Powerpoint Templates and Google slides for Cyber Security Apps
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Raising Cyber Security Awareness In Organizations Using Various Tools And Tactics PPT Template Bundles DK MD
Raising Cyber Security Awareness In Organizations Using Various Tools And Tactics PPT Template Bundles DK MDDeliver a credible and compelling presentation by deploying this Raising Cyber Security Awareness In Organizations Using Various Tools And Tactics PPT Template Bundles DK MD. Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The fifteen slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Raising Cyber Security Awareness In Organizations Using Various Tools And Tactics PPT Template Bundles DK MD PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.
-
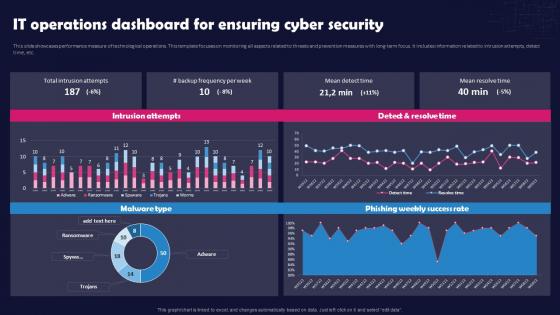 Unlocking The Impact Of Technology It Operations Dashboard For Ensuring Cyber Security
Unlocking The Impact Of Technology It Operations Dashboard For Ensuring Cyber SecurityThis slide showcases performance measure of technological operations. This template focuses on monitoring all aspects related to threats and prevention measures with long-term focus. It includes information related to intrusion attempts, detect time, etc. Present the topic in a bit more detail with this Unlocking The Impact Of Technology It Operations Dashboard For Ensuring Cyber Security. Use it as a tool for discussion and navigation on IT Operations Dashboard, Ensuring Cyber Security, Threats And Prevention, Technological Operations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Expenditure Summary Dashboard Creating Cyber Security Awareness
Information Technology Expenditure Summary Dashboard Creating Cyber Security AwarenessThe following slide showcases the cyber security expense overview to better allocate budget. It includes elements such as IT cost, revenue, security incidents, services down, issue status summary, total business hours lost etc. Deliver an outstanding presentation on the topic using this Information Technology Expenditure Summary Dashboard Creating Cyber Security Awareness Dispense information and present a thorough explanation of Inadequate Security Guidelines, Inappropriate Privacy Policies, Insufficient Security Failure By Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Expenditure Summary Implementing Strategies To Mitigate Cyber Security Threats
Information Technology Expenditure Summary Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the cyber security expense overview to better allocate budget. It includes elements such as IT cost, revenue, security incidents, services down, issue status summary, total business hours lost etc. Deliver an outstanding presentation on the topic using this Information Technology Expenditure Summary Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Cyber Security Budget Spent, It Costs And Revenue, Issue Status Summary using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Budget Allocation For Big Data Cyber Security Application
Budget Allocation For Big Data Cyber Security ApplicationThis slide showcases the budget allocation for various activities in big data cyber security. Its purpose is to understand the budgetary plan for cyber security. This slide includes authentication, monitoring, incident response, malware protection, network traffic, log management, data protection, etc. Introducing our Budget Allocation For Big Data Cyber Security Application set of slides. The topics discussed in these slides are Allocation, Cyber, Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Securing Food Safety In Online Cloud Based Cyber Security For Third Party Applications
Securing Food Safety In Online Cloud Based Cyber Security For Third Party ApplicationsThis slide covers cloud based cyber security strategies such as vendor ecosystem, security compliance and role based access controls. Present the topic in a bit more detail with this Securing Food Safety In Online Cloud Based Cyber Security For Third Party Applications. Use it as a tool for discussion and navigation on Vendor Ecosystem, Security Compliance, Role Based Access Controls. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Automation Ideas Mechanization Cyber Security Infrastructure Implement Technology Material
Automation Ideas Mechanization Cyber Security Infrastructure Implement Technology MaterialEnhance your audiences knowledge with this well researched complete deck. Showcase all the important features of the deck with perfect visuals. This deck comprises of total of ten slides with each slide explained in detail. Each template comprises of professional diagrams and layouts. Our professional PowerPoint experts have also included icons, graphs and charts for your convenience. All you have to do is DOWNLOAD the deck. Make changes as per the requirement. Yes, these PPT slides are completely customizable. Edit the colour, text and font size. Add or delete the content from the slide. And leave your audience awestruck with the professionally designed Automation Ideas Mechanization Cyber Security Infrastructure Implement Technology Material complete deck.
