Powerpoint Templates and Google slides for Cyber Network
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Security Icon Network Protection Threat Server Database Software
Cyber Security Icon Network Protection Threat Server Database SoftwareKeep your audience glued to their seats with professionally designed PPT slides. This deck comprises of total of twelve slides. It has PPT templates with creative visuals and well researched content. Not just this, our PowerPoint professionals have crafted this deck with appropriate diagrams, layouts, icons, graphs, charts and more. This content ready presentation deck is fully editable. Just click the DOWNLOAD button below. Change the colour, text and font size. You can also modify the content as per your need. Get access to this well crafted complete deck presentation and leave your audience stunned.
-
 Ethical Hacking And Network Security Loss Caused By Different Types Of Cyber Attacks
Ethical Hacking And Network Security Loss Caused By Different Types Of Cyber AttacksThis slide represents the different types of cyber-attacks throughout the year, including the percentage of total loss caused by these attacks. Present the topic in a bit more detail with this Ethical Hacking And Network Security Loss Caused By Different Types Of Cyber Attacks. Use it as a tool for discussion and navigation on Cyber Attacks Throughout, Online Or Web Based Attacks, Malware Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Hids Cyber Security Dashboard To Identify Network Threats
Hids Cyber Security Dashboard To Identify Network ThreatsThis slide represents HIDS cyber security dashboard to identify network issues and monitor malicious activity in host devices which could lead to serious breaches. It includes key components such as number of alerts, summary of alerts, etc Introducing our Hids Cyber Security Dashboard To Identify Network Threats set of slides. The topics discussed in these slides are Security, Dashboard, Network Threats. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Dashboard For Evaluating Cyber Deception Networking Tool
Dashboard For Evaluating Cyber Deception Networking ToolThe purpose of this slide is to showcase a dashboard for evaluating a cyber deception networking tool, enabling organizations to assess phases of attack, severity of attempts, etc. Introducing our Dashboard For Evaluating Cyber Deception Networking Tool set of slides. The topics discussed in these slides are Initial Access, Execution, Persistence. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Potential Impact Of Mitigating Network Vulnerabilities On Cyber Attacks Cybersecurity SS
Potential Impact Of Mitigating Network Vulnerabilities On Cyber Attacks Cybersecurity SSThis slide shows the impact of strategies implemented by IT and security professionals to prevent and mitigate network vulnerabilities, including phishing attacks, malware attacks, insider attacks and software vulnerabilities.Deliver an outstanding presentation on the topic using this Potential Impact Of Mitigating Network Vulnerabilities On Cyber Attacks Cybersecurity SS. Dispense information and present a thorough explanation of Cyber Attacks, Secure Passwords, Compliant Monitoring And Auditing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IoT Cyber Network Security Framework
IoT Cyber Network Security FrameworkThe below slide provides the six principles for IoT cyber network security that ensures the end to end IoT solution for businesses and organizations. The various principles are device intelligence, edge processing, messaging control, etc.Presenting our well structured IoT Cyber Network Security Framework. The topics discussed in this slide are Secure Communication, Secure Lifecycle Management, Important Security. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Neural Networks And Cyber Security Applications A Beginners Guide To Neural AI SS
Neural Networks And Cyber Security Applications A Beginners Guide To Neural AI SSThis slide showcases how cyber security tasks can be performed by technicians when integrated with artificial neural networks ANN. It provides details about fraud detection, prioritized notifications, content moderation, etc. Increase audience engagement and knowledge by dispensing information using Neural Networks And Cyber Security Applications A Beginners Guide To Neural AI SS. This template helps you present information on six stages. You can also present information on Detection, Notifications, Prevention using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Business Network Security In Powerpoint And Google Slides Cpb
Cyber Security Business Network Security In Powerpoint And Google Slides CpbPresenting Cyber Security Business Network Security In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cyber Security Business Network Security. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Comparative Analysis Of Cyber Security Network Audit Tools
Comparative Analysis Of Cyber Security Network Audit ToolsThis slide covers a comparison of cyber audit tools and provides details about features that help to identify suitable software for organizations. It includes elements such as description, subscriptions, etc. Introducing our Comparative Analysis Of Cyber Security Network Audit Tools set of slides. The topics discussed in these slides are Vulnerability Assessment, Tamper Protection, Cloud Based. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Network Security Audit Technology Icon
Cyber Network Security Audit Technology IconPresenting our set of slides with Cyber Network Security Audit Technology Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Network Security, Audit Technology Icon.
