Powerpoint Templates and Google slides for Cyber Security Apps
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Strategies For Implementing AI Powered Global Technology In Cyber Security
Strategies For Implementing AI Powered Global Technology In Cyber SecurityThis slide shows strategic approaches for implementing AI in cyber security. The purpose of this slide is to strengthen organizations defence against potential cyber attacks to maximize effectiveness of global technological solutions. It covers strategies such as resource allocation, training data, internal processes, etc. Presenting our set of slides with Strategies For Implementing AI Powered Global Technology In Cyber Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Resource Allocation, Training Data, Internal Processes.
-
 Applications For Big Data Analytics In Cyber Security
Applications For Big Data Analytics In Cyber SecurityThis slide represents big data analytics in cybersecurity applications. This includes algorithms for anomalies, boost security intelligence, detect potential frauds, statistical parameter calculations. Presenting our set of slides with name Applications For Big Data Analytics In Cyber Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Detect Potential Frauds, Algorithms For Anomalies, Statistical Parameter Calculation .
-
 Comparative Assessment Of Cyber Security Tools In Automotive Industry
Comparative Assessment Of Cyber Security Tools In Automotive IndustryThis slide highlights comparison of digital security tools in automobile sector. The purpose of this slide is to aid businesses in utilizing reliable software for managing automotive cybersecurity. It includes elements such as intrusion detection, secure boot, etc. Introducing our Comparative Assessment Of Cyber Security Tools In Automotive Industry set of slides. The topics discussed in these slides are Intrusion Detection, Access Control, Network Monitoring This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Icon For Role Of 5g Technology In Automotive Cyber Security
Icon For Role Of 5g Technology In Automotive Cyber SecurityIntroducing our premium set of slides with Icon For Role Of 5g Technology In Automotive Cyber Security Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon For Role, 5G Technology In Automotive, Cyber Security So download instantly and tailor it with your information.
-
 Regular Backup Techniques Application Business Recovery Plan To Overcome Cyber Security Threat
Regular Backup Techniques Application Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information on various methods of data backups that should be implemented by a company to avoid data loss. It includes data backup types such as full, incremental, differential, and mirror. Present the topic in a bit more detail with this Regular Backup Techniques Application Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Techniques, Application, Incremental. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Applications Of SIEM Cyber Security With Functions
Applications Of SIEM Cyber Security With FunctionsThis slide showcases the applicational theory of SIEM cyber security. Its aim is to collect and normalise and prove SIEM capabilities. This slide includes collection, normalisation, enrichment, correlation, etc. Introducing our Applications Of SIEM Cyber Security With Functions set of slides. The topics discussed in these slides are Collection, Enrichment, Correlation . This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Comparative Analysis Of SIEM Cyber Security Monitoring Tools
Comparative Analysis Of SIEM Cyber Security Monitoring ToolsThis slide showcases the comparative analysis of SIEM cyber security tools. Its objective is to detect threats and log analysis. This slide includes log analysis, LogPoint, ExaBeam infusion, ManageEngine and DataDog security. Presenting our well structured Comparative Analysis Of SIEM Cyber Security Monitoring Tools. The topics discussed in this slide are Datadog Security, Logpoint, Manageengine Log. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Attacks In Blockchain Technology
Cyber Security Attacks In Blockchain TechnologyPresenting our set of slides with Cyber Security Attacks In Blockchain Technology. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Interception, Floods Networks, False Identities.
-
 Icon For Blockchain Technology In Cyber Security
Icon For Blockchain Technology In Cyber SecurityPresenting our well structured Icon For Blockchain Technology In Cyber Security. The topics discussed in this slide are Icon, Blockchain Technology, Cyber Security. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Ai Technology Implementation Icon For Robust OT Cyber Security
Ai Technology Implementation Icon For Robust OT Cyber SecurityPresenting our set of slides with Ai Technology Implementation Icon For Robust OT Cyber Security This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on AI Technology Implementation Icon, Robust OT Cyber Security
-
 Applications Of Cyber Security In Industry 4 0
Applications Of Cyber Security In Industry 4 0This slide showcases the various applications of cyber security in industry 4.0. Its objective is to include the elements of remote interface and desktop. This slide includes IP, ethernet, CIP, Modbus and RFID. Presenting our well structured Applications Of Cyber Security In Industry 4 0. The topics discussed in this slide are Functions, Comments, Ethernet, CIP. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 NIDS Tools Comparison To Ensure Cyber Security
NIDS Tools Comparison To Ensure Cyber SecurityThis Slide Represents NIDS Software Comparative Assessment To Establish Cyber Security. It Aims To Select Right NIDS Tool Depending On Specific Requirements Of Organization. Presenting Our Well Structured NIDS Tools Comparison To Ensure Cyber Security. The Topics Discussed In This Slide Are Cyber Security, Comparison, Organization. This Is An Instantly Available Powerpoint Presentation That Can Be Edited Conveniently. Download It Right Away And Captivate Your Audience.
