Powerpoint Templates and Google slides for Cyber Risk Assessment
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Monitor And Assess Vendor Risk Management Creating Cyber Security Awareness
Monitor And Assess Vendor Risk Management Creating Cyber Security AwarenessThe following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Deliver an outstanding presentation on the topic using this Monitor And Assess Vendor Risk Management Creating Cyber Security Awareness Dispense information and present a thorough explanation of Select Strong Password, Conduct Password Test, Password Encryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Conduct Third Party Risk Assessment Implementing Strategies To Mitigate Cyber Security Threats
Conduct Third Party Risk Assessment Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide illustrates checklist to evaluate third party risk assessment to eliminate unnecessary threats. It includes elements such as cyber security policies, patch management process, physical security guidelines, information safety etc. Deliver an outstanding presentation on the topic using this Conduct Third Party Risk Assessment Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Parameters, Response, Status using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security Threats
Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Present the topic in a bit more detail with this Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Information Security And Privacy, Physical Assets And Data Security, Web Application Security This template is free to edit as deemed fit for your organization. Therefore download it now.
-
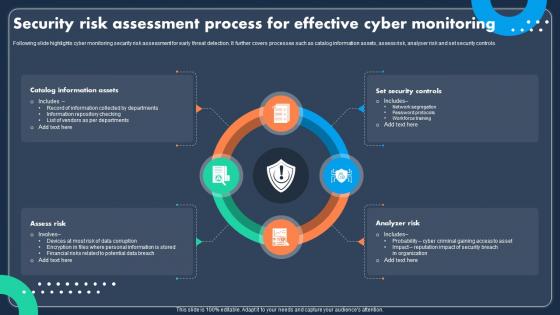 Security Risk Assessment Process For Effective Cyber Monitoring
Security Risk Assessment Process For Effective Cyber MonitoringFollowing slide highlights cyber monitoring security risk assessment for early threat detection. It further covers processes such as catalog information assets, assess risk, analyser risk and set security controls. Introducing our premium set of slides with Security Risk Assessment Process For Effective Cyber Monitoring Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Information Assets, Security Controls, Analyzer Risk. So download instantly and tailor it with your information.
-
 Cyber Impact And Risk Assessment Matrix Business Recovery Plan To Overcome Cyber Security Threat
Cyber Impact And Risk Assessment Matrix Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about the cyber security attack risk assessment matrix which can be leveraged to determine the severity of cyber threats, the likelihood of occurrence, and future action plan. Present the topic in a bit more detail with this Cyber Impact And Risk Assessment Matrix Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Assessment Matrix, Occurrence, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Assessment For Cyber Crisis Management
Risk Assessment For Cyber Crisis ManagementThe purpose of this slide is to underscore how cyber crisis risk assessment proactively identifies. It evaluates and mitigates threats, safeguarding against cyberattacks and minimizing operational impact. Introducing our Risk Assessment For Cyber Crisis Management set of slides. The topics discussed in these slides are Unauthorized Access, Phishing Attacks, Ransomware. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Risk Based Methodology To Cyber Encountered Risks Summary And Their Impact Assessment
Risk Based Methodology To Cyber Encountered Risks Summary And Their Impact AssessmentMentioned slide provides information about the risks encountered by the company till date and their impact on existing business operations.Present the topic in a bit more detail with thisRisk Based Methodology To Cyber Encountered Risks Summary And Their Impact Assessment Use it as a tool for discussion and navigation on Encountered Risks Summary And Their Impact Assessment This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encountered Risks Summary And Their Impact Assessment Risk Based Methodology To Cyber
