Powerpoint Templates and Google slides for Cyber
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Technological Use Cases Of Fintech Cyber Security
Technological Use Cases Of Fintech Cyber SecurityThis slide graphically represent the best technologies of fintech cyber security industry. Its aim is to manage the best available method for securing the industry. This slide includes cloud, data analytics, cyber security, mobile banking, AI, payments, etc. Introducing our Technological Use Cases Of Fintech Cyber Security set of slides. The topics discussed in these slides are . This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Areas Contributing To Data Breach In Banking Cyber Security
Areas Contributing To Data Breach In Banking Cyber SecurityThis slide represents areas where banks are most vulnerable to cyber security breach. It aims toincrease need for cyber security as part of design architecture aiming to detect emerging attacks in real-time. It includes various constituents such as web apps, card skimmers, etc. Presenting our well structured Areas Contributing To Data Breach In Banking Cyber Security. The topics discussed in this slide are Vectors Of Attack, Key Insights, Avoid Public. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Dashboard To Enhance Cyber Security In Banking Sector
Dashboard To Enhance Cyber Security In Banking SectorThis slide represents dashboard to improve cyber security in financial industry. This slide aims to proactively address security threats and vulnerabilities in banking sector. It includes various elements such as banking health risk, secured payments by year, etc. Introducing our Dashboard To Enhance Cyber Security In Banking Sector set of slides. The topics discussed in these slides are Attacks, Cyber Security Risks, Recent Campaigns. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Analyzing High Risk Employees And Departments IT Security Awareness Training Cybersecurity SS
Analyzing High Risk Employees And Departments IT Security Awareness Training Cybersecurity SSThis slide represents report for analyzing high risk participants and departments that requires continuous IT security awareness training. It includes details related to high risk participants etc. Present the topic in a bit more detail with this Analyzing High Risk Employees And Departments IT Security Awareness Training Cybersecurity SS. Use it as a tool for discussion and navigation on Analyzing High Risk, Employees And Departments, Marketing Team, Operations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Security Awareness Training Program Outline IT Security Awareness Training Cybersecurity SS
Cloud Security Awareness Training Program Outline IT Security Awareness Training Cybersecurity SSThis slide represents overview of training program highlighting set of measures which protects data stored online from theft, leakage and detection. It includes details related to program overview, skills etc. Introducing Cloud Security Awareness Training Program Outline IT Security Awareness Training Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Security Awareness, Training Program Outline, Cloud Architecture And Design, Cloud Infrastructure Security, using this template. Grab it now to reap its full benefits.
-
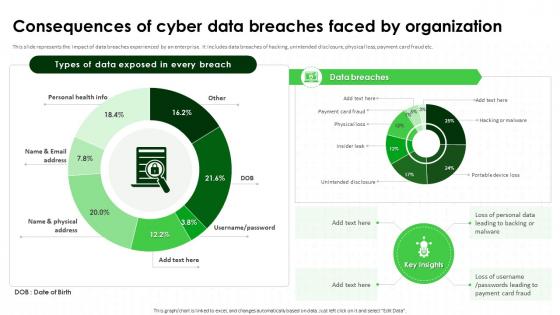 Consequences Of Cyber Data Breaches Faced IT Security Awareness Training Cybersecurity SS
Consequences Of Cyber Data Breaches Faced IT Security Awareness Training Cybersecurity SSThis slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Present the topic in a bit more detail with this Consequences Of Cyber Data Breaches Faced IT Security Awareness Training Cybersecurity SS. Use it as a tool for discussion and navigation on Consequences Of Cyber Data Breaches, Unintended Disclosure, Physical Loss, Payment Card Fraud. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Gap Analysis Representing Current Situation Of Cyber IT Security Awareness Training Cybersecurity SS
Gap Analysis Representing Current Situation Of Cyber IT Security Awareness Training Cybersecurity SSThis slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. Deliver an outstanding presentation on the topic using this Gap Analysis Representing Current Situation Of Cyber IT Security Awareness Training Cybersecurity SS. Dispense information and present a thorough explanation of Gap Analysis Representing, Current Situation Of Cyber Attacks, Employee Productivity Rates using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Impact Of IT Security Awareness Program On Organizational Kpis Cybersecurity SS
