Powerpoint Templates and Google slides for Cyber Analysis
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Security Analysis Powerpoint Ppt Template Bundles
Cyber Security Analysis Powerpoint Ppt Template BundlesDeliver a credible and compelling presentation by deploying this Cyber Security Analysis Powerpoint Ppt Template Bundles. Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The Fourteen slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Cyber Security Analysis Powerpoint Ppt Template Bundles PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.
-
 Eight stage infographic analysis profitability cyber security social media strategy
Eight stage infographic analysis profitability cyber security social media strategyIf you require a professional template with great design, then this Eight Stage Infographic Analysis Profitability Cyber Security Social Media Strategy is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using twelve slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Data Breach Trend Analysis With KPI Dashboard Implementing Cyber Risk Management Process
Data Breach Trend Analysis With KPI Dashboard Implementing Cyber Risk Management ProcessThe following slide depicts the data breach trends to minimize information leakage and patch affected system. It includes elements such as breach risk trend, breach by risk category, current and future goal analysis etc. Deliver an outstanding presentation on the topic using this Data Breach Trend Analysis With KPI Dashboard Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Current And Future Goal Analysis, Breach Risk Trend using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Trend Analysis With KPI Dashboard Cyber Risk Assessment
Data Breach Trend Analysis With KPI Dashboard Cyber Risk AssessmentThe following slide depicts the data breach trends to minimize information leakage and patch affected system. It includes elements such as breach risk trend, breach by risk category, current and future goal analysis etc. Present the topic in a bit more detail with this Data Breach Trend Analysis With KPI Dashboard Cyber Risk Assessment Use it as a tool for discussion and navigation on Breach Risk, Business Unit, Risk Category This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Trend Analysis With Kpi Dashboard Creating Cyber Security Awareness
Data Breach Trend Analysis With Kpi Dashboard Creating Cyber Security AwarenessThe following slide depicts the data breach trends to minimize information leakage and patch affected system. It includes elements such as breach risk trend, breach by risk category, current and future goal analysis etc. Deliver an outstanding presentation on the topic using this Data Breach Trend Analysis With Kpi Dashboard Creating Cyber Security Awareness Dispense information and present a thorough explanation of Systems And Passwords, Phishing Exercise, Penetration Test using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Trend Analysis With KPI Dashboard Implementing Strategies To Mitigate Cyber Security Threats
Data Breach Trend Analysis With KPI Dashboard Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the data breach trends to minimize information leakage and patch affected system. It includes elements such as breach risk trend, breach by risk category, current and future goal analysis etc. Present the topic in a bit more detail with this Data Breach Trend Analysis With KPI Dashboard Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Current And Future Goal Analysis, Breach Risk Trend This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Global Cyber Detection Technology Market Analysis
Global Cyber Detection Technology Market AnalysisThe purpose of this slide is to present a snapshot of the global regional cyber detection technology market, offering insights into market trends and key growth factors. Presenting our well structured Global Cyber Detection Technology Market Analysis. The topics discussed in this slide are Key Insights, Key Growth Factors, Market Size Dollar Billion. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Gap Analysis Representing Current Situation Of Cyber IT Security Awareness Training Cybersecurity SS
Gap Analysis Representing Current Situation Of Cyber IT Security Awareness Training Cybersecurity SSThis slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. Deliver an outstanding presentation on the topic using this Gap Analysis Representing Current Situation Of Cyber IT Security Awareness Training Cybersecurity SS. Dispense information and present a thorough explanation of Gap Analysis Representing, Current Situation Of Cyber Attacks, Employee Productivity Rates using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Threat Analysis With Data Encryption
Cyber Threat Analysis With Data EncryptionThe purpose of this slide is to highlight how cyber threat analysis with data encryption fortifies security. It offers proactive insights into potential threats, ensuring a robust defense, and safeguarding sensitive information in the evolving landscape of cyber threats. Introducing our Cyber Threat Analysis With Data Encryption set of slides. The topics discussed in these slides are Cybersecurity Threat, Budget Constraints, Inadequate Training And Awareness. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Risk Analysis Process In Cyber Security
Risk Analysis Process In Cyber SecurityThis slide outlines the risk analysis process for cyber security to effectively and efficiently protect their department assets. It includes key steps such as conduct risk assessment survey, identify risks, analyse risks, develop a risk management plan, implement risk management plan and monitor risks.Introducing our premium set of slides with Risk Analysis Process In Cyber Security. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Assessment Survey, Identify Risks, Analyze Risks. So download instantly and tailor it with your information.
