Powerpoint Templates and Google slides for Computing Implementation
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 High Performance Computing Implementation Plan Powerpoint Presentation Slides
High Performance Computing Implementation Plan Powerpoint Presentation SlidesEnthrall your audience with this High Performance Computing Implementation Plan Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising fifty three slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Strategies To Implement Cloud Computing Infrastructure Powerpoint Presentation Slides
Strategies To Implement Cloud Computing Infrastructure Powerpoint Presentation SlidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Strategies To Implement Cloud Computing Infrastructure Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought provoking. All the fifty six slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Marketing Strategies And Its Implementation In Computer Industry Powerpoint Ppt Template Bundles BP MM
Marketing Strategies And Its Implementation In Computer Industry Powerpoint Ppt Template Bundles BP MMDeliver a lucid presentation by utilizing this Marketing Strategies And Its Implementation In Computer Industry Powerpoint Ppt Template Bundles BP MM. Use it to present an overview of the topic with the right visuals, themes, shapes, and graphics. This is an expertly designed complete deck that reinforces positive thoughts and actions. Use it to provide visual cues to your audience and help them make informed decisions. A wide variety of discussion topics can be covered with this creative bundle such as Promotional Strategies, Sales Strategy, Importance Of Marketing, Pricing Strategy. All the eleven slides are available for immediate download and use. They can be edited and modified to add a personal touch to the presentation. This helps in creating a unique presentation every time. Not only that, with a host of editable features, this presentation can be used by any industry or business vertical depending on their needs and requirements. The compatibility with Google Slides is another feature to look out for in the PPT slideshow.
-
 Various Use Cases Of Implementing IoT Enabled Edge Computing Comprehensive Guide For IoT Edge IOT SS
Various Use Cases Of Implementing IoT Enabled Edge Computing Comprehensive Guide For IoT Edge IOT SSFollowing slide exhibits various use cases of deploying IoT edge computing technology to improve business efficiency and decision making. It includes pointers such as autonomous vehicles, security solutions, etc. Introducing Various Use Cases Of Implementing IoT Enabled Edge Computing Comprehensive Guide For IoT Edge IOT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Advanced Surveillance, Emergency Situations, Provide Statistical Actions, using this template. Grab it now to reap its full benefits.
-
 Various use cases of implementing applications and role of IOT edge computing IoT SS V
Various use cases of implementing applications and role of IOT edge computing IoT SS VFollowing slide exhibits various use cases of deploying IoT edge computing technology to improve business efficiency and decision making. It includes pointers such as autonomous vehicles, security solutions, etc. Deliver an outstanding presentation on the topic using this Various use cases of implementing applications and role of IOT edge computing IoT SS V. Dispense information and present a thorough explanation of Autonomous Vehicles, Security Solutions, Data Aggregation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Losses To Firm Before High Performance Computing Implementation
Losses To Firm Before High Performance Computing ImplementationThe purpose of this slide is to highlight the statistics related to losses to firms before high-performance computing such as security breaches, network outages, hardware failure, etc. Present the topic in a bit more detail with this Losses To Firm Before High Performance Computing Implementation. Use it as a tool for discussion and navigation on High Performance Computing, Security Breaches, Network Outages, Hardware Failure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Green Computing Technology Implementation Statistics
Green Computing Technology Implementation StatisticsThis slide represents application of green computing technology for sustainable future which assists to reduce waste. Introducing our Green Computing Technology Implementation Statistics set of slides. The topics discussed in these slides are Green Computing Technolog, Implementation Statistics This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
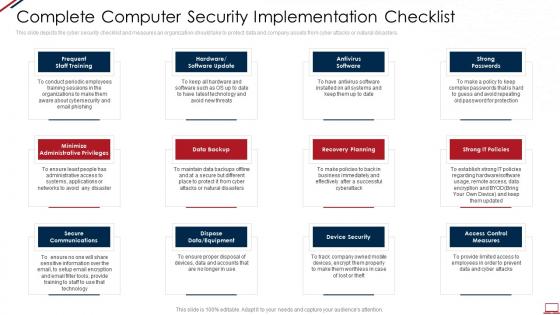 Computer system security complete computer security implementation checklist
Computer system security complete computer security implementation checklistThis slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Increase audience engagement and knowledge by dispensing information using Computer System Security Complete Computer Security Implementation Checklist. This template helps you present information on twelve stages. You can also present information on Data Backup, Secure Communications, Recovery Planning, Strong Passwords, Device Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Computer system security impact on organization after implementing computer security strategy and training
Computer system security impact on organization after implementing computer security strategy and trainingThis slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Increase audience engagement and knowledge by dispensing information using Computer System Security Impact On Organization After Implementing Computer Security Strategy And Training. This template helps you present information on five stages. You can also present information on Phishing, Network Intrusion, Inadvertent Disclosure, Stolen Or Lost Devises Or Records, System Misconfiguration using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Computer system security implementation of strong password policy
Computer system security implementation of strong password policyThis slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Introducing Computer System Security Implementation Of Strong Password Policy to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Implementation Of Strong Password Policy, using this template. Grab it now to reap its full benefits.