Impact Of IT Security Awareness Program On Organizational Kpis Cybersecurity SSThis slide represents impact of strategy deployed by IT and security professionals for preventing and mitigating cyber security risks on organizational KPIs such as annual revenue etc. Present the topic in a bit more detail with this Impact Of IT Security Awareness Program On Organizational Kpis Cybersecurity SS. Use it as a tool for discussion and navigation on Increase In Potential Annual Revenue, Increase In Employee Productivity Rates, Increase In Customer Satisfaction Rates. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
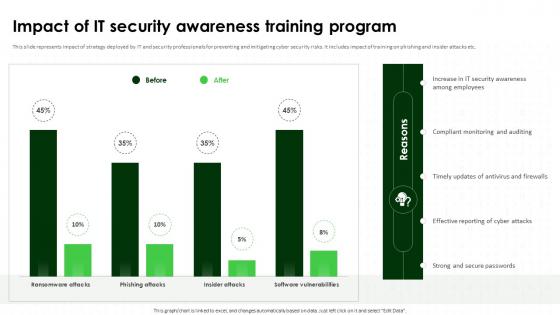 Impact Of IT Security Awareness Training Program Cybersecurity SS
Impact Of IT Security Awareness Training Program Cybersecurity SSThis slide represents impact of strategy deployed by IT and security professionals for preventing and mitigating cyber security risks. It includes impact of training on phishing and insider attacks etc. Deliver an outstanding presentation on the topic using this Impact Of IT Security Awareness Training Program Cybersecurity SS. Dispense information and present a thorough explanation of Compliant Monitoring And Auditing, Security Awareness Training Program, Strong And Secure Passwords using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
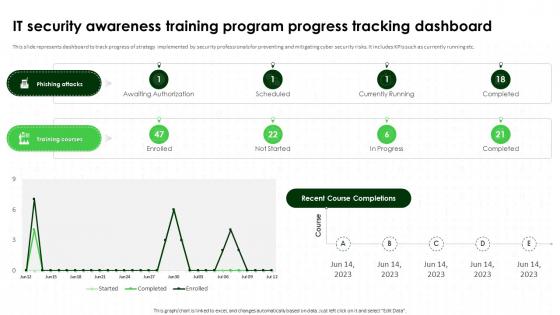 IT Security Awareness Training Program Progress Tracking Dashboard Cybersecurity SS
IT Security Awareness Training Program Progress Tracking Dashboard Cybersecurity SSThis slide represents dashboard to track progress of strategy implemented by security professionals for preventing and mitigating cyber security risks. It includes KPIs such as currently running etc. Deliver an outstanding presentation on the topic using this IT Security Awareness Training Program Progress Tracking Dashboard Cybersecurity SS. Dispense information and present a thorough explanation of Dashboard To Track Progress, Strategy Implemented, Security Professionals using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IT Security Awareness Training Statistical Data Highlighting It Security Unawareness Cybersecurity SS
IT Security Awareness Training Statistical Data Highlighting It Security Unawareness Cybersecurity SSThis slide represents statistical insights highlighting importance of implementing strategy adopted by IT teams and security professionals for preventing and mitigating security risks. Present the topic in a bit more detail with this IT Security Awareness Training Statistical Data Highlighting It Security Unawareness Cybersecurity SS. Use it as a tool for discussion and navigation on Implementing Strategy, Security Professionals, Mitigating Security Risks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
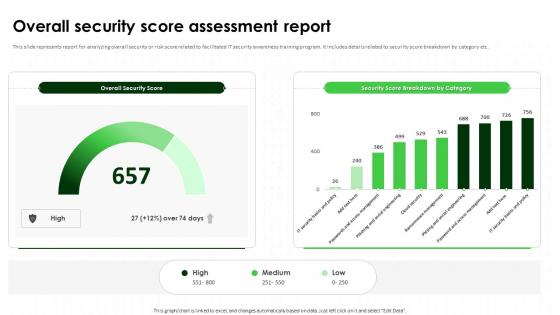 Overall Security Score Assessment Report IT Security Awareness Training Cybersecurity SS
Overall Security Score Assessment Report IT Security Awareness Training Cybersecurity SSThis slide represents report for analyzing overall security or risk score related to facilitated IT security awareness training program. It includes details related to security score breakdown by category etc. Deliver an outstanding presentation on the topic using this Overall Security Score Assessment Report IT Security Awareness Training Cybersecurity SS. Dispense information and present a thorough explanation of Overall Security Score, Assessment Report, Security Or Risk Score, Awareness Training Program using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Training Awareness And Defense IT Security Awareness Training Cybersecurity SS
Social Engineering Training Awareness And Defense IT Security Awareness Training Cybersecurity SSThis slide represents overview of training course for mitigating cybercrime which involves tracking a target into giving money or data. It includes details related to training program overview, target audience etc. Introducing Social Engineering Training Awareness And Defense IT Security Awareness Training Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Social Engineering Training, Awareness And Defense Course Outline, Training Program Overview, Target Audience, using this template. Grab it now to reap its full benefits.