Encountered Risks Summary And Their Impact Assessment Risk Based Methodology To CyberMentioned slide provides information about the risks encountered by the company till date and their impact on existing business operations.Present the topic in a bit more detail with this Encountered Risks Summary And Their Impact Assessment Risk Based Methodology To Cyber Use it as a tool for discussion and navigation on Encountered Risks Summary And Their Impact Assessment This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Intelligence Risk Assessment Dashboard With Heat Map
Cyber Intelligence Risk Assessment Dashboard With Heat MapThis slide exhibits risk rating breakdown and heat map for analyzing current cyber security measures effectiveness. It covers top 5 vulnerabilities and clients under scrutiny. Introducing our Cyber Intelligence Risk Assessment Dashboard With Heat Map set of slides. The topics discussed in these slides are Risk Possibility, Risk Threshold, Risk Assessment Status. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Attacks Faced By Organization In Risk Assessment And Management Plan For Information Security
Cyber Attacks Faced By Organization In Risk Assessment And Management Plan For Information SecurityThis slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type if cyber attacks and formulate strategies to tackle them Present the topic in a bit more detail with this Cyber Attacks Faced By Organization In Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Experienced, Organization, Financial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
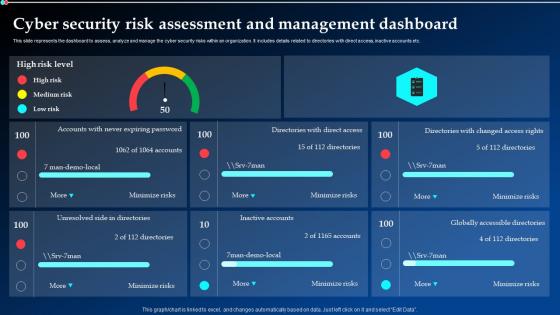 Cyber Security Risk Assessment And Management Dashboard Ppt Portrait
Cyber Security Risk Assessment And Management Dashboard Ppt PortraitThis slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Deliver an outstanding presentation on the topic using this Cyber Security Risk Assessment And Management Dashboard Ppt Portrait. Dispense information and present a thorough explanation of Cyber Security, Risk Assessment, Management Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Risk Assessment And Management Dashboard Incident Response Strategies Deployment
Cyber Security Risk Assessment And Management Dashboard Incident Response Strategies DeploymentThis slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Present the topic in a bit more detail with this Cyber Security Risk Assessment And Management Dashboard Incident Response Strategies Deployment. Use it as a tool for discussion and navigation on Accounts, Globally, Unresolved. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Risk Assessment And Management Dashboard Development And Implementation Of Security
Cyber Security Risk Assessment And Management Dashboard Development And Implementation Of SecurityThis slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Deliver an outstanding presentation on the topic using this Cyber Security Risk Assessment And Management Dashboard Development And Implementation Of Security. Dispense information and present a thorough explanation of Medium Risk, Unresolved Side, Inactive Accounts using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Attacks Response Plan Cyber Security Risk Assessment And Management Dashboard
Cyber Security Attacks Response Plan Cyber Security Risk Assessment And Management DashboardThis slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Plan Cyber Security Risk Assessment And Management Dashboard. Dispense information and present a thorough explanation of Cyber Security, Risk Assessment, Management Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Risk Assessment And Management Dashboard Deploying Computer Security Incident
Cyber Security Risk Assessment And Management Dashboard Deploying Computer Security IncidentThis slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc.Present the topic in a bit more detail with this Cyber Security Risk Assessment And Management Dashboard Deploying Computer Security Incident. Use it as a tool for discussion and navigation on Expiring Password, Accessible Directories, Directories Direct Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Risk Assessment Program Cyber Attacks Faced By Organization