-
 Key Metrics For Cyber Network Security Audit
Key Metrics For Cyber Network Security AuditThis slide covers various KPIs of cyber audit and provides details about metrics to identify problems to resolve issues in organizations. It includes elements such as compliance score, security ROI, etc. Introducing our Key Metrics For Cyber Network Security Audit set of slides. The topics discussed in these slides are Compliance Score, Vulnerability Count, Incident Response Time. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security Stocks Network Security In Powerpoint And Google Slides Cpb
Cyber Security Stocks Network Security In Powerpoint And Google Slides CpbPresenting our Cyber Security Stocks Network Security In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Cyber Security Stocks Network Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cyber Threats In Blockchain Comparative Analysis Of Various Types Of Blockchain Network BCT SS V
Cyber Threats In Blockchain Comparative Analysis Of Various Types Of Blockchain Network BCT SS VThe following slide depicts the comparative assessment of major types of blockchain network to analyze the level of security. It includes elements such as decentralization, accessibility, security, transparency, scalability, etc. Present the topic in a bit more detail with this Cyber Threats In Blockchain Comparative Analysis Of Various Types Of Blockchain Network BCT SS V Use it as a tool for discussion and navigation on Public Blockchain, Private Blockchain, Consortium Blockchain This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Threats In Blockchain How Does Phishing Attack Works On Blockchain Network BCT SS V
Cyber Threats In Blockchain How Does Phishing Attack Works On Blockchain Network BCT SS VThe following slide depicts the workflow model of phishing attack carried out on blockchain network. It includes activities such as attackers sending emails to users, opening up emails, obtaining information from system, stealing data from user, etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain How Does Phishing Attack Works On Blockchain Network BCT SS V This template helps you present information on Seven stages. You can also present information on Steals Data From User System, Obtains Information From System using this PPT design. This layout is completely editable so personaize it now
-
 Cyber Threats In Blockchain Key Scenarios Of Sybil Attack On Blockchain Network BCT SS V
Cyber Threats In Blockchain Key Scenarios Of Sybil Attack On Blockchain Network BCT SS VThe following slide showcases major scenarios of sybil attack to minimize the impact and manage operations. It includes elements such as attack on bitcoin network, tor network, peer-to-peer model, etc. Deliver an outstanding presentation on the topic using this Cyber Threats In Blockchain Key Scenarios Of Sybil Attack On Blockchain Network BCT SS V Dispense information and present a thorough explanation of Bitcoin Network, Attack On Tor Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Threats In Blockchain Reviewing Consensus Mechanism To Manage Decentralized Network BCT SS V
Cyber Threats In Blockchain Reviewing Consensus Mechanism To Manage Decentralized Network BCT SS VThe following slide showcases some tips for consensus mechanism to ensure record of legitimate transactions. It includes elements such as proof of work pow, proof of stake pos, delegated pos, resolving complicated puzzles, verifying transactions, sharing monetary risks, etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain Reviewing Consensus Mechanism To Manage Decentralized Network BCT SS V This template helps you present information on Three stages. You can also present information on Proof Of Work, Proof Of Stake, Delegated POS using this PPT design. This layout is completely editable so personaize it now
-
 Cyber Threats In Blockchain Threats Imposed By Sybil Attack On Blockchain Network BCT SS V
Cyber Threats In Blockchain Threats Imposed By Sybil Attack On Blockchain Network BCT SS VThe following slide highlights major issues faced by users due to sybil frauds to reduce fake account creations. It includes elements such as block users from network, breach of privacy, fosters 51percent attack, etc. Deliver an outstanding presentation on the topic using this Cyber Threats In Blockchain Threats Imposed By Sybil Attack On Blockchain Network BCT SS V Dispense information and present a thorough explanation of Block Users From Network, Breach Of Privacy, Attack Edge using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Advantages Of SAP Cyber Security To Safeguard Company Networks
Advantages Of SAP Cyber Security To Safeguard Company NetworksThis slide highlights the advantages of SAP cybersecurity to safeguard company networks. The purpose of this template is to help the company leverage SAP cybersecurity to prevent malware infections. It includes advantages such as identification of risks and vulnerabilities, protection of application data, etc. Presenting our set of slides with Advantages Of SAP Cyber Security To Safeguard Company Networks. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify Risks And Vulnerabilities, Protect Application Data, Identify Anomalies.