-
 Cyber Security Risk Assessment And Technology Deployment Plan To Improve Organizations
Cyber Security Risk Assessment And Technology Deployment Plan To Improve OrganizationsThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution Deliver an outstanding presentation on the topic using this Cyber Security Risk Assessment And Technology Deployment Plan To Improve Organizations. Dispense information and present a thorough explanation of Consequences, Vulnerability, Risk using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Various Cyber Security Incidents Detected By Technology Deployment Plan To Improve Organizations
Various Cyber Security Incidents Detected By Technology Deployment Plan To Improve OrganizationsThis slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Introducing Various Cyber Security Incidents Detected By Technology Deployment Plan To Improve Organizations to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Phishing, Malware, Application, using this template. Grab it now to reap its full benefits.
-
 Technology Cyber Security In Powerpoint And Google Slides Cpb
Technology Cyber Security In Powerpoint And Google Slides CpbPresenting our Technology Cyber Security In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Technology Cyber Security. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Applications Of Big Data Analytics In Cyber Security
Applications Of Big Data Analytics In Cyber SecurityThis slide depicts the applications of big data analytics in implementing cybersecurity. The purpose of this slide is to help the business utilize big data security analytics in an appropriate manner for safeguarding business information. It includes data segmentation and clustering, tie series analysis and forecasting, etc. Introducing our premium set of slides with Applications Of Big Data Analytics In Cyber Security. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Calculation Of Statistical Parameters, Data Segmentation Clustering. So download instantly and tailor it with your information.
-
 Communication Plan For Cyber Security Technology Initiatives
Communication Plan For Cyber Security Technology InitiativesThis slide shows communication plan for tackling with different types of cyber attacks that can affect organization security in several ways. It include cyber attacks, initiates and owner, etc. Introducing our premium set of slides with Communication Plan For Cyber Security Technology Initiatives. Ellicudate the one stage and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Ransom Ware, Denial Of Services, Malicious Insider. So download instantly and tailor it with your information.
-
 Advanced Technologies Cyber Security Technology Market Overview
Advanced Technologies Cyber Security Technology Market OverviewThis slide explains Cyber security technology market overview with top players in the year 2021. It also predicts market growth and compound annual growth rate from year 2021 till 2028. Increase audience engagement and knowledge by dispensing information using Advanced Technologies Cyber Security Technology Market Overview. This template helps you present information on Two stages. You can also present information on Pros, Cons using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Advanced Technologies Need For Cyber Security Technology
Advanced Technologies Need For Cyber Security TechnologyThis slide gives an overview of cyber security technology. It also gives an idea about which industries are most venerable for a cyber attack and why cyber security is needed. Deliver an outstanding presentation on the topic using this Advanced Technologies Need For Cyber Security Technology. Dispense information and present a thorough explanation of Need For Cyber Security, Technology using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Advanced Technologies Objectives Of Cyber Security Technology
Advanced Technologies Objectives Of Cyber Security TechnologyThis slide explains the objectives of cyber security technology such as confidentiality, integrity and availability. It also talks about the three goals and how they collectively ensures the data protection. Increase audience engagement and knowledge by dispensing information using Advanced Technologies Objectives Of Cyber Security Technology. This template helps you present information on Three stages. You can also present information on Confidentiality, Integrity, Availability using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Emerging Technologies Cyber Security Technology Market Overview
Emerging Technologies Cyber Security Technology Market OverviewThis slide explains Cyber security technology market overview with top players in the year 2021. It also predicts market growth and compound annual growth rate from year 2021 till 2028. Deliver an outstanding presentation on the topic using this Emerging Technologies Cyber Security Technology Market Overview. Dispense information and present a thorough explanation of Overview Of Cyber Security, False Sense Of Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Emerging Technologies Need For Cyber Security Technology
Emerging Technologies Need For Cyber Security TechnologyThis slide gives an overview of cyber security technology. It also gives an idea about which industries are most venerable for a cyber attack and why cyber security is needed. Deliver an outstanding presentation on the topic using this Emerging Technologies Need For Cyber Security Technology. Dispense information and present a thorough explanation of Protection, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Emerging Technologies Objectives Of Cyber Security Technology
Emerging Technologies Objectives Of Cyber Security TechnologyThis slide explains the objectives of cyber security technology such as confidentiality, integrity and availability. It also talks about the three goals and how they collectively ensures the data protection. Introducing Emerging Technologies Objectives Of Cyber Security Technology to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Confidentiality, Integrity, using this template. Grab it now to reap its full benefits.