Cybersecurity Risk Assessment Program Cyber Attacks Faced By OrganizationThis slide provides information regarding the number of cyber attacks faced by the organization and its impact on IT operations and system downtime. It also provides details of percentage rise in such attacks since last month. Present the topic in a bit more detail with this Cybersecurity Risk Assessment Program Cyber Attacks Faced By Organization. Use it as a tool for discussion and navigation on Cyber Attacks, IT Operations, System Downtime. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Risk Assessment Program Dashboard For Tracking Cyber Attack Risk Levels
Cybersecurity Risk Assessment Program Dashboard For Tracking Cyber Attack Risk LevelsThe slide represents the dashboard for tracking cyber attack risk levels. It includes information regarding the multiple threat agents, attack methods, preventive controls along with details of risk score and infected systems. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Assessment Program Dashboard For Tracking Cyber Attack Risk Levels. Dispense information and present a thorough explanation of Infrastructure Controls, Preventive Controls, Detective Controls using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity Risk Assessment Program Dashboard To Monitor Cyber Attack Incidents
Cybersecurity Risk Assessment Program Dashboard To Monitor Cyber Attack IncidentsThis slide indicates the dashboard to monitor cyber attacks on IT assets of the firm. It includes information regarding the total cyber attack incidents both month and day wise along with the details of threat class, overall risk factor and top vulnerabilities. Present the topic in a bit more detail with this Cybersecurity Risk Assessment Program Dashboard To Monitor Cyber Attack Incidents. Use it as a tool for discussion and navigation on Dashboard To Monitor, Cyber Attack Incidents, Vulnerabilities, Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Risk Assessment Program Monetary Losses Due To Cyber Crime Events
Cybersecurity Risk Assessment Program Monetary Losses Due To Cyber Crime EventsThis slide tabulates the financial losses faced by the organization in multiple regions across the globe due to cyber crime incidents. The major losses highlighted are data, operational and revenue loss. It also contains details of solution, a cybersecurity program with risk assessment module. Present the topic in a bit more detail with this Cybersecurity Risk Assessment Program Monetary Losses Due To Cyber Crime Events. Use it as a tool for discussion and navigation on Monetary Losses Due, Cyber Crime Events, Mitigation Strategy. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Risk Assessment Program Summary Of Key Cyber Attacks Occurred
Cybersecurity Risk Assessment Program Summary Of Key Cyber Attacks OccurredThis slide shows the summary of key of cybers attacks occurred in organization such as phishing, malware attack, denial of service, SQL injections, identity thefts. It also contains details of the cyber attacker origin such as inadvertent actors, malicious insiders. Present the topic in a bit more detail with this Cybersecurity Risk Assessment Program Summary Of Key Cyber Attacks Occurred. Use it as a tool for discussion and navigation on Cyber Attacks Occurred, Financial Loss, Cyber Attack Origins. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
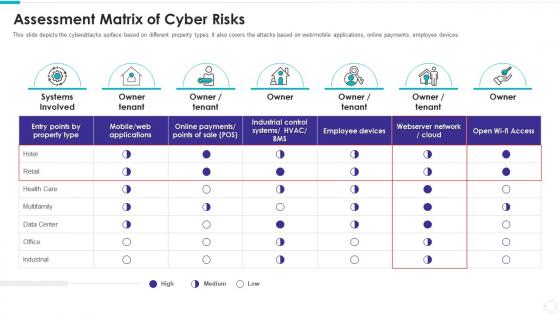 Electronic information security assessment matrix of cyber risks
Electronic information security assessment matrix of cyber risksThis slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Present the topic in a bit more detail with this Electronic Information Security Assessment Matrix Of Cyber Risks. Use it as a tool for discussion and navigation on Systems Involved, Owner Tenant, Data Center, Industrial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Criticality assessment of identified assets managing cyber risk in a digital age
Criticality assessment of identified assets managing cyber risk in a digital ageFollowing slide demonstrates the asset criticality of identified system components. It covers details such as major components used along with criticality rating and failure cost. Introducing Criticality Assessment Of Identified Assets Managing Cyber Risk In A Digital Age to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Major Components, Criticality, Infrastructure, using this template. Grab it now to reap its full benefits.
-
 Information Security Assessment Matrix Of Cyber Risks
