Powerpoint Templates and Google slides for Cyber Attacks
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Security Attack Control Icon
Cyber Security Attack Control IconIntroducing our premium set of slides with Cyber Security Attack Control Icon Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Security Attack Control Icon So download instantly and tailor it with your information.
-
 Web Security Icon To Prevent Cyber Attacks
Web Security Icon To Prevent Cyber AttacksPresenting our set of slides with Web Security Icon To Prevent Cyber Attacks This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Web Security Icon, Prevent Cyber Attacks
-
 Types Of Cyber Attacks Faced By Organization Impact Of Generative AI SS V
Types Of Cyber Attacks Faced By Organization Impact Of Generative AI SS VThis slide showcases various types of cyber attacks that significantly damage the organization resources and reputation. Different types of attacks faced are Malware, Phishing, Man in middle attack, SQL injection etc. Introducing Types Of Cyber Attacks Faced By Organization Impact Of Generative AI SS V to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Malware, Phishing, Injection, using this template. Grab it now to reap its full benefits.
-
 Cyber Attack And Readiness Assessment And Management Matrix
Cyber Attack And Readiness Assessment And Management MatrixFollowing slide highlights readiness evaluation to cyber security management for compliance with regulations. It further covers process, technology used, people target and basis such as basic, advanced and extended, etc. Introducing our Cyber Attack And Readiness Assessment And Management Matrix set of slides. The topics discussed in these slides are Process, Technology, People. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Complete Phases Of Lateral Movement In Cyber Attack
Complete Phases Of Lateral Movement In Cyber AttackThe slide maps the comprehensive phases of lateral movement in a cyber attack, covering elements such as email with malicious content, user actions, DNS logs, web proxy, compromised accounts, multi-factor authentication, and privilege escalation. It serves as a guide for understanding and fortifying defenses across the entire lateral movement spectrum. Presenting our set of slides with Complete Phases Of Lateral Movement In Cyber Attack. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Compromised Account, Escalation Of Privileges, Lateral Movement .
-
 Lateral Movement Cyber Attack Stages
Lateral Movement Cyber Attack StagesThe slide illuminates stages of a cyber attack, focusing on reconnaissance, credential dumping, and gaining access in the context of lateral movement. It facilitates comprehension and mitigation strategies for enhancing cybersecurity resilience. Introducing our premium set of slides with Lateral Movement Cyber Attack Stages. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Reconnaissance, Credential Dumping Privilege Escalation, Gaining Access. So download instantly and tailor it with your information.
-
 Lateral Movement Cyber Attack Techniques
Lateral Movement Cyber Attack TechniquesThe slide illustrates lateral movement cyber attack techniques, including pass the hash, remote execution, man-in-the-middle attacks, lateral phishing, and living off the land. It serves as a valuable resource for enhancing awareness and implementing countermeasures against these sophisticated tactics. Presenting our set of slides with Lateral Movement Cyber Attack Techniques. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Remote Execution, Lateral Phishing, Living Off The Land.
-
 Types Of Cyber Attacks Possessing Lateral Movements
Types Of Cyber Attacks Possessing Lateral MovementsThe slide categorizes cyber threats, such as advanced persistent threats, ransomware attacks, data breaches, credential theft, and insider threats, emphasizing their lateral movement potential. This classification aids in strategizing comprehensive defenses against varied types of cyber attacks. Introducing our premium set of slides with Types Of Cyber Attacks Possessing Lateral Movements. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Ransomware Attacks, Data Breaches, Credential Theft Attacks. So download instantly and tailor it with your information.
-
 Icon For Phishing Attack As Cyber Deception
Icon For Phishing Attack As Cyber DeceptionPresenting our set of slides with Icon For Phishing Attack As Cyber Deception. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Icon, Phishing Attack As, Cyber Deception.