-
 Edr Cybersecurity Dashboard To Track Threats Building Next Generation Endpoint Security Cybersecurity SS
Edr Cybersecurity Dashboard To Track Threats Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases endpoint detection and response EDR dashboard which can help analyze malicious operations Malops and provide information about scans, investigations, activities, etc.Deliver an outstanding presentation on the topic using this Edr Cybersecurity Dashboard To Track Threats Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Affected, Affected Users, Recent Activity using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Endpoint Cyber Security Budget Plan Building Next Generation Endpoint Security Cybersecurity SS
Endpoint Cyber Security Budget Plan Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases security budget plan for endpoint operations. It provides details about secure data transmission, frontline defense, external network threats, etc.Present the topic in a bit more detail with this Endpoint Cyber Security Budget Plan Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Endpoint Operations, Secure Data Transmission, Frontline Defense, External Network Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Endpoint Security Issues With Compromised Building Next Generation Endpoint Security Cybersecurity SS
Endpoint Security Issues With Compromised Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases organizational survey highlighting endpoint security issues with compromised devices. It includes details about desktops, laptops, online servers, etc.Present the topic in a bit more detail with this Endpoint Security Issues With Compromised Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Key Insights, Survey Question, Reasons. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Endpoint Security Market Size Analysis Building Next Generation Endpoint Security Cybersecurity SS
Endpoint Security Market Size Analysis Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases endpoint security market size analysis, referable for related businesses and investors. It provides details about bring your own device BYOD, smart sensors, etc.Present the topic in a bit more detail with this Endpoint Security Market Size Analysis Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Market Projection, Factors Driving Growth, Smart Sensors. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Financial Impact Of Endpoint Security Attacks Building Next Generation Endpoint Security Cybersecurity SS
Financial Impact Of Endpoint Security Attacks Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases financial impact of endpoint attacks, which can help organizations assess their costs and plan recovery strategies of system downtime, information assets, etc.Deliver an outstanding presentation on the topic using this Financial Impact Of Endpoint Security Attacks Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Zero Day, Polymorphic Malware, Malicious Code using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Just In Time For Access Management Building Next Generation Endpoint Security Cybersecurity SS
Just In Time For Access Management Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases managing endpoint security access management through just in time method. It provides details about access request, permission duration, etc.Present the topic in a bit more detail with this Just In Time For Access Management Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Access Request, Our Process, Potential Impact. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Organization Cybersecurity Risk Scoring Dashboard
Organization Cybersecurity Risk Scoring DashboardThe below slide provides a cybersecurity risk management and scoring dashboard to analyze the threat severity. It measures various key performance indicators such as data sensitivity rating, compliance tracker, risk management cost, etc. Introducing our Organization Cybersecurity Risk Scoring Dashboard set of slides. The topics discussed in these slides are Financial Implications, Breach Notification Cost, Residual Risk Cost. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Crisis Management Budget Allocation
Cyber Crisis Management Budget AllocationThe purpose of this slide is to elucidate how cyber crisis management budget allocation strategically distributes resources, optimizing preparedness, response, and recovery capabilities, ultimately enhancing an organizations resilience against cyber threats. Presenting our well structured Cyber Crisis Management Budget Allocation. The topics discussed in this slide are Security Assessment, Incident Response, Security Awareness. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cybersecurity And Crisis Management Technology Adoption Trends
