, Action Plan Breakdown using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Incident Response Kpi Dashboard Cyber Security Attacks Response Plan
Cyber Security Incident Response Kpi Dashboard Cyber Security Attacks Response PlanThis slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. Present the topic in a bit more detail with this Cyber Security Incident Response Kpi Dashboard Cyber Security Attacks Response Plan. Use it as a tool for discussion and navigation on Cyber Security, Incident Response, KPI Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Attack Prevention Techniques Raising Cyber Security Awareness In Organizations
Social Engineering Attack Prevention Techniques Raising Cyber Security Awareness In OrganizationsThe purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no sharing of password. Present the topic in a bit more detail with this Social Engineering Attack Prevention Techniques Raising Cyber Security Awareness In Organizations. Use it as a tool for discussion and navigation on Verify The Source, Sharing Of Password, Public Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attack Incident Generating Security Awareness Among Employees To Reduce
Cyber Attack Incident Generating Security Awareness Among Employees To ReduceThe following slide depicts the number of cyber attacks incurred during year end to monitor security trends. It includes elements such as prevented, allowed attacks, additional threats detected, number of infected hosts and malicious files etc. Present the topic in a bit more detail with this Cyber Attack Incident Generating Security Awareness Among Employees To Reduce Use it as a tool for discussion and navigation on Infected Hosts, Prevented Attacks This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber security risk management determine sequence phases for threat attack
Cyber security risk management determine sequence phases for threat attackThis slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Increase audience engagement and knowledge by dispensing information using Cyber Security Risk Management Determine Sequence Phases For Threat Attack. This template helps you present information on four stages. You can also present information on Reconnaissance, Weaponization, Exploitation, Delivery using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine sequence phases for threat attack contd cyber security risk management
Determine sequence phases for threat attack contd cyber security risk managementThis slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Introducing Determine Sequence Phases For Threat Attack Contd Cyber Security Risk Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Installation, Command And Control, Actions And Objectives, Covering Tracks, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Kpis To Measure Phishing Attacks
Cyber Security Kpis To Measure Phishing AttacksMentioned slide showcases 5 cyber security KPI which can be used by organization to measure phishing attacks. The KPIs mentioned in the slide are intrusion attempts, security incidents, mean time to detect MTTD, etc. Presenting our well structured Cyber Security Kpis To Measure Phishing Attacks. The topics discussed in this slide are Intrusion Attempts, Security Incidents, Mean Time to Resolve. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Attacks Statistics Ppt Powerpoint Presentation File Display Cpb
Cyber Security Attacks Statistics Ppt Powerpoint Presentation File Display CpbPresenting our Cyber Security Attacks Statistics Ppt Powerpoint Presentation File Display Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Cyber Security Attacks Statistics This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Roadmap To Implement Cyber Security Cyber Terrorism Attacks
Roadmap To Implement Cyber Security Cyber Terrorism AttacksThis slide depicts the roadmap to implement strategies to mitigate cyber terrorism such as training employees about cyber terrorism, creating personal accounts. Introducing Roadmap To Implement Cyber Security Cyber Terrorism Attacks to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Personal Accounts, Awareness Training, Software Updated, using this template. Grab it now to reap its full benefits.
-
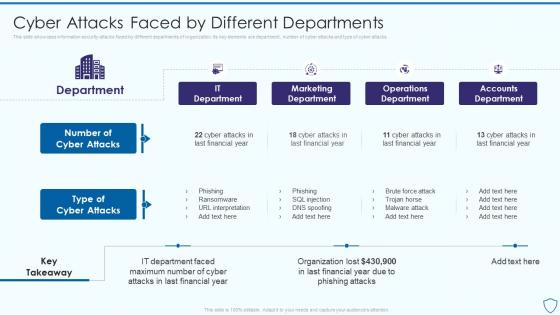 Risk Assessment And Management Plan For Information Security Cyber Attacks Faced By Different
Risk Assessment And Management Plan For Information Security Cyber Attacks Faced By DifferentThis slide showcase information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks Deliver an outstanding presentation on the topic using this Risk Assessment And Management Plan For Information Security Cyber Attacks Faced By Different. Dispense information and present a thorough explanation of Marketing Department, Operations Department, Accounts Department using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Incident Response Plan For Attack
Cyber Security Incident Response Plan For AttackThe following slide highlights the cyber security incident response plan for attack illustrating objective, planning and action, which helps the management to take decision for risk mitigation strategy and allocation of budget and resources depending on criticality of cyber attack. Presenting our set of slides with name Cyber Security Incident Response Plan For Attack. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Objective, Planning, Action.
-
 Understanding The Frequency And Weightage Of Cyber Attacks Conducting Security Awareness
Understanding The Frequency And Weightage Of Cyber Attacks Conducting Security AwarenessThe purpose of this slide is to showcase the frequency and weightage of different cyber attacks on multiple departments. The major departments mentioned in the slide are financial, marketing, information technology IT and human resource HR. Increase audience engagement and knowledge by dispensing information using Understanding The Frequency And Weightage Of Cyber Attacks Conducting Security Awareness. This template helps you present information on four stages. You can also present information on Financial Department, Marketing Team, HR Department, IT Department using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Elements IT Types Of Cyber Attackers Ppt Professional
Cyber Security Elements IT Types Of Cyber Attackers Ppt ProfessionalThis slide represents the types of cyber attackers, including cyber criminals, hacktivists, state sponsored attackers, and insider threats. Insider threats can be occurred from within the organization and can be malicious, accidental or negligent. Introducing Cyber Security Elements IT Types Of Cyber Attackers Ppt Professional to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Criminals, Insider Threats, Hacktivists, using this template. Grab it now to reap its full benefits.