-
 Trending Technologies Cyber Security Technology Market Overview
Trending Technologies Cyber Security Technology Market OverviewThis slide explains Cyber security technology market overview with top players in the year 2021. It also predicts market growth and compound annual growth rate from year 2021 till 2028. Deliver an outstanding presentation on the topic using this Trending Technologies Cyber Security Technology Market Overview. Dispense information and present a thorough explanation of Pros, Cons using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Trending Technologies Need For Cyber Security Technology
Trending Technologies Need For Cyber Security TechnologyThis slide gives an overview of cyber security technology. It also gives an idea about which industries are most venerable for a cyber attack and why cyber security is needed. Increase audience engagement and knowledge by dispensing information using Trending Technologies Need For Cyber Security Technology. This template helps you present information on three stages. You can also present information on Cyber Security Solutions, Malicious Criminals, Data And Privacy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
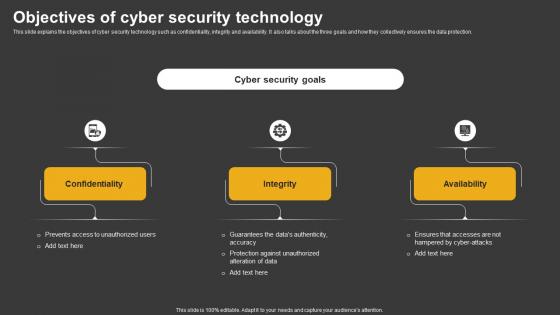 Trending Technologies Objectives Of Cyber Security Technology
Trending Technologies Objectives Of Cyber Security TechnologyThis slide explains the objectives of cyber security technology such as confidentiality, integrity and availability. It also talks about the three goals and how they collectively ensures the data protection. Introducing Trending Technologies Objectives Of Cyber Security Technology to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Confidentiality, Integrity, Availability, using this template. Grab it now to reap its full benefits.
-
 Applications Of ML In Cyber Security Analytics
Applications Of ML In Cyber Security AnalyticsThe following slide highlights threat identification, antivirus software, modeling, AI threats, and email monitoring to showcase the applications of ML in cybersecurity analytics. It helps organizations enhance cyber threat detection and mitigation capabilities through advanced machine learning techniques. Presenting our set of slides with Applications Of ML In Cyber Security Analytics. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identification, Antivirus, Behavior.
-
 Benefits Of Cyber Security Analytics Tools
Benefits Of Cyber Security Analytics ToolsThe following slide highlights key points like automated risks, incident detections, forensic investigation, and priority alert to show the benefits of cybersecurity analytics tools. It helps organizations to strengthen cybersecurity posture and respond more effectively to threats. Presenting our set of slides with Benefits Of Cyber Security Analytics Tools. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Automated, Priority, Investigation.