-
 Comparative Tool Analysis Of Cyber Security
Comparative Tool Analysis Of Cyber SecurityThe following slide showcases comparative tool analysis of cyber security. It includes functionality, deployment, threat detection, integration, and cost. Presenting our set of slides with Comparative Tool Analysis Of Cyber Security. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Functionality, Deployment, Detection.
-
 Comparative Analysis Of Cyber Security Network Audit Tools
Comparative Analysis Of Cyber Security Network Audit ToolsThis slide covers a comparison of cyber audit tools and provides details about features that help to identify suitable software for organizations. It includes elements such as description, subscriptions, etc. Introducing our Comparative Analysis Of Cyber Security Network Audit Tools set of slides. The topics discussed in these slides are Vulnerability Assessment, Tamper Protection, Cloud Based. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Threats In Blockchain Comparative Analysis Of Multiple Blockchain Security Vendors BCT SS V
Cyber Threats In Blockchain Comparative Analysis Of Multiple Blockchain Security Vendors BCT SS VThe following slide showcases comparative analysis of blockchain cybersecurity vendors. It includes elements such as experience, services, technical capabilities, response time, costing, offering competitive pricing, reviews, 247 availability, etc. Deliver an outstanding presentation on the topic using this Cyber Threats In Blockchain Comparative Analysis Of Multiple Blockchain Security Vendors BCT SS V Dispense information and present a thorough explanation of Experience, Services, Technical Capabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Threats In Blockchain Comparative Analysis Of Various Types Of Blockchain Network BCT SS V
Cyber Threats In Blockchain Comparative Analysis Of Various Types Of Blockchain Network BCT SS VThe following slide depicts the comparative assessment of major types of blockchain network to analyze the level of security. It includes elements such as decentralization, accessibility, security, transparency, scalability, etc. Present the topic in a bit more detail with this Cyber Threats In Blockchain Comparative Analysis Of Various Types Of Blockchain Network BCT SS V Use it as a tool for discussion and navigation on Public Blockchain, Private Blockchain, Consortium Blockchain This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Threats In Blockchain Remediation Comparative Analysis Of Various Penetration Testing Tools BCT SS V
Cyber Threats In Blockchain Remediation Comparative Analysis Of Various Penetration Testing Tools BCT SS VThe following slide depicts comparative analysis of penetration tools to remediate cybersecurity vulnerabilities. It includes elements such as services, features, reviews, security audits, compliance reporting, website and network security, etc. Deliver an outstanding presentation on the topic using this Cyber Threats In Blockchain Remediation Comparative Analysis Of Various Penetration Testing Tools BCT SS V Dispense information and present a thorough explanation of Services, Features, Reviews using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Global Cyber Security Trend Analysis Implementing Cyber Risk Management Process
Global Cyber Security Trend Analysis Implementing Cyber Risk Management ProcessThe following slide depicts the key statistics about cyber security trends to project future performance. It mainly includes elements such as increase in ransomware attacks, average data breach costs, approximate number of businesses prone to cyber-attacks etc. Introducing Global Cyber Security Trend Analysis Implementing Cyber Risk Management Process to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Businesses Targeted, Ransomware Attack, Cyber Attacks, using this template. Grab it now to reap its full benefits.
-
 Classify Incident Report Template For Cyber Security Analysis
Classify Incident Report Template For Cyber Security AnalysisThis slide exhibits cyber report template categorization for ensuring quick and effective understanding of incident nature, impact and implication. It includes elements such as Michigan, sysnets security, techtargets and thycotics template. Presenting our set of slides with Classify Incident Report Template For Cyber Security Analysis. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Michigan Template, Sysnets Security Template, Thycotics Template.
