Powerpoint Templates and Google slides for Cyber Attack Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Security Elements IT Types Of Cyber Attackers Ppt Professional
Cyber Security Elements IT Types Of Cyber Attackers Ppt ProfessionalThis slide represents the types of cyber attackers, including cyber criminals, hacktivists, state sponsored attackers, and insider threats. Insider threats can be occurred from within the organization and can be malicious, accidental or negligent. Introducing Cyber Security Elements IT Types Of Cyber Attackers Ppt Professional to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Criminals, Insider Threats, Hacktivists, using this template. Grab it now to reap its full benefits.
-
 Dos And Donts Of Prevention From Ransomware Attack Developing Cyber Security Awareness Training
Dos And Donts Of Prevention From Ransomware Attack Developing Cyber Security Awareness TrainingThe purpose of this slide is to showcase the Dos and donts of ransomware prevention attack. The slide covers information about updating the software, installing a firewall software, using reliable website and sources etc. Increase audience engagement and knowledge by dispensing information using Dos And Donts Of Prevention From Ransomware Attack Developing Cyber Security Awareness Training. This template helps you present information on two stages. You can also present information on Confidential Files, Devices Safe, Firewall Software, Malware Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 General Outlook Of Ransomware Attack Developing Cyber Security Awareness Training Program For Staff
General Outlook Of Ransomware Attack Developing Cyber Security Awareness Training Program For StaffThe purpose of this slide is to outline an example of ransomware attack. The slide provides information about the working of ransomware attack work and how it can encrypts the victims data. Introducing General Outlook Of Ransomware Attack Developing Cyber Security Awareness Training Program For Staff to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Files Are Encrypted, Ransomware Works, General Outlook, using this template. Grab it now to reap its full benefits.
-
 Outlook Of Social Engineering Attack Developing Cyber Security Awareness Training Program For Staff
Outlook Of Social Engineering Attack Developing Cyber Security Awareness Training Program For StaffThe purpose of this slide is to showcase an example of social engineering attack. It also covers information about how the social engineering attack work and spread malware. Increase audience engagement and knowledge by dispensing information using Outlook Of Social Engineering Attack Developing Cyber Security Awareness Training Program For Staff. This template helps you present information on one stages. You can also present information on Social Engineering, Attack Works, Completion Of A Survey using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview Of Business Email Compromise Attack Developing Cyber Security Awareness Training Program
Overview Of Business Email Compromise Attack Developing Cyber Security Awareness Training ProgramThe purpose of this slide is to delineate an example of business email compromise attack. Information covered in this slide is related to the working of this attack and how it can result in loss of company reputation. Introducing Overview Of Business Email Compromise Attack Developing Cyber Security Awareness Training Program to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Overview Of Business, Email Compromise Attack, Restricted, using this template. Grab it now to reap its full benefits.
-
 Understanding The Frequency And Weightage Of Cyber Attacks By Departments Developing Cyber Security Awareness
Understanding The Frequency And Weightage Of Cyber Attacks By Departments Developing Cyber Security AwarenessThe purpose of this slide is to showcase the frequency and weightage of different cyber attacks on multiple departments. The major departments mentioned in the slide are financial, marketing, information technology IT and human resource HR. Increase audience engagement and knowledge by dispensing information using Understanding The Frequency And Weightage Of Cyber Attacks By Departments Developing Cyber Security Awareness. This template helps you present information on four stages. You can also present information on Marketing Team, HR Department, Financial Department, IT Department using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Various Techniques To Successfully Prevent Business Email Compromise Attack Developing Cyber Security Awareness
Various Techniques To Successfully Prevent Business Email Compromise Attack Developing Cyber Security AwarenessThe purpose of this slide is to outline different techniques which can be used to protect organization from business email compromise attack. The techniques covered in the slide are sender policy framework SPF, using strong password policy and process for wire transfers. Present the topic in a bit more detail with this Various Techniques To Successfully Prevent Business Email Compromise Attack Developing Cyber Security Awareness. Use it as a tool for discussion and navigation on Various Techniques, Successfully Prevent, Business Email, Compromise Attack. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attacks Faced By Different Departments Information Security Risk Management
Cyber Attacks Faced By Different Departments Information Security Risk ManagementThis slide showcase information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks. Introducing Cyber Attacks Faced By Different Departments Information Security Risk Management to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispense information on Department, Number Of Cyber Attacks, Type Of Cyber Attacks, using this template. Grab it now to reap its full benefits.