-
 Areas And Application Of Fintech Cyber Security
Areas And Application Of Fintech Cyber SecurityThis slide showcases the areas of fintech cyber security. Its purpose is to secure the various applications against financial attacks. This slide includes payment, insurance, deposit, investment management, deposit, market provision, etc. Presenting our set of slides with name Areas And Application Of Fintech Cyber Security. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Payment, Deposit, Insurance, Raise Capital.
-
 Best Technology Strategies For Fintech Cyber Security
Best Technology Strategies For Fintech Cyber SecurityThis slide showcases the best technologies to choose for fintech security management. Its aim is to prioritise the resources and execute the best strategy. This slide includes governance, risk, crisis, service, threat, access, privacy, etc. Presenting our set of slides with name Best Technology Strategies For Fintech Cyber Security. This exhibits information on eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Governance Strategy, Emerging Trends, Risk Compliance, Crisis Management .
-
 Steps To Build Fintech Cyber Security Application
Steps To Build Fintech Cyber Security ApplicationThis slide showcases the steps to create efficient fintech cyber security application. Its objective is to ensure successful implementation of a bug free fintech application. This slide includes app purpose, functionalities, interface, deployment and monitor. Introducing our premium set of slides with name Steps To Build Fintech Cyber Security Application. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Define Your Apps Purpose, Design Intuitive User Interface, Analyze, Monitor And Iterate. So download instantly and tailor it with your information.
-
 Applications Of Cyber Security In Banking For Data Protection
Applications Of Cyber Security In Banking For Data ProtectionThis slide represents cyber security applications in banking for data protection. This template aims to safeguard data and systems, ensure variety of cyber security tools and methodologies at access. It includes different approaches such as network security surveillance, software security, etc. Introducing our Applications Of Cyber Security In Banking For Data Protection set of slides. The topics discussed in these slides are Network Security Surveillance, Software Security, Risk Management. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Types Of Endpoint Cyber Security Tools Building Next Generation Endpoint Security Cybersecurity SS
Types Of Endpoint Cyber Security Tools Building Next Generation Endpoint Security Cybersecurity SSPresent the topic in a bit more detail with this Types Of Endpoint Cyber Security Tools Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Mobile Threat Defense, Endpoint Protection Platform, Advanced Threat Protection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Information Technology List
Cyber Security Information Technology ListThis slide showcases list of cyber security data technology. The purpose of this template is to help businesses in maintaining confidentiality of information systems for building trust of customers in digital age. It includes elements such as firewalls, antivirus, etc. Presenting our set of slides with name Cyber Security Information Technology List. This exhibits information on Eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Firewalls, Intrusion Detection And Prevention Systems, Antivirus, Access Control Systems.
-
 Statistical Analysis Applications In Cyber Security Statistical Analysis Techniques
Statistical Analysis Applications In Cyber Security Statistical Analysis TechniquesThe purpose of this slide is to represent the uses of statistical analysis in cyber security. These include anomaly detection, intrusion detection, risk assessment, incident response, phishing detection and vulnerability assessment. Introducing Statistical Analysis Applications In Cyber Security Statistical Analysis Techniques to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Anomaly Detection, Intrusion Detection, Risk Assessment, Incident Response, using this template. Grab it now to reap its full benefits.