-
 Global Cyber Security Trend Analysis Cyber Risk Assessment
Global Cyber Security Trend Analysis Cyber Risk AssessmentThe following slide depicts the key statistics about cyber security trends to project future performance. It mainly includes elements such as increase in ransomware attacks, average data breach costs, approximate number of businesses prone to cyber attacks etc. Deliver an outstanding presentation on the topic using this Global Cyber Security Trend Analysis Cyber Risk Assessment Dispense information and present a thorough explanation of Global Cyber Security, Trend Analysis using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Global Cyber Security Trend Analysis Creating Cyber Security Awareness
Global Cyber Security Trend Analysis Creating Cyber Security AwarenessThe following slide depicts the key statistics about cyber security trends to project future performance. It mainly includes elements such as increase in ransomware attacks, average data breach costs, approximate number of businesses prone to cyber-attacks etc. Introducing Global Cyber Security Trend Analysis Creating Cyber Security Awareness to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Parameters, Probability, Risk Score using this template. Grab it now to reap its full benefits.
-
 Comparative Tool Analysis Of Cyber Protection
Comparative Tool Analysis Of Cyber ProtectionThe following slide showcases comparative tool analysis of cyber security. It includes functionality, deployment, threat detection, integration, and cost Introducing our Comparative Tool Analysis Of Cyber Protection set of slides. The topics discussed in these slides are Tool Name, Functionality, Deployment. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Comparative Analysis Of Csirt And Soc Cyber Security
Comparative Analysis Of Csirt And Soc Cyber SecurityThis slide showcases difference between CSIRT and SOC cyber security. The main purpose of this template is assisting business in determining most suitable approach for cyber security. This I Introducing our premium set of slides with Comparative Analysis Of Csirt And Soc Cyber Security. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Through Investigation, Analysis And Improvement, Forensics Analysis. So download instantly and tailor it with your information.
-
 Global Cyber Security Trend Analysis Implementing Strategies To Mitigate Cyber Security Threats
Global Cyber Security Trend Analysis Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the key statistics about cyber security trends to project future performance. It mainly includes elements such as increase in ransomware attacks, average data breach costs, approximate number of businesses prone to cyber attacks etc. Increase audience engagement and knowledge by dispensing information using Global Cyber Security Trend Analysis Implementing Strategies To Mitigate Cyber Security Threats This template helps you present information on six stages. You can also present information on Attack, Data Breaches, Cyber Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Comparative Analysis Of Antivirus Software Useful In Cyber Monitoring
Comparative Analysis Of Antivirus Software Useful In Cyber MonitoringFollowing slide highlights cyber monitoring antivirus software comparative analysis to choose better option. It further covers tools, free trial, price, reviews and features such as offers VPN, trojan protection, firewall and email security, etc. Presenting our well structured Comparative Analysis Of Antivirus Software Useful In Cyber Monitoring The topics discussed in this slide are Trojan Protection, Email Security, Software Useful. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Comparative Analysis Of Cyber Network Monitoring Tools
Comparative Analysis Of Cyber Network Monitoring ToolsFollowing slide represents network security monitoring tools for comparative analysis to choose better option. It further covers tools, price, platforms and features such as offline analysis, triggering alerts on real time basis, block third party trackers, etc. Introducing our Comparative Analysis Of Cyber Network Monitoring Tools set of slides. The topics discussed in these slides are Threat Levels, Website Traffic, Real Time Analysis. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Comparative Analysis Of ATP Cyber Security Tools
Comparative Analysis Of ATP Cyber Security ToolsThis slide depicts the comparative analysis of ATP cyber security tools. Its aim is to use the tools to protect the system from advanced threats. This slide include Microsoft defender, ESET endpoint, Palo Alto network, Fortinet sandbox. Presenting our set of slides with name Comparative Analysis Of ATP Cyber Security Tools. This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Microsoft Defender, ESET Endpoint, Palo Alto Network, Fortinet Sandbox.
-
 Comparison Analysis Of SCADA Cyber Security Solutions
Comparison Analysis Of SCADA Cyber Security SolutionsThis slide represents comparison analysis of various solutions that assist IT companies to enhance their SCADA cyber security and data protection. It includes various solutions such as Indegy, clarity, Nozomi networks, and Dragos. Presenting our well structured Comparison Analysis Of SCADA Cyber Security Solutions The topics discussed in this slide are Anomaly Detection, Asset Discovery, Vulnerability Management. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Gap Analysis Process
Cyber Security Gap Analysis ProcessThis slide covers procedure for cyber security gap analysis such as establishing security goal, assembling skilled team, and gathering documentation to identify and address vulnerabilities and shortcomings in an organizations security measures to enhance overall resilience against cyber threats. Presenting our set of slides with name Cyber Security Gap Analysis Process. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Establish Security Goal, Assemble Skilled Team, Gather Necessary Documentation.