Information Security Assessment Matrix Of Cyber RisksThis slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Present the topic in a bit more detail with this Information Security Assessment Matrix Of Cyber Risks. Use it as a tool for discussion and navigation on Assessment Matrix Of Cyber Risks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Criticality Assessment Of Identified Assets Risk Based Methodology To Cyber
Criticality Assessment Of Identified Assets Risk Based Methodology To CyberFollowing slide demonstrates the asset criticality of identified system components. It covers details such as major components used along with criticality rating and failure cost.Increase audience engagement and knowledge by dispensing information using Criticality Assessment Of Identified Assets Risk Based Methodology To Cyber This template helps you present information on five stages. You can also present information on Major Components, Criticality Rating, Infrastructure Hardware using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber security risk management comparative assessment various threat agents
Cyber security risk management comparative assessment various threat agentsThis slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver an outstanding presentation on the topic using this Cyber Security Risk Management Comparative Assessment Various Threat Agents. Dispense information and present a thorough explanation of Insider Threat, Social Engineering, Threat Agents, Cyber Threats using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
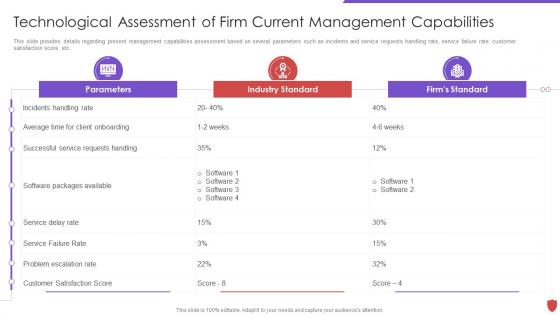 Technological assessment of firm current capabilities cyber security risk management
Technological assessment of firm current capabilities cyber security risk managementThis slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver an outstanding presentation on the topic using this Technological Assessment Of Firm Current Capabilities Cyber Security Risk Management. Dispense information and present a thorough explanation of Parameters, Industry Standard, Firms Standard, Service Delay Rate using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Assessment Matrix Of Cyber Risks
Information Technology Security Assessment Matrix Of Cyber RisksThis slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Deliver an outstanding presentation on the topic using this Information Technology Security Assessment Matrix Of Cyber Risks. Dispense information and present a thorough explanation of Assessment Matrix Of Cyber Risks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
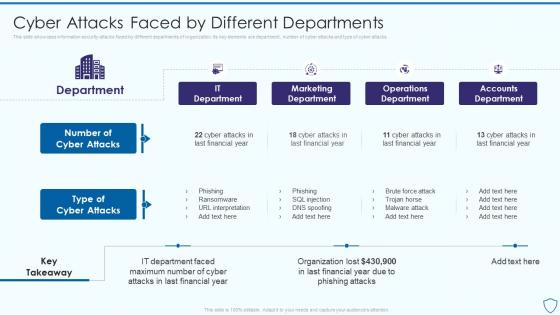 Risk Assessment And Management Plan For Information Security Cyber Attacks Faced By Different
Risk Assessment And Management Plan For Information Security Cyber Attacks Faced By DifferentThis slide showcase information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks Deliver an outstanding presentation on the topic using this Risk Assessment And Management Plan For Information Security Cyber Attacks Faced By Different. Dispense information and present a thorough explanation of Marketing Department, Operations Department, Accounts Department using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Business Cyber Security Risk Assessment Process
Business Cyber Security Risk Assessment ProcessThe slide shows cyber threat detection and protection measures in order to eliminate the potential risks to the business. The steps include identifying, detecting, responding, protecting, and recovering. Presenting our set of slides with Business Cyber Security Risk Assessment Process. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify, Detect, Respond, Protect.
-
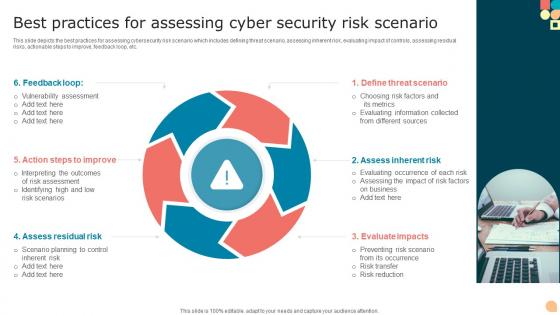 Best Practices For Assessing Cyber Security Risk Scenario
Best Practices For Assessing Cyber Security Risk ScenarioThis slide depicts the best practices for assessing cybersecurity risk scenario which includes defining threat scenario, assessing inherent risk, evaluating impact of controls, assessing residual risks, actionable steps to improve, feedback loop, etc. Introducing our premium set of slides with Best Practices For Assessing Cyber Security Risk Scenario. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Feedback Loop, Define Threat Scenario, Assess Inherent Risk. So download instantly and tailor it with your information.