-
 Agenda For Implementing Security Awareness Training To Prevent Cyber Attacks
Agenda For Implementing Security Awareness Training To Prevent Cyber AttacksIntroducing Agenda For Implementing Security Awareness Training To Prevent Cyber Attacks to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Awareness Campaign, Cyber Security, Awareness Training, using this template. Grab it now to reap its full benefits.
-
 G33 Table Of Contents Implementing Security Awareness Training To Prevent Cyber Attacks
G33 Table Of Contents Implementing Security Awareness Training To Prevent Cyber AttacksIntroducing G33 Table Of Contents Implementing Security Awareness Training To Prevent Cyber Attacks to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Current Assessment, Organization, Cyber Security, using this template. Grab it now to reap its full benefits.
-
 Icons Slide For Implementing Security Awareness Training To Prevent Cyber Attacks
Icons Slide For Implementing Security Awareness Training To Prevent Cyber AttacksIntroducing our well researched set of slides titled Icons Slide For Implementing Security Awareness Training To Prevent Cyber Attacks. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Cyber Attacks Faced By Different Departments Information System Security And Risk Administration Plan
Cyber Attacks Faced By Different Departments Information System Security And Risk Administration PlanThis slide showcases information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks. Present the topic in a bit more detail with this Cyber Attacks Faced By Different Departments Information System Security And Risk Administration Plan. Use it as a tool for discussion and navigation on It Department, Marketing Department, Operations Department. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks In Powerpoint And Google Slides Cpb
Cyber Security Attacks In Powerpoint And Google Slides CpbPresenting our Cyber Security Attacks In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Cyber Security Attacks This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Dos And Donts Of Prevention From Ransomware Attack Preventing Data Breaches Through Cyber Security
Dos And Donts Of Prevention From Ransomware Attack Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase the Dos and donts of ransomware prevention attack. The slide covers information about updating the software, installing a firewall software, using reliable website and sources etc. Introducing Dos And Donts Of Prevention From Ransomware Attack Preventing Data Breaches Through Cyber Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Online Criminals, Foreign Government Officials, Malicious Insiders, using this template. Grab it now to reap its full benefits.
-
 General Outlook Of Ransomware Attack Preventing Data Breaches Through Cyber Security
General Outlook Of Ransomware Attack Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to outline an example of ransomware attack. The slide provides information about the working of ransomware attack work and how it can encrypts the victims data. Introducing General Outlook Of Ransomware Attack Preventing Data Breaches Through Cyber Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on System, Data, Employees, using this template. Grab it now to reap its full benefits.
-
 Outlook Of Social Engineering Attack Preventing Data Breaches Through Cyber Security
Outlook Of Social Engineering Attack Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase an example of social engineering attack. It also covers information about how the social engineering attack work and spread malware. Introducing Outlook Of Social Engineering Attack Preventing Data Breaches Through Cyber Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Social Engineering, Employees, using this template. Grab it now to reap its full benefits.