-
 Cyber Attack Vulnerability Icon For Security Management
Cyber Attack Vulnerability Icon For Security ManagementPresenting our set of slides with Cyber Attack Vulnerability Icon For Security Management This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Attack Vulnerability, Security Management
-
 Cyber Attack Restriction Plan Checklist Business Recovery Plan To Overcome Cyber Security Threat
Cyber Attack Restriction Plan Checklist Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information on various cyber attack containment strategies that can be implemented to prevent further data breaches such as restraining lateral movements, and data breach evident collection. Deliver an outstanding presentation on the topic using this Cyber Attack Restriction Plan Checklist Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Containment, Strategies, Implemented using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Potential Consistent Cyber Security Attacks Business Recovery Plan To Overcome Cyber Security Threat
Potential Consistent Cyber Security Attacks Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about various solutions that can be adopted for business cyber-attack management. It includes key solutions such as staff training, collaboration with experts, and develop business recovery plan. Deliver an outstanding presentation on the topic using this Potential Consistent Cyber Security Attacks Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Solution Scope, Solution Duration, Requisites using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Setting Goals For Cyber Attack Management Business Recovery Plan To Overcome Cyber Security Threat
Setting Goals For Cyber Attack Management Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about time-based goals set for cyber attack management. It includes goals such as mean time to detect incidents, containment time, resolution time, and recovery time. Introducing Setting Goals For Cyber Attack Management Business Recovery Plan To Overcome Cyber Security Threat to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Mean Time To Contain, Mean Time To Resolve, Mean Time To Recover, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Attacks In Blockchain Technology
Cyber Security Attacks In Blockchain TechnologyPresenting our set of slides with Cyber Security Attacks In Blockchain Technology. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Interception, Floods Networks, False Identities.
-
 Blockchain Technology Cyber Attack Illustration
Blockchain Technology Cyber Attack IllustrationThis colourful PowerPoint icon features a delicious assortment of cyber treats, representing the exciting world of blockchain technology. Perfect for presentations on cryptocurrency, digital security, and the future of finance, this icon adds a fun and eye-catching touch to your slides. Get your audience hungry for knowledge with this vibrant icon.
-
 Firewall Features To Effectively Prevent Cyber Attacks Revolutionizing Connectivity Exploring
Firewall Features To Effectively Prevent Cyber Attacks Revolutionizing Connectivity ExploringThis slide outlines the primary characteristics a firewall should have to prevent cyber attacks on a network. The purpose of this slide is to showcase the different features that a firewall should possess, including scalable performance, Unified Security Management, threat prevention, etc. Increase audience engagement and knowledge by dispensing information using Firewall Features To Effectively Prevent Cyber Attacks Revolutionizing Connectivity Exploring This template helps you present information on Five stages. You can also present information on Scalable Performance, Threat Prevention, Hybrid Cloud Support using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Digital Infrastructure Technology Applications To Prevent Cyber Attacks
Digital Infrastructure Technology Applications To Prevent Cyber AttacksThe following slide provides the use of various digital technologies to prevent cyber threats and risks. It mentions the technologies such as behavioral analytics, blockchain, cloud encryption, etc. Introducing our premium set of slides with Digital Infrastructure Technology Applications To Prevent Cyber Attacks. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Behavioural Analytics, Blockchain, Cloud Encryption, Defensive AI. So download instantly and tailor it with your information.
-
 Impact Of Cyber Attacks On Organizational Operations IT Security Awareness Training Cybersecurity SS
Impact Of Cyber Attacks On Organizational Operations IT Security Awareness Training Cybersecurity SSThis slide represents impact of attacks that are attempted to steal sensitive information in the form of user names, credit card numbers etc. on organizational operations. Increase audience engagement and knowledge by dispensing information using Impact Of Cyber Attacks On Organizational Operations IT Security Awareness Training Cybersecurity SS. This template helps you present information on four stages. You can also present information on Reputational Damage, Stolen Intellectual Property, Operational Disruption, Increased Costs using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Chatbot Security Icon To Reduce Cyber Attacks
Chatbot Security Icon To Reduce Cyber AttacksIntroducing our premium set of slides with Chatbot Security Icon To Reduce Cyber Attacks. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Chatbot Security, Icon To Reduce, Cyber Attacks. So download instantly and tailor it with your information.