-
 Prioritized Cyber Security Threats With Risk Mitigation Plan Risk Assessment Of It Systems
Prioritized Cyber Security Threats With Risk Mitigation Plan Risk Assessment Of It SystemsThis slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Present the topic in a bit more detail with this Prioritized Cyber Security Threats With Risk Mitigation Plan Risk Assessment Of It Systems. Use it as a tool for discussion and navigation on Mitigation Plan, Prioritized, Security Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
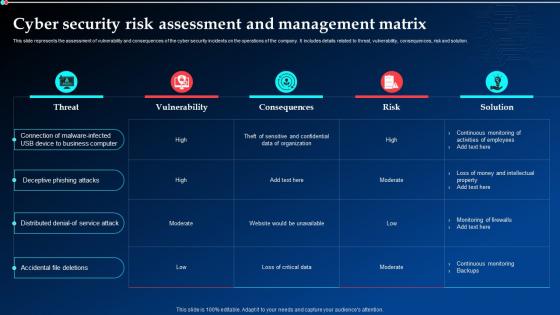 Cyber Security Risk Assessment And Management Matrix Ppt Powerpoint Presentation Layouts Skills
Cyber Security Risk Assessment And Management Matrix Ppt Powerpoint Presentation Layouts SkillsThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Present the topic in a bit more detail with this Cyber Security Risk Assessment And Management Matrix Ppt Powerpoint Presentation Layouts Skills. Use it as a tool for discussion and navigation on Cyber Security, Risk Assessment, Management Matrix. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
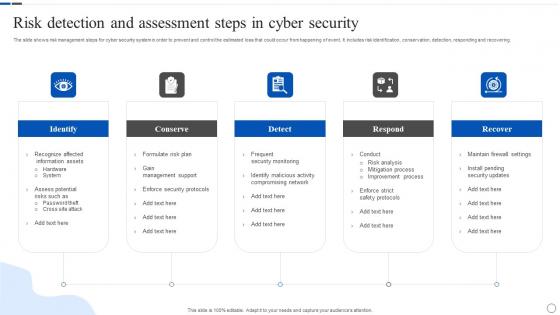 Risk Detection And Assessment Steps In Cyber Security
Risk Detection And Assessment Steps In Cyber SecurityThe slide shows risk management steps for cyber security system in order to prevent and control the estimated loss that could occur from happening of event. It includes risk identification, conservation, detection, responding and recovering. Presenting our set of slides with Risk Detection And Assessment Steps In Cyber Security. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify, Conserve, Respond, Recover.
-
 Risk Assessment Cyber Security In Powerpoint And Google Slides Cpb
Risk Assessment Cyber Security In Powerpoint And Google Slides CpbPresenting Risk Assessment Cyber Security In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase six stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Risk Assessment Cyber Security. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Importance Risk Assessment Cyber Security In Powerpoint And Google Slides Cpb
Importance Risk Assessment Cyber Security In Powerpoint And Google Slides CpbPresenting our Importance Risk Assessment Cyber Security In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases two stages. It is useful to share insightful information on Importance Risk Assessment Cyber Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cyber security risk assessment matrix ppt powerpoint presentation file guidelines cpb
Cyber security risk assessment matrix ppt powerpoint presentation file guidelines cpbPresenting this set of slides with name Cyber Security Risk Assessment Matrix Ppt Powerpoint Presentation File Guidelines Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Cyber Security Risk Assessment Matrix to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Strategy To Minimize Cyber Attacks Multistep Approach To Conduct Cybersecurity Risk Assessment
Strategy To Minimize Cyber Attacks Multistep Approach To Conduct Cybersecurity Risk AssessmentThis slide indicates the multistep approach to conduct cybersecurity risk assessment in business organization. The major steps of process are risk identification, quantification, evaluation, mitigation and monitoring. Introducing Strategy To Minimize Cyber Attacks Multistep Approach To Conduct Cybersecurity Risk Assessment to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Risk Identification, Risk Mapping, Risk Evaluation, Risk Mitigation And Monitoring, using this template. Grab it now to reap its full benefits.
-
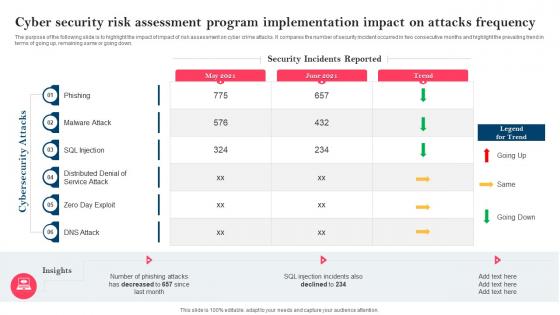 Strategy To Minimize Cyber Attacks Risks Cyber Security Risk Assessment Program Implementation
Strategy To Minimize Cyber Attacks Risks Cyber Security Risk Assessment Program ImplementationThe purpose of the following slide is to highlight the impact of impact of risk assessment on cyber crime attacks. It compares the number of security incident occurred in two consecutive months and highlight the prevailing trend in terms of going up, remaining same or going down. Present the topic in a bit more detail with this Strategy To Minimize Cyber Attacks Risks Cyber Security Risk Assessment Program Implementation. Use it as a tool for discussion and navigation on Cyber Security, Risk Assessment, Program Implementation, Impact On Attacks Frequency. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
