Powerpoint Templates and Google slides for Cyber Risk
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Gap identification current approach process flaws managing cyber risk in a digital age
Gap identification current approach process flaws managing cyber risk in a digital agePurpose of this slide is to highlight the existing approach and process flaws along with the cost incur details. It also shows that company is treating security and privacy as after thoughts. Present the topic in a bit more detail with this Gap Identification Current Approach Process Flaws Managing Cyber Risk In A Digital Age. Use it as a tool for discussion and navigation on Gap Identification Current Approach Process Flaws And Cost. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Icons slide for managing cyber risk in a digital age
Icons slide for managing cyber risk in a digital agePresenting our well crafted Icons Slide For Managing Cyber Risk In A Digital Age set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly.
-
 Information security program framework managing cyber risk in a digital age
Information security program framework managing cyber risk in a digital ageMentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver an outstanding presentation on the topic using this Information Security Program Framework Managing Cyber Risk In A Digital Age. Dispense information and present a thorough explanation of Information Security Program Framework Key Components using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Introducing new incidents logging process managing cyber risk in a digital age
Introducing new incidents logging process managing cyber risk in a digital ageThis slide displays the new incident logging process that company will introduce. It covers information of logging process, its description and responsible person details. Present the topic in a bit more detail with this Introducing New Incidents Logging Process Managing Cyber Risk In A Digital Age. Use it as a tool for discussion and navigation on Introducing New Incidents Logging Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key security controls to be addressed in the program managing cyber risk in a digital age
Key security controls to be addressed in the program managing cyber risk in a digital agePurpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Increase audience engagement and knowledge by dispensing information using Key Security Controls To Be Addressed In The Program Managing Cyber Risk In A Digital Age. This template helps you present information on three stages. You can also present information on Framework, Elaborates, Security, Controls, Recovery using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Managing cyber risk in a digital age information security program values to business
Managing cyber risk in a digital age information security program values to businessFollowing slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. Introducing Managing Cyber Risk In A Digital Age Information Security Program Values To Business to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Response, Management, Vulnerabilities, using this template. Grab it now to reap its full benefits.
-
 Overview of new it policy framework managing cyber risk in a digital age
Overview of new it policy framework managing cyber risk in a digital ageThis slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies. Present the topic in a bit more detail with this Overview Of New It Policy Framework Managing Cyber Risk In A Digital Age. Use it as a tool for discussion and navigation on Overview Of New IT Policy Framework. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Responsibility matrix to ensure effective risk managing cyber risk in a digital age
Responsibility matrix to ensure effective risk managing cyber risk in a digital ageThis slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed. Deliver an outstanding presentation on the topic using this Responsibility Matrix To Ensure Effective Risk Managing Cyber Risk In A Digital Age. Dispense information and present a thorough explanation of Responsibility Matrix To Ensure Effective Risk Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk governance structure managing cyber risk in a digital age
Risk governance structure managing cyber risk in a digital ageMentioned slide illustrates risk governance framework of the company. It include information about different governing committees along with their deliverables. Present the topic in a bit more detail with this Risk Governance Structure Managing Cyber Risk In A Digital Age. Use it as a tool for discussion and navigation on Risk Governance Structure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Scorecard to check cybersecurity managing cyber risk in a digital age
Scorecard to check cybersecurity managing cyber risk in a digital ageFollowing slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. Present the topic in a bit more detail with this Scorecard To Check Cybersecurity Managing Cyber Risk In A Digital Age. Use it as a tool for discussion and navigation on Organization, Misconduct, Prevention, Appropriate. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security lifecycle managing cyber risk in a digital age
Security lifecycle managing cyber risk in a digital ageIncrease audience engagement and knowledge by dispensing information using Security Lifecycle Managing Cyber Risk In A Digital Age. This template helps you present information on one stages. You can also present information on Security Lifecycle using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Setting scenario for cybersecurity control managing cyber risk in a digital age
Setting scenario for cybersecurity control managing cyber risk in a digital ageFollowing slide displays information about the companys cyber security control scenario setting. It includes scenario detail, category of security controls and controls description. Deliver an outstanding presentation on the topic using this Setting Scenario For Cybersecurity Control Managing Cyber Risk In A Digital Age. Dispense information and present a thorough explanation of Setting Scenario For Cybersecurity Control using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Summary existing security managing cyber risk in a digital age
Summary existing security managing cyber risk in a digital ageFollowing slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Present the topic in a bit more detail with this Summary Existing Security Managing Cyber Risk In A Digital Age. Use it as a tool for discussion and navigation on Summary Existing Security Management Capabilities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table of contents managing cyber risk in a digital age
Table of contents managing cyber risk in a digital ageDeliver an outstanding presentation on the topic using this Table Of Contents Managing Cyber Risk In A Digital Age. Dispense information and present a thorough explanation of Market, Digitization, Understanding, Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat drivers and emerging managing cyber risk in a digital age
Threat drivers and emerging managing cyber risk in a digital ageMentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. Introducing Threat Drivers And Emerging Managing Cyber Risk In A Digital Age to increase your presentation threshold. Encompassed with threee stages, this template is a great option to educate and entice your audience. Dispence information on Internet Of Things, Artificial Intelligence, Human Machine Interface, using this template. Grab it now to reap its full benefits.