-
 Overview Of Business Email Compromise Attack Preventing Data Breaches Through Cyber Security
Overview Of Business Email Compromise Attack Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to delineate an example of business email compromise attack. Information covered in this slide is related to the working of this attack and how it can result in loss of company reputation. Increase audience engagement and knowledge by dispensing information using Overview Of Business Email Compromise Attack Preventing Data Breaches Through Cyber Security. This template helps you present information on four stages. You can also present information on Email, Services, Account using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Checklist To Mitigate Threats Of Attack
Cyber Security Checklist To Mitigate Threats Of AttackThe given slide provides the key activities to be done to alleviate the effects of cyber threats. It includes managing social media profiles, backing up the data, crosschecking privacy and security settings etc. Introducing our premium set of slides with Cyber Security Checklist To Mitigate Threats Of Attack. Ellicudate the seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Security Checklist, Mitigate Threats Attack. So download instantly and tailor it with your information.
-
 Network Security Practices To Prevent Cyber Attacks
Network Security Practices To Prevent Cyber AttacksThe given slide highlights some of the best practices to mitigate cyber attacks. Some of them are as backing up the data, training employees, preparing cyber incident response plan, securing sites and updating systems and software. Presenting our set of slides with Network Security Practices To Prevent Cyber Attacks. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Train Employees, Secure Sites.
-
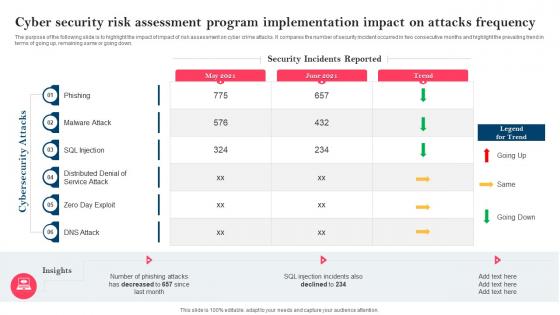 Strategy To Minimize Cyber Attacks Risks Cyber Security Risk Assessment Program Implementation
Strategy To Minimize Cyber Attacks Risks Cyber Security Risk Assessment Program ImplementationThe purpose of the following slide is to highlight the impact of impact of risk assessment on cyber crime attacks. It compares the number of security incident occurred in two consecutive months and highlight the prevailing trend in terms of going up, remaining same or going down. Present the topic in a bit more detail with this Strategy To Minimize Cyber Attacks Risks Cyber Security Risk Assessment Program Implementation. Use it as a tool for discussion and navigation on Cyber Security, Risk Assessment, Program Implementation, Impact On Attacks Frequency. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Adopt Cyber Security Data Policies Cyber Attack Risks Mitigation
Adopt Cyber Security Data Policies Cyber Attack Risks MitigationThe following slide highlights various cyber security policies to manage data control and breach. It includes elements such as network security, data, workstations, remote access etc. Introducing Adopt Cyber Security Data Policies Cyber Attack Risks Mitigation to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Network Security Policies, Data Security Policies, Workstation Policies, using this template. Grab it now to reap its full benefits.
-
 Impact Of Cyber Security Policies And Practices Cyber Attack Risks Mitigation
Impact Of Cyber Security Policies And Practices Cyber Attack Risks MitigationThe following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions, etc. Present the topic in a bit more detail with this Impact Of Cyber Security Policies And Practices Cyber Attack Risks Mitigation. Use it as a tool for discussion and navigation on Inadequate Security Guidelines, Inappropriate Privacy Policies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Multiple Strategic Cyber Security Approaches Cyber Attack Risks Mitigation
Multiple Strategic Cyber Security Approaches Cyber Attack Risks MitigationThe following slide depicts various cyber safety approaches to encrypt and back up key data to avoid information loss and improved accessibility. It includes elements such as data, application, infrastructure, network, devices, automation etc. Increase audience engagement and knowledge by dispensing information using Multiple Strategic Cyber Security Approaches Cyber Attack Risks Mitigation. This template helps you present information on one stage. You can also present information on Identities, Organization Policy, Threat Intelligence using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Organize Cyber Security Training For Employees Regularly Cyber Attack Risks Mitigation
Organize Cyber Security Training For Employees Regularly Cyber Attack Risks MitigationThe following slide depicts the staff cyber security training plan to educate them regarding technology threats and practices. It mainly includes elements such as topics to be covered, target audience, trainer name, mode, proposed date, timings etc. Introducing Organize Cyber Security Training For Employees Regularly Cyber Attack Risks Mitigation to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Document Management, Response Process, Social Media Policy, using this template. Grab it now to reap its full benefits.