-
 Email Security Best Practices Steps To Secure Email From Cyber Attacks
Email Security Best Practices Steps To Secure Email From Cyber AttacksThis slide outlines the steps for implementing email security policies to avoid cyber attacks. These include strong password, two-factor authentication, email encryption, software updating, choose a trustworthy email provider, etc. Present the topic in a bit more detail with this Email Security Best Practices Steps To Secure Email From Cyber Attacks. Use it as a tool for discussion and navigation on Two-Factor Authentication, Email Encryption, Virtual Private Network. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attacks Caused By IOT Security Vulnerabilities
Cyber Attacks Caused By IOT Security VulnerabilitiesThis slide showcases an overview of attacks that disrupt smooth functioning. Threats covered in the slide are IoT botnets and data exfiltration. Introducing our Cyber Attacks Caused By IOT Security Vulnerabilities set of slides. The topics discussed in these slides are Examples, Description, IOT Botnets, Data Exfiltration . This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Email Protection Against Cyber Attacks Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Email Protection Against Cyber Attacks Colored Icon In Powerpoint Pptx Png And Editable Eps FormatProtect your emails from cyber threats with our Email Security PowerPoint icon. This vibrant and eye-catching icon features a shield with a lock symbol, representing the strong defense against potential attacks. Use it to educate your audience on the importance of email security in todays digital world.
-
 Email Protection Against Cyber Attacks Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Email Protection Against Cyber Attacks Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is the perfect visual aid for presentations on Email security and defense against cyber threats. With its simple yet impactful design, it effectively conveys the importance of protecting email communications from potential cyber attacks. Add this icon to your slides to enhance your message and engage your audience.
-
 Cyber Attacks Detection In Iot Systems Strategic Guide To Implement Strategy SS
Cyber Attacks Detection In Iot Systems Strategic Guide To Implement Strategy SSPresent the topic in a bit more detail with this Cyber Attacks Detection In Iot Systems Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Social Media, Gamepad, Firewall, Storage, Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Espionage Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS
Cyber Espionage Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SSThis slide showcases Cyber Espionage attack with mitigation strategies and example. It includes mitigation strategies such as regular security audits and threat intelligence.Increase audience engagement and knowledge by dispensing information using Cyber Espionage Attack With Mitigation Strategies And Example Strategic Guide To Implement Strategy SS. This template helps you present information on three stages. You can also present information on Key Elements, Mitigation Strategies, Example using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Train Employees On Cyber Attack Prevention Strategic Guide To Implement Strategy SS
Train Employees On Cyber Attack Prevention Strategic Guide To Implement Strategy SSThis slide showcases the Train employees on cyber attack prevention. It includes techniques such as email impersonation, vigilance in clicking links, verification of email addresses and use of common sense.Present the topic in a bit more detail with this Train Employees On Cyber Attack Prevention Strategic Guide To Implement Strategy SS. Use it as a tool for discussion and navigation on Threat Scenario, Description, Employee Awareness. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attack Icon To Affect Supply Chain Operations
Cyber Attack Icon To Affect Supply Chain OperationsPresenting our set of slides with name Cyber Attack Icon To Affect Supply Chain Operations. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Attack Icon, Affect Supply Chain Operations.