-
 Threat vulnerability asset matrix managing cyber risk in a digital age
Threat vulnerability asset matrix managing cyber risk in a digital ageMentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Present the topic in a bit more detail with this Threat Vulnerability Asset Matrix Managing Cyber Risk In A Digital Age. Use it as a tool for discussion and navigation on Threat Vulnerability Asset Matrix. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber security risk management framework for threat protection
Cyber security risk management framework for threat protectionThis slide highlights the cyber security risk management framework which include third party risk management, IT risk assessment and security center operations. Presenting our set of slides with Cyber Security Risk Management Framework For Threat Protection. This exhibits information on eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security Governance, Security Assessment, Independent Audit.
-
 Cyber threat report with risk indicator and affected systems
Cyber threat report with risk indicator and affected systemsPresenting our well structured Cyber Threat Report With Risk Indicator And Affected Systems. The topics discussed in this slide are Risk Level, Risk Indication, Potential Affected Systems. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber threat security planning process with risk tolerance and threats
Cyber threat security planning process with risk tolerance and threatsThis following slide illustrates the cyber security threat program planning which include steps like identify key personnel, risk tolerance strategy and developing frequency. Presenting our set of slides with Cyber Threat Security Planning Process With Risk Tolerance And Threats. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Built Risk Tolerance, Identify And Document, Establish Governance.
-
 Risk Based Methodology To Cyber Threat Drivers And Emerging Technologies Impact On Cyber Security
Risk Based Methodology To Cyber Threat Drivers And Emerging Technologies Impact On Cyber SecurityMentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security.Increase audience engagement and knowledge by dispensing information using Risk Based Methodology To Cyber Risk Based Methodology To Cyber Threat Drivers And Emerging Technologies Impact On Cyber Security security This template helps you present information on one stage. You can also present information on Artificial Intelligence, Human Machine Interface, Internet Of Things using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Risk Based Methodology To Cyber And Information Security Table Of Contents
Risk Based Methodology To Cyber And Information Security Table Of ContentsDeliver an outstanding presentation on the topic using this Risk Based Methodology To Cyber And Information Security Table Of Contents Dispense information and present a thorough explanation of Threat Matrix, Identified Assets, Impact Assessment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Risk Management Framework Introduction
Cyber Risk Management Framework IntroductionThe slide highlights the cyber risk management framework introduction by outlining legal compliance, operations, human resources, contingency plan and governance. Presenting our set of slides with Cyber Risk Management Framework Introduction. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Legal Compliance, Operations, Human Resource, Contingency Plan, Governance.
-
 Risk Based Methodology To Cyber Information Security Program Framework Key Components
Risk Based Methodology To Cyber Information Security Program Framework Key ComponentsMentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc.Introducing Risk Based Methodology To Cyber Information Security Program Framework Key Components to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Culture And Awareness, Security Risk Management, Data Security And Privacy, using this template. Grab it now to reap its full benefits.