-
 Passive Active And Offensive Cyber Security Strategies Cyber Attack Risks Mitigation
Passive Active And Offensive Cyber Security Strategies Cyber Attack Risks MitigationThe following slide showcases passive, active and offensive cyber safety techniques to ensure customer data safety. It includes elements such as inspecting vulnerabilities, penetration testing, deception technology, threat hunting etc. Increase audience engagement and knowledge by dispensing information using Passive Active And Offensive Cyber Security Strategies Cyber Attack Risks Mitigation. This template helps you present information on three stages. You can also present information on Passive Safety, Active Safety, Offensive Safety using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Proactive And Reactive Phases Of Cyber Security Cyber Attack Risks Mitigation
Proactive And Reactive Phases Of Cyber Security Cyber Attack Risks MitigationThe following slide depicts the stages of cyber security to avoid information loss and improved accessibility. It includes elements such as managing attack surface, optimizing process, stakeholder engagement etc. Introducing Proactive And Reactive Phases Of Cyber Security Cyber Attack Risks Mitigation to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Proactive, Managing Attack Surface, Optimize Process, Stakeholder Engagement, using this template. Grab it now to reap its full benefits.
-
 Stages Of Implementing Cyber Security Strategies Cyber Attack Risks Mitigation
Stages Of Implementing Cyber Security Strategies Cyber Attack Risks MitigationThe following slide highlights major stages of executing cyber security techniques to ensure effective implementation. It includes elements such as plan, analyze, upgrade, continuous improvement etc. Increase audience engagement and knowledge by dispensing information using Stages Of Implementing Cyber Security Strategies Cyber Attack Risks Mitigation. This template helps you present information on four stages. You can also present information on Plan Strategy, Implement Strategy, Analyse Strategy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Steps To Create Cyber Security Strategies Cyber Attack Risks Mitigation
Steps To Create Cyber Security Strategies Cyber Attack Risks MitigationThe following slide illustrates some steps to create and implement cybersecurity techniques. It includes elements such as determining threat type, selecting security framework, optimizing plan, implementing strategy etc. Introducing Steps To Create Cyber Security Strategies Cyber Attack Risks Mitigation to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Comprehend Threat Landscape, Evaluate Cybersecurity Maturity, Optimize Cybersecurity Program, using this template. Grab it now to reap its full benefits.
-
 Strategic Cyber Security Action Plan Cyber Attack Risks Mitigation
Strategic Cyber Security Action Plan Cyber Attack Risks MitigationThe following slide depicts action plan to minimize impact of cyber attacks. It includes elements such as understand, develop, deliver, assess organizational principles, evaluate alternatives, examine possible alternatives, execute actions etc. Increase audience engagement and knowledge by dispensing information using Strategic Cyber Security Action Plan Cyber Attack Risks Mitigation. This template helps you present information on three stages. You can also present information on Understand, Develop, Deliver, Organizational Principles using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Courses For Malware Cyber Security Attack Awareness
Courses For Malware Cyber Security Attack AwarenessThis slides shows various training programs of cyber security awareness to aware staff. The purpose of this slide is to reducing threat in future. The various course are Cofense online security, webroot security training, etc.Introducing our Courses For Malware Cyber Security Attack Awareness set of slides. The topics discussed in these slides are Awareness Training, Security Awareness Training, Security Awareness. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security Attacks Response Guid Cyber Security Incident Management Checklist During An Incident
Cyber Security Attacks Response Guid Cyber Security Incident Management Checklist During An IncidentThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management during the occurrence of the incident. Increase audience engagement and knowledge by dispensing information using Cyber Security Attacks Response Guid Cyber Security Incident Management Checklist During An Incident. This template helps you present information on one stages. You can also present information on Cyber Security, Incident Management, Checklist During An Incident using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Agenda For Cyber Security Attacks Response Plan Ppt Infographic Template Background Images