-
 Techniques Employed Under SAP Cyber Security To Safeguard Company Networks
Techniques Employed Under SAP Cyber Security To Safeguard Company NetworksThis slide showcases the strategies employed under SAP cybersecurity to secure company networks. The purpose of this template is to help the business implement SAP cybersecurity measures through the use of techniques such as roles and authorizations, patch management, etc. Introducing our premium set of slides with Techniques Employed Under SAP Cyber Security To Safeguard Company Networks. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Roles And Authorizations, Patch Management, Transaction Monitoring. So download instantly and tailor it with your information.
-
 Firewall Network Security Understanding The Cyber Threats Prevented By Waf
Firewall Network Security Understanding The Cyber Threats Prevented By WafThis slide represents the many cyberattacks that a WAF is designed to stop. The purpose of this slide is to showcase the various cyber attacks that can avoided with the help of WAF, such as DDoS attacks, zero-day threats, cross-site scripting XSS, cookie poisoning, web scrapping, parameter tampering, and SQL injection. Introducing Firewall Network Security Understanding The Cyber Threats Prevented By Waf to increase your presentation threshold. Encompassed with Eight stages, this template is a great option to educate and entice your audience. Dispence information on Cookie Poisoning, Sql Injection, Parameter Tampering using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Why Firewalls Are Frontline Defense Against Cyber Attacks
Firewall Network Security Why Firewalls Are Frontline Defense Against Cyber AttacksThis slide outlines the various reasons why firewalls are used as a first line of defense against cyber attacks. The purpose of this slide is to showcase the multiple reasons that make firewalls a frontline defense against cyber attacks, including blocking incoming risks, providing in-depth security, and so on. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Why Firewalls Are Frontline Defense Against Cyber Attacks This template helps you present information on Five stages. You can also present information on Blocks Incoming Threats, Provides In Depth Security, Offers Individualized Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Firewall Features To Effectively Prevent Cyber Attacks
Firewall Network Security Firewall Features To Effectively Prevent Cyber AttacksThis slide outlines the primary characteristics a firewall should have to prevent cyber attacks on a network. The purpose of this slide is to showcase the different features that a firewall should possess, including scalable performance, unified security management, threat prevention, and so on. Introducing Firewall Network Security Firewall Features To Effectively Prevent Cyber Attacks to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on URL Categories By Traffic, Traffic Source IP, Traffic Desintation IP using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Common Types Of Cyber Crime
Ethical Hacking And Network Security Common Types Of Cyber CrimeThis slide describes the common types of cybercrime such as identity theft, computer fraud, privacy breach, electronic money laundering, electronic funds transfer, and so on. Introducing Ethical Hacking And Network Security Common Types Of Cyber Crime to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Electronic Money Laundering, Electronic Funds Transfer, Denial Of Service Attacks, Sharing Copyrighted Files Or Data, using this template. Grab it now to reap its full benefits.
-
 Comparative Analysis Of Cyber Network Monitoring Tools
Comparative Analysis Of Cyber Network Monitoring ToolsFollowing slide represents network security monitoring tools for comparative analysis to choose better option. It further covers tools, price, platforms and features such as offline analysis, triggering alerts on real time basis, block third party trackers, etc. Introducing our Comparative Analysis Of Cyber Network Monitoring Tools set of slides. The topics discussed in these slides are Threat Levels, Website Traffic, Real Time Analysis. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Monitoring Organization Cyber Network Safety Icon
Monitoring Organization Cyber Network Safety IconPresenting our set of slides with Monitoring Organization Cyber Network Safety Icon This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Monitoring Organization, Network Safety.
-
 Cyber Security Policies For Robust Organizational Network
Cyber Security Policies For Robust Organizational NetworkThis slide covers essential cybersecurity policies. The purpose of this template is to provide a focused understanding of the intrusion prevention policy, host integrity policy, live update policy, and information security policy. Introducing our premium set of slides with Cyber Security Policies For Robust Organizational Network Ellicudate the Five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Intrusion Prevention Policy, Host Integrity Policy, Information Security Policy. So download instantly and tailor it with your information.
-
 Cyber Security Policies Safeguarding Network Infrastructure
Cyber Security Policies Safeguarding Network InfrastructureThis slide covers essential security policies. The purpose of this template is to provide a comprehensive overview of essential IT security policies, including Program, Issue-Specific, and System-Specific policies. Presenting our set of slides with Cyber Security Policies Safeguarding Network Infrastructure This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Program Policy, System-Specific Policy
-
 ATP Cyber Network Security Icon
ATP Cyber Network Security IconPresenting our set of slides with name ATP Cyber Network Security Icon. This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on ATP Cyber Network, Security Icon.