-
 Information Security Assessment Matrix Of Cyber Risks
Information Security Assessment Matrix Of Cyber RisksThis slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Present the topic in a bit more detail with this Information Security Assessment Matrix Of Cyber Risks. Use it as a tool for discussion and navigation on Assessment Matrix Of Cyber Risks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Strategies To Manage Cyber Risks
Information Security Strategies To Manage Cyber RisksThis slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Introducing Information Security Strategies To Manage Cyber Risks to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Strategies To Manage Cyber Risks, using this template. Grab it now to reap its full benefits.
-
 Solution Recommendation For Common Business Cyber Security Risks
Solution Recommendation For Common Business Cyber Security RisksThis slide covers the major IT support skills that could potentially help organizations to solve the most common IT problems. It includes solutions for common cyber risks such as poor network security, data backup issues, etc. Introducing our premium set of slides with Solution Recommendation For Common Business Cyber Security Risks. Ellicudate the two stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Risks, Solution Recommendation, Network Security. So download instantly and tailor it with your information.
-
 Action Plan In Case Of Breaches Risk Based Methodology To Cyber
Action Plan In Case Of Breaches Risk Based Methodology To CyberMentioned slide illustrates the mitigation plan of the company in case of any security breach. Sections covered are threat encountered, risk level, resources required and expected resolution time.Present the topic in a bit more detail with this Action Plan In Case Of Breaches Risk Based Methodology To Cyber Use it as a tool for discussion and navigation on Security Breach, Confidential Information, Resources Required This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Addressing The Companies Digitization Levelsby Sectors Risk Based Methodology To Cyber
Addressing The Companies Digitization Levelsby Sectors Risk Based Methodology To CyberMentioned slide provides information about the companys digitalization levels by sectors. Digitalization level is measured based on asset, usage and labor.Deliver an outstanding presentation on the topic using this Addressing The Companies Digitization Levelsby Sectors Risk Based Methodology To Cyber Dispense information and present a thorough explanation of Business Processes, Digital Spend On Workers, Digitalization Of Work using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Categorization Worksheet For Assets Owned By Organization Risk Based Methodology To Cyber
Categorization Worksheet For Assets Owned By Organization Risk Based Methodology To CyberThis slide illustrates asset categorization worksheet covering information about security system such as system name, its version, system location and other general information.Introducing Categorization Worksheet For Assets Owned By Organization Risk Based Methodology To Cyber to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on System Accessibility, Individual System, Organizational Information using this template. Grab it now to reap its full benefits.
-
 Checklist For Effectively Managing Asset Security Risk Based Methodology To Cyber
Checklist For Effectively Managing Asset Security Risk Based Methodology To CyberFollowing slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them.Increase audience engagement and knowledge by dispensing information using Checklist For Effectively Managing Asset Security Risk Based Methodology To Cyber This template helps you present information on one stage. You can also present information on System Monitoring, Data Backup, Security Patches using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Communication Plan For Cyberbreaches Risk Based Methodology To Cyber
Communication Plan For Cyberbreaches Risk Based Methodology To CyberMentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible.Introducing Communication Plan For Cyberbreaches Risk Based Methodology To Cyber to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Address Potential Security, Development Process, Quality Standards using this template. Grab it now to reap its full benefits.