-
 Computer system security timeline for the implementation of computer security
Computer system security timeline for the implementation of computer securityThis slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Present the topic in a bit more detail with this Computer System Security Timeline For The Implementation Of Computer Security. Use it as a tool for discussion and navigation on Security, Risk Assessments, Perform. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Market Budget For Implementing Confidential Computing Architecture
Confidential Computing Market Budget For Implementing Confidential Computing ArchitectureThis slide describes the implementation cost of confidential computing, including required tools, hardware and software costs, and other expenditures. The purpose of this slide is to showcase the estimated cost, actual cost and variance. Deliver an outstanding presentation on the topic using this Confidential Computing Market Budget For Implementing Confidential Computing Architecture. Dispense information and present a thorough explanation of Implementing, Confidential, Architecture using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Market Checklist To Implement Confidential Computing Architecture
Confidential Computing Market Checklist To Implement Confidential Computing ArchitectureThis slide depicts the checklist to implement confidential computing architecture in a cloud environment. The purpose of this slide is to showcase the various steps to be taken to deploy confidential computing, including its status and the responsible person. Deliver an outstanding presentation on the topic using this Confidential Computing Market Checklist To Implement Confidential Computing Architecture. Dispense information and present a thorough explanation of Confidential, Computing, Architecture using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Market Confidential Computing Architecture Implementation Timeline
Confidential Computing Market Confidential Computing Architecture Implementation TimelineThis slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Introducing Confidential Computing Market Confidential Computing Architecture Implementation Timeline to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Architecture, Implementation, Timeline, using this template. Grab it now to reap its full benefits.
-
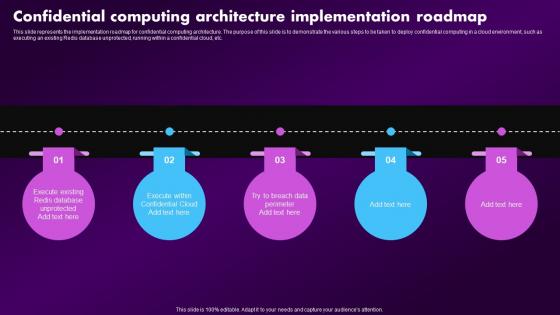 F1602 Confidential Computing Architecture Implementation Roadmap Confidential Computing Market
F1602 Confidential Computing Architecture Implementation Roadmap Confidential Computing MarketThis slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Increase audience engagement and knowledge by dispensing information using F1602 Confidential Computing Architecture Implementation Roadmap Confidential Computing Market. This template helps you present information on five stages. You can also present information on Architecture, Implementation, Roadmap using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
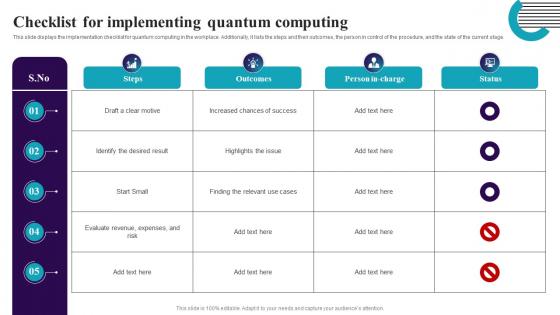 Checklist For Implementing Quantum Computing Quantum Computing It
Checklist For Implementing Quantum Computing Quantum Computing ItThis slide displays the implementation checklist for quantum computing in the workplace. Additionally, it lists the steps and their outcomes, the person in control of the procedure, and the state of the current stage. Present the topic in a bit more detail with this Checklist For Implementing Quantum Computing Quantum Computing It. Use it as a tool for discussion and navigation on Implementing, Quantum Computing, Additionally. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Iot Blockchain Image Implementing In Computer Operators
Iot Blockchain Image Implementing In Computer OperatorsPresenting our set of slides with Iot Blockchain Image Implementing In Computer Operators. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Iot Blockchain, Computer Operators.