Cybersecurity And Crisis Management Technology Adoption TrendsThe purpose of this slide is to highlight how cybersecurity and crisis management technology adoption trends enable organizations to stay ahead by identifying and adopting emerging technologies, enhancing resilience against cyber threats and crises. Introducing our Cybersecurity And Crisis Management Technology Adoption Trends set of slides. The topics discussed in these slides are Cybersecurity, Crisis Management Technology, Adoption Trends. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
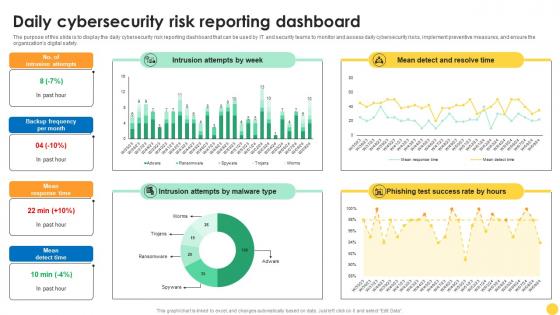 Daily Cybersecurity Risk Reporting Dashboard
Daily Cybersecurity Risk Reporting DashboardThe purpose of this slide is to display the daily cybersecurity risk reporting dashboard that can be used by IT and security teams to monitor and assess daily cybersecurity risks, implement preventive measures, and ensure the organizations digital safety. Introducing our Daily Cybersecurity Risk Reporting Dashboard set of slides. The topics discussed in these slides are Intrusion Attempts By Week, Intrusion Attempts, Test Success Rate. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Penetration Testing Approaches Budged Allocation For Cybersecurity By Us
Penetration Testing Approaches Budged Allocation For Cybersecurity By UsThis slide highlights the budget of the United States of America for cybersecurity from the financial year 2023-2023. The purpose is to showcase the significant rise in the funding for cybersecurity which contains penetration testing also in part of it. Present the topic in a bit more detail with this Penetration Testing Approaches Budged Allocation For Cybersecurity By Us. Use it as a tool for discussion and navigation on Cybersecurity, Financial, Safeguard Sensitive Citizen Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Standard Cyber Threat Hunting Activities
Standard Cyber Threat Hunting ActivitiesThis slide highlights common cyber threat-hunting activities, such as clustering, grouping, stack counting, and so on. Deliver an outstanding presentation on the topic using this Standard Cyber Threat Hunting Activities. Dispense information and present a thorough explanation of Clustering, Grouping, Stack Counting, Standard Cyber Threat using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Global Overview Of Mdr Cybersecurity Market Size
Global Overview Of Mdr Cybersecurity Market SizeThis slide graphically represents global overview of MDR markets that assist companies to enhance their cybersecurity and business continuity plan. It includes various growth drivers such as increasing cybersecurity threats, highly complex IT environments, etc. Presenting our well structured Global Overview Of Mdr Cybersecurity Market Size. The topics discussed in this slide are Overview, Cybersecurity, Environments. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Mdr Dashboard To Analyze And Enhance Data Cybersecurity
Mdr Dashboard To Analyze And Enhance Data CybersecurityThis slide represents dashboard that helps companies to monitor and analyze various threats and enhance their cybersecurity, it includes various elements such as active investigations, pending response, hunt outcomes, most mitigated threats, etc. Introducing our Mdr Dashboard To Analyze And Enhance Data Cybersecurity set of slides. The topics discussed in these slides are Dashboard, Analyze, Data Cybersecurity. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Budget Share For Implementing Mobile Security Solutions Mobile Device Security Cybersecurity SS
Budget Share For Implementing Mobile Security Solutions Mobile Device Security Cybersecurity SSBudget Share For Implementing Mobile Security Solutions Mobile Device Security Cybersecurity SS This slide showcases expenses share to implement mobile device threat management solutions. Its key elements are biometric solutions, VPN, software upgradation, mobile device management Present the topic in a bit more detail with this Biometric Solutions, Security Awareness Use it as a tool for discussion and navigation on Biometric Solutions, Security Awareness This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attacks On Employee Mobile Devices Mobile Device Security Cybersecurity SS
Cyber Attacks On Employee Mobile Devices Mobile Device Security Cybersecurity SSThis slide showcases cyber threats faced by workforce on mobile devices. It highlights data regarding malware, phishing attacks, ransomware etc. Present the topic in a bit more detail with this Cyber Attacks On Employee Mobile Devices Mobile Device Security Cybersecurity SS Use it as a tool for discussion and navigation on Awareness Training, Weak Security Measures This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attacks Reduction After Implementing Mobile Security Techniques Mobile Device Security Cybersecurity SS