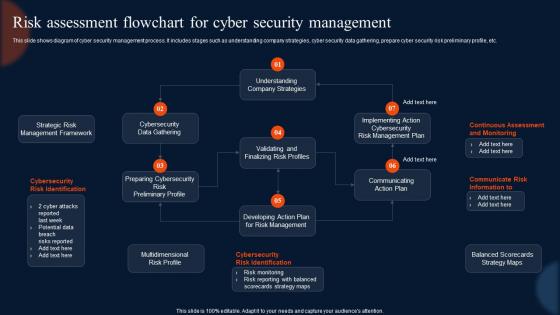 Risk Assessment Flowchart For Cyber Security Management
Risk Assessment Flowchart For Cyber Security ManagementThis slide shows diagram of cyber security management process. It includes stages such as understanding company strategies, cyber security data gathering, prepare cyber security risk preliminary profile, etc. Introducing our Risk Assessment Flowchart For Cyber Security Management set of slides. The topics discussed in these slides are Assessment, Flowchart, Management. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Monitor And Assess Vendor Risk Management Cyber Attack Risks Mitigation
Monitor And Assess Vendor Risk Management Cyber Attack Risks MitigationThe following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Introducing Monitor And Assess Vendor Risk Management Cyber Attack Risks Mitigation to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Web Application Security, Infrastructure Security, Vendor Management, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Risk Assessment And Management Matrix Incident Response Strategies Deployment
Cyber Security Risk Assessment And Management Matrix Incident Response Strategies DeploymentThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Deliver an outstanding presentation on the topic using this Cyber Security Risk Assessment And Management Matrix Incident Response Strategies Deployment. Dispense information and present a thorough explanation of Vulnerability, Consequences, Risk using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Risk Assessment And Management Matrix Development And Implementation Of Security Incident
Cyber Security Risk Assessment And Management Matrix Development And Implementation Of Security IncidentThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Present the topic in a bit more detail with this Cyber Security Risk Assessment And Management Matrix Development And Implementation Of Security Incident. Use it as a tool for discussion and navigation on Consequences, Vulnerability, Risk. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Risk Assessment And Management Matrix Cyber Security Attacks Response Plan
Cyber Security Risk Assessment And Management Matrix Cyber Security Attacks Response PlanThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Deliver an outstanding presentation on the topic using this Cyber Security Risk Assessment And Management Matrix Cyber Security Attacks Response Plan. Dispense information and present a thorough explanation of Cyber Security, Risk Assessment, Management Matrix using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
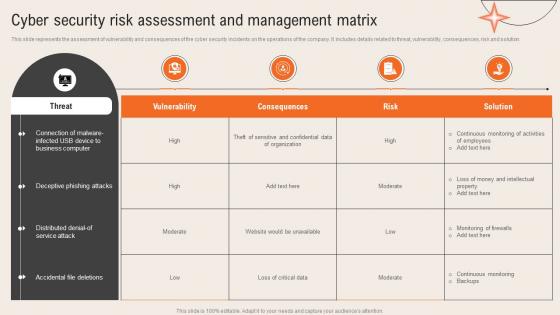 Deploying Computer Security Incident Cyber Security Risk Assessment And Management Matrix
Deploying Computer Security Incident Cyber Security Risk Assessment And Management MatrixThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution.Present the topic in a bit more detail with this Deploying Computer Security Incident Cyber Security Risk Assessment And Management Matrix. Use it as a tool for discussion and navigation on Deceptive Phishing, Business Computer, Accidental File Deletions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
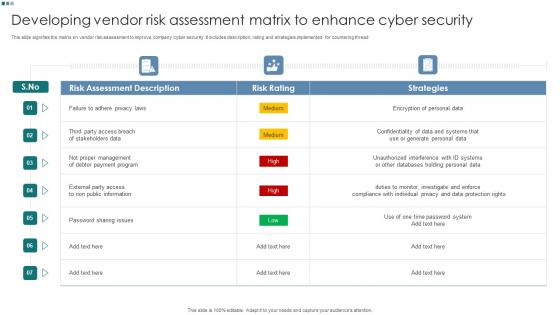 Developing Vendor Risk Assessment Matrix To Enhance Cyber Security
Developing Vendor Risk Assessment Matrix To Enhance Cyber SecurityThis slide signifies the matrix on vendor risk assessment to improve company cyber security. It includes description, rating and strategies implemented for countering thread. Introducing our Developing Vendor Risk Assessment Matrix To Enhance Cyber Security set of slides. The topics discussed in these slides are Strategies, Risk Assessment, Risk Rating. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security Risk Assessment Matrix
Cyber Security Risk Assessment MatrixThis slide shows risk assessment table of cyber security that tells about the severity of different threats. It includes threats like phishing, ransomware and web app attacks etc Introducing our premium set of slides with Cyber Security Risk Assessment Matrix Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Risk, Vulnerability, Impact So download instantly and tailor it with your information.