-
 Confidential Cloud Computing Confidential Computing Architecture Implementation Roadmap
Confidential Cloud Computing Confidential Computing Architecture Implementation RoadmapThis slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Increase audience engagement and knowledge by dispensing information using Confidential Cloud Computing Confidential Computing Architecture Implementation Roadmap. This template helps you present information on five stages. You can also present information on Architecture, Implementation, Roadmap using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Architecture Implementation Roadmap Confidential Computing Hardware
Confidential Computing Architecture Implementation Roadmap Confidential Computing HardwareThis slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Introducing Confidential Computing Architecture Implementation Roadmap Confidential Computing Hardware to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Implementation Roadmap, Confidential Computing Architecture, Demonstrate, Deploy Confidential Computing, Cloud Environment, Existing Redis Database Unprotected, using this template. Grab it now to reap its full benefits.
-
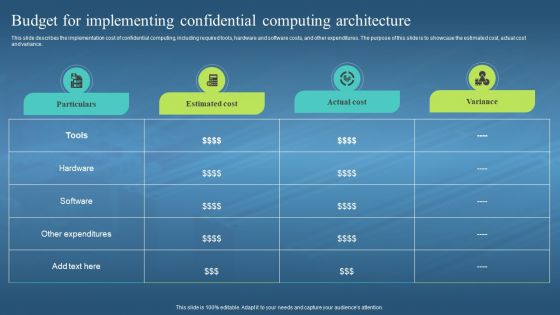 Confidential Computing Hardware Budget For Implementing Confidential Computing
Confidential Computing Hardware Budget For Implementing Confidential ComputingThis slide describes the implementation cost of confidential computing, including required tools, hardware and software costs, and other expenditures. The purpose of this slide is to showcase the estimated cost, actual cost and variance. Present the topic in a bit more detail with this Confidential Computing Hardware Budget For Implementing Confidential Computing. Use it as a tool for discussion and navigation on Cost Of Confidential Computing, Hardware And Software Costs, Estimated Cost, Actual Cost And Variance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Computing Hardware Checklist To Implement Confidential Computing
Confidential Computing Hardware Checklist To Implement Confidential ComputingThis slide depicts the checklist to implement confidential computing architecture in a cloud environment. The purpose of this slide is to showcase the various steps to be taken to deploy confidential computing, including its status and the responsible person. Present the topic in a bit more detail with this Confidential Computing Hardware Checklist To Implement Confidential Computing. Use it as a tool for discussion and navigation on Execute Within Confidential Cloud, Confidential Computing Architecture, Cloud Environment. Deploy Confidential Computing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
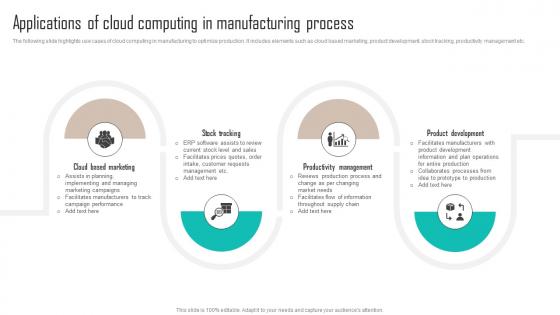 Applications Of Cloud Computing In Manufacturing Process Implementing Latest Manufacturing Strategy SS V
Applications Of Cloud Computing In Manufacturing Process Implementing Latest Manufacturing Strategy SS VThe following slide highlights use cases of cloud computing in manufacturing to optimize production. It includes elements such as cloud based marketing, product development, stock tracking, productivity management etc. Increase audience engagement and knowledge by dispensing information using Applications Of Cloud Computing In Manufacturing Process Implementing Latest Manufacturing Strategy SS V. This template helps you present information on four stages. You can also present information on Cloud Based Marketing, Stock Tracking, Product Development using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Implementing Cloud Computing In Manufacturing Process Implementing Latest Manufacturing Strategy SS V
Implementing Cloud Computing In Manufacturing Process Implementing Latest Manufacturing Strategy SS VThe following slide showcases cloud computing implementation process to boost collaboration and scalability. It includes elements such as design, product, maintenance, inventory, cloud based storage etc. Present the topic in a bit more detail with this Implementing Cloud Computing In Manufacturing Process Implementing Latest Manufacturing Strategy SS V. Use it as a tool for discussion and navigation on Design, Monitoring, Maintenance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview And Key Benefits Of Cloud Computing Implementing Latest Manufacturing Strategy SS V
Overview And Key Benefits Of Cloud Computing Implementing Latest Manufacturing Strategy SS VThe following slide represents brief introduction of how cloud computing assist in optimizing manufacturing process. It includes elements such as flexibility, production quality, shared accounts, load sharing etc. Increase audience engagement and knowledge by dispensing information using Overview And Key Benefits Of Cloud Computing Implementing Latest Manufacturing Strategy SS V. This template helps you present information on four stages. You can also present information on Flexibility, Production Quality, Load Sharing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Consortium Budget For Implementing Confidential Computing Architecture