-
 Supply Chain Security Checklist To Prevent Cyber Attacks
Supply Chain Security Checklist To Prevent Cyber AttacksThis slide represents checklist that helps companies to enhance their supply chain security and prevent suppliers from potential cyberattacks effectively. It includes various parameters such as documenting supply chain security plan, conducting suppliers meeting, etc. Presenting our well structured Supply Chain Security Checklist To Prevent Cyber Attacks. The topics discussed in this slide are Supply Chain Security Plan, Network, Evaluation Processes. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Most Common Cyber Attack Building A Security Awareness Program
Most Common Cyber Attack Building A Security Awareness ProgramThe purpose of this slide is to showcase various kind of cyber attack which are currently faced by the employees. The most common cyber attacks are ransomware, password attack, crypto jacking, IoT based attacks, malware, social engineering attack and business email compromise. Present the topic in a bit more detail with this Most Common Cyber Attack Building A Security Awareness Program. Use it as a tool for discussion and navigation on Ransomware, Password Attack, Cryptojacking. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attacks Faced By The Company In Previous Year Implementing Cyber Security Ppt Demonstration
Cyber Attacks Faced By The Company In Previous Year Implementing Cyber Security Ppt DemonstrationThis slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Present the topic in a bit more detail with this Cyber Attacks Faced By The Company In Previous Year Implementing Cyber Security Ppt Demonstration. Use it as a tool for discussion and navigation on Ransomware Attacks, Phishing Attacks, Previous Year. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Technical Analysis Of DDOS Attacks Against Ukrainian Websites String Of Cyber Attacks Against
Technical Analysis Of DDOS Attacks Against Ukrainian Websites String Of Cyber Attacks AgainstThis slide represents the technical analysis of ddos attacks against ukrainian websites by showing the internet traffic to the oschad bank website on 15 16 february 2022. Deliver an outstanding presentation on the topic using this Technical Analysis Of DDOS Attacks Against Ukrainian Websites String Of Cyber Attacks Against. Dispense information and present a thorough explanation of Customers, Accessing Banking, Websites using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
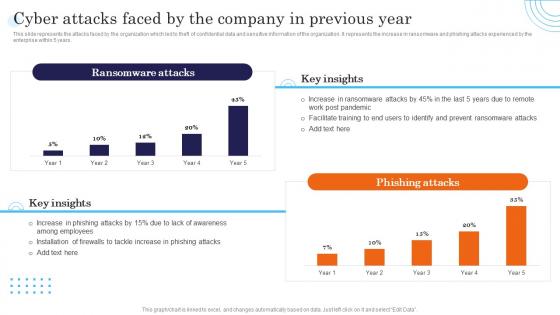 Cyber Attacks Faced By The Company In Previous Year Incident Response Strategies Deployment
Cyber Attacks Faced By The Company In Previous Year Incident Response Strategies DeploymentThis slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Deliver an outstanding presentation on the topic using this Cyber Attacks Faced By The Company In Previous Year Incident Response Strategies Deployment. Dispense information and present a thorough explanation of Ransomware, Phishing, Cyber using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
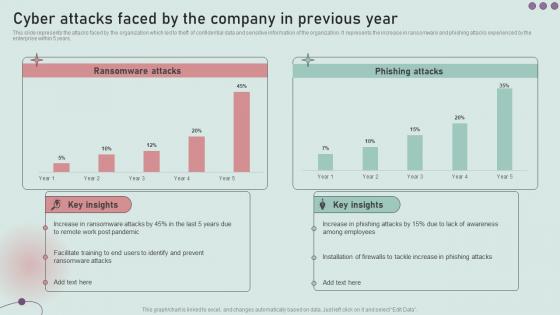 Cyber Attacks Faced By The Company In Previous Year Development And Implementation Of Security
Cyber Attacks Faced By The Company In Previous Year Development And Implementation Of SecurityThis slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Present the topic in a bit more detail with this Cyber Attacks Faced By The Company In Previous Year Development And Implementation Of Security. Use it as a tool for discussion and navigation on Ransomware Attacks, Phishing Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Cyber Attacks Faced By The Company In Previous Year
Cyber Security Attacks Response Plan Cyber Attacks Faced By The Company In Previous YearThis slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Plan Cyber Attacks Faced By The Company In Previous Year. Dispense information and present a thorough explanation of Ransomware Attacks, Phishing Attacks, Post Pandemic using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
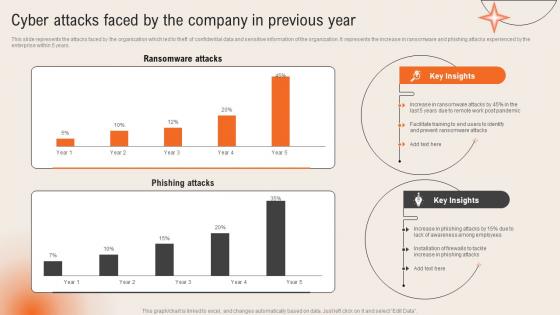 Cyber Attacks Faced By The Company In Previous Year Deploying Computer Security Incident Management
Cyber Attacks Faced By The Company In Previous Year Deploying Computer Security Incident ManagementThis slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years.Present the topic in a bit more detail with this Cyber Attacks Faced By The Company In Previous Year Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Ransomware Attacks, Phishing Attacks, Awareness Among Employees. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Phishing Attacks Tracking Dashboard Phishing Attacks And Strategies