-
 Checklist To Enhance Cyber Security Of SCADA Networks
Checklist To Enhance Cyber Security Of SCADA NetworksThis slide represents checklist that assist IT companies to enhance their SCADA networks cyber security for improving data protection. It includes various elements such as recognizing connections, disconnecting irrelevant networks, etc. Introducing our Checklist To Enhance Cyber Security Of SCADA Networks set of slides. The topics discussed in these slides are Essential Connections, Inadvertent Disclosure, SCADA Network This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
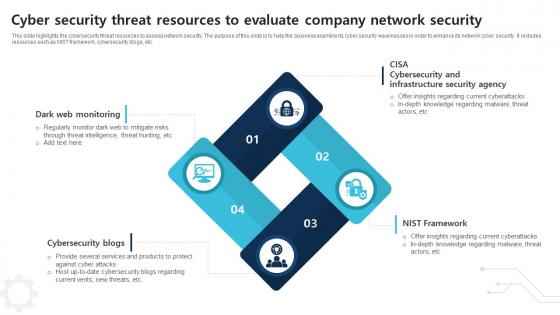 Cyber Security Threat Resources To Evaluate Company Network Security
Cyber Security Threat Resources To Evaluate Company Network SecurityThis slide highlights the cybersecurity threat resources to assess network security. The purpose of this slide is to help the business examine its cyber security weaknesses in order to enhance its network cyber security. It includes resources such as NIST framework, cybersecurity blogs, etc. Introducing our premium set of slides with Cyber Security Threat Resources To Evaluate Company Network Security Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Dark Web Monitoring, Cybersecurity Blogs, Nist Framework So download instantly and tailor it with your information.
-
 Cyber Threat Intelligence Framework To Safeguard Business Networks
Cyber Threat Intelligence Framework To Safeguard Business NetworksThis slide depicts the cyber threat intelligence framework utilized to safeguard business networks. The purpose of this slide is to help the business properly integrate cyber threat intelligence. It includes elements such as strategic CTI, tactical CTI, etc. Presenting our set of slides with Cyber Threat Intelligence Framework To Safeguard Business Networks This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Operational CTI, Strategic CTI
-
 Comparative Analysis For Network Intrusion Protection Cyber Security Tools
Comparative Analysis For Network Intrusion Protection Cyber Security ToolsThis slide depicts the comparative evaluation of NIPS security tools. The purpose of this slide is to help the business make a well informed purchase decision. It includes comparison on the basis of the free trial period, features, ratings, etc. Introducing our premium set of slides with Comparative Analysis For Network Intrusion Protection Cyber Security Tools Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Distinctive Features, Free Trial, Tools So download instantly and tailor it with your information.
-
 Network Intrusion And Prevention Cyber Security Icon
Network Intrusion And Prevention Cyber Security IconPresenting our set of slides with Network Intrusion And Prevention Cyber Security Icon This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Intrusion, Prevention Cyber Security Icon
-
 Network Intrusion Prevention Cyber Security System
Network Intrusion Prevention Cyber Security SystemThis slide highlights the network intrusion prevention system cybersecurity. The purpose of this slide is to help ensure that suitable processes are undertaken during security incidents. It includes elements such as network perimeters, internet, LAN, etc. Introducing our Network Intrusion Prevention Cyber Security System set of slides. The topics discussed in these slides are Internet, Network Perimeter, Prevention Systems This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Enterprise Network Cyber Security Management
Enterprise Network Cyber Security ManagementFollowing slide represents cyber security management enterprise network for financial protection. It further covers network deployment, feature configuration, network security management, network monitoring and network maintenance, etc. Presenting our set of slides with Enterprise Network Cyber Security Management. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Deployment, Feature Configuration, Network Security Management.
-
 Network Encryption Protection Icon For Cyber Security Management
Network Encryption Protection Icon For Cyber Security ManagementPresenting our set of slides with Network Encryption Protection Icon For Cyber Security Management. This exhibits information on two stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Encryption Protection Icon, Cyber Security Management.