-
 Cyber Threat Intelligence Vendor Comparative Analysis
Cyber Threat Intelligence Vendor Comparative AnalysisThis slide showcases the cyber threat intelligence vendor comparative analysis. The purpose of this slide is to help the business make an informed purchase decision regarding vendor services. It includes comparison on the basis of description, pricing and ratings Introducing our Cyber Threat Intelligence Vendor Comparative Analysis set of slides. The topics discussed in these slides are Vendor, Description, Pricing This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security Controls Software Comparative Analysis
Cyber Security Controls Software Comparative AnalysisThis slide highlights the comparative analysis of cyber security control software to protect confidential data and protection from data breach. It includes various factors such as features, ratings, etc Introducing our Cyber Security Controls Software Comparative Analysis set of slides. The topics discussed in these slides are Secpod Sanernow, Intruder, Solar Winds Security Event Manager This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Comparative Analysis For Network Intrusion Protection Cyber Security Tools
Comparative Analysis For Network Intrusion Protection Cyber Security ToolsThis slide depicts the comparative evaluation of NIPS security tools. The purpose of this slide is to help the business make a well informed purchase decision. It includes comparison on the basis of the free trial period, features, ratings, etc. Introducing our premium set of slides with Comparative Analysis For Network Intrusion Protection Cyber Security Tools Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Distinctive Features, Free Trial, Tools So download instantly and tailor it with your information.
-
 Impact Analysis Of Cyber Security Threats In Automotive Industry
Impact Analysis Of Cyber Security Threats In Automotive IndustryThis slide highlights influence assessment cyber security risks in automobile industry. The purpose of this slide is to aid businesses in evaluating potential consequences of digital factors. It includes elements such as data privacy, supply chain disruption, etc. Introducing our premium set of slides with Impact Analysis Of Cyber Security Threats In Automotive Industry Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Privacy, Intellectual Property, Supply Chain Disruption So download instantly and tailor it with your information.
-
 Comparative Analysis Of Hids And Nids Cyber Security
Comparative Analysis Of Hids And Nids Cyber SecurityThis slide represents comparative analysis of HIDS and NIDS cyber security which assists to detect suspicious attack and about system administrator. It includes comparative analysis of HIDS and NIDS cyber security based on features such as management, detects large network attacks, etc Introducing our Comparative Analysis Of Hids And Nids Cyber Security set of slides. The topics discussed in these slides are Management, Analyse Encrypted Network Traffic, Protection Against Targeted Attacks . This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Comparative Analysis Of Cyber Security Gamification Platforms
Comparative Analysis Of Cyber Security Gamification PlatformsThe purpose of this slide is to showcase platforms that offer a variety of approaches to acquire cybersecurity skills, including walkthroughs, interactive learning, and exploratory tasks including platforms such as Hoxhunt, Hack The Box, etc. Presenting our well structured Comparative Analysis Of Cyber Security Gamification Platforms. The topics discussed in this slide are Goal Setting Or Tracking, Asynchronous Learning, Compliance Management. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Threat Intelligence Tools Comparative Analysis
Cyber Threat Intelligence Tools Comparative AnalysisThis slide showcases cyber threat intelligence tools which help in effective shield against data and allow proactively detect cyber threats. It includes elements such as Cisco umbrella, DeCYFIR, Echosec and GreyNoise. Presenting our well structured Cyber Threat Intelligence Tools Comparative Analysis. The topics discussed in this slide are Key Features, USP, Pricing. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Comparative Analysis Of SIEM Cyber Security Monitoring Tools
Comparative Analysis Of SIEM Cyber Security Monitoring ToolsThis slide showcases the comparative analysis of SIEM cyber security tools. Its objective is to detect threats and log analysis. This slide includes log analysis, LogPoint, ExaBeam infusion, ManageEngine and DataDog security. Presenting our well structured Comparative Analysis Of SIEM Cyber Security Monitoring Tools. The topics discussed in this slide are Datadog Security, Logpoint, Manageengine Log. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Comparative Analysis Of OT Cyber Security Solutions