-
 Cyber security technology skills gap priorities
Cyber security technology skills gap prioritiesThis slide illustrates the top IT security concerns for business managers. It includes data loss prevention, firewalls, access management, cloud security, risk management, legal compliance and predictive analysis. Introducing our Cyber Security Technology Skills Gap Priorities set of slides. The topics discussed in these slides are Cyber Security Technology Skills Gap Priorities. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber threat security industry overview with technology adoption rate
Cyber threat security industry overview with technology adoption rateThis slide highlights the cyber threat security industry overview which illustrates the total malware reported and technology invested. Presenting our well structured Cyber Threat Security Industry Overview With Technology Adoption Rate. The topics discussed in this slide are Technology Investment. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
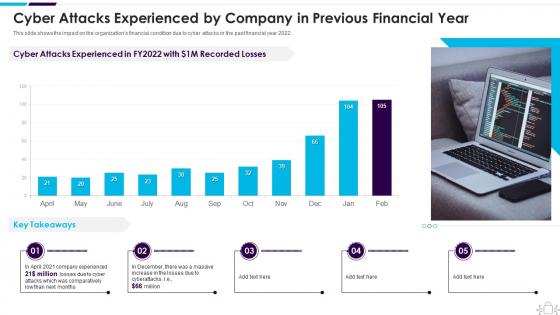 Cyber Attacks Experienced By Company In Previous Information Technology Security
Cyber Attacks Experienced By Company In Previous Information Technology SecurityThis slide shows the impact on the organizations financial condition due to cyber attacks in the past financial year 2022. Present the topic in a bit more detail with this Cyber Attacks Experienced By Company In Previous Information Technology Security. Use it as a tool for discussion and navigation on Experienced, Previous, Financial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Assessment Matrix Of Cyber Risks
Information Technology Security Assessment Matrix Of Cyber RisksThis slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Deliver an outstanding presentation on the topic using this Information Technology Security Assessment Matrix Of Cyber Risks. Dispense information and present a thorough explanation of Assessment Matrix Of Cyber Risks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Cyber Threat Landscape In Information Technology Security
Information Technology Security Cyber Threat Landscape In Information Technology SecurityThis slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Deliver an outstanding presentation on the topic using this Information Technology Security Cyber Threat Landscape In Information Technology Security. Dispense information and present a thorough explanation of Landscape, Information, Technology using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Strategies To Manage Cyber Risks
Information Technology Security Strategies To Manage Cyber RisksThis slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Increase audience engagement and knowledge by dispensing information using Information Technology Security Strategies To Manage Cyber Risks. This template helps you present information on four stages. You can also present information on Strategic, Structures, Implementation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber security apps ppt powerpoint presentation professional background designs cpb
Cyber security apps ppt powerpoint presentation professional background designs cpbPresenting our Cyber Security Apps Ppt Powerpoint Presentation Professional Background Designs Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Cyber Security Apps This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Need Of Cyber Security In Organization Integration Of Digital Technology In Business
Need Of Cyber Security In Organization Integration Of Digital Technology In BusinessThis slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation.Introducing Need Of Cyber Security In Organization Integration Of Digital Technology In Business to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Security For Confidential Data, Protection Phishing Scams, Protection Against Malware using this template. Grab it now to reap its full benefits.
-
 Information Technology Cyber Security Icon
Information Technology Cyber Security IconIntroducing our premium set of slides with Information Technology Cyber Security Icon. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Information Technology, Cyber Security. So download instantly and tailor it with your information.
-
 Cyber Security Reporting Tools For Business
Cyber Security Reporting Tools For BusinessThis slide shows comparative analysis of business cyber security reporting software. It includes features, compatibility, price and ratings.Presenting our well structured Cyber Security Reporting Tools For Business. The topics discussed in this slide are Threat Notification, Threat Monitoring, Attacks Blocking. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Prioritized Cyber Security Threats With Risk Risk Management Guide For Information Technology Systems
Prioritized Cyber Security Threats With Risk Risk Management Guide For Information Technology SystemsThis slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Present the topic in a bit more detail with this Prioritized Cyber Security Threats With Risk Risk Management Guide For Information Technology Systems. Use it as a tool for discussion and navigation on Threat Risk, Risk Mitigation Plan, Risk Owner. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Elements IT Application Security Element Of Cyber Security Ppt Background