Confidential Computing Consortium Budget For Implementing Confidential Computing ArchitectureThis slide describes the implementation cost of confidential computing, including required tools, hardware and software costs, and other expenditures. The purpose of this slide is to showcase the estimated cost, actual cost and variance. Deliver an outstanding presentation on the topic using this Confidential Computing Consortium Budget For Implementing Confidential Computing Architecture. Dispense information and present a thorough explanation of Budget For Implementing Confidential, Computing Architecture, Hardware And Software Costs using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Consortium Checklist To Implement Confidential Computing Architecture
Confidential Computing Consortium Checklist To Implement Confidential Computing ArchitectureThis slide depicts the checklist to implement confidential computing architecture in a cloud environment. The purpose of this slide is to showcase the various steps to be taken to deploy confidential computing, including its status and the responsible person. Deliver an outstanding presentation on the topic using this Confidential Computing Consortium Checklist To Implement Confidential Computing Architecture. Dispense information and present a thorough explanation of Cloud Environment, Confidential Computing, Execute Within Confidential Cloud, Redis Database Unprotected using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 K88 Confidential Computing Architecture Implementation Roadmap Confidential Computing Consortium
K88 Confidential Computing Architecture Implementation Roadmap Confidential Computing ConsortiumThis slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Introducing K88 Confidential Computing Architecture Implementation Roadmap Confidential Computing Consortium to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Execute Within Confidential Cloud, Execute Existing Redis, Database Unprotected, Breach Data Perimeter, using this template. Grab it now to reap its full benefits.
-
 K89 Confidential Computing Architecture Implementation Timeline Confidential Computing Consortium
K89 Confidential Computing Architecture Implementation Timeline Confidential Computing ConsortiumThis slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Increase audience engagement and knowledge by dispensing information using K89 Confidential Computing Architecture Implementation Timeline Confidential Computing Consortium. This template helps you present information on six stages. You can also present information on Confidential Computing, Architecture Implementation Timeline, Redis Database Unprotected using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing Hardware Confidential Computing Architecture Implementation Timeline
Confidential Computing Hardware Confidential Computing Architecture Implementation TimelineThis slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Increase audience engagement and knowledge by dispensing information using Confidential Computing Hardware Confidential Computing Architecture Implementation Timeline. This template helps you present information on six stages. You can also present information on Implementation Timeline, Confidential Computing Architecture, Deploy Confidential Computing, Cloud Environment, Existing Redis Database Unprotected using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
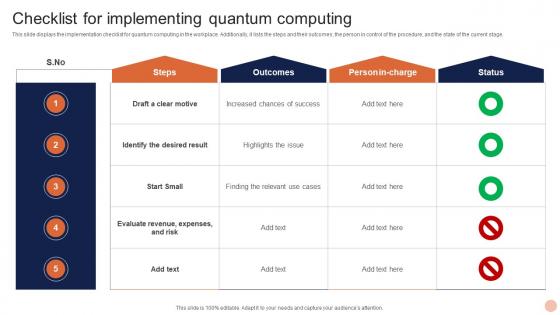 Advanced Technologies Checklist For Implementing Quantum Computing
Advanced Technologies Checklist For Implementing Quantum ComputingThis slide displays the implementation checklist for quantum computing in the workplace. Additionally, it lists the steps and their outcomes, the person in control of the procedure, and the state of the current stage. Present the topic in a bit more detail with this Advanced Technologies Checklist For Implementing Quantum Computing. Use it as a tool for discussion and navigation on Steps, Outcomes, Status. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Yearly Milestones For Successful Growth Computer Repair And Maintenance BP SS
Implementing Yearly Milestones For Successful Growth Computer Repair And Maintenance BP SSThe purpose of this slide is to facilitate managers to convey project progress updates to stakeholders and get their approvals. The slide portrays key milestones of the computer shop to be achieved in the year 1, year 3, and years 5 onwards. Introducing Implementing Yearly Milestones For Successful Growth Computer Repair And Maintenance BP SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Establish Relationships, Develop An Effective, using this template. Grab it now to reap its full benefits.