Cyber Phishing Attacks Tracking Dashboard Phishing Attacks And StrategiesThis slide represents the dashboard to track cyber phishing attacks. The purpose of this slide is to provide a graphical representation of cyber attacks occurred in a specific time span. It also depicts the organizations health risk.Deliver an outstanding presentation on the topic using this Cyber Phishing Attacks Tracking Dashboard Phishing Attacks And Strategies. Dispense information and present a thorough explanation of Cyber Phishing Attacks, Tracking Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Electronic information security cyber attacks experienced company previous
Electronic information security cyber attacks experienced company previousThis slide shows the impact on the organizations financial condition due to cyber attacks in the past financial year 2022. Deliver an outstanding presentation on the topic using this Electronic Information Security Cyber Attacks Experienced Company Previous. Dispense information and present a thorough explanation of Cyber Attacks, Massive Increase using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Technical analysis of ddos attacks against ukrainian websites ukraine and russia cyber warfare it
Technical analysis of ddos attacks against ukrainian websites ukraine and russia cyber warfare itThis slide represents the technical analysis of DDoS attacks against Ukrainian websites by showing the internet traffic to the Oschad Bank website on 15 16 February 2022. Present the topic in a bit more detail with this Technical Analysis Of Ddos Attacks Against Ukrainian Websites Ukraine And Russia Cyber Warfare It. Use it as a tool for discussion and navigation on Technical, Analysis, Ukrainian. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ukraine and russia cyber warfare it global uprising of grassroots volunteer attacks
Ukraine and russia cyber warfare it global uprising of grassroots volunteer attacksThis slide describes the global uprising of Grassroots volunteer attacks on Russia by spray painting anti war slogans on news outlets and exposing information from competing for hacking operations. Deliver an outstanding presentation on the topic using this Ukraine And Russia Cyber Warfare It Global Uprising Of Grassroots Volunteer Attacks. Dispense information and present a thorough explanation of Global Uprising Of Grassroots Volunteer Attacks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ukraine and russia cyber warfare it technical analysis of ddos attacks against ukrainian websites
Ukraine and russia cyber warfare it technical analysis of ddos attacks against ukrainian websitesThis slide depicts the technical analysis of distributed denial of service attacks against Ukrainian websites on 15-16 February 2022, and the graph shows internet traffic to the private bank. Deliver an outstanding presentation on the topic using this Ukraine And Russia Cyber Warfare It Technical Analysis Of Ddos Attacks Against Ukrainian Websites. Dispense information and present a thorough explanation of Technical, Analysis, Websites using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Loss caused by different types of cyber attacks ppt powerpoint presentation layouts
Loss caused by different types of cyber attacks ppt powerpoint presentation layoutsThis slide represents the different types of cyber attacks throughout the year, including the percentage of total loss caused by these attacks. Present the topic in a bit more detail with this Loss Caused By Different Types Of Cyber Attacks Ppt Powerpoint Presentation Layouts. Use it as a tool for discussion and navigation on Loss Caused By Different Types Of Cyber Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Reverse Proxy It Cyber Attacks On The Main Server Of Company
Reverse Proxy It Cyber Attacks On The Main Server Of CompanyThis slide shows the current situation of the organization through the total losses in millions experienced because of different types of the cyber attacks. Deliver an outstanding presentation on the topic using this Reverse Proxy It Cyber Attacks On The Main Server Of Company. Dispense information and present a thorough explanation of Cyber Attacks On The Main Server Of Company using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Loss due to different cyber attacks hacking it
Loss due to different cyber attacks hacking itThis slide represents the different types of cyber attacks throughout the year, including the percentage of total loss caused by these attacks. Present the topic in a bit more detail with this Loss Due To Different Cyber Attacks Hacking It. Use it as a tool for discussion and navigation on Loss Due To Different Cyber Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attacks On Ukraine Global Uprising Of Grassroots Volunteer Attacks