Comparative Analysis Of OT Cyber Security SolutionsThis slide represents comparative analysis of various OT security tools assisting companies to enhance their data protection against multiple cyber risks. It includes various tools such as Nozomi networks, Claroty, mission secure, etc. Presenting our well structured Comparative Analysis Of OT Cyber Security Solutions The topics discussed in this slide are Network Visualization, Vulnerability Assessment, Risk MonitoringThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Analysis Of Cyber Security 4 0 And 3 0 And Industry
Analysis Of Cyber Security 4 0 And 3 0 And IndustryThis slide showcases the cyber security in industry. Its objective is to analyse comparative analysis of cyber security and industry. This slide includes industry, network control, industrial internet, ad hoc, cyber threats and technology. Introducing our Analysis Of Cyber Security 4 0 And 3 0 And Industry set of slides. The topics discussed in these slides are First Programmable Controller, Security Related Trend, Industrial Internet. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Comparative Analysis For Cyber Crises Management Tools
Comparative Analysis For Cyber Crises Management ToolsThe purpose of this slide is to assess and select the most effective solutions for mitigating and responding to cyber threats by using tools like CyberToolX, SecureGuard, SentinelOne, etc. Introducing our Comparative Analysis For Cyber Crises Management Tools set of slides. The topics discussed in these slides are Features, Ease Of Use, Integration, Cost. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Statistical Analysis Applications In Cyber Security Statistical Analysis Techniques
Statistical Analysis Applications In Cyber Security Statistical Analysis TechniquesThe purpose of this slide is to represent the uses of statistical analysis in cyber security. These include anomaly detection, intrusion detection, risk assessment, incident response, phishing detection and vulnerability assessment. Introducing Statistical Analysis Applications In Cyber Security Statistical Analysis Techniques to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Anomaly Detection, Intrusion Detection, Risk Assessment, Incident Response, using this template. Grab it now to reap its full benefits.
-
 Technical Analysis Of DDOS Attacks Against Ukrainian Websites String Of Cyber Attacks Against
Technical Analysis Of DDOS Attacks Against Ukrainian Websites String Of Cyber Attacks AgainstThis slide represents the technical analysis of ddos attacks against ukrainian websites by showing the internet traffic to the oschad bank website on 15 16 february 2022. Deliver an outstanding presentation on the topic using this Technical Analysis Of DDOS Attacks Against Ukrainian Websites String Of Cyber Attacks Against. Dispense information and present a thorough explanation of Customers, Accessing Banking, Websites using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
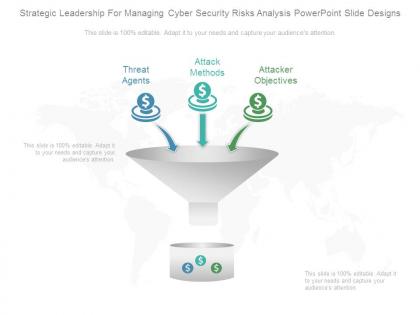 Strategic leadership for managing cyber security risks analysis powerpoint slide designs
Strategic leadership for managing cyber security risks analysis powerpoint slide designsPresenting strategic leadership for managing cyber security risks analysis powerpoint slide designs. This is a strategic leadership for managing cyber security risks analysis powerpoint slide designs. This is a three stage process. The stages in this process are threat agents, attack methods, attacker objectives.
-
 Cyber defense testing analysis ppt powerpoint guide
Cyber defense testing analysis ppt powerpoint guidePresenting cyber defense testing analysis ppt powerpoint guide. This is a cyber defense testing analysis ppt powerpoint guide. This is a five stage process. The stages in this process are test planning, vulnerabilities identification, defining targets, vulnerability test, penetration test.
-
 Cyber threat analysis sample diagram ppt presentation visual aids
Cyber threat analysis sample diagram ppt presentation visual aidsPresenting cyber threat analysis sample diagram ppt presentation visual aids. This is a cyber threat analysis sample diagram ppt presentation visual aids. This is a four stage process. The stages in this process are successful attack, system susceptibility, threat accessibility, threat capability.