-
 Neural Networks And Cyber Security Applications A Beginners Guide To Neural AI SS
Neural Networks And Cyber Security Applications A Beginners Guide To Neural AI SSThis slide showcases how cyber security tasks can be performed by technicians when integrated with artificial neural networks ANN. It provides details about fraud detection, prioritized notifications, content moderation, etc. Increase audience engagement and knowledge by dispensing information using Neural Networks And Cyber Security Applications A Beginners Guide To Neural AI SS. This template helps you present information on six stages. You can also present information on Detection, Notifications, Prevention using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Deploy Tools To Minimize Impact Of Cyber Security Risks Improving Cyber Security Risks Management
Deploy Tools To Minimize Impact Of Cyber Security Risks Improving Cyber Security Risks ManagementThe following slide highlights some best tools to track and minimize the impact of cyber risks. It includes elements such as tool name, features, trial period, cost and reviews etc. Deliver an outstanding presentation on the topic using this Deploy Tools To Minimize Impact Of Cyber Security Risks Improving Cyber Security Risks Management. Dispense information and present a thorough explanation of Determines Suspicious, Features, Cyber Security Risks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Technology Market Overview Modern Technologies
Cyber Security Technology Market Overview Modern TechnologiesThis slide explains Cyber security technology market overview with top players in the year 2021. It also predicts market growth and compound annual growth rate from year 2021 till 2028.Present the topic in a bit more detail with this Cyber Security Technology Market Overview Modern Technologies. Use it as a tool for discussion and navigation on Business Continuity,Cybersecurity Measures,Manufacturing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Need For Cyber Security Technology Modern Technologies
Need For Cyber Security Technology Modern TechnologiesThis slide gives an overview of cyber security technology. It also gives an idea about which industries are most venerable for a cyber attack and why cyber security is needed.Deliver an outstanding presentation on the topic using this Need For Cyber Security Technology Modern Technologies. Dispense information and present a thorough explanation of Confidentiality,Integrity,Availability using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
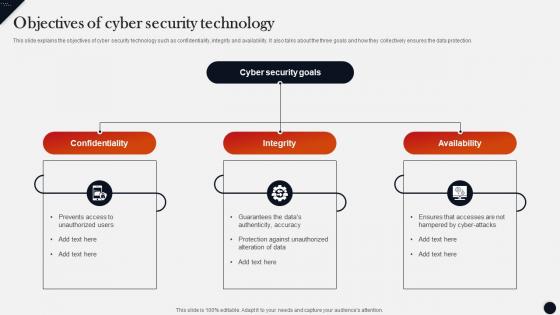 Objectives Of Cyber Security Technology Modern Technologies
Objectives Of Cyber Security Technology Modern TechnologiesThis slide explains the objectives of cyber security technology such as confidentiality,integrity and availability. It also talks about the three goals and how they collectively ensures the data protection.Introducing Objectives Of Cyber Security Technology Modern Technologies to increase your presentation threshold. Encompassed with three stages,this template is a great option to educate and entice your audience. Dispence information on Entertainment Gaming,Hardware Components,Sensors Such,using this template. Grab it now to reap its full benefits.
-
 Comparative Analysis Of Cyber Security Network Audit Tools
Comparative Analysis Of Cyber Security Network Audit ToolsThis slide covers a comparison of cyber audit tools and provides details about features that help to identify suitable software for organizations. It includes elements such as description, subscriptions, etc. Introducing our Comparative Analysis Of Cyber Security Network Audit Tools set of slides. The topics discussed in these slides are Vulnerability Assessment, Tamper Protection, Cloud Based. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Network Security Audit Technology Icon
Cyber Network Security Audit Technology IconPresenting our set of slides with Cyber Network Security Audit Technology Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Network Security, Audit Technology Icon.
-
 Cyber Security Risk Mitigation Methods Of Collaboration Tools
Cyber Security Risk Mitigation Methods Of Collaboration ToolsThe purpose of this slide is to highlight cyber security risk mitigation solutions of collaboration tools such as training employees on security awareness, contacting source, etc. Introducing our premium set of slides with Cyber Security Risk Mitigation Methods Of Collaboration Tools. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Simulate Phishing Tests, Verify Senders Identity, Use Official Channels . So download instantly and tailor it with your information.
-
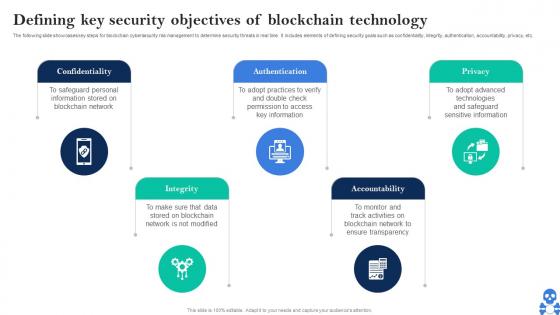 Cyber Threats In Blockchain Defining Key Security Objectives Of Blockchain Technology BCT SS V
Cyber Threats In Blockchain Defining Key Security Objectives Of Blockchain Technology BCT SS VThe following slide showcases key steps for blockchain cybersecurity risk management to determine security threats in real time. It includes elements of defining security goals such as confidentiality, integrity, authentication, accountability, privacy, etc. Introducing Cyber Threats In Blockchain Defining Key Security Objectives Of Blockchain Technology BCT SS V to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Confidentiality, Integrity, Authentication using this template. Grab it now to reap its full benefits.