-
 Budget For Implementing Architecture Confidential Computing System Technology
Budget For Implementing Architecture Confidential Computing System TechnologyThis slide describes the implementation cost of confidential computing, including required tools, hardware and software costs, and other expenditures. The purpose of this slide is to showcase the estimated cost, actual cost and variance. Deliver an outstanding presentation on the topic using this Budget For Implementing Architecture Confidential Computing System Technology. Dispense information and present a thorough explanation of Implementing, Confidential, Architecture using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Implement Architecture Confidential Computing System Technology
Checklist To Implement Architecture Confidential Computing System TechnologyThis slide depicts the checklist to implement confidential computing architecture in a cloud environment. The purpose of this slide is to showcase the various steps to be taken to deploy confidential computing, including its status and the responsible person. Deliver an outstanding presentation on the topic using this Checklist To Implement Architecture Confidential Computing System Technology. Dispense information and present a thorough explanation of Confidential, Computing, Architecture using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing Architecture Implementation Confidential Computing System Technology
Confidential Computing Architecture Implementation Confidential Computing System TechnologyThis slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Introducing Confidential Computing Architecture Implementation Confidential Computing System Technology to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Architecture, Implementation, Timeline, using this template. Grab it now to reap its full benefits.
-
 Confidential Implementation Roadmap Confidential Computing System Technology
Confidential Implementation Roadmap Confidential Computing System TechnologyThis slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Increase audience engagement and knowledge by dispensing information using Confidential Implementation Roadmap Confidential Computing System Technology. This template helps you present information on five stages. You can also present information on Architecture, Implementation, Roadmap using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Edge Computing Technology Edge AI Technology Implementation Tool Stack AI SS
Edge Computing Technology Edge AI Technology Implementation Tool Stack AI SSThis slide showcases edge data strategy implementation tool stack, which helps developers of this technology to further foresee their deployment techniques. It provides details about customization, design, software, etc. Increase audience engagement and knowledge by dispensing information using Edge Computing Technology Edge AI Technology Implementation Tool Stack AI SS. This template helps you present information on five stages. You can also present information on Custom Design Services, Modular Hardware Platforms, AI Technology Implementation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Emerging Technologies Checklist For Implementing Quantum Computing
Emerging Technologies Checklist For Implementing Quantum ComputingThis slide displays the implementation checklist for quantum computing in the workplace. Additionally, it lists the steps and their outcomes, the person in control of the procedure, and the state of the current stage. Present the topic in a bit more detail with this Emerging Technologies Checklist For Implementing Quantum Computing. Use it as a tool for discussion and navigation on Draft A Clear Motive, Start Small. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Computer Repair Shop Business Plan Implementing Yearly Milestones For Successful Growth BP SS
Computer Repair Shop Business Plan Implementing Yearly Milestones For Successful Growth BP SSThe purpose of this slide is to facilitate managers to convey project progress updates to stakeholders and get their approvals. The slide portrays key milestones of the computer shop to be achieved in the year 1, year 3, and years 5 onwards. Introducing Computer Repair Shop Business Plan Implementing Yearly Milestones For Successful Growth BP SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Implementing, Successful, Growth, using this template. Grab it now to reap its full benefits.