-
 Criticality Assessment Of Identified Assets Risk Based Methodology To Cyber
Criticality Assessment Of Identified Assets Risk Based Methodology To CyberFollowing slide demonstrates the asset criticality of identified system components. It covers details such as major components used along with criticality rating and failure cost.Increase audience engagement and knowledge by dispensing information using Criticality Assessment Of Identified Assets Risk Based Methodology To Cyber This template helps you present information on five stages. You can also present information on Major Components, Criticality Rating, Infrastructure Hardware using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Defining Business Priorities To Ensure Information Security Risk Based Methodology To Cyber
Defining Business Priorities To Ensure Information Security Risk Based Methodology To CyberThis slide illustrates the key business priorities of the organization such as efficient risk management, standardized incident management process to ensure information security.Increase audience engagement and knowledge by dispensing information using Defining Business Priorities To Ensure Information Security Risk Based Methodology To Cyber This template helps you present information on three stages. You can also present information on Efficient Risk Management, Transparent Communication, Standardized Incident using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Defining Risk Events Based On Impact Size And Risk Based Methodology To Cyber
Defining Risk Events Based On Impact Size And Risk Based Methodology To CyberThis slide provides information about risk based events that company will use to define the risks based on impact size and likelihood of occurrence.Present the topic in a bit more detail with this Defining Risk Events Based On Impact Size And Risk Based Methodology To Cyber Use it as a tool for discussion and navigation on Level Is Extremely, Risk Appetite, Level Is Highly Critical This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Eliminating Manual Security Processes Through Automation Risk Based Methodology To Cyber
Eliminating Manual Security Processes Through Automation Risk Based Methodology To CyberMentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools.Present the topic in a bit more detail with this Eliminating Manual Security Processes Through Automation Risk Based Methodology To Cyber Use it as a tool for discussion and navigation on Manual Vulnerability, Scanning And Resolution, Vulnerability Scanning This template is free to edit as deemed fit for your organization. Therefore download it now.
-
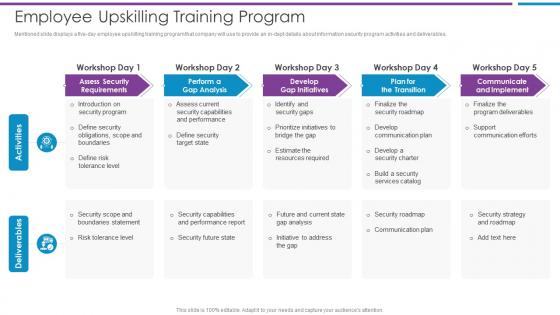 Employee Upskilling Training Program Risk Based Methodology To Cyber
Employee Upskilling Training Program Risk Based Methodology To CyberMentioned slide displays a five day employee upskilling training program that company will use to provide an in dept details about information security program activities and deliverables.Deliver an outstanding presentation on the topic using this Employee Upskilling Training Program Risk Based Methodology To Cyber Dispense information and present a thorough explanation of Assess Security Requirements, Perform A Gap Analysis, Develop Gap Initiatives using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Flow Diagram Of Incident Response Process Risk Based Methodology To Cyber
Flow Diagram Of Incident Response Process Risk Based Methodology To CyberMentioned slide addresses the upcoming incident response process through flow diagram. Here the diagram is divided into three sections namely preparatory, core response and close down.Deliver an outstanding presentation on the topic using this Flow Diagram Of Incident Response Process Risk Based Methodology To Cyber Dispense information and present a thorough explanation of Capture And Analyze, Contain Mitigate, Remediate Eradicate using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Gap Identification Current Approach Process Flaws And Cost Risk Based Methodology To Cyber
Gap Identification Current Approach Process Flaws And Cost Risk Based Methodology To CyberPurpose of this slide is to highlight the existing approach and process flaws along with the cost incur details. It also shows that company is treating security and privacy as after thoughts.Introducing Gap Identification Current Approach Process Flaws And Cost Risk Based Methodology To Cyber to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Design And Development, Requirements, Deployment using this template. Grab it now to reap its full benefits.
-
 Gap Identification Current Approach Process Flaws And Risk Based Methodology To Cyber
Gap Identification Current Approach Process Flaws And Risk Based Methodology To CyberPurpose of this slide is to highlight the existing approach and process flaws along with the cost incur details. It also shows that company is treating security and privacy as after thoughts.Increase audience engagement and knowledge by dispensing information using Gap Identification Current Approach Process Flaws And Risk Based Methodology To Cyber This template helps you present information on three stages. You can also present information on Security Organization, Information Security Processes, Technology Controls using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide For Risk Based Methodology To Cyber and Information Security
Icons Slide For Risk Based Methodology To Cyber and Information SecurityPresenting our well crafted Icons Slide For Risk Based Methodology To Cyber and Information Security set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly
-
 Information Security Program Framework Key Components Risk Based Methodology To Cyber
Information Security Program Framework Key Components Risk Based Methodology To CyberMentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc.Introducing Information Security Program Framework Key Components Risk Based Methodology To Cyber to increase your presentation threshold. Encompassed with one stage this template is a great option to educate and entice your audience. Dispence information on Culture And Awareness, Security Risk Management, Data Security And Privacy using this template. Grab it now to reap its full benefits.