-
 Network SIEM Cyber Security Icon
Network SIEM Cyber Security IconIntroducing our Network SIEM Cyber Security Icon set of slides. The topics discussed in these slides are Network SIEM, Cyber Security, Icon. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Mitigating Challenges Of Cyber Security On OT Network
Mitigating Challenges Of Cyber Security On OT NetworkThis slide represents various strategies that assist companies to mitigate various cyber security challenges on operational technology network effectively. It includes various challenges such as cloud and internet, IoT bots, DDoS attacks, etc. Introducing our premium set of slides with Mitigating Challenges Of Cyber Security On OT Network Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cloud And Internet, Ddos Attacks, Human Error And BYOD So download instantly and tailor it with your information.
-
 NIDS Cyber Security Icon To Enhance Network Protection
NIDS Cyber Security Icon To Enhance Network ProtectionPresenting our set of slides with NIDS Cyber Security Icon To Enhance Network Protection. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Protection, NIDS Cyber Security.
-
 Security Configuration Management Solutions In Cyber Network
Security Configuration Management Solutions In Cyber NetworkThis slide depicts the management solution for security configuration in cyber network. Its objective is to find the weak points of the company and fix them fast to safeguard them from attacks. This slide includes vulnerability assessment, remediation phase, etc. Introducing our premium set of slides with name Security Configuration Management Solutions In Cyber Network. Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Vulnerability, Automated Remediation, Configuration Assessment. So download instantly and tailor it with your information.
-
 Security Automation Dashboard Highlighting Network Enabling Automation In Cyber Security Operations
Security Automation Dashboard Highlighting Network Enabling Automation In Cyber Security OperationsThis slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline. Present the topic in a bit more detail with this Security Automation Dashboard Highlighting Network Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Automation, Dashboard, Highlighting. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Network Security VS Cyber Security Ppt Powerpoint Presentation Slides Diagrams Cpb
Network Security VS Cyber Security Ppt Powerpoint Presentation Slides Diagrams CpbPresenting Network Security VS Cyber Security Ppt Powerpoint Presentation Slides Diagrams Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Network Security VS Cyber Security. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Network Security Cyber Threat Landscape In Network Security
Network Security Cyber Threat Landscape In Network SecurityThis slide depicts the cyber threat landscape based on cybercriminal roles actors and the impacts of successful cyberattacks on business. Deliver an outstanding presentation on the topic using this Network Security Cyber Threat Landscape In Network Security. Dispense information and present a thorough explanation of Cyber Threat Landscape In Network Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Various Cyber Security Threats And Strategies To Manage Network Service
Various Cyber Security Threats And Strategies To Manage Network ServiceThis slide highlights different types of cybersecurity threat such as malware, phishing, trojan horse and rootkit. The template also provides information about various strategies which will assist IT department to manage its network services. Introducing our premium set of slides with Various Cyber Security Threats And Strategies To Manage Network Service. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Strategies Overcome Threats, IT Security Services, Provide Security Awareness. So download instantly and tailor it with your information.
-
 Cyber Physical Systems Architecture Network Layer Ppt Powerpoint Presentation File Outline
Cyber Physical Systems Architecture Network Layer Ppt Powerpoint Presentation File OutlineThis slide describes the network layer of cyber physical system architecture, including the tasks performed and protocols used at this level, such as IPv6, LTE, IR, and so on. Present the topic in a bit more detail with this Cyber Physical Systems Architecture Network Layer Ppt Powerpoint Presentation File Outline. Use it as a tool for discussion and navigation on Applications Services, Communication Networks, Physical Infrastructures. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Intelligent System Cyber Physical Systems Architecture Network Layer
Intelligent System Cyber Physical Systems Architecture Network LayerThis slide describes the network layer of cyber-physical system architecture, including the tasks performed and protocols used at this level, such as IPv6, LTE, IR, and so on. Present the topic in a bit more detail with this Intelligent System Cyber Physical Systems Architecture Network Layer. Use it as a tool for discussion and navigation on Architecture, Technologies, Transmission. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Elements IT Network Security Element Of Cyber Security Ppt Background
Cyber Security Elements IT Network Security Element Of Cyber Security Ppt BackgroundThis slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, end point security, virtual private security and antivirus software. Introducing Cyber Security Elements IT Network Security Element Of Cyber Security Ppt Background to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Email Security, Virtual Private Network, Antivirus Software, using this template. Grab it now to reap its full benefits.