Cyber Attacks Reduction After Implementing Mobile Security Techniques Mobile Device Security Cybersecurity SSThis slide showcases decrease in cyber attacks after implementation of mobile security. Its key elements are malware, phishing attacks and ransomware Deliver an outstanding presentation on the topic using this Cyber Attacks Reduction After Implementing Mobile Security Techniques Mobile Device Security Cybersecurity SS Dispense information and present a thorough explanation of Advanced Persistent Threats, Diverse Cyber Threat Landscape using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Dashboard To Track Cyber Threats In Organization Mobile Device Security Cybersecurity SS
Dashboard To Track Cyber Threats In Organization Mobile Device Security Cybersecurity SSThis slides showcases dashboard that can help to track number of cyber threats in organization. Its key elements are hacker attacks, spyware, viruses and zero day attacks Present the topic in a bit more detail with this Dashboard To Track Cyber Threats In Organization Mobile Device Security Cybersecurity SS Use it as a tool for discussion and navigation on Track Cyber Threats, Attacks Types This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Decrease In Cyber Attacks On Different Mobile Devices Mobile Device Security Cybersecurity SS
Decrease In Cyber Attacks On Different Mobile Devices Mobile Device Security Cybersecurity SSThis slide showcases decline in cyber attacks after implementation of mobile security techniques. It highlights decrease in cyber attacks on android and iOS devices Deliver an outstanding presentation on the topic using this Decrease In Cyber Attacks On Different Mobile Devices Mobile Device Security Cybersecurity SS Dispense information and present a thorough explanation of Security Attacks, Mobile Devices using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Distribution Of Spyware Threats By Geographical Region Mobile Device Security Cybersecurity SS
Distribution Of Spyware Threats By Geographical Region Mobile Device Security Cybersecurity SSThis slide showcases impact of mobile threats on organization. It highlights impact in terms of company financial loss, operational distribution, cybersecurity expenses, data breach etc. Present the topic in a bit more detail with this Distribution Of Spyware Threats By Geographical Region Mobile Device Security Cybersecurity SS Use it as a tool for discussion and navigation on Support And Maintenance, Device Troubleshooting, Access Control This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Faced By Organization Due To Mobile Threats Mobile Device Security Cybersecurity SS
Impact Faced By Organization Due To Mobile Threats Mobile Device Security Cybersecurity SSThis slide showcases impact of mobile threats on organization. It highlights impact in terms of company financial loss, operational distribution, cybersecurity expenses, data breach etc. Present the topic in a bit more detail with this Impact Faced By Organization Due To Mobile Threats Mobile Device Security Cybersecurity SS Use it as a tool for discussion and navigation on Before Mobile Security, Management Plan This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Mobile Cyber Attacks Occurrence Globally Mobile Device Security Cybersecurity SS
Mobile Cyber Attacks Occurrence Globally Mobile Device Security Cybersecurity SSThis slide showcases number of cyber attacks faced by mobile users around the world. It highlights data regarding attacks faced in last three years Deliver an outstanding presentation on the topic using this Mobile Cyber Attacks Occurrence Globally Mobile Device Security Cybersecurity SS Dispense information and present a thorough explanation of Fingerprint Scanner, Facial Recognition, Voice Recognition using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Mobile Malware Attacks By Country Share Mobile Device Security Cybersecurity SS
Mobile Malware Attacks By Country Share Mobile Device Security Cybersecurity SSThis slide showcases percentage share of mobile malware attacks faced in different countries. It highlights share of China, Iran, Yemen, Switzerland, Kenya etc. Present the topic in a bit more detail with this Mobile Malware Attacks By Country Share Mobile Device Security Cybersecurity SS Use it as a tool for discussion and navigation on Purpose, Scope, Loss And Theft This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Mobile Security Initiatives Tracking Dashboard Mobile Device Security Cybersecurity SS
Mobile Security Initiatives Tracking Dashboard Mobile Device Security Cybersecurity SSThis slide showcases dashboard that can help organization to track mobile device security initiatives. Its key elements are incident management, compliance, patches and vulnerabilities management Deliver an outstanding presentation on the topic using this Mobile Security Initiatives Tracking Dashboard Mobile Device Security Cybersecurity SS Dispense information and present a thorough explanation of Mobile Malware, Country Share using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Number Of Phishing Sites Exploiting Mobile Devices Mobile Device Security Cybersecurity SS