-
 Information Security Program Values To Business Risk Based Methodology To Cyber
Information Security Program Values To Business Risk Based Methodology To CyberFollowing slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management.Increase audience engagement and knowledge by dispensing information using Information Security Program Values To Business Risk Based Methodology To Cyber This template helps you present information on two stages. You can also present information on Undetectable By Current, Vulnerabilities In The Current, Threats To The Companys Environment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Introducing New Incidents Logging Process Risk Based Methodology To Cyber
Introducing New Incidents Logging Process Risk Based Methodology To CyberThis slide displays the new incident logging process that company will introduce. It covers information of logging process, its description and responsible person details.Increase audience engagement and knowledge by dispensing information using Introducing New Incidents Logging Process Risk Based Methodology To Cyber This template helps you present information on one stage. You can also present information on Provide Integration, Category Selection, Consider Internal using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key Security Controls To Be Addressed In The Program Risk Based Methodology To Cyber
Key Security Controls To Be Addressed In The Program Risk Based Methodology To CyberPurpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications.Present the topic in a bit more detail with this Key Security Controls To Be Addressed In The Program Risk Based Methodology To Cyber Use it as a tool for discussion and navigation on Prevents Attacks, Limits Extent Of Attacks, Data Recovery This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview Of New It Policy Framework Risk Based Methodology To Cyber
Overview Of New It Policy Framework Risk Based Methodology To CyberThis slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies.Introducing Overview Of New It Policy Framework Risk Based Methodology To Cyber to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Acceptable Usage Policy, Data Policies, Data Management Policy using this template. Grab it now to reap its full benefits.
-
 Responsibility Matrix To Ensure Effective Risk Management Risk Based Methodology To Cyber
Responsibility Matrix To Ensure Effective Risk Management Risk Based Methodology To CyberThis slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed.Present the topic in a bit more detail with this Responsibility Matrix To Ensure Effective Risk Management Risk Based Methodology To Cyber Use it as a tool for discussion and navigation on Cybersecurity Strategy, Program Implementation, Program Monitoring This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Governance Structure Risk Based Methodology To Cyber
Risk Governance Structure Risk Based Methodology To CyberMentioned slide illustrates risk governance framework of the company. It include information about different governing committees along with their deliverables.Deliver an outstanding presentation on the topic using this Risk Governance Structure Risk Based Methodology To Cyber Dispense information and present a thorough explanation of Executive Committee, Risk And Audit Committee, Investment Oversight Committee using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Setting Scenario For Cybersecurity Control Risk Based Methodology To Cyber
Setting Scenario For Cybersecurity Control Risk Based Methodology To CyberFollowing slide displays information about the companys cyber security control scenario setting. It includes scenario detail, category of security controls and controls description.Present the topic in a bit more detail with this Setting Scenario For Cybersecurity Control Risk Based Methodology To Cyber Use it as a tool for discussion and navigation on Technical Controls, Management Controls, Operational Controls This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Summary Existing Security Management Capabilities Risk Based Methodology To Cyber
Summary Existing Security Management Capabilities Risk Based Methodology To CyberFollowing slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating.Deliver an outstanding presentation on the topic using this Summary Existing Security Management Capabilities Risk Based Methodology To Cyber Dispense information and present a thorough explanation of Information From Breaching, Occurrence Identification, Information Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents For Risk Based Methodology To Cyber and Information Security
Table Of Contents For Risk Based Methodology To Cyber and Information SecurityPresent the topic in a bit more detail with this Table Of Contents For Risk Based Methodology To Cyber and Information Security Use it as a tool for discussion and navigation on Defining Business Priorities, Global Market Insights, Companies Digitization Levels This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat Vulnerability Asset Matrix Risk Based Methodology To Cyber
Threat Vulnerability Asset Matrix Risk Based Methodology To CyberMentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least.Present the topic in a bit more detail with this Threat Vulnerability Asset Matrix Risk Based Methodology To Cyber Use it as a tool for discussion and navigation on Social Engineering, Ranked Critical Resources, Present IT Safeguards This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Action Plan In Case Of Breaches Introducing A Risk Based Approach To Cyber Security
Action Plan In Case Of Breaches Introducing A Risk Based Approach To Cyber SecurityMentioned slide illustrates the mitigation plan of the company in case of any security breach. Sections covered are threat encountered, risk level, resources required and expected resolution time.Present the topic in a bit more detail with this Action Plan In Case Of Breaches Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on Expected Resolution Time, Responsible Person, Communication Mode This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Agenda Of Introducing A Risk Based Approach To Cyber Security
Agenda Of Introducing A Risk Based Approach To Cyber SecurityIntroducing Agenda Of Introducing A Risk Based Approach To Cyber Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Agenda using this template. Grab it now to reap its full benefits.