Cyber Attacks On Ukraine Global Uprising Of Grassroots Volunteer AttacksThis slide describes the global uprising of Grassroots volunteer attacks on Russia by spray painting anti war slogans on news outlets and exposing information from competing for hacking operations. Deliver an outstanding presentation on the topic using this Cyber Attacks On Ukraine Global Uprising Of Grassroots Volunteer Attacks. Dispense information and present a thorough explanation of Global Uprising Of Grassroots Volunteer Attacks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Attacks On Ukraine Technical Analysis Of DDOS Attacks Against
Cyber Attacks On Ukraine Technical Analysis Of DDOS Attacks AgainstThis slide represents the technical analysis of DDoS attacks against Ukrainian websites by showing the internet traffic to the Orchid Bank website on 15 16 February 2022. Present the topic in a bit more detail with this Cyber Attacks On Ukraine Technical Analysis Of DDOS Attacks Against. Use it as a tool for discussion and navigation on Technical Analysis Of Ddos Attacks Against Ukrainian Websites. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Technical Analysis Of Ddos Attacks Against Ukrainian Cyber Attacks On Ukraine
Technical Analysis Of Ddos Attacks Against Ukrainian Cyber Attacks On UkraineThis slide depicts the technical analysis of distributed denial of service attacks against Ukrainian websites on 15 16 February 2022, and the graph shows internet traffic to the private bank. Present the topic in a bit more detail with this Technical Analysis Of Ddos Attacks Against Ukrainian Cyber Attacks On Ukraine. Use it as a tool for discussion and navigation on Technical Analysis Of Ddos Attacks Against Ukrainian Websites. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
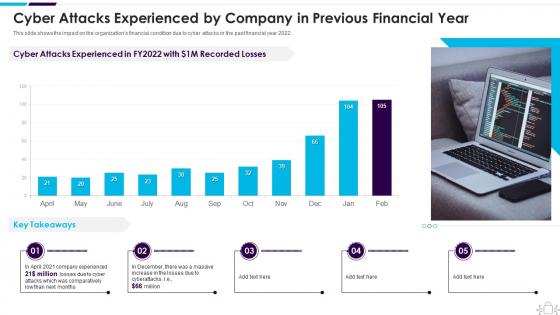 Cyber Attacks Experienced By Company In Previous Information Technology Security
Cyber Attacks Experienced By Company In Previous Information Technology SecurityThis slide shows the impact on the organizations financial condition due to cyber attacks in the past financial year 2022. Present the topic in a bit more detail with this Cyber Attacks Experienced By Company In Previous Information Technology Security. Use it as a tool for discussion and navigation on Experienced, Previous, Financial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Average Loss To Firms In European Countries Cyber Terrorism Attacks
Average Loss To Firms In European Countries Cyber Terrorism AttacksThis slide depicts the average loss to firms in European countries, representing Germany as the most affected country. Present the topic in a bit more detail with this Average Loss To Firms In European Countries Cyber Terrorism Attacks. Use it as a tool for discussion and navigation on Average Loss To Firms In European Countries. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Terrorism Attacks Impact Of Implementing Cyber Security
Cyber Terrorism Attacks Impact Of Implementing Cyber SecurityThis slide represents the current state of cyber assaults in a business after implementing the cyber security model. Deliver an outstanding presentation on the topic using this Cyber Terrorism Attacks Impact Of Implementing Cyber Security. Dispense information and present a thorough explanation of Impact Of Implementing Cyber Security Measures In The Company using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Terrorism Faced By Companies In US Cyber Terrorism Attacks
Cyber Terrorism Faced By Companies In US Cyber Terrorism AttacksThis slide depicts the cyber terrorism attacks faced by the companies in the US, and the graph represents the financial losses in the last five years. Present the topic in a bit more detail with this Cyber Terrorism Faced By Companies In US Cyber Terrorism Attacks. Use it as a tool for discussion and navigation on Cyber Terrorism Faced By Companies In Us. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Terrorism Faced By Various Industries Cyber Terrorism Attacks
Cyber Terrorism Faced By Various Industries Cyber Terrorism AttacksThis slide describes the cyber terrorism attacks various industries face, including health, finance, media, transportation and education. Deliver an outstanding presentation on the topic using this Cyber Terrorism Faced By Various Industries Cyber Terrorism Attacks. Dispense information and present a thorough explanation of Cyber Terrorism Faced By Various Industries using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Terrorist Experienced By Company Cyber Terrorism Attacks