Cyber Security Elements IT Application Security Element Of Cyber Security Ppt BackgroundThis slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. The application threat categories include input validation, authorization, session management, parameter tampering, and encryption. Present the topic in a bit more detail with this Cyber Security Elements IT Application Security Element Of Cyber Security Ppt Background. Use it as a tool for discussion and navigation on Session Management, Application Security, Application Threat Categories. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Elements IT Tools Used For Cyber Security Goals Ppt Brochure
Cyber Security Elements IT Tools Used For Cyber Security Goals Ppt BrochureThis slide outlines the tools used to achieve cyber security goals such as confidentiality, integrity, and availability. The tools for confidentiality include encryption, access control, authentication, authentication, authorization, and physical security. Increase audience engagement and knowledge by dispensing information using Cyber Security Elements IT Tools Used For Cyber Security Goals Ppt Brochure. This template helps you present information on one stage. You can also present information on Tools For Confidentiality, Tools For Integrity, Tools For Availability using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Risk Management Icon In Information Technology
Cyber Security Risk Management Icon In Information TechnologyPresent the topic in a bit more detail with this Cyber Security Risk Management Icon In Information Technology. Use it as a tool for discussion and navigation on Cyber Security, Risk Management, Icon In Information Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Different Security Automation Tools With Pros And Cons Enabling Automation In Cyber Security Operations
Different Security Automation Tools With Pros And Cons Enabling Automation In Cyber Security OperationsThis slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM. Present the topic in a bit more detail with this Different Security Automation Tools With Pros And Cons Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Security Information, Management, Automation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impacts Of Ineffective Information Technology Security Enabling Automation In Cyber Security Operations
Impacts Of Ineffective Information Technology Security Enabling Automation In Cyber Security OperationsThis slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Increase audience engagement and knowledge by dispensing information using Impacts Of Ineffective Information Technology Security Enabling Automation In Cyber Security Operations. This template helps you present information on four stages. You can also present information on Ineffective, Information, Technology using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Automation Integrates Tools Systems And Processes Enabling Automation In Cyber Security Operations
Security Automation Integrates Tools Systems And Processes Enabling Automation In Cyber Security OperationsThis slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. Present the topic in a bit more detail with this Security Automation Integrates Tools Systems And Processes Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Security Automation, Integrates, Processes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Assessment Of Cyber Security Incident Response Tools
Comparative Assessment Of Cyber Security Incident Response ToolsThis slide covers comparative assessment of cyber security incident response tools. It involves features such as advanced threat hunting ability, net flow analysis, user behavior analytics and superior forensic analysis. Introducing our premium set of slides with name Comparative Assessment Of Cyber Security Incident Response Tools. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Comparative Assessment, Cyber Security, Incident Response Tools. So download instantly and tailor it with your information.
-
 Benefits Of Implementing Web Application Firewall Implementing Cyber Security Ppt Structure
Benefits Of Implementing Web Application Firewall Implementing Cyber Security Ppt StructureThis slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc. Increase audience engagement and knowledge by dispensing information using Benefits Of Implementing Web Application Firewall Implementing Cyber Security Ppt Structure. This template helps you present information on one stage. You can also present information on Fights Vulnerabilities, Implementing, Application Firewall using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Comparative Analysis Of Web Application Firewall Products Implementing Cyber Security Ppt Themes
Comparative Analysis Of Web Application Firewall Products Implementing Cyber Security Ppt ThemesThis slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. Present the topic in a bit more detail with this Comparative Analysis Of Web Application Firewall Products Implementing Cyber Security Ppt Themes. Use it as a tool for discussion and navigation on Cookie Tampering, Comparative Analysis, Firewall Products. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Management Technology Framework
Cyber Security Management Technology FrameworkThis slide provides a strategic framework for cyber security management used by organisations to implement and monitor the essential activities. Key components are to identify, protect, detect, respond and recover. Introducing our premium set of slides with Cyber Security Management Technology Framework. Elucidate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Protect, Identify, Detect, Respond, Recover. So download instantly and tailor it with your information.