-
 Select Tools To Reduce Cyber Security Failure Implementing Cyber Risk Management Process
Select Tools To Reduce Cyber Security Failure Implementing Cyber Risk Management ProcessThe following slide highlights some best tools to track and minimize the impact of cyber risks. It includes elements such as tool anme, features, trial period, cost and reviews etc. Deliver an outstanding presentation on the topic using this Select Tools To Reduce Cyber Security Failure Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Features, Free Trial, Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Elements Of Systems Applications And Products Cyber Security
Elements Of Systems Applications And Products Cyber SecurityThis slide depicts the components of SAP cybersecurity. The purpose of this template is to help understand the areas of business networks that can be safeguarded with the help of SAP cybersecurity elements. It includes data base security, infrastructure security, etc. Presenting our set of slides with Elements Of Systems Applications And Products Cyber Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Database Security, Operating System Security, Network Security, Infrastructure Security.
-
 Use Cases Of System Application And Product Cyber Security
Use Cases Of System Application And Product Cyber SecurityThis template depicts the applications of SAP cyber security. The purpose of this slide is to help the business leverage SAP cybersecurity to improve its internal network safety. It includes use cases such as ensuring data integrity, identification of unauthorized access, etc. Presenting our well structured Use Cases Of System Application And Product Cyber Security. The topics discussed in this slide are Prevent Exploitation And Fraud, Ensuring Data Integrity, Continuous Results. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Current Trending Technologies Cyber Security Technology Market Overview
Current Trending Technologies Cyber Security Technology Market OverviewThis slide explains Cyber security technology market overview with top players in the year 2021. It also predicts market growth and compound annual growth rate from year 2021 till 2028. Deliver an outstanding presentation on the topic using this Current Trending Technologies Cyber Security Technology Market Overview. Dispense information and present a thorough explanation of Cyber Security Technology, Market Growth, Compound Annual Growth Rate, Business Continuity using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Current Trending Technologies Need For Cyber Security Technology
Current Trending Technologies Need For Cyber Security TechnologyThis slide gives an overview of cyber security technology. It also gives an idea about which industries are most venerable for a cyber attack and why cyber security is needed. Increase audience engagement and knowledge by dispensing information using Current Trending Technologies Need For Cyber Security Technology. This template helps you present information on three stages. You can also present information on Cyber Security Technology, Prevention Of Cybercrime, Protection Of Sensitive Information using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Current Trending Technologies Objectives Of Cyber Security Technology
Current Trending Technologies Objectives Of Cyber Security TechnologyThis slide explains the objectives of cyber security technology such as confidentiality, integrity and availability. It also talks about the three goals and how they collectively ensures the data protection. Introducing Current Trending Technologies Objectives Of Cyber Security Technology to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Confidentiality, Cyber Security Technology, Data Protection, Integrity And Availability, using this template. Grab it now to reap its full benefits.
-
 New Technologies Cyber Security Technology Market Overview
New Technologies Cyber Security Technology Market OverviewThis slide explains Cyber security technology market overview with top players in the year 2021. It also predicts market growth and compound annual growth rate from year 2021 till 2028. Present the topic in a bit more detail with this New Technologies Cyber Security Technology Market Overview. Use it as a tool for discussion and navigation on Technology, Overview, Cyber Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 New Technologies Need For Cyber Security Technology
New Technologies Need For Cyber Security TechnologyThis slide gives an overview of cyber security technology. It also gives an idea about which industries are most venerable for a cyber attack and why cyber security is needed. Deliver an outstanding presentation on the topic using this New Technologies Need For Cyber Security Technology. Dispense information and present a thorough explanation of Technology, Information, Protecting using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
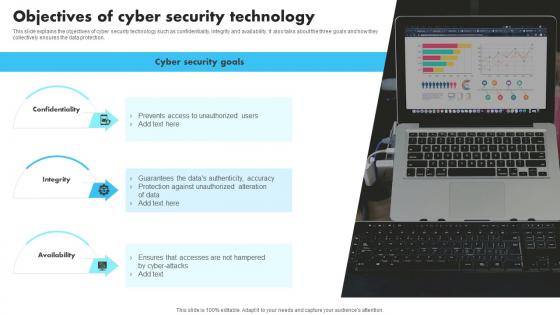 New Technologies Objectives Of Cyber Security Technology
New Technologies Objectives Of Cyber Security TechnologyThis slide explains the objectives of cyber security technology such as confidentiality, integrity and availability. It also talks about the three goals and how they collectively ensures the data protection. Introducing New Technologies Objectives Of Cyber Security Technology to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Confidentiality, Technology, Availability, using this template. Grab it now to reap its full benefits.