-
 Green Cloud Computing V2 Checklist To Implement Green Cloud Computing
Green Cloud Computing V2 Checklist To Implement Green Cloud ComputingThis slide describes the checklist to implementing green cloud computing in a company. The purpose of this slide is to showcase the different strategies to implement green IT, including knowing when to use the cloud, offsetting carbon emissions, green cloud architecture, and choosing the right cloud service. Deliver an outstanding presentation on the topic using this Green Cloud Computing V2 Checklist To Implement Green Cloud Computing. Dispense information and present a thorough explanation of Green Cloud Architecture, Offsetting Carbon Emissions, Green Cloud Computing, Environmental Goals And Commitments using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Green Cloud Computing V2 Roadmap To Implement Green Cloud Computing
Green Cloud Computing V2 Roadmap To Implement Green Cloud ComputingThis slide outlines the roadmap to implement green cloud computing in the organization. The purpose of this slide is to showcase the various steps organizations should take while deploying green cloud computing, including implementing energy-efficient building systems, installing power-efficient lighting systems, etc. Introducing Green Cloud Computing V2 Roadmap To Implement Green Cloud Computing to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Green Cloud Computing, Energy Efficient Building Systems, Efficient Lighting Systems, using this template. Grab it now to reap its full benefits.
-
 Green Cloud Computing V2 Timeline To Implement Green Cloud Computing
Green Cloud Computing V2 Timeline To Implement Green Cloud ComputingThis slide outlines the timeline to implement green cloud computing in an organization. The purpose of this slide is to showcase the steps to be taken by businesses to implement green cloud computing, including selecting a carbon-aware provider, optimizing the cloud environment, ensuring solid carbon measurement and reporting plans, etc. Introducing Green Cloud Computing V2 Timeline To Implement Green Cloud Computing to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Optimize Cloud Environment, Ensure Solid Carbon Measurement, Reporting Plans, Green Cloud Computing, using this template. Grab it now to reap its full benefits.
-
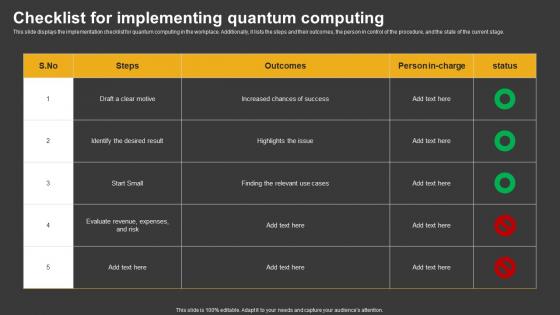 Trending Technologies Checklist For Implementing Quantum Computing
Trending Technologies Checklist For Implementing Quantum ComputingThis slide displays the implementation checklist for quantum computing in the workplace. Additionally, it lists the steps and their outcomes, the person in control of the procedure, and the state of the current stage. Present the topic in a bit more detail with this Trending Technologies Checklist For Implementing Quantum Computing. Use it as a tool for discussion and navigation on Steps, Outcomes, Person In Charge. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Before Vs After Implementing Serverless Computing V2 Ppt Ideas Example
Before Vs After Implementing Serverless Computing V2 Ppt Ideas ExampleThis slide compares the business scenario after deploying serverless applications. The purpose of this slide is to represent before and after situation based on several parameters. The factors used to do the comparison are cost, scalability, developer productivity, etc. Deliver an outstanding presentation on the topic using this Before Vs After Implementing Serverless Computing V2 Ppt Ideas Example. Dispense information and present a thorough explanation of Serverless Computing, Developer Productivity, Several Parameters, Business Scenario using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Optimal Scenarios For Serverless Computing V2 Implementation
Optimal Scenarios For Serverless Computing V2 ImplementationThis slide outlines the various scenarios which can help in deciding if serverless computing is a right choice or not. These factors are infrequent or unpredictable workloads, event-driven architecture, microservices, rapid prototyping and cost savings. Introducing Optimal Scenarios For Serverless Computing V2 Implementation to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Infrequent Or Unpredictable Workloads, Serverless Computing Implementation, Rapid Prototyping, Event Driven Architecture, using this template. Grab it now to reap its full benefits.