-
 Ukraine and russia cyber warfare it technical analysis of ddos attacks against ukrainian websites
Ukraine and russia cyber warfare it technical analysis of ddos attacks against ukrainian websitesThis slide depicts the technical analysis of distributed denial of service attacks against Ukrainian websites on 15-16 February 2022, and the graph shows internet traffic to the private bank. Deliver an outstanding presentation on the topic using this Ukraine And Russia Cyber Warfare It Technical Analysis Of Ddos Attacks Against Ukrainian Websites. Dispense information and present a thorough explanation of Technical, Analysis, Websites using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Attacks On Ukraine Technical Analysis Of DDOS Attacks Against
Cyber Attacks On Ukraine Technical Analysis Of DDOS Attacks AgainstThis slide represents the technical analysis of DDoS attacks against Ukrainian websites by showing the internet traffic to the Orchid Bank website on 15 16 February 2022. Present the topic in a bit more detail with this Cyber Attacks On Ukraine Technical Analysis Of DDOS Attacks Against. Use it as a tool for discussion and navigation on Technical Analysis Of Ddos Attacks Against Ukrainian Websites. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Technical Analysis Of Ddos Attacks Against Ukrainian Cyber Attacks On Ukraine
Technical Analysis Of Ddos Attacks Against Ukrainian Cyber Attacks On UkraineThis slide depicts the technical analysis of distributed denial of service attacks against Ukrainian websites on 15 16 February 2022, and the graph shows internet traffic to the private bank. Present the topic in a bit more detail with this Technical Analysis Of Ddos Attacks Against Ukrainian Cyber Attacks On Ukraine. Use it as a tool for discussion and navigation on Technical Analysis Of Ddos Attacks Against Ukrainian Websites. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Key Performance Indicator Metrics Analysis
Cyber Security Key Performance Indicator Metrics AnalysisThe following slide highlights the cyber security key performance indicator metrics analysis illustrating operational health, compliance health, controls, project status, progress, trend, compliance investigation, training compliance, incident response process and vulnerability schedule. Presenting our well structured Cyber Security Key Performance Indicator Metrics Analysis. The topics discussed in this slide are Incident Response Process, Vulnerability Schedule, Training Compliance. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Conducting Cyber Security Gap Analysis Of Organization Developing Cyber Security Awareness Training
Conducting Cyber Security Gap Analysis Of Organization Developing Cyber Security Awareness TrainingThe purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. Present the topic in a bit more detail with this Conducting Cyber Security Gap Analysis Of Organization Developing Cyber Security Awareness Training. Use it as a tool for discussion and navigation on Conducting Cyber, Security Gap, Analysis Of Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Data Analysis With Reported Incident KPI
Cyber Security Data Analysis With Reported Incident KPIThis slide displays the chart which includes the year wise distribution of information breaches incidents involving personal information and other security information with a five year annual average. Introducing our Cyber Security Data Analysis With Reported Incident KPI set of slides. The topics discussed in these slides are Cyber Security Data Analysis, Reported Incident KPI. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security KPI Dashboard With Risk Analysis
Cyber Security KPI Dashboard With Risk AnalysisThis slide covers the multiple types of risks under the cyber security that could hinder the process and break the security. It also includes the critical risk events with the weighted index percentage for three months and the value of risks involved or occurred during these months. Introducing our Cyber Security KPI Dashboard With Risk Analysis set of slides. The topics discussed in these slides are Cyber Security, Dashboard, Risk Analysis. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Two Year Comparative Analysis Of Cyber Security Key Performance Indicators
Two Year Comparative Analysis Of Cyber Security Key Performance IndicatorsThis slide contains the information related to the cyber security kpis and the issues that are been occurred in this year as well as the previous year to compare how the company is working and what needs to be done to make it even better. Presenting our well structured Two Year Comparative Analysis Of Cyber Security Key Performance Indicators. The topics discussed in this slide are Comparative Analysis, Performance Indicators, Cyber Security. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Incident And Privacy Analysis With KPI Dashboard