-
 Select Tools To Reduce Cyber Security Failure Cyber Risk Assessment
Select Tools To Reduce Cyber Security Failure Cyber Risk AssessmentThe following slide highlights some best tools to track and minimize the impact of cyber risks. It includes elements such as tool anme, features, trial period, cost and reviews etc. Introducing Select Tools To Reduce Cyber Security Failure Cyber Risk Assessment to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Suspicious Activities, Select Tools, Cyber Security Failure using this template. Grab it now to reap its full benefits.
-
 Select Tools To Reduce Cyber Security Failure Creating Cyber Security Awareness
Select Tools To Reduce Cyber Security Failure Creating Cyber Security AwarenessThe following slide highlights some best tools to track and minimize the impact of cyber risks. It includes elements such as tool anme, features, trial period, cost and reviews etc. Deliver an outstanding presentation on the topic using this Select Tools To Reduce Cyber Security Failure Creating Cyber Security Awareness Dispense information and present a thorough explanation of Duration, Mode, Start Date, End Date using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Software Comparison Tools
Cyber Security Software Comparison ToolsThis slide showcases cyber security software tools comparison analysis which helps to monitor and fix potential security concerns. It includes elements such as SecPod SanerNow, Intruder, ManageEngine vulnerability Manager Plus, SolarWinds Security Event Manager and Malwarebytes. Presenting our well structured Cyber Security Software Comparison Tools. The topics discussed in this slide are Best For Features, Free Trial. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Real Time Cyber Security Threat Monitoring Tools
Real Time Cyber Security Threat Monitoring ToolsThis slide showcases cyber security threat monitoring tool that helps in real-time spectating and identifies malicious behavior on network. It includes elements such as HoneyMap, Norse Map, Digital Attack Map, FireEye, Trend Micro and Akamai. Presenting our well structured Real Time Cyber Security Threat Monitoring Tools. The topics discussed in this slide are Visualization Tools, Real Time, Additional Features. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Applications Of Cryptography In Cyber Security
Applications Of Cryptography In Cyber SecurityThis slide covers various of applications and provides details about how the company secures data for users. It includes elements such as computer passwords, digital currencies, etc. Presenting our set of slides with Applications Of Cryptography In Cyber Security. This exhibits information on seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Computer Passwords, Secure Web Browsing, Authentication.
-
 Cryptography In Cyber Security Tools
Cryptography In Cyber Security ToolsThis slide covers various tools in cybersecurity and provides details about software that determines cryptography in organizations. It includes elements such as docker Introducing our premium set of slides with Cryptography In Cyber Security Tools. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Authentication Token, Authentication Using Key, Java Cryptography Architecture. So download instantly and tailor it with your information.
-
 Cyber Security Technology Stack Icon
Cyber Security Technology Stack IconIntroducing our Cyber Security Technology Stack Icon set of slides. The topics discussed in these slides are Cyber Security Technology Stack Icon. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Advantage Of Triage Technology In Cyber Security
Advantage Of Triage Technology In Cyber SecurityThis slide represents advantage of triage technology which assists to prioritize levels to task and determine most effective order to deal with them. It includes advantage of triage technology in cyber security such as efficient utilization of resources, prioritize critical data, etc Presenting our set of slides with name Advantage Of Triage Technology In Cyber Security This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Utilization Of Resources, Prioritize Critical Data, Resolve Threats Speedily
-
 Select Tools To Reduce Cyber Security Failure Implementing Strategies To Mitigate Cyber Security Threats
Select Tools To Reduce Cyber Security Failure Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide highlights some best tools to track and minimize the impact of cyber risks. It includes elements such as tool anme, features, trial period, cost and reviews etc. Present the topic in a bit more detail with this Select Tools To Reduce Cyber Security Failure Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Features, Free Trial, Cost This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Leverage Big Data In Cyber Security Application
Leverage Big Data In Cyber Security ApplicationThis slide showcases the various applications of big data in cybersecurity. Its objective is to tackle different situation for processing big set of data. This slide includes intrusion detection, malware, social media, code security, lightweight cyber security, etc. Presenting our set of slides with Leverage Big Data In Cyber Security Application. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Detection, Social, security.