-
 Serverless Computing V2 Serverless Application Patterns For Effective Implementation
Serverless Computing V2 Serverless Application Patterns For Effective ImplementationThis slide demonstrates the various patterns of serverless applications. The purpose of this slide is to highlight their importance to meet the business requirements. These are serverless functions, serverless Kubernetes, serverless workflows, etc. Introducing Serverless Computing V2 Serverless Application Patterns For Effective Implementation to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Serverless Workflows, Serverless Application Environments, Serverless Kubernetes, Serverless Functions, using this template. Grab it now to reap its full benefits.
-
 Computer Accessories Business Plan Implementing Yearly Milestones For Successful Growth BP SS
Computer Accessories Business Plan Implementing Yearly Milestones For Successful Growth BP SSThe purpose of this slide is to facilitate managers to convey project progress updates to stakeholders and get their approvals. The slide portrays key milestones of the computer shop to be achieved in the year 1, year 3, and years 5 onwards. Increase audience engagement and knowledge by dispensing information using Computer Accessories Business Plan Implementing Yearly Milestones For Successful Growth BP SS. This template helps you present information on three stages. You can also present information on Generate Excitement, Marketing Efforts, Technicians Or Salespeople using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Implementing Yearly Milestones For Computer Software Business Plan BP SS
Implementing Yearly Milestones For Computer Software Business Plan BP SSThe purpose of this slide is to facilitate managers to convey project progress updates to stakeholders and get their approvals. The slide portrays key milestones of the computer shop to be achieved in the year 1, year 3, and years 5 onwards. Introducing Implementing Yearly Milestones For Computer Software Business Plan BP SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Implementing, Successful, Growth, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing V2 Architecture Implementation Roadmap
Confidential Computing V2 Architecture Implementation RoadmapThis slide represents the implementation roadmap for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Increase audience engagement and knowledge by dispensing information using Confidential Computing V2 Architecture Implementation Roadmap. This template helps you present information on five stages. You can also present information on Execute Within Confidential Cloud, Redis Database Unprotected, Confidential Computing Architecture using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Confidential Computing V2 Architecture Implementation Timeline
Confidential Computing V2 Architecture Implementation TimelineThis slide outlines the implementation timeline for confidential computing architecture. The purpose of this slide is to demonstrate the various steps to be taken to deploy confidential computing in a cloud environment, such as executing an existing Redis database unprotected, running within a confidential cloud, etc. Introducing Confidential Computing V2 Architecture Implementation Timeline to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Redis Database Unprotected, Execute Within Confidential Cloud, Breach Data Perimeter, using this template. Grab it now to reap its full benefits.
-
 Confidential Computing V2 Budget For Implementing Confidential Computing Architecture
Confidential Computing V2 Budget For Implementing Confidential Computing ArchitectureThis slide describes the implementation cost of confidential computing, including required tools, hardware and software costs, and other expenditures. The purpose of this slide is to showcase the estimated cost, actual cost and variance. Deliver an outstanding presentation on the topic using this Confidential Computing V2 Budget For Implementing Confidential Computing Architecture. Dispense information and present a thorough explanation of Confidential Computing Architecture, Cost Of Confidential Computing, Hardware And Software Costs using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Confidential Computing V2 Checklist To Implement Confidential Computing Architecture
Confidential Computing V2 Checklist To Implement Confidential Computing ArchitectureThis slide depicts the checklist to implement confidential computing architecture in a cloud environment. The purpose of this slide is to showcase the various steps to be taken to deploy confidential computing, including its status and the responsible person. Deliver an outstanding presentation on the topic using this Confidential Computing V2 Checklist To Implement Confidential Computing Architecture. Dispense information and present a thorough explanation of Confidential Computing Architecture, Responsible Person, Cloud Environment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Implement Green Cloud Computing Green IT
Checklist To Implement Green Cloud Computing Green ITThis slide describes the checklist to implementing green cloud computing in a company. The purpose of this slide is to showcase the different strategies to implement green IT, including knowing when to use the cloud, offsetting carbon emissions, green cloud architecture, and choosing the right cloud service. Present the topic in a bit more detail with this Checklist To Implement Green Cloud Computing Green IT. Use it as a tool for discussion and navigation on Cloud, Computing, Responsible. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Roadmap To Implement Green Cloud Computing Green IT