Cyber Security Incident And Privacy Analysis With KPI DashboardThe following slide highlights some kpas of cyber security incidents to evaluate and monitor threats. It includes elements such as open incidents, warnings by severity, average response time, warnings pending for inspection etc. Introducing our Cyber Security Incident And Privacy Analysis With KPI Dashboard set of slides. The topics discussed in these slides are Cyber Security, Incident And Privacy Analysis, KPI Dashboard. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Conducting Cyber Security Gap Analysis Of Organization Contd Conducting Security Awareness
Conducting Cyber Security Gap Analysis Of Organization Contd Conducting Security AwarenessThe purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. Present the topic in a bit more detail with this Conducting Cyber Security Gap Analysis Of Organization Contd Conducting Security Awareness. Use it as a tool for discussion and navigation on Desired State, Reasons Identified, Priority. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Landscape Dashboard With Cyber Attacks Analysis
Risk Landscape Dashboard With Cyber Attacks AnalysisThis slide illustrates risk landscape dashboard with cyber attacks analysis which contains malware attack frequency, country wise attacks, top 10 attacks, etc. It can assist IT managers in analyzing top threats so that they can be dealt with proper efficiency. Introducing our Risk Landscape Dashboard With Cyber Attacks Analysis set of slides. The topics discussed in these slides are Risk Landscape Icon, Financial Threat. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Conducting Cyber Security Gap Analysis Of Organization Implementing Security Awareness Training
Conducting Cyber Security Gap Analysis Of Organization Implementing Security Awareness TrainingThe purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. Present the topic in a bit more detail with this Conducting Cyber Security Gap Analysis Of Organization Implementing Security Awareness Training. Use it as a tool for discussion and navigation on Desired State, Reasons Identified, Approaches To Be Deployed. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
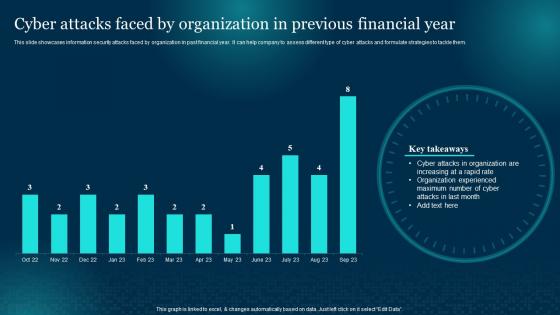 Cyber Attacks Faced By Organization Previous Cybersecurity Risk Analysis And Management Plan
Cyber Attacks Faced By Organization Previous Cybersecurity Risk Analysis And Management PlanThis slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type of cyber attacks and formulate strategies to tackle them. Deliver an outstanding presentation on the topic using this Cyber Attacks Faced By Organization Previous Cybersecurity Risk Analysis And Management Plan. Dispense information and present a thorough explanation of Organization, Financial Year, Experienced using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Conducting Cyber Security Gap Analysis Of Organization Preventing Data Breaches Through Cyber Security
Conducting Cyber Security Gap Analysis Of Organization Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. Deliver an outstanding presentation on the topic using this Conducting Cyber Security Gap Analysis Of Organization Preventing Data Breaches Through Cyber Security. Dispense information and present a thorough explanation of Current State, Email, Business using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Dashboard Analysis For Cyber Security In Healthcare Industry
Dashboard Analysis For Cyber Security In Healthcare IndustryThis slide depicts the dashboard used for analyzing the cyber security in the healthcare industry. The purpose of this template is to define different products offered in the healthcare industry and risk faced by them. It includes information related to the device, manufacturer, alerts and risks. Introducing our Dashboard Analysis For Cyber Security In Healthcare Industry set of slides. The topics discussed in these slides are Device Inventory, Manufacturer Distribution, Protocol Distribution. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Risk Impact And Likelihood Analysis Dashboard
Cyber Risk Impact And Likelihood Analysis DashboardThis slide defines the dashboard for analyzing the cyber risk impact and likelihood. It includes information related to the risk, rating and vulnerabilities. Introducing our Cyber Risk Impact And Likelihood Analysis Dashboard set of slides. The topics discussed in these slides are Risk Rating Breakdown, Risk Heat Map, Action Plan Breakdown. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber threat management workplace determine threat scenario analysis
Cyber threat management workplace determine threat scenario analysisThis slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Deliver an outstanding presentation on the topic using this Cyber Threat Management Workplace Determine Threat Scenario Analysis. Dispense information and present a thorough explanation of Threat Scenario, Threat Campaign, Exploitation, Command And Control, Actions And Objectives using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.