Agenda For Cyber Security Attacks Response Plan Ppt Infographic Template Background ImagesIntroducing Agenda For Cyber Security Attacks Response Plan Ppt Infographic Template Background Images to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Security, Attacks Response Plan, Security Incidents, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Attacks Response Comparative Analysis Of Cyber Security Incident Mitigation Software
Cyber Security Attacks Response Comparative Analysis Of Cyber Security Incident Mitigation SoftwareThis slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Present the topic in a bit more detail with this Cyber Security Attacks Response Comparative Analysis Of Cyber Security Incident Mitigation Software. Use it as a tool for discussion and navigation on Comparative Analysis, Cyber Security Incident, Mitigation Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Cyber Security Incident Management Team Roles And Responsibilities
Cyber Security Attacks Response Cyber Security Incident Management Team Roles And ResponsibilitiesPresent the topic in a bit more detail with this Cyber Security Attacks Response Cyber Security Incident Management Team Roles And Responsibilities. Use it as a tool for discussion and navigation on Cyber Security Incident, Management Team, Roles And Responsibilities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Gap Analysis Representing Current Situation Of Cybersecurity Incident
Cyber Security Attacks Response Gap Analysis Representing Current Situation Of Cybersecurity IncidentThis slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. Present the topic in a bit more detail with this Cyber Security Attacks Response Gap Analysis Representing Current Situation Of Cybersecurity Incident. Use it as a tool for discussion and navigation on Gap Analysis, Representing Current Situation, Cybersecurity Incident, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Impact Of Implementing Cyber Security Incident Management
Cyber Security Attacks Response Impact Of Implementing Cyber Security Incident ManagementThis slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Impact Of Implementing Cyber Security Incident Management. Dispense information and present a thorough explanation of Cyber Security Incident, Management On Organization, Software Vulnerabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Attacks Response Key Lessons Learned By Organization From Cyber Security Incident
Cyber Security Attacks Response Key Lessons Learned By Organization From Cyber Security IncidentIncrease audience engagement and knowledge by dispensing information using Cyber Security Attacks Response Key Lessons Learned By Organization From Cyber Security Incident. This template helps you present information on three stages. You can also present information on Key Lessons Learned By Organization, Cyber Security, Incident Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Attacks Response Plan Benefits Of Implementing Web Application Firewall
Cyber Security Attacks Response Plan Benefits Of Implementing Web Application FirewallThis slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Benefits Of Implementing Web Application Firewall. Use it as a tool for discussion and navigation on Fights Vulnerabilities, Application Firewall, Confidential Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Best Practices For Cybersecurity Incident Management
Cyber Security Attacks Response Plan Best Practices For Cybersecurity Incident ManagementThis slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Introducing Cyber Security Attacks Response Plan Best Practices For Cybersecurity Incident Management to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Incident Management Process, Incident Management Plan, Responsibilities, Team Members, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Attacks Response Plan Common Sources Of Precursors And Indicators
Cyber Security Attacks Response Plan Common Sources Of Precursors And IndicatorsThis slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Common Sources Of Precursors And Indicators. Use it as a tool for discussion and navigation on Precursors And Indicators, Suspicious Data, Identify Malicious Activity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Comparative Analysis Of Web Application Firewall Products
Cyber Security Attacks Response Plan Comparative Analysis Of Web Application Firewall ProductsThis slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Plan Comparative Analysis Of Web Application Firewall Products. Dispense information and present a thorough explanation of Comparative Analysis, Web Application, Firewall Products using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Attacks Response Plan Cyber Security Attacks Response Plan For Table Of Contents
Cyber Security Attacks Response Plan Cyber Security Attacks Response Plan For Table Of ContentsIncrease audience engagement and knowledge by dispensing information using Cyber Security Attacks Response Plan Cyber Security Attacks Response Plan For Table Of Contents. This template helps you present information on one stages. You can also present information on Cyber Security Attacks, Response Plan, Incident Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Attacks Response Plan Cyber Security Crisis Management Action Plan Timeline