Cyber Terrorist Experienced By Company Cyber Terrorism AttacksThis slide describes the number of cyber terrorist attacks experienced by the company in the previous financial year 2022. Present the topic in a bit more detail with this Cyber Terrorist Experienced By Company Cyber Terrorism Attacks. Use it as a tool for discussion and navigation on Cyber Terrorist Experienced By Company In Previous Financial Year. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Dashboard For Threat Tracking Cyber Terrorism Attacks
Dashboard For Threat Tracking Cyber Terrorism AttacksThis slide depicts the dashboard for threat tracking of cyber terrorism by covering top threats, threats by class name, etc. Deliver an outstanding presentation on the topic using this Dashboard For Threat Tracking Cyber Terrorism Attacks. Dispense information and present a thorough explanation of Dashboard For Threat Tracking Of Cyber Terrorism using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Distributed Denial Of Service DDOS Cyber Terrorism Attacks
Distributed Denial Of Service DDOS Cyber Terrorism AttacksThis slide explains the distributed denial of services DDOS as a cyber terrorism attacks tool and the common types of DDOS attacks. Present the topic in a bit more detail with this Distributed Denial Of Service DDOS Cyber Terrorism Attacks. Use it as a tool for discussion and navigation on Distributed Denial Of Service Ddos As Cyber Terrorism Tool. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implement Strong IT Guidelines In The Company Cyber Terrorism Attacks
Implement Strong IT Guidelines In The Company Cyber Terrorism AttacksThis slide depicts the strong IT guidelines which should be implemented in the company, such as security software, backups, fraud detection. Present the topic in a bit more detail with this Implement Strong IT Guidelines In The Company Cyber Terrorism Attacks. Use it as a tool for discussion and navigation on Implement Strong It Guidelines In The Company. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Installation And Update Of Antivirus Software Cyber Terrorism Attacks
Installation And Update Of Antivirus Software Cyber Terrorism AttacksThis slide represents the companys installation and update of antivirus software and the different antivirus software available in the market with the share of usage. Deliver an outstanding presentation on the topic using this Installation And Update Of Antivirus Software Cyber Terrorism Attacks. Dispense information and present a thorough explanation of Installation And Update Of Antivirus Software using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IT Infrastructure Cyber Security Budget Against Cyber Terrorism Attacks
IT Infrastructure Cyber Security Budget Against Cyber Terrorism AttacksThis slide depicts the IT infrastructure budget of incorporating cyber security, as well as the cost of each activity to the company. Present the topic in a bit more detail with this IT Infrastructure Cyber Security Budget Against Cyber Terrorism Attacks. Use it as a tool for discussion and navigation on It Infrastructure Cyber Security Budget Against Cyber Terrorism Fy19 20. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Use Of Strong Encrypted Password In The Company Cyber Terrorism Attacks
Use Of Strong Encrypted Password In The Company Cyber Terrorism AttacksThis slide demonstrates the need to have encrypted passwords for various online accounts and indicates how almost every employee has the same password. Present the topic in a bit more detail with this Use Of Strong Encrypted Password In The Company Cyber Terrorism Attacks. Use it as a tool for discussion and navigation on Use Of Strong Encrypted Password In The Company. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Hacker Loss Due To Different Cyber Attacks Ppt Powerpoint Presentation Slides
Security Hacker Loss Due To Different Cyber Attacks Ppt Powerpoint Presentation SlidesThis slide represents the different types of cyber attacks throughout the year, including the percentage of total loss caused by these attacks. Present the topic in a bit more detail with this Security Hacker Loss Due To Different Cyber Attacks Ppt Powerpoint Presentation Slides. Use it as a tool for discussion and navigation on Different Cyber Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attacks Faced By Organization In Risk Assessment And Management Plan For Information Security
Cyber Attacks Faced By Organization In Risk Assessment And Management Plan For Information SecurityThis slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type if cyber attacks and formulate strategies to tackle them Present the topic in a bit more detail with this Cyber Attacks Faced By Organization In Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Experienced, Organization, Financial. This template is free to edit as deemed fit for your organization. Therefore download it now.





