Powerpoint Templates and Google slides for Controlling Information Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Implementation Of Information Key Access Security Control Models Strategy SS V
Implementation Of Information Key Access Security Control Models Strategy SS VThis slide represents key access security control models for organizations. It includes discretionary access control, mandatory access control, role based access control and attributes based access control, Present the topic in a bit more detail with this Implementation Of Information Key Access Security Control Models Strategy SS V. Use it as a tool for discussion and navigation on Discretionary Access, Mandatory Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Plan Control Measures
Information Security Plan Control MeasuresThis slide covers types of information security plan control parameters which provides safeguard and countermeasures for protecting information of organization. It involves preventive control, detective control and corrective control. Presenting our set of slides with Information Security Plan Control Measures. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Preventive Controls, Detective Controls, Corrective Controls.
-
 Steps To Place Information Security Control Plan
Steps To Place Information Security Control PlanThis slide highlights stages to place information security control measures for protecting defences and risks of business effectively. It involves deter, deny, detect, delay, correct and recover. Introducing our premium set of slides with Steps To Place Information Security Control Plan. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Deter, Correct, Recover. So download instantly and tailor it with your information.
-
 Information Security Management Controls To Enhance Data Integrity
Information Security Management Controls To Enhance Data IntegrityThis slide represents controls that help businesses to manage information security effectively from data breaches. It includes controls such as physical control, access control, procedural control, etc, Presenting our well structured Information Security Management Controls To Enhance Data Integrity. The topics discussed in this slide are Physical Control, Access Control, Procedural Control. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Information Security Control Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Information Security Control Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful PowerPoint icon represents a client onboarding checklist, designed to streamline the process and optimize resource utilization. With its eye-catching design and clear visual cues, this icon is perfect for presentations and documents related to client onboarding procedures and strategies.
-
 Information Security Control Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Information Security Control Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is designed to assist with client onboarding checklists, ensuring efficient resource utilization. With a sleek and minimalist design, this icon is perfect for presentations and documents related to client onboarding processes. It is a must-have for any business looking to streamline their onboarding procedures.
-
 Controls information security ppt powerpoint presentation file design ideas cpb
Controls information security ppt powerpoint presentation file design ideas cpbPresenting this set of slides with name - Controls Information Security Ppt Powerpoint Presentation File Design Ideas Cpb. This is an editable three stages graphic that deals with topics like Controls Information Security to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
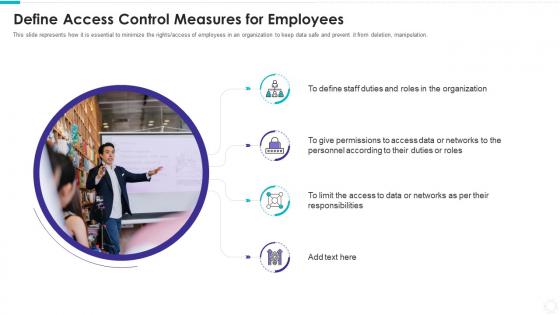 Electronic information security define access control measures employees
Electronic information security define access control measures employeesThis slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. Introducing Electronic Information Security Define Access Control Measures Employees to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Organization, Data Or Networks, Personnel According, Responsibilities, using this template. Grab it now to reap its full benefits.
-
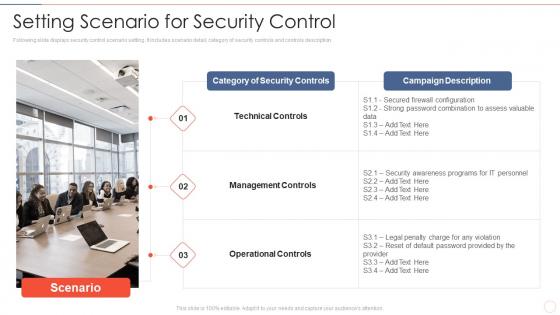 Setting scenario security control effective information security risk management process
Setting scenario security control effective information security risk management processFollowing slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description.Introducing Setting Scenario Security Control Effective Information Security Risk Management Process to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Management Controls, Operational Controls, Technical Controls, using this template. Grab it now to reap its full benefits.
-
 Information Security Define Access Control Measures For Employees
Information Security Define Access Control Measures For EmployeesThis slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. Introducing Information Security Define Access Control Measures For Employees to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Control, Measures, Employees, using this template. Grab it now to reap its full benefits.