-
 Communication Plan For Cyber Breaches Introducing A Risk Based Approach To Cyber Security
Communication Plan For Cyber Breaches Introducing A Risk Based Approach To Cyber SecurityMentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible.Present the topic in a bit more detail with this Communication Plan For Cyber Breaches Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on Evaluate Sprint Status, Quality Standards, Project Coordinator This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Criticality Assessment Of Identified Assets Introducing A Risk Based Approach To Cyber Security
Criticality Assessment Of Identified Assets Introducing A Risk Based Approach To Cyber SecurityFollowing slide demonstrates the asset criticality of identified system components. It covers details such as major components used along with criticality rating and failure cost.Deliver an outstanding presentation on the topic using this Criticality Assessment Of Identified Assets Introducing A Risk Based Approach To Cyber Security Dispense information and present a thorough explanation of Infrastructure Hardware, Routers And Switches, Server Computers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Defining Business Security Introducing A Risk Based Approach To Cyber Security
Defining Business Security Introducing A Risk Based Approach To Cyber SecurityThis slide illustrates the key business priorities of the organization such as efficient risk management, standardized incident management process to ensure information security.Introducing Defining Business Security Introducing A Risk Based Approach To Cyber Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Efficient Risk Management, Standardized Incident, Management Process using this template. Grab it now to reap its full benefits.
-
 Defining Risk Events Based On Introducing A Risk Based Approach To Cyber Security
Defining Risk Events Based On Introducing A Risk Based Approach To Cyber SecurityThis slide provides information about risk based events that company will use to define the risks based on impact size and likelihood of occurrence.Present the topic in a bit more detail with this Defining Risk Events Based On Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on Defining Risk Events Based On Impact Size And Likelihood Of Occurrence This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Eliminating Manual Security Introducing A Risk Based Approach To Cyber Security
Eliminating Manual Security Introducing A Risk Based Approach To Cyber SecurityMentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools.Present the topic in a bit more detail with this Eliminating Manual Security Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on Manual Vulnerability, Scanning And Resolution, Automation Vulnerability This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Embedding Risk Based Approach Into Introducing A Risk Based Approach To Cyber Security
Embedding Risk Based Approach Into Introducing A Risk Based Approach To Cyber SecurityPurpose of this slide is to highlight the risK based approach and process efficiency along with the cost incur details. It also shows that company will develop agile security and privacy models.Introducing Embedding Risk Based Approach Into Introducing A Risk Based Approach To Cyber Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Cyberrisk Management, Security Organization, Information Security Processes using this template. Grab it now to reap its full benefits.
-
 Employee Upskilling Training Program Introducing A Risk Based Approach To Cyber Security
Employee Upskilling Training Program Introducing A Risk Based Approach To Cyber SecurityMentioned slide displays a five day employee upskilling training program that company will use to provide an in dept details about information security program activities and deliverables.Present the topic in a bit more detail with this Employee Upskilling Training Program Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on Assess Security Requirements, Perform A Gap Analysis, Develop Gap Initiatives This template is free to edit as deemed fit for your organization. Therefore download it now.