Roadmap To Implement Green Cloud Computing Green ITThis slide outlines the roadmap to implement green cloud computing in the organization. The purpose of this slide is to showcase the various steps organizations should take while deploying green cloud computing, including implementing energy efficient building systems, installing power efficient lighting systems, etc. Increase audience engagement and knowledge by dispensing information using Roadmap To Implement Green Cloud Computing Green IT. This template helps you present information on five stages. You can also present information on Reflective, Deactivate, Equipment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Timeline To Implement Green Cloud Computing Green IT
Timeline To Implement Green Cloud Computing Green ITThis slide outlines the timeline to implement green cloud computing in an organization. The purpose of this slide is to showcase the steps to be taken by businesses to implement green cloud computing, including selecting a carbon aware provider, optimizing the cloud environment, ensuring solid carbon measurement and reporting plans, etc. Increase audience engagement and knowledge by dispensing information using Timeline To Implement Green Cloud Computing Green IT. This template helps you present information on six stages. You can also present information on Provider, Reporting, Innovating using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Checklist For Implementing Quantum Computing Modern Technologies
Checklist For Implementing Quantum Computing Modern TechnologiesThis slide displays the implementation checklist for quantum computing in the workplace. Additionally,it lists the steps and their outcomes,the person in control of the procedure,and the state of the current stage.Deliver an outstanding presentation on the topic using this Checklist For Implementing Quantum Computing Modern Technologies. Dispense information and present a thorough explanation of Desired Result,Evaluate Revenue,Finding Relevant using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Computer Shop Business Plan Implementing Yearly Milestones For Successful Growth Of Start BP SS
Computer Shop Business Plan Implementing Yearly Milestones For Successful Growth Of Start BP SSThe purpose of this slide is to facilitate managers to convey project progress updates to stakeholders and get their approvals. The slide portrays key milestones of the computer shop to be achieved in the year 1, year 3, and years 5 onwards. Increase audience engagement and knowledge by dispensing information using Computer Shop Business Plan Implementing Yearly Milestones For Successful Growth Of Start BP SS. This template helps you present information on three stages. You can also present information on Loyalty Program, Incentivize Repeat Business, Encourage Existing Customers, Customer Engagement Initiatives using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Solutions To Mitigate Fog Computing Implement Challenges
Solutions To Mitigate Fog Computing Implement ChallengesThe following slide outlines solutions to mitigate edge computing implementation challenges, focusing on key points such as network bandwidth, distributed computing, latency, security, and management control. This visual aid provides insights into addressing crucial aspects for a successful fog computing deployment. Presenting our well structured Solutions To Mitigate Fog Computing Implement Challenges. The topics discussed in this slide are Aspect, Challenges, Solutions. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Current Trending Technologies Checklist For Implementing Quantum Computing
Current Trending Technologies Checklist For Implementing Quantum ComputingThis slide displays the implementation checklist for quantum computing in the workplace. Additionally, it lists the steps and their outcomes, the person in control of the procedure, and the state of the current stage. Deliver an outstanding presentation on the topic using this Current Trending Technologies Checklist For Implementing Quantum Computing. Dispense information and present a thorough explanation of Quantum Computing, Draft A Clear Motive, Evaluate Revenue, Expenses And Risk using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 New Technologies Checklist For Implementing Quantum Computing
New Technologies Checklist For Implementing Quantum ComputingThis slide displays the implmentation checklist for quantum computing in the workplace. Additionally, it lists the steps and their outcomes, the person in control of the procedure, and the state of the current stage. Deliver an outstanding presentation on the topic using this New Technologies Checklist For Implementing Quantum Computing. Dispense information and present a thorough explanation of Implementing, Quantum, Computing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Process To Implement Fuzzy Logic In Computational Intelligence
Process To Implement Fuzzy Logic In Computational IntelligenceThe purpose of this slide is to showcase a process involved in implementation of fuzzy logic computational intelligence technique. It covers various stages such as defining linguistic terms, membership function creation, rule construction, fuzzification and defuzzification Presenting our set of slides with Process To Implement Fuzzy Logic In Computational Intelligence. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Function Creation, Rule Construction, Established Rules.