-
 Information Security Program Cybersecurity Setting Scenario For Cybersecurity Control
Information Security Program Cybersecurity Setting Scenario For Cybersecurity ControlFollowing slide displays information about the companys cyber security control scenario setting. It includes scenario detail, category of security controls and controls description. Deliver an outstanding presentation on the topic using this Information Security Program Cybersecurity Setting Scenario For Cybersecurity Control. Dispense information and present a thorough explanation of Technical Controls, Management Controls, Operational Controls using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Program Key Security Controls To Be Addressed In The Program
Information Security Program Key Security Controls To Be Addressed In The ProgramPurpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Deliver an outstanding presentation on the topic using this Information Security Program Key Security Controls To Be Addressed In The Program. Dispense information and present a thorough explanation of Prevents Attacks, Limits Extent Of Attacks, Data Recovery using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Management Framework For Information Security Setting Scenario For Security Control
Risk Management Framework For Information Security Setting Scenario For Security ControlFollowing slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description. Present the topic in a bit more detail with this Risk Management Framework For Information Security Setting Scenario For Security Control. Use it as a tool for discussion and navigation on Category Security Controls, Controls Description, Operational Controls, Management Controls, Technical Controls. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Iso 27001 performance indicators to measure information security controls ppt slides
Iso 27001 performance indicators to measure information security controls ppt slidesFollowing slide illustrates performance indicators for measuring information security controls. It includes controls details, performance indicator formula, target and periodicity. Deliver an outstanding presentation on the topic using this ISO 27001 Performance Indicators To Measure Information Security Controls Ppt Slides. Dispense information and present a thorough explanation of Information Security Policy, Information Security Training, Asset Inventory using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Iso 27001 Performance Indicators To Measure Information Security Controls
Information Security And Iso 27001 Performance Indicators To Measure Information Security ControlsFollowing slide illustrates performance indicators for measuring information security controls. It includes controls details, performance indicator formula, target and periodicity. Present the topic in a bit more detail with this Information Security And Iso 27001 Performance Indicators To Measure Information Security Controls. Use it as a tool for discussion and navigation on Performance, Indicators, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Define Access Control Measures For Employees
Information Technology Security Define Access Control Measures For EmployeesThis slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. Increase audience engagement and knowledge by dispensing information using Information Technology Security Define Access Control Measures For Employees. This template helps you present information on four stages. You can also present information on Organization, Permissions, Responsibilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Access Control Methods Information Security Ppt Powerpoint Presentation Pictures Visual Aids Cpb
Access Control Methods Information Security Ppt Powerpoint Presentation Pictures Visual Aids CpbPresenting our Access Control Methods Information Security Ppt Powerpoint Presentation Pictures Visual Aids Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Access Control Methods Information Security. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cloud Security Checklist Access Control Cloud Information Security
Cloud Security Checklist Access Control Cloud Information SecurityThis slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management.Introducing Cloud Security Checklist Access Control Cloud Information Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Service Provider, Physical Access, Natural Disasters using this template. Grab it now to reap its full benefits.
-
 Cloud Security Threats End User Control Cloud Information Security
Cloud Security Threats End User Control Cloud Information SecurityThis slide represents the end user threat in cloud security and how an organization needs to control user access and be aware of potential threats.Introducing Cloud Security Threats End User Control Cloud Information Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Wisely Considering, Storage Location, Procedures Strategies using this template. Grab it now to reap its full benefits.
-
 Measures And Controls In Cloud Security Cloud Information Security
Measures And Controls In Cloud Security Cloud Information SecurityThis slide depicts the measures and controls taken in cloud security systems, namely preventive controls, deterrent controls, detective controls, and corrective controls.Increase audience engagement and knowledge by dispensing information using Measures And Controls In Cloud Security Cloud Information Security This template helps you present information on four stages. You can also present information on Implement Information, Restrict Data, Implement Advanced using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security Controls Ppt Powerpoint Presentation Model Professional Cpb
Information Security Controls Ppt Powerpoint Presentation Model Professional CpbPresenting Information Security Controls Ppt Powerpoint Presentation Model Professional Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Information Security Controls. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Performance Indicators To Measure Information Security Controls Iso 27001certification Process
Performance Indicators To Measure Information Security Controls Iso 27001certification ProcessFollowing slide illustrates performance indicators for measuring information security controls. It includes controls details, performance indicator formula, target and periodicity. Deliver an outstanding presentation on the topic using this Performance Indicators To Measure Information Security Controls Iso 27001certification Process. Dispense information and present a thorough explanation of Performance, Measure, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Obtaining ISO 27001 Certificate Performance Indicators To Measure Information Security Controls
Obtaining ISO 27001 Certificate Performance Indicators To Measure Information Security ControlsFollowing slide illustrates performance indicators for measuring information security controls. It includes controls details, performance indicator formula, target and periodicity. Deliver an outstanding presentation on the topic using this Obtaining ISO 27001 Certificate Performance Indicators To Measure Information Security Controls. Dispense information and present a thorough explanation of Control, Performance Indicator Formula, Target, Periodicity using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Technical Security Control Model With Isk Management Guide For Information Technology Systems