-
 Cybersecurity Risk Assessment Cyber Security Risk Assessment Program Implementation Impact
Cybersecurity Risk Assessment Cyber Security Risk Assessment Program Implementation ImpactThe purpose of the following slide is to highlight the impact of impact of risk assessment on cyber crime attacks. It compares the number of security incident occurred in two consecutive months and highlight the prevailing trend in terms of going up, remaining same or going down. Present the topic in a bit more detail with this Cybersecurity Risk Assessment Cyber Security Risk Assessment Program Implementation Impact. Use it as a tool for discussion and navigation on Cyber Security, Risk Assessment, Program Implementation, Impact On Attacks Frequency. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Risk Assessment Program Key Approaches To Minimize Cyber Attacks Risks
Cybersecurity Risk Assessment Program Key Approaches To Minimize Cyber Attacks RisksThis slide indicates the key approaches to minimize the risk associated with cyber attacks. The approaches discussed are update and upgrade outdated software, control accounts access, introduce signed software execution policies, regularly track network intrusions and use multifactor authentication. Increase audience engagement and knowledge by dispensing information using Cybersecurity Risk Assessment Program Key Approaches To Minimize Cyber Attacks Risks. This template helps you present information on five stages. You can also present information on Control Accounts Access, Multifactor Authentication, Track Network Intrusions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cybersecurity Risk Assessment Program Major Cyber Attacks Faced By Organization
Cybersecurity Risk Assessment Program Major Cyber Attacks Faced By OrganizationThis purpose of this slide is to showcase the major cyber attacks faced by business organization. The key attacks listed are phishing, malware attack, denial of service attacks, SQL injections, and ransomware. It also provides details regarding the major IT assets impacted and primary objective of each of the attacks. Present the topic in a bit more detail with this Cybersecurity Risk Assessment Program Major Cyber Attacks Faced By Organization. Use it as a tool for discussion and navigation on Phishing, Malware Attack, Denial Of Service Attack, Ransomware. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Risk Assessment Program Mapping Of Multiple Cyber Attacks Using Risk Heat Map
Cybersecurity Risk Assessment Program Mapping Of Multiple Cyber Attacks Using Risk Heat MapThis slide shows the mapping of cyber attacks based on the likelihood of risk occurrence and its impact. It also contains details of attacks segmentation and the control actions that must be taken such as track, monitor and mitigate against such cyber attacks. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Assessment Program Mapping Of Multiple Cyber Attacks Using Risk Heat Map. Dispense information and present a thorough explanation of Cyber Attacks, Risk Heat Map, Cyber Attacks Segmentation, Mitigate using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity Risk Assessment Program Risk Register To Measure Cyber Attacks Vulnerabilities
Cybersecurity Risk Assessment Program Risk Register To Measure Cyber Attacks VulnerabilitiesThis slide indicates the risk register to measure the cyber attack risk vulnerabilities faced by an organization. It includes information regarding the multiple risks in terms of vulnerability exploited, impact level, likelihood of occurrence and control recommended. Present the topic in a bit more detail with this Cybersecurity Risk Assessment Program Risk Register To Measure Cyber Attacks Vulnerabilities. Use it as a tool for discussion and navigation on Cyber Attacks, Vulnerabilities, Cloud Network Compromised, Outdated Antivirus. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Risk Assessment Program Strategic Plan To Mitigate Cyber Attacks
Cybersecurity Risk Assessment Program Strategic Plan To Mitigate Cyber AttacksThe slide indicates the risk mitigation plan for the multiple cyber attacks. It also includes details of cost involved and implementation time required for each mitigation approach. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Assessment Program Strategic Plan To Mitigate Cyber Attacks. Dispense information and present a thorough explanation of Strategic Plan, Mitigate Cyber Attacks, Malware Attack, Recommended Mitigation Strategy using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Risk Assessment And Management Matrix Ppt File Visual Aids
Cyber Security Risk Assessment And Management Matrix Ppt File Visual AidsThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution.Present the topic in a bit more detail with this Cyber Security Risk Assessment And Management Matrix Ppt File Visual Aids. Use it as a tool for discussion and navigation on Deceptive Phishing Attacks, Monitoring Firewalls, Continuous Monitoring. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Product Risk Assessment And Management Icon
Cyber Product Risk Assessment And Management IconPresenting our set of slides with Cyber Product Risk Assessment And Management Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Product, Risk Assessment, Management Icon.