Number Of Phishing Sites Exploiting Mobile Devices Mobile Device Security Cybersecurity SSThis slide showcases percentage of phishing websites that are exploiting the mobile users. It highlights monthly phishing attack data of last year Present the topic in a bit more detail with this Number Of Phishing Sites Exploiting Mobile Devices Mobile Device Security Cybersecurity SS Use it as a tool for discussion and navigation on Decrease In Company Loses, Decrease In Operational Disruption This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Volume Of Mobile Malware Detected Globally Mobile Device Security Cybersecurity SS
Volume Of Mobile Malware Detected Globally Mobile Device Security Cybersecurity SSThis slide showcases mobile malware threats globally faced by the users. It also sites key reasons for mobile malware that are lack of security awareness, inadequate security practices etc. Present the topic in a bit more detail with this Volume Of Mobile Malware Detected Globally Mobile Device Security Cybersecurity SS Use it as a tool for discussion and navigation on Security Awareness, Exploitation Of Vulnerabilities, Inadequate Security Practices This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Introduction To Types Of Attacks In Cyberterrorism Strategic Guide To Implement Strategy SS
Introduction To Types Of Attacks In Cyberterrorism Strategic Guide To Implement Strategy SSThis slide showcases the different types of attacks in cyber terrorism. It includes attacks such as DoS and DDoS attack, Man-in-the-Middle MITM attack, Phishing attack, Whale phishing attack, Spear phishing attack and Ransomware attack.Increase audience engagement and knowledge by dispensing information using Introduction To Types Of Attacks In Cyberterrorism Strategic Guide To Implement Strategy SS. This template helps you present information on six stages. You can also present information on Whale Phishing Attack, Spear Phishing Attack, Ransomware Attack, Phishing Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Implementing Intrusion Prevention Gap Analysis For Intrusion Prevention System Cybersecurity SS
Implementing Intrusion Prevention Gap Analysis For Intrusion Prevention System Cybersecurity SSThis slide represents the gap analysis to help organizations understand the gaps so that they can build effective strategies to eliminate these gaps and achieve desired results. Present the topic in a bit more detail with this Implementing Intrusion Prevention Gap Analysis For Intrusion Prevention System Cybersecurity SS. Use it as a tool for discussion and navigation on Proactive Security Measures, Average Incident Response, Network Traffic Monitored. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
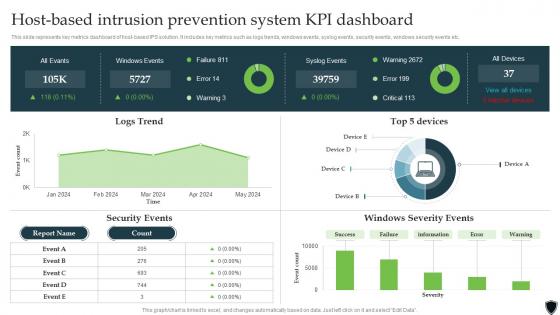 Implementing Intrusion Prevention Host Based Intrusion Prevention System KPI Cybersecurity SS
Implementing Intrusion Prevention Host Based Intrusion Prevention System KPI Cybersecurity SSThis slide represents key metrics dashboard of host-based IPS solution. It includes key metrics such as logs trends, windows events, syslog events, security events, windows security events etc. Present the topic in a bit more detail with this Implementing Intrusion Prevention Host Based Intrusion Prevention System Kpi Cybersecurity SS. Use it as a tool for discussion and navigation on Success, Failure, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
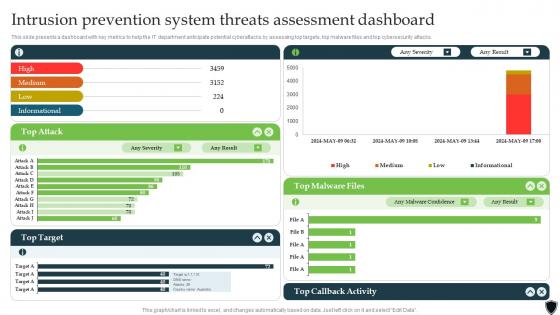 Implementing Intrusion Prevention Intrusion Prevention System Threats Assessment Cybersecurity SS
Implementing Intrusion Prevention Intrusion Prevention System Threats Assessment Cybersecurity SSThis slide presents a dashboard with key metrics to help the IT department anticipate potential cyberattacks by assessing top targets, top malware files and top cybersecurity attacks. Present the topic in a bit more detail with this Implementing Intrusion Prevention Intrusion Prevention System Threats Assessment Cybersecurity SS. Use it as a tool for discussion and navigation on Callback Activity, Malware Files, Target. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Intrusion Prevention Overview Steps For Implementing Intrusion Cybersecurity SS
Implementing Intrusion Prevention Overview Steps For Implementing Intrusion Cybersecurity SSThis slide represents the process for effectively deploying a network security tool that monitors the network for malicious activities. It includes steps such as defining network segmentation etc. Introducing Implementing Intrusion Prevention Overview Steps For Implementing Intrusion Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Define Network Segmentation, Select Right Hardware And Software, Installation And Configuration, using this template. Grab it now to reap its full benefits.