Technical Security Control Model With Isk Management Guide For Information Technology SystemsThe following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Deliver an outstanding presentation on the topic using this Technical Security Control Model With Isk Management Guide For Information Technology Systems. Dispense information and present a thorough explanation of Technical Security, Control Model, Supporting Technical, Control Function using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Automation In Information Technology Domain Security Controls That Can Be Automated
Security Automation In Information Technology Domain Security Controls That Can Be AutomatedThis slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. Present the topic in a bit more detail with this Security Automation In Information Technology Domain Security Controls That Can Be Automated. Use it as a tool for discussion and navigation on Information Security, Organization, Operations Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Application environment security controls application development security information accuracy
Application environment security controls application development security information accuracyPresenting this set of slides with name - Application Environment Security Controls Application Development Security Information Accuracy. This is an editable seven stages graphic that deals with topics like Application Environment Security Controls, Application Development Security, Information Accuracy to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Information security strategy activities controls monitor measure
Information security strategy activities controls monitor measurePresenting this set of slides with name - Information Security Strategy Activities Controls Monitor Measure. This is a three stage process. The stages in this process are Information Security Strategy, Information Security Plan, Information Protection Strategy.
-
 Information security control framework ppt powerpoint presentation show good cpb
Information security control framework ppt powerpoint presentation show good cpbPresenting this set of slides with name Information Security Control Framework Ppt Powerpoint Presentation Show Good Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Information Security Control Framework to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Access control models information security ppt powerpoint presentation file tips cpb
Access control models information security ppt powerpoint presentation file tips cpbPresenting our Access Control Models Information Security Ppt Powerpoint Presentation File Tips Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Access Control Models Information Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Types of information security controls to strengthen cybersecurity
Types of information security controls to strengthen cybersecurityIntroducing our premium set of slides with Types Of Information Security Controls To Strengthen Cybersecurity. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Preventative Controls, Detective Controls, Corrective Controls. So download instantly and tailor it with your information.
-
 Password based access control system for information security
Password based access control system for information securityPresenting our set of slides with Password Based Access Control System For Information Security. This exhibits information on one stage of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Password Based Access Control System For Information Security.
-
 Setting scenario control information security risk management program
Setting scenario control information security risk management programFollowing slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description. Present the topic in a bit more detail with this Setting Scenario Control Information Security Risk Management Program. Use it as a tool for discussion and navigation on Controls, Security, Management Controls. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information security dashboard with control compliance and overview
Information security dashboard with control compliance and overviewIntroducing our Information Security Dashboard With Control Compliance And Overview set of slides. The topics discussed in these slides are Information Security Dashboard With Control Compliance And Overview. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Quality control kpi dashboard slide for data confidentiality information security powerpoint template
Quality control kpi dashboard slide for data confidentiality information security powerpoint templateYou can use this Quality Control Kpi Dashboard Slide For Data Confidentiality Information Security Powerpoint Template to showcase the most crucial verticals of your organization or a project. This dashboard template comes with graphical representations to make the depiction of insights, data, reports, etc, very easy. It is useful in simplifying complex business concepts, allowing the viewers to make better decisions and judgments. This PowerPoint layout is specially designed for different department heads to display diverse sets of information on the topic and help make the viewers become better analysts. Therefore, this PowerPoint layout is not only resourceful, but it is also attention-grabbing and high-quality. Everything from the content and graphics used in this slide can be modified and adjusted as per your needs. It can also be reproduced in PNG, JPG, and PDF formats, which increases the user-friendliness of this layout.
-
 Remote access control steps set up advanced security management plan ppt information
Remote access control steps set up advanced security management plan ppt informationThis slide provides information about the sixth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Remote Access Control. Deliver an outstanding presentation on the topic using this Remote Access Control Steps Set Up Advanced Security Management Plan Ppt Information. Dispense information and present a thorough explanation of Types Remote Access Control, Control Security Status, Remote Access Control using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Aspects Of Information System Access Control Security Audit
Aspects Of Information System Access Control Security AuditThe following slide highlights the aspects of information system access control security audit illustrating key headings which incudes data access control, authentication privacy, user identity, user management, password management, network access control, and login Presenting our set of slides with name Aspects Of Information System Access Control Security Audit. This exhibits information on eight stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on User Management, Password Management, Authentication .