-
 Cyber Security Tools Technologies In Powerpoint And Google Slides Cpb
Cyber Security Tools Technologies In Powerpoint And Google Slides CpbPresenting our Cyber Security Tools Technologies In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Cyber Security Tools Technologies. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Operational Technology Cyber Security In Powerpoint And Google Slides Cpb
Operational Technology Cyber Security In Powerpoint And Google Slides CpbPresenting our Operational Technology Cyber Security In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Operational Technology Cyber Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cyber Security Policy Critical Components Of Information Technology Policy
Cyber Security Policy Critical Components Of Information Technology PolicyThis slide depicts the critical components of information technology policy, and it includes integrity, confidentiality, and availability, including how these components work. Deliver an outstanding presentation on the topic using this Cyber Security Policy Critical Components Of Information Technology Policy. Dispense information and present a thorough explanation of Information, Technology, Components using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Policy Information Technology Policy Implementation Budget For Fy2022
Cyber Security Policy Information Technology Policy Implementation Budget For Fy2022This slide represents the companys IT policy implementation budget for FY2022. It covers the details of the software application and security services that need to be purchased and updated. Present the topic in a bit more detail with this Cyber Security Policy Information Technology Policy Implementation Budget For Fy2022. Use it as a tool for discussion and navigation on Information, Technology, Implementation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Policy Introduction To Information Technology Policy
Cyber Security Policy Introduction To Information Technology PolicyThis slide represents the introduction to information technology policy, and it also describes the components of IT policy, such as investments, business applications, architecture, and infrastructure. Increase audience engagement and knowledge by dispensing information using Cyber Security Policy Introduction To Information Technology Policy. This template helps you present information on seven stages. You can also present information on Introduction, Information, Technology using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
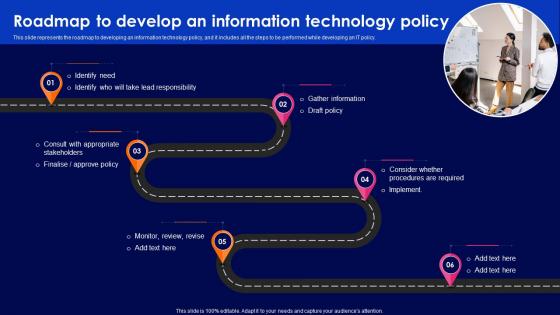 Cyber Security Policy Roadmap To Develop An Information Technology Policy
Cyber Security Policy Roadmap To Develop An Information Technology PolicyThis slide represents the roadmap to developing an information technology policy, and it includes all the steps to be performed while developing an IT policy. Introducing Cyber Security Policy Roadmap To Develop An Information Technology Policy to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Roadmap, Information, Technology, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Policy Timeline To Develop An Information Technology Policy
Cyber Security Policy Timeline To Develop An Information Technology PolicyThis slide represents the timeline to develop an information technology policy and it includes all the steps to be performed while developing an IT policy. Introducing Cyber Security Policy Timeline To Develop An Information Technology Policy to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Timeline, Information, Technology, using this template. Grab it now to reap its full benefits.
-
 Latest Technologies Cyber Security Technology Market Overview Ppt Slides Summary
Latest Technologies Cyber Security Technology Market Overview Ppt Slides SummaryThis slide explains Cyber security technology market overview with top players in the year 2021. It also predicts market growth and compound annual growth rate from year 2021 till 2028. Deliver an outstanding presentation on the topic using this Latest Technologies Cyber Security Technology Market Overview Ppt Slides Summary. Dispense information and present a thorough explanation of Technology, Security, Market using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Latest Technologies Need For Cyber Security Technology Ppt Slides Inspiration
Latest Technologies Need For Cyber Security Technology Ppt Slides InspirationThis slide gives an overview of cyber security technology. It also gives an idea about which industries are most venerable for a cyber attack and why cyber security is needed. Increase audience engagement and knowledge by dispensing information using Latest Technologies Need For Cyber Security Technology Ppt Slides Inspiration. This template helps you present information on three stages. You can also present information on Internet, Security, Cyber using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
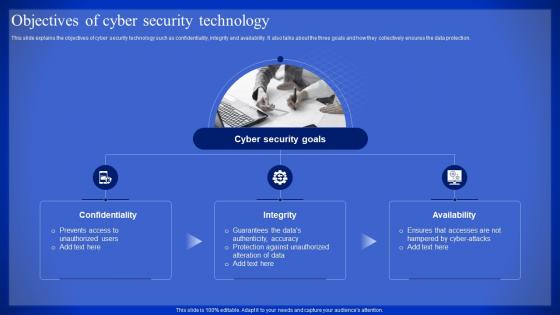 Latest Technologies Objectives Of Cyber Security Technology Ppt Slides Infographics
Latest Technologies Objectives Of Cyber Security Technology Ppt Slides InfographicsThis slide explains the objectives of cyber security technology such as confidentiality, integrity and availability. It also talks about the three goals and how they collectively ensures the data protection. Introducing Latest Technologies Objectives Of Cyber Security Technology Ppt Slides Infographics to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Confidentiality, Integrity, Availability, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Attacks Response Plan Benefits Of Implementing Web Application Firewall
Cyber Security Attacks Response Plan Benefits Of Implementing Web Application FirewallThis slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Benefits Of Implementing Web Application Firewall. Use it as a tool for discussion and navigation on Fights Vulnerabilities, Application Firewall, Confidential Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Comparative Analysis Of Web Application Firewall Products
Cyber Security Attacks Response Plan Comparative Analysis Of Web Application Firewall ProductsThis slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Plan Comparative Analysis Of Web Application Firewall Products. Dispense information and present a thorough explanation of Comparative Analysis, Web Application, Firewall Products using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents Raising Cyber Security Awareness In Organizations Using Various Tools And Tactics
Table Of Contents Raising Cyber Security Awareness In Organizations Using Various Tools And TacticsIncrease audience engagement and knowledge by dispensing information using Table Of Contents Raising Cyber Security Awareness In Organizations Using Various Tools And Tactics. This template helps you present information on twelve stages. You can also present information on Cyber Security, Training Software, Prevention Techniques using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Applications Of Artificial Intelligence In Cyber Security
Applications Of Artificial Intelligence In Cyber SecurityThis slide signifies the software of artificial intelligence to increase cyber security. It covers information about applications like system security, crime prevention, analyse mobile endpoints and detection of cyber attacks Presenting our set of slides with Applications Of Artificial Intelligence In Cyber Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Systems Security, Security, Analyse.