Cyber Security Attacks Response Plan Cyber Security Crisis Management Action Plan TimelineThis slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Cyber Security Crisis Management Action Plan Timeline. Use it as a tool for discussion and navigation on Incident Response, Business Continuity, Review And Recovery, Management Action, Plan Timeline. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Cyber Security Event And Incident Flow Diagram
Cyber Security Attacks Response Plan Cyber Security Event And Incident Flow DiagramThis slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Plan Cyber Security Event And Incident Flow Diagram. Dispense information and present a thorough explanation of Cyber Security Event, Incident Flow Diagram, Business Operations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Attacks Response Plan Cyber Security Incident Handler Contact Information
Cyber Security Attacks Response Plan Cyber Security Incident Handler Contact InformationThis slide represents the contact information of the members responsible for handling and managing the cyber security incidents. It includes details related to name, organization, role and contact details of cyber security incident handler. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Cyber Security Incident Handler Contact Information. Use it as a tool for discussion and navigation on Cyber Security, Incident Handler, Contact Information, Forensic Expert. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Cyber Security Incident Response Plan Timeline
Cyber Security Attacks Response Plan Cyber Security Incident Response Plan TimelineThis slide represents the timeline representing the action plan to effectively respond to cyber security incidents experienced by the organization. It starts with preparation of cyber incident report and ends with return to normal flow. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Plan Cyber Security Incident Response Plan Timeline. Dispense information and present a thorough explanation of Cyber Security, Incident Response, Plan Timeline, Operations Resume using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Attacks Response Plan Cyber Security Incidents Follow Up Report
Cyber Security Attacks Response Plan Cyber Security Incidents Follow Up ReportThis slide represents the follow up report prepared by cyber security incident management team after successfully responding to cyber incidents experienced by the organization. It includes details related to date of incident, actions taken by responsible officer. Present the topic in a bit more detail with this Cyber Security Attacks Response Plan Cyber Security Incidents Follow Up Report. Use it as a tool for discussion and navigation on Cyber Security Incidents, Follow Up Report, Management Team. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Attacks Response Plan Cyber Security Threats Detection Techniques
Cyber Security Attacks Response Plan Cyber Security Threats Detection TechniquesThis slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response Plan Cyber Security Threats Detection Techniques. Dispense information and present a thorough explanation of Cyber Security Threats, Detection Techniques, Compromised Credentials using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Attacks Response Plan Five Phases Of Cybersecurity Incident Management
Cyber Security Attacks Response Plan Five Phases Of Cybersecurity Incident ManagementThis slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Introducing Cyber Security Attacks Response Plan Five Phases Of Cybersecurity Incident Management to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Plan And Prepare, Post Incident Activity, Assess And Design, Incident Management, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Attacks Response Plan Impact Of Cybersecurity Incidents On Organization
Cyber Security Attacks Response Plan Impact Of Cybersecurity Incidents On OrganizationThis slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Increase audience engagement and knowledge by dispensing information using Cyber Security Attacks Response Plan Impact Of Cybersecurity Incidents On Organization. This template helps you present information on six stages. You can also present information on Reputational Damage, Stolen Intellectual Property, Altered Business Practices, Operational Disruption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Attacks Response Plan Key Issues Faced By Organization Due To Cybersecurity Incidents
Cyber Security Attacks Response Plan Key Issues Faced By Organization Due To Cybersecurity IncidentsThis slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. Introducing Cyber Security Attacks Response Plan Key Issues Faced By Organization Due To Cybersecurity Incidents to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Faced By Organization Due, Cybersecurity Incidents, Confidential Information , using this template. Grab it now to reap its full benefits.