-
 Enterprise Network It Security Automation Enabling Automation In Cyber Security Operations
Enterprise Network It Security Automation Enabling Automation In Cyber Security OperationsThis slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps. Deliver an outstanding presentation on the topic using this Enterprise Network It Security Automation Enabling Automation In Cyber Security Operations. Dispense information and present a thorough explanation of Orchestrating Network Security, Troubleshooting, Integrating Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 F735 Cyber Physical Systems Architecture Network Layer Next Generation Computing Systems
F735 Cyber Physical Systems Architecture Network Layer Next Generation Computing SystemsThis slide describes the network layer of cyber-physical system architecture, including the tasks performed and protocols used at this level, such as IPv6, LTE, IR, and so on. Present the topic in a bit more detail with this F735 Cyber Physical Systems Architecture Network Layer Next Generation Computing Systems. Use it as a tool for discussion and navigation on Architecture, Applications Services, Monitoring . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Q916 Cyber Physical Systems Architecture Network Layer Collective Intelligence Systems
Q916 Cyber Physical Systems Architecture Network Layer Collective Intelligence SystemsThis slide describes the network layer of cyber-physical system architecture, including the tasks performed and protocols used at this level, such as IPv6, LTE, IR, and so on. Present the topic in a bit more detail with this Q916 Cyber Physical Systems Architecture Network Layer Collective Intelligence Systems. Use it as a tool for discussion and navigation on Monitoring, Control, Dispatchers, Routers. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Network Security Practices To Prevent Cyber Attacks
Network Security Practices To Prevent Cyber AttacksThe given slide highlights some of the best practices to mitigate cyber attacks. Some of them are as backing up the data, training employees, preparing cyber incident response plan, securing sites and updating systems and software. Presenting our set of slides with Network Security Practices To Prevent Cyber Attacks. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Train Employees, Secure Sites.
-
 Cyber Security Network Development Roadmap
Cyber Security Network Development RoadmapThe following slide depicts a roadmap to plan an action plan to ensure data safety and prevent threats. It also includes quarter wise actions such as analyse, establish, select and practice.Presenting our set of slides with Cyber Security Network Development Roadmap. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Policies, Cybersecurity Services, Corrective Actions.
-
 Cyber Security Policy Overview Of Network Security Policy For Workers
Cyber Security Policy Overview Of Network Security Policy For WorkersThis slide describes the network security policy, which ensures systems have the proper hardware, software, and auditing processes. It logs details of activities such as failed log-in attempts, information starts up or shutdown, etc. Increase audience engagement and knowledge by dispensing information using Cyber Security Policy Overview Of Network Security Policy For Workers. This template helps you present information on six stages. You can also present information on Overview, Information, Confidentiality using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Network Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Network Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful PowerPoint icon is perfect for illustrating global protection. It features a globe surrounded by a shield, signifying security and safety on a global scale. Its ideal for presentations on international security, risk management, and more.
-
 Cyber Network Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Network Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone PowerPoint icon is perfect for presentations on global protection. It features a shield with a globe in the center, symbolizing the protection of the world. The icon is simple and professional, making it ideal for any presentation.
-
 Cyber Security Threat And Network Hacking Icon
Cyber Security Threat And Network Hacking IconIntroducing our premium set of slides with Cyber Security Threat And Network Hacking Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Security, Network Hacking. So download instantly and tailor it with your information.
-
 Cyber Security Strategy Network Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Security Strategy Network Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Cyber security strategy network colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Cyber Security Strategy Network Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Security Strategy Network Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Cyber security strategy network monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
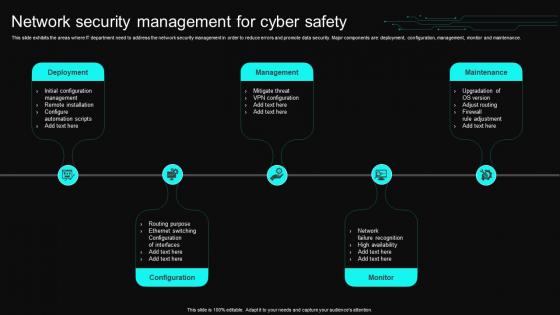 Network Security Management For Cyber Safety
Network Security Management For Cyber SafetyThis slide exhibits the areas where IT department need to address the network security management in order to reduce errors and promote data security. Major components are deployment, configuration, management, monitor and maintenance. Presenting our set of slides with Network Security Management For Cyber Safety. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Deployment, Management, Maintenance, Configuration.
-
 Cyber Security Remote Work Network Security In Powerpoint And Google Slides Cpb
Cyber Security Remote Work Network Security In Powerpoint And Google Slides CpbPresenting our Cyber Security Remote Work Network Security In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Cyber Security Remote Work Network Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.