-
 Cyber Security Checklist To Protect Saas Applications
Cyber Security Checklist To Protect Saas ApplicationsThis slide represents cybersecurity checklist for SaaS applications to protect data. It aims to assist organizations in identifying potential vulnerabilities as well as examining security standards. It includes various elements such as backing up creation and testing, using real-time security service, etc. Introducing our Cyber Security Checklist To Protect Saas Applications set of slides. The topics discussed in these slides are Determines Data Isolation, Safeguards Against Data Theft This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security Tools For Saas Companies
Cyber Security Tools For Saas CompaniesThis slide represents SaaS cyber security tools and technologies. It aims to provide specialized capabilities for endpoint security of SaaS companies operating. It includes various tools such as authentication and access control, network and endpoint security, etc. Introducing our premium set of slides with Cyber Security Tools For Saas Companies Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Authentication And Access Control, Secure Remote Access Technology, Network And Endpoint Security. So download instantly and tailor it with your information.
-
 Role Of Saas Applications In Cyber Security
Role Of Saas Applications In Cyber SecurityThis slide represents SaaS apps significance to cyber security. It aims to ensure continuous monitoring and updates to mitigate risks and protect sensitive data within applications. It includes various aspects such as authentication, leveraging data, etc. Introducing our premium set of slides with Role Of Saas Applications In Cyber Security Ellicudate the Five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Authentication, Enhanced Security, High Scalability, Strong Encryption. So download instantly and tailor it with your information.
-
 ATP Cyber Technology Security Icon
ATP Cyber Technology Security IconPresenting our set of slides with name ATP Cyber Technology Security Icon. This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on ATP Cyber Technology, Security Icon.
-
 Comparative Analysis Of ATP Cyber Security Tools
Comparative Analysis Of ATP Cyber Security ToolsThis slide depicts the comparative analysis of ATP cyber security tools. Its aim is to use the tools to protect the system from advanced threats. This slide include Microsoft defender, ESET endpoint, Palo Alto network, Fortinet sandbox. Presenting our set of slides with name Comparative Analysis Of ATP Cyber Security Tools. This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Microsoft Defender, ESET Endpoint, Palo Alto Network, Fortinet Sandbox.
-
 Cyber Security Mesh Applications For Business
Cyber Security Mesh Applications For BusinessThe following slide features key elements like IAM support, MSSPS, identity-proofing tools, standards, and demographic bias in illustrating the diverse applications of cybersecurity mesh for business. This aids in understanding its potential impact on security and operations. Presenting our set of slides with Cyber Security Mesh Applications For Business This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Mesh Supporting Iam Requests, Identity Life Cycle, Decentralized Identity Standards
-
 Icon For Role Of 5g Technology In Retail Cyber Security
Icon For Role Of 5g Technology In Retail Cyber SecurityIntroducing our Icon For Role Of 5g Technology In Retail Cyber Security set of slides. The topics discussed in these slides are Icon For Role Of 5G Technology, Retail Cyber Security This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Comparative Analysis For Network Intrusion Protection Cyber Security Tools
Comparative Analysis For Network Intrusion Protection Cyber Security ToolsThis slide depicts the comparative evaluation of NIPS security tools. The purpose of this slide is to help the business make a well informed purchase decision. It includes comparison on the basis of the free trial period, features, ratings, etc. Introducing our premium set of slides with Comparative Analysis For Network Intrusion Protection Cyber Security Tools Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Distinctive Features, Free Trial, Tools So download instantly and tailor it with your information.
-
 Main Applications Of Cyber Security Framework
Main Applications Of Cyber Security FrameworkThis slide outlines the main applications of cyber security framework which includes enhance cybersecurity program, prioritize improvement tasks, etc. Introducing Main Applications Of Cyber Security Framework to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Enhance Cybersecurity Program, Prioritize Improvement Tasks, Know Security Status, Guide Investment Decisions, using this template. Grab it now to reap its full benefits.