-
 Implementing Intrusion Prevention Potential Impact Of Intrusion Prevention Cybersecurity SS
Implementing Intrusion Prevention Potential Impact Of Intrusion Prevention Cybersecurity SSThis slide highlights the impact of deploying effective Intrusion prevention system solution on organizational operations, such as increased real-time threat visibility, proactive threat detection etc. Present the topic in a bit more detail with this Implementing Intrusion Prevention Potential Impact Of Intrusion Prevention Cybersecurity SS. Use it as a tool for discussion and navigation on Increase In Real-Time Threat Visibility, Increase In Proactive Threat Detection Rates, Decrease In Average Cost Per Breach. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Intrusion Prevention Potential Roi After Implementing Intrusion Cybersecurity SS
Implementing Intrusion Prevention Potential Roi After Implementing Intrusion Cybersecurity SSThis slide demonstrates the positive impact of implementing Intrusion prevention system solution on returns on investments. The graph depicts an increase in ROI and savings over time. Present the topic in a bit more detail with this Implementing Intrusion Prevention Potential Roi After Implementing Intrusion Cybersecurity SS. Use it as a tool for discussion and navigation on Potential ROI After Implementing, Intrusion Prevention System. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Network Vulnerabilities Assessment KPI Dashboard Implementing Strategies For Mitigating Cybersecurity SS
Network Vulnerabilities Assessment KPI Dashboard Implementing Strategies For Mitigating Cybersecurity SSThis dashboard tracks and assesses the network vulnerabilities faced by the organization. It includes KPIs such as critical vulnerabilities, new vulnerabilities, and unresolved vulnerabilities etc.Present the topic in a bit more detail with this Network Vulnerabilities Assessment KPI Dashboard Implementing Strategies For Mitigating Cybersecurity SS. Use it as a tool for discussion and navigation on New Vulnerabilities, Unresolved Vulnerabilities, Activity, Insecure Libraries. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Password Authentication For Protection Against Brute Force Attacks Cybersecurity SS
Password Authentication For Protection Against Brute Force Attacks Cybersecurity SSThis slide outlines strategies for protecting networks from brute-force attacks, including password authentication methods such as limiting the number of login attempts and password requests etc.Deliver an outstanding presentation on the topic using this Password Authentication For Protection Against Brute Force Attacks Cybersecurity SS. Dispense information and present a thorough explanation of Password Authentication, Solutions, Login Attempts using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Potential Impact Of Mitigating Network Vulnerabilities On Cyber Attacks Cybersecurity SS
Potential Impact Of Mitigating Network Vulnerabilities On Cyber Attacks Cybersecurity SSThis slide shows the impact of strategies implemented by IT and security professionals to prevent and mitigate network vulnerabilities, including phishing attacks, malware attacks, insider attacks and software vulnerabilities.Deliver an outstanding presentation on the topic using this Potential Impact Of Mitigating Network Vulnerabilities On Cyber Attacks Cybersecurity SS. Dispense information and present a thorough explanation of Cyber Attacks, Secure Passwords, Compliant Monitoring And Auditing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Potential Roi After Implementing Tools And Technologies To Reduce Network Vulnerabilities Cybersecurity SS
Potential Roi After Implementing Tools And Technologies To Reduce Network Vulnerabilities Cybersecurity SSThis slide demonstrates the positive impact of implementing network vulnerability management solutions on returns on investments. The graph depicts an increase in ROI and savings over time..Deliver an outstanding presentation on the topic using this Potential Roi After Implementing Tools And Technologies To Reduce Network Vulnerabilities Cybersecurity SS. Dispense information and present a thorough explanation of Key Insights, Improved Compliance, Password Hacking using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Common Ecommerce Platforms Cybersecurity Threats B2b Ecommerce Service Challenges
Common Ecommerce Platforms Cybersecurity Threats B2b Ecommerce Service ChallengesThis slide showcases current vulnerabilities in b2b ecommerce platforms, referable for businesses in recognizing major issues. It provides details about the lack of proper security testing, inadequate encryption protocols, etc.Present the topic in a bit more detail with this Common Ecommerce Platforms Cybersecurity Threats B2b Ecommerce Service Challenges. Use it as a tool for discussion and navigation on Inadequate Encryption Protocols, Proper Security Testing, Software And Systems. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tools To Address Supply Chain Cybersecurity Attacks For Data Protection