-
 Comparative Analysis Of Cyber Security Threat Assessment Tools
Comparative Analysis Of Cyber Security Threat Assessment ToolsThis slide provides a comparative analysis of various tools to detect and assess cyber security threats in the industry to gain insights about which tool to implement. The major tools are Nessus home, GFI Languard, QualysGuard and n Circle IP 360 Presenting our well structured Comparative Analysis Of Cyber Security Threat Assessment Tools. The topics discussed in this slide are Nessus Home, Compatible Mechanisms. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
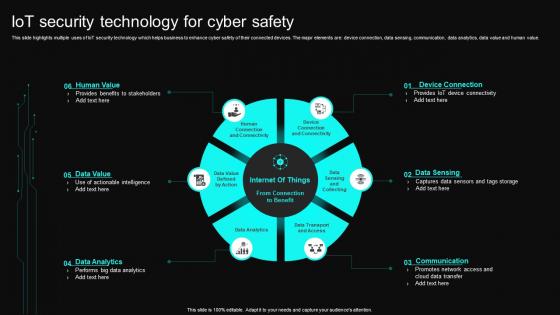 IOT Security Technology For Cyber Safety
IOT Security Technology For Cyber SafetyThis slide highlights multiple uses of IoT security technology which helps business to enhance cyber safety of their connected devices. The major elements are device connection, data sensing, communication, data analytics, data value and human value. Presenting our set of slides with IOT Security Technology For Cyber Safety. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Device Connection, Data Sensing, Communication, Data Analytics.
-
 Blockchain Technology Cyber Security Cases
Blockchain Technology Cyber Security CasesThis slide outlines cyber security use cases of block chain technology aimed at adopting secure, vigilant, resilient solution for building secure infrastructure. It covers secure private messaging, IoT security, secure DNS and DDoS, provenance of software and infrastructure verification. Presenting our set of slides with Blockchain Technology Cyber Security Cases. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Secure Private Messaging, Infrastructure Verification, Iot Security.
-
 Use Of Blockchain Technology In Cyber Security Blockchain Applications In Different Sectors
Use Of Blockchain Technology In Cyber Security Blockchain Applications In Different SectorsThis slide outlines the applications of blockchain technology in protecting against cyber security attacks. The purpose of this slide is to showcase the benefits, deployment factors, and top adopters for blockchain technology. It also includes the key feature that prevents fraud. Deliver an outstanding presentation on the topic using this Use Of Blockchain Technology In Cyber Security Blockchain Applications In Different Sectors. Dispense information and present a thorough explanation of Blockchain Features, Blockchain Platforms, Data Tampering using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Baseline security encryption secure print cyber security local applications
Baseline security encryption secure print cyber security local applicationsPresenting this set of slides with name - Baseline Security Encryption Secure Print Cyber Security Local Applications. This is an editable six graphic that deals with topics like Baseline Security, Encryption Secure Print, Cyber Security, Local Applications to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Latest cyber security technology ppt powerpoint presentation gallery rules cpb
Latest cyber security technology ppt powerpoint presentation gallery rules cpbPresenting this set of slides with name Latest Cyber Security Technology Ppt Powerpoint Presentation Gallery Rules Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Latest Cyber Security Technology to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.