-
 Cyber risk management ethical supply chain leadership effectiveness assessment cpb
Cyber risk management ethical supply chain leadership effectiveness assessment cpbPresenting this set of slides with name - Cyber Risk Management Ethical Supply Chain Leadership Effectiveness Assessment Cpb. This is an editable one stages graphic that deals with topics like Cyber Risk Management, Ethical Supply Chain, Leadership Effectiveness Assessment to help convey your message better graphically. This product is a premium product available for immediate download,and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Five years cyber security roadmap to assess and manage operational risk
Five years cyber security roadmap to assess and manage operational riskPresenting Five Years Cyber Security Roadmap To Assess And Manage Operational Risk PowerPoint slide which is 100 percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.
-
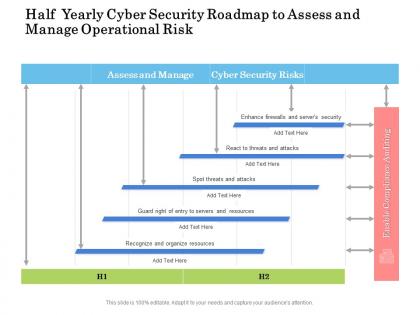 Half yearly cyber security roadmap to assess and manage operational risk
Half yearly cyber security roadmap to assess and manage operational riskPresenting Half Yearly Cyber Security Roadmap To Assess And Manage Operational Risk PowerPoint slide which is 100 percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.
-
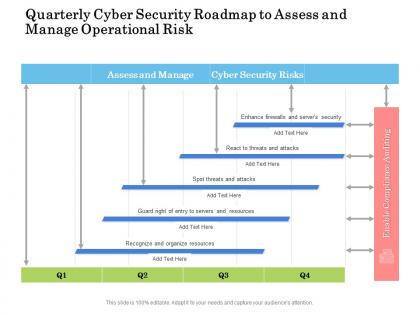 Quarterly cyber security roadmap to assess and manage operational risk
Quarterly cyber security roadmap to assess and manage operational riskPresenting Quarterly Cyber Security Roadmap To Assess And Manage Operational Risk PowerPoint slide which is 100 percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.
-
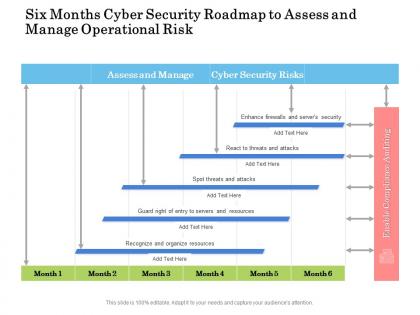 Six months cyber security roadmap to assess and manage operational risk
Six months cyber security roadmap to assess and manage operational riskPresenting Six Months Cyber Security Roadmap To Assess And Manage Operational Risk PowerPoint slide which is 100 percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.
-
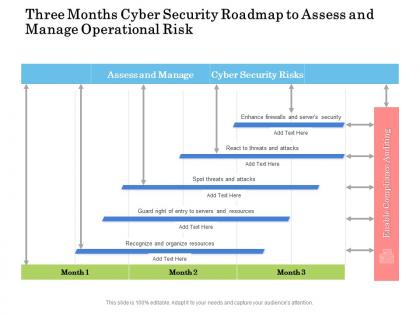 Three months cyber security roadmap to assess and manage operational risk
Three months cyber security roadmap to assess and manage operational riskPresenting Three Months Cyber Security Roadmap To Assess And Manage Operational Risk PowerPoint slide which is 100 percent editable. You can change the color, font size, font type, and shapes of this PPT layout according to your needs. This PPT template is compatible with Google Slides and is available in both 4,3 and 16,9 aspect ratios. This ready to use PowerPoint presentation can be downloaded in various formats like PDF, JPG, and PNG.