Tools To Address Supply Chain Cybersecurity Attacks For Data ProtectionThis slide graphically represents use of various tools and approaches that assist companies in addressing various supply chain cybersecurity attacks and optimizing data protection. It includes tools such as IT vendor risk management tools, supply chain risk management tools, etc. Presenting our well structured Tools To Address Supply Chain Cybersecurity Attacks For Data Protection. The topics discussed in this slide are Audits Of Suppliers, Manufacturers, Logistics Partners. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Threat Analysis With Data Encryption
Cyber Threat Analysis With Data EncryptionThe purpose of this slide is to highlight how cyber threat analysis with data encryption fortifies security. It offers proactive insights into potential threats, ensuring a robust defense, and safeguarding sensitive information in the evolving landscape of cyber threats. Introducing our Cyber Threat Analysis With Data Encryption set of slides. The topics discussed in these slides are Cybersecurity Threat, Budget Constraints, Inadequate Training And Awareness. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Automation Ideas Mechanization Cyber Security Infrastructure Implement Technology Material
Automation Ideas Mechanization Cyber Security Infrastructure Implement Technology MaterialEnhance your audiences knowledge with this well researched complete deck. Showcase all the important features of the deck with perfect visuals. This deck comprises of total of ten slides with each slide explained in detail. Each template comprises of professional diagrams and layouts. Our professional PowerPoint experts have also included icons, graphs and charts for your convenience. All you have to do is DOWNLOAD the deck. Make changes as per the requirement. Yes, these PPT slides are completely customizable. Edit the colour, text and font size. Add or delete the content from the slide. And leave your audience awestruck with the professionally designed Automation Ideas Mechanization Cyber Security Infrastructure Implement Technology Material complete deck.
-
 Example active cyber attack ppt powerpoint presentation file samples cpb
Example active cyber attack ppt powerpoint presentation file samples cpbPresenting our Example Active Cyber Attack Ppt Powerpoint Presentation File Samples Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Example Active Cyber Attack This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Reverse engineering cyber security ppt powerpoint presentation infographic portfolio cpb
Reverse engineering cyber security ppt powerpoint presentation infographic portfolio cpbPresenting Reverse Engineering Cyber Security Ppt Powerpoint Presentation Infographic Portfolio Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Reverse Engineering Cyber Security. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Alert cyber security law ppt powerpoint presentation slides download cpb
Alert cyber security law ppt powerpoint presentation slides download cpbPresenting Alert Cyber Security Law Ppt Powerpoint Presentation Slides Download Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Alert Cyber Security Law. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cyber security information security ppt powerpoint presentation layouts demonstration cpb
Cyber security information security ppt powerpoint presentation layouts demonstration cpbPresenting Cyber Security Information Security Ppt Powerpoint Presentation Layouts Demonstration Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase six stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cyber Security Information Security. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Data security it assessment matrix of cyber risks ppt slides outline
Data security it assessment matrix of cyber risks ppt slides outlineThis slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Present the topic in a bit more detail with this Data Security IT Assessment Matrix Of Cyber Risks Ppt Slides Outline. Use it as a tool for discussion and navigation on Systems Involved, Owner Tenant, Mobile, Web Applications, Health Care. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
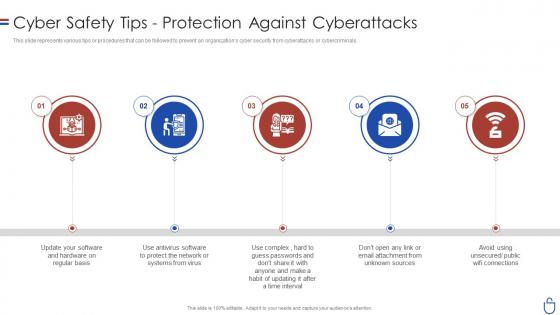 Data security it cyber safety tips protection against cyberattacks
Data security it cyber safety tips protection against cyberattacksThis slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. Increase audience engagement and knowledge by dispensing information using Data Security IT Cyber Safety Tips Protection Against Cyberattacks. This template helps you present information on five stages. You can also present information on Sources, Public Wifi Connections, Time Interval, Protect Network using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.