-
 Cyber Security Attacks Response Plan Key Parameters To Select Cyber Security Containment Strategy
Cyber Security Attacks Response Plan Key Parameters To Select Cyber Security Containment StrategyThis slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. Increase audience engagement and knowledge by dispensing information using Cyber Security Attacks Response Plan Key Parameters To Select Cyber Security Containment Strategy. This template helps you present information on five stages. You can also present information on Cyber Security, Containment Strategy, Incident Management Solutions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Attacks Response Plan Strategies To Analyze Cyber Security Incidents
Cyber Security Attacks Response Plan Strategies To Analyze Cyber Security IncidentsThis slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Introducing Cyber Security Attacks Response Plan Strategies To Analyze Cyber Security Incidents to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Profile Network And Systems, Understand Normal Behaviors, Perform Event Correlation, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Attacks Response Plan Various Cyber Security Incidents Detected By It Department
Cyber Security Attacks Response Plan Various Cyber Security Incidents Detected By It DepartmentThis slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Increase audience engagement and knowledge by dispensing information using Cyber Security Attacks Response Plan Various Cyber Security Incidents Detected By It Department. This template helps you present information on five stages. You can also present information on Insider Threat, Phishing Attack, Malware Attack, Password Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Attacks Response Plan Ways To Detect Cyber Security Incidents
Cyber Security Attacks Response Plan Ways To Detect Cyber Security IncidentsThis slide represents the activities through which cyber incident management team can effectively and efficiently detect cyber security incidents. It includes various ways of detecting cyber security incidents such as unusual behavior from privileged user accounts etc. Introducing Cyber Security Attacks Response Plan Ways To Detect Cyber Security Incidents to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Privileged User Accounts, Outbound Network Traffic, Changes In Configuration, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Attacks Response User Awareness Training Program To Prevent Cyber Security Incidents
Cyber Security Attacks Response User Awareness Training Program To Prevent Cyber Security IncidentsThis slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. Deliver an outstanding presentation on the topic using this Cyber Security Attacks Response User Awareness Training Program To Prevent Cyber Security Incidents. Dispense information and present a thorough explanation of User Awareness, Training Program, Prevent Cyber Security Incidents using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Incident Communication Strategy Cyber Security Attacks Response Plan
Cyber Security Incident Communication Strategy Cyber Security Attacks Response PlanThis slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders. Introducing Cyber Security Incident Communication Strategy Cyber Security Attacks Response Plan to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Senior Management, Communication Strategy, Stakeholder Needs, Suppliers, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Handling Checklist Cyber Security Attacks Response Plan
Cyber Security Incident Handling Checklist Cyber Security Attacks Response PlanThis slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post incident activity. Present the topic in a bit more detail with this Cyber Security Incident Handling Checklist Cyber Security Attacks Response Plan. Use it as a tool for discussion and navigation on Containment, Eradication And Recovery, Detection And Analysis, Handling Checklist Acquisition. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Incident Management Checklist After An Incident Cyber Security Attacks Response
Cyber Security Incident Management Checklist After An Incident Cyber Security Attacks ResponseThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management after the occurrence of the incident. Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Management Checklist After An Incident Cyber Security Attacks Response. This template helps you present information on one stages. You can also present information on Cyber Security, Incident Management, Checklist After An Incident using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incident Management Team Structure Cyber Security Attacks Response Plan
Cyber Security Incident Management Team Structure Cyber Security Attacks Response PlanThis slide represents the org chart of team which is responsible for minimizing and managing cyber security incidents. It includes details related to team structure of cyber security incident management team. Deliver an outstanding presentation on the topic using this Cyber Security Incident Management Team Structure Cyber Security Attacks Response Plan. Dispense information and present a thorough explanation of Cyber Security, Incident Management, Team Structure, Human Resources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





